#Software Build Computers
Explore tagged Tumblr posts
Text
Laptops
Cheap Deals On Laptops Are Bought At Broker Shop.
BROKER SHOP INTERNATIONAL
Windows laptops and more. A laptop is a personal computer that can be easily moved and used in various locations. Most laptops are designed to have all of the functionality of a desktop computer, which means they can generally run the same software and open the same types of files.
#laptop#deals#shopping deals#Broker Shop#birmingham uk#Broker#Computer#Sales#Wholesales#Laptops Designs#Desktop Computer#Software Build Computers#Students Laptops#Free Laptops#High Quality Laptops#Public Laptops#Functionality of Desktop#UK Laptops#USA Today#Online Shopping#Windows Laptops#Note Books#Intel Computers#Brandad Laptops#Buy Now Laptops
0 notes
Text



Day 2! Lots of fun with Kimblee, a surprising amount of people were really excited to see him XD (it's also kind of funny that the building fire that happened next door occurred while I was wearing him >.>)
Met up with a bunch of homunculi for some photos and then hung out at a bar for more photos food; Envy and Greed had a little worm!Envy with them and it was SO CUTE 😭😭😭


And then went as Zenos to the Final Fantasy concert -- I've been to Distant Worlds several times, but this was my first time going to A New World; it was soooo beautiful. The musicians and the conductor were clearly enjoying themselves so much too, their arrangements were gorgeous and their ending piece was hilarious.


I'm so used to seeing FFVII dominating the cosplay scene at these things, but there were so many FFXIV cosplayers at this one! Everyone looked amazing; Fandaniel nearly leaping over the seats once he spotted me way in the back made my evening 😂






#not doing day 3 today lmaoooo i'm beat#this year's sakcon was WILD#first half of the staff didn't show up for registration on thurs/fri plus they were trying a new software provider for the badges#and that crashed and only five computers were able to print out badges for everyone... keep in mind this event draws around 40-50k people#which led to 4-5 hrs waiting in line for your badge#and then on saturday the building across the street caught fire so fire department shut the whole block down.#one of our con center buildings was evacuated too due to the smoke coming in. lots of panels etc were cancelled. so that was fun.#and then very early in the am hours today there was a natural gas leak discovered#so fire department was back AGAIN with more people this time#i guess the reading was at 4% which is. the lower explosion limit...........#haha#it sounds like maybe things are back to normal now?? but it's last day of con so everything shuts down early#weirdest convention experience i've ever had by far#i feel so bad for the artists. they lost about a day and a half's worth of sales between the lines and the fire.#but yeah doing two cosplays in one day yesterday and being in cosplay for a total of about seventeen hours?#i'm staying home today lol#pajamas and coffee and writing fic in bed are what's on my schedule ^^#withoutwords#kimblee#zenos#cosplay
9 notes
·
View notes
Text
building a computer taught me that a ssd? smaller than i thought it was. a gpu? much bigger than i thought it was
8 notes
·
View notes
Text




ALEXANDER YOU'RE DOING ✨AMAZING✨ SWEETIE
#computer build24#the ram is being stupid but yknow#i'll have todownload a 3rd party software to get all the lights to sync#BUT!!! CURE MARINE!!!#PRETTY CURE??? IN MY PC BUILD??#you bet your ass
12 notes
·
View notes
Text
just got epic praise at work
#being a ux designer building software on a team of computer engineers means when u design a UI that’s even slightly intuitive#everyone’s like 🤯#.txt
4 notes
·
View notes
Text
Your Guide to B.Tech in Computer Science & Engineering Colleges

In today's technology-driven world, pursuing a B.Tech in Computer Science and Engineering (CSE) has become a popular choice among students aspiring for a bright future. The demand for skilled professionals in areas like Artificial Intelligence, Machine Learning, Data Science, and Cloud Computing has made computer science engineering colleges crucial in shaping tomorrow's innovators. Saraswati College of Engineering (SCOE), a leader in engineering education, provides students with a perfect platform to build a successful career in this evolving field.
Whether you're passionate about coding, software development, or the latest advancements in AI, pursuing a B.Tech in Computer Science and Engineering at SCOE can open doors to endless opportunities.
Why Choose B.Tech in Computer Science and Engineering?
Choosing a B.Tech in Computer Science and Engineering isn't just about learning to code; it's about mastering problem-solving, logical thinking, and the ability to work with cutting-edge technologies. The course offers a robust foundation that combines theoretical knowledge with practical skills, enabling students to excel in the tech industry.
At SCOE, the computer science engineering courses are designed to meet industry standards and keep up with the rapidly evolving tech landscape. With its AICTE Approved, NAAC Accredited With Grade-"A+" credentials, the college provides quality education in a nurturing environment. SCOE's curriculum goes beyond textbooks, focusing on hands-on learning through projects, labs, workshops, and internships. This approach ensures that students graduate not only with a degree but with the skills needed to thrive in their careers.
