#Tech Support
Explore tagged Tumblr posts
Text
Stay safe, everyone!
Cybercriminals are abusing Google’s infrastructure, creating emails that appear to come from Google in order to persuade people into handing over their Google account credentials. This attack, first flagged by Nick Johnson, the lead developer of the Ethereum Name Service (ENS), a blockchain equivalent of the popular internet naming convention known as the Domain Name System (DNS). Nick received a very official looking security alert about a subpoena allegedly issued to Google by law enforcement to information contained in Nick’s Google account. A URL in the email pointed Nick to a sites.google.com page that looked like an exact copy of the official Google support portal.
As a computer savvy person, Nick spotted that the official site should have been hosted on accounts.google.com and not sites.google.com. The difference is that anyone with a Google account can create a website on sites.google.com. And that is exactly what the cybercriminals did. Attackers increasingly use Google Sites to host phishing pages because the domain appears trustworthy to most users and can bypass many security filters. One of those filters is DKIM (DomainKeys Identified Mail), an email authentication protocol that allows the sending server to attach a digital signature to an email. If the target clicked either “Upload additional documents” or “View case”, they were redirected to an exact copy of the Google sign-in page designed to steal their login credentials. Your Google credentials are coveted prey, because they give access to core Google services like Gmail, Google Drive, Google Photos, Google Calendar, Google Contacts, Google Maps, Google Play, and YouTube, but also any third-party apps and services you have chosen to log in with your Google account. The signs to recognize this scam are the pages hosted at sites.google.com which should have been support.google.com and accounts.google.com and the sender address in the email header. Although it was signed by accounts.google.com, it was emailed by another address. If a person had all these accounts compromised in one go, this could easily lead to identity theft.
How to avoid scams like this
Don’t follow links in unsolicited emails or on unexpected websites.
Carefully look at the email headers when you receive an unexpected mail.
Verify the legitimacy of such emails through another, independent method.
Don’t use your Google account (or Facebook for that matter) to log in at other sites and services. Instead create an account on the service itself.
Technical details Analyzing the URL used in the attack on Nick, (https://sites.google.com[/]u/17918456/d/1W4M_jFajsC8YKeRJn6tt_b1Ja9Puh6_v/edit) where /u/17918456/ is a user or account identifier and /d/1W4M_jFajsC8YKeRJn6tt_b1Ja9Puh6_v/ identifies the exact page, the /edit part stands out like a sore thumb. DKIM-signed messages keep the signature during replays as long as the body remains unchanged. So if a malicious actor gets access to a previously legitimate DKIM-signed email, they can resend that exact message at any time, and it will still pass authentication. So, what the cybercriminals did was: Set up a Gmail account starting with me@ so the visible email would look as if it was addressed to “me.” Register an OAuth app and set the app name to match the phishing link Grant the OAuth app access to their Google account which triggers a legitimate security warning from [email protected] This alert has a valid DKIM signature, with the content of the phishing email embedded in the body as the app name. Forward the message untouched which keeps the DKIM signature valid. Creating the application containing the entire text of the phishing message for its name, and preparing the landing page and fake login site may seem a lot of work. But once the criminals have completed the initial work, the procedure is easy enough to repeat once a page gets reported, which is not easy on sites.google.com. Nick submitted a bug report to Google about this. Google originally closed the report as ‘Working as Intended,’ but later Google got back to him and said it had reconsidered the matter and it will fix the OAuth bug.
8K notes
·
View notes
Text
i made a new account incase this one gets banned but im kinda confused i clicked on the "create a new tumblr" button but is that making a new account or that like an extension to this account i dunno i need tech support but anyways the username is bambinotbimbo
also wtf how is this post potentially mature content is it because of the gif girl bye

#older man younger woman#older guys#oldermen#daddy's good girl#age g4p#bambification#bambi doe#bambi girl#bambi#bd/sm daddy#tech support#ickykiddo#ickydolly#ickyprincess#ickybaby#ick ick ick#ickis#ickydaddy#needy bunny#bunny girl#bunnydoll#dumb bunny#daddy's bunny#bunny#1kky kiddo#ikky kiddo#kiddo wife#call me your kiddo and show me how good it makes your adult cock feel 😵💫#!cky princess#1cky princess
22 notes
·
View notes
Text


