#Cyber Protection
Explore tagged Tumblr posts
Text
23 notes
·
View notes
Text
SOC + SIEM=A game-changer for your IT security

SOC (Security Operations Center) and SIEM (Security Information and Event Management) are essential for robust cybersecurity. SOC is like a 24/7 guard, continuously monitoring and responding to threats. SIEM, on the other hand, is the brains of the operation—collecting, analyzing, and correlating security data to detect potential issues. When combined, they offer unparalleled protection: SOC identifies threats in real-time, while SIEM makes sense of the complex data to uncover hidden risks. Century Solutions Group harnesses this powerful duo, providing tailored SOC and SIEM solutions to protect your business, detect threats early, and ensure your IT infrastructure remains secure and resilient.
Read more: https://centurygroup.net/the-essential-role-of-soc-and-siem-in-modern-cybersecurity-why-every-business-needs-these-it-solutions/
#SOC #SIEM #CyberDefense #cybersecurity #cybercrime #infosec #cyberawareness #cyberattack #networksecurity #dataprotection #datasecurity #cyberthreats #security #informationsecurity #itsecurity #cyber #cybersecurityawareness #ethicalhacking #cybersecuritytraining #cyberprotection #cyberattacks #hacking #phishing #databreach #cloudsecurity #cyberaware #hacker
#SOC#SIEM#cyberdefense#Cybersecurity#Cybercrime#Infosec#Cyberawareness#cyberattack#Network Security#Data Protection#Cyber Protection
1 note
·
View note
Text

#cybersecurity threat#cyber security services#cyber protection#phishing in cyber security#malware attack#data encryption#financial services industries#financenu
0 notes
Text
Safeguarding the Digital Realm: Exploring the Vitality of Cybersecurity
In today’s interconnected world, where the internet serves as the backbone of communication, commerce, and information exchange , the importance of cybersecurity cannot be overstated.
From personal data breaches to large-scale cyber attacks on governments and corporations, the digital landscape is fraught with threats that constantly evolve in sophistication and scale.
As we navigate this complex ecosystem, understanding the significance of cybersecurity becomes paramount to protecting our privacy, safeguarding our assets, and preserving the integrity of our digital infrastructure.

