#Visitor Access Control Systems
Explore tagged Tumblr posts
Text
#visitormanagementsystem #visitoraccesscontrolsystem #visitorregistrationsystemuae #visitorregistrationsoftwareabudhabi #visitorregistrationsystemssharjah #visitorregistrationsoftwareuae #
#visitorregistrationsystemuae #visitormanagementsystemforoffice
#visitorregistrationsoftwareinburdubai #visitorregistrationsysteminsharjah
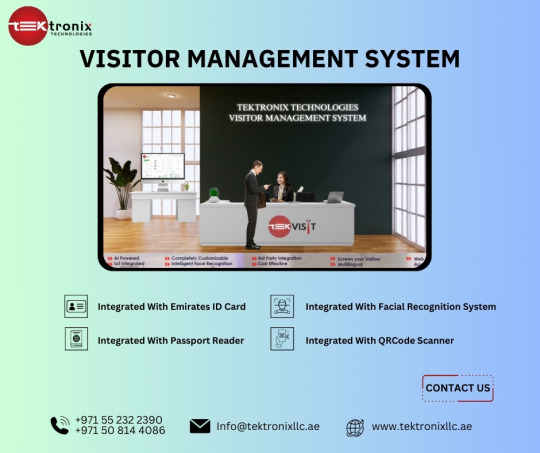
Streamlined Visitor Check-In Process
Eliminate the protracted lineup at the front desk. Quick and straightforward check-in procedures are made possible by the Tektronix Technologies system. With the help of the user-friendly interface, users can quickly and easily complete their personal information, leaving a lasting impression.
Real-Time Monitoring and Notifications
One of the major priorities is security. Because security is of utmost significance, Tektronix Technologies recognizes the value of staying informed. It offers real-time notifications to staff members who are in the appropriate position as well as ongoing user activity monitoring. This offers prompt replies in the event of an emergency in addition to being a means of enhancing security.
#registration #visitor
visitor management system
#visitor management system abu dhabi#visitor access control system uae#visitor registration system#visitor access control system in bur dubai#visitor registration system in alain#visitor management system#visitor registration system in uae#visitor access control systems#visitor management system with id scanner#visitor management system with id scanner uae#visitor management system with id scanner abu dhabi#visitor management system with id scanner in ajman#visitor management system with id scanner bur dubai#visitor management system with id scanner alain#visitor access control system in abu dhabi#visitor registration system in sharjah
0 notes
Text
#Visitor Management Software abu dhabi#visitor management Systems UAE#Visitor Management Systems in Dubai#Visitor Access Control Systems in Sharjah#Visitor Registration systems in abu dhabi#visitor registration software in bur dubai#visitor access control systems in ajman#Visitor Access Control Systems in Ajman#visitor tracking system#Visitor Access Control Systems#visitor registration system
0 notes
Text
Idiot devices spasming and reacting without reasonable analysis should not be trusted, should not be emulated, and should not be followed after in actions.
Cascade effects related to chains of devices spasming and reacting to the tiniest frown or negative perception relate to criminal strategies and effects these times.
Do not reduce appropriate analysis time, effort, expenditures or resources. And do not act if more analysis is needed.
I have been protected, like this whole globe, since birth, by transporter inhibitors, as well as temporal change inhibitors erected by my robots who resurrected me after having been killed in the womb and having been dead for 250000 years. There is no more criminal time travel (time travel the duplicates living or dead beings) possible, and there never will be.
#protected#cascade effects#dominoes#domino#dominos#analysis#terrorism intended to produce perceptions of an essentially continuous emergency situation#davis terrorism#invaders from outside this galactic cluster#bright cluster of galaxies#invasion by foreign military members#spies walking around without their military uniforms on or even passports or travel documents#uninvited visitors clearly distinguished because of their lack of advanced internal metal military skeletal systems and artificial brains#idiots without active cell phone connections#counterfeit currency#voter fraud#criminals using references to different criminals to terrorize#militaries masquerading as being well meaning and legal but secretly or unknowingly controlled by time traveling criminals#square military rank insignia militaries and janitors who stole lab coats to access experimental transporters
5 notes
·
View notes
Text
How Biometric Devices Improve Employee Time Tracking
In an era where organizations strive for efficiency, accuracy, and security, managing employee attendance has evolved from traditional punch cards and manual logbooks to high-tech solutions. Among the most transformative innovations is the biometric device, a software that has revolutionized how companies track and manage employee time.
