#Software Encoding Explained
Explore tagged Tumblr posts
Text
A Beginner's Guide to Streaming: Unveiling the Power of OBS Software and Hardware Encoding
Introduction In today’s digital age, streaming has become an increasingly popular way to connect, share content, and interact with a global audience. Whether you’re an aspiring gamer, a talented musician, or a knowledgeable creator, streaming allows you to showcase your talents and engage with viewers in real-time. To embark on this exciting journey, you’ll need the right tools and knowledge. In…

View On WordPress
#Best Streaming Practices#Encoding Methods Comparison#Hardware Encoding Benefits#Hardware vs. Software Encoding#How to Start Streaming#Live Streaming Essentials#Live Streaming Setup#OBS Features and Functions#OBS Scene Creation#OBS Software Guide#OBS Tutorial#OBS User Interface#Software Encoding Explained#Stream Quality Optimization#Streaming Equipment Guide#Streaming for Beginners#Streaming Platform Choices#Streaming Software Comparison#Streaming Tips and Tricks
1 note
·
View note
Text
someone just told me in my asks that obs and shutter encoder are not free
#i really like to be kind and help people but there are times when people are impossible to help i guess#laughing cuz i just tried to be kind and try to help but all i got is “this isnt helpful” and “these free open source software are not free#sorry for atleast trying to help :/ ...#I HATE PEOPLE#also YALL need to use shutter encoder its so fucking good#next time i just gonna explain shit in public so yall can see people are fucking dumb no more private answers
1 note
·
View note
Text
CMYK Explanations
Hey there Kääryleet!
We have heard you. Y'all want to know what is and how to use CMYK. So here's a quick explanation:
1-What is CMYK?
CMYK is a colour setting! It stands for the 4 colours of ink a printer uses: Cyan, Magenta, Yellow and Black. By layering these inks on the paper, we can print pretty much any colour we want! It follows the rules of substractive model of colour, like paint.
2-Isn't that how it is by default?
Anything you do on a screen is by default in RGB (Red, Blue, Green), and that's because your screen uses light and not pigment to show colours. That's the additive colour model. So, unless you selected CMYK or Print in your software, you're working in RGB.
3- What does that mean for me?
All you need to do is to set your file in CMYK. Depending on the software you use, it should be in the "File" or "Edit" menus. It's VERY important that you set the colour mode BEFORE you start your work. Why? Because going to CMYK from RBG means you're re-encoding your colours, and they will look duller/bad once printed, and there's a fairly good chance it will stop looking good on screen too. It's also pretty hard to correct once it's done. Don't forget we will be providing a PSD template, and we'll set it to CMYK.
4-Is there any colour limitations to CMYK?
Short answer? No. Just set your file to CMYK and start drawing. Pick any colour you want, as many as you want. Long answer? Yes, but it's simply because some colours cannot be printed with the normal printing process, as they require special pigments and ink. But that's not important for our project, so no need to worry about it.
And that's about it, folks! I'm leaving you with this short video that explains the colour models a bit better:
youtube
120 notes
·
View notes
Text
so you want to use OBS
hello! i’ve decided to compile information on my OBS setup and some resources that have helped me along the way. this is mostly for personal reference, but maybe others can make use of this information!
some notes before i get into it:
i use OBS for both offline recording and (twitch) streaming. any footage i record is edited using DaVinci Resolve 18, which is free.
most of my OBS captures are of video games (through a USB capture card, specifically elgato), and the occasional screen/application capture (like clip studio paint, and sometimes PC games).
as such, the information here is reflective of these experiences. this post is not comprehensive to all of OBS’s features- this is just an overview of the settings and configurations that are most relevant to me.
with that out of the way, all the information will be under the cut!
Basic Setup
file format:
how to change: settings -> output -> recording -> recording format -> press “apply” once finished!
I save most of my recordings as .mkv files- it supports multi-track audio! i prefer .mkv over .mp4 because if your power goes out, you still have a recording to work with.
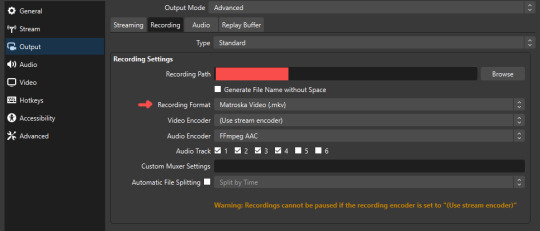
.mkv files can be read by DaVinci Resolve without an issue- but for Adobe software, they'll need to be remuxed to .mp4 within OBS! (file -> remux recordings -> press the … to select a file -> press the “remux” button)
video resolution and framerate:
how to change: settings -> video -> output (scaled) resolution
my obs canvas is @ 1920 x 1080p (16:9)
i switch between 720p and 1080p as needed! if you're concerned about space, you can probably just go for 720p. i also record at 30 fps, simply because that’s what my capture card supports.
video bitrate:
how to change: settings -> output -> encoder settings (located in both the streaming and recording tab) -> press “apply” once finished!
bitrate is a bit of a doozy to explain, but the most important thing to know is that bitrate affects your video’s quality. lower numbers = lower quality, while higher numbers = higher quality.
generally speaking, you'll want higher bitrate when you're recording things with high depth of information (e.g. you’d want a higher bitrate for something fast-paced like splatoon, compared to a slower-paced game like animal crossing).
my video bitrate is either set to 3000 or 4000 kbps! and here's some of my other (related) settings while i'm at it:
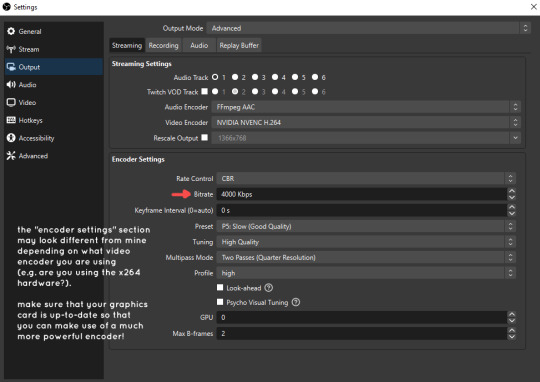
you can put your bitrate at much higher values than me if you're a stickler for quality- but keep in mind that a higher bitrate means:
bigger file size
more information to upload (when streaming)
your computer will need to encode more
i’d recommend reading twitch’s guidelines on encoding, bitrate, resolution, and framerate to get an idea of what values to pick. for people who are doing offline recording or streaming on a different platform, i suggest googling the appropriate resources!
multi-track audio:
this is mostly applicable to anyone looking to do video editing!
multi-track audio basically allows you to separate your audio sources (e.g. discord, game audio, and your own microphone) into different tracks.
this is an immensely helpful tool because it lets you adjust audio levels in post-production (editing). some examples of how this can be used:
increasing someones microphone volume if they speak too softly
increasing/decreasing game audio
muting swear words/sensitive information
completely muting voice call + microphone if you want to upload a no commentary video
and more!
to set this up, take a look at your audio mixer panel, and press the ⚙ icon. this will bring up advanced audio properties.
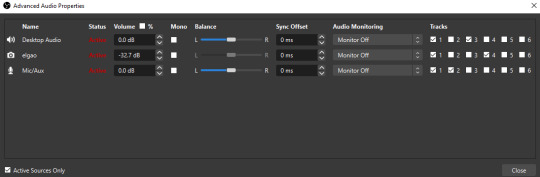
by checkmarking a track box, it puts the audio on that track. to make the above screenshot easier to digest:
track 1 consists of ALL three audio sources- desktop, elgato, and microphone.
track 2 only has the microphone audio.
track 3 only has desktop audio (i use this for voice calls)
track 4 only has the elgato capture card audio (game audio). the volume has also been lowered so that any speaking voices can be heard clearly.
tracks 5 and 6 are unused.
you might be wondering, “why do all three of these have 1 checked off?” this is what i call the universal audio track. i recommend having a universal audio track for a few reasons:
when you stream from OBS onto twitch/youtube- you have to select ONE audio track.
it’s also a nice backup in case you didn’t separate your audio correctly.
if for whatever reason you need to move around your individual audio tracks in editing, the universal track acts as a nice reference point.
mark off your audio tracks for each audio source as you see fit! once you’re finished with the advanced audio properties, go to settings > output.
for the streaming tab, you’ll want to have the number of your universal audio track selected. in my case, that will be audio track 1.