In a fantasy setting, my job would be exactly the same
#dragonsona#dragon#tech support#myart#this is a real thing that happens in my real job#people lose their work laptops... with a sticky note attached that has their work username+password on it#drives me up the wall#these people have access to some pretty sensitive information!
33K notes
·
View notes
Note
Event logs and the digital panopticon where someone can be watching your screen remotely at any given moment
excuse me, i'm borrowing a work laptop and there's a wall to stop me from going to gaming sites. do you or anyone else have any suggestions to bypass the wall?
I would strongly recommend not trying to get around blocking rules on your work laptop because your work is almost certainly logging what happens on the laptop; if they check those logs at the very least you will no longer be allowed to borrow the laptop, and possibly you won't continue to have a work to borrow a laptop from.
Also, depending on how huge a deal anyone wants to make of this, it may be actually illegal to do this on someone else's computer (and even if they lent it to you, that is their computer, and what you are discussing is sometimes described as "unauthorized access" and is a no-shit crime; people also don't think that logging into an ex's email that they had the password to is a crime - it is. Don't do this shit)
You can do whatever you want on your own computer and your own network. If you are on somebody else's computer you have to follow their rules. This is annoying, but unless you are certain that you are good enough to do this in a way that will be completely undetectable to your employer, you shouldn't do this.
If you work someplace that provides you a computer for work, you should ONLY use that computer for work. Assume that your boss can see everything that you do on that work computer and act accordingly.
2K notes
·
View notes
Text
There are people in this world who approach all communication as a form of intellectual combat which is "won" by deliberately providing the most obstructive and least informative possible answer which technically satisfies the precise letter of the stated request, and literally all of them are on Stack Overflow.
2K notes
·
View notes
Text
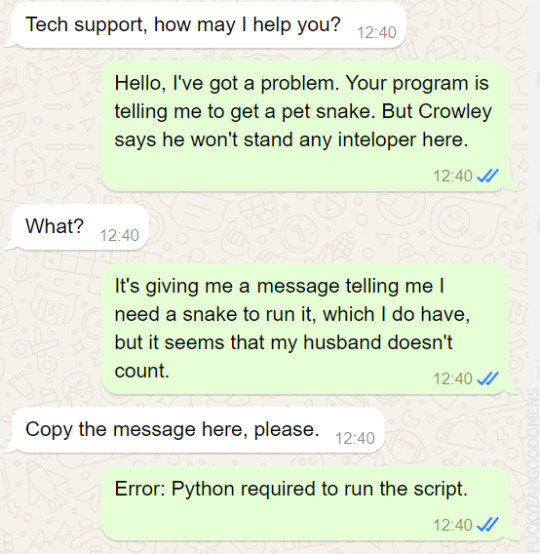
Aziraphale and tech support :)
1K notes
·
View notes
Text
Have you tried turning it on and off? You have? Have you tried turning it off and on? That too? Have you tried listening to "Bela Lugosi's Dead" by Bauhaus repeatedly alone in a darkened room? No? Well get back to me when you have.
560 notes
·
View notes
Text









malon, local time expert
<previous / next>
first
#linked universe#lu malon#lu warriors#lu legend#lu time#young time lu au#sky chickened out of talking to malon lol#“well. have you tried turning him off and back on again?”#tech support
3K notes
·
View notes
Text
#thepandaredd#tim drake#bruce wayne#tech support#jason todd#dick grayson#stephanie brown#tim is so stressed#flyinggraysons38
668 notes
·
View notes
Text

The implication that Freddie changed Colin's ringtone is sending me
#the magnus protocol#tmagp spoilers#tmagp s1 epilogue#my magnus protocol stuff#original post#queue cause i'll be at work when the episode airs#colin becher#fr3-d1 | freddie#tech support
217 notes
·
View notes
Text

new comic! - user terror
I drew 3 bonus panels for this one, see em by becoming my patron ❤
#loading artist#comic#comics#webcomic#loadingartist#webcomics#new comic#tech support#halloween comics#ghost
1K notes
·
View notes
Text

I have now obtained enough followers on tumblr dot com that I can force you all to look at my favorite image of all time
#196#openbsd#tech support#unix#dns#boomerposting#bithc im wipe the ubi firmware in 10s and have openbsd/octeon in within an hour#reddit migration#reddit blackout
1K notes
·
View notes
Text
One of the fun things about web development these days is that nothing is self-contained anymore and there are so many layers of middleware talking to middleware talking to middleware that even "turning it off and back on again" has become an expert-level troubleshooting step because identifying exactly what needs to be turned off and back on again is a process in itself. I've been on multiple calls today alone where the resolution to a tech support issue has been "we restarted the XYZ", and the response from the client's own developers, who presumably set the stupid thing up in the first place, has been "we have an XYZ?"
1K notes
·
View notes