#cross site scripting
Explore tagged Tumblr posts
Text
The Hacker's Guidebook:
Aspiring hackers! I’ve created a guide covering core cybersecurity concepts new hackers should master before tools. I break down networking, OS internals, & hacking tactics. Recognize hacking as lifelong journey—arm yourself with the basics!
Core Concepts for Budding Cybersecurity Enthusiasts The Building Blocks of Ethical Hacking So you want to become an ethical hacker and enter the exciting world of cybersecurity. That’s awesome! However, before you dive headfirst into firing up Kali Linux and hacking everything in sight, it’s vital to build up your foundational knowledge across several InfoSec domains. Mastering the fundamentals…

View On WordPress
#attacking tools#basics of hacking#cross site scripting#Cyber Threat Defense#cybersec#cybersecurity learning#cybersecurity professional#Ethical Hacking#fundamentals#hacking basics#hacking for beginners#hacking guide#hacking networks#hacking web#how to hack#infosec#learn hacking#learn to hack#linux#malware basics#malware for hacking#metasploit#netsec#network hacking#nmap#operating systems#Pentesting#phishing#phishing attacks#Red Team
35 notes
·
View notes
Text
Navigating the Risks of JavaScript in Web Development
JavaScript is the linchpin of interactive web experiences, fueling everything from form validation to video streaming. While JavaScript enriches user engagement, it also raises significant security considerations. This post examines JavaScript's potential for misuse and the best practices to mitigate these risks.
The Dual Facets of JavaScript
JavaScript’s ability to execute on the client side is a bedrock feature of dynamic web pages, empowering developers to script complex features and responsive user interfaces. Unfortunately, the same capabilities that streamline user experience can also be exploited for malicious purposes.
Potential Misuse Cases
Malicious actors can leverage JavaScript for a range of harmful activities, including:
Data Theft: Scripts can covertly transmit personal data to unauthorized parties.
Session Hijacking: Exploiting cookies or session tokens to impersonate users.
Malware Distribution: Executing scripts that install harmful software on users' devices.
Understanding misuse scenarios is the first step in fortifying web applications against such threats.
Notable Attack Vectors: XSS and CSRF
The two most prevalent JavaScript-based threats are Cross-Site Scripting (XSS) and Cross-Site Request Forgery (CSRF). Each exploit different aspects of web application interaction with the user.
Cross-Site Scripting (XSS)
XSS attacks involve inserting malicious scripts into otherwise benign web pages. These scripts activate when unsuspecting users interact with the web pages, leading to unauthorized actions or data exposure.
Defense Strategy:
Input Encoding: Systematically encode user-generated content before displaying it on the web, effectively defanging embedded scripts.
Use of CSP: Employ a Content Security Policy to specify legitimate sources for executable scripts and resources.
Cross-Site Request Forgery (CSRF)
In CSRF attacks, attackers con the victim's browser into performing unintended actions on a site where the victim is authenticated, ranging from changing a user profile to initiating financial transactions.
Defense Strategy:
Anti-CSRF Tokens: Deploy one-time tokens that must accompany each form submission, ensuring requests originate from the site's own pages.
Cookie Attributes: Set 'SameSite' attributes on cookies to limit their flow to requests originating from the site that set them.
Building Defenses into JavaScript
Deploying defensive coding practices is essential to protect against the weaponization of JavaScript. Here are tactics developers can leverage:
Input Validation and Sanitization
Vigilant validation and sanitization of user input are fundamental:
// Validate acceptable characters (e.g., alphanumeric for a username) function isValidUsername(username) { return /^[a-zA-Z0-9]+$/.test(username); }
Implementing a Content Security Policy (CSP)
CSP can significantly reduce the success rate of XSS attacks:
Content-Security-Policy: default-src 'self'; script-src 'self' https://trusted.cdn.com;
Managing Cookie Security
Correctly setting cookie attributes can prevent CSRF:
document.cookie = "sessionToken=xyz123; Secure; HttpOnly; SameSite=Strict";
Enlisting Users in Their Defense
While technical defenses are critical, empowering users to protect themselves can add another layer of security:
Educate Users: Regularly inform users on the importance of browser updates, installing security extensions, and recognizing phishing attempts.
Enable Security Features: Encourage users to install Firefox and use privacy-focused Browser extensions like uBlock Origin.
Conclusion
JavaScript's agility is a double-edged sword; its seamless integration into web pages can also serve nefarious purposes. Recognizing the potential for misuse compels us to employ rigorous defensive measures. Whether through stringent input handling, careful session management, or leveraging robust browser security features, a proactive approach to JavaScript security is the greatest defense against its weaponization. As technologies advance and threats evolve, so too must our strategies for maintaining web security and user trust.
#ko-fi#kofi#geeknik#nostr#art#blog#writing#twitter#xss#csrf#javascript#web development#dev#coding#programming#csp#content security policy#cross site scripting#information security#security#secure coding#infosec
1 note
·
View note
Text
Btw if you're looking for a cool sounding computer-themed name for your character you can call them Ajax. It's an acronym that stands for Asynchronous JavaScript and XML (Extensible Markup Language) and in extremely simple terms is a method for getting/handling incoming data in a web application. I just think it would be really neat as a character name
#yes programmers put acronyms inside of acronyms..... yes i hate it as much as you do.... no i cant do anything about it#they also seem to really like using the letter X as shown by XML and XSS (cross site scripting) and probably some others im forgetting#though with the ungodly amount of acronyms being thrown around in this profession i really cant blame them for wanting something unique#rambling#anyway sometimes programmers have really cool acronyms and sometimes they have CRUD. cant win em all
6 notes
·
View notes
Text
Mastering Content Security Policy in ASP.NET

Dive into our comprehensive guide on Content Security Policy (CSP) in ASP.NET to enhance your web application's security. Learn how CSP mitigates risks like cross-site scripting (XSS) and data injection attacks. This resource covers essential concepts, step-by-step instructions for setting up CSP headers, and best practices to follow. With practical examples and troubleshooting tips, both beginners and seasoned developers can effectively secure their ASP.NET applications. Empower your projects with robust security measures today!
0 notes
Text
Mtskheta, Jvari Monastery, Svetistkhoveli Church Georgia
Mtskheta Orthodox Church The daytrip to Mtskheta, Jvari Monastery, and Svetistkhoveli Cathedral was very educational. The historical area in central-eastern Georgia is wrapped in a peaceful environment of lush greenery and expansive mountain vistas. The stunning area is located about 12 miles north of Tbilisi at the confluence of the Mtkvari and Aragvi Rivers. Mtskheta is home to UNESCO World…

View On WordPress
#"Mtskheta Ancient Capital of Kartli East Georgian Kingdom 3rd Century BC to 5th Century AD#Aragvi River#Asomtavruli Script#Catholicos Patriarch Melkisedec#Caucasus Region#Christ&039;s Robe Svetistkhoveli Cathedral#Gates of the Katholikos Melchizedek#Georgian Christianity#Georgian Hagiography#Georgian Kingdom of Kartli#Georgian Orthodox and Apostolic Church#Golgotha#Great Silk Road#Holy Cross Monastery of Jvari#Javari Church of the Holy Cross#Jvari Monastery#Medieval Georgia#Mirian III First Christian King of Georgia#Mtkvari River#Mtskheta#Mtskheta Jew Elioz#Mtskheta Old Capital City of Georgia#Samtavro Monastery#St. Nino#Stepanoz I King of Iberia#Svetistkhoveli Cathedral#Svetitskhoveli Cathedral#Tetraconch#UNESCO World Heritage Sites
0 notes
Text
1 note
·
View note
Text
StableHost Review: Is Their Clustered Hosting Really Worth a Try?
