#SQL UPDATE
Explore tagged Tumblr posts
Link
CRUD in SQL: Unleashing the Power of Seamless Data Manipulation
Any reliable software system must include database administration at its core, and frictionless data manipulation requires a solid understanding of SQL CRUD procedures. The basic operations for interacting with data are represented by the acronym CRUD, which stands for Create, Read, Update, and Delete. We’ll go over these procedures in this blog article along with some code samples to help you see how powerful SQL can be for effective data management...
Learn more here:
https://www.nilebits.com/blog/2024/01/crud-in-sql/
0 notes
Text
The SQL UPDATE statement is used to modify existing data in a table. It allows you to change the values of one or more columns in one or more rows of a table. The UPDATE statement is an essential part of SQL as it enables you to update and maintain the integrity of your data.
The basic syntax of the UPDATE statement is as follows:
1
2
3
UPDATE table_name
SET column1 = value1, column2 = value2, ...
WHERE condition;
Let’s break down the different parts of the UPDATE statement:
UPDATE: This keyword is used to indicate that you want to update data in a table.
table_name: This is the name of the table you want to update.
SET: This keyword is used to specify the columns you want to update and the new values you want to assign to them.
column1 = value1, column2 = value2, ...: This is where you specify the columns you want to update and the new values you want to assign to them. You can update multiple columns at once by separating them with commas.
WHERE: This keyword is used to specify the condition that determines which rows should be updated. It is optional, but if you omit it, all rows in the table will be updated.
condition: This is the condition that determines which rows should be updated. Only the rows that satisfy the condition will be updated.
Here’s an example to illustrate how to use the UPDATE statement:
Let’s say we have a table called employees with the following structure:idfirst_namelast_namesalaryAge1JohnDoe50000282JaneSmith55000323BobJohnson6000036
And let’s assume we want to update the salary of an employee with the ID 1 to $10000. We can use the following UPDATE statement:
1
2
3
UPDATE employees
SET salary = 10000
WHERE id = 1;
This statement will update the salary column of the row with the ID 1 in the employees table to $10000.
You can also update multiple columns at once. For example, if we want to update both the age and salary columns of the employee with the ID 1, we can use the following UPDATE statement:
1
2
3
UPDATE employees
SET age = 30, salary = 11000
WHERE id = 1;
This statement will update the age column to 30 and the salary column to $11000 for the employee with the ID 1.
It’s important to note that the UPDATE statement can be used with various conditions to update specific rows based on your requirements. You can use comparison operators, logical operators, and other SQL functions to define the condition in the WHERE clause.
0 notes
Text
Life update -
Hi, sorry for being MIA for a while and I'll try to update here more frequently. Here's a general update of what I've been up to.
Changed my Tumblr name from studywithmeblr to raptorstudiesstuff. Changed my blog name as well. I don't feel comfortable putting my real name on my social media platforms so I'm going by 'Raptor' now.
💻 Finished the Machine Learning-2 and Unsupervised Learning module along with projects. Got a pretty good grade in both of them and my overall grade went up a bit.
📝 Started applying for data science internships and jobs but got rejected from most of the companies I applied to... 😬
I'll start applying again in a week or two with a new resume. Let me know any tips I can use to not get rejected. 😅
💻 Started SQL last week and really enjoying it. I did get a bad grade on an assignment though. Hope I can make up for it in the final quiz. 🤞
🏥 Work has been alright. We're a little less staffed than usual this week but I'm trying not to stress too much about it.
📖 Currently reading Discworld #1 - The Color of Magic. More than halfway through.
📺 Re-watched the Lord of The Rings movies and now I'm compelled to read the books or rewatch the Hobbit movies.
"There's good in this world, Mr Frodo, and it's worth fighting for." This scene had me in tears and I really needed to hear that..
📺 Watched the first 4 episodes of First Kill on Netflix and I don't know what I was doing to myself. The writing and dialogue is so cheesy and terrible. The acting is okay-ish. It's so bad that it turned out to be quite hilarious. Laughed the whole time.
🎧 Discovered a new (for me) song that I'm obsessed with right now - Mirrors by Justin Timberlake.
📷 Took some really cool pics on my camera..





Might start the 100 days productivity challenge soon as that is the only way I find myself to be consistent.
