#compelled speech
Text
Forcing your computer to rat you out

Powerful people imprisoned by the cluelessness of their own isolation, locked up with their own motivated reasoning: “It’s impossible to get a CEO to understand something when his quarterly earnings call depends on him not understanding it.”
Take Mark Zuckerberg. Zuckerberg insists that anyone who wanted to use a pseudonym online is “two-faced,” engaged in dishonest social behavior. The Zuckerberg Doctrine claims that forcing people to use their own names is a way to ensure civility. This is an idea so radioactively wrong, it can be spotted from orbit.
From the very beginning, social scientists (both inside and outside Facebook) told Zuckerberg that he was wrong. People have lots of reasons to hide their identities online, both good and bad, but a Real Names Policy affects different people differently:
https://memex.craphound.com/2018/01/22/social-scientists-have-warned-zuck-all-along-that-the-facebook-theory-of-interaction-would-make-people-angry-and-miserable/
For marginalized and at-risk people, there are plenty of reasons to want to have more than one online identity — say, because you are a #MeToo whistleblower hoping that Harvey Weinstein won’t sic his ex-Mossad mercenaries on you:
https://www.newyorker.com/news/news-desk/harvey-weinsteins-army-of-spies
Or maybe you’re a Rohingya Muslim hoping to avoid the genocidal attentions of the troll army that used Facebook to organize — under their real, legal names — to rape and murder you and everyone you love:
https://www.amnesty.org/en/latest/news/2022/09/myanmar-facebooks-systems-promoted-violence-against-rohingya-meta-owes-reparations-new-report/
But even if no one is looking to destroy your life or kill you and your family, there are plenty of good reasons to present different facets of your identity to different people. No one talks to their lover, their boss and their toddler in exactly the same way, or reveals the same facts about their lives to those people. Maintaining different facets to your identity is normal and healthy — and the opposite, presenting the same face to everyone in your life, is a wildly terrible way to live.
None of this is controversial among social scientists, nor is it hard to grasp. But Zuckerberg stubbornly stuck to this anonymity-breeds-incivility doctrine, even as dictators used the fact that Facebook forced dissidents to use their real names to retain power through the threat (and reality) of arrest and torture:
https://pluralistic.net/2023/01/25/nationalize-moderna/#hun-sen
Why did Zuck cling to this dangerous and obvious fallacy? Because the more he could collapse your identity into one unitary whole, the better he could target you with ads. Truly, it is impossible to get a billionaire to understand something when his mega-yacht depends on his not understanding it.
This motivated reasoning ripples through all of Silicon Valley’s top brass, producing what Anil Dash calls “VC QAnon,” the collection of conspiratorial, debunked and absurd beliefs embraced by powerful people who hold the digital lives of billions of us in their quivering grasp:
https://www.anildash.com/2023/07/07/vc-qanon/
These fallacy-ridden autocrats like to disguise their demands as observations, as though wanting something to be true was the same as making it true. Think of when Eric Schmidt — then the CEO of Google — dismissed online privacy concerns, stating “If you have something that you don’t want anyone to know, maybe you shouldn’t be doing it in the first place”:
https://www.eff.org/deeplinks/2009/12/google-ceo-eric-schmidt-dismisses-privacy
Schmidt was echoing the sentiments of his old co-conspirator, Sun Microsystems CEO Scott McNealy: “You have zero privacy anyway. Get over it”:
https://www.wired.com/1999/01/sun-on-privacy-get-over-it/
Both men knew better. Schmidt, in particular, is very jealous of his own privacy. When Cnet reporters used Google to uncover and publish public (but intimate and personal) facts about Schmidt, Schmidt ordered Google PR to ignore all future requests for comment from Cnet reporters:
https://www.cnet.com/tech/tech-industry/how-cnet-got-banned-by-google/
(Like everything else he does, Elon Musk’s policy of responding to media questions about Twitter with a poop emoji is just him copying things other people thought up, making them worse, and taking credit for them:)
https://www.theverge.com/23815634/tesla-elon-musk-origin-founder-twitter-land-of-the-giants
Schmidt’s actions do not reflect an attitude of “If you have something that you don’t want anyone to know, maybe you shouldn’t be doing it in the first place.” Rather, they are the normal response that we all have to getting doxed.
When Schmidt and McNealy and Zuck tell us that we don’t have privacy, or we don’t want privacy, or that privacy is bad for us, they’re disguising a demand as an observation. “Privacy is dead” actually means, “When privacy is dead, I will be richer than you can imagine, so stop trying to save it, goddamnit.”
We are all prone to believing our own bullshit, but when a tech baron gets high on his own supply, his mental contortions have broad implications for all of us. A couple years after Schmidt’s anti-privacy manifesto, Google launched Google Plus, a social network where everyone was required to use their “real name.”
This decision — justified as a means of ensuring civility and a transparent ruse to improve ad targeting — kicked off the Nym Wars:
https://epeus.blogspot.com/2011/08/google-plus-must-stop-this-identity.html
One of the best documents to come out of that ugly conflict is “Falsehoods Programmers Believe About Names,” a profound and surprising enumeration of all the ways that the experiences of tech bros in Silicon Valley are the real edge-cases, unreflective of the reality of billions of their users:
https://www.kalzumeus.com/2010/06/17/falsehoods-programmers-believe-about-names/
This, in turn, spawned a whole genre of programmer-fallacy catalogs, falsehoods programmers believe about time, currency, birthdays, timezones, email addresses, national borders, nations, biometrics, gender, language, alphabets, phone numbers, addresses, systems of measurement, and, of course, families:
https://github.com/kdeldycke/awesome-falsehood
But humility is in short supply in tech. It’s impossible to get a programmer to understand something when their boss requires them not to understand it. A programmer will happily insist that ordering you to remove your “mask” is for your own good — and not even notice that they’re taking your skin off with it.
There are so many ways that tech executives could improve their profits if only we would abandon our stubborn attachment to being so goddamned complicated. Think of Netflix and its anti-passsword-sharing holy war, which is really a demand that we redefine “family” to be legible and profitable for Netflix:
https://pluralistic.net/2023/02/02/nonbinary-families/#red-envelopes
But despite the entreaties of tech companies to collapse our identities, our families, and our online lives into streamlined, computably hard-edged shapes that fit neatly into their database structures, we continue to live fuzzy, complicated lives that only glancingly resemble those of the executives seeking to shape them.