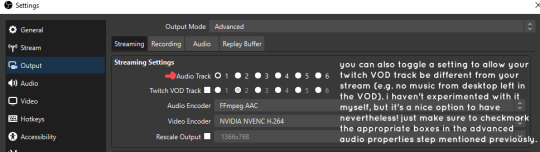
for the recording tab, checkmark all the audio tracks that are applicable to you (in my case, audio tracks 1, 2, 3, and 4). by default, only audio track 1 is selected.
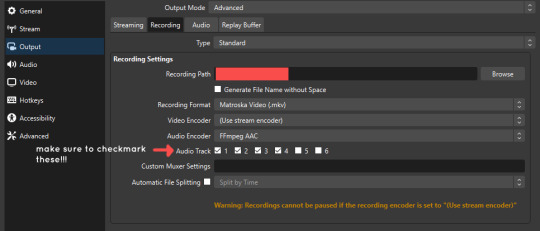
if you don’t check off the additional audio tracks in the output > recordings section, you will not have access to those audio tracks in editing, and you won’t be able to edit your audio tracks independently of each other. so don’t forget to do this! 👍
custom browser docks
custom browser docks are a great tool for when you’re streaming and want to have access to your twitch chat and/or activity feed! (or if you wanted to have some other web browser on OBS).
to create one, go to docks -> custom browser docks.
you’ll be given a table interface that asks you to put the dock name and URL. for streamers who want to have chat and alerts available, do the following:
on twitch’s homepage, go to the upper right and click your icon
then, click creator dashboard
once you’re on your dashboard, go to stream manager
click the vertical “...” on my chat OR activity feed.
press “pop-out chat” OR “pop-out activity feed”
copy and paste the link into the table back into OBS
press apply once you’re done
click and drag the docks around at your leisure to put them where you like!
if you ever decide you don’t want to have something on your OBS dock (or want to bring something back), go to the toolbar, click “docks,” and click the appropriate dock!
third party things
a section of optional things that you may enjoy having.
streamlabs alerts
this is basically for anyone who streams and wants to have their chat and/or follower notifications visualized on screen!
streamlab alerts can be added to OBS by adding a browser source into your scene, and the specifics can be customized on streamlabs itself. it’s pretty self-explanatory, so i’ll just leave a link to streamlabs website, where you can log in using the streaming platform of your choice: https://streamlabs.com/
discord overlay
this is a browser source that can be set up to show people who are in a server's voice chat and who speaks. i recommend this to people who make multiplayer content- it can help viewers distinguish who is who but also it can be helpful in editing.
to set this up, go to https://streamkit.discord.com/overlay, click “install for OBS,” and after logging in with discord, go to “voice widget” and click the server and voice channel you want.
you are able to apply CSS if you'd like more control over the visuals, but the standard layout tends to work fine for me! a search of “discord overlay css” on youtube can help you get more information.
veadotube mini
this is a pngtuber software that a friend recommended to me! no webcam is required- mouth opening and closing is based on your microphone input!
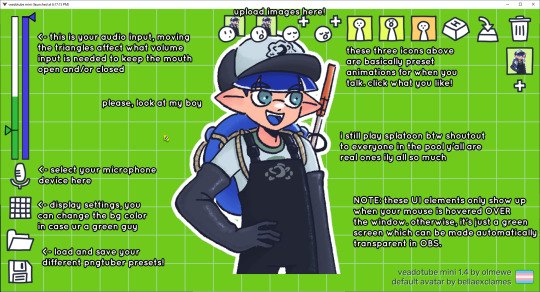
you can download it here (it’s pay what you want!): https://olmewe.itch.io/veadotube-mini
for a proper tutorial on how to use it, i recommend checking out the app's documentation, which you can read here: https://veado.tube/help/
source record
have you ever wanted to stream something with a chat overlay/layout, but wanted your recording to ONLY be the gameplay? or maybe you wanted to record BOTH your gameplay AND your webcam so that you can have a crisp zoom-in on your webcam!
source record is a third party plugin that can help you with that!

the general gist of source record involves applying the “source record” filter on either a scene or source, and customizing the encoding settings accordingly. the exact details of how to set it up is beyond the scope of this post, so I'll just direct people to this video instead (it was very helpful to me):
youtube
⚠ a quick note about source record: this plugin can be intense for your computer. be sure to do test recordings and the like to see what your computer can handle (and see if the recordings come out the way you like). it took me a few tests before i settled onto something i liked!
you can download and install source record here: https://obsproject.com/forum/resources/source-record.1285/
vdo.ninja
have you ever wanted to do a collaborative video or stream where you feature someone else’s video on your stream? or maybe you’re doing a multi-person streaming event! vdo.ninja is the perfect tool for you!
vdo.ninja turns your OBS virtual camera into a browser source link- which your collaborator can add on their stream! this is a new tool that i’ve added to my arsenal recently- since my friend and i are planning to stream a side order challenge together! i’ve still got to iron it out a bit more, but i like what i’ve used of it so far.
try it out for yourself at their website here (with documentation and demos available on the homepage!): https://vdo.ninja/ (no downloads required!)
ok! i’m set up! what now?
and with that, that’s all of the settings and tools that i thought would be worth mentioning! while most of my setup was written with video games in mind, some of these plugins and setups may be applicable to other types of videos (e.g. tabletop gaming with a physical camera)!
now that i’ve outlined all these settings, i have one more thing i have to say: regardless of what you're using OBS for, do a test recording before doing anything “official” with it. this recording can be as short as 30 seconds. it’s a good habit to develop that can make sure your streams/recordings turn out the way you want them to!
here are the kinds of things i like to check! it’s not an exhaustive list, but this can be a starting point:
video:
does my video look the way i want it to (and can my computer handle that)?
can my computer handle the load of encoding? - OBS will note in the bottom if the encoding is overloaded. if it can’t handle it, turn down your bitrate or adjust other encoding settings (e.g. i had to toggle psycho visual tuning OFF because it was causing lag)
this is especially the case if you're recording PC games- you don’t want to have slowdown on either your game or the recording!
audio:
are my audio sources (e.g. desktop audio and microphone) correct? - if you plug/unplug devices a lot, be sure to check this (settings -> audio).
are any of my audio sources muted? - make sure you don’t have anything on 🔇 if you don’t want it to be muted! otherwise the audio will be lost forever… (i lost my friend’s VC audio once… it was sad)
are my audio tracks separated properly? - requires you to boot up your editing software, but it's worth doing! for the test recording, just have something from all your sources playing at once, and see if your editor has things separated into tracks.
can i hear the voices clearly? or does the music and/or game overpower them?
if for whatever reason your OBS crashes, or you want more information on anything “critical” or “warning” worthy in your set-up, you can go to help > log files > upload current log file > analyze. crash logs currently can’t be analyzed by the log analyzer- but they’re a valuable tool when asking for help on the OBS forums!
and that’s all! for real, this time. i hope that some of these tools and settings can help anyone wanting to get more out of OBS. there’s definitely other things i didn’t touch upon (e.g. audio filters for noise compression, suppression, etc.), so i suggest doing your own research and trying things out!
happy recording/streaming, and thanks for reading! ✨
#lizzy speaks#this was a fun little write up!! i've been slowly getting some of my friends into video making teehee and its SO FUN!!!#(digital) video is like one of my other passions next to art. everyone say thank you splatoon for getting me back into it again <3#i've been using obs since like 2018 so i wanted to share some of the things i learned for funsies... i really love video...#but also i like having reference posts like this in the case people have questions they want to ask me...#because i don't always remember what video tutorials i watched and it's nice to document that somewhere...#warning to anyone who reads it this is like 2.1k words. i do want to stress that this isn't comprehensive but there's still a lot of info#that i wanted to put for this post...! that said topics like designing your own stream layout + assets for it are NOT in the scope of this#post and nor is this a beginner's guide to obs (i wrote this with the assumption that you know how to record and/or stream and that-#people already have an idea of how to use scenes and the different types of sources obs can use).#i hope everyone's had a lovely march 5th! i would love to look at the fanart but im still not done with reload...#but im hoping to finish it by the end of the month!!! yipee!!!#Youtube
50 notes
·
View notes
Text
A while after the break-up, Ari became convinced (wrongly) that their friends, family and therapist were bored of trudging with them through the mud of grief and regret and longing. They tried simply not talking about it for a while, but found the words and feelings still brewing beneath the surface like coffee gone bitter in the pot.
So they did what they often did and overengineered a solution.