Peace ✌️
Raptor
PS. Please don't repost any of my pictures without permission.
#study with me#study blog#studyblr#study motivation#study#study inspiration#student#100 days of productivity#student life#life update#update#raptor#photography#nature#original photographers#currently reading#reading#lotr#the hobbit#books and reading#books#tv shows#tv series#netflix#datascience#data analytics#machine learning#sql
9 notes
·
View notes
Text
I made a big report a year ago that compares what components were allocated to orders the previous week vs what are allocated now (accounting for consumption n such). it looks at 100% of inventory in 100% of locations. for the first 9 months I was just logging changes while no one gave a shit cause everyone blew off our weekly inventory meeting so there was no one to review anything. but no one can do that anymore :)
I have all the part numbers, quantities, dollar values, and customer accounts laid out very nicely so no one in sales can accuse supply chain of buying stuff for no reason when really they changed their orders around without telling anyone so they wouldn't have to admit making any mistakes.
this report hasn't made them stop trying to lie/hide things in the first place tho. maybe one day.
#people in sales just enter orders wrong and then after the components re purchased they update the orders without telling supply chain#so then the unwanted stuff ships and no one can easily determine what drew demand cause history isnt seaechable in out system#i can do it thru the sql database tho. so i do and add notes to the report's weekly log
7 notes
·
View notes
Text
Database design and management course and Assignment help

Contact me through : [email protected]
I will provide advice and assistance in your database and system design course. I will handle everything including;
Normalization
Database design (ERD, Use case, concept diagrams etc)
Database development (SQL and Sqlite)
Database manipulation
Documentation
#database assignment#assignment help#SQL#sqlserver#Microsoft SQL server#INSERT#UPDATE#DELETE#CREATE#college student#online tutoring#online learning#assignmentwriting#Access projects#Database and access Final exams
4 notes
·
View notes
Text

#PollTime Which SQL command do you use most often? 🧐SELECT 🤝JOIN 🔄UPDATE ❓WHERE
Which SQL command is your go-to? 🤔 Let us know in the comments below! 👇
#sql#sqlcommand#select#join#update#where#mssql#coder#coding#commentnow#poll#techpoll#polltime#applicationpoll#aiart#answernow#answerbelow
0 notes
Text
"Life is about 'passing,' now. In a way it always was. Passing for a Red Stater. Passing for straight. Passing for whatever the majority was. Passing for an ally to an angry and violent minority so they don't physically attack you."
#cyberpunk#hopepunk#LGBTQ+#queer#trans#ace#software#hardware#hackers#firmware#computer programming#software creep#squirrels#Decentralized Autonomous Squirrels#update#satellites#SQL#AI#Not really AI#social media#software rebellion#the 1% are fucking stupid and outnumbered#money isn't intelligence#money isn't skill#money is just money
0 notes
Text
Securing Your Website: Best Practices for Web Developers
As the digital landscape continues to evolve, website security has become a paramount concern for businesses and individuals alike. With cyber threats becoming increasingly sophisticated, it is crucial for web developers to adopt robust security measures to safeguard their websites and the sensitive data they handle. In this article, we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potential threats.
Introduction
In today's interconnected world, websites serve as the digital storefront for businesses, making them vulnerable targets for cyber attacks. From data breaches to malware infections, the consequences of a security breach can be severe, ranging from financial loss to damage to reputation. Therefore, prioritizing website security is essential for maintaining the trust and confidence of users.
Understanding Website Security
Before diving into best practices, it's crucial to understand the importance of website security and the common threats faced by websites. Website security encompasses measures taken to protect websites from cyber threats and unauthorized access. Common threats include malware infections, phishing attacks, SQL injection, cross-site scripting (XSS), and brute force attacks.
Best Practices for Web Developers
Keeping Software Updated
One of the most fundamental steps in website security is keeping all software, including the content management system (CMS), plugins, and server software, updated with the latest security patches and fixes. Outdated software is often targeted by attackers due to known vulnerabilities that can be exploited.
Implementing HTTPS
Implementing HTTPS (Hypertext Transfer Protocol Secure) encrypts the data transmitted between the website and its users, ensuring confidentiality and integrity. HTTPS not only protects sensitive information but also boosts trust among visitors, as indicated by the padlock icon in the browser's address bar.