Now, the rich, powerful people making these demands don’t plan on being constrained by them. They are conservatives, in the tradition of #FrankWilhoit, believers in a system of “in-groups whom the law protects but does not bind, alongside out-groups whom the law binds but does not protect”:
https://crookedtimber.org/2018/03/21/liberals-against-progressives/#comment-729288
As with Schmidt’s desire to spy on you from asshole to appetite for his own personal gain, and his violent aversion to having his own personal life made public, the tech millionaires and billionaires who made their fortune from the flexibility of general purpose computers would like to end that flexibility. They insist that the time for general purpose computers has passed, and that today, “consumers” crave the simplicity of appliances:
https://memex.craphound.com/2012/01/10/lockdown-the-coming-war-on-general-purpose-computing/
It is in the War On General Purpose Computing that we find the cheapest and flimsiest rhetoric. Companies like Apple — and their apologists — insist that no one wants to use third-party app stores, or seek out independent repair depots — and then spend millions to make sure that it’s illegal to jailbreak your phone or get it fixed outside of their own official channel:
https://doctorow.medium.com/apples-cement-overshoes-329856288d13
The cognitive dissonance of “no one wants this,” and “we must make it illegal to get this” is powerful, but the motivated reasoning is more powerful still. It is impossible to get Tim Cook to understand something when his $49 million paycheck depends on him not understanding it.
The War on General Purpose Computing has been underway for decades. Computers, like the people who use them, stubbornly insist on being reality-based, and the reality of computers is that they are general purpose. Every computer is a Turing complete, universal Von Neumann machine, which means that it can run every valid program. There is no way to get a computer to be almost Turing Complete, only capable of running programs that don’t upset your shareholders’ fragile emotional state.
There is no such thing as a printer that will only run the “reject third-party ink” program. There is no such thing as a phone that will only run the “reject third-party apps” program. There are only laws, like the Section 1201 of the Digital Millennium Copyright Act, that make writing and distributing those programs a felony punishable by a five-year prison sentence and a $500,000 fine (for a first offense).
That is to say, the War On General Purpose Computing is only incidentally a technical fight: it is primarily a legal fight. When Apple says, “You can’t install a third party app store on your phone,” what they means is, “it’s illegal to install that third party app store.” It’s not a technical countermeasure that stands between you and technological self-determination, it’s a legal doctrine we can call “felony contempt of business model”:
https://locusmag.com/2020/09/cory-doctorow-ip/
But the mighty US government will not step in to protect a company’s business model unless it at least gestures towards the technical. To invoke DMCA 1201, a company must first add the thinnest skin of digital rights management to their product. Since 1201 makes removing DRM illegal, a company can use this molecule-thick scrim of DRM to felonize any activity that the DRM prevents.
More than 20 years ago, technologists started to tinker with ways to combine the legal and technical to tame the wild general purpose computer. Starting with Microsoft’s Palladium project, they theorized a new “Secure Computing” model for allowing companies to reach into your computer long after you had paid for it and brought it home, in order to discipline you for using it in ways that undermined its shareholders’ interest.
Secure Computing began with the idea of shipping every computer with two CPUs. The first one was the normal CPU, the one you interacted with when you booted it up, loaded your OS, and ran programs. The second CPU would be a Trusted Platform Module, a brute-simple system-on-a-chip designed to be off-limits to modification, even by its owner (that is, you).
The TPM would ship with a limited suite of simple programs it could run, each thoroughly audited for bugs, as well as secret cryptographic signing keys that you were not permitted to extract. The original plan called for some truly exotic physical security measures for that TPM, like an acid-filled cavity that would melt the chip if you tried to decap it or run it through an electron-tunneling microscope:
https://pluralistic.net/2020/12/05/trusting-trust/#thompsons-devil
This second computer represented a crack in the otherwise perfectly smooth wall of a computer’s general purposeness; and Trusted Computing proposed to hammer a piton into that crack and use it to anchor a whole superstructure that could observe — and limited — the activity of your computer.
This would start with observation: the TPM would observe every step of your computer’s boot sequence, creating cryptographic hashes of each block of code as it loaded and executed. Each stage of the boot-up could be compared to “known good” versions of those programs. If your computer did something unexpected, the TPM could halt it in its tracks, blocking the boot cycle.
What kind of unexpected things do computers do during their boot cycle? Well, if your computer is infected with malware, it might load poisoned versions of its operating system. Once your OS is poisoned, it’s very hard to detect its malicious conduct, since normal antivirus programs rely on the OS to faithfully report what your computer is doing. When the AV program asks the OS to tell it which programs are running, or which files are on the drive, it has no choice but to trust the OS’s response. When the OS is compromised, it can feed a stream of lies to users’ programs, assuring these apps that everything is fine.
That’s a very beneficial use for a TPM, but there’s a sinister flipside: the TPM can also watch your boot sequence to make sure that there aren’t beneficial modifications present in your operating system. If you modify your OS to let you do things the manufacturer wants to prevent — like loading apps from a third-party app-store — the TPM can spot this and block it.
Now, these beneficial and sinister uses can be teased apart. When the Palladium team first presented its research, my colleague Seth Schoen proposed an “owner override”: a modification of Trusted Computing that would let the computer’s owner override the TPM:
https://web.archive.org/web/20021004125515/http://vitanuova.loyalty.org/2002-07-05.html
This override would introduce its own risks, of course. A user who was tricked into overriding the TPM might expose themselves to malicious software, which could harm that user, as well as attacking other computers on the user’s network and the other users whose data were on the compromised computer’s drive.
But an override would also provide serious benefits: it would rule out the monopolistic abuse of a TPM to force users to run malicious code that the manufacturer insisted on — code that prevented the user from doing things that benefited the user, even if it harmed the manufacturer’s shareholders. For example, with owner override, Microsoft couldn’t force you to use its official MS Office programs rather than third-party compatible programs like Apple’s iWork or Google Docs or LibreOffice.
Owner override also completely changed the calculus for another, even more dangerous part of Trusted Computing: remote attestation.
Remote Attestation is a way for third parties to request a reliable, cryptographically secured assurances about which operating system and programs your computer is running. In Remote Attestation, the TPM in your computer observes every stage of your computer’s boot, gathers information about all the programs you’re running, and cryptographically signs them, using the signing keys the manufacturer installed during fabrication.
You can send this “attestation” to other people on the internet. If they trust that your computer’s TPM is truly secure, then they know that you have sent them a true picture of your computer’s working (the actual protocol is a little more complicated and involves the remote party sending you a random number to cryptographically hash with the attestation, to prevent out-of-date attestations).
Now, this is also potentially beneficial. If you want to make sure that your technologically unsophisticated friend is running an uncompromised computer before you transmit sensitive data to it, you can ask them for an attestation that will tell you whether they’ve been infected with malware.
But it’s also potentially very sinister. Your government can require all the computers in its borders to send a daily attestation to confirm that you’re still running the mandatory spyware. Your abusive spouse — or abusive boss — can do the same for their own disciplinary technologies. Such a tool could prevent you from connecting to a service using a VPN, and make it impossible to use Tor Browser to protect your privacy when interacting with someone who wishes you harm.