Whether you're a small business or a large enterprise, ensuring accurate time tracking is essential for payroll, productivity, and workforce management. Biometric devices offer a modern solution by linking attendance to unique human characteristics such as fingerprints, facial recognition, or iris scans - making time fraud and buddy punching things of the past.

What Is a Biometric Device?
A biometric device is a piece of hardware used to identify individuals based on unique biological traits. In the context of workplace management, these devices are typically deployed for access control and attendance tracking. Unlike traditional systems that require ID cards or PINs, biometric systems ensure that only the actual individual can clock in or access a restricted area.
Biometric devices can come in various forms:
Fingerprint scanners
Facial recognition systems
Iris recognition devices
Voice recognition tools
The growing popularity of biometric technology is due to its speed, accuracy, and ease of integration with other HR and payroll systems.
Common Problems with Traditional Time Tracking Methods
Before diving into how biometric devices improve employee time tracking, it’s worth understanding the limitations of traditional systems:
Buddy punching: Employees clock in or out for each other, leading to time theft.
Manual errors: Human oversight when entering or correcting data can lead to payroll discrepancies.
Lost or stolen access cards: These can pose both a security and operational risk.
Lack of real-time data: Delayed updates make it difficult to monitor workforce performance.
These challenges not only impact payroll accuracy but also affect overall productivity and morale.
How Biometric Devices Transform Time Tracking
1. Accuracy and Reliability
Biometric devices are incredibly accurate. Because they rely on individual traits that cannot be duplicated or shared, they offer reliable verification each time an employee clocks in or out. This eliminates common issues like buddy punching or fraudulent time logging.
For instance, a facial recognition-based biometric device ensures that only the authorized individual can record attendance. This means more accurate payroll processing and fewer disputes between HR and employees.
2. Real-Time Attendance Monitoring
Biometric systems provide real-time data on employee attendance. This allows HR departments and team managers to monitor punctuality, break times, and absenteeism more effectively. Cloud-based biometric devices like those offered by Spintly offer real-time syncing across multiple locations, perfect for businesses with distributed teams or multiple branches.
This live data can be accessed through dashboards and reports, offering actionable insights that go beyond mere attendance tracking.
3. Integration with Payroll and HRMS
A modern biometric device does more than log time. Many advanced systems integrate seamlessly with Human Resource Management Systems (HRMS) and payroll software. This eliminates the need for manual data entry, ensuring timely and accurate salary processing, tax compliance, and leave management.
Solutions like Spintly’s biometric access control and attendance management platforms are built with open APIs, making it easy to integrate with third-party software - resulting in a streamlined workflow and reduced administrative burden.
4. Improved Compliance and Audit Trail
Maintaining proper records of working hours is essential to comply with labor laws and industry standards. Biometric devices automatically log every time an employee enters or exits the workplace, providing a secure and tamper-proof audit trail.
This data becomes especially useful during labor audits or legal disputes, ensuring organizations remain compliant without having to dig through manual records.
5. Contactless and Hygienic Options
In the post-pandemic world, hygiene has become a critical consideration in workplace technology. Modern biometric devices now offer touchless options, such as facial recognition and mobile-based check-ins, which minimize physical contact.
Cloud-enabled platforms like Spintly even offer mobile-based biometric attendance solutions, where employees can check in via their smartphones - reducing shared touchpoints while maintaining strict security protocols.
Industry Use Cases
1. Corporate Offices
Biometric time tracking helps monitor in-office attendance while integrating with access control systems to manage entry permissions.
2. Manufacturing & Industrial Units
These devices ensure workers clock in accurately despite working in high-volume shifts, often across different parts of the plant.
3. Healthcare Institutions
Hospitals benefit from biometric tracking to maintain 24/7 shift records and manage attendance in a critical-care environment where staffing is essential.
4. Educational Institutions
Schools and colleges use biometric devices to track faculty and staff attendance while maintaining secure access to restricted areas.
Advantages Over RFID and PIN Systems
While RFID cards and PINs offer basic functionality, they’re prone to misuse and loss. A biometric device offers a level of certainty and convenience that traditional systems can't match. Employees can’t forget or lose their fingerprint or face, making the system more dependable and reducing the cost and hassle of replacements.
Furthermore, combining biometric devices with access control solutions, such as those provided by Spintly, enhances building security. The system ensures that only verified individuals gain access to sensitive areas, creating a safer workplace.
Key Features to Look for in a Biometric Device
If you're considering investing in a biometric time tracking solution, keep the following features in mind:
Cloud connectivity for remote access and real-time syncing
Integration capabilities with HRMS and payroll systems
Touchless operation for post-COVID hygiene standards
Mobile authentication for flexible, remote check-ins
Data encryption to protect biometric data and ensure compliance
Providers like Spintly are paving the way for secure, scalable, and easy-to-deploy biometric solutions that fit businesses of all sizes.