New Post has been published on https://thedigitalinsider.com/stablehost-review-is-their-clustered-hosting-really-worth-a-try/
StableHost Review: Is Their Clustered Hosting Really Worth a Try?
As a digital marketer who has helped dozens of business owners set up their websites, my goal is always to find a reliable web host that offers dependable, performance-driven features. When I first came across StableHost, I hesitated since they’re less popular than GoDaddy, BlueHost, and other A-list providers. But after trying out their hosting services, I can boldly say StableHost is worth a try.
In this StableHost review, I shared everything – well, almost – you need to know about this web host, including its performance, customer support, pricing plans, and features.
Before we do, let’s cover some basics.
StableHost Review
StableHost isn’t the youngest kid on the block. The company was founded in 2009 and has since grown into one of the best hosting providers in the industry.
One thing you’ll love about StableHost is their customer-centricity. Despite its large customer base (housing over 50,000 domains), this host is led and managed by just 15 employees. According to them, having a tight-knit team helps them reduce operational costs and channel revenue into providing premium hosting solutions for their users. Awesome, right?
If you’re looking for all-inclusive web hosting, StableHost is an excellent choice. They offer domain registration services and even have a proprietary site builder (BaseKit) that allows you to build your websites in one click.
BaseKit has over 100 customizable templates to choose from, including a drag-and-drop editor that allows you to alter the design to your preferences. The best part about this site builder is that it is included in all StableHost’s plans at no extra cost.
StableHost provides a variety of hosting solutions, including shared, reseller, VPS, dedicated, and WordPress hosting. They are rated excellent on Trustpilot for garnering 4.9-star reviews from over 2000 users:
Pros and Cons
They offer VPS, WordPress, dedicated and reseller hosting
24/7/365 customer support
Their user interface has a steep learning curve, perfect for beginners or users with no-code skills
They offer 45-day money-back guarantee
They use cluttered hosting for faster performance
They built a proprietary website builder – BaseKit
Unmetered bandwidth
No proprietary control panel
StableHost Rating – my personal take
Currently, over 2 billion web pages are competing for the ‘best web hosting provider’ keyword. This includes web hosting providers and other third-party sites such as review platforms.
How do you sift through this list to find the right hosting provider for your website? To simplify this, I created a personal rating system that grades each provider based on six vital metrics: Performance, features, customer support, pricing plans, and user intuitiveness. This helps me to fairly evaluate each host’s capabilities and overall performance.
For effectiveness, I used a 5-point grading scale and provided reasons for each score given.
Quality My rating Why I gave this score Features and specs 4.4 Unlimited storage, unmetered bandwidth, DDoS protection, SSL certificates, and free site builder … StableHost provides several functionalities for a seamless hosting experience. However, I gave them this score because I believe they can provide more enterprise features. Pricing 4.5 StableHost is one of the most affordable web hosts in the market! Starting at $0.9, users can access basic tools to kickstart their digital journey. I gave them this score because their pricing packages are not so detailed. Performance stats 4.4 StableHost boasts a good performance with 100% uptime and 1.8s loading time. I gave them this score because I believe the overall performance can be improved. Ease of use 4.5 You’ll love StableHost’s user interface. It’s sleek, modern, and easy to use. They also use the traditional control panel – cPanel – to lessen the learning curve for their users. Awesome! But I gave them this score because other providers have more advanced UI. Customer support guarantee 4.5 StableHost offers four levels of customer support – phone, live chat, knowledge base, and emails, which is fantastic. Their response time is also satisfactory. I gave them this score because they have a quick response time compared to other popular providers.
StableHost Prices & Plans
Like every other provider, StableHost offers shared, VPS, reseller, dedicated, and WordPress hosting solutions.
Each plan comes with unlimited bandwidth, a free site builder, and a 45-day money-back guarantee, which is enough time to decide if they’re worth a try. Let’s explore what each plan entails.
StableHost’s Shared Hosting Plans
Mini
Space offered – 5GB SSD
Bandwidth – 500GB bandwidth
Number of websites – 1 website allowed
Price – $0.9/month
Starter
Space offered – Unlimited
Bandwidth – Unmetered bandwidth
Number of websites – 1 website allowed
Price – $4.30/month
Pro
Space offered – Unlimited
Bandwidth – Unmetered bandwidth
Number of websites – Unlimited number of websites allowed
Price – $4.25/month
Platinum
Space offered – Unlimited
Bandwidth – Unmetered bandwidth
Number of websites – Unlimited number of websites allowed
Price – $27.99/month
I recommend the StableHost pro plan, especially if you plan on building/managing a site with high traffic. At $4.25/month, you get unlimited disk space, bandwidth, email accounts, and databases. You can also access a free website builder, SSL let’s encrypt certificate, 99.9 SLA, and more.
Who is this for?
StableHost shared hosting plans are perfect for anyone with minimal hosting needs. Whether you’re just starting your website or looking to host several sites simultaneously, you’ll find a package tailored to your needs. However, if you have high-traffic sites, check out the next hosting plan.
StableHost’s dedicated hosting Prices & Plans
Professional
Space offered – 40 GB SSD Storage
Bandwidth – 2TB Bandwidth
Features – Intel Pentium G3450 3.4GHz 2C, RAID 0 or 1, Hard drives 2 * 300 GB SAS
Price – $145/month billed annually
Premium
Space offered – 40 GB SSD Storage
Bandwidth – 3TB Bandwidth
Features – 2 CPU cores, SSH and root access, Intel Xeon E3 – 1240L v3 2.0GHz 4C, RAID 0 or 1, Hard drives 2 * 300 GB SAS
Price – $165/month billed annually
Ultimate
Space offered – 100 GB SSD Storage
Bandwidth – 4TB Bandwidth
Features – 4 CPU cores, SSH and root access, Intel Xeon E5-2603 v3 1.6GHz 6C, hard drives 2 * 300 GB SAS, RAID 0 or 1
Price – $245/month billed annually
I recommend StableHost’s Ultimate dedicated hosting plan, considering it offers more robust features.
The Intel Xeon processor offers high performance and multi-core capabilities, ensuring the servers can handle demanding workloads. This is perfect if you run high-traffic websites or heavy applications.
The SAS drives are equally designed for enterprise-level reliability so the server remains operational and accessible during peak periods.
Who’s this for?
The StableHost’s dedicated hosting plan is a perfect choice if you need more performance-based features beyond what’s offered on shared hosting. The Intel Xeon processors, CPU cores, and RAID O or 1 keep your sites at blazing performance, provide faster data access, and minimize the risk of data loss due to disk failure.