The Role of Computer Science Engineering Colleges in Career Development
The role of computer science engineering colleges like SCOE is not limited to classroom teaching. These institutions play a crucial role in shaping students' futures by providing the necessary infrastructure, faculty expertise, and placement opportunities. SCOE, established in 2004, is recognized as one of the top engineering colleges in Navi Mumbai. It boasts a strong placement record, with companies like Goldman Sachs, Cisco, and Microsoft offering lucrative job opportunities to its graduates.
The computer science engineering courses at SCOE are structured to provide a blend of technical and soft skills. From the basics of computer programming to advanced topics like Artificial Intelligence and Data Science, students at SCOE are trained to be industry-ready. The faculty at SCOE comprises experienced professionals who not only impart theoretical knowledge but also mentor students for real-world challenges.
Highlights of the B.Tech in Computer Science and Engineering Program at SCOE
Comprehensive Curriculum: The B.Tech in Computer Science and Engineering program at SCOE covers all major areas, including programming languages, algorithms, data structures, computer networks, operating systems, AI, and Machine Learning. This ensures that students receive a well-rounded education, preparing them for various roles in the tech industry.
Industry-Relevant Learning: SCOE’s focus is on creating professionals who can immediately contribute to the tech industry. The college regularly collaborates with industry leaders to update its curriculum, ensuring students learn the latest technologies and trends in computer science engineering.
State-of-the-Art Infrastructure: SCOE is equipped with modern laboratories, computer centers, and research facilities, providing students with the tools they need to gain practical experience. The institution’s infrastructure fosters innovation, helping students work on cutting-edge projects and ideas during their B.Tech in Computer Science and Engineering.
Practical Exposure: One of the key benefits of studying at SCOE is the emphasis on practical learning. Students participate in hands-on projects, internships, and industry visits, giving them real-world exposure to how technology is applied in various sectors.
Placement Support: SCOE has a dedicated placement cell that works tirelessly to ensure students secure internships and job offers from top companies. The B.Tech in Computer Science and Engineering program boasts a strong placement record, with top tech companies visiting the campus every year. The highest on-campus placement offer for the academic year 2022-23 was an impressive 22 LPA from Goldman Sachs, reflecting the college’s commitment to student success.
Personal Growth: Beyond academics, SCOE encourages students to participate in extracurricular activities, coding competitions, and tech fests. These activities enhance their learning experience, promote teamwork, and help students build a well-rounded personality that is essential in today’s competitive job market.
What Makes SCOE Stand Out?
With so many computer science engineering colleges to choose from, why should you consider SCOE for your B.Tech in Computer Science and Engineering? Here are a few factors that make SCOE a top choice for students:
Experienced Faculty: SCOE prides itself on having a team of highly qualified and experienced faculty members. The faculty’s approach to teaching is both theoretical and practical, ensuring students are equipped to tackle real-world challenges.
Strong Industry Connections: The college maintains strong relationships with leading tech companies, ensuring that students have access to internship opportunities and campus recruitment drives. This gives SCOE graduates a competitive edge in the job market.
Holistic Development: SCOE believes in the holistic development of students. In addition to academic learning, the college offers opportunities for personal growth through various student clubs, sports activities, and cultural events.
Supportive Learning Environment: SCOE provides a nurturing environment where students can focus on their academic and personal growth. The campus is equipped with modern facilities, including spacious classrooms, labs, a library, and a recreation center.
Career Opportunities After B.Tech in Computer Science and Engineering from SCOE
Graduates with a B.Tech in Computer Science and Engineering from SCOE are well-prepared to take on various roles in the tech industry. Some of the most common career paths for CSE graduates include:
Software Engineer: Developing software applications, web development, and mobile app development are some of the key responsibilities of software engineers. This role requires strong programming skills and a deep understanding of software design.
Data Scientist: With the rise of big data, data scientists are in high demand. CSE graduates with knowledge of data science can work on data analysis, machine learning models, and predictive analytics.
AI Engineer: Artificial Intelligence is revolutionizing various industries, and AI engineers are at the forefront of this change. SCOE’s curriculum includes AI and Machine Learning, preparing students for roles in this cutting-edge field.
System Administrator: Maintaining and managing computer systems and networks is a crucial role in any organization. CSE graduates can work as system administrators, ensuring the smooth functioning of IT infrastructure.
Cybersecurity Specialist: With the growing threat of cyberattacks, cybersecurity specialists are essential in protecting an organization’s digital assets. CSE graduates can pursue careers in cybersecurity, safeguarding sensitive information from hackers.