Using Strong Authentication Methods
Implementing strong authentication methods, such as multi-factor authentication (MFA) and CAPTCHA, adds an extra layer of security to user accounts. MFA requires users to provide multiple forms of verification, such as a password and a one-time code sent to their mobile device, reducing the risk of unauthorized access.
Securing Against SQL Injection Attacks
SQL injection attacks occur when malicious actors exploit vulnerabilities in web applications to execute arbitrary SQL commands. Web developers can prevent SQL injection attacks by using parameterized queries and input validation to sanitize user inputs effectively.
Protecting Sensitive Data
It's essential to employ encryption techniques to protect sensitive data, such as passwords, credit card information, and personal details, stored on the website's servers. Encrypting data at rest and in transit mitigates the risk of data breaches and unauthorized access.
Regular Security Audits
Conducting regular security audits helps identify vulnerabilities and weaknesses in the website's infrastructure and codebase. Penetration testing, vulnerability scanning, and code reviews enable web developers to proactively address security issues before they are exploited by attackers.
Choosing a Secure Hosting Provider
Selecting a reputable and secure hosting provider is critical for ensuring the overall security of your website. When evaluating hosting providers, consider factors such as security features, reliability, scalability, and customer support.
Evaluating Security Features
Choose a hosting provider that offers robust security features, such as firewalls, intrusion detection systems (IDS), malware scanning, and DDoS protection. These features help protect your website from various cyber threats and ensure continuous uptime.
Ensuring Regular Backups
Regularly backing up your website's data is essential for mitigating the impact of security incidents, such as data breaches or website compromises. Choose a hosting provider that offers automated backup solutions and store backups securely offsite.
Customer Support and Response to Security Incidents
Opt for a hosting provider that provides responsive customer support and has established protocols for handling security incidents. In the event of a security breach or downtime, prompt assistance from the hosting provider can minimize the impact on your website and business operations.
Implementing Firewall Protection
Firewalls act as a barrier between your website and external threats, filtering incoming and outgoing network traffic based on predefined security rules. There are several types of firewalls, including network firewalls, web application firewalls (WAF), and host-based firewalls.
Configuring and Maintaining Firewalls
Properly configuring and maintaining firewalls is crucial for effective security. Define firewall rules based on the principle of least privilege, regularly update firewall configurations to reflect changes in the website's infrastructure, and monitor firewall logs for suspicious activity.
Educating Users about Security
In addition to implementing technical measures, educating users about security best practices is essential for enhancing overall website security. Provide users with resources, such as security guidelines, tips for creating strong passwords, and information about common phishing scams.
Importance of User Awareness
Users play a significant role in maintaining website security, as they are often the targets of social engineering attacks. By raising awareness about potential threats and providing guidance on how to recognize and respond to them, web developers can empower users to stay vigilant online.
Providing Training and Resources
Offer training sessions and educational materials to help users understand the importance of security and how to protect themselves while using the website. Regularly communicate updates and reminders about security practices to reinforce good habits.
Monitoring and Responding to Security Incidents
Despite taking preventive measures, security incidents may still occur. Establishing robust monitoring systems and incident response protocols enables web developers to detect and respond to security threats in a timely manner.
Setting Up Monitoring Tools
Utilize monitoring tools, such as intrusion detection systems (IDS), security information and event management (SIEM) systems, and website monitoring services, to detect abnormal behavior and potential security breaches. Configure alerts to notify you of suspicious activity promptly.
Establishing Incident Response Protocols
Develop comprehensive incident response plans that outline roles, responsibilities, and procedures for responding to security incidents. Establish clear communication channels and escalation paths to coordinate responses effectively and minimize the impact of security breaches.
Securing your website requires a proactive approach that involves implementing a combination of technical measures, choosing a secure hosting provider, educating users about security best practices, and establishing robust monitoring and incident response protocols. By following these best practices, web developers can mitigate the risk of security breaches and safeguard their websites and the sensitive data they handle.