The thing is, it’s completely normal and good for computers to lie to other computers on behalf of their owners. Like, if your IoT ebike’s manufacturer goes out of business and all their bikes get bricked because they can no longer talk to their servers, you can run an app that tricks the bike into thinking that it’s still talking to the mothership:
https://nltimes.nl/2023/07/15/alternative-app-can-unlock-vanmoof-bikes-popular-amid-bankruptcy-fears
Or if you’re connecting to a webserver that tries to track you by fingerprinting you based on your computer’s RAM, screen size, fonts, etc, you can order your browser to send random data about this stuff:
https://jshelter.org/fingerprinting/
Or if you’re connecting to a site that wants to track you and nonconsensually cram ads into your eyeballs, you can run an adblocker that doesn’t show you the ads, but tells the site that it did:
https://www.eff.org/deeplinks/2019/07/adblocking-how-about-nah
Owner override leaves some of the beneficial uses of remote attestation intact. If you’re asking a friend to remotely confirm that your computer is secure, you’re not going to use an override to send them bad data about about your computer’s configuration.
And owner override also sweeps all of the malicious uses of remote attestation off the board. With owner override, you can tell any lie about your computer to a webserver, a site, your boss, your abusive spouse, or your government, and they can’t spot the lie.
But owner override also eliminates some beneficial uses of remote attestation. For example, owner override rules out remote attestation as a way for strangers to play multiplayer video games while confirming that none of them are using cheat programs (like aimhack). It also means that you can’t use remote attestation to verify the configuration of a cloud server you’re renting in order to assure yourself that it’s not stealing your data or serving malware to your users.
This is a tradeoff, and it’s a tradeoff that’s similar to lots of other tradeoffs we make online, between the freedom to do something good and the freedom to do something bad. Participating anonymously, contributing to free software, distributing penetration testing tools, or providing a speech platform that’s open to the public all represent the same tradeoff.
We have lots of experience with making the tradeoff in favor of restrictions rather than freedom: powerful bad actors are happy to attach their names to their cruel speech and incitement to violence. Their victims are silenced for fear of that retaliation.
When we tell security researchers they can’t disclose defects in software without the manufacturer’s permission, the manufacturers use this as a club to silence their critics, not as a way to ensure orderly updates.
When we let corporations decide who is allowed to speak, they act with a mixture of carelessness and self-interest, becoming off-the-books deputies of authoritarian regimes and corrupt, powerful elites.
Alas, we made the wrong tradeoff with Trusted Computing. For the past twenty years, Trusted Computing has been creeping into our devices, albeit in somewhat denatured form. The original vision of acid-filled secondary processors has been replaced with less exotic (and expensive) alternatives, like “secure enclaves.” With a secure enclave, the manufacturer saves on the expense of installing a whole second computer, and instead, they draw a notional rectangle around a region of your computer’s main chip and try really hard to make sure that it can only perform a very constrained set of tasks.
This gives us the worst of all worlds. When secure enclaves are compromised, we not only lose the benefit of cryptographic certainty, knowing for sure that our computers are only booting up trusted, unalterted versions of the OS, but those compromised enclaves run malicious software that is essentially impossible to detect or remove:
https://pluralistic.net/2022/07/28/descartes-was-an-optimist/#uh-oh
But while Trusted Computing has wormed its way into boot-restrictions — preventing you from jailbreaking your computer so it will run the OS and apps of your choosing — there’s been very little work on remote attestation…until now.
Web Environment Integrity is Google’s proposal to integrate remote attestation into everyday web-browsing. The idea is to allow web-servers to verify what OS, extensions, browser, and add-ons your computer is using before the server will communicate with you:
https://github.com/RupertBenWiser/Web-Environment-Integrity/blob/main/explainer.md
Even by the thin standards of the remote attestation imaginaries, there are precious few beneficial uses for this. The googlers behind the proposal have a couple of laughable suggestions, like, maybe if ad-supported sites can comprehensively refuse to serve ad-blocking browsers, they will invest the extra profits in making things you like. Or: letting websites block scriptable browsers will make it harder for bad people to auto-post fake reviews and comments, giving users more assurances about the products they buy.
But foundationally, WEI is about compelling you to disclose true facts about yourself to people who you want to keep those facts from. It is a Real Names Policy for your browser. Google wants to add a new capability to the internet: the ability of people who have the power to force you to tell them things to know for sure that you’re not lying.
The fact that the authors assume this will be beneficial is just another “falsehood programmers believe”: there is no good reason to hide the truth from other people. Squint a little and we’re back to McNealy’s “Privacy is dead, get over it.” Or Schmidt’s “If you have something that you don’t want anyone to know, maybe you shouldn’t be doing it in the first place.”
And like those men, the programmers behind this harebrained scheme don’t imagine that it will ever apply to them. As Chris Palmer — who worked on Chromium — points out, this is not compatible with normal developer tools or debuggers, which are “incalculably valuable and not really negotiable”:
https://groups.google.com/a/chromium.org/g/blink-dev/c/Ux5h_kGO22g/m/5Lt5cnkLCwAJ
This proposal is still obscure in the mainstream, but in tech circles, it has precipitated a flood of righteous fury:
https://arstechnica.com/gadgets/2023/07/googles-web-integrity-api-sounds-like-drm-for-the-web/
As I wrote last week, giving manufacturers the power to decide how your computer is configured, overriding your own choices, is a bad tradeoff — the worst tradeoff, a greased slide into terminal enshittification:
https://pluralistic.net/2023/07/24/rent-to-pwn/#kitt-is-a-demon
This is how you get Unauthorized Bread:
https://arstechnica.com/gaming/2020/01/unauthorized-bread-a-near-future-tale-of-refugees-and-sinister-iot-appliances/
All of which leads to the question: what now? What should be done about WEI and remote attestation?
Let me start by saying: I don’t think it should be illegal for programmers to design and release these tools. Code is speech, and we can’t understand how this stuff works if we can’t study it.
But programmers shouldn’t deploy it in production code, in the same way that programmers should be allowed to make pen-testing tools, but shouldn’t use them to attack production systems and harm their users. Programmers who do this should be criticized and excluded from the society of their ethical, user-respecting peers.
Corporations that use remote attestation should face legal restrictions: privacy law should prevent the use of remote attestation to compel the production of true facts about users or the exclusion of users who refuse to produce those facts. Unfair competition law should prevent companies from using remote attestation to block interoperability or tie their products to related products and services.
Finally, we must withdraw the laws that prevent users and programmers from overriding TPMs, secure enclaves and remote attestations. You should have the right to study and modify your computer to produce false attestations, or run any code of your choosing. Felony contempt of business model is an outrage. We should alter or strike down DMCA 1201, the Computer Fraud and Abuse Act, and other laws (like contract law’s “tortious interference”) that stand between you and “sole and despotic dominion” over your own computer. All of that applies not just to users who want to reconfigure their own computers, but also toolsmiths who want to help them do so, by offering information, code, products or services to jailbreak and alter your devices.