StableHost’s VPS hosting Prices & Plans
VZ 1GB
Space offered – 40 GB SSD Storage
Bandwidth – 2TB Bandwidth
Features – 1 CPU core, SSH and root access
Price – $61.95/month billed annually
VZ 2GB
Space offered – 40 GB SSD Storage
Bandwidth – 2TB Bandwidth
Features – 2 CPU cores, SSH and root access
Price – $61.95/month billed annually
VZ 4GB
Space offered – 100 GB SSD Storage
Bandwidth – 4TB Bandwidth
Features – 4 CPU cores, SSH and root access
Price – $61.95/month billed annually
Who is this for?
Try out StableHost’s VPS plans to launch or run your website applications on enterprise-level hardware. Whether you manage a video streaming platform, gaming apps, or large eCommerce sites, the servers are built to handle high traffic volume and complex workloads easily. This ensures that the servers experience minimal downtime and optimal performance. If you also need to install your operating system, StableHost offers free access to KVM virtual machines.
StableHost’s Reseller hosting Prices & Plans
Basic
Space offered – 20 GB SSD Storage
Bandwidth – Unmetered bandwidth
Features – Allows to host up to 10 clients, LiteSpeed PHP Caching, unlimited FTP accounts, SSL Let’s Encrypt Certificates, etc.
Price – $9.12/month billed annually
Pro
Space offered – 40 GB SSD Storage
Bandwidth – Unmetered bandwidth
Features – Allows to host up to 50 clients, unlimited email accounts, advanced analytics, unlimited MySQL databases, etc.
Price – $18.29/month billed annually
Plus
Space offered – 60 GB SSD Storage
Bandwidth – Unmetered Bandwidth
Features – Allows to host up to 100 clients, unlimited email accounts, Softaculous, cPanel, etc.
Price – $27.45/month billed annually
Who is this for?
StableHost’s reseller hosting plans are a good choice for web developers, digital marketers, web hosting entrepreneurs, and IT professionals who manage multiple websites simultaneously.
They offer a white labeling option that allows you to customize the hosting solutions to your brand. On each plan, you also enjoy unmetered bandwidth, daily automatic backups, cPanel, access to LiteSpeed PHP caching, and more.
StableHost’s WordPress hosting Prices & Plans
Starter
Bandwidth – Unmetered bandwidth
Features – LiteSpeed PHP Caching, enterprise grade SSD drives, dual CPUs, unlimited MySQL databases, SSL Let’s Encrypt certificates
Price – $4.30/month billed annually
Pro
Bandwidth – Unmetered bandwidth
Features – One-click Softaculous installer, LiteSpeed PHP caching, unlimited email accounts, Site.Pro web builder, etc.
Price – $4.25/month billed annually
Platinum
Bandwidth – Unmetered Bandwidth
Features – Enterprise grade SSD drives, RISoft daily backups, advanced analytics, LiteSpeed PHP caching, etc.
Price – $27.99/month billed annually
Who’s this for?
StableHost’s WordPress plans are for WordPress owners even though they do not provide detailed features for each plan. They did cite that all plans have automatic daily backups, cPanel, SSH access (at an extra fee), unlimited email accounts, free site builder, etc.
StableHost’s Features
These are some of the functionalities you’ll enjoy if you decide to stick to this web host:
Free site builder
Enterprise-grade SSD storage
OpenLiteSpeed caching
cPanel
Free email tools
Softaculous one-click installer
24/7/365 customer support
To be candid, I didn’t find many top-of-the-line features with StableHost compared to other hosting providers such as BlueHost or Hostinger.
However, their clustered hosting features give them a distinct advantage. Let me explain.
StableHost uses a clustered technology that regularly monitors the health of the SSD drives. Since these drives are in sync, every file stored in the drive is replicated across multiple drives to minimize redundancy.
In addition, the technology also monitors your drives for issues such as high traffic volume or hardware malfunction. But if this happens, you don’t need to worry about a performance outage as the system automatically switches you to another drive/node. This way, your website remains accessible and functional to users at all times.
StableHost’s Performance Tests
The true test of any web host is its reliability in terms of performance, speed and uptime. These metrics give you real-time insights into the effectiveness of the host’s functionalities in keeping your site accessible, even during peak periods.
The three top metrics are:
Speed: Denoted as the time to the first byte (TTFB), it measures the responsiveness of a web server. It also tracks the time the user receives the response from the server.
A good TTFB should be 300ms or less. Although Google didn’t state explicitly that it affects rankings, I believe it does (indirectly) because of its influence on the Google Core Web Vitals.
Uptime: measures the reliability of the web server, that is, the amount of time it is operational and available to users. A good uptime should be around 99.9% – 100%.
Lastly…
The website’s loading time: this measures the time it takes for a web page to display fully on the user’s browser. It’s one of Google’s core ranking factors because it has a direct influence on user experience. The average website loading time should be 3s or less.
StableHost promises a 99.9% uptime guarantee, fast load time, and satisfactory server reliability. But how true is this?
I tested their performance using a website hosted on their servers, and here are the results.
First, I used GTMetrix to test the server response time and overall performance.
The TTFB was 300 ms, which is quite quick. While this is a good score, I believe it should be better since other hosts have lesser TTFB.
I validated their uptime in the last 30 days using Uptime Robot:
The uptime showed 100% in the last 30 days, proving that their web servers are reliable. Excellent!
Keep in mind that the location of your web host data center can impact the performance of your website. I’ll share more insights on this later.
StableHost’s Customer Support
StableHost boasts reliable customer support. According to them, they only hire talents passionate about web hosting. Let’s prove that.
Phone
Want a quick response? You can reach any of StableHost’s technicians by phone. This line is available for all regions but incurs charges for those outside the US:
Emails:
Whether you have sales-related, payment, or technical issues, StableHost allows you to get professional and specialized support through their email support system.
For sales inquiries, content them via [email protected]. For technical assistance, use [email protected]. This ensures you receive expert help tailored to your needs.
Live Chat
StableHost’s live chat support is readily available on the bottom-left of their website for quick fixes. I decided to try it out since they claim to respond within 10 minutes.
I sent a message, and a bot responded giving me a countdown till an agent attended to me. And three minutes later, a human responded. Cool!
KnowledgeBase
Do you prefer quick, accessible support? StableHost has a vast library of resources that features several articles on diverse topics:
The articles were authored by the StableHost team, so you can be confident of getting an expert’s view on any related issue.
Mailing Address
Who uses a mailing address in this modern age? StableHost includes their company address for post mails.
StableHost’s Security Features
I love how StableHost prioritizes the safety of their domains hosted on their platform. Although their security features aren’t the best in the industry, you still have access to the basic tools that protect your sites for the bad guys.
Whichever plan you opt for, you get SSL Let’s encrypt certificates, spam filtering, and DDoS protection.
You’ll also get Imunify 360, a multilayer security system, which is the major layer of protection on shared servers. This system helps detect and stop website attacks before infiltrating the web server.
If you want a more stringent security system, purchase any of StableHost’s security audit plans.
The system was built in-house and is used to scan servers for any attacks, even to the smallest point. This includes port scanning and intrusion testing, cross-site scripting vulnerability testing, SQL injection scanning, etc.