Conclusion: Why B.Tech in Computer Science and Engineering at SCOE is the Right Choice
Choosing the right college is crucial for a successful career in B.Tech in Computer Science and Engineering. Saraswati College of Engineering (SCOE) stands out as one of the best computer science engineering colleges in Navi Mumbai. With its industry-aligned curriculum, state-of-the-art infrastructure, and excellent placement record, SCOE offers students the perfect environment to build a successful career in computer science.
Whether you're interested in AI, data science, software development, or any other field in computer science, SCOE provides the knowledge, skills, and opportunities you need to succeed. With a strong focus on hands-on learning and personal growth, SCOE ensures that students graduate not only as engineers but as professionals ready to take on the challenges of the tech world.
If you're ready to embark on an exciting journey in the world of technology, consider pursuing your B.Tech in Computer Science and Engineering at SCOE—a college where your future takes shape.
#In today's technology-driven world#pursuing a B.Tech in Computer Science and Engineering (CSE) has become a popular choice among students aspiring for a bright future. The de#Machine Learning#Data Science#and Cloud Computing has made computer science engineering colleges crucial in shaping tomorrow's innovators. Saraswati College of Engineeri#a leader in engineering education#provides students with a perfect platform to build a successful career in this evolving field.#Whether you're passionate about coding#software development#or the latest advancements in AI#pursuing a B.Tech in Computer Science and Engineering at SCOE can open doors to endless opportunities.#Why Choose B.Tech in Computer Science and Engineering?#Choosing a B.Tech in Computer Science and Engineering isn't just about learning to code; it's about mastering problem-solving#logical thinking#and the ability to work with cutting-edge technologies. The course offers a robust foundation that combines theoretical knowledge with prac#enabling students to excel in the tech industry.#At SCOE#the computer science engineering courses are designed to meet industry standards and keep up with the rapidly evolving tech landscape. With#NAAC Accredited With Grade-“A+” credentials#the college provides quality education in a nurturing environment. SCOE's curriculum goes beyond textbooks#focusing on hands-on learning through projects#labs#workshops#and internships. This approach ensures that students graduate not only with a degree but with the skills needed to thrive in their careers.#The Role of Computer Science Engineering Colleges in Career Development#The role of computer science engineering colleges like SCOE is not limited to classroom teaching. These institutions play a crucial role in#faculty expertise#and placement opportunities. SCOE#established in 2004#is recognized as one of the top engineering colleges in Navi Mumbai. It boasts a strong placement record
2 notes
·
View notes
Text
Should I actually make meaningful posts? Like maybe a few series of computer science related topics?
I would have to contemplate format, but I would take suggestions for topics, try and compile learning resources, subtopics to learn and practice problems
#computer science#embedded systems#linux#linuxposting#arch linux#gcc#c language#programming#python#infosecawareness#cybersecurity#object oriented programming#arduino#raspberry pi#computer building#amd#assembly#code#software#software engineering#debugging#rtfm#documentation#learning#machine learning#artificial intelligence#cryptology#terminal#emacs#vscode
4 notes
·
View notes
Text
It’s hard to make music when you have no instruments or software or skills or talent and also you don’t actually know how to play anything or make music and you’re dumb as hell
#hey it’s about that time of year where I get the urge again to try and make music before getting frustrated and quitting#don’t let your inability to do anything right get in the way of messing everything up forever and ever amen#every time I sit down to try and set up software and whatnot I end up wasting half a dozen hours before giving up#repeat once or twice every year or so for the last decade#how did I used to do this junk??? whaaaaa? I don’t understand computers.#I have an ooooold laptop buried in a box someone with sooo many unfinished songs. albums and albums worth. mostly just missing vocals#I used to sit and work on music for hours and hours#pretty much the only productive thing I did my first year of college was make an album#and now I’m just like… I don’t understand how anything works. I’m so old.#but I guess it’s… ya know… it’s been awhile and you can’t just expect to jump back in with the same skill and comfort#you’ve got get all the tedious beginning stuff out of the way. that’s just how it goes. it builds and builds.#it’s the opposite of eating an elephant. it’s frankensteining and elephant. gotta do it piece by piece.#basically I got another hand me down laptop. clean slate freshly wiped.#then I spent about 5 hours just setting it up and thennnnnn getting a bad virus bc I’m stupid as hell and don’t want to pay for software#I lost my software installer I already had so I rushed to 🏴☠️ the first decent one I could find#and then when I got warnings I said ‘meh the antivirus is probably exaggerating’#ARE YOU KIDDING ME!? ARE YOU STUPID!? you trust the illegal file over your own antivirus!? whatttt!?#i am very stupid#at least the laptop is pretty much empty. just gonna do another clean wipe and start again. hopefully smarter.#I really want this. I hate HATE talking about things I want to do because I invariable always fuck it up#it’s so stupid and sad but if pressed I would easily say my old shitty music are the things I’m most proud of in my life. even if they suck#I stopped making music when I moved to NY to be with my ex and I haven’t been able to get back into it since#I don’t even like music. it’s stupid and I’m half deaf. fuck you I hate you.#okay I love you bye#you can ignore this#text
4 notes
·
View notes
Text
MY DAD MIGHT BUY ME A PC????