Tech giants will squeal at this, insisting that they serve your interests when they prevent rivals from opening up their products. After all, those rivals might be bad guys who want to hurt you. That’s 100% true. What is likewise true is that no tech giant will defend you from its own bad impulses, and if you can’t alter your device, you are powerless to stop them:
https://pluralistic.net/2022/11/14/luxury-surveillance/#liar-liar
Companies should be stopped from harming you, but the right place to decide whether a business is doing something nefarious isn’t in the boardroom of that company’s chief competitor: it’s in the halls of democratically accountable governments:
https://www.eff.org/wp/interoperability-and-privacy
So how do we get there? Well, that’s another matter. In my next book, The Internet Con: How to Seize the Means of Computation (Verso Books, Sept 5), I lay out a detailed program, describing which policies will disenshittify the internet, and how to get those policies:
https://www.versobooks.com/products/3035-the-internet-con
Predictably, there are challenges getting this kind of book out into the world via our concentrated tech sector. Amazon refuses to carry the audio edition on its monopoly audiobook platform, Audible, unless it is locked to Amazon forever with mandatory DRM. That’s left me self-financing my own DRM-free audio edition, which is currently available for pre-order via this Kickstarter:
http://seizethemeansofcomputation.org

I’m kickstarting the audiobook for “The Internet Con: How To Seize the Means of Computation,” a Big Tech disassembly manual to disenshittify the web and bring back the old, good internet. It’s a DRM-free book, which means Audible won’t carry it, so this crowdfunder is essential. Back now to get the audio, Verso hardcover and ebook:
https://www.kickstarter.com/projects/doctorow/the-internet-con-how-to-seize-the-means-of-computation

If you’d like an essay-formatted version of this post to read or share, here’s a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2023/08/02/self-incrimination/#wei-bai-bai

[Image ID: An anatomical drawing of a flayed human head; it has been altered to give it a wide-stretched mouth revealing a gadget nestled in the back of the figure's throat, connected by a probe whose two coiled wires stretch to an old fashioned electronic box. The head's eyes have been replaced by the red, menacing eye of HAL 9000 from Stanley Kubrick's '2001: A Space Odyssey.' Behind the head is a code waterfall effect as seen in the credits of the Wachowskis' 'The Matrix.']

Image:
Cryteria (modified)
https://commons.wikimedia.org/wiki/File:HAL9000.svg
CC BY 3.0
https://creativecommons.org/licenses/by/3.0/deed.en
#pluralistic#chaffing#spoofing#remote attestation#rene descartes#adversarial interoperability#war on general purpose computing#canvas attacks#vpns#compelled speech#onion routing#owner override#stalkerware#ngscb#palladium#trusted computing#secure enclaves#tor#interop#net neutrality#taking the fifth#right to remain silent#real names policy#the zuckerberg doctrine#none of your business#the right to lie#right to repair#bossware#spyware#wei web environment integrity
2K notes
·
View notes
Text
By: Matt Dathan
Published: Sep 29, 2023
Holding a view that does not subscribe to critical race theory is a protected characteristic under equality laws, a judge has ruled in what is believed to be a legal first in the UK.
Sean Corby, an employee of the government’s workplace conciliation service Acas, took the organisation to an employment tribunal after bosses ordered him to remove comments that he posted on social media that were critical of Black Lives Matter (BLM).
Corby had written that critical race theory, an ideology that believes racism is entrenched in society and which is at the heart of the BLM movement, is divisive because it portrays white people as racist.

[ Corby argued that Martin Luther King’s methods of confronting racism in society were better than those of Black Lives Matter ]
He argued that a better approach to addressing racism in society was to follow the approach of Martin Luther King, who said we should aspire to a day when people would be judged by the content of their character rather than the colour of their skin.
Corby made the comments on Yammer, a workplace social media platform.
Some of Corby’s colleagues complained to Acas’ management that the comments were offensive and brought a grievance case against him. They claimed that he was “using the Yammer platform to promote racist ideas” and suggested he could be member of a far-right group. They also said they would not feel safe to be “in contact with him” and questioned his right to be employed by Acas.
Acas dismissed their complaints, but instructed Corby to remove the posts on the grounds that employees had found them offensive.
Corby has taken Acas to an employment tribunal, claiming he had been unlawfully discriminated against and his views were protected under the Equalities Act in the same way as his colleagues’ views on critical race theory. Religion or belief are among nine protected characteristics under the Equalities Act.
The Free Speech Union, which has supported Corby in his case against Acas, said his colleagues had wrongly tried to silence him.
Acas defended its decision to instruct him to remove his social media posts, arguing that what he was posting were only opinions, rather than beliefs and were subsequently not protected under the Equalities Act.
Employment Judge Kirsty Ayre, presiding over the case in Leeds in a three-day hearing earlier this month, ruled in Corby’s favour on the basis that he had given his beliefs careful consideration and much thought.

[ Corby said his beliefs on race are rooted in the ideas of Howard Thurman, above, and “others who railed against segregation and separatism” ]
As a result, she said his comments opposing Black Lives Matter and critical race theory fall under the “religion or belief” section of the Equalities Act. The ruling paves the way for the tribunal to consider in April whether Corby was unlawfully discriminated against by Acas.
It is believed to be the first time a judge has ruled that holding a contrary view to critical race theory is a protected characteristic under equality laws.
“Colleagues who’d never met me and knew nothing about me or my life targeted me and called me a racist. This caused me a great deal of distress,” Corby said.
“My beliefs on race are rooted in the ideas of Howard Thurman and others who railed against segregation and separatism, as well as in my personal experience. I grew up with black people, was immersed in their culture and dedicated my life to music and education. I have also experienced bigotry from white and black people in various forms and on many occasions. It is reprehensible of anyone to seek to divide us along lines of colour or to try and bully anti-racists like me into silence.
“I’m delighted we have made a stand and taken a step to embedding a in the workplace a more conciliatory and harmonious approach to dealing with issues around race.”
Toby Young, general secretary of the Free Speech Union, said the case was “a significant victory for the cause of freedom of speech” in the UK.
He added: “Sean’s belief that we should judge people on the content of their character rather than the colour of their skin is eminently sensible and shared by most people, save for a handful of far-right and far-left activists. His employer should not have taken seriously the vexatious complaints of Sean’s colleagues, who claimed that his quoting Martin Luther King made them feel ‘unsafe’.”
An Acas spokesman said: “We take pride in having a diverse workforce and have noted the tribunal’s decision on one aspect of this case that is set to conclude next year. We value Acas staff having a voice and our regular staff surveys continue to show that Acas is an inclusive organisation.”
[ Via: https://archive.md/WCowc ]
--
Here's a diagram:

==
Separation of church and state.
"cAnCeL cULtUrE dOeSnT eXiSt!!"