The best part is that they don’t stop at the audits. The StableHost security audit system also assists in remedying the issues affecting your server security.
StableHost’s website builder
You might be used to WordPress, Wix, Joomla, and other popular website builders. But StableHost did something unique – creating their own site builder – BaseKit!
BaseKit has over 100 customizable templates (responsive, too), a drag-and-drop editor for beginners, advanced analytics features, and more. It comes at no extra cost; you can access it after purchasing any of StableHost’s plans.
However, if you prefer WordPress, Drupal, Joomla, or other popular CMSs (content management systems), you can download it from Softaculous via cPanel.
User-Friendliness – Ease of use
One thing I admire about StableHost is that affordability isn’t an excuse to build a subpar interface.
The StableHost UI is user-friendly, and requires almost no technical knowledge. In fact, if you encounter any issues, they have a ton of how-to articles on their resource page to guide you.
Registering an account with StableHost
To register an account with StableHost, you have to purchase one of their hosting plans.
Step 1:
Navigate to the menu bar to find the hosting plan that best fits your needs:
Step 2:
Once you’ve found the package that fits your needs, click ‘Order Now.’ You’ll be redirected to a new page where you enter your domain.
If you have an existing domain or want to transfer your domain, just click any of the options listed and follow the prompts.
Tip: If you don’t have a domain name, StableHost also offers domain registration services so you can find and register the perfect name for your business:
Step 3:
You’ll see the product review page, where you will be required to choose your payment option. I love that StableHost offers a flexible means of payment – credit card, PayPal, AMEX, Stripe, MasterCard and Visa.
Step 4:
Once you choose your payment method, click ‘Continue to CheckOut.’ This is the second stage.
In the third stage, you’ll be asked to create an account with StableHost. Fill all the required information and click ‘Create Account:’
Step 5:
Next, you’ll receive a congratulatory message that your order has been received for review:
StableHost’s intuitive Control Panel
StableHost uses the default cPanel as its control panel. Here, you’ll find everything you need to manage your hosting environment efficiently. Although the user interface isn’t modern, you can easily find the tools and features conveniently.
Overall, I found it easy to use and navigate. However, I believe it can be upgraded to meet the modern consumer standards.
Installing WordPress on StableHost
Installing WordPress on StableHost is a breeze!
To do this, log into cPanel from your account.
Next, search for the ‘Softaculous Apps Installer’ and click ‘WordPress.’
You’ll be directed to a new page to install WordPress in one click. Then, hit the ‘Install >> Quick Install’ button.
Then, choose the domain name you want for your WordPress account and ‘wp’ for the directory field:
Also, add your preferred user name, password, and email address to receive the installation details.
Lastly, click the ‘Install” button and you’re all set!
You’ll get a congratulatory email alongside your installation details:
Server footprint and CDN
Before choosing any hosting provider, you need to consider the server footprint and content delivery network (CDN).
The server footprint is the geographical spread of a web host’s servers. The wider the server footprint, the faster the loading time, and vice versa.
Also, proximity matters. The closer a web server is to you (or your audience), the faster the speed and vice versa.
Using a CDN helps to reduce the distance between the server and the users, therefore making web pages load faster and improving the overall user experience of your website.
StableHost has data centers in different regions across the world – the US, Netherlands, Sweden, Singapore, Spain and Germany. They also use an advanced content caching technology and a globally distributed CDN to improve the performance of sites hosted on their platform.
Conclusion: Do We Recommend StableHost?
Yes!
I was impressed by StableHost’s hosting solutions, especially their commitment to improving customer experience. One thing that stood out to me is how they struck a balance between reliability and affordability. Also, their support team is good, but I think it needs to be improved.
Overall, I recommend StableHost to anyone looking for a holistic hosting platform. It offers a platform with enterprise grade functionalities to start your digital journey, grow and scale accordingly.
Visit StableHost →
FAQs
Is StableHost legit?
Yes, StableHost is a credible web host. They are well known for their affordable and reliable web hosting services. Their hosting services feature many attractive functionalities, including unlimited bandwidth, a 99.9% uptime guarantee, a web application firewall, DDoS protection for security, and more.
What is the money back guarantee on StableHost?
StableHost offers a 45-day money-back guarantee, which is enough time to evaluate the host’s services to see if they fit your website well.
Which web hosting performs best: Hostinger or StableHost?
Personally, there’s no perfect answer to this. Hostinger and StableHost are reliable and credible providers in the hosting industry, with unique features and specs. Let’s consider some use cases:
Affordability: StableHost trumps Hostinger by a few dollars if you’re considering costs. The Hostinger shared hosting plan starts at $2.99/month. StableHost offers the same deal at $0.90/month!
Speed: In this case, I’ll go with Hostinger. This is because they offer cloud hosting solutions, free CDN, servers in over 6 locations worldwide, LiteSpeed web server technology, and a 99.99% uptime reliability.
Security: I’ll also choose Hostinger over StableHost. Why? They offer advanced DDoS protection, web application firewall, cloudflare protected name servers, secure access manager, and more.
Customer support: I believe StableHost shines, thanks to its 24/7/365 customer support availability.
#000#Accounts#agent#amp#Analytics#applications#apps#Articles#audit#backups#billion#bot#browser#Building#Business#Byte#cdn#certificates#channel#Cloud#Cloud hosting#cloudflare#code#content#content management systems#control panel#cpu#credit card#cross-site scripting#customer experience
0 notes
Text
Securing Your Website: Best Practices for Web Developers
As the digital landscape continues to evolve, website security has become a paramount concern for businesses and individuals alike. With cyber threats becoming increasingly sophisticated, it is crucial for web developers to adopt robust security measures to safeguard their websites and the sensitive data they handle. In this article, we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potential threats.
Introduction
In today's interconnected world, websites serve as the digital storefront for businesses, making them vulnerable targets for cyber attacks. From data breaches to malware infections, the consequences of a security breach can be severe, ranging from financial loss to damage to reputation. Therefore, prioritizing website security is essential for maintaining the trust and confidence of users.
Understanding Website Security
Before diving into best practices, it's crucial to understand the importance of website security and the common threats faced by websites. Website security encompasses measures taken to protect websites from cyber threats and unauthorized access. Common threats include malware infections, phishing attacks, SQL injection, cross-site scripting (XSS), and brute force attacks.
Best Practices for Web Developers
Keeping Software Updated
One of the most fundamental steps in website security is keeping all software, including the content management system (CMS), plugins, and server software, updated with the latest security patches and fixes. Outdated software is often targeted by attackers due to known vulnerabilities that can be exploited.
Implementing HTTPS
Implementing HTTPS (Hypertext Transfer Protocol Secure) encrypts the data transmitted between the website and its users, ensuring confidentiality and integrity. HTTPS not only protects sensitive information but also boosts trust among visitors, as indicated by the padlock icon in the browser's address bar.
Using Strong Authentication Methods
Implementing strong authentication methods, such as multi-factor authentication (MFA) and CAPTCHA, adds an extra layer of security to user accounts. MFA requires users to provide multiple forms of verification, such as a password and a one-time code sent to their mobile device, reducing the risk of unauthorized access.