Conclusion
In a digital-first world, managing your workforce with accuracy and efficiency isn’t just about technology - it’s about trust, compliance, and operational excellence. A biometric device simplifies employee time tracking while eliminating common pitfalls like buddy punching, manual errors, and data delays.
By integrating biometric attendance with access control and cloud-based dashboards, organizations get a holistic view of employee movement and performance. Solutions such as Spintly’s smart biometric access platform are leading this transformation by offering sleek, wireless systems that combine convenience with security.
Whether you're looking to tighten security, reduce administrative overhead, or simply improve the employee experience, adopting a biometric solution could be the smartest investment your business makes this year.
#biometric machine#biometric attendance#biometric access#mobile access#attendance management#time and attendance software#accesscontrol#spintly#smartacess#biometrics#smartbuilding#visitor management system#access control solutions
0 notes
Text
Custom Kiosks & Terminals: Tailored Solutions for Smart Parking & Access Management
In an increasingly automated world, businesses and municipalities are turning to custom kiosks and terminals to streamline operations, enhance user experience, and reinforce security. From smart parking systems to access control and visitor management, these customisable solutions serve as vital touchpoints for both users and operators. At Parkomax, we offer advanced custom kiosk and terminal solutions designed to meet the unique operational demands of every environment — whether it’s a mall, office complex, school, or beachfront facility.
What Are Custom Kiosks & Terminals?
Custom kiosks and terminals are standalone or integrated digital systems built with tailored software and hardware features to perform specific tasks. Unlike off-the-shelf options, custom solutions allow organisations to design interfaces, functionalities, and physical layouts that align with their brand, infrastructure, and operational workflows.
They can be configured to handle various applications, including:
Ticketless and ticket-based parking management
Employee access control
Visitor registration and validation
Payment processing
Wayfinding and information display
Key Benefits of Custom Kiosks & Terminals
1. Tailored Functionality for Unique RequirementsEach organisation has its own set of challenges and goals. Custom kiosks allow you to select and integrate only the components you need, ensuring optimal performance and avoiding unnecessary complexity. Whether you need license plate recognition, NFC payment, or biometric authentication, custom kiosks can accommodate it all.
2. Enhanced User ExperienceUser-friendliness is at the heart of a successful kiosk. Custom terminals can be designed with intuitive touchscreens, multilingual support, and ADA-compliant accessibility to create a smooth experience for all users.
3. Seamless Integration with Existing SystemsParkomax custom kiosks integrate effortlessly with your current access control systems, ERP software, or cloud-based management platforms. This makes upgrades more efficient and ensures continuity across operations.
4. Scalable and Future-readyAs your needs evolve, custom kiosks can be easily upgraded or modified to incorporate new features — such as facial recognition or AI-powered analytics — making them a future-proof investment.
5. Brand Alignment and Aesthetic ValuePhysical design plays a crucial role in brand perception. Custom terminals can be manufactured with specific colors, logos, and materials to match your organisation's branding and architectural aesthetics.
Applications Across Industries
1. Smart Parking FacilitiesCustom kiosks are essential components in modern parking systems, enabling ticketless entry, real-time slot updates, mobile payments, and automated exit validation. They reduce congestion and manual oversight, ensuring a smoother parking experience.
2. Commercial Buildings and OfficesUse customised access terminals to control employee and visitor entry, capture attendance, and manage credentials. These systems can also help meet compliance standards for data logging and security audits.
3. Shopping Malls and Entertainment VenuesMalls benefit from kiosks that provide information, validate parking, and offer loyalty program integration. Customisation ensures the kiosks blend seamlessly into the venue's branding and customer service model.
4. Schools and Educational InstitutionsControl visitor access, student attendance, and vehicle entry with custom-built terminals that support biometric recognition, ID scanning, and real-time alerts.
5. Beachfront and Outdoor FacilitiesWeather-resistant custom kiosks can be deployed at open-air locations like beaches, parks, or events, offering features like automated entry tickets, mobile payments, and usage analytics.
Why Choose Parkomax Custom Kiosks & Terminals?
At Parkomax, we specialise in delivering purpose-built kiosk solutions that combine advanced technology, elegant design, and user-centric interfaces. Here’s what sets us apart:
End-to-End Customisation: From software functionality to physical design and user flow, we tailor every component.
Robust Hardware: Our kiosks are built to last, with high-quality enclosures, vandal-proof screens, and weatherproof options.