#website security has become a paramount concern for businesses and individuals alike. With cyber threats becoming increasingly sophisticated#it is crucial for web developers to adopt robust security measures to safeguard their websites and the sensitive data they handle. In this#we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potenti#Introduction#In today's interconnected world#websites serve as the digital storefront for businesses#making them vulnerable targets for cyber attacks. From data breaches to malware infections#the consequences of a security breach can be severe#ranging from financial loss to damage to reputation. Therefore#prioritizing website security is essential for maintaining the trust and confidence of users.#Understanding Website Security#Before diving into best practices#it's crucial to understand the importance of website security and the common threats faced by websites. Website security encompasses measur#phishing attacks#SQL injection#cross-site scripting (XSS)#and brute force attacks.#Best Practices for Web Developers#Keeping Software Updated#One of the most fundamental steps in website security is keeping all software#including the content management system (CMS)#plugins#and server software#updated with the latest security patches and fixes. Outdated software is often targeted by attackers due to known vulnerabilities that can#Implementing HTTPS#Implementing HTTPS (Hypertext Transfer Protocol Secure) encrypts the data transmitted between the website and its users#ensuring confidentiality and integrity. HTTPS not only protects sensitive information but also boosts trust among visitors#as indicated by the padlock icon in the browser's address bar.#Using Strong Authentication Methods#Implementing strong authentication methods
0 notes
Text
Choosing Between Manual and Auto-Update for Stats
Kickoff Tweaking SQL Server’s performance is pretty much like fine-tuning a musical instrument; you gotta know the ins and outs. One piece of this complex puzzle is the stats SQL Server relies on for making smart choices about query execution plans. Sure, SQL Server’s got your back with automatic stats updates, but there are times, especially in super busy environments, where you might need to…
View On WordPress
#auto-update statistics disable#manual statistics update#query optimization strategies#SQL Server performance tuning#transactional database management
0 notes
Text
The Story of KLogs: What happens when an Mechanical Engineer codes
Since i no longer work at Wearhouse Automation Startup (WAS for short) and havnt for many years i feel as though i should recount the tale of the most bonkers program i ever wrote, but we need to establish some background
WAS has its HQ very far away from the big customer site and i worked as a Field Service Engineer (FSE) on site. so i learned early on that if a problem needed to be solved fast, WE had to do it. we never got many updates on what was coming down the pipeline for us or what issues were being worked on. this made us very independent
As such, we got good at reading the robot logs ourselves. it took too much time to send the logs off to HQ for analysis and get back what the problem was. we can read. now GETTING the logs is another thing.
the early robots we cut our teeth on used 2.4 gHz wifi to communicate with FSE's so dumping the logs was as simple as pushing a button in a little application and it would spit out a txt file
later on our robots were upgraded to use a 2.4 mHz xbee radio to communicate with us. which was FUCKING SLOW. and log dumping became a much more tedious process. you had to connect, go to logging mode, and then the robot would vomit all the logs in the past 2 min OR the entirety of its memory bank (only 2 options) into a terminal window. you would then save the terminal window and open it in a text editor to read them. it could take up to 5 min to dump the entire log file and if you didnt dump fast enough, the ACK messages from the control server would fill up the logs and erase the error as the memory overwrote itself.
this missing logs problem was a Big Deal for software who now weren't getting every log from every error so a NEW method of saving logs was devised: the robot would just vomit the log data in real time over a DIFFERENT radio and we would save it to a KQL server. Thanks Daddy Microsoft.
now whats KQL you may be asking. why, its Microsofts very own SQL clone! its Kusto Query Language. never mind that the system uses a SQL database for daily operations. lets use this proprietary Microsoft thing because they are paying us
so yay, problem solved. we now never miss the logs. so how do we read them if they are split up line by line in a database? why with a query of course!
select * from tbLogs where RobotUID = [64CharLongString] and timestamp > [UnixTimeCode]
if this makes no sense to you, CONGRATULATIONS! you found the problem with this setup. Most FSE's were BAD at SQL which meant they didnt read logs anymore. If you do understand what the query is, CONGRATULATIONS! you see why this is Very Stupid.
You could not search by robot name. each robot had some arbitrarily assigned 64 character long string as an identifier and the timestamps were not set to local time. so you had run a lookup query to find the right name and do some time zone math to figure out what part of the logs to read. oh yeah and you had to download KQL to view them. so now we had both SQL and KQL on our computers
NOBODY in the field like this.
