#SOC. network
Explore tagged Tumblr posts
Text
I feel like maybe my biggest problem is that the vast majority if not all of the club is able bodied and it's a sport designed for able-bodied people so I feel extremely singled out as the cripple™ just by virtue of being there and it's not like actively malicious or anything like that it's just yeah.
#it also feels very straight#and that's a bit unfair I haven't like asked anyone's sexuality and nobody has a problem with me being trans/queer#it's more that everything else i do is full of queer people lol.#like wheelchair fencing disabled student network folk soc is all very very queer and trans
4 notes
·
View notes
Text
NETFLIX COUNT YOUR FUCKING DAYS
8 notes
·
View notes
Text
SOC + SIEM=A game-changer for your IT security

SOC (Security Operations Center) and SIEM (Security Information and Event Management) are essential for robust cybersecurity. SOC is like a 24/7 guard, continuously monitoring and responding to threats. SIEM, on the other hand, is the brains of the operation—collecting, analyzing, and correlating security data to detect potential issues. When combined, they offer unparalleled protection: SOC identifies threats in real-time, while SIEM makes sense of the complex data to uncover hidden risks. Century Solutions Group harnesses this powerful duo, providing tailored SOC and SIEM solutions to protect your business, detect threats early, and ensure your IT infrastructure remains secure and resilient.
Read more: https://centurygroup.net/the-essential-role-of-soc-and-siem-in-modern-cybersecurity-why-every-business-needs-these-it-solutions/
#SOC #SIEM #CyberDefense #cybersecurity #cybercrime #infosec #cyberawareness #cyberattack #networksecurity #dataprotection #datasecurity #cyberthreats #security #informationsecurity #itsecurity #cyber #cybersecurityawareness #ethicalhacking #cybersecuritytraining #cyberprotection #cyberattacks #hacking #phishing #databreach #cloudsecurity #cyberaware #hacker
#SOC#SIEM#cyberdefense#Cybersecurity#Cybercrime#Infosec#Cyberawareness#cyberattack#Network Security#Data Protection#Cyber Protection
1 note
·
View note
Text
NOC vs. SOC

NOC vs. SOC – While a NOC (Network Operations Center) focuses on network performance and uptime, a SOC (Security Operations Center) safeguards systems from cyber threats. Both play vital roles in IT infrastructure but serve different missions.
0 notes
Text
Palo Alto Networks Acquires IBM’s QRadar SaaS Assets: Revolutionizing Cybersecurity with AI-Powered Security Solutions #technology #news
Palo Alto Networks Completes Acquisition of IBM’s QRadar SaaS Assets: A Landmark Move in Cybersecurity In a major strategic move that highlights the shifting dynamics in the global cybersecurity landscape, Palo Alto Networks, the global cybersecurity leader, recently announced the completion of its acquisition of IBM’s QRadar Software as a Service (SaaS) assets. This transaction not only…
#AI in Cybersecurity#AI-Powered Security#Cortex XSIAM#Cyber Threat Prevention#Cybersecurity Acquisition#IBM Consulting#IBM QRadar#Managed Security Services#Palo Alto Networks#SOC Innovation
0 notes
Text
0 notes
Text
Understanding the Vital Difference Between NOC and SOC Support: A Comprehensive Guide
Difference Between NOC And SOC Support
Introduction:
In today's digitally-driven world, businesses rely heavily on their IT infrastructure to operate efficiently. With the increasing complexity of networks and the evolving threat landscape, the need for robust support services has become more critical than ever. Two key pillars of IT infrastructure support, Network Operations Center (NOC) and Security Operations Center (SOC), play distinct yet interconnected roles in ensuring the smooth functioning and security of IT environments. In this guide, we'll delve into the nuances of NOC and SOC support, highlighting their differences, functions, and significance in modern business operations.