Smart Integrations: Compatible with ANPR cameras, RFID, barcode scanners, biometric readers, and more.
24/7 Support & Maintenance: Advanced technical support ensures your systems remain functional and secure.
Proven Deployments: Trusted by organisations across the GCC for their parking and access control needs.
Conclusion
Custom kiosks and terminals are no longer a luxury — they are a necessity for modern, efficient, and secure operations. Whether you're managing a high-traffic parking lot or streamlining access to a commercial facility, a tailor-made kiosk can significantly improve both user satisfaction and operational efficiency. With Parkomax’s expertise in smart infrastructure, you can bring your ideal system to life.
Explore our full range of custom kiosk solutions today and discover how Parkomax can help you elevate your space.
#Custom kiosks and terminals#Smart kiosk solutions#Parking management kiosk#Access control terminals#Visitor management kiosks#Tailored kiosk solutions#Self-service kiosk systems#Parkomax kiosk solutions#Ticketless parking kiosk#Ticket-based parking terminal#Payment processing kiosk#Biometric access kiosk#Employee access terminal#License plate recognition kiosk#NFC payment kiosk#Facial recognition kiosk#Real-time attendance kiosk#Wayfinding digital kiosk
0 notes
Text
Advanced Access Control Devices for Modern Security
In today’s fast-moving, security-conscious world, traditional locks and keys are no longer enough. Businesses, residential buildings, educational institutions, and public infrastructures are all upgrading to smarter, more reliable solutions. Access control devices are at the heart of this transformation – offering not only security but also convenience, accountability, and peace of mind.
0 notes
Text

Enhancing Security: Expedite Technology's Contributions in Saudi Arabia, Qatar, and Oman
Middle East security management has shown itself to be at the forefront of cutting-edge technological innovations to bolster its infrastructure, with countries like Saudi Arabia, Qatar and Oman leading this charge by adopting Visitor Management Systems that use AI for enhanced efficiency and protection. This trend includes advanced Visitor Management Systems such as Visitor Tracker.
Visitor Management Systems with AI Integration
Traditional security measures often fall short in meeting modern security challenges head-on. Visitor Management Systems equipped with AI are revolutionizing how businesses and institutions approach security; their AI-integrated features not only streamline visitor management but also offer valuable analytics that inform better decision-making processes.
#Visitor Management System KSA#Visitor Access Control System KSA#school visitor check-in system KSA#Visitor Management System Al-Khobar#visitor management system with passport scanner KSA#school check-in systems Sharjah#school check-in systems KSA
0 notes
Text
I thought I was being overestimated by podcast advertising until I suddenly realized that actually I Was involved in enterprise grade software procurement decisions. I didn’t get to choose which one the company would use (and we’re talking about some big numbers here, especially over the contract lifetime), but I picked the field of options that the decision makers were choosing from… so I actually really was kinda making the decision in part; I decided what wasn’t on the table at least.
I'm not sure if Spotify has drastically over estomated my net worth or someone's really over spending on ad buys but it's kind of amusing how often IBM is trying to convince me to commission them to make a bespoke AI model to handle my business' data AND applications.
31 notes
·
View notes
Text
Enhancing Office Security and Efficiency.
Tektronix Visitor Management Software

In today's fast-paced world, managing office security and streamlining visitor processes are essential for maintaining a safe and efficient workplace. To address these needs, Tektronix Technology has developed cutting-edge Visitor Management Software that offers a comprehensive solution for modern offices. In this blog, we'll explore how Tektronix's technology is transforming the way offices manage visitors, ensuring a secure and seamless experience for both employees and guests.

Importance
Visitor management plays a crucial role in maintaining office security and professionalism. Traditional paper sign-in sheets and manual processes are not only inefficient but also pose security risks. A robust visitor management system is necessary to.
Enhance Security :- Prevent unauthorized access to your office premises by verifying the identity of visitors and cross-referencing them with watchlists or employee databases.
Streamline Processes :- Simplify the check-in and check-out processes, reducing wait times and ensuring a smoother experience for visitors.
Record Keeping :- Maintain accurate records of visitor data for compliance, auditing, and security purposes.
Improve Professionalism :- Impress clients and partners with a modern, efficient, and tech-savvy approach to managing visitors.

Features
Tektronix Technology has designed its Visitor Management Software with an array of features to meet the diverse needs of modern offices:
Visitor Registration :- Visitors can pre-register using a web-based interface or register upon arrival using a self-service kiosk. This minimizes wait times and ensures a faster check-in process.