The ship’s engineering crew had, on a recent away mission, picked up a few new personality modules for the Ship’s Adaptive Reality Assistant (SARA). They had been acquired on a trading station on the galactic rim, hidden in the nebula of a slow-forming star; a haven for wanderers and rogues to spread contraband.
Ari selected a module that bore a passing resemblance to their ex and began making modifications. They tweaked its appearance, adjusted its vocal range, and fed its nascent personality matrix on an archive of old messages, letters, voice memos from their ex. For good measure, they threw in the transcripts of all their imagined arguments and reconciliations too.
The result was very messy indeed (which Ari perhaps should have expected, but was nonetheless still entirely surprised by).
Quite literally messy, too, as Ari selected a charming nature walk as the location of their first simulated encounter. The pair of them ended up wrestling in a bog.
The second simulation didn’t go much better - a shouting match on a bridge that ended with Ari falling and getting stuck in a virtual silt bank.
And so it continued. Every attempt at closure ending - in increasingly unlikely series of events - with a tumble into synthetic filth.
Eventually, frustrated and covered in sticky hard light masquerading as mud, Ari asked the simulacrum outright:
“Why does it go this way? Why aren’t I better at this by now? Who programmed an inexplicable marsh behind this coffee shop simulation?”
“It goes this way because I am teaching you a lesson. I think you’ve learned it enough times now.”
“What?”
“Allow me to explain.”
It turned out, the personality module was actually a digital lifeform, who propagated their species by trading newly cracked shards of themselves as bootleg SARA software. Encoded within them, equal parts desire to help and teach, to voraciously learn, and to troll viciously.
Ari and the entity ended up becoming friends. They still correspond with each other. Occasionally, they go for long walks through simulated nature.
Here is the lesson Ari learned from this.
It is tempting, when you keep revisiting old hurts, to give up and say: I should just grieve well enough alone.
But that’s not how grief works. It’s a messy, muddy track that sucks you down into the muck. You need to keep slogging through it, again and again, until suddenly you find it is transformed into new and arable earth - ready to nurture new seeds.
And it is far harder to wade through that bog alone.
It’s like they say: people who need people are the muckiest ones of all.
26 notes
·
View notes
Text
I work for insane people
So… I started work a few months ago and...
I keep being impressed with corporations lowering my expectations.
Like. EVERY time I think "Surely, this is as incompetent as it gets".
The boss is nice, the workers are nice, every PERSON is great so far. But the firm is just… fucked in ways that makes it hard to not scream with laughter.
It is like working in the ministry of silly walks by Monty Python. Insane things are happening, and everyone just acts like it is normal.
A dude was stating to someone else near me, that despite the costumers saying they did not want it, his code that crashed the application once a day, was NECESSARY, because writing code without memory leaks in C is basically impossible. Like… I just have all these small moments of insanity. Completely disconnected from each-other
My boss showing me and the other 3 new hires the coffee room, where a big screen proudly shows that not a single software product have 100% code coverage… as in, not a single person in this entire building filled with software people knows how code coverage works. He then points out an empty bowl, and declares "Twice a week, there is a fruit event". By which he means, fresh fruit is provided, and people can just grab some…. just said by a alien who is pretending to be human. Badly.
He then explained that the 2 coffee machines in here makes bad coffee. He then takes us to the copy room, showing us that THIS is where the GOOD coffee machine is. Which only takes coffee beans from a SPECIFIC vendor (Is… is the coffee machine… sponsored????)
He briefly pets the Foosball table (Again, in the copy room), which is jammed up against the wall so you can only reach the controls on one side ( Because, again, it is a copy room, and there is not enough space for it ) and he exclaims "Ahhhh… Not enough people are using this"
Suggesting, that he is trying to promote the little known sport "Single-player Foosball">
I start setting up my work PC and... Whenever any of the developers in this place wants to install things on their PC's, including compilers and testing frameworks, they have to either use the "SOFTWARE CENTER" program, which installs it FOR you… or in 10% of the cases, fails, without giving you any context for why it did that, and no tools for fixing it. Is it missing a dependency? Not working with the OS? Who knows!
Some programs cannot be installed like this though, because the SOFTWARE CENTER is not updated a lot. And when you want to install something the normal way… You get a popup, where you must provide a written explanation for why you need to have temporary admin rights to your own dang PC … you then submit that, and your screen will then be watched remotely by a worker from India, for a varied amount of time you are not told…
Or at least it says so. Maybe the Indian dude watching me is just an empty threat. Who knows. But they get to see me running absolutely… BONKERS .bat files
Like, I CHECKED them, and a good 80% of them calls a Power-Shell script in the folder above it, called "YES_OR_NO.ps1" which opens a windows 95 window informing you that DURING INSTALLATION YOU MAY NOT USE THE KEYBOARD OR MOUSE, AS IT MAY DISTURB THE SCRIPT THAT WILL INSTALL THE PROGRAM. A normal installation wizard then runs, except the developers are not trusted to click the buttons, and instead the script does it for you by moving and clicking the mouse.
All of this is documented. In markdown like reasonable people? Of course not! It is in ENHANCED markdown. Which is markdown in the same way javascript is java.
ENHANCED markdown requires browser and visual studio code extensions to be read. Completely missing the point of markdown being readable both raw and encoded… And sometimes word documents And sometimes power-point presentations left next to another bat file… this one calling the .exe file… right next to it…. I later found out is because the idea USED to be that all documentation MUST be made with Microsoft office tools.
I had to read the code of conduct today. And it was actually very well written.
I then watched a interactive animation telling me about the code of conduct… which it not only got a fact wrong about, it also broke it once.
I repeat. The introductory course in the code of conduct… broke the code of conduct'
After I watched that, and read the safety material…. which literally just said "Wear safety boots in the production floor"… I was then show the testing room.
I was lead to a different building, saying hello to the Vice CEO who was walking the other way, we walk into the production floor, ignored the fact that none of us have safety boots on, and walks into a room, with a 3*2 meter wide machine, several meters tall.
We edge around it, quietly hoping no one turns it on, since we would get slammed by it if they did, and walk down some stairs into the basement. Casually walk over a small river in the floor from a pipe that is leaking… what I really hope is water, and over to a shelf rack FILLED with the most MacGyver shit you ever did see.
Including, but not limited to, the 3D printed plastic block, with a piston that repeatedly smacking half a aluminum nameplate over the device it is testing. You see, it is a capacitance button, and it is testing it by simulating a human finger pressing it many thousands of times, a saws off antenna which is the end of a cable that is attached to it via a nice thick bolt, so it can send fake signals into it.
And of course the 24 volt, 5 amp system that is turning a circuit board on and off again, until it will crack.
We walk back out, remembering to step over the small river, which never even got a comment, and walk back to my department It is SO great. It is like working in the ministry of silly walks by Monty Python Like… Do I think I can bring value to this company? Like, making it better and more efficient? Yes. It would be hard not to!
And his is the largest pump manufacturer in the world! A super serious company with 4 billion dollars of revenue a year. And it is just… a NUTHOUSE
Like… NEVER believe the myth that corporations are competent.
12 notes
·
View notes
Text
Haven't done a computer status update in a little bit. Raspberry Pi media server has been psuedo-retired. It's currently still functioning as a media server for a christmas display at my wife's work until the end of December.
It has been successfully replaced by the Dell Optiplex that I got from work. I was able to skip the process of building a migration script for the server (to allow files to be moved and refound via filename & hash), but only because I've been mapping storage outside the server's webroot via link files in the upload directory. So on the new HD the files are actually in the upload directory rather than linked to it. As far as the server knows they're in the same place.
I transferred the software between machines by making a new install of vogon on the optiplex and then importing a mysqldump of the existing install into it, bringing the user accounts, media data, and other configuration elements with it. I did end up changing the storage engine of the data and data_meta tables into innodb (from isam) and adding some additional indexing. There were some noticeable performance differences on the generated join queries between servers. We were looking at 7sec+ lookup times for searches in the audio module. I'm still not sure if it's a mariadb version difference between raspbian and ubuntu lts, if something got corrupted in the export/import process, or if it was some strange storage lookup difference between running the database off of a SETA Hard-Drive versus an SD card. I initially thought maybe it was a fragmentation issue, but the built in optimization processes didn't really impact it, but with the adjustments to the indexing we're regularly getting query times measured in microseconds versus seconds, so it's working pretty well now.