NOC (Network Operation Center) Support:
The Network Operations Center (NOC) is the nerve centre of an organization's IT infrastructure. It is primarily responsible for monitoring and managing the health, performance, and availability of network devices, servers, and applications. NOC engineers proactively detect and address network issues to minimize downtime and ensure optimal performance.
Key functions of NOC support include:
Monitoring Network Infrastructure: NOC engineers use advanced monitoring tools to continuously monitor network devices, including routers, switches, and servers, to identify performance bottlenecks, network congestion, or hardware failures promptly.
Incident Management: In the event of a network outage or performance degradation, NOC engineers spring into action to troubleshoot and resolve the issue swiftly. They follow predefined protocols and escalation procedures to ensure timely resolution and minimal impact on business operations.
Performance Optimization: NOC teams analyze network traffic patterns and performance metrics to identify opportunities for optimization. This may involve adjusting network configurations, deploying additional resources, or implementing performance-tuning measures to enhance network efficiency.
SOC (Security Operation Center)Support:
While NOC focuses on monitoring and managing network infrastructure, the Security Operations Center (SOC) protects organizations against cybersecurity threats. SOC analysts are tasked with detecting, analyzing, and responding to security incidents to safeguard sensitive data and mitigate risks. Key functions of SOC support include:
Threat Detection: SOC analysts leverage advanced security tools and technologies to monitor network traffic, log data, and system events for signs of suspicious or malicious activity. They employ techniques like intrusion detection, threat intelligence analysis, and behaviour analytics to detect and classify security threats accurately.
Incident Response: When a security incident is detected, SOC analysts initiate a rapid response process to contain the threat, investigate the root cause, and mitigate its impact. This may involve isolating compromised systems, conducting forensic analysis, and implementing remediation measures to prevent future occurrences.
Security Monitoring and Analysis: SOC teams continuously monitor security events and alerts to identify emerging threats and vulnerabilities. They analyze security logs, conduct threat-hunting activities, and collaborate with threat intelligence sources to stay ahead of evolving cyber threats.
Difference Between NOC and SOC Support:
While NOC and SOC support share a common goal of ensuring the reliability and security of IT infrastructure, they differ significantly in their focus, scope, and objectives. Here's a concise comparison of NOC and SOC support:
Focus:
NOC Support: Primarily focuses on monitoring and managing network infrastructure to ensure optimal performance and availability.
SOC Support: Primarily focuses on detecting, analyzing, and responding to cybersecurity threats to protect against data breaches and unauthorized access.
Function:
NOC Support: Manages network devices, servers, and applications, optimises performance, and resolves network issues.
SOC Support: Monitors security events, detects and responds to security threats, conducts incident response, and enhances cybersecurity posture.
Objective:
NOC Support: Aims to maintain network uptime, optimize performance, and ensure seamless business operations.
SOC Support: Aims to protect sensitive data, mitigate cybersecurity risks, and prevent security breaches and incidents.
Conclusion:
In conclusion, NOC and SOC support are indispensable components of modern IT operations, each playing a crucial role in ensuring the reliability, performance, and security of organizational networks. While NOC focuses on managing network infrastructure and maintaining uptime, SOC is dedicated to protecting against cybersecurity threats and mitigating risks. By understanding the key differences between NOC and SOC support, organizations can effectively leverage both functions to achieve a resilient and secure IT environment.
#it infrastructure support#noc support#soc support#security operation center#network operation center#soci#soc service
0 notes
Text
Enhancing IT Security: Strategies and Best Practices