#Andrew Doyle#Sean Corby#critical race theory#secularism#Martin Luther King Jr#MLK Jr#cancel culture#compelled speech#ideological corruption#Black Lives Matter#BLM#criticism of ideas#religion is a mental illness
61 notes
·
View notes
Text
Compelled Speech !

Your made up terms
Mean nothing to me
And I won't use any words
With which I don't agree
Don't call me CiS gendered
I am simply a man
That term has served us forever
And I believe it still can
You can call yourself anything
And whatever you will
But don't expect me to
Because I never will
And don't try to tell me
That I am causing you pain
Your notions of trauma
Are simply insane
I won't use a plural
When I only mean one
And if you do not like that
Stick it where there's no sun
You see the problem with you
When you're picking your fights
Is it's all about you
And not everyone's rights
Compelled Speech is a tool
For Dictators to use
When oppressing their people
It's like verbal thumbscrews
No system can tell me
What I can & can't say
They may try to take my freedom
And lock me away
But I won't use any terms
With which I don't agree
And if that is a problem
Then simply don't talk to me
I'm not trying to upset you
Or to pick a fight
But I choose what I say
Because that is my right !
Smackemback 30/07/23
2 notes
·
View notes
Text
2 notes
·
View notes
Text
The Pronoun Equivocation - "Respect"
Having recently gotten into a discussion about the misnamed “Gender Affirming Care” with some of my acquaintances we broached many contentious topics but one point that stuck out was when we got into pronoun territory.
My interlocutor was brought up the idea that the shortening of names – like Stan for Stanley – was a preference and that people were just being polite by referring to the…
View On WordPress
0 notes
Text
What terfs think "compelled speech" is : being considered a rude transphobic asshole for misgendering or deadnaming someone
What should actually be considered "compelled speech" : trans people being threatened with "if you don't misgender yourself by calling yourself a man/woman /mother/father you don't get to access this healthcare or services that could potentially save your life because I beleive trans people need to be forced into closenting or detransitioning themselves under threat of death and i will hold healthcare and protection for DV survivors hostage in order to compel trans people into misgendering themselves "
Notice how no terf or transphobe has ever been killed or maimed by correctly gendering a trans person or even when they misgender trans people - but PLENTY of trans and intersex people have been killed by these ciscentric policies limiting things like cancer treatments to cis people or trans people who've been forced into detransitioning or recloseting themselves.
And yet terfs and transphobes try to say that We are the self obsessed ones who are hurting others for our feelings like your transphobic and intersexist BS has a literal death toll compared to the hurt feelings from cis people's superiority complex and control over language being challenged who really has the power here to "compel speech" it's cis people in positions of power and they're doing it to trans and intersex people
0 notes
Text










:)
#chuck Should be directing most of his ire at sam bc he's the one who always pulls off these crazy feats of love that#tie the cosmos into knots lmao#also this sam speech. ''you protected me from dad.... from lucifer....''#he did neither of those things baby but i understand you need to reframe your trauma (even tho the writers don't)#regardless this sequence of scenes is more compelling to me than anything in the following 3 eps#spn#liveblog tag#15.17#i like that it's titled 'unity' and features samndean having a physical altercation while chuck (dean mirror) convinces amara (sam mirror)#that nobody else in the universe understands them and that the only way for them to go on is by him absorbing her into himself#and he was able to convince her of this bc she was crushed that dean lied to her and intended to kill her to take down chuck#i like it. picasso
34 notes
·
View notes
Text
honestly beth and jerry have maybe my second favourite relationship in the entire show just for how interesting and tragic it is. like its brushed aside a lot in favour of other stuff but they were really both just kids... and the saddest part about them is that they maybe do love each other but its always in some way artificial
#‘i would find you in any lifetime’ but they never really had a choice#rick and morty#makes stuff like rixty minutes wayyy more sad#like they say they only had summer bc they blew a tire on the way to the clinic… JAW DROP.#but also stuff like jerry talking beth back thru their first kiss and her admitting to hating it#alsooo like. ik they bring up a lot that beth was 17 but jerry was also like. 17. or around it. they were BOTH kids and they both had to#make hard decisions. and they both did everything wrong and are both unhappy#like as much as ppl cling to that one speech abt jerry being a parasite i think its true for both of them#they both need each other in a sick way. yhey both love each other and they both hate wach other#its just their different personalities and they way they view each other that sets them apart#rick views jerry as a parasite bc well.. beth is his daughter and a lot like him#and also u can argue he was projecting a lot in that scene#but in the end its beth who ends up going back to jerry#she needs jerry as much as he needs her. bc he gives her that unconditional love she missed growinh up#..anyway#do they have a ship name btw. berry. jereth. lol#for the record their relationship is terrible. but i love thinking abt it its sooooo compelling to me
57 notes
·
View notes
Text
pondering on a meta diving into Gale's abstract brand of selflessness (willingness to go away to a corner of the world to die so that none of the faceless masses will be harmed by his mistake) vs his personal selfishness (willingness to stick by tav despite being repulsed by tiefling camp murder + general vocal approval or interest in accumulating more power) and Gale's status as someone who is good aligned but generally ineffectual at enforcing actual good (the way that wyll or karlach will actually leave the party) which is fascinating for a fairly good-aligned person. just love when the Good Guy is actually kind of fucking weird. edit: tumblr cut off my tags Okay. and how all of this ties back in an interesting way to his relationship and power imbalance with mystra. he was wronged, deeply, but he also desires still that ... status / closeness to divinity in some way, by her influence. Gale thinks that he would be a better god simply by virtue of his mortality but he cannot escape the appeal of holding himself apart from others and being more than, greater than, something closer to godliness and thus inherently removed from mortal values and standards of right and wrong, which the gods themselves don't adhere to in the same way.