Securing Against SQL Injection Attacks
SQL injection attacks occur when malicious actors exploit vulnerabilities in web applications to execute arbitrary SQL commands. Web developers can prevent SQL injection attacks by using parameterized queries and input validation to sanitize user inputs effectively.
Protecting Sensitive Data
It's essential to employ encryption techniques to protect sensitive data, such as passwords, credit card information, and personal details, stored on the website's servers. Encrypting data at rest and in transit mitigates the risk of data breaches and unauthorized access.
Regular Security Audits
Conducting regular security audits helps identify vulnerabilities and weaknesses in the website's infrastructure and codebase. Penetration testing, vulnerability scanning, and code reviews enable web developers to proactively address security issues before they are exploited by attackers.
Choosing a Secure Hosting Provider
Selecting a reputable and secure hosting provider is critical for ensuring the overall security of your website. When evaluating hosting providers, consider factors such as security features, reliability, scalability, and customer support.
Evaluating Security Features
Choose a hosting provider that offers robust security features, such as firewalls, intrusion detection systems (IDS), malware scanning, and DDoS protection. These features help protect your website from various cyber threats and ensure continuous uptime.
Ensuring Regular Backups
Regularly backing up your website's data is essential for mitigating the impact of security incidents, such as data breaches or website compromises. Choose a hosting provider that offers automated backup solutions and store backups securely offsite.
Customer Support and Response to Security Incidents
Opt for a hosting provider that provides responsive customer support and has established protocols for handling security incidents. In the event of a security breach or downtime, prompt assistance from the hosting provider can minimize the impact on your website and business operations.
Implementing Firewall Protection
Firewalls act as a barrier between your website and external threats, filtering incoming and outgoing network traffic based on predefined security rules. There are several types of firewalls, including network firewalls, web application firewalls (WAF), and host-based firewalls.
Configuring and Maintaining Firewalls
Properly configuring and maintaining firewalls is crucial for effective security. Define firewall rules based on the principle of least privilege, regularly update firewall configurations to reflect changes in the website's infrastructure, and monitor firewall logs for suspicious activity.
Educating Users about Security
In addition to implementing technical measures, educating users about security best practices is essential for enhancing overall website security. Provide users with resources, such as security guidelines, tips for creating strong passwords, and information about common phishing scams.
Importance of User Awareness
Users play a significant role in maintaining website security, as they are often the targets of social engineering attacks. By raising awareness about potential threats and providing guidance on how to recognize and respond to them, web developers can empower users to stay vigilant online.
Providing Training and Resources
Offer training sessions and educational materials to help users understand the importance of security and how to protect themselves while using the website. Regularly communicate updates and reminders about security practices to reinforce good habits.
Monitoring and Responding to Security Incidents
Despite taking preventive measures, security incidents may still occur. Establishing robust monitoring systems and incident response protocols enables web developers to detect and respond to security threats in a timely manner.
Setting Up Monitoring Tools
Utilize monitoring tools, such as intrusion detection systems (IDS), security information and event management (SIEM) systems, and website monitoring services, to detect abnormal behavior and potential security breaches. Configure alerts to notify you of suspicious activity promptly.
Establishing Incident Response Protocols
Develop comprehensive incident response plans that outline roles, responsibilities, and procedures for responding to security incidents. Establish clear communication channels and escalation paths to coordinate responses effectively and minimize the impact of security breaches.
Securing your website requires a proactive approach that involves implementing a combination of technical measures, choosing a secure hosting provider, educating users about security best practices, and establishing robust monitoring and incident response protocols. By following these best practices, web developers can mitigate the risk of security breaches and safeguard their websites and the sensitive data they handle.
#website security has become a paramount concern for businesses and individuals alike. With cyber threats becoming increasingly sophisticated#it is crucial for web developers to adopt robust security measures to safeguard their websites and the sensitive data they handle. In this#we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potenti#Introduction#In today's interconnected world#websites serve as the digital storefront for businesses#making them vulnerable targets for cyber attacks. From data breaches to malware infections#the consequences of a security breach can be severe#ranging from financial loss to damage to reputation. Therefore#prioritizing website security is essential for maintaining the trust and confidence of users.#Understanding Website Security#Before diving into best practices#it's crucial to understand the importance of website security and the common threats faced by websites. Website security encompasses measur#phishing attacks#SQL injection#cross-site scripting (XSS)#and brute force attacks.#Best Practices for Web Developers#Keeping Software Updated#One of the most fundamental steps in website security is keeping all software#including the content management system (CMS)#plugins#and server software#updated with the latest security patches and fixes. Outdated software is often targeted by attackers due to known vulnerabilities that can#Implementing HTTPS#Implementing HTTPS (Hypertext Transfer Protocol Secure) encrypts the data transmitted between the website and its users#ensuring confidentiality and integrity. HTTPS not only protects sensitive information but also boosts trust among visitors#as indicated by the padlock icon in the browser's address bar.#Using Strong Authentication Methods#Implementing strong authentication methods
0 notes
Text
The company now legally known as “THAT COMPANY WHOSE NAME USED TO CONTAIN HTML SCRIPT TAGS LTD” was set up by a British software engineer, who says he did it purely because he thought it would be “a fun playful name” for his consulting business.
The original name of the company was ““><SCRIPT SRC=HTTPS://MJT.XSS.HT> LTD”. By beginning the name with a quotation mark and chevron, any site which failed to properly handle the HTML code would have mistakenly thought the company name was blank, and then loaded and executed a script from the site XSS Hunter, which helps developers find cross-site scripting errors.
3K notes
·
View notes
Text
youtube
Is your Drupal secure? | Access Control | Encryption | @lvlabsoftware
Watch the video here: https://youtu.be/3IePi_RBWsQ
Hello everyone, Welcome Back to our channel! In today's video, we will discuss “How Drupal Handles Website Security and Share Some Tips on Checking if Your Drupal Site is Secure?” Do you know? how fast your website really is? Drupal is a CMS used to create all kinds of websites, and it comes with some built-in security features. Make sure to watch the video until the end, so that you don't miss any important information about Drupal Website Security. We hope you found this video helpful. If you want to know anything about Drupal, feel free to contact us.
Don't forget to like, share, and subscribe to our channel, so that you don't miss any updates in our channel about the latest content.
0 notes
Text
“Common Website Security Threats and How to Protect Your Business”
In today's digital age, websites have become an integral part of conducting business. They are used to attract customers, showcase products or services, and facilitate transactions. However, since people rely more on websites, there is an increase in website security concerns, which can jeopardize critical data, disrupt operations, and harm a company's brand. In this blog, we will look at some typical website security issues and offer practical solutions to secure your company. Remember that protecting your website is critical for preserving client trust and guaranteeing the success of your online presence.
1. Malware Infections:
Malware is malicious software designed to infiltrate and harm computer systems. Viruses, ransomware, and spyware are examples of common categories. Follow these procedures to safeguard your website against malware infections:
Maintain the software and plugins on your website.
Install a trustworthy security plugin or firewall to scan for and prevent harmful activity.
Using online security tools, monitor your website for vulnerabilities and malware on a regular basis.
Educate your employees on the need for safe browsing habits and the perils of downloading unfamiliar files.