#i have to use it to do graphic design stuff for his job so that he can write it off as a business expense but? holy shit?#i was sooo not expecting this but we were talking abt how seniors at my school get special privileges and that includes getting out of#school months early as long as they spend that time on a project which will hypothetically benefit their future careers#and what i had in mind for it which is like. professional internet merch artist stuff. but i mentioned the bit abt how i'd need to build a#pc first bc my computer is busted as hell and can't run any decent drawing software and like. dpi is an issue.#and without missing a beat he was like 'hey could you hypothetically like. design posters' and i was ofc like 'no i'm an illustrator not a#graphic designer' and he was like 'but could you learn' and uhm. holy shit?#the benefits of presenting things as 'this is how i'd use it in a practical capacity' and not 'here's all the video games that won't run on#my piece of shit macbook'. bc i've mentioned my intention of building a pc to him half a million times but i've always led w the video game#he also might pay for photoshop and like. thank god bc i am Not doing that. i'm going to try and get him to cover illustrator too bc i hate#adobe but. vector files :/.#romeo.txt
4 notes
·
View notes
Text

Elevate Your Mobile App with AI & Chatbots Build Your AI-Powered App: Unlock Next-Gen Capabilities Master the integration of AI and chatbots with our 2025 guide, designed to help you create next-gen mobile applications boasting unmatched intelligence. Ready to elevate? This comprehensive guide equips you with the knowledge to seamlessly integrate AI chatbots and advanced AI into your mobile app for a truly intelligent and future-ready solution.
#Generative AI Software Development | openai chatbot#We build custom AI software#OpenAI chatbots#machine learning#computer vision#and RPA solutions. Empower your business with transformative#intelligent AI#Taxi Booking & Ride Sharing App Development Company#Food Delivery App Development Company | Build Food App#Leading eCommerce App Development Company|Hire Developers#Top Education App Development Company | LMS App Development#Custom Real‑Estate App Development Company | Custom CRM App#On‑Demand Healthcare Mobile App Development Company#Fitness & Wellness App Development Company | Calorie Counter App#Affordable Dating App Development Company | Tinder Clone App#Custom Laundry & Dry‑Cleaning App Development Company#On‑Demand Pickup and Delivery App Development Company#Best Social Media & Networking App Development Company#on-demand Beauty Service App Development#Online Medicine Delivery & Pharmacy App Development Company#Custom On-Demand Delivery App Development Company#Android & IOS Marketplace App And Software Development Company#On‑Demand Grocery Delivery App Development Company
0 notes
Text
comp sci is still a great field to get hired within, provided you magically already have 5 years of experience, then the amounts of money they want to pay you are obscene. You’ll make more in an hour than my min-wage part time friends will make in a week. Also everyone’s willing to take you for free. Which is why there are ‘jobs’ in the US tech market. Ask those ‘interns’ how much they’re making. No-pay jobs are illegal in Canada and that’s why no one’s hiring. That’s why the stories about how programmers and otherwise thinking roles in software development are ‘obsolete’ and ‘can be done by AI’. They can’t actually. Firstly because having your AI write your code would require you to give someone like OpenAI, Google or Meta, third parties that are not between you and your clients, protected data, which is insane. Secondly the one non-tech guy you retain or the tech lead you’ve asked to double check the AI’s work but is in Teams meetings from 6 AM to 7 PM, is not going to catch an AI’s various security vulnerabilities. So have fun. “We don’t need software developers anymore” my whole entire sat-in-an-office-chair-for-8-hours ass. Private companies will crumble without us. This is purely a cash thing.