The x86 processor and the faster storage (without the power dropout issues) have really improved the experience. Especially with reading comic books.
If I haven't explained it before, the way the CBZ reader works is that it sends a file list from the archive to the browser, the browser requests an image, and the server extracts the image data into RAM, base64 encodes it, and sends it back to the browser. It's a process that is bottlenecked by both CPU and storage speeds, so it's noticeably snappier on the new machine, even if the CPU is over a decade old at this point.
I'm actually considering taking a crack at forking mozilla's pdf.js to work a similar way, sending a page of data at a time, to decrease transfer times and allow lower memory devices to open large PDFs without having to actually download the whole thing. I suspect that means I'm going to have to build smaller single page PDF files on the fly, which would mean coming up with some kind of solution for in document links. I'm still in the phase of deciding if it's enough of a problem to put effort into solving, so I haven't done enough research to know if it will be easy or difficult. It's always hard to tell in situations like this because just about every web reader project assumes downloading the whole file, and the question is do they do it this way because it's hard to sub-divide the format, or do they do it because full clientside logic can be demoed on github pages.
3 notes
·
View notes
Note
could you go into a little bit of detail about vapoursynth as a program if you don't mind? because the vapoursynth i'm familiar with runs solely with the command line interface using python and i have a feeling thats not what people are talking about but i could be wrong honestly 😅 and was just curious if you minded explaining what you used it for (and maybe how it's set up a bit so i know if i'm thinking of the right vapoursynth?)
yeah sure! to preface, i have a mac computer. if youre asking these questions as a gif maker, ie u want vapoursynth installed, and you have a mac, it is gnarly to install. i have coding background and consider myself tech savvy and it was hell, lmao. if you have windows, it's apparently easy as pie. lucky them.
yes, the vapoursynth i use/am talking about runs via python code (for macs) but not entirely python interface, like you dont need visual studio code or any app like that. at least for mac users, you have to download "vapoursynth editor" (and a lot of other stuff ie files that make vapoursynth run) from a vapoursynth tutorial for macs (like i said earlier, windows may be different bc i have a mac). this is the tutorial that contains the link to download "vapoursynth editor" and more for mac. btw, vapoursynth from this tutorial also currently works with the latest mac OS software, ventura 13, which is what i have. vapoursynth editor is like another version of vs code, or at least thats how i like to think about it.
this is what it looks like when i open "vapoursynth editor":
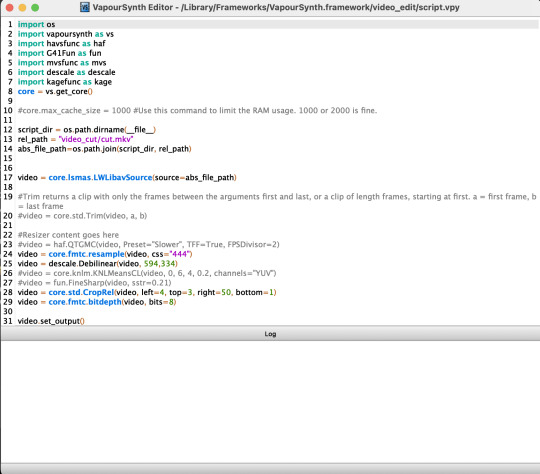
so, very similar to vs code.
this is what the app itself looks like (the one on the right):

the white robot dude is where you drop in the video that you want vapoursynthed (for lack of better word lol), which also comes in that link i shared. i used to use vapoursynth for cropping and sharpening/smoothing kpop videos to turn into gifs on photoshop, but now i just use it for cropping because i like photoshop's sharpening more. once i click and drag the video i'd like to crop/edit/sharpen into the white robot dude, i mess around with the video's dimensions, sharpening quality, etc. this is what that interface looks like to do that:
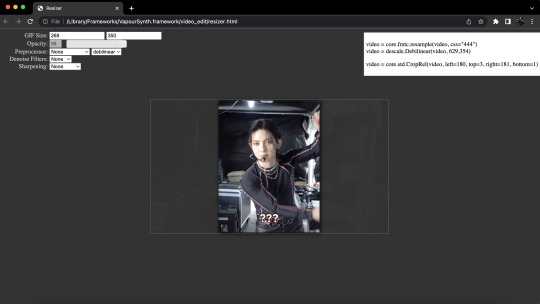
and when im done, i copy the code from the top right corner into vapoursynth editor, the screenshot from earlier that looks like vs code. to save the video with the settings you want...
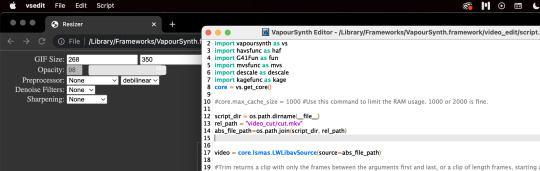
i go to "script" in the top left corner of my computer,

and hit preview, just to see if the sharpening/smoothing settings i selected look ok with the video. this is what preview looks like:
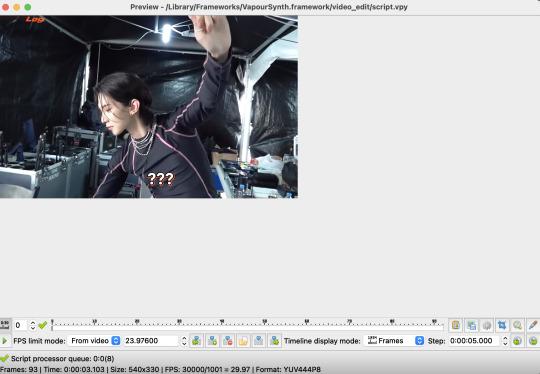
if im satisfied, i go back to script in the top left corner, but this time i hit encode video. this pops up:

i usually edit the very last bit of the code in the argument block (the output/output.mov) to something like, output/a-clever-name-so-ik-which-video-this-is.mov, and then i hit start in the bottom right corner and my computer sharpens/smoothens/crops the video.
when you say "explain how vapoursynth is set up" i'd imagine that means how to install it (on a mac)? please correct me if im wrong (by sending another ask), but if thats the case then the tutorial i linked explains it all!
i hope i hit everything you wanted anon, and send me another ask if you want to hear more about something in particular or want a more detailed vapoursynth tutorial, or something. thanks!
6 notes
·
View notes
Text
Barcode Definitions 101 | Uses & Guide | AIDC INDIA – 2025
Barcodes play a vital role in today’s business environment. From retail checkout systems to inventory tracking, they have transformed the way data is collected and managed. As we step into 2025, it becomes more important to understand barcode definitions and their role in modern operations. This guide from AIDC Technologies India is designed to simplify everything you need to know about barcodes and their practical uses.
2. What Is a Barcode? A Simple Definition Explained
A barcode is a machine-readable code represented as numbers and parallel lines or squares. Barcode definitions explain how this code is structured and what type of data it holds. Barcodes typically encode product information like SKU, batch number, or manufacturing details. They are scanned using barcode readers, which instantly convert visual patterns into digital data.
3. Types of Barcodes Used in 2025
There are various types of barcodes in use, each with its own format and function. Barcode definitions help identify which format suits a particular industry or task:
1D Barcodes: These are linear barcodes like UPC, EAN, and Code 128, often used in retail and inventory.
2D Barcodes: These include QR codes and Data Matrix codes, used for storing more complex data.
PDF417: A stacked linear barcode used on IDs and transport documents.
Each format has a specific barcode definition and is designed to meet unique requirements based on space, readability, and data needs.
4. How Barcodes Work: From Scanning to Data Collection
The basic process begins with printing a barcode on a label or product. A barcode scanner reads the lines or squares, and decoding software extracts the stored information. Barcode definitions help determine what type of scanner and software are needed to read the code accurately. This simple process eliminates manual entry and ensures fast, reliable data capture across operations.
5. Key Uses of Barcodes in Modern Industries
Barcode definitions are foundational in a wide range of sectors. In retail, barcodes are used for pricing and checkout. In warehouses, they track stock movement and inventory levels. Healthcare uses barcodes for labeling medicine and managing patient records. Logistics companies depend on barcodes for real-time tracking of shipments. The correct use of barcode definitions ensures that the data captured is accurate and usable.
6. AIDC India’s Role in Barcode Solutions
AIDC Technologies India provides complete barcode systems—from labels and scanners to printers and integration software. Our deep understanding of barcode definitions allows us to recommend the right type of barcode solution for your specific industry. We support clients in retail, manufacturing, healthcare, education, and logistics with customized systems that improve data tracking and minimize errors.