2. DDoS Attacks:
Distributed Denial of Service (DDoS) attacks aim to overwhelm a website's server by flooding it with traffic, making the website inaccessible to legitimate users.
Use the following procedures to protect your company from DDoS attacks:
Use a web hosting service that includes DDoS protection.
Use rate-limiting methods to detect and prevent excessive traffic.
To disperse traffic and mitigate assaults, consider employing a Content Delivery Network (CDN).
3. SQL Injection:
SQL Injection: SQL injection is a web security flaw that allows attackers to manipulate the database of a website by injecting malicious SQL queries. To avoid SQL injection attacks, use these steps:
Use parameterized queries or prepared statements in your code to sanitize user input.
Update and patch your database management system on a regular basis.
Use a web application firewall (WAF) to detect and prevent SQL injection attempts.
4. Cross-Site Scripting (XSS) :
XSS attacks occur when malicious scripts are injected into web pages that users view, allowing attackers to steal sensitive information or take control of the website. Protect your company from XSS attacks:
Implement input validation and output encoding to prevent malicious scripts from running.
Control which scripts can run on your website by using security headers such as Content Security Policy (CSP).
Review and sanitize user-generated content, such as comments and form inputs, on a regular basis.
5. Phishing Attacks:
Phishing attacks entail deceiving people into disclosing sensitive information, such as passwords or credit card information, by impersonating a trustworthy institution. Protect your company and consumers from phishing attacks:
Teach your staff how to identify and report phishing attempts.
To prevent email spoofing, use email authentication methods such as SPF, DKIM, and DMARC.
To increase client trust, display visible security indications such as SSL certificates and trust seals on your website.
When it comes to website security, proactive measures are essential. Protect your business from these common threats and ensure the safety of your online presence. Partner with Shariwaa, a leading web security provider, to safeguard your website from cyber threats. Contact us today to learn more about our comprehensive security solutions.
#shariwaa#websitesecurity#malwareinfections#securityplugins#DDoS Attacks#webhosting#sqlinjection#cross-site scripting#securitypolicy#phishingattacks
1 note
·
View note
Note
I have an idea. A self-aware au. What if Jing yuan/Blade is aware of darling's affection for him since they would log in the game and just see him and just admire them that is until Genshin drops 4.1 trailer and saw Arlecchino and Neuvillette and now they're envious of these two taking away their darling's attention.
It's just an interesting idea tho. But in actuality I'd think neuvillette and him would be friends or somewhat


Hello, this anon has similar thoughts!! Put them together to answer >_< I think they will be really jealous of the genshin impact characters who are stealing your attention lol. Jing Yuan's jealousy is more harmless (seemingly), while Blade's is more aggressive (?)
This is my first time writing a self-aware AU, hope you like it!!
CW: yandere, self-aware au
Jing Yuan and Blade have their own lives.
When you're not with them, when you're not in front of the screen or looking at them with a smile or wonder. They are handling the work/tasks of the Seat of Divine Foresight/Stellaron Hunters. Blade, Silver Wolf and Kafka were practicing the new "destiny" script and took away another Stellaron. Jing Yuan is managing Luofu and attending meetings. How strange. Once you click on the space screen to enter the game, they can see your face. You organize your team and do daily tasks with them.
At first, they thought it was some kind of prank or a conspiracy, but over time they got used to it. In Elio's words, "The world is like a video game. No one can prove whether the world is real or false. Feeling the current destiny is the most important thing."
For Jing Yuan, he just got familiar with your personality. He confirmed that your presence would not put Luofu in danger, and that you acted like a cute kitten playing with a ball of yarn. You can control Luofu's General and Stellaron Hunter, and all you do is wander around Xianzhou and buy snacks to feed them, break every poor object on the way, fight to get some rewards, take the books on the table, etc.
You didn't forget to "build" them either. They watch you search for "Jing Yuan", "Blade", "build", "guide" and other keywords on the Internet, and take them to fight again and again to get materials to upgrade. Although they have actually participated in some wars and have terrible strength, what you see here is "lv 1-80".
You really like them, otherwise you wouldn’t pull, right? You even take photos of them while wandering around the map. Jing Yuan snickered when you took Blade to take a selfie in front of his wanted poster. The general is not shy about giving you a smile either. They know your admiration because you always take more than one photo.




Until… recently, they noticed that you weren't online as often. At one point, you log in again, and then, as if you thought of something important, you search "genshin impact" on Youtube (they know the name of the site) and start watching trailers and special programs.
What's this?
You stared intently at those…those people. White curly bangs, long hair like a waterfall, and his gorgeous and decent attire. The other man has short black hair. He punches enemies in live. A woman with short gray and white hair smiles confidently.
Jing Yuan opened his eyes wide, not expecting you to be so "frivolous" - did you plan to be unfaithful to him? You found Jing Yuan pouting at you in the game, but you thought you were hallucinating, so you gave him immortal's delight and puffergoat milk to comfort him. Blade clicked his tongue, crossed his arms in boredom, and stopped observing what you were doing on the other side of the screen. Silver Wolf and Kafka teased him about whether he was separated from the little player? Jealous? You're surprised to notice that his damage has been doubled. While on a mission, Blade almost lost control and killed a person on the script. His eyes as red as candlelight flashed, and he almost swung down the sword in his hand.
They are all looking for opportunities to get close to you. That part of Xianzhou's large computer installation called "loom" is running, investigating and analyzing you.
#yandere jing yuan x reader#yandere blade x reader#yandere hsr#yandere honkai star rail#yandere jing yuan#yandere hsr x reader#honkai x reader#honkai star rail x reader#honkai star rail x you#blade x reader#hsr x reader#hsr blade x reader#blade x you#hsr x you
875 notes
·
View notes
Text
cw: streamer au! you and hawks have a popular channel and you have some special guests! fluff! reader and hawks are married. 'dove' as a nickname. written for @pastelle-rabbit.
“Did you finish setting up the microphones, dove?” Keigo asks, while you’re just about to adjust your PC setup. The stream begins in five minutes, and while it’s not the first time you’ve gone live with your love, it’s the first time that you’ve had guests on your streaming site, and this is highly anticipated enough that you expect a higher turnout for today, and commensurately likely more trolls. You’re used to Keigo’s trolls as a top-ranking hero, but Izuku’s trolls are a whole different beast.
“Yes!” you sing out to him. After the final adjustment, you shoot a glance to Izuku and his wife who are poised very politely on gaming chairs you got just for them; his hand is holding hers, the thumb caressing the back of her hand while she crosses her legs at the ankle. She looks distressed and you stifle a giggle. Horror and gore are the themes for your stream today and from what Izuku has told you, she’s a screamer, but so is Keigo, so the two will be squawking like birds for the remainder of the night.
You can’t wait.
“Are you guys comfortable?” you ask. The chair arrangement is a little more complex to make sure everyone stays huddled around your huge monitor, but you’ve figured it out.
She nods slowly, and Izuku grins. “We’re doing perfect!”
There are now two minutes until the stream starts, and Keigo slips into the chair right beside you and kisses your cheek, his other hand deep in a bag of chicken chips which he brings to your mouth.