#computer science#software development#artificial intelligence#if you���re trusting an AI to build your website or internal applications—what are they calling it now? ‘Vibe coding’?#Then you better not have any data of consequence on there lmao#Invariably you will. It’s a cute proof of concept but unless your AI is fully inhouse you’re mad to use it#And if you’ve gone to the effort of building your own AI why not sell that product etc etc we’re back to square one
0 notes
Text
#computer games#video games#first person shooters#boomer shooters#id software#doom engine#build engine#apogee software#3d realms#bungie#raven software#monolith productions
0 notes
Text
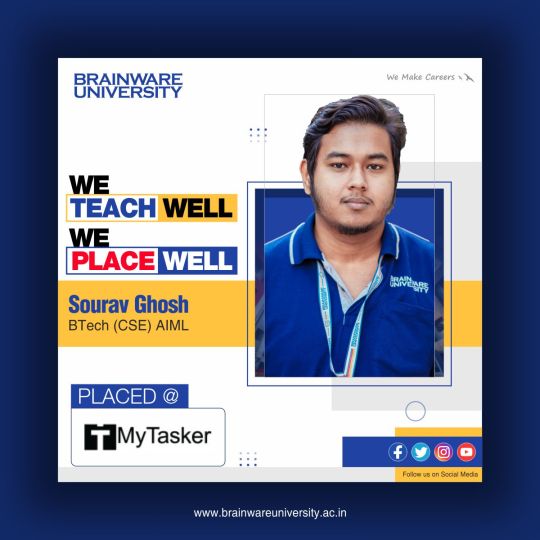
BTech CSE: Your Gateway to High-Demand Tech Careers
Apply now for admission and avail the Early Bird Offer
In the digital age, a BTech in Computer Science & Engineering (CSE) is one of the most sought-after degrees, offering unmatched career opportunities across industries. From software development to artificial intelligence, the possibilities are endless for CSE graduates.
Top Job Opportunities for BTech CSE Graduates
Software Developer: Design and develop innovative applications and systems.
Data Scientist: Analyze big data to drive business decisions.
Cybersecurity Analyst: Safeguard organizations from digital threats.
AI/ML Engineer: Lead the way in artificial intelligence and machine learning.
Cloud Architect: Build and maintain cloud-based infrastructure for global organizations.
Why Choose Brainware University for BTech CSE?
Brainware University provides a cutting-edge curriculum, hands-on training, and access to industry-leading tools. Our dedicated placement cell ensures you’re job-ready, connecting you with top recruiters in tech.
👉 Early Bird Offer: Don’t wait! Enroll now and take the first step toward a high-paying, future-ready career in CSE.
Your journey to becoming a tech leader starts here!
#n the digital age#a BTech in Computer Science & Engineering (CSE) is one of the most sought-after degrees#offering unmatched career opportunities across industries. From software development to artificial intelligence#the possibilities are endless for CSE graduates.#Top Job Opportunities for BTech CSE Graduates#Software Developer: Design and develop innovative applications and systems.#Data Scientist: Analyze big data to drive business decisions.#Cybersecurity Analyst: Safeguard organizations from digital threats.#AI/ML Engineer: Lead the way in artificial intelligence and machine learning.#Cloud Architect: Build and maintain cloud-based infrastructure for global organizations.#Why Choose Brainware University for BTech CSE?#Brainware University provides a cutting-edge curriculum#hands-on training#and access to industry-leading tools. Our dedicated placement cell ensures you’re job-ready#connecting you with top recruiters in tech.#👉 Early Bird Offer: Don’t wait! Enroll now and take the first step toward a high-paying#future-ready career in CSE.#Your journey to becoming a tech leader starts here!#BTechCSE#BrainwareUniversity#TechCareers#SoftwareEngineering#AIJobs#EarlyBirdOffer#DataScience#FutureOfTech#Placements
1 note
·
View note
Text
i just think it’s funny that raspberry pi seems to plan their releases around that of apple’s
#stream#both cult followings ….#that im apart of ………#idk i’ve always been an apple fanthem i guess#perhaps it’s also due to me growing up poor & seeing it as a status symbol but by the time the 5s or so was released they had started being#subsidized for the poors following the monopoly breakup w at&t so i had an what was it it was either an 8 or 16gb 4s for 99c in#it was 2014/2015 or so i don’t remember i still have that fucking phone the back cracked bc my sexy fatass geometry teacher fucking stepped#on my binder on accident during a test u know when in school u had to put ur bag or binder at the front of class during tests#but i also got an ipod touch in like 2012 i think loved it it was green my mother got it for my brother & i for christmas#& that’s when i hopped on the Dual Phone Train#never grew out of it#i had an 14 & se 1st gen now i’m triple wielding bc i got robbed so ptsd ive got 12 mini 15 ? 16 ? idk i dont use it it just stays home that#the tx phone bc it doesn’t have a sim card slot as american so it’s esim only therefore literally an ipod#& that’s what i use it as - i also have my us whatsapp on there & i use it to call my banks#but that’s like once a month#so#triple wielding w the se#i hate the new ios like ios 18 it’s gotten too complicated#literally loved apple bc of its simplicity idk as if i didn’t get a pi to get into software & webhosting as was my dream as a child#literally in elementary school i wanted to build my own website so bad i literally went to the library & was reading books on how to build a#server then i asked my parents & they were like ‘wow that’s so cool :) we don’t have any money :) that’s why u were at the library :) & know#so much about libraries :) bc they’re free :) bc ur poor :)’ ALSKALSKALKSLAKSLALSASL#MORE PPL NEED TO USE LIBRARIES#blessed to live like down the street from a library#actually blessed to literally be living in a ‘15 minute city’#also accidentally ordered a compute module 4 so :/#i thought i was ordering the module 5 ALSJALKSLAKSLAKSLAKSLAKSLKSLA#RASPBERRY DROP THE 5S I KNOW U GOT STOCK FUCK U#i’m literally going to make a dual cloud hosting server & also a website host so i can finally provide my family back home w a website for#them to see when i take pics & stuff
1 note
·
View note
Text