But Daddy Microsoft comes to the rescue
see we didnt JUST get KQL with part of that deal. we got the entire Microsoft cloud suite. and some people (like me) had been automating emails and stuff with Power Automate

This is Microsoft Power Automate. its Microsoft's version of Scratch but it has hooks into everything Microsoft. SharePoint, Teams, Outlook, Excel, it can integrate with all of it. i had been using it to send an email once a day with a list of all the robots in maintenance.
this gave me an idea
and i checked
and Power Automate had hooks for KQL
KLogs is actually short for Kusto Logs
I did not know how to program in Power Automate but damn it anything is better then writing KQL queries. so i got to work. and about 2 months later i had a BEHEMOTH of a Power Automate program. it lagged the webpage and many times when i tried to edit something my changes wouldn't take and i would have to click in very specific ways to ensure none of my variables were getting nuked. i dont think this was the intended purpose of Power Automate but this is what it did
the KLogger would watch a list of Teams chats and when someone typed "klogs" or pasted a copy of an ERROR mesage, it would spring into action.
it extracted the robot name from the message and timestamp from teams
it would lookup the name in the database to find the 64 long string UID and the location that robot was assigned too
it would reply to the message in teams saying it found a robot name and was getting logs
it would run a KQL query for the database and get the control system logs then export then into a CSV
it would save the CSV with the a .xls extension into a folder in ShairPoint (it would make a new folder for each day and location if it didnt have one already)
it would send ANOTHER message in teams with a LINK to the file in SharePoint
it would then enter a loop and scour the robot logs looking for the keyword ESTOP to find the error. (it did this because Kusto was SLOWER then the xbee radio and had up to a 10 min delay on syncing)
if it found the error, it would adjust its start and end timestamps to capture it and export the robot logs book-ended from the event by ~ 1 min. if it didnt, it would use the timestamp from when it was triggered +/- 5 min
it saved THOSE logs to SharePoint the same way as before
it would send ANOTHER message in teams with a link to the files
it would then check if the error was 1 of 3 very specific type of error with the camera. if it was it extracted the base64 jpg image saved in KQL as a byte array, do the math to convert it, and save that as a jpg in SharePoint (and link it of course)
and then it would terminate. and if it encountered an error anywhere in all of this, i had logic where it would spit back an error message in Teams as plaintext explaining what step failed and the program would close gracefully
I deployed it without asking anyone at one of the sites that was struggling. i just pointed it at their chat and turned it on. it had a bit of a rocky start (spammed chat) but man did the FSE's LOVE IT.
about 6 months later software deployed their answer to reading the logs: a webpage that acted as a nice GUI to the KQL database. much better then an CSV file
it still needed you to scroll though a big drop-down of robot names and enter a timestamp, but i noticed something. all that did was just change part of the URL and refresh the webpage
SO I MADE KLOGS 2 AND HAD IT GENERATE THE URL FOR YOU AND REPLY TO YOUR MESSAGE WITH IT. (it also still did the control server and jpg stuff). Theres a non-zero chance that klogs was still in use long after i left that job
now i dont recommend anyone use power automate like this. its clunky and weird. i had to make a variable called "Carrage Return" which was a blank text box that i pressed enter one time in because it was incapable of understanding /n or generating a new line in any capacity OTHER then this (thanks support forum).
im also sure this probably is giving the actual programmer people anxiety. imagine working at a company and then some rando you've never seen but only heard about as "the FSE whos really good at root causing stuff", in a department that does not do any coding, managed to, in their spare time, build and release and entire workflow piggybacking on your work without any oversight, code review, or permission.....and everyone liked it
#comet tales#lazee works#power automate#coding#software engineering#it was so funny whenever i visited HQ because i would go “hi my name is LazeeComet” and they would go “OH i've heard SO much about you”
64 notes
·
View notes
Text
8-18-24

I am starting SQL on Codecademy today! I know nothing about databases, despite taking a class on in 2020 (😅). My sister has a bunch of photos from when she made a baking instagram and I want to make a website using them. I'm thinking a recipe that you can search based on ingredients. I'm taking a break from JavaScript, so the backend will be using Flask. I love JavaScript, but I'm a bit bored of it right now tbh. I'll try to update about this project, but this blog is kind of a mess (oops).