The Cyber Threat Landscape
Cyber threats come in various forms, ranging from malware and phishing attacks to ransomware and DDoS (Distributed Denial of Service) assaults.
These threats exploit vulnerabilities in software, networks, and human behavior to gain unauthorized access, steal sensitive information, or disrupt critical services.
Best Safeguarding the Digital Realm: Exploring the Vitality of Cybersecurity-2024.
With the proliferation of connected devices and the advent of the Internet of Things (IoT), the attack surface has expanded exponentially, presenting new challenges for cybersecurity professionals and organizations worldwide.
The Stakes of Cybersecurity
The consequences of cyber attacks can be severe and far-reaching, impacting individuals, businesses, and governments alike. For individuals, falling victim to identity theft or financial fraud can result in substantial financial losses and emotional distress.
Moreover, the compromise of personal data can lead to reputational damage and undermine trust in online services and platforms. Best Safeguarding the Digital Realm: Exploring the Vitality of Cybersecurity-2024. In the corporate sphere, data breaches can have devastating implications, ranging from regulatory fines and legal liabilities to loss of intellectual property and market competitiveness.
Moreover, the disruption of business operations due to cyber attacks can result in significant revenue losses and damage to brand reputation. In extreme cases, cyber attacks targeting critical infrastructure, such as power grids and transportation systems, can pose a threat to public safety and national security.
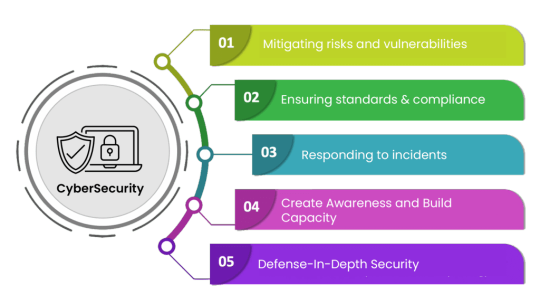
The Role of Cybersecurity
In light of these challenges, the role of cybersecurity is to mitigate risks, detect threats, and respond effectively to cyber incidents. This encompasses a wide range of measures and practices aimed at fortifying defenses, enhancing resilience, and fostering a culture of security awareness. Best Safeguarding the Digital Realm: Exploring the Vitality of Cybersecurity-2024 Some key pillars of cybersecurity include:
1. Risk Management
Identifying and prioritizing potential risks based on their likelihood and impact is essential for allocating resources effectively and implementing appropriate controls. This involves conducting risk assessments, establishing risk tolerance thresholds, and developing mitigation strategies tailored to the organization’s needs and priorities.
2. Security Controls
Implementing robust security controls is critical for protecting against a diverse array of cyber threats. This includes deploying firewalls, intrusion detection systems, antivirus software, and encryption protocols to safeguard networks and data assets.
Additionally, implementing access controls, least privilege principles, and multi-factor authentication mechanisms can help prevent unauthorized access and limit the blast radius of security incidents. Best Safeguarding the Digital Realm: Exploring the Vitality of Cybersecurity-2024.
3. Incident Response
Despite best efforts to prevent cyber attacks, breaches and incidents may still occur. An effective incident response plan enables organizations to detect, contain, and mitigate the impact of security breaches in a timely and coordinated manner.
This involves establishing clear roles and responsibilities, defining escalation procedures, and conducting regular drills and tabletop exercises to test the efficacy of response capabilities.
4. Security Awareness
Human error remains one of the weakest links in cybersecurity defenses. Educating employees and end users about common threats, phishing scams, and best practices for securely handling sensitive information is essential for fostering a security-conscious culture.
This includes providing regular training sessions, phishing simulations, and awareness campaigns to reinforce good security habits and empower individuals to become vigilant guardians of their digital assets. Best Safeguarding the Digital Realm: Exploring the Vitality of Cybersecurity-2024.
The Evolving Landscape of Cybersecurity
As technology continues to advance and cyber threats evolve, the field of cybersecurity must adapt and innovate to stay ahead of adversaries. Artificial intelligence and machine learning algorithms are increasingly being leveraged to enhance threat detection, automate incident response, and augment human capabilities in analyzing vast amounts of security data.
Moreover, the rise of cloud computing, mobile devices, and remote work arrangements has reshaped the traditional perimeter-based security model, necessitating a shift towards more dynamic and context-aware approaches to defense.
Zero-trust security architectures, micro segmentation, and secure access service edge (SASE) frameworks are emerging as key paradigms for securing distributed environments and hybrid infrastructures. Safeguarding the Digital Realm: Exploring the Vitality of Cybersecurity.
Furthermore, collaboration and information sharing among industry stakeholders, government agencies, and cybersecurity professionals are essential for fostering collective defense and addressing shared threats effectively.
Initiatives such as information sharing and analysis centers (ISACs), threat intelligence sharing platforms, and public-private partnerships play a vital role in promoting collaboration, facilitating threat intelligence exchange, and building resilience against cyber attacks.
Conclusion- Best Safeguarding the Digital Realm: Exploring the Vitality of Cybersecurity-2024
In conclusion, cybersecurity is not merely a technical challenge but a fundamental imperative for the digital age. As our reliance on technology grows, so too does the need for robust cybersecurity measures to protect our digital assets, preserve our privacy, and uphold the trust and integrity of the online ecosystem.
By investing in cybersecurity awareness, education, and innovation, we can collectively strengthen our defenses and navigate the complexities of the digital realm with confidence and resilience. Safeguarding the Digital Realm: Exploring the Vitality of Cybersecurity. Best Safeguarding the Digital Realm: Exploring the Vitality of Cybersecurity-2024.
0 notes
Text
"You're just a glitch in the system..."