Some updates on things
So, this is the first time I’ve cross-posted from WordPress to Bluesky, Mastodon, and Threads, although Twitter is no longer part of that equation because you can’t cross-post to Twitter any more due to the changes made! This post also serves as a test to see if my connections all work properly; I eventually want to self-host WordPress, but that’ll be a bit later on! I was initially going to post…
#2024#computer hardware#computer repairs & upgrades#computers#Content Creation#Legacy PC hardware#Legacy PC software#linux#New hardware with older hardware#New PC Build#operating systems#PC (Platform)#PC updates#PC upgrades#Retro Computing#retro hardware#retro pc hardware#Steam#Storm&039;s Workshop (SGU)#Twitter#Update
1 note
·
View note
Text
The societal implications of digital WMDs - CyberTalk
New Post has been published on https://thedigitalinsider.com/the-societal-implications-of-digital-wmds-cybertalk/
The societal implications of digital WMDs - CyberTalk
Bryan Neilson is an experienced Cyberspace & Intelligence Operations professional who built his career supporting Cyberspace Operations, Intelligence Collection, and Counterintelligence for the U.S. Intelligence Community. Bryan’s work, which has spanned the globe, can be directly tied to saving the lives of countless officers and assets, enabling of kinetic military objectives, and helping to build and maintain the strategic advantage of the United States throughout Cyberspace and beyond. Fusing his proficiencies in Cyberspace Operations and Human Intelligence, Bryan has become a trailblazer in his industry and has brought his unique expertise to Check Point Software Technologies – where he serves as Regional Architect, Evangelist, and global Subject Matter Expert in Sophisticated Cyberspace and Intelligence Tradecraft.
In the last several days, the cyber security industry has been rocked by a rare acknowledgement from U.S. Government Officials regarding the likelihood of extensive compromise of U.S. Critical Infrastructure by specific state-sponsored hacking groups. In a rare public pronouncement, the United States’ National Security Agency (NSA) revealed the extent to which it (and other federal agencies) believes that specific Nation-State sponsored actors have been actively and successfully engaging in broad campaigns to compromise various systems controlling critical infrastructure components within the U.S.
It has been a long-held belief among many cyberspace professionals that sophisticated state-enabled offensive actors have been actively and covertly compromising various critical infrastructure systems and networks across the United States and its allies – activity that has been on-going for several years. Nevertheless, these public statements from the NSA – an organization known for keeping such issues and ‘troubles’ concealed from the general public – suggest mounting concerns among U.S. intelligence, military, diplomacy, and congressional officials.
Furthermore, U.S. officials have noted how this observed ‘buildup’ is predominantly targeting critical infrastructure systems of little to no intelligence value; thus, raising alarm that the motivation behind this activity is for the sole purpose of gaining a strategic advantage (the ability to disrupt U.S. and allied critical infrastructure) in the event conflicts arise.
Since early 2023, when the NSA and Microsoft collaboratively identified and publicly-revealed the existence of China’s Volt Typhoon program and alluded to the extent to which this mission had gained strategic access among critical infrastructure, worry throughout Washington has been mounting. The primary concerns are three-fold: A) strategic pre-positioning and control over U.S. critical infrastructure represents a substantive threat to the United States government, economy, and society; B) such wide-ranging pre-positioning has the potential to fundamentally shift the balance of power and displace the United States’ strategic advantage and dominance within the Cyberspace Domain; and C) such pre-positioning activity positions adversarial nation states with a “first-strike” capacity against the United States. These concerns have been echoed by Air Force General Timothy Haugh (Commander of U.S. Cyber Command and the top military official in the United States for cyberspace), in a telling statement made to the Washington Times, “We see attempts to be latent in a network that is critical infrastructure, that has no intelligence value, which is why it is so concerning.”
Recent public statements from the NSA and the subsequent comments from the Commander of the U.S. Cyber Command paint a rather bleak picture for the continuing security of United States critical infrastructure – and in turn, the future stability and resiliency of the U.S. government, economy, and society. Nevertheless, it is imperative to remember that this pre-positioning activity some U.S. adversaries are being accused of is neither new, unprecedented, nor, legally speaking, an act of outright hostility. Many countries with cyberspace operations capacities that are at least moderately sophisticated are actively engaged in the premeditated, organized, nation-sanctioned, and clandestine compromise of systems and networks for the sole purpose of gaining a strategic advantage over their adversaries – the United States being no exception. Lacking the critical element of direct and overt hostility, such activity is predominantly viewed and handled in the same manner as espionage, rather than actions indicative of war.