Introduction:
In the contemporary digital landscape, where businesses and individuals heavily rely on interconnected systems, ensuring robust IT security is paramount. The exponential growth of cyber threats poses significant challenges to organizations of all sizes, requiring proactive measures to safeguard sensitive data, protect privacy, and maintain operational integrity. This article explores the importance of IT security, key challenges, and effective strategies to fortify digital defenses.
Importance of IT Security:
IT security encompasses a range of measures designed to safeguard digital assets, including hardware, software, networks, and data, against unauthorized access, breaches, and cyber attacks. The consequences of security breaches can be severe, leading to financial losses, reputational damage, legal liabilities, and compromised customer trust.
With the proliferation of connected devices, cloud services, and sophisticated attack vectors, the attack surface has expanded, making organizations more vulnerable to exploitation. Consequently, investing in robust IT security frameworks is essential to mitigate risks and ensure business continuity in an increasingly volatile threat landscape.
Key Challenges in IT Security:
Despite advancements in security technologies, organizations face several challenges in maintaining effective IT security:
1. **Sophisticated Threat Landscape**: Cybercriminals leverage advanced techniques such as malware, ransomware, phishing, and social engineering to infiltrate networks and compromise systems.
2. **Insider Threats**: Malicious insiders or negligent employees pose significant risks to organizational security by intentionally or inadvertently disclosing sensitive information or engaging in malicious activities.
3. **Compliance Requirements**: Organizations must adhere to regulatory mandates and industry standards governing data protection and privacy, such as GDPR, HIPAA, PCI DSS, and SOX, which impose stringent requirements and penalties for non-compliance.
4. **Resource Constraints**: Limited budgets, shortage of skilled cybersecurity professionals, and competing priorities often constrain organizations' ability to implement comprehensive security measures.
Strategies for Enhancing IT Security:
To address these challenges and bolster IT security posture, organizations can adopt the following strategies and best practices:
1. **Risk Assessment and Management**: Conduct regular risk assessments to identify potential threats, vulnerabilities, and impact on critical assets. Develop risk management frameworks to prioritize mitigation efforts and allocate resources effectively.
2. **Implement Multi-Layered Defense Mechanisms**: Deploy a multi-layered approach to security, combining preventive, detective, and corrective controls at the network, host, and application layers. This includes firewalls, intrusion detection systems (IDS), antivirus software, endpoint protection, encryption, and access controls.
3. **User Education and Awareness**: Foster a culture of security awareness among employees through training programs, workshops, and simulated phishing exercises. Educate users about common threats, phishing scams, password hygiene, and best practices for safeguarding sensitive information.
4. **Regular Software Patching and Updates**: Keep software, operating systems, and firmware up-to-date with the latest security patches and fixes to address known vulnerabilities and mitigate potential exploitation by attackers.
5. **Secure Configuration Management**: Harden system configurations, disable unnecessary services, and enforce least privilege access controls to minimize the attack surface and limit the impact of security incidents.
6. **Data Encryption and Privacy Controls**: Encrypt sensitive data both in transit and at rest using robust encryption algorithms and cryptographic protocols. Implement data loss prevention (DLP) solutions and access controls to prevent unauthorized disclosure or misuse of confidential information.
7. **Incident Response and Contingency Planning**: Develop incident response plans outlining procedures for detecting, analyzing, and responding to security incidents promptly. Establish communication channels, escalation paths, and recovery strategies to minimize downtime and restore normal operations.
8. **Continuous Monitoring and Auditing**: Deploy security information and event management (SIEM) solutions to monitor network traffic, detect suspicious activities, and generate real-time alerts. Conduct regular security audits, penetration testing, and vulnerability assessments to identify weaknesses and remediate security gaps proactively.
Conclusion:
In conclusion, prioritizing IT security is imperative for organizations to mitigate cyber risks, protect critical assets, and preserve stakeholder trust in an increasingly interconnected world. By adopting proactive measures, leveraging best practices, and fostering a culture of security awareness, organizations can strengthen their resilience against evolving threats and maintain a competitive edge in today's digital landscape. Remember, in the realm of cybersecurity, vigilance and preparedness are key to staying one step ahead of adversaries and safeguarding the integrity of digital ecosystems.

#Cybersecurity Analyst#Information Security Specialist#IT Security Consultant#Network Security Engineer#Security Operations Center (SOC) Analyst#Penetration Tester (Ethical Hacker)#Chief Information Security Officer (CISO)#Security Architect#Security Compliance Officer#Incident Response Analyst
0 notes
Text
– « My family, my comrades, my homeland… They disappeared forever under the onslaught of the Abyss.

This is an ongoing pain, and no amount of time can numb it… even five hundred years.