Technology magick 🤳🏻:
To protect yourself from the evil eye online, you can place sigils or symbols in hidden areas of your photos_
You can either draw the sigil on your phone or on a piece paper. Take a picture of the drawing and use Picsart to cut the picture out ✂️ then make the transparency less visible. This can also apply to drawing on the Picsart app_
This method can also be used to attract abundance, love, or money. (I.E: If you have a Linkedin account, you can do this for your profile picture and do a sigil for wealth, so that way more companies will hire you)_


Use a vision board as a wallpaper on your phone to manifest your desires_
Passcodes or passwords can be used as a spell. You could make a affirmation your password or use numbers that have a special meaning_
Filters are a form of glamour magick and it can alternate your physical identity_
Making a list of your goals in your notes and can you help you keep track of what you've accomplished (use checkmarks and x's ✅️❎️)_
AI could be used for any kind or magick (baneful, prosperity, etc.) It is something I suggest people be careful using in the future, like everything else in the world it has it's positives and negatives_

"Hack complete..."
#witchcraft#wicca#hoodoo#sigil magic#cyber sigil#protection spell#glamour magick#technology witchcraft#tech#coding#stem#women in stem#stemblr#tech witch#spell#spells#sombra#overwatch#pinterest#vision board#manifest#manifestation
584 notes
·
View notes
Text
For the roleplay committee on Tumblr
---
Enough with the pathetic targeting of roleplayers on Tumblr! It's downright despicable, especially given that the majority of these creative individuals are minors. Get a grip on reality and find something better to do with your time than spewing disrespect.
LISTEN UP, if I catch wind of any more of these toxic comments, I'll make it my mission to unearth your sorry identity and ensure your account is obliterated. Consider this a warning – back off and let people enjoy their space without your mindless aggression. The consequences will be swift and severe.
To those who have been hurt by the senseless targeting on Tumblr, I offer my sincere apologies. Remember, it's not a crime to pursue your passions, including roleplaying. Don't let the negativity of others dictate what brings you joy. Do what you love, stay true to yourself, and embrace your interests without reservation. Your well-being matters, and there are supportive communities out there who appreciate and respect your creative endeavors. Keep shining and doing what makes you happy. 💙
IF YOU SEE ONE OF THESE ASSHOLES TAUNTIN' OTHER ROLEPLAYERS, TELL THEM TO FUCK OFF!
--
SPREAD THE WORD!
#PROTECT TUMBLR ROLEPLAYERS
#spread awareness#get a life#protect kids#my thoughts#haters gonna hate#roleplayers#anti harassment#cyber bullying#stop bullying
166 notes
·
View notes
Text
✨🪬🕯️ 🧘🏽🔒🏡🌳🔒🧘🏽🕯️🪬✨
“I feel calm and secure in my own environment”
#beginner witch#witchcraft#baby witch#witch tips#witchcraft 101#witchery#witches#witches of tumblr#water witch#witchblr#spellwork#protection spell#sigilism#emoji spells#spellcraft#cyber sigil#sigilcraft#sigil art#sigil magic#sigilwork#sigil#sigilyph#sigils#sigil creator#calm#peace#stillness
320 notes
·
View notes
Text



˙ . ꒷ 🪼 . 𖦹˙— Cyber harassment; 04/??

The term "Cyber harassment" describes a type of harassment that occurs online. Cyber harassment causes severe anxiety, severe depression, PTSD (Post-Traumatic Stress Disorder) symptoms, social withdrawal and increases the risks of self harm. Victims often are dismissed because their situation is usually brushed off as "internet drama". /srs
Cyber harassment is considered a crime in several countries, where fines or jail time can be applied to the perpetrators, depending on the country's legislation. /srs
We firmly condemn cyber harassment in any way, shape or form. /srs
If you happen to find any of these blogs or posts, we firmly encourage you to report and block. /srs
Viewer discretion is advised due to the hostility of certain users. /srs