Identity Verification :- The software can verify visitor identities through various means, including photo ID scanning, QR code scanning, or biometric authentication, ensuring that only authorized individuals gain access.
Access Control Integration :- Seamlessly integrate the software with your existing access control systems to grant temporary access badges or keycards to visitors.

Real-time Notifications :- Notify hosts via email, SMS, or app notifications when their guests arrive, enhancing communication and responsiveness.
Customization :- Tailor the software to your office's unique requirements, from branding and logo customization to language preferences.
Compliance and Reporting :- Automatically generate visitor logs and reports for compliance with security regulations and auditing purposes.
Data Privacy :- Tektronix prioritizes data security and privacy, ensuring that visitor data is handled in accordance with the highest standards.
Benefits
Enhanced Security :- Protect your office against unauthorized access and enhance overall security with identity verification and access control integration.
Improved Efficiency :- Streamline visitor processes, reduce wait times, and improve the overall visitor experience.
Compliance and Reporting :- Easily maintain records and generate reports to meet compliance requirements and enhance auditing capabilities.
Professional Image :- Impress visitors with a modern and efficient visitor management system that reflects your office's professionalism.

Scalability
Whether you have a small office or a large corporate headquarters, Tektronix's software is scalable to meet your needs. Tektronix Technology's Visitor Management Software is revolutionizing the way offices manage visitors. With its advanced features, security enhancements, and focus on efficiency, it's a valuable addition to any office environment. By prioritizing security, professionalism, and user-friendliness, Tektronix is helping offices create a safe and welcoming environment for employees and guests alike.
youtube
Contact Details

Tektronix Technology Systems Dubai-Head Office
[email protected] +971 50 814 4086 Office No.1E1 | Hamarain Center 132 Abu Baker Al Siddique Rd – Deira – Dubai P.O. Box 85955
#Visitor Management System#Visitor Management Software Dubai#Visitor Management Software Abu Dhabi#Visitor Management Software UAE#Visitor Access Control System#Visitor Registration System#Visitor Management System Dubai#Visitor Management System Abu Dhabi#Visitor Management Software for School#Youtube
0 notes
Text
Trump and Musk Are Pushing the U.S. Toward a Shutdown—Here’s What That Means for You
Once again, the U.S. is on the brink of a government shutdown. But this time, it’s not just political infighting—tech billionaire Elon Musk is playing a role, too. By leveraging his influence and platform, Musk has joined forces with Donald Trump to push for chaos, blocking a budget plan that would keep the government running.
What’s Happening?
A government shutdown occurs when Congress fails to pass a budget. Without funding, federal agencies shut down, leaving millions of workers unpaid and essential services suspended. Trump has been pressuring Republicans to reject the current spending plan, while Musk has amplified right-wing voices that oppose it, turning a routine budget negotiation into a high-stakes political crisis.
How This Affects You
A government shutdown doesn’t just impact politicians—it hits everyday Americans hard. Here’s what you need to know:
Federal Workers & Military Personnel: Over 4 million federal employees, including service members, could be forced to work without pay or be furloughed entirely. Many live paycheck to paycheck and would struggle to cover rent, utilities, or groceries.
Social Security & Medicare: While benefits continue, customer service lines and claims processing could be severely delayed, making it harder for seniors and disabled individuals to access their payments or healthcare services.
Food Assistance Programs: Families relying on the Supplemental Nutrition Assistance Program (SNAP) could see delays in benefits, and funding for food banks may dry up, exacerbating food insecurity.
National Parks, Museums, and Public Services: Expect closures of national parks, Smithsonian museums, and other federally funded sites. This affects not only visitors but also the small businesses that rely on tourism revenue.
Air Travel Disruptions: TSA agents and air traffic controllers will be required to work without pay, increasing the risk of flight delays and staff shortages that could create chaos at airports.
Housing & Small Business Loans: FHA-backed home loans could be delayed, making it harder for people to buy homes. Small businesses relying on federal grants or loans may also face significant funding gaps.
Economic Instability: The uncertainty and disruption from a shutdown can rattle financial markets, leading to job losses, increased inflation, and setbacks for businesses large and small.
Why Are Trump and Musk Doing This?
The Democrats argue that the budget proposal favored by Trump is nothing more than a disguised tax cut that would primarily benefit the ultra-wealthy—people like Musk. Additionally, they refuse to support a plan that would burden the U.S. with trillions of dollars in additional debt. Notably, alongside the Democrats, 38 Republican members of Congress also voted against Trump’s proposal.