I could not save the Khaenri'ah from the ravages of the Abyss…

And I can't just lose you, Mavuika. »
My navigation card 🌸
[ soc networks · commission · donate ]
#my art#genshin fanart#genshin impact#mmd#capitano#il capitano#genshin capitano#capitano genshin#mavuika#genshin impact fatui#natlan#genshin spoilers#genshin#genshin mavuika#genshin fanfic#5.2 spoilers#abyss#мавуика#капитано#MMD#mavuitano#fatui fanart#fatui capitano#fatui harbingers
461 notes
·
View notes
Text

The Kingdom of Mapungubwe: An In-Depth Analysis of Southern Africa’s First Great Civilization
Introduction: Mapungubwe – The Forgotten African Power
The Kingdom of Mapungubwe (c. 1075–1300 CE) was one of the earliest known states in Southern Africa, preceding Great Zimbabwe and laying the foundation for later powerful African empires. Located in modern-day South Africa, Botswana, and Zimbabwe, Mapungubwe was a centre of trade, wealth, governance, and advanced social organization.
Despite its historical significance, Eurocentric narratives often ignore or downplay Mapungubwe’s role in African civilization, falsely portraying Africa as “uncivilized” before European contact. From a Garveyite perspective, studying Mapungubwe is essential because it represents:
Black economic success – Mapungubwe controlled Southern Africa’s early gold trade.
Black architectural and governance excellence – It had organized cities and a structured ruling system.
Black global influence – Mapungubwe’s trade networks extended to the Middle East, India, and China.
By understanding the Kingdom of Mapungubwe, Black people today can reclaim their lost history, reject colonial distortions, and recognize Africa’s early global impact.
1. The Origins and Rise of the Kingdom of Mapungubwe
A. Geographic and Strategic Importance
Mapungubwe was located at the confluence of the Limpopo and Shashe Rivers, making it a key trade hub in Southern Africa.
The region had fertile land for agriculture, abundant cattle, and access to gold, making it economically prosperous.
The kingdom’s rulers established a socially stratified society, separating elite rulers from commoners—a system that later influenced Great Zimbabwe.
Example: The Mapungubwe Hill, a sacred royal centre, symbolized the kingdom’s centralized leadership and class-based society.
Key Takeaway: African civilizations were highly structured, organized, and rich in resources long before European contact.
2. The Economic and Trade Power of Mapungubwe
A. Gold, Ivory, and the Rise of African Trade
Mapungubwe was one of the earliest African states to exploit gold mining, exporting gold to Swahili coastal cities, the Middle East, and Asia.
The kingdom also traded in ivory, copper, animal hides, and ceramics, making it a key supplier in the early African economy.
Gold from Mapungubwe was transported to Kilwa, Sofala, and other major Swahili trading cities, where it was exchanged for glass beads, Chinese porcelain, and luxury goods.
Example: Archaeological excavations have uncovered Chinese porcelain, Indian glass beads, and Arabian goods, proving that Mapungubwe was linked to the global economy centuries before European exploration.
Key Takeaway: Africa was not isolated—Mapungubwe’s wealth fueled a sophisticated global trade network before European colonization.
B. Agricultural and Cattle Economy
Mapungubwe’s people were also skilled agriculturalists, growing crops such as sorghum, millet, and beans to sustain their population.
The kingdom raised large herds of cattle, which were not only a source of food but also a symbol of wealth and social status.
The economy was so advanced that wealthy families lived in stone homes, while commoners lived in well-structured settlements.
Example: Cattle and grain were taxed, and surpluses were stored in granaries, showing that Mapungubwe had a regulated economy and a taxation system.
Key Takeaway: Africa’s economic systems were sophisticated, with taxation, surplus storage, and wealth redistribution.
3. The Political and Social Organization of Mapungubwe