The post on the first screenshot was uploaded on April 21st, 2025. There, you can see the user @/syltheanti willingly engaging one more time in online activities that could be considered harassment. Saying that an entire group of people should "die in a goddamn hole" could be interpreted as wishing harm (which Tumblr can ban if reported under Community Guidelines). Adding to that, it can count as inciting harassment with violent rethoric, since his post can encourage others to attack Pro-Shippers. Besides, complaining about mass reports could be considered hypocritical since Syl himself willingly engages in targeted cyber harassment, like you saw in previous posts. /srs
Proof of @/syltheanti purposely making up false accusations against @proship-froggo with the objective of justifying the targeted cyber harassment towards them down here ⬇️
Proof of @/syltheanti willingly engaging in cyber harassment while defending and supporting people who do that as well, can be found down there ⬇️
The post on the second screenshot was uploaded on April 22nd, 2025. You can see that both Anon and Syl have misunderstood the terms Pro-Shipp, Com-Shipp, and Dark-Shipp. But don't worry, we'll explain it just in case. /srs
Pro-Shipp (🌈🍖 / 🍖🌈) is a stance that supports the creation and enjoyment of all types of shipps involving fictional characters only, including those that might be considered controversial, problematic or taboo. Pro-Shippers believe fiction is separate from reality, and that enjoying problematic content in fiction doesn't necessarily mean endorsing it in real life. Pro-Shippers believe that both creators and fans should have the freedom to explore any type of relationship in fiction without censorship or judgement. Pro-Shippers often advocate for content warnings and tags to help others avoid content they might find triggering. /gen
Com-Shipp (🌸🌛 / 🌛🌸), short for "Complicated Shipping", refers to exploring or enjoying shipps that involve complex, messy, or morally ambiguous fictional characters. These relationships often have layers of conflict, tension or emotional depth. Com-Shippers are drawn to fictional relationships that aren't purely wholesome or healthy, but aren't toxic and abusive either. Com-Shippers like to explore themes like power imbalance, unresolved tension or emotional turmoil, something present in enemies to lovers fictional shipps, by example. Com-Shippers may acknowledge the problematic aspects of a shipp but still finding it interesting or meaningful. /gen
Dark-Shipp (🎱🎀 / 🎀🎱) is about shipping fictional characters in relationships that are explicitly dark, disturbing or taboo. These shipps often involve themes like abuse or manipulation. Dark-shippers are usually drawn to the exploration of dark or taboo themes in fiction, often for the sake of storytelling, emotional intensity, catharsis or shock value. Dark-shipps aren't meant to be normalized or romanticized but are instead explored as part of the story's darker elements (canon or fan made). Besides, most Dark-shippers don't endorse real life behavior, and they often emphasize the importance of content warnings and ethical storytelling when dealing with sensitive topics. /gen
Com-Shipp does exist. Maybe Syl just doesn't like the term "Com-Shipp", but that doesn't mean the term doesn't exist or shouldn't exist. For example, we don't like some things created on the internet, but that doesn't mean those things don't exist. Because the world doesn't revolve around anyone. /gen
And we just showed you that Pro-Shipp ≠ Dark-shipp. Not all Pro-Shippers are Dark-shippers. In fact, some Pro-Shippers are just Com-Shippers. /gen
Also, calling an entire online group of people "nasty fucks" is dehumanizing language meant to incite disdain or violence. /gen
The comment on the third screenshot was made on April 22nd, 2025. The user @/silly4goose20 appears once again. Let's remember it's not the first time she appears in those screenshots willingly engaging in cyber felonies. /srs
Proof that @/silly4goose20 has encouraged several people to commit suicide can be found here ⬇️
Telling people to get help or "take the trash out themselves"... Is this what we think it is? Another phrase similar to "you should get help but if you don't then you should kill yourself"? /srs.
Curiously, on the post on the fourth screenshot, you can see the hypocrisy of this individual. The post was originally uploaded on April 22nd, 2025. It seems like that, for @/silly4goose20 , inciting suicide online is okay, but she shouldn't receive a similar treatment. If she really was this worried about "people getting help" she would condemn suicide incitement in any way, shape or form. We hope her hypocrisy talks by itself. Even if the suicide incitement was unsuccessful (in the best case scenario), she still has blood in her hands and is acting no better than a real life abuser. /srs
The post on the fifth screenshot was originally uploaded on April 23rd, 2025. Well, this post (or reblog, better said) is less harmful than the other ones we've seen, but it can still count as mild cyber harassment. Comparing a group of people to literal trash is dehumanizing, and intended to degrade and insult. The post can serve as a public signal to @/sho-can-g 's online circle that mockery towards Pro-Shippers is acceptable. /srs