The Bigger Picture
This isn’t just a budget dispute. It’s an alarming sign of how billionaires and political extremists can manipulate the system for their own gain. When an unelected tech mogul like Musk and a former president under multiple indictments can grind the government to a halt, it raises serious concerns about power, accountability, and the future of democracy.
What Can You Do?
Stay informed and share credible news sources.
Contact your representatives and demand they stand up to political obstruction.
Support journalism that holds those in power accountable.
Most importantly: Vote. A government shutdown is a preview of the dysfunction that could become permanent if Trump and his allies regain full control.
This is bigger than one political battle—it’s a fight for the stability of the country. And the outcome depends on all of us.
Source:
https://www.reuters.com/world/us/us-senate-democrats-debate-path-forward-government-funding-bill-2025-03-12/
#president trump#trump is a threat to democracy#us politics#elon musk#white house#usa news#donald trump#government shutdown#shutdown#american politics#politics#usa politics#political#us government#trump administration#economy#washington
143 notes
·
View notes
Text
📢 ALERT: System Outage
Attention all staff and visitors,
We regret to inform you that a major system outage is affecting operations at the Gallifrey Institute for Learning. Our tech team assures us they're working tirelessly to resolve the issue, but here's a quick overview of the systems currently impacted:
Food Machines: Producing only Earth Pot Noodles.
Cloister Bell: Now chiming every 42 seconds for no apparent reason.
Transmat System: Experiencing delays and occasional misrouting to entirely incorrect coordinates.
Lighting Controls: Some areas now illuminated in unexpected colours (purple seems to be popular).
Archive Access Terminals: Offline entirely, except for one terminal that only displays Gallifreyan cat memes.
There will be no daily posts this week and ask responses may be delayed.
We apologise for the inconvenience and appreciate your patience while we resolve these issues. Thank you for your understanding! Normal operations will resume shortly.
Announcements by GIL
Any orange text is educated guesswork or theoretical. More content ... →📫Got a question? | 📚Complete list of Q+A and factoids →📢Announcements |🩻Biology |🗨️Language |🕰️Throwbacks |🤓Facts → Features: ⭐Guest Posts | 🍜Chomp Chomp with Myishu →🫀Gallifreyan Anatomy and Physiology Guide (pending) →⚕️Gallifreyan Emergency Medicine Guides →📝Source list (WIP) →📜Masterpost If you're finding your happy place in this part of the internet, feel free to buy a coffee to help keep our exhausted human conscious. She works full-time in medicine and is so very tired 😴
#doctor who#dr who#dw eu#gallifrey#GIL#gallifrey institute for learning#GIL: Announcements#whoniverse#GIL: Internal
23 notes
·
View notes
Text
School Visitor Managements Software abu dhabi
Visitor Registration software in dubai
visitor registration software for schools uae
School Visitor Access Control Systems Dubai

#schoolvisitormanagementsoftware #visitorregistrationsoftwaredevelopment #visitoraccesscontrolsystems #visitorregistrationsystems
#visitormanagementsoftwareforschools #visitoraccesscontrolsystems #visitorregistrationsolutionsinburdubai #visitormanagementsoftwaresharjah
#school visitor registration bur dubai#school visitor registration system abu dhabi#visitor management Software abu dhabi#visitor access control systems in uae#visitor access control system in sharjah#visitor access control system in bur dubai#visitor registration system in ajman#visitor registration systems in sharjah#visitor registration systems for schools abu dhabi#visitor access control systems in bur dubai#visitor access control systems#visitor managements system for schools UAE#Visitor Access Control System Abu Dhabi#visitor registration system for schools#visitor registration software for schools in alain
0 notes
Text
Credentials: Users need some form of identification to gain access. This could be in the form of access cards, key fobs, PIN codes, biometric data (such as fingerprints or retina scans), or a combination of these.
Reader Devices: These devices read the credentials provided by users. There are different types of readers, such as card readers, biometric scanners, and keypad entry systems.
Control Panel/Controller: The control panel is the central processing unit of the access control system. It receives information from the reader devices and makes decisions based on the access control policies configured in the system.
Locking Mechanisms: Physical barriers like doors, gates, or turnstiles are equipped with locking mechanisms controlled by the access control system. These can include electronic locks, electromagnetic locks, or other locking devices.
Database: A database stores information about authorized users, their credentials, and access permissions. This information is used by the control panel to make decisions regarding access.
Software: Access control systems are managed through software, which allows administrators to set up and customize access levels, view logs of access events, and make changes to the system's configuration.
Monitoring and Logging: Access control systems often include features for monitoring and logging access events. This information can be useful for security audits, investigations, and tracking user activity.