#it's just one of those things that's really compelling about his character to me in terms of ...#Gale hesitates with the shadow lantern not really because he's put off by the magic#in fact if a sorcerer Tav condemns dark magic he rebukes it and argues that all magic is inherently neutral; some simply more#frowned upon than others#He appreciates good acts. he'll say We Should Do The Good Act. but he's not going to really fight FOR doing the right thing the way#others might; and when you get beyond the act itself he can very quickly rationalize#necessity. or mistake. or the value of power + strength behind it.#the dichotomy between his fearful willingness to die at Mystra's behest while not really tamping down his interest in power and survival#that peers out and I think (?) feels almost obfuscated behind his eloquence and his manners and charm and general clockability as a#guy who approves of good things.#and there are things he says & does that are further beyond the expectations of what you might expect from someone who is 'good'#the initial interest in a deal with Raphael; the approval of taking tadpoles despite the uncertainty and possible cost; the acknowledgment#that powerful forms (slayer form or ascending astarion) will be useful onward#His Fucking Speech to Tav after the grove slaughter where he's outraged and disgusted but can be swayed to stay#he's so... sunk cost fallacy too I think. at some point the ends must surely justify the means right#and his God of Ambition thing is sooo compelling because it really drives to the max the part of gale's personality that is always there#but obfuscated by his immediate insistence that he's a moral person right. you know him to be of sound judgement. trust him.#He likes seeing good happen and he's happy to go along with doing good things and he'll#state his opinion when he thinks something EVIL is happening. but he's not necessarily#going out of his way here either if tav isn't -- and to be fair game mechanics technically mean#no one is - but we can read from Wyll/Karlach removing themselves from the situation#(need to double check but can't Wyll also leave a slayer dark urge?)#that they CAN go out of their way#Wizard Apathy Baby! you feel benevolent toward others but you crave what is beyond humanity and#deeply rooted in the arcane; which you see as beyond too basic concepts of 'good' vs 'bad' magic; neutrality that sways with intent#you trust good actions but you didn't ACTUALLY use your power at the time For Others either; you probably could have but#you craved MORE. something BETTER.#and there's a lot there in how that interacts with his relationship to mystra too#his desire to achieve something closer to godliness and both thinking that he can do better because he's mortal but at the same time#has proven that he can separate himself or his technical moralities from a situation if it means exploration of power/knowledge Beyond
69 notes
·
View notes
Text
i like yosuke’s aphorisms and idioms. he’s such a “you know what they say” guy to me. he’s out here saying sayings with incredible frequency
#he makes a really notable amount of them. it’s a minor but incredibly compelling speech quirk#it suits him. that mix of genuinely insightful nearly philosophical strain of thinking with his loyalty to societal status quo#if/when i ever replay p4 i’m adding a yosuke proverb counter#yosukeposting#rambles
24 notes
·
View notes
Text
#april fools#joke post#shitpost#pigeon.img#parody#meme#joke#april fools day#french revolution#marat#jean paul marat#simone evrard#frev#fun fact I did actually do this#as part of a creative writing project a while back#but the apology part is a meme#riffing off evrard's (very interesting & compelling) speech to the convention#about plagiarism and impersonation when it comes to ami du peuple
21 notes
·
View notes
Text
SIX SENTENCE SUNDAY
I was going to work on this more during my shift but then I remembered it is Oscars day and I’m chronically addicted to awards shows 😔 anyways here’s the intro to my grandekofi bar au <3
~~~~~~
Two drinks. Just two.
That was how many drinks it took for Dame to admit she was in love with Tia. Well, admit it to herself at least.
She stared at her reflection in the grimy bathroom mirror of the bar Hannah had dragged them all out to for her birthday. Even with the dingy lighting, Dame could see the flush of her cheeks, left over from when Tia had wrapped her arms around her waist as they waited at the bar. It wasn’t long after that that she had excused herself.
#six sentence sunday#sss#grandekofi#I do have more than this written I realize that intro makes it seem like I don’t#but I do!!!#I just think the intro is compelling enough to post :)#anyways Oscar’s are going okay so far da’vine won but I had it muted during her speech bc I’m at work#so I’ll watch that when I get home#and they showed a dog :)#I don’t like jimmy Kimmel so he’s annoying me but whatever#anyways!!!!#my writing#La grande dame#tia kofi#dametia#drag race#rpdr#RuPaul’s drag race#uk vs the world#ukvtw2#drag race uk vs the world
22 notes
·
View notes
Text

By: Andrew Doyle
Published: Feb 17, 2024
This is how it begins. “Why not add your pronouns to your email signature?” “Why not announce your pronouns at the beginning of meetings?” “Why not encourage your staff members to ask for pronouns in day-to-day conversation?” After all, it’s just about being compassionate and creating a more “inclusive” work environment. Only a bigot would object to that…
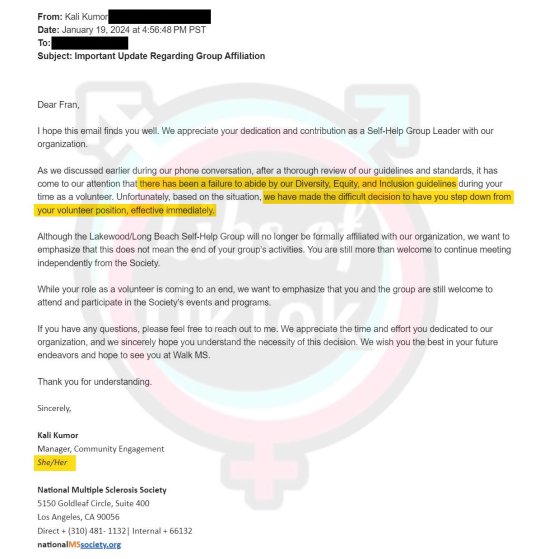
It’s this kind of skewed reasoning that has led to the firing of Fran Itkoff, a 90-year-old volunteer for the National Multiple Sclerosis Society, who simply expressed confusion when faced with a request that she add pronouns to her emails. “I had seen it on a couple of letters that had come in after the person’s name”, Itkoff said in an interview, “but I didn’t know what it meant”.
We can hardly be surprised when a nonagenarian is befuddled by this strange new quasi-religious ritual, so rapidly has the practice taken hold. This didn’t stop the National MS Society from turning its back on Itkoff, a volunteer whose commitment to the charity dated back for six decades. For committing heresy against the Holy Creed of Diversity, Equity and Inclusion, Itkoff was immediately sacrificed. The statement issued by the National MS Society claimed that her query about pronouns was “viewed as not aligning with our policy of inclusion”.
Declaring pronouns makes little sense in any case, given that they are used in place of a name when talking about someone, not to someone. And besides, human beings are perfectly capable of determining someone’s sex without being told, usually instantaneously. Of course, according to activists, all of this is irrelevant. We are assured that sex has been superseded by “gender identity”, that mysterious sense of self that few of us believe even exists. It would be like being told to announce the colour of your aura every time you began a conversation.
Like the vast majority of the population, I use pronouns to denote the biological sex of the person to whom I’m referring. And I certainly would not comply if commanded to declare my own due to my innate aversion to any form of compelled speech. The lessons of history are clear: when those in authority begin to demand the use of certain phrases, they have taken the first step on the pathway to tyranny. I do not wish to see a future in which we are forced to stand in lockstep and chant the approved slogans of the ruling class.
Of course, the declaration of pronouns is far removed from any such scenario, but the principle to me is sacrosanct. I will not be told what to say by anyone, least of all those who claim to know what is best for the good of society. Authoritarians have always couched their demands in faux-benevolence, and we have seen how gender ideologues have a particular tendency to viciousness and bullying. “Be kind… or else” is not a maxim to which I am willing to capitulate.