Chartered, in part, with maintaining and increasing the strategic advantage and dominance the United States has long held throughout the cyberspace domain, U.S. Cyber Command actively engages in this same strategic pre-positioning targeting U.S. adversaries. Such maneuvers intend and ultimately result in the compromise of and surreptitious control over thousands of systems and networks deemed advantageous to the interest and strategic advantage of the United States (systems and networks critical to the governmental, military, economic, and societal functions of other nations). This type of activity neither intends nor results in any immediate denial effect and therefore, does not meet the legal standard of Cyberspace Attack – a hostile act. Rather, this type of activity is more aligned with acts of Cyberspace Exploitation.
Understanding this subtle yet crucial nuance between cyberspace attack and cyberspace exploitation is paramount to properly framing the situation that the world now faces. Cyberspace attack and cyberspace exploitation are two sides of the same coin. While both seek the compromise of systems, networks, data, and other assets, they fundamentally differ in both execution and motivation.
Cyberspace Attack, being of more substantial concern, consists of acts carried out within or through the cyberspace domain that have either the intent or result of causing immediate denial effects (defined as any form of degradation, disruption, or destruction). Actions carried out in this manner are still classified as Cyberspace Attack, even if this denial effect impacts resources outside the cyberspace domain. Cyberspace Exploitation, on the other hand, does not arise from the motivation of causing an immediate denial effect. Rather, Cyberspace Exploitation consists of acts of espionage or enablement carried out within or through the cyberspace domain. Lacking any motivation or outcome of an immediate denial effect, acts of Cyberspace Exploitation are not considered directly hostile and, from a legal, military, and diplomatic perspective handled much differently – through espionage, military maneuvers, counterintelligence, international pressure, and diplomacy. Notable however, is the standard setting forth “Enablement Activity” as an act of cyberspace exploitation. Such enablement activity consists of actions carried out for the purpose of enabling future activity or operations within or outside the cyberspace domain – regardless of the intent, motivation, or ultimate outcome inherent to such future activity.
Cyberspace Operations (which includes the aforementioned Cyberspace Attack and Cyberspace Exploitation, along with Cyberspace Security and Cyberspace Defense) establishes the current legal, military, and diplomatic doctrine and framework adopted by a majority of countries. The pre-positioning activity that is now raising alarm within the United States, while concerning and notable, represents non-hostile enablement activity within the discipline of Cyberspace Exploitation. The inclusion of “enablement activity” under the umbrella of Cyberspace Exploitation is a direct causal factor in the increased targeting and successful compromise of critical infrastructure systems around the world.
The rapid expansion in actors capable and willing to engage in cyberspace exploitation combined with the relative ease by which many critical infrastructure components can be compromised has led to a new “Mutually Assured Destruction” (MAD) style buildup of offensive capabilities and strategically pre-compromised and controlled critical assets. Though not directly hostile, this enablement activity does tactically position an actor to have control over the critical infrastructure of another country – thus providing the actor the ability to cause substantial damage to the country’s government, military, economy, and society.
Today, the world finds itself again in the grips of a transformed Cold War – watching the proliferation, buildup, and strategic placement of weapons of mass destruction. Reminiscent of global issues faced in decades past, this race towards mutually assured destruction is now driven by computer code rather than fissile material – a new age of weapons known as Digital Weapons of Mass Destruction.
The implications go beyond the direct impacts these digital WMDs would have on the physical world to the social and psychological impacts that they could have on people. In his 1955 book titled, “The Sane Society” social psychologist Erich Fromm describes the “Socially Patterned Defect”: a systemic illness underlying and inherent to modern societies, that absent the distractions of modern technology, would present in clinical signs of neurosis, psychosis, and socially-deviant behaviors among the population. Though more than half a century has passed since originally theorized, the hypothesis of a Socially Patterned Defect has been tested and upheld throughout the decades – even in today’s modern world. The aggressive adoption by modern societies of technologies providing on-demand access to real-time communications and information represents a new social and public health threat posed by such Digital WMDs. Unfortunate, but true, is the fact that most societies and individuals within the modern world are ill-prepared and would be effectively unable to function in a world without the modern technologies they have come to rely on.
Consider, as one example, the very real possibility of disruption to a nation’s power and communications infrastructure. While undoubtedly damaging to the nation’s government, military, and economy, the impact such an event would have on the society could be far more substantial. The co-dependency and reliance most modern societies have on current technology creates an ideal comorbidity condition where, any unexpected, immediate, and long-term absence of such technology could have the potential of causing this Socially Patterned Defect to emerge – resulting in mass disorder, public health and law enforcement crises, and ultimately societal and government collapse within the impacted population(s). Such effects resulting from a population’s loss of modern technology are not simply theoretical but have been observed on numerous occasions (and in relatively small scale) in the aftermath of recent natural disasters. This scenario represents a simple and limited-in-scope example of what is possible and of interests to sophisticated actors today. Considering the enablement activity being observed intends to acquire control over the whole of a nation’s critical infrastructure (communications, energy, emergency services, healthcare, transportation, and water systems – to name a few), the outcomes could be even more grave.