#accesscontrolsystemuae #accesscontrolsystems
#accesscontrolsysteminuae #accesscontrolsysteminsharjah #accesscontrolsystemdubai #accesscontrolsysteminstallationabudhabi
#accesscontrolsysteminstallation
#access control system abu dhabi#access control system in uae#access control system in sharjah#access control system dubai#access control system installtion#access control system installation abu dhabi#access control system installation uae#access control system installation sharjah#access control system in bur dubai#visitor access control system uae#visitor access control systems in alain#visitor access control system in bur dubai
0 notes
Text

One touch, endless possibilities. Explore Spintly’s Bluetooth biometric solutions - secure access from your phone to the front door: https://spintly.com/blog/biometrics-the-future-and-recent-trends-in-access-control/
#biometric machine#biometric attendance#biometric access#biometrics#mobile access#spintly#accesscontrol#visitor management system#access control solutions#smartbuilding#smartacess
0 notes
Text
Streamlining Amusement Park Entry: Modern Solutions for Efficient Visitor Management
Efficient visitor entry management is crucial for amusement parks to enhance guest experiences, ensure safety, and optimize operations. With advancements in technology, parks can now implement systems that facilitate seamless entry processes.
The Importance of Efficient Entry Management
Long queues and manual ticket checks can detract from the visitor experience. Implementing streamlined entry systems not only improves guest satisfaction but also aids in crowd control and security.
Key Components of Modern Entry Management Systems
1. Online Ticketing and Pre-registration
Allowing guests to purchase tickets online and register in advance reduces wait times at entry points. This system can also provide valuable data on expected attendance, aiding in resource planning.
2. Contactless Entry Solutions
Utilizing QR codes or RFID-enabled wristbands enables quick and hygienic access to the park. These methods minimise physical contact and expedite the entry process.
3. Real-time Monitoring and Analytics
Implementing systems that monitor visitor flow in real-time allows for dynamic crowd management. Data analytics can help identify peak times and areas, facilitating better staff allocation and enhancing safety measures.
4. Customisable Access Permissions
Advanced systems can assign different access levels to various visitor categories, such as VIPs or group tours, ensuring a tailored experience and efficient movement within the park.
5. Automated Notifications and Alerts
Integrating alert systems that notify staff of large group arrivals or potential security concerns enables proactive management and swift response to situations.
Benefits of Implementing Advanced Entry Management
Enhanced Guest Experience: Reduced wait times and personalised services lead to higher satisfaction.
Improved Operational Efficiency: Automation reduces manual workload, allowing staff to focus on guest engagement.
Increased Security: Real-time monitoring and controlled access points bolster safety measures.
Data-driven Decisions: Analytics provide insights into visitor behavior, informing marketing and operational strategies.
Adopting modern visitor entry management systems for amusement parks is essential, aiming to provide exceptional guest experiences while maintaining efficient and secure operations. By embracing technological advancements, parks can ensure smooth entry processes, better crowd control, and enhanced overall satisfaction. Upgrade your amusement park with smart entry solutions – Contact Parkomax today for seamless, secure, and data-driven visitor management!
#Visitor Entry Management System#Amusement Park Entry Solutions#Entry Management for Theme Parks#Parkomax Entry Systems#Smart Access Control for Parks#Contactless Entry Systems#RFID Wristband Entry#QR Code Ticketing#Real-time Visitor Monitoring#Automated Park Entry#Secure park entry system#Online ticketing system for amusement parks#Park access control technology#Smart ticketing solutions for theme parks#Amusement park management software
0 notes
Text
The Universe Next-door
Summary: While on his "Search for a New Anchor Being" montage, Wade comes across Wolverine and Storm variants who rain on his parade.
A spin on the scene from Deadpool Vol 5 #15 (2013)
Pairing: Storm x Wolverine
Word Count: 980
No Warnings/ Pretty Tame
A/N: Is the humor forced and bad? Mayhaps, but I gave it a try. Please be merciful upon me.

If Wade had known that jumping from one universe to the next in search of a new anchor being would take this much time and painful effort, he would have packed snacks. What situation can't be improved with snacks? This one could use a protein bar or something. Low blood sugar is a bitch! It’s only when the TemPad opens another gate that Wade's nostrils are filled with the oh-so-sweet smell of breakfast foods.
“Huh, so does the X-Mansion look the same in every universe, or did the studio just not want to pay for another location? I guess it is all about location, location, location.” That might work to his advantage. Besides much of the layout remaining the same, only a few noticeable differences were noticeable: a painting and chachi here and there, different light fixtures, and rugs.