A. A Centralized Monarchy and Class System
The king ruled from Mapungubwe Hill, separating himself from the common people, showing a class-based hierarchy.
The ruling class controlled trade, wealth, and religious ceremonies, reinforcing their power.
Unlike previous African societies that were more egalitarian, Mapungubwe introduced a system where royalty and the elite were separate from the working class.
Example: This system of social separation was later adopted by Great Zimbabwe and other successor states in Southern Africa.
Key Takeaway: Africa had complex governance systems with structured leadership, taxation, and social classes.
B. Religious and Cultural Practices
The kingdom’s religion was deeply rooted in ancestor worship and spiritual connections to the land.
Rulers were seen as divine or semi-divine figures, reinforcing their authority through spiritual beliefs.
The elite class performed ceremonial rituals on Mapungubwe Hill, which was considered sacred.
Example: The Golden Rhino of Mapungubwe, one of Africa’s most famous artifacts, symbolizes the royalty and religious significance of the king.
Key Takeaway: African civilizations had spiritual and political institutions that reinforced governance and stability.
4. The Decline of Mapungubwe and the Rise of Great Zimbabwe
A. Environmental and Economic Factors
Around 1300 CE, Mapungubwe declined due to climate change, specifically a severe drought that affected food production and trade.
The gold trade shifted further north, leading to the rise of Great Zimbabwe, which became the new center of power in Southern Africa.
Internal conflicts and population movements also contributed to the kingdom’s decline.
Example: Great Zimbabwe (1300–1450 CE) inherited many of Mapungubwe’s political and economic traditions, proving that African civilizations evolved and adapted.
Key Takeaway: African civilizations didn’t simply “disappear” as colonial historians claim—they transformed into new political entities.
5. The European Suppression of Mapungubwe’s History
A. Colonial Erasure and Historical Racism
When European archaeologists discovered Mapungubwe in the 1930s, they attempted to suppress its significance to maintain the colonial myth that Africans had no history.
The Golden Rhino and other artifacts were hidden for decades, because they proved that Africans had advanced civilizations before colonialism.
South Africa’s apartheid government censored Mapungubwe’s history, fearing it would empower Black South Africans by proving their rich heritage.
Example: The Golden Rhino was kept hidden until the 1990s, when post-apartheid South Africa finally acknowledged the greatness of Mapungubwe.
Key Takeaway: Colonial powers deliberately erased African history to justify oppression—our job is to restore the truth.
6. The Garveyite Vision: Reclaiming the Legacy of Mapungubwe
Africa must reclaim its economic independence, just as Mapungubwe controlled its own gold trade.
Black people must rebuild strong governance systems, inspired by Mapungubwe’s centralized leadership.
Pan-African unity is necessary—African nations must work together, just as Mapungubwe influenced later African states.
African history must be decolonized, ensuring that the legacy of Mapungubwe is properly taught worldwide.
Final Thought: Will We Reclaim Mapungubwe’s Legacy?
Marcus Garvey said:
“A people without the knowledge of their past history, origin, and culture is like a tree without roots.”
Will Black people allow our history to remain hidden, or demand its full recognition?
Will we continue to depend on foreign economies, or reclaim Africa’s economic power?
Will we build new African empires, or allow our civilization’s achievements to be forgotten?
The Choice is Ours. The Time is Now.
#black history#black people#blacktumblr#black tumblr#black#pan africanism#black conscious#africa#black power#black empowering#blog#Mapungubwe#african kingdom#black excellence#south africa#botswana#zimbabwe#african history#garveyism#garveyite#ReclaimOurHistory
54 notes
·
View notes
Text