While the totality of impact such Digital WMDs would have on society seems dire, there is hope on the horizon. In May 2024, the United States Department of State published the “International Cyberspace and Digital Policy Strategy”. Laying the foundation for a brighter, more secure, and more sustainable future, this policy seeks to set the cornerstone of a more diplomatic approach to cyberspace. Though seen as a watershed moment in the history of cyberspace, it is important to remember that these efforts are still very much in their infancy and will take years to fully formalize and canonize; and could be easily disrupted should tensions between key nations reach a point where conflict involving hostile actions within or through cyberspace seem warranted. Until such time, this new strategy is only complementary to and in no way contradicting or superseding the current military-minded doctrine of cyberspace operations.
With the stakes so high and any global realignment of doctrine so far off, it now rests on the shoulders of the global collective of cyberspace operations and cyber security professionals to help drive the world to this more secure reality – one where Digital WMDs are less prolific and the thought of triggering such weapons is considered a taboo in the same vein as the use of nuclear weapons. As an industry, the most powerful countermeasures are not the cyber security technologies – they have time and again proven inadequate and unable to stand up against sophisticated offensivecapabilities – but rather the knowledge, expertise, good nature, and voices of these unique professionals. In the interest of prevention, advocating for non-proliferation, disarmament, and international oversight and control of Digital WMDs is essential. Through this, governments can be pressured to ensure such weapons are rarely used; and if so, are employed in a restrained manner accounting for all reasonable measures to ensure societal stability. While seeking prevention would be ideal, mutually agreed global disarmament and restraint among nations who possess (or who could easily develop) Digital WMDs is doubtful. Therefore, a measure of focus must be shifted to preparation and response rather than prevention.
With this new Cold War being fought out within a realm that is largely intangible and through actions rarely perceptible or considered, the seriousness and criticality of the situation the world now faces is often overlooked or not entirely comprehended. Just as populations around the world took measures in preparation for nuclear war throughout the mid-20th century, the world once again must proactively prepare for the possibility of conflict involving actions taken through cyberspace intended to result in disruptions to critical infrastructure. Everyone, from individuals to the largest organizations and educational institutions, to governments must preemptively address these threats and plan for a reality where critical services are made unavailable for an extended period of time.
Organizations can take strategic and common-sense measures to help ensure they are better prepared for such possibilities. Building comprehensive Continuity of Operations Plans that include contingencies for loss of critical infrastructure is fundamental. Through this, organizations should identify resources and services that are deemed critical (those a company would be unable to function without) and identify alternative means of operations should these resources and services be made unavailable. Organizations should also seek to establish substitute communications strategies, alternate work site locations, and disaster-scenario personnel reporting requirements. Additionally, any continuity of operations program should account for identification and loss of human resources that provide or hold critical knowledge for the organization.
To be more proactive, organizations should build teams (or partner with services) to provide real-time monitoring, investigations, digital forensics, incident handling, cyber threat intelligence, and proactive threat hunting capabilities. Governments must also come to the table and lower the bar for entry to build strategic public-private partnerships for the purposes of sharing critical information and intelligence. While sophisticated offensive activity can very likely go unseen even with the latest incident response strategies, technologies, and intelligence, this remains the best method of identifying and curtailing the compromise of critical systems for the purpose of pre-positioning. Furthermore, where employed, organizations should exercise restraint in the use and deployment of counteroffensive capabilities, actions, and services to avoid causing further escalation.
Lastly, while an uncomfortable conversations, all organizations and individuals must come to grips with the limitations and fallibility of many modern security technologies. Where most of these technologies are employed, a sobering fact must be acknowledged: no matter how robust a system is believed to be, the likelihood of previous, current, and ongoing compromise by a sophisticated actor is unquestionable – even more so for any system controlling or maintaining critical infrastructure. Nevertheless, there do exist some truly capable frameworks employing a consolidated and comprehensive approach coupled with AI-powered and cloud-delivered next-generation capabilities. Leveraging these advanced all-encompassing solutions (such as the Check Point Infinity Platform) remains the only method proven successful in preventing sophisticated offensive activity.
#2023#2024#accounting#adversaries#ai#AI-powered#air#air force#amp#approach#assets#book#Building#career#Check Point#Check Point Infinity#Check Point Infinity Platform#Check Point Software#China#Cloud#cloud-delivered#code#Collective#command#communications#Community#comprehensive#compromise#computer#computer code
0 notes