Wade looks around the halls curiously. “Now, which door leads to the Blackbird? No, no, stay focused. Note to self, though, find universe with easily accessible Blackbird.”
A joyride would have to wait for now; Wade starts to follow where that oh-so-delectable smell came from. A systems crash is now becoming a controlled systems crash. Students move around the dining room, gathering food on their plates and searching for friends to sit and eat with.
“I don’t think they'll mind if I help myself.”
The dining room went silent as all eyes focused on the strangely dressed visitor helping himself to a large stack of pancakes. Students murmured amongst themselves in disbelief. This couldn't be a new teacher.
“Be not afraid, you beautiful freaks of nature. Don't mind me. I’m just grabbing a quick shnack; then I have to grab another shnack who happens to be one of your hairy custodians, and no, I’m not talking about that hairy blue guy with the glasses. The sofa in the foyer is covered in hair.” He leans into his plate of pancakes. “That hair shall not taint you, my sweet, sweet flapjacks.”
After a bit of bribery, which entailed kidnapping their history professor, which would guarantee them no more homework, Wade makes his way to the second floor, down the hall, takes a right, and it’s three doors down.
“Oh my gosh.” He squeals. “I love that band.”
Wade does grant the courtesy of knocking on the door three times before bursting in unannounced. The curtains are closed, the room smells faintly of cigars, clothes lay askew on the floor, and an unmistakable lump lies curled up in bed, buried deep under the covers.
“Oh my. He does sleep like an animal. Hairy and nude.” Wade's body shutters with excitement before skipping over to the curtains. “Ding, dong, my Wolvie is dead. Rub your eyes, get out of bed.” With one motion, the room is flooded with sunlight. “Ooooh, what a beautiful morning!” The lump under the covers only stirs slightly. “Huh, I thought I could summon him with singing. Maybe if I tell him, he can host the Oscars again.”
Wade walks over to the lump, placing a firm smack on his ass before laying down next to him. “You must be like me and need your eight hours of beauty sleep, cuz let’s be honest, it isn't just diet, exercise, and good mental health that keeps thyself oh so lovely. “ No response is given. “Alright,” Wade sighs heavily, getting up from the bed. “Time to get dressed for school.” Before Wade can feed the impulse to stick a sword up his target's ass, he suddenly feels a tiny droplet of water on his forehead. It would have been of little concern until heavy rain began to fill the room. "Guess ol Charlie needs to fix his pipes."
Wade is pulled from his ramblings when his intended target emerges from the adjoining bathroom with a towel around his waist and slicked-back hair. He freezes upon seeing the uninvited guest. “You ain’t supposed to be here, bub.” He snarls, his claws extended in a flash of light. Wade's eyes widen as he ever so slowly turns his head back towards the bed.
The body under the blankets pulls itself out to reveal a very unpleasant morning-faced, dark-skinned woman with shockingly short, white, spiked hair. “Huh,” Wade looks curiously at the woman. “Gotta admit I love the hair. If it wasn't for the rain, I was gonna assume that the studio just gender and ethnicity bent another Wolverine.” He stares off into the distance, seemingly addressing no one. “Wierd move, guys.”
The weather Goddess sneers at Wade. “Do you know what happens to-”
“Yes, I know what happens to a toad when it’s struck by lightning.” Wade groans. “Man, Bryan Singer did not do you justice. Unless you’re from the new timeline, then Simon Kinberg really did you dirty. And apparently, this fuckin fanfic writer likes callbacks like some musical theater putz.”
Her smile then turns wicked. “Then you should know what happens next.”
Wade doesn't get a word out before his body receives an agonizing jolt of blazing hot electricity through its system. This was undoubtedly a first for him, and this amount of voltage bleeding through him is a record.
He raises his trembling hand to speak, only to fall straight back onto the floor with a loud thud. “There is a nice tingly feeling all over now.” Wade whispers weakly. "Got it. This one's not up for grabs." He says to Storm. Wade manages enough movement to activate the TemPad and slip through the gateway before the angered Wolverine can stab him through his corneas. Thankfully, he doesn't fall far and lands on something soft. In one quick motion, he returns to a seated position, trying to shake out the remainder of the body tingles. “Well,” He huffs, finally getting back up. That’s certainly a rarity in the fanbase. But those two are getting freaky? Tsk, that girl should know better.”
*Wink*
#deadpool and wolverine#deadpool 3#logan x ororo#logan and ororo#storm x wolverine#wade wilson#logan howlett#ororo munroe#ororo x logan#marvel#mcu#fanfiction
39 notes
·
View notes