DEEP-SEA DOMINANCE: THE SUPERGIANT AMPHIPOD ACROSS THE ABYSS
The deep-sea amphipod Alicella gigantea, described in 1899, currently known as the world’s largest amphipod, inhabits depths of the lower abyssal and upper hadal zones. Historically, it has been sampled or observed in situ infrequently relative to other deep-sea amphipods, suggesting low population densities and providing a sense of rarity. Consequently, little is known about the demography, genetic variation and population dynamics of A. gigantea.
Although elusive, Alicella gigantea is one of the most widely distributed amphipods known, thriving across more than half of the world’s oceans, according to a recent study by researchers at the University of Western Australia. Amphipods like A. gigantea are shrimp-like crustaceans with narrow bodies and a distinctive hunched posture. They inhabit nearly every aquatic habitat on Earth, from shallow coasts to the hadal trenches, though their numbers dwindle with increasing depth.
In the most comprehensive assessment to date, scientists compiled 195 records from 75 locations across the Pacific, Atlantic, and Indian Oceans, including both published data and new expeditions. Genetic analysis of mitochondrial and nuclear genes revealed extremely low divergence among global populations, supporting the existence of a single, globally distributed species. The haplotype network showed minimal regional differentiation, with shared haplotypes across vast distances and the Pacific identified as the species’ main stronghold. Far from being rare, A. gigantea occupies nearly 60% of the global ocean, a silent giant spanning the deep.
Main photograph: The supergiant amphipods. Oceanlab, University of Aberdeen, UK.
Reference (Open Access): Paige et al., 2025. The supergiant amphipod Alicella gigantea may inhabit over half of the world’s oceansR. Soc. Open Sci.
21 notes
·
View notes
Text
ㅤㅤㅤ ੭୧ a night to remember
𝘰𝘳 𝘳𝘢𝘵𝘩𝘦𝘳 a break-in forms a relationship between strangers, 심재윤 x fem reader, ✶ warnings . . . fluff, crack, periods, suggestive jokes, profanity soc med au strangers to lovers ! 𝐑𝐄𝐀𝐃 𝐓𝐇𝐄 𝐂𝐀𝐓𝐀𝐋𝐎𝐆𝐔𝐄 . . .
𝓛iAS NOTE : it's been a good minute since i last posted :p I'M BACK BBYS