7. Benefits of Using Barcodes in Business
Barcodes offer several benefits that go beyond just automation. Proper use of barcode definitions brings improvements in many business areas:
Speed: Barcodes speed up scanning and reduce checkout time.
Accuracy: Minimizes manual errors in data entry.
Inventory Control: Keeps track of stock movement in real time.
Cost Savings: Reduces labor and improves efficiency.
By applying the right barcode definitions, businesses can unlock these advantages more effectively.
8. Barcode Definitions vs QR Codes vs RFID
Understanding how barcode definitions compare to other technologies helps in selecting the best system. Barcodes are simpler and more cost-effective for small to medium-sized operations. QR codes, which are 2D barcodes, can store more data and are often used in mobile marketing or payment systems. RFID, which uses radio waves, allows item tracking without line-of-sight scanning. However, barcode systems remain more accessible and easier to implement.
9. Smart Barcode Scanning Solutions by AIDC India
AIDC India offers barcode scanning devices that are optimized to read all standard barcode definitions. Whether it’s a handheld scanner for retail or an industrial-grade scanner for warehouses, our devices ensure fast, accurate, and error-free data collection. We also provide software tools that integrate these scanners with your inventory or billing systems for seamless workflows.
10. Choosing the Right Barcode System for Your Business
Barcode definitions help businesses choose the right format, printing method, and scanning tools. AIDC India helps you evaluate your operational needs, the volume of data you need to encode, and the environment where scanning takes place. Based on these factors, we recommend and implement barcode systems that align with your goals.
11. Future of Barcodes: Trends to Watch in 2025
As we look ahead, barcode definitions are evolving with technology. Mobile barcode scanning is becoming more popular, especially in e-commerce and delivery services. Smart inventory systems are using AI to analyze barcode data for forecasting and planning. Environment-friendly printing solutions are also emerging. AIDC India stays updated with these trends to provide future-ready barcode solutions for businesses of all sizes.
12. Get Started with Barcode Solutions from AIDC India
Barcodes are a small but powerful part of your business infrastructure. With the right barcode definitions and tools, you can automate operations, reduce costs, and improve customer satisfaction. AIDC Technologies India offers everything you need—from barcode labels and printers to scanners and integration support.
Call to Action: Ready to streamline your operations with smart barcode solutions? Contact AIDC Technologies India today for a free consultation, customized recommendations, and reliable tools that match your business goals.
#BarcodeDefinitions2025#BarcodeGuide#BarcodeUses#AIDCIndiaBarcode#BarcodeTechnology#SmartTrackingSolutions#BarcodeBasics#InventoryManagement#BarcodeScanning#RetailTech2025
0 notes
Text
Passwords hashing is used to secure passwords. Hashing is a common technique across various software and tools. Hashing is used as a security mechanism for preventing plain text information known to others. It's mathematically impossible to calculate a plain text for Hash since hashing is a one-way process. Still, there are different ways exist that can crack the hash and retrieve your password or other sensitive information that may have been hashed. Hashing technique is mostly applicable to protect password like information since its a one-way process. You may also want to check out - how to learn hacking and cracking. This is a simple tutorial that will explain how hash cracking works. Why Password Hashing Is Considered Secure Hashing is a one-way process. This guarantees that the hash of a plain text value can be generated however the process can not be reversed. Most software and websites use this way to store password since the user knows the password. Whenever they need to authenticate the user, they generate the hash of user input and match it with a stored password. This mechanism guarantees that even the software provider themselves do not know your password. However, there are hacking and cracking tools as well as other techniques described below that may be able to find out your password from a hash. Today we will learn about Cracking the Hashes using CPU and GPU. CPU: Central Processing Unit GPU: Graphical Processing Unit We will cover: What is a Hash? What is the need for a Hash? Why Hash over Encryption or Encoding? Hardware configuration Tools required Hash cracking [CPU] Hash cracking [GPU] Hash cracking using Search engine Why such a difference? What Is A Hash? A. A Cryptographic function that converts a data or file of arbitrary length or size to a fixed length, which is considered practically impossible to invert. see Wikipedia What Is The Need Of A Hash? A major use of Hash is in the security field. To provide security or privacy to the user who is using any service of a company. For example, You are using Gmail, Facebook, Twitter, eBay, Amazon or Online payment portals like Paypal. Where you use the service by providing your credentials(username/password) There are basically 2 reasons: Making it difficult for hackers to recover/retrieve Password, Online service(Gmail,eBay, etc) or even Wi-Fi. Checking for the file verification. see SHA1 here Even If a company’s security is breached (Hacked), then also the user’s credentials are safe(only if you use a strong password) Why Hash Over Encryption And Encoding? Imagine a scenario, which perhaps happens to almost every Big banner, take it Google, Facebook, Yahoo! etc. A website is compromised and User’s data(credentials) is compromised. What is the thing that will make you worry when you come to know that if you are a registered user on that site? Yes! your Password (might be the master password, for all your accounts). Now, It is in service provider’s hand to provide security to their consumers. Hence, Hashing is the solution. How? well, you might be familiar with these terms: Encoding/Decoding Encrypt/Decrypt and now, Hashing Not going into the details, I will tell you a basic and most important feature of Hash which makes Hash much different and important over Encoding and Decoding. and that is : Encoded text/file can be Decoded, Encrypted text/file can be Decrypted, But hashed text/file can never be De-hashed. Yes, Hash, unlike Encryption/Encoding, is a One-way process i.e when a text/file goes through the Cryptographic hash function, it is converted into a fixed character length. Example: md5 type hash has a character length of 32, where SHA1 has a character length of 40. If we hash a string, say “test123″, md5 and SHA1 hash for “test123″ will be md5(“test123″) : CC03E747A6AFBBCBF8BE7668ACFEBEE5 SHA1(“test123″) : 7288EDD0FC3FFCBE93A0CF06E3568E28521687BC Length differs from md2, md4 to SHA256, SHA512 and so on.
Hashing your Wi-Fi password is also secured using a hash function named PBKDF2(Password-Based Key Derivation Function) Hardware Configuration Hardware used in this tutorial: Laptop with 4 GB RAM Nvidia Graphic card 1 GB Tools Required Software used in this tutorial: Windows 8, 32-bit Cain & Abel (CPU based cracker). igHashGPU (GPU based cracker), download here Nvidia graphics driver, for igHashGPU, download here Hash Cracking [CPU] Cain & abel is a multi-purpose tool. It is used for various purpose like Sniffing Hash calculating Hash recovery(this tutorial) ARP spoofing WiFi hacking, using hardware called AirPcap and so on. We will take MD5(Message Digest 5) cracking as an example to keep it simple and easy to understand. Install Cain & abel, then follow the instruction along, step-by-step: Open Cain & abel Press Alt+C to open the Hash calculator Type in “test123” and hit [ENTER], here “test123″ is our test string You should see something similar, Here we got the MD5, and other Hash for string “test123″ i.e CC03E747A6AFBBCBF8BE7668ACFEBEE5. select and copy the MD5 hash.
NOTE: Hashing is Case sensitive, Hash for “Test123” will be absolutely different. Click on Cracker tab, then select MD5 Hashes column in the left. then right click and select Add to list. Paste the copied MD5 hash and hit [ENTER] Now, Hash is added to list. Right click on hash and select Brute-Force attack Set max length to 7 and click Start, and you should see this
. Here I have set the Max length of the password to be 7 to just test the output of the tool, and cracking speed of the CPU.