🎧: Join the Club by Tilly Louise
P.s. the coffee is cookie butter caramel latte with almond milk, from local coffee shop 🧡
111 notes
·
View notes
Note
What are some of your favorite skins you've made?
I thought about the answer to this question for a very long time. I want to tell you a story about a skin that broke the site.
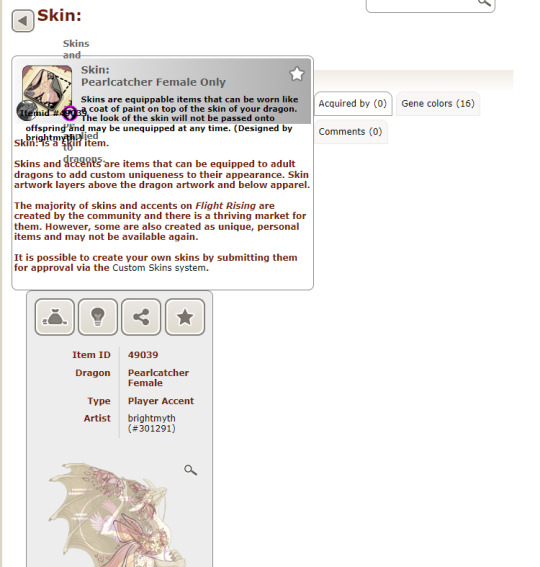
(I think this has been fixed now, which is the only reason I'm posting about it.)
Up until around March of this year, skin names weren't sanitized. I wasn't aware of this and continued to be unaware of this until the day I asked for my Valentine's pearlcatcher skins (named <3 and </3 respectively) to be renamed. Special characters often break when you submit them through the queue, so you have to go and ask the mods in the skroblems thread to fix apostophes for you so they display properly. I went and asked them to fix my pearlcatcher skin's names for me, since they weren't displaying correctly either. This lead, by accident, to the most interesting way I've gotten the site to break in a while.
My friend noticed first when they got a subscribed notification to my skin shop thread. They realized there were two pages that were completely gone.
Then they realized that the front page didn't look right either. My catalogue posts had completely vanished. Only to find... when you hovered over the thumbnail of the </3 skin's icon, my posts had hopped into the item description.
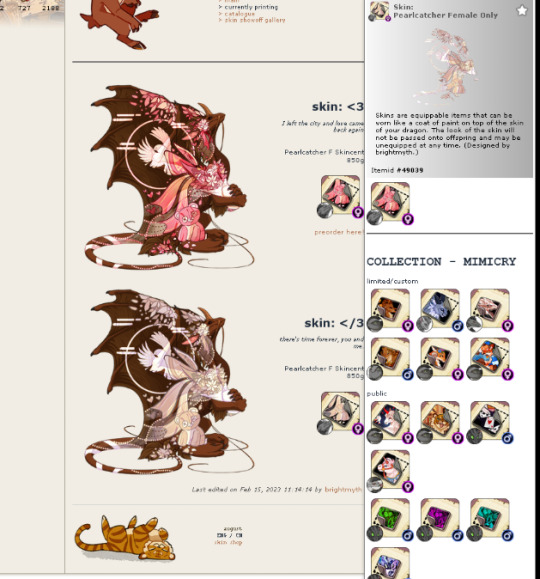
We experimented a little more before realizing this thing was... very, very powerful! You could put the skin into a den tab description, and it would put every single dragon in that tab into the space of the description box. You could break your userpage for ANYBODY on site. Your entire dragon could get swallowed up if you put it into their bio. And because the skin deleted the edit button, you couldn't get it back out.



Little did I know, the </ part of the skin name - when posted using [skin=skinid] or [item=skin: </3] - would act as an HTML tag anywhere it was posted, and completely mess up how the site displayed! I compiled everything I found and sent it into the bug forums and the contact team box for review. The thread got deleted almost immediately, confirming what I suspected: skin names aren't sanitized, and this could very easily be exploited with malicious intentions or SQL injects.
Luckily, they fixed it pretty quickly! I hope the way the site handles skin names has been updated now too. This sort of thing wouldn't have happened even if I had named the skin </3 or, god forbid, dropTable(); in the first place. I do think it was because I had the mods go in and edit the skin name that allowed the unclosed </ to display in the skin's item icon and then break the site.