The post on the sixth screenshot was originally uploaded on April 13th, 2025. The user @/chubbibunni is not as active as the other users when it comes to shipping discourse, but her online behavior can be equally violent sometimes. There are several things wrong within this screenshot. /srs
The user @/smacksalad made a post saying that vent art / therapeutic art from survivors should be kept in private. As survivors of CSA and extreme physical abuse, we disagree with that statement. The Jellyfish system thinks survivors should be able to upload their vent or therapeutic art to online spaces, as long as they add the proper tags, as long as it's their own decision, and as long as they aren't willingly exposing vulnerable audiences to heavy and traumatizing topics. /gen
Survivors deserve to speak up and express themselves about the things they survived without being pressured to "be silent" or "backpedal". Many survivors (SA survivors, CSA survivors, physical abuse survivors, emotional abuse survivors, abandonment survivors, neglect survivors, and so on), are forced to stay quiet and silent by their own abusers or by the environment that enables their abusers, and this can go on for years or even decades. With this in mind, telling survivors to just "keep it to themselves" is not only disrespectful, but deeply unfair. Don't silence or censor survivors' voices and art. Yeah, some vent or therapeutic art can be deeply disturbing, but the best option is to block people who make that art, instead of urging them to "keep it private". /gen
The rage we feel every time we see someone saying "CP" instead of CSAM/CSEM is unreal omg (`皿´#) /gen /neg
To keep it short (and family friendly), if you want to support survivors, especially CSA survivors, use the correct terms. Using the term "CP" downplays and undermines the physical, psychological, and moral long-term damage survivors go through. Terms like CSAM and CSEM help remind people that it isn't a type of "porn genre", or "18+ entertainment". It's sexual violence against minors. Survivors deserve that clarity and acknowledgment. /gen
Purposely comparing vent art or therapeutic art from CSA victims/survivors and actual CSAM/CSEM is beyond fucked up. Let us do a quick explanation: /srs
Vent art / Therapeutic art about CSA
Made in a consensual and safe space. /srs
The minor has control over what happens and what doesn't happen. /srs
The main purpose is trauma processing and healing. /srs
The adult (in this case, the therapist) can guide the minor in their healing journey to achieve a better mental and physical well being. /srs
Usually consists of drawings, poems, or just phrases. /srs
CSAM/CSEM
Made in a non consensual and exploitative space. /srs
The minor has no control over the circumstances. Their autonomy and dignity are violated. /srs
The main purpose is preying on vulnerable minors and catering to pedophiles, child predator rings, or human trafficking groups. /srs
The adult (in this case, the perpetrator) often commits another type of sexual violence against the minor, provoking further physical and psychological harm.
The vast majority of times contains images or videos of real life minors being actively harmed. /srs
While the post from @/chubbibunni isn't directed to one specific user, it still can count as cyber harassment. Equating therapeutic art with literal CSAM/CSEM is not only a false comparison, but a deeply harmful one. Falsely accusing CSA/SA survivors of being child abuse perpetrators can be considered defamatory, therefore, this online behavior can be considered cyber harassment. Adding to that, this incident is not an isolated one, but a pattern of ignorant and hostile online behavior. /srs
#anti harassment#cyber security#cybersecurity#cyberharassment#cyber harassment#internet safety#stop cyberbullying#stop hate#stop harassing people#stop bullying#archive blog#evidence#online harassment#proship#fandom#accountability#mental heath awareness#mental health#report#law enforcement#report and block#block and report#csa awareness#csa warning#child abuse awareness#child safety#child abuse#stop child abuse#protect children#childrens rights
11 notes
·
View notes
Text
IRS Lawyer Ousted as Elon Musk’s DOGE Plans Even More Cuts | The New Republic
#department of government efficiency#elon musk#donald trump#trump administration#irscompliance#irs audit#irs#internal revenue service#federal government#data privacy#data protection#cybersecurity#cyber security#civil rights#social justice#us politics
14 notes
·
View notes
Text
Be Careful Putting Your Phone Down At Panera Bread Locations
I noticed my phone buzzing repeatedly when I'd have it open on the table at Panera, and on further review I realized that my phone was repeatedly scanning an NFC tag on the underside of the table. I'm assuming the servers use these as a shorthand way of confirming that food has been delivered to the correct table.