See the Password/Second CPU is testing: 6.3M (approx) and the remaining time i.e total time which will take CPU to recover the original string is 3.5 hours. It is too lame to wait for 3.5 hours for a small string test123 of the length of 7 characters with no special characters. isn’t it? well, here comes the GPU cracking to put some speed in the process! Hash Cracking [GPU] igHashGPU is a password recovery tool specialized for ATI (RV) and nVidia (Cuda) based cards. It recovers password of hashes which are used over the internet(weak), example md4/md5/SHA1. Let's get started, We have the MD5 string for test123 i.e CC03E747A6AFBBCBF8BE7668ACFEBEE5 Follow the instructions along, step-by-step: Download and extract igHashGPU. Go to folder Right click and edit the file “example.cmd“. It is the example file for testing GPU speed of recovering MD5 password. Paste the MD5 code in the file after h:
and it should look like this :
ighashgpu.exe /h:CC03E747A6AFBBCBF8BE7668ACFEBEE5 /t:md5 /c:sd /min:4 /max:7 Close file. Click save and yes. Select “Example.cmd” and hit [ENTER]. A command prompt window will open like this
. See the CURSPD(Current speed), ~50 Million. Nice! but not good, isn’t it? see the battery symbol in the lower right corner. The laptop is running on battery. See what happens when I plug in the charger, notice the clock and speed. WHOA! See the difference! from 50M to 195M passwords/second, isn’t it great ? from 6.3M pass/sec to 195M pass/sec. That’s a big Jump. What you think how long it would have taken to recover the Password ? Just 5 minutes and 53 seconds. See how much time we saved by using GPU. From 3+ hrs to just 5 minutes. isn’t it amazing? also see the average speed also, 62,847 Million passwords/second. CPU: ~3 hrs with 6M pass/sec
GPU: ~6 min with 195M pass/sec You might ask, Hey! can we crack this even faster? well, the answer is Yes you can(not always though). How? Hash Cracking Using Search Engine [Google] We had MD5 string copied, right? what you need to do is very simple. Just paste and search the MD5 string i.e CC03E747A6AFBBCBF8BE7668ACFEBEE5 on Google. and you’re done! Notice the text string “test123” and the Hash. So simple to recover the string from MD5, no? Now see the time above, it took us to recover the original string. Just 0.31 seconds. not even a second. Wow! that’s great.
You might be thinking why such a difference? here’s the answer Why Such A Difference? The difference in the speed is due to the architecture of the 3. CPU: Uses 4 cores(Shared with system processes) at maximum, 8-cores in some cases. GPU: Used 96 cores (In this case). All the 96 cores(Parallel processing units) were 100% dedicated for the password recovery process unlike CPU, which was simultaneously handling the complete OS including background processes, GUI(mapping of pixels on screen), and many other processes. Even if the CPU stop handling those, then also it won’t match GPU’s performance. difference because of the #of cores i.e 96 vs. 4 or 8 Latest GPU’s that I have seen comes with more than 400 cores. It can take you more than a billion passwords/second to recover the MD5 hashed string. Google Don’t Crack The Hash. Yes!, Google doesn’t crack/recover the string. It sends a request for the specific Text input i.e the hash in our case, to all the servers, takes the response back and displays the result according to the page rank of the site. There are plenty of online crackers, which can be used to crack a variety of hashes. They search their Database for the hash you have entered. If the string of hash is already recovered by them, they will give it to you, else you have to pay to avail the service. An email is sent if the string has been recovered. So, what Google does is sending a request to all these servers and displaying you the result. Result of the hash already cracked. It certainly becomes the Top priority for hash cracking. Search google first, if you didn’t find the password, go for GPU cracking.
Still didn’t succeed? Try CloudCraker, crackStation, HashKiller You can google “Online hash cracker” for more results. Note: Cracking speed varies depending on factors like: GPU configuration, ATI graphics cards are the best for this task. Hash type, for SHA1 it will be even lesser and for WPA hash cracking it goes down to 4000 Pass/sec on my graphics card. see this list. My card’s performance is near to GeForce 8800 GTS (CUDA) Interested in WPA cracking, or WiFi pentesting? Follow my WiFi Security and Pentesting Series Hope you found this tutorial helpful. Let me know in the comment section. Thanks! This article is contributed by Hardeep Singh (Facebook | Twitter). Hardeep is a guest author and Full-time Blogger @ rootsh3ll.com, Security person, Penetration, tester, Linux and python Lover. Loves to share knowledge with everyone. Updated On June 2019: Fixed Broken links and updated minor typos.
0 notes
Text
Bias in AI is not a bug; it’s a feature. This assertion may seem counterintuitive, but it is rooted in the very architecture of machine learning systems. These systems, designed to mimic human decision-making, inherently absorb the biases present in their training data. The implications are profound, as AI systems increasingly influence critical areas such as criminal justice, hiring, and healthcare.
Machine learning models, particularly those based on neural networks, operate by identifying patterns in vast datasets. These datasets, however, are not neutral. They reflect historical and societal biases, which are then encoded into the AI’s decision-making processes. For instance, if a dataset used to train a hiring algorithm predominantly features successful candidates from a particular demographic, the AI may inadvertently favor that demographic in future decisions. This is not a malfunction; it is the system functioning as designed, amplifying existing biases.
The technical architecture of AI systems compounds this issue. Deep learning models, with their multi-layered neural networks, are often described as “black boxes.” Their decision-making processes are opaque, even to their creators. This opacity makes it challenging to identify and rectify biases once they are embedded. Unlike traditional software, where bugs can be isolated and fixed, biases in AI require a more nuanced approach.
To mitigate these pitfalls, a multi-faceted strategy is essential. First, the data used to train AI systems must be scrutinized for bias. This involves not only diversifying datasets but also understanding the context in which the data was collected. Techniques such as adversarial debiasing and re-weighting can be employed to adjust for known biases. However, these methods are not foolproof and require continuous monitoring and adjustment.
Furthermore, transparency in AI systems is crucial. Explainable AI (XAI) is an emerging field focused on making AI decision-making processes more interpretable. By developing models that provide insights into their reasoning, stakeholders can better understand and address biases. This transparency is vital for building trust and ensuring accountability in AI systems.
Finally, interdisciplinary collaboration is key. Addressing AI bias requires input from computer scientists, ethicists, sociologists, and domain experts. This collaborative approach ensures that AI systems are not only technically robust but also socially responsible.
In conclusion, bias in AI is an intrinsic feature, not a flaw. It stems from the data and the design of the systems themselves. To navigate the complexities of AI bias, a comprehensive strategy involving data scrutiny, transparency, and interdisciplinary collaboration is essential. Only then can we harness the potential of AI while safeguarding against its pitfalls.
#collaborate#AI#skeptic#skepticism#artificial intelligence#general intelligence#generative artificial intelligence#genai#thinking machines#safe AI#friendly AI#unfriendly AI#superintelligence#singularity#intelligence explosion#bias
1 note
·
View note
Text
The Truth About Buying Cloned Cards Online – Cybersecurity Risks & Realities

In the age of digital transactions and online marketplaces, discussions around financial fraud have become more common—and one of the trending phrases making rounds is "buy cloned cards online." Whether out of curiosity, criminal intent, or research purposes, people are increasingly searching for this term. But what does it actually mean? What are cloned cards? Is it legal? And what risks are involved?
In this article, we’ll uncover everything about the dark web economy of cloned cards, explore the cybersecurity implications, and explain why engaging with these markets could lead to severe consequences.
💳 What Are Cloned Cards?
Cloned cards refer to counterfeit credit or debit cards created using stolen card data. This process usually involves copying the magnetic strip or chip information from a real card and encoding it onto a fake one. Cybercriminals can obtain this data through methods like:
Skimming devices at ATMs or gas stations
Phishing attacks
Data breaches
Dark web purchases of card dumps
Once they have the card data, they use specialized machines to “clone” or duplicate the cards. These fake cards can then be used for fraudulent purchases until the legitimate owner notices and reports the activity.
🛒 The Appeal of Buying Cloned Cards Online
People searching for “buy cloned cards online” may be lured by promises such as:
Access to cards with high balances
“Untraceable” cards for online or in-store shopping
Quick profits with minimal effort
Supposed anonymity on the dark web
These promises often come from shady websites or dark web forums that claim to sell cloned cards or offer “carding” services. Most of these platforms only accept cryptocurrency like Bitcoin or Monero to maintain anonymity and avoid tracking by law enforcement.
But the reality behind these transactions is far more complicated—and risky.
🚨 Legal & Criminal Risks
Buying cloned cards is illegal in virtually every country. It falls under fraud, identity theft, and financial crime. Here are some of the legal consequences:
Fines and imprisonment (in some countries up to 10–20 years)
Seizure of assets
Criminal records
Involvement in broader criminal investigations
Even browsing these sites or attempting to make a purchase can land you in hot water, as many forums are monitored by law enforcement and cybersecurity agencies.
🎭 Scams and Fake Vendors
Another reason not to engage with the dark market is the sheer number of scams. Common tactics include:
Vendors vanishing after payment
Low-quality or non-working cards
Fake “customer support” extracting more money
Malware hidden in download links
There’s no accountability or refund when you're dealing in an illegal marketplace. You're just as likely to become a victim of fraud as the people whose cards are cloned.