more under the cut!




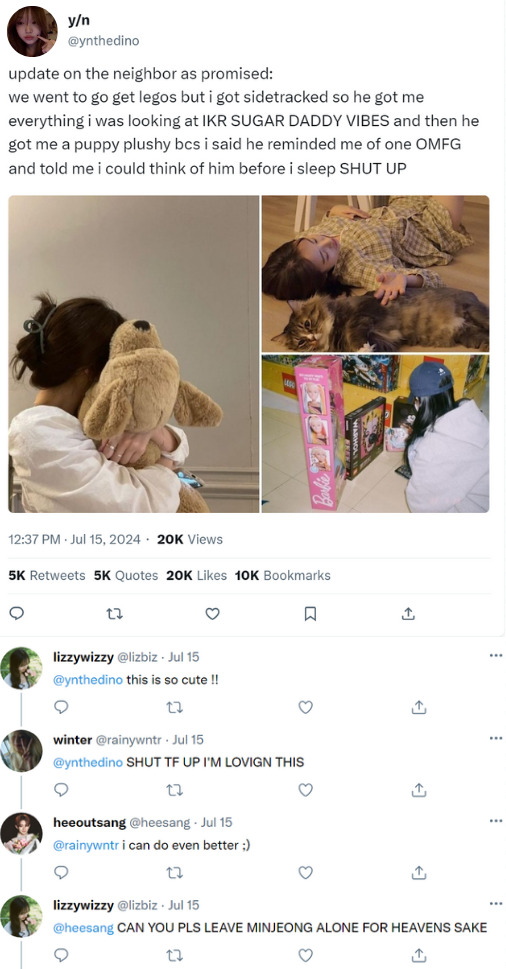




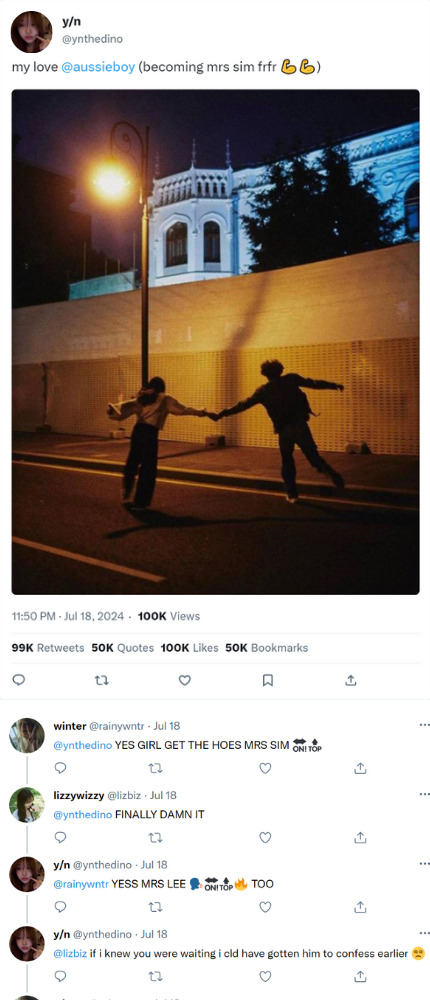

PERMANENT TAGLIST : @07sleepykatz @moknu @bunnbam @jlheon @luvlyhee @flwrstqr @sunrenity @jakesprincess1 ( to join, click here ! ) networks : @enhablr @enchive, © EN-GELIC, 2024
#✶ : iT GiRL#≋ 𝑠ℎ𝑒 𝑤𝑟𝑖𝑡𝑒𝑠#enchive#enhablr#[⠀ㅤㅤㅤboyfhee ੭୧ 𝓌heel of 𝒻ate ]#enhypen imagines#enhypen fluff#enhypen scenarios#enhypen soft hours#enhypen fanfiction#enhypen drabbles#enhypen reactions#enhypen headcanons#enha#enha fluff#enha x reader#jake x reader#jake fluff#jake imagines#jake sim#enhypen jake#jake enhypen#sim jaeyun#enhypen#enhypen x reader#enhypen smau
89 notes
·
View notes
Note
based on the hcs uve been writing wb darry in high school when he was the golden child and his relationship between being from the east side but all his friends are west side
Tbh I’ve always been curious about what Darry was actually like in high school. In pretty much every medium of the work, it’s made clear that Darry almost “went Soc” or would have become a Soc had the Curtis parents not died. Either way, Darry’s Soc-y persona didn’t just drop when he came back to the East side.
I think of it as Darry feeling ostracized by the greasers for his decisions, so he falls back on the Socs, people who seem to actually be his friends *or* can give him an edge socially. Call it networking. But obviously, when push comes to shove, the Socs were never going to let Darry lean on them with real problems he’s having, they mock those kinds of things. So Darry’s dug himself into a hole at that point. He can’t be real with greasers because he’s associated too heavily with Socs, and he can’t be real with Socs because not only is he still too much of a greaser, Socs don’t even talk about their problems with each other, it’s taboo.
The problem is absolutely exacerbated by the fact that his parents likely never graduated high school and/or went to college, so Darry pushing so hard for his education and making a life for himself someplace better than Tulsa was encouraged by the Curtises.
Something even more interesting is Pony and Soda’s reactions to Darry’s past with the Socs. Pony doesn’t really comment that much on it, and staying in line with his own wishes to see more beyond Tulsa, I don’t think he blames him that much, or can at least understand it. He pretty much does the same thing with Cherry after all.
In the musical, Soda denies it even happened when Dally accuses Darry of having almost gone Soc. At first I thought maybe it could have been embarrassment, but I seriously doubt that now. Especially now, with all the weight Darry carries having to be the sole caretaker and provider for the brothers, Soda might understand better the appeal at running with the West side where money’s rarely a problem, even if he didn’t before. But also, he’s protective of Darry’s cracked reputation on both the East and West side.
So overall, you can’t help but feel bad for Darry even during high school. His West side friends are snobbish and mock the issues that not only greasers have, but Darry has, and will switch up on him if he says or does something out of line. Meanwhile is East side friends hate the Socs on principle for constantly beating up on them, so Darry’s caught in a massive divide that, no matter how it ends, will involve a massive sacrifice of either his home or his dreams.
So yeah. I don’t think Darry was ever going to win even if the Curtis parents had lived. In “Throwing in the Towel” he says that they were damned from the beginning, but you can honestly argue that Darry was damned from the beginning.
#darry curtis in the top three tragedies jfc#the outsiders#the outsiders darry#darry curtis#the outsiders headcanons#the outsiders musical#the outsiders ponyboy#the outsiders sodapop
35 notes
·
View notes
Text
SOC (Security Operation Center) Service Providers in India