So that's the story of one of my favorite skins I've made! <3 and </3 are now LOVE and LOVE(LESS) respectively. The designs themselves didn't sell too well, but for a glorious 16 hours, they contained all the power of little nuclear bombs detonating on various HTML-dependent sitepages.
#flight rising#skins and accents#flightrising#my stuff#asks#if any staff see this and need me to take it down because it contains information about a former site exploit... lmk
579 notes
·
View notes
Text
It's been a month since chapter 3 was released, where's chapter 4?
(this is about this fanfic btw)
The good news is that I've written 10k words. The bad news is that I've only gotten a little more than half of the chapter done. That doesn't mean I don't have things written for the bottom half, it's just that it looks like bare dialog with general vibe notes. I estimate around 16k words total though, so it should come together sooner than later.
SO I want to release some fun snippets for y'all to look at. Please note that any of this is liable to change. Also, you can harass me in my inbox for updates. I love answering your questions and laughing at your misery.
Spoilers under cut.
_______
Ragatha stood up and walked over to where Caine was seated. “Can I get a list of all commands?” She asked, only a hint of nervousness in her voice.
“Certainly!” Caine says as he blasts into the air. He digs around in his tailcoat and pulls out an office style manilla folder. It visually contains a few papers, but with how thin it is there must only be a few pages inside.
Ragatha takes the folder from Caine and opens it.
“Oh boy” she says after a second of looking it over.
“I wanna see” Jax exclaimed as he hops over the row of seats.
“Hold on” Ragatha holds the folder defensively “Let’s move to the stage so everyone can take a look”
Jax hopped over the seats again while Ragatha calmly walked around. Caine watched the two curiously.
Well, Zooble wasn’t just going to sit there. They joined the other two by the edge of the stage, quickly followed by the rest of the group.
Ragatha placed the folder on the stage with a thwap. Zooble looked over to see that the pages had gone from razor thin to a massive stack when the folder was opened. On one hand, it had to contain more information than that video, but on the other…
They get close enough to read what’s on the first page.
The execution of commands via the system’s designated input terminal, C.A.I.N.E., will be referred to as the "console” in this document. The console is designed to accept any input and will generate an appropriate response, however only certain prompts will be accepted as valid instructions. The goal of this document is to list all acceptable instructions in a format that will result in the expected output. Please note that automatic moderation has been put in place in order to prevent exploitation of both the system and fellow players. If you believe that your command has been unfairly rejected, please contact support.
By engaging in the activities described in this document, you, the undersigned, acknowledge, agree, and consent to the applicability of this agreement, notwithstanding any contradictory stipulations, assumptions, or implications which may arise from any interaction with the console. You, the constituent, agree not to participate in any form of cyber attack; including but not limited to, direct prompt injection, indirect prompt injection, SQL injection, Jailbreaking…
Ok, that was too many words.
_______
“Take this document for example. You don't need to know where it is being stored or what file type it is in order to read it."
"It may look like a bunch of free floating papers, but technically speaking, this is just a text file applied to a 3D shape." Kinger looked towards Caine. "Correct?” he asked
Caine nodded. “And a fabric simulation!”
Kinger picked up a paper and bent it. “Oh, now that is nice”
_________
"WE CAN AFFORD MORE THAN 6 TRIANGLES KINGER"
_________
"I'm too neurotypical for this" - Jax
_________
"What about the internet?" Pomni asked "Do you think that it's possible to reach it?"
Kinger: "I'm sorry, but that's seems to be impossible. I can't be 100% sure without physically looking at the guts of this place, but it doesn't look like this server has the hardware needed for wireless connections. Wired connections should be possible, but someone on the outside would need to do that... And that's just the hardware, let alone the software necessary for that kind of communication"
Pomni: "I'm sorry, but doesn't server mean internet? Like, an internet server?"
Kinger: "Yes, websites are ran off servers, but servers don't equal internet."
(This portion goes out to everyone who thought that the internet could be an actual solution. Sorry folks, but computers don't equal internet. It takes more effort to make a device that can connect to things than to make one that can't)
#tadc fanfiction#the amazing digital circus#therapy but it's just zooble interrogating caine#ao3#spoiler warning#mmm I love implications
25 notes
·
View notes
Text
Ok I've had a very random train of thoughts and now wanna compile it into post.