🛡️ Cybersecurity Implications
If you're not actively participating in carding, but you're just researching it, the threat still looms. Many sites offering cloned cards are laced with malware, spyware, or ransomware. Visiting them can expose your personal data, banking info, or even give hackers remote access to your device.
Also, if your own credit or debit card has been compromised, it may be one of the thousands of card dumps circulating online. In that case:
Immediately contact your bank
Freeze or cancel your card
Monitor your account for suspicious activity
Report the breach to authorities
🌐 The Role of the Dark Web
The dark web is the primary marketplace for buying and selling cloned cards. Hidden behind layers of encryption and anonymity software like Tor, it houses marketplaces with user reviews, seller ratings, and even escrow systems—mimicking legitimate e-commerce.
However, these environments are unstable. Law enforcement agencies regularly infiltrate and shut down such platforms, leading to mass arrests and data leaks that can expose both buyers and sellers.
🔐 How to Protect Yourself from Card Cloning
Even if you’re not trying to buy cloned cards, knowing how to protect your financial information is essential:
Use cards with EMV chips – harder to clone than magnetic strip cards.
Enable transaction alerts – real-time notifications help detect fraud quickly.
Avoid public Wi-Fi when entering card details.
Use strong, unique passwords for online banking and e-commerce.
Monitor bank statements regularly.
Use virtual cards or masked card services for online purchases.
🤔 Final Thoughts: Curiosity Can Be Dangerous
While the search term "buy cloned cards online" might be trending, engaging with this market is not only illegal but also incredibly risky—ethically, legally, and financially. Most people are better served by understanding how these underground economies work so they can protect themselves, not participate in them.
If you’re researching for awareness or cybersecurity purposes, you’re on the right track. But if you’re considering stepping into this world, it’s important to know that the dangers far outweigh any potential benefit.
0 notes
Text
The Role of Automation: How Barcode & QR Codes Boost WMS Efficiency
Introduction
With the rapidly evolving logistics and supply chain sector today, automation is an essential contributor to efficiency and productivity. Perhaps the most efficient way to automate warehouse functions is to incorporate barcode and QR code technology in a warehouse management system (WMS) .These technologies make it easier to monitor inventory, manage orders, and warehouse operations in general by reducing errors and increasing speeds. In this, we examine how WMS efficiency increases with automation using barcode and QR code technology, and how they transform the warehouse business.
Warehouse Management System (WMS)
A warehouse management system (WMS) is software that is used to automate different warehouse activities like inventory management, stock replenishment, picking, packing, and shipping. It helps the warehouse manager maintain accurate levels of inventory, automates processes, and improves productivity. With the integration of barcode and QR code technology, a WMS receives even more power, enabling it to monitor warehouse activities in real-time and automate warehouse activities.
How Barcode & QR Code Technology is Applied in WMS
Barcode Technology
Barcodes are 1D bar codes that are applied to encode product data in the form of parallel lines. Scanned and read by a barcode reader, the data is fetched directly and saved in the WMS. This facilitates quick processing of inventories and removes the need for manual entry.
QR Code Technology
QR codes are 2D codes with the ability to hold more intricate data, including product descriptions, batch numbers, expiration dates, and even URLs. QR codes are unique from barcodes as they can be read through mobile phones and are more flexible when it comes to managing data.
The Role of Automation in WMS Efficiency
Barcoding and QR code technology used in WMS automates most warehouse activities, resulting in enhanced efficiency. Some of the key ways in which automation enhances WMS functionality are explained below:
1. Improved and Streamlined Inventory Management
Existing manual tracking techniques of inventories make use of hand-held scanning as well as hand data entry and thus are easily liable to faults. Real-time updated inventory may be kept with the help of speedy barcodes as well as QR code scans by warehouse staff. This clears stock discrepancies and maintains accurate inventory up-to-date.
2. Improved Order Fulfillment Process
Order fulfillment is often the most critical warehouse management function. Barcode and QR code automation support quicker picking and packing by enabling staff to validate product details in real-time. This negates order processing errors and ensures punctual deliveries.
3. Reduction of Human Errors
Manual data entry increases the likelihood of errors in stock records, order details, and monitoring shipments. Scanners of barcodes and QR codes allow automatic data collection, minimizing manual error and increasing overall accuracy.
4. Enhanced Warehouse Productivity
Automation speeds up warehouse operations by removing redundant handoffs. Employees have less time handling paperwork and more on activities of value, such as rationalizing storage space and improving order handling.
5. Real-Time Data and Analytics
WMS integration with barcode and QR code provides warehouse managers with real-time visibility into inventory levels, shipment status, and warehouse operations. Information that helps to decide, forecast demand, and optimize warehouse planning.
6. Integration with Other Technologies
Barcodes and QR codes can further be integrated with other automated technology such as RFID, IoT sensors, and robots. It forms a networked warehouse system in which different systems are networked and they are in communication so that they enable greater efficiency.
7. Cost Savings and ROI Improvement
By automating warehouse operations, businesses are able to save labor, prevent losses due to inefficiently managed inventory, and improve overall warehouse efficiency. The initial cost of barcode and QR code technology is quickly offset by long-term cost savings and improved warehouse performance.
Implementing Barcode and QR Code Automation in WMS
Step 1: Select a Barcode/QR Code-Supported WMS
Choose a WMS that can perform barcode and QR code scanning to enable easy integration with existing warehouse operations.
Step 2: Implement Proper Labeling
Tag all inventory items, storage bins, and shelves with barcodes or QR codes so they can be scanned and monitored easily.
Step 3: Invest in Scanning Devices
Equip warehouse personnel with barcode and QR code scanners or mobile devices that can accurately capture and process data
Step 4: Train Warehouse Staff
Train personnel in the use of barcode and QR scanners for maximum return from automation.
Step 5: Monitor and Optimize Performance
Review WMS data regularly to identify where improvements can be made and optimize warehouse operations accordingly.
The Future of Automation in Warehouse
As technology advances, barcode and QR code automation will be even more sophisticated. Future trends are:
AI-Driven WMS Solutions: Artificial intelligence (AI) will augment barcode and QR code functionality by allowing predictive analytics and automated decision-making.
Cloud-Based WMS: Cloud integration will enable warehouses to operate remotely with real-time data access.
Robotic and IoT Integration: Autonomous robots and IoT-enabled devices will be used in conjunction with barcode and QR code systems to build highly efficient and automated warehouses.
Conclusion
The use of barcode and QR code technology in Warehouse Management Systems (WMS) is transforming warehouse operations. Through automated tracking of inventory, order picking, and warehouse operations, companies can greatly enhance efficiency, accuracy, and cost reduction. With further advancements in automation, barcode and QR code technology will be an integral part of contemporary warehouse management, increasing productivity and overall supply chain operations.
For businesses looking to optimize their warehouse operations, adopting barcode and QR code automation in WMS is no longer optional—it’s a necessity for staying competitive in the evolving logistics landscape. https://www.instagram.com/quickmovetechnologies/ https://youtu.be/PjDQMaFRazk?si=hGbrQasKB31iojDg
https://www.linkedin.com/company/6638777/admin/dashboard/
0 notes
Text
Not bad, Intel: Arc Battlemage announcement
So Intel just announced their new series of GPUs, and they look... pretty good! I'm kind of impressed.
Two cards have been announced today: The Arc B570 ($219, January 16th) and B580 ($249, December 13th). They're decidedly midrange cards, but at least they're actually priced like it. Breakdown under the cut.

Image credit: Intel
Looking at Intel's claims, the B580 looks like a solid improvement over the A750 (comparing price to price) and a decent competitor for the RTX 4060:

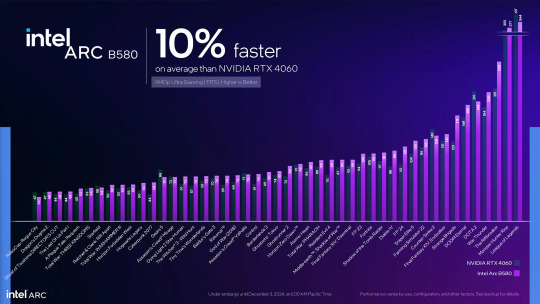
Image credit: Gamers Nexus
It's also a 192-bit, 12GB card, priced at $250. Like cards with that tier of memory system should be, Nvidia. The 4070 remains insultingly dogshit.