You indulge him with a bite, and he grins, then whispers if you want him to be your chair this time, and while Izuku grins politely at the two of you, you can sense yourself warming in the face.
“We have guests,” you remind him. Keigo throws a glance at Izuku who immediately waves his hands.
“Pretend we’re not here.”
“What do you mean we’re not here, we were in-”
You start the stream and Izuku’s wife falls silent, immediately switching to camera ready mode. “Welcome guys and thanks for coming back to our channel! As promised, we have special guests today! -” Deku and his wife wave politely to the camera in million-watt smiles, “- and we’ll be continuing with our horror themed stream!”
Keigo chews loudly and waves at the camera. “I’ll be here!” he motions a salute to the screen. As expected, you can already see the influx of his fans filling the chat, painfully polite in their thirst since the last time he reminded them on screen he was happily married.
“Ooh can we have streamer nicknames?” Izuku’s wife asks.
“Sure, what would you like to be called?” you offer. She looks around, then up at the ceiling, then her eyes light up.
“Hm… BLOODCRUSH.” She says with dramatic glee. The rest of the three of you blink rapidly, but no one argues.
“Bloodcrush it is!” you announce as she kicks her feet. Izuku gives her a mildly concerned look, but then rubs her shoulder affectionately. The chat starts to rile up with comments in support of new nickname Bloodcrush (bloodcrush x deku otp, bloodcrush fighting!) to her delight while the less savory ones are promptly ignored.
“I think the rest of us will just go by our hero or streamer names, is that okay?” Keigo says, stretching out in his chair and resting his arm around the shoulder of your gaming chair, pose relaxed.
“So what game are we playing?” Deku starts per your loosely prepared script.
“RAID AND EXECUTION,” Hawks announces, excitedly. You laugh as the story intro video begins, and Hawks claps his hands dimming the lights while Bloodcrush looks stunned to her husband then to you.
“Raid and what?”
“Oh, that sounds awesome! I’ve heard of this one!” Deku chirps, and immediately his info-dumping begins. “So from what I’ve read, this game is set in the early 1400s in the Caribbean where a group of pirates are lost at sea and encounter a group of enchanted beings, most likely zombies, and you’re meant to survive as long as possible when they’re active at night, and raid the villagers during the daytime or else you’ll run out of resources and die, not to mention the game mechanics heavily rely on you using context clues of the environment in order to determine if a settlement is nearby and-”
Hawks and Bloodcrush both scream as the first zombie shows up on screen armed with a machete and cleanly slices the head off of your avatar.
‘Ooh, that was fast,” you say, frowning as the “Game Over” screen shows up on the monitor. The chat explodes with comments telling Deku to shut the hell up which makes him frown.
“Just trying to provide context,” he grumbles. You start up the game again and instead of jumping right off the ship and walking right onto the island, you pause and look for clues. Hawks encourages you to explore the bottom of the ruins first, which has you find a rusty machete of your own as well as some 14th century hardtack, and Bloodcrush leans in and asks you if there’s any way you can find a musket or other gun.
“Baby, I think muskets weren’t invented till the 15th century,” Deku says, and she pats his cheek gently, whispering only mildly threatening, “I didn’t ask you for historical accuracy, honey.”
“Here, I think we found one!” you exclaim and Hawks gives you a high five while Bloodcrush raises her eyebrow at him.
While you begin arranging your inventory, Hawks repeats some questions in the chat for their guests.
“So, herofootfetish69 has a question for you, Deku.”
Izuku pales while you and his wife unintentionally bursts out laughing from how nonchalantly Hawks reads the username, then your avatar inadvertently falls off a cliff and dies.
“Man!” you exclaim as you restart. Bloodcrush laughs even harder as she points to new resources that you can pick up while you’re repacking your knapsack.
“They ask, do you have time to play video games when you’re supposed to be protecting the city?” Hawks asks, then giggles.
“Why am I being heckled?” he frowns. “Yes, heroes have time off too.” He pauses. “Hawks is literally on this stream!”
“Hey, I think if you alternate the musket and the dagger, you might have a chance with those zombies,” Bloodcrush murmurs. Someone in the chat tells her that she has a better chance with the dagger alone. “Never mind, just do that.”
“Next question for LoveDove!” Keigo presses a kiss to your forehead, then reads off, “gains4fame asks, how long have you and Bloodcrush known each other?”
“Not long!” you say, “but I think we’ve become fast friends!”
Bloodcrush’s eyes light up and she playfully bops you on the shoulder. Hawks offers an affectionate awwww, and hugs you while Deku rubs his wife’s back.
In the process of your husband hugging you, you’re shot by an arrow.
“NO!” you and Bloodcrush scream in unison, then look at each other and giggle.
“Next question from chickenchipenthusiast-” Izuku pauses, then reaches for the extra bag Hawks has brought, “not sponsored by the way,” he reminds everyone, “for Hawks - how do you choose your guests on the show?”
Hawks shrugs. “When I called, you picked up.”
Izuku sighs in defeat.
“We’ll move on to the next question. For LoveDove again - do you think you’ll get better at these games?”
Hawks bristles but you laugh. “I’m having fun and so are you, aren’t you?”
chickenchipenthusiast writes: exactly!
You get your first kill of a zombie on the island and you and Bloodcrush share double high fives in delight.
The chat fills with overwhelming support and the stream continues late into the night, the chatter amongst you guys never ending and the subscribers ticking higher and higher all night.
#hawks x reader#keigo takami x reader#takami keigo x reader#keigo x reader#daydreams: bnha#mimi's notes#treasures: amira
244 notes
·
View notes
Text
SORRY - Chapter 5

I do NOT give permission for my work to be translated or reposted on here or any other site, even if you give me credit. DO NOT REPOST MY FICS
❤ Reblogs, comments, likes, and feedback ALWAYS appreciated ❤
All OC Characters belong to me


“Here are your winners and the new WWE undisputed tag team champions! Jimmy and Jey, THE USOS!” Dominique spoke into the mic, with a smile on her face. The smile quickly dropped from her face as Jon stormed over to her and pulled her with him, out of the time keeper's area and into the crowd towards the backstage area.
“Jon.. What are you doing?” She asked as she stumbled after him, trying to keep up with his long strides. She was confused, because he was definitely going off script. He was supposed to be out there attacking Randy and Riddle with his brother and cousin.
Jon didn't respond, his jaw clenched as he continued to pull her along. “Hey, what the fuck!” She yelled at him when he pushed her into The Bloodline’s empty locker room, causing her to stumble in her heels. “What is your problem!?"
“You fucking Randy?! Huh! Is that why you won’t forgive me!” Dominique snorted and crossed her arms over her chest.
“And what if I am? You were definitely gonna fuck that girl last night , oh and don’t get me started on the fact that you spent the night with Trinity.”
“Don’t fuckin’ play with me Dominque.” He gruffed out as he stalked towards her, backing her into the wall.
“Ain't nobody playin’ with you. If you can do it, so can I.” She shrugged, not backing down as she stared into his eyes. Jon closed his eyes and took a deep breath. He knew she was testing his patience and it was working. Jon opened his eyes, his jaw clenched as he struggled to keep his composure.