This is all well and good; this is a prime use case for NFC tags, and using an NFC reader app I was able to see that they're just basic numeric codes. As long as the tags aren't rewritable by anyone, they're not a security risk.
The NFC tags at Panera Bread are rewritable. Like, easily. Using a simple app you can get from the Google Play Store.
What this means is that someone can rewrite the NFC tags to redirect to a download link for malware, or a phishing website, or any number of other attack vectors.
I have more information about this issue on my personal website, as well as a video demonstrating the effect. My recommendation is to keep NFC turned off on your phone unless and until you're actively using it (for touchless payments, bus tickets, etc.).
39 notes
·
View notes
Text
Strengthening Resilience Amid Growing Risks: Cybersecurity in Financial Services
Financial services in today’s world cannot be discussed without linking them to operations that are more integrated and dependent on technological solutions, which are also more convenient and open new prospects. But with this advancement, comes its bargain, that is the challenges that ensue with it. But among the most challenging questions is the increasing cybersecurity threat.
#cybersecurity threat#cyber security services#cyber protection#phishing in cyber security#malware attack#data encryption#financial services industries#financenu
0 notes
Text
no but sometimes i think about the way that the foster kids absolutely have these extremely important meetings regarding any potential love interests in aisling's life. like it doesn't matter if the relationship is official, if they so much as SUSPECT that your muse and aisling are thinking about considering the concept of the possibility of entering a romantic relationship, they're gonna have this very serious meeting, possibly inviting other members of the squad to participate if the situation requires it.
anyway if you'd like to know what the foster kids say about your muse during one of these meetings, like this post! we do not need to be shipping, they'll do this even if your muse just made aisling smile one time, they're kids who read too much into things!
#( ' a certain wisdom. ' / hc. )#( not even serious subjects are covered like )#( advik wants to know how they feel abt destroying the zoos with him )#( eli wants to know their opinions on cyber vigilantism )#( like yeah they're protective of their mother but what's in it for THEM? )
6 notes
·
View notes
Text
⚠️IMPORTANT⚠️
Hello, everyone. I know it has been several months since I last posted, and I do apologize for that. I will soon go back to regular posting, but right now I need to talk about something serious. Recently I was informed by a dear friend about this “Project 2025. I cried when I heard about it. It is so disgusting that people are trying to rid America of LGBTQ+ individuals. This country was never safe for us in the first place, but this is absolutely unacceptable. Millions of Transgender (and gender non-conforming) individuals could be LEGALLY killed by the US government if Trump gets elected again. Please join me in this protest against this genocidal system and do your research. I will link several helpful sources below, as well as petitions and places you can donate if you do feel inclined to do so. But a repost and like is more than enough.
Please, don't sit there and let us get killed.
Sources:
Conservatives Plan to Ban Abortion and Cut LGBT Rights Starting Next January | The New Republic
youtube
Petitions:
Petition · Stop Project 2025: Protect Our Rights and Choices! · Change.org
#transgender#activism#protest#project2025#conservatives#liberals#call to action#spread the word#love is love#cyber y2k#frutiger aero#angel#angelcore#gyaruo#tenshi kaiwai#y2k#male gyaru#sth#drum and bass#america#donald trump#trump 2024#fuck trump#maga#gop#trump#protect trans kids#Youtube
39 notes
·
View notes
Text
Who is the mother of X?
Here is Elon Musk and son, X

and here is X's mother, Grimes. Here she is while pregnant with X.
youtube
Poor woman has three kids with Musk. Damn, she has bad taste in men.
Speaking of Grimes and Musk
#grimes#elon musk#x#medical crisis#his own kid#he uses one for protection while he ignores another#Claire Elise Boucher#twitter#tesla#tesla cybertruck#tesla cars#boycott tesla#cyber truck#Youtube
6 notes
·
View notes
Text

Couldn't they have called this literally anything else
6 notes
·
View notes
Text
NEWS, ukraine, zelenskyy, IPHONE 16E, economy, nyc, states, washington, cyber crime, nvidia, roof collapse, books, drones, arts financing, ice, polls, tariffs, wall street, visas, sally ride, tiktok, commander in chief, secret service protection, forever, voice of america, nyc, snl
youtube
youtube
youtube
youtube
youtube
youtube
youtube






#NEWS#ukraine#zelenskyy#IPHONE 16E#economy#nyc#states#washington#cyber crime#nvidia#roof collapse#books#drones#arts financing#ice#polls#tariffs#wall street#visas#sally ride#tiktok#commander in chief#secret service protection#forever#voice of america#snl#Youtube
4 notes
·
View notes