To ask for pronouns in the workplace is the equivalent of suggesting that employees pledge fealty to a deity they do not worship. It is a kind of test, a way to ensure that the tenets of Critical Social Justice – otherwise known as “wokeness” – are being observed. Spinoza argued that for any man to “be compelled to speak only according to the dictates of the supreme power” is a violation of his “indefeasible natural right” to be “the master of his own thoughts”. Once you agree to make statements in favour of a belief-system you do not hold, you are surrendering your agency to those who will exploit it.
While the declaration of pronouns remains a purely voluntary matter, it is fair to say that no-one’s free speech is being violated. But the consequences for non-compliance in the workplace are becoming increasingly severe. Members of staff are passed over for promotion, they are smeared as unreconstructed bigots and “transphobes”, and eventually shunned and isolated. I have written before about friends of mine in the acting profession who feel uncomfortable in stating pronouns at the beginning of rehearsals, but know that they are unlikely to be recast if they refuse. This may not be compulsion, but it is coercion.
We see the same phenomenon on social media, where trans rights activists routinely denounce and defame those guilty of the crime of “misgendering”. They report users in the hope of seeing them banned, contact employers and claim to feel “unsafe”, and even occasionally call the police. This is the essence of cancel culture. They are, of course, free to criticise, even in a robust and rude manner. But to seek to destroy someone’s livelihood for their choice of language is fundamentally authoritarian.
In the same vein, we have seen a handful of gender-critical feminists attacking people online for choosing to use “preferred pronouns” in certain cases. Again, the criticism is valid, but once it strays into the realm of libel, misrepresentation and character assassination, these critics are merely borrowing from the playbook of trans activists. In the tenor of some of these online free-for-alls, it has been difficult to tell one faction from the other.
When it comes to the declaration of pronouns, I have often wondered how long it would take before requests transformed into demands. The sacking of Fran Itkoff by the National Multiple Sclerosis Society has the ring of inevitability about it. Many of us saw this coming. This is why we need to be vigilant against anyone who attempts to compel the speech of others, for whatever reason, and in whatever context. If we tolerate this inchmeal erosion of our liberties, we will doubtless live to regret it.
--
If you haven't been following it, Fran Itkoff is a 90 year old woman who volunteered for the MS Society for sixty years after her husband had MS (multiple sclerosis). She didn't understand what all this talk about pronouns was about, asked, and was then told her volunteering services were no longer required.
Some of you may well go, "ew, LibsOfTikTok, ew, ew." Okay, but hear me out: shut up and read the screenshots. They tell the story.

youtube
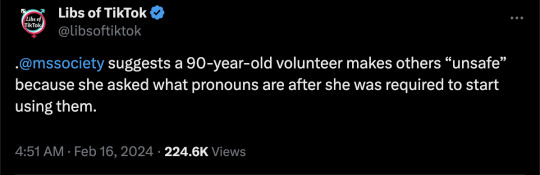
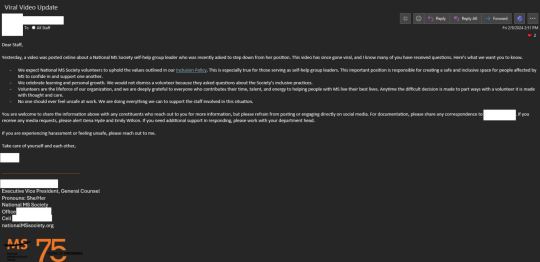
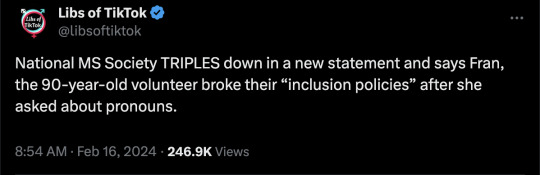

Kali Kumor is the stupid little girl who removed a woman who had dedicated her life, and worked longer than this vacuous apparatchik has been alive, to helping others.
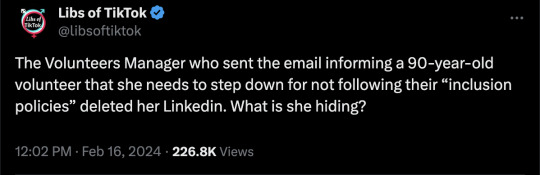
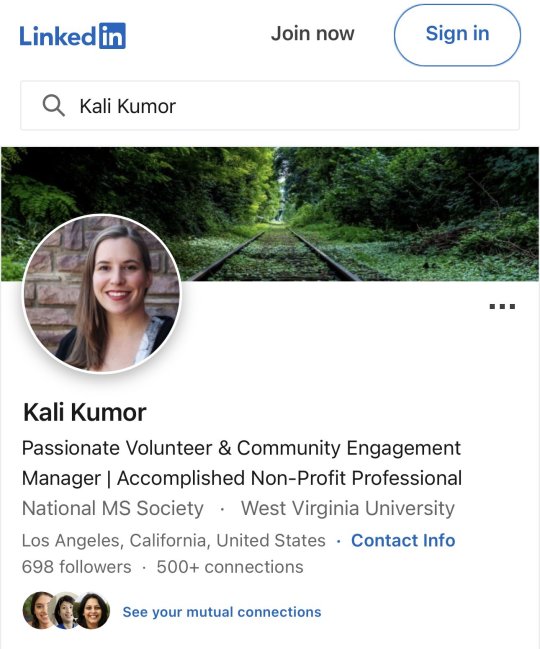

One supposes that all the MS in the world has been cured, given how eager they are to tell dedicated volunteers that they're no longer needed.
--
A few years ago, there was a fuss about atheists being turned away from volunteering activities.
This is the same principle: adherence to their dogmatic ideology supersedes what is supposed to be their organization's mission and purpose: their "telos". This is why you cannot have two "teloi." One will always win over the other.
This is what I mean by ideological capture. The telos of the MS Society is no longer services and support for those with MS, it's "Diversity, Equity and Inclusion." That's their number one objective. And that means pronoun-policing and excommunicating those who aren't part of the cult.
It would seem both humorous, being so petty and stupid, and sad, given Fran's long service to the organization, but as Andrew Doyle points out, it's more insidious than that. It's compelled speech. It's about punishing those who will decline to be part of - or even simply don't understand - the fundamentalist, puritan religious ideology these fanatics have adopted and imbued throughout the organization.
Just as you must testify to Jesus as your lord and savior in order to volunteer at a soup kitchen or to raise money for cancer, they will demand you adhere to the belief in gender thetans in mismatched meat prisons in order to volunteer for the MS Society. In the name of "Inclusion,"
As Fran mentions, the MS Society has always been inclusive, but what she doesn't understand is that it's now Inclusive™, a brand name which doesn't mean including as many people as possible but including as many members of their cult as possible.
They're not looking for behaviors - e.g. respect, tolerance, etc - they're looking for beliefs. Enforcing a particular ideological belief system. They don't care that you might be an atheist who subscribes to secular humanism, or you could be a Xian who believes we're all children of God, they want to make you believe what they believe.