ACS Networks & Technologies provides Security Operations Center (SOC) solutions designed to expedite businesses' technology transitions. These solutions leverage cloud services, cybersecurity measures, networking capabilities, data centers, digital workplaces, and IT-managed services. ACS Networks & Technologies employs cybersecurity tactics to safeguard business interests, uphold strict confidentiality regarding data and operations, facilitate virtual discussions, and ultimately contribute to their financial growth.
#security operation center#soc support#soc service#soc support in india#security operation center support#acs networks & technologies
0 notes
Note
heyyy hii hello [curiosity voice] how did u decide on spsx for yourself over the other 5 ivs? what was the Process? :3
OKAY so as you might have guessed i just had to fish this out of my inbox after like a week... tumblr needs to pay et cetera. anyway. putting this under a cut because it's. kinda embarrassing and a lot of text but we're on tumblr so. whatever
tbh. the easiest and most important part was figuring out i'm soc blind... i'm weird i'm a weirdo have you ever seen me without this hat on. that's weird. i just suck at all things social tbh. which. is not that easy to pick up on (hopefully) these days because i'm working in a field that requires me to talk to all kinds of people on a daily basis but before? that was a catastrophe. to give you a rough idea of how bad it was my closest irl friend throughout high/middle school had to act as a messenger between me and teachers/classmates/etc because i just. did not know how to communicate with those people in an appropriate manner. i had a few people i was somewhat close with irl and outside of school i could only be bothered to hang out with one (1) of them. and even then i lied my ass off about my family being strict just so i could avoid doing it regularly because. i just did not feel the need to. mind you it wasn't because i did not like her/did not want to talk to her or something, i just really couldn't be bothered to do all that that often and did not see why she wanted to. wait now that i think of it is this more of a sp dom thing than soc blind... or Both... regardless tl;dr is i cannot network for the life of me. i'm not clueless to the way it works etc etc (tert fe o7) but i just. cannot do it in a way that doesn't feel off. even if i know what i need to do in theory.
what's even funnier is that like. it's really obvious that whatever social skills i have right now are very much taught the hard way (by having the same conversations over and over again at work) and not actually learned because everything work-related i do i do in my fourth language and the moment i have to do it in any other language my social filter disappears like. i went to see my dentist yesterday and the thing with their practice is. all of them speak russian as well and the moment they decided to switch to it with me it became a disaster bc all of a sudden i had no idea how to hold a friendly small talk adjacent conversation in a way that wouldn't get me weird looks. and since we're talking dentists: the only coworker i was on more or less friendly terms with at my former workplace was the coworker i could regularly spend the entire 2 hours of our break talking about politics since we're both from. uh. areas that have seen a lot, basically. like unfortunately that's my way of casually bonding with ppl at workplace. ANYWAY...
deciding between sp/sx vs sx/sp was very much a no brainer for me. i'm like. kind of the stereotypical sp dom unfortunately. no matter how much i feed my sx (which i do. a lot. lmao) at the end of the day i always end up prioritizing my sp needs. like having a strictly maintained comfort zone is one of the things i'm borderline mental about unfortunately. like mental-mental. so there's that
5 notes
·
View notes
Text
First Pride festival with people.
I came out last summer (2023) and got invited to join my coworkers at our local Pride parade and festival. I was still waaaay to new to all of this, so I showed up as the company photographer, so I could be there without really being there. Disappearing into a role/task.
A few weeks earlier, while I was coming out, I wandered around the Pride festival in Vancouver (I came out while on vacation), taking in the atmosphere, but basically keeping to myself and off the radar. Soon after, I did the same solo-stop-in on the Banff Pride events, coincidentally timed with a workplace retreat that I was the photographer for. In my mind it still counted, but it felt a bit… less. This felt like an experience to share.
It took me a few months after coming out to really feel part of the 2SLGBTQIA+ scene at work (it’s Canada we prefix LGBTQIA+ with 2S for the Two Spirit category the First Nations people use). But a year later, I’m on the committee that organizes the Pride Team Member Network (as a Loveless nerd, I mentally call it Pride Soc), and today in an hour or so, I’m meeting up with coworker friends to watch the parade and stroll over to the festival.
Out, proud, sharing the experience with friends, feeling accepted, being included, and absolutely nervous as fuck about getting it all wrong. 🤣
That’s still progress. 😁
Follow-up 1 of 3: It went great. I stressed out about nothing, like I often do.
Follow-up 2 of 3: There was lots of Aspec representation!
Follow-up 3 of 3: A small but maybe meaningful little way to let others, who can’t go to a pride event yet, know they were represented there.
18 notes
·
View notes