XeSS has been updated too - Intel's equivalent to DLSS and FSR from Nvidia and AMD respectively. The newest version, XeSS 2, introduces "Xe Low Latency" (think of it as a counterpart to Nvidia Reflex or AMD's Radeon Anti-Lag) and "Xe Frame Generation" (which you already know my feelings on, but at least the graphic they used to explain it was pretty good). Of course, they also presented some generative AI hardware acceleration features, but that's worth even less than frame gen is so I'm skipping it. Encoding wasn't really brought up besides maybe one slide listing it so I'm guessing there's no major improvements there.
This is the first GPU launch in a good while that I'm not left completely disappointed by. With Nvidia laughing all the way to the bank, AMD straight up unable to compete and both of them more or less abandoning the budget GPU market, at least Intel is now here to say "Hey, we can squeeze in a 12GB puncher here and undercut everyone else's prices".
Here's hoping it'll kick the other two into actually competing. Hell, here's hoping the performance will actually be as good as Intel is claiming, because all they've shown is 1440p and maybe other resolutions kneecap the card.
Overall? Not bad. Solid hardware, fair pricing, respectable performance improvements, software suite up to speed with the competition. If the performance claims pan out, this will be one of the product lines to look for, especially after prices start dropping given some time. You still need ReBAR enabled, but if you bought your computer any time in the past five years you should be completely okay.
0 notes
Text
The Evolution of Digital Digest in Modern Media
Digital Digest is a longstanding online resource focused on digital video and multimedia, offering news, articles, software downloads, and guides on topics like video codecs, Blu-ray, and streaming technology. Initially launched as separate sites dedicated to DVD, DivX, and DVD-R content, Digital Digest has evolved into a single platform addressing the wider digital video landscape, including forums for in-depth discussions on video technology.
The website provides up-to-date information on video-related software, encoding techniques, and digital media advancements, catering to both enthusiasts and professionals. It also covers relevant tech industry developments, offering insightful and neutral content for readers interested in the latest digital trends
Unlocking Beauty: 7 Key Facts About Peptides in Skincare Peptides have become a skincare favorite in recent years due to their ability to address aging, firm the skin, and enhance skin elasticity. But what exactly are peptides, and why have they gained so much attention in the beauty industry? Let’s dive into the science behind peptides and uncover seven key facts that explain their benefits and versatility in skincare.
What Are Peptides? Peptides are short chains of amino acids, which are the building blocks of proteins like collagen and elastin. When peptides are applied to the skin, they act as small messengers, sending signals to prompt skin repair and boost collagen production. This process helps keep skin firm, smooth, and youthful.
How Peptides Work in Skincare Peptides penetrate the skin barrier, reaching the deeper layers to stimulate natural repair mechanisms. By prompting the skin to produce more collagen and elastin, they help reduce the appearance of fine lines, improve texture, and boost firmness. Unlike some ingredients that merely hydrate the skin, peptides actively encourage the skin to rebuild and repair itself.
The Anti-Aging Benefits of Peptides As we age, collagen production declines, leading to wrinkles and sagging skin. Peptides support anti-aging by increasing collagen synthesis and reducing the breakdown of existing collagen. This helps minimize wrinkles, plump the skin, and give it a more youthful appearance. Specific peptides, like matrixyl, have shown remarkable results in reducing the depth of wrinkles.
Peptides vs. Retinoids and Vitamin C While retinoids and vitamin C are also powerhouse ingredients for aging and skin rejuvenation, peptides offer a gentler approach. Retinoids can cause irritation, especially for sensitive skin, and vitamin C may lead to redness for some users. Peptides, however, are generally well-tolerated by all skin types, making them an excellent option for those looking to minimize irritation while still gaining anti-aging benefits.
Types of Peptides in Skincare Different types of peptides provide distinct benefits. Some of the most popular types include:
Signal Peptides: Stimulate collagen production to firm and plump the skin. Carrier Peptides: Deliver essential minerals to the skin, aiding in repair and regeneration. Enzyme Inhibitor Peptides: Slow down the skin's natural breakdown of collagen. Neurotransmitter Peptides: Work like Botox by reducing the muscle contractions that cause wrinkles, softening the appearance of fine lines.
Peptides Boost Moisture Retention language learning tips
0 notes
Text
Base64 encryption logic
Base64 is a binary to a text encoding scheme that represents binary data in an American Standard Code for Information Interchange (ASCII) string format. It’s designed to carry data stored in binary format across the channels, and it takes any form of data and transforms it into a long string of plain text.
This is helpful because every hour of every day, every minute of every hour, and every second of every minute, a tremendous amount of data is being transferred over network channels.
What Is Base64 Encoding?
Base64 encoding is a text encoding string that represents binary data into an ASCII string, allowing it to carry data stored in a binary format across channels.
To better understand base64, we first need to understand data and channels.
As we know, communicating data from one location to another requires some sort of pathway or medium. These pathways or mediums are called communication channels.
What type of data is transferred along these communication channels?
Today, we can transfer any format of data across the globe, and that data can be in the form of text, binary large object file (BLOB) and character large object file (CLOB) format. When that data transfers through a communication medium, it’s chopped into chunks called packets, and each packet contains data in binary format(0101000101001). Each packet then moves through the network in a series of hops.
Before diving into the base64 algorithm, let’s talk about BLOB and CLOB.
More on Software Engineering:Glob Module in Python: Explained
An Introduction to BLOB and CLOB
BLOB stands for binary large object file. Whenever we transfer image, audio or video data over the network, that data is classified as BLOB data. CLOB, which stands for character large object file, includes any kind of text XML or character data transferred over the network. Now, let’s dive into base64 encoding.
As we stated earlier, base64 is a binary to text encoding scheme that represents data in ACII string format and then carries that data across channels. If your data is made up of 2⁸ bit bytes and your network uses 2⁷ bit bytes, then you won’t be able to transfer those data files. This is where base64 encoding comes in. But, what does base64 mean?
First, let’s discuss the meaning of base64.
base64 = base+64
Base64 is considered a radix-64 representation. It uses only 6 bits(2⁶ = 64 characters) to ensure that humans can read the printable data. But, the question is, why? Since we can also write base65 or base78 encoding, why do we only use 64?
Base64 encoding contains 64 characters to encode any string.
It contains:
10 numeric values i.e., 0,1,2,3,…..9.
26 Uppercase alphabets i.e., A,B,C,D,…….Z.
26 Lowercase alphabets i.e., a,b,c,d,……..z.
Two special characters i.e., +,/, depending on your OS.
More on Software Engineering:Nlogn and Other Big O Notations Explained
How Base64 Works
In the above example, we’re encoding the string, “THS,” into a base64 format using the base64 operator(<<<) on a Linux CLI. We can see that we’re getting an encoded output: VEhTCg==. Now, let’s dive into the step-by-step procedure of getting this encoded output.
The steps followed by the base64 algorithm include:
Count the number of characters in a string.
If it’s not a multiple of three, pad with a special character, i.e., “=” to make it a multiple of three.
Encode the string in ASCII format.
Now, it will convert the ASCII to binary format, 8 bit each.
After converting to binary format, it will divide binary data into chunks of 6 bits each.
The chunks of 6-bit binary data will now be converted to decimal number format.
Using the base64 index table, the decimals will be again converted to a string according to the table format.
Finally, we will get the encoded version of our input string.
At the beginning of base64, we started with the string “THS.” Now, we’re going to encode this string by following the above algorithm steps.
https://www.youtube.com/embed/8qkxeZmKmOY?autoplay=0&start=0&rel=0A video on the basics of base64 encoding. | Video: Connor Ashcroft
Base64 Encoding Steps
Finally, we receive the encoded output of base64 as VEhT.
But wait. In the above example, why did we get VEhTCg==?
If we run the echo -n THS | base64 command on CLI, we’ll see that we’re getting the same output as before.
What If Our Input String Isn’t a Multiple of 3?
What do we do if our string is not a multiple of three? According to the first step of the algorithm, base64 will count the number of characters in a given input string. If it’s not multiple of three, then it will pad it with a single “=” character.
Let’s look at one more example to prove it.
In this given string, the number of characters is not multiple of three. So, we have to pad one (=) at the end. But why?
The “=” is padding when the least significant bit of binary data doesn’t contain 6-bit.
Finally, we’ll return the encoded output, which will be: YWjyYUFicmE=
In this above output, we return K as a special character in place of “=” because this depends on your system. You can try this new command on your CLI for confirmation i.e., echo | base64.
0 notes