Resist it. They'll try to act like you're just being unreasonable for a small accommodation, but they know that it's how they get you to start complying with their demands. Like Islam, it's one little thing at a time. Don't draw pictures of Muhammad, that's not a big ask is it? Then it's respecting the Quran, then it's not blaspheming Muhammad or Allah, and so on.
#Andrew Doyle#Fran Itkoff#Kali Kumor#MS Society#gender identity ideology#gender ideology#queer theory#pronoun culture#pronouns in bio#pronouns#volunteering#compelled speech#ideological conformity#religion is a mental illness
28 notes
·
View notes
Text
Seeing as a lot more compelling evidence than the evidence used in the original theory has come to light, I’ve decided to redo the manifestation theory. So here we go and far warning for any potential plot twist reveals.
Overview
The manifestation theory is a theory of mine that the show operates as one huge D&D game and that a lot of the settings that we see such as characters, locations, and events aren’t real, at least not in the traditional sense. They exist in the real world, but they originated from a child’s mind. Mike’s mind.
First let’s see why Mike would’ve randomly started manifesting monsters. The simple answer is that he wouldn’t not without a reason and certainly not on purpose. What I think Mike did is that he tried to turn back time and succeeded, but with the consequence of having expended the reach of his mind a little too far and releasing beings from the mind. Mike is the DM after all so if anyone might be pulling the strings it’s him.
Let’s provide some evidence that the events aren’t actually happening first.





Do I have your attention yet? Good. What I think happened is that Will died. He was murdered in another timeline and after around a year of learning to use his powers Mike turned back the clock to the last time, he saw Will alive, the initial D&D game. This would’ve been something of a save point and is why so many important things show up in relations to that game.
At 8:15, Karen stops the game. Will dies after rolling a seven, Mike wanted twenty more minutes. The works. Will leaves and is kidnapped into the upside down. If Mike is the writer here, then Will is acting as the main character. The game is built around protecting Will except it’s hitting a point beyond Mike’s control.
The barrier between Mike’s mind and reality is weak and it keeps getting weaker the more time passes. The involvement of time travel explains Mr. Clarke bringing up that multiple world’s interpretation and the references to curiosity voyages.


Mike is highly suspicious in the way that he seems to be constantly framed over dialogue suggesting a connection to other worlds and the “Vale of Shadows”, which is what the kids were originally calling the upside-down.


There is also the way Mike sometimes knows stuff and is completely unable to explain how.



So, none of this is real. We’re in a kid’s game and Mike is the DM. This I think is the reason that the three playlist left belong to Will, Billy – literally the other William, and Mike. Mike’s playlist description is also referring to a 5-hour (season?) D&D session despite the fact that none of Mike’s campaigns are that short nor does his playlist actually last for that long.
So, Mike dies = the upside down dies or something to that effect. The Hawkins National Lab isn’t real, but wasn’t one of their main goal to discover time travel?

Weren’t they pushing so hard that they released monsters onto the world. No one from the lab would’ve seen Will prior to his kidnapping to the upside-down, at least not in enough detail to recreate it quite that perfectly, but Mike saw him. They spoke, Mike was acting weird, Will told Mike that the Demogorgon got him. Why do I think the lab isn’t real well…
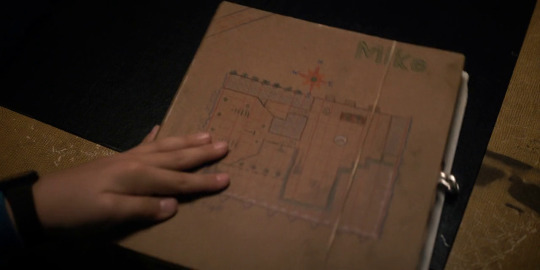
This is the very first DM book that Mike has. We get a nice shot of it right before Dustin starts to read about the “Vale of Shadows”. As he’s reading, we see Hopper traveling through the interior of HNL. This is also Mike’s first campaign book, so it makes an appearance twice, which is interesting simply because the DM books don’t seem to appear twice, but especially not in the same season.
When Mike narrates from it is connected with the guy in the lab running from a Demogorgon. It’s also interesting to note that the book is the only DM book that we can clearly see has the design of a building on it. So a building design connected with the interior of the lab. It also carries a small drawing of the cardinal directions right above the building and considering that later Dustin is using a compass to lead them to the lab that’s pretty interesting.
This and the fact that Mike’s D&D campaigns take place in the basement and most gates only open in a basement of some sorts. For example, the HNL basement and the starcourt basement, but also the Mindflayer’s main operation being in the basement of steelworks. Basements, basements everywhere.
Why do I think that Mike might’ve turned back time first?



This and the way that Mike is constantly associated with running out of time. With that I’ll leave you to it, but if you decide to watch the show with this interpretation fair warning it gets trippy.
#slay#manifestation theory but part 2 and make it compelling#manifesation theory#byler#<- for attention#jason's speech is insane too tbh
133 notes
·
View notes
Text
happy aro week to everyone who celebrates. give your local aro a hundred dollars to compensate for their suffering (me).
#i've been thinking a lot about aromaticism lately ... ! perfect time for it to coincide with aro week.#➤ ooc. ┊ she’s nauseous,she’s hysterical,and she’s exhausted.#i've been seeing quite a lot of posts lately that .. hm. speak on romance in fiction / the habit of shipping / writing romance and sex#from a perspective of 'oh; think of the aros!' 'we hate shipping-focused fandom!'#well one thing about me love to make characters have insane sex. i do not follow these practices in my own life.#i tend to find real-life discussions of sex and romance generally unpleasant; but this is something you sort of just have to deal with.#but i love shipping. air that i breathe. i love to read romance. and full-m smut. love to write or draw them kissing.#i also like when characters murder each other ; or talk to ghosts ; or drive without seatbelts ; i should note i also#don't practice these things or in most cases condone them!#to me – this is just another aspect of fiction that is separate to my real-life experience. it's no more inherently#positive or negative than anything else characters do.#i don't find love to be something that is fundamental to the human condition but it is a big; broad human story. and a compelling one!#anyways. that's my speech. thanks for the on-sale chocolate allos.
14 notes
·
View notes
Text
A Victory Over Compelled Speech and Gender Identity Ideology - Respecting Female Boundaries
A Victory Over Compelled Speech and Gender Identity Ideology – Respecting Female Boundaries
This was the result of a male student ‘self-id’ing into a female sport locker room. The female child that complained about having a male perv on them and her Father were both subject to censure and school disciplinary procedures, including attempting to compel their speech and actions. Thankfully that bullshit was stopped dead in its tracks.
Blake’s father, Travis, got involved when he responded…
View On WordPress
0 notes