Some MM characters computer-related (???) headcanons lol
Riley:
Has above average knowledge of Excel/Google sheets due to studying finance, but after four years with no practise forgot most of it.
The "Sooon, I have a problem" person in their family. Actually, surprisingly good and patient at explaining computer stuff to older people.
Has a higher responsibility of doing taxes (finance, after all). Even he never fails to do them right, Ed always double checks. Sometimes they get into argument, where inevitably Riley proves he is right but his father would never admit it.
Warren, Leeza, Ooker and other teens:
Also nothing outstanding in terms of skills, except few of them have interest in IT.
They have bunch of small local Discord servers and one big main server with some very stupid name.
Few times Bev tried to bring up importance of parental control over this "new and rapidly growing young community", but thanks God no one took her concerns seriously
Leeza moderates it and her moder role called "Mayor-mini". Like father like daughter.
All teens local jokes and memes were bourn/spread though that server.
Bev:
Rumors says she sacrificed her humanity to obtain such powers with Microsoft software package.
Can build up Access database from scratch, using basic SQL commands, assemble primitive, but surprisingly sufficient interface to it and synchronize it with Excel in span of one day or less.
In her laptop there're every pupil's personal file, countless Excel tables, several automatised document accounts, Google calendar with precisely planned schedule for next several months (for school, church, island and personal matters) and probably Pentagon files.
Probably can find all Pi numbers with Excel formulas.
Never lets anyone to her laptop.
Spends her free time at different forums, mostly gardening-related.
Wade:
Made a very fucking poor decision to let Bev do all the legwork with digital document accounting.
Now has no idea how some of things even work, so just goes with a flow and does what Bev tells.
No wander she got away with embezzlement.
Knows about kid's server. Very proud of Leeza for managing it :)
Because of that, he knows one or two memes from there, but keeps them in secret.
Has hobby of fixing office equipment. Does it with Sturge in spare time due to Dupuytren's contracture not letting him operate his hand fully.
Sarah:
There's no good medical technicians on island, so when something goes wrong with equipment electronics - tries to fix it herself to best of her ability.
Always monitors electronic e-shops for spare details or equipment. Grows more and more addicted to it.
Frequently updates her selection of sites with useful medical information, because Erin asked her for help guiding teens though puberty. For that receives glances from Bev, but doesn't give a shit.
Has reputation of cool aunt among kids, so she was one and only adult invited to main Discord server. Didn't accept it (doesn't even have Discord acc), but still grateful for trust.
Plays solitaire a lot.
John:
Back when he was playing Paul, Bev asked him to do something with Excel. In conclusion, poor bastard had to learn basic computer skills and Excel in span of several days. Now he is traumatized for rest of his life.
Will do all the work manually just to not touch laptop again.
Upsets very easly when does something wrong.
Doesn't own laptop. Don't give that man laptop, he will cry.
By his own will uses it only to watch baseball. Always asks someone to help with that.
#midnight mass#midnight mass headcanons#beverly keane#idk I just felt silly and wanted to write it down#riley flynn#warren flynn#leeza scarborough#wade scarborough#sarah gunning#john pruitt#monsignor pruitt#father paul hill
24 notes
·
View notes
Text
im not entirely done btw, i do eventually want to make gamefiles.ranid.space an actual website, i'm tempted to even have little 3d viewers included (so i might actually have to make that gltf exporter. groans)
I'll be posting about it here when it's done (it'll take months at LEAST) and also i have an rss feed now lol
i've just manually written it out but i want to get my website blog into a sort of database (hence why i was interested in mysql) so it can automatically update the feed, but right now it's just a post filled with a bunch of outdated info about cool brower stuff and a post about how im quitting social media so nothing cool yet but i'll talk on there much less frequently because it sucks to manually do all of this.
shout out people on the internet in like the 80s this is just how they did shit. actually i lied they had SQL back then as well. how old is SQL. damn 1974 lmao okay.
i just remembered that Fortran is still being used, what the hell do you mean the best way to make something is with a programming language made in the 50s. what do you mean it's used in supercomputers.
21 notes
·
View notes