“Imma ask you one last time.” He muttered as he opened his eyes to look at her. “Are you fuckin’ Orton?"
Dominique rolled her eyes. “No, I'm not like you Jon, I would never cheat on the person I love.” Jon's expression darkened at Dominique's response. The tension in the room was so thick you could cut it with a knife.
Jon sucked his teeth just as Joe and Josh walked through the doors. Jon ignored them though, keeping his glare on Dominique. “Stop with that bullshit Dominique. I aint cheat on you and I never will.”
“What bullshit Jonathan?!” She yelled. “I have caught you up in TWO bitches faces and you got the nerve to be acting like this because what? Randy was comforting me!”
“He don’t need to comfort you Dom! Thats my fuckin’ job!” Josh decided to step in between them.
“Aye, y’all chill out.” He said placing his hand on Jon’s chest, pushing him back from Dominique.
“I’m chill.” Dominique said, tossing her hair over her shoulder. “It’s him, he needs to chill.” Joe snorted, then held his hands up defensively as she turned her glare to him.
“Y’all are perfect for eachother,” He muttered as he walked into the bathroom to take a shower.
“We been together for four fucking years and I’ve never even thought about another woman. I fuck up one time and you won’t let it go. I’m sorry Dominique” He stressed, trying to grab her hands but she swatted him away. Josh shook his head at them and walked out the room to call his wife, he was happy as hell he wasn’t Jon right now.
“Jonathan, it’s not just one tiny little fuck up. You let that woman into your space. You let her think that she actually had a chance with you.” Dominique tried to stop her tears from falling, but she was hurt and angry and looking at his face wasn’t making her feel any better. “And then, you spent the night with your ex? You didn’t come to me, you didn’t try to talk to me, you went to her and I'm supposed to just forgive you?”
Jon stood there frozen as he watched the tears fall down her face, his heart heavy with the weight of Dominique’s pain that he caused. This was the second time in the four years they had been together that he had made her cry; the first being when he proposed in Paris.
“If I can take it all back I would Dominique.” Dominique sniffled and wiped her tears away.
“I don’t wanna talk about this anymore.” She muttered as Joe walked out the bathroom. “We have a flight to catch, are y’all ready?” Without waiting for a response she walked out of the locker room and towards the writers room to grab her bags.
Jon watched her walk away as a feeling of hopelessness washed over him. Their relationship was hanging on by a thread and he feared that with every passing moment, that thread was growing thinner and thinner. But he also knew that he couldn't force Dominique to forgive him, couldn't demand her love in return for his apologies.
“Sis, you okay?” Josh asked her as she walked past him.
“No,” She shrugged, sending him a soft smile. “But I will be.”
“I know Jon’s my twin, but I'm here for you, aight?” She nodded.
“Thank you Josh.”
Back in the locker room Jon groaned and plopped down on the steel chair. “You know I don’t like to get in y’all relationship business.” Joe started, walking closer to his cousin. “But Dominique is the one for you. I mean after you broke up with Trinity and brought Dom around, everyone and I mean everyone was skeptical about y’all relationship. But shit the whole family loves her now. Y’all gotta fix this,”
"I know, Joe," Jonathan admitted, his voice heavy with regret. "I messed up, big time. I don't know how to fix things with her."
Joe placed a reassuring hand on Jonathan's shoulder, offering him a sympathetic smile. "You just gotta show her, man.”

“Hey” Ishana said as Dom walked in. “You look rough.” Dominique rolled her eyes.
“I feel rough.” She muttered, walking over and grabbing her luggage.
“Jon again huh?” Dom nodded and let out a sigh. “So y’all still beefing?”
“Yes, he seems to think that he can just say sorry and everything will go back to normal.”
“Have you expressed how you feel though? About the whole situation, why you don’t wanna get married?” Dominique sighed and rolled her eyes.
“Ishana, I don't wanna talk about my problems with Jon right now.”
Ishana ignored her, “Communication is key, Dom. he’s taking accountability and you need to too.” Dom scoffed but Ishana held her hand up to silence her. “Okay I get it the girl kissed him and yes, he went to Trinity this morning but to be honest you were looking for a way out of the engagement anyway.” Dominique's eyes widened. Ishana's words hung in the air, heavy with truth and accusation. Dominique felt a mix of shock and anger rising within her, her mind racing to process what she had just heard.
“You’re joking right? Now is not the time to be funny.” Dominique said glaring at Ishana. “No, I wasn’t tryna find a way out of my engagement. I wanted to get married to Jon, just not right away.”
Ishana rolled her eyes.
“Bullshit. Ever since yall got engaged you’ve been picking fights with him and as your best friend it’s time I spoke up and told you about yourself. Yes he fucked up by letting that girl into his personal space but he’s been trying to talk to you, trying to apologize to you but you blocked him, how can he make things right if you’re closing off all communication with him?"
“You’re supposed to be on my side!”
Ishana shook her head, not believing how stubborn her best friend was being. “There is no sides, Dom. I want you and Jon to be happy. And in order for that to happen, you need to grow up. Not all marriages end in divorce.” Ishana said, grabbing her pocket book and walking out the room. Dominique stared at the closed door in shock. What the fuck was that?!

Heyyyy... long time no see 😭🫣
I was having second thoughts about this story but talking to @paigereeder i got a second wind and was able to finish this chapter!
Hopefully you guys won't have to wait as long for the next chapter.
❤ Reblogs, comments, likes, and feedback ALWAYS appreciated ❤
🏷️: @empressdede @abadbitchblogs @wrestlingprincess80 @harmshake @cyberdejos2
@almondmilkdeinker11 @girlwhogaf @alyyaanna @paigereeder @amandairene88
@skyesthebomb @yana3sworld @mindairy @hllokttysoprtty @christinabae
@tbmotw @rantfandombloggg @jeyusosgirl @southerngirl41 @wooahmiri
@theninthwonder @saintaquarius @raya-hunter01 @rebelrel0987 @feelinuceyy
@qveenmikaelson @black-yn @mzv11 @shantinextdoor @sheydnni
@zillasvilla @thatone-girly @xmonetsworld @li-da-savage @kill-the-artiste
@reci1996 @that-one-anxious-mango @mersers-moonypadfoot-prongs @trashbin-nie @adoreesun
@meggylynnloves @shayaaaaaaa
@tableofthehead @lovelyhunnys @wwelovergirl @meannaim
#wwe#jimmy uso imagine#jimmy uso fanfiction#jimmy uso#jimmy uso x fem reader#jimmy uso x black reader#jimmy uso x you#jimmy uso x oc#jimmy uso x reader#jimmy uso fic#wwe fanfiction#wwe x black reader#wwe x fem reader#wwe x reader#wwe fic#wwe x black oc#x black reader
110 notes
·
View notes
Text
ok so ive been rewatching psychoville and saw on the wikipedia that there were a bunch of websites made for the series (they were all written by reece and steve btw) which i've been looking through cos they are genuinely SO fucking funny & also just amazingly creative lol!
anyway i know people in the fandom probs already know about this (since the show came out literally 15 years ago pfft) but i thought i'd share some of my fav bits (but honestly would just recommend just checking them out if you haven't i have been crying with laughter for literally hours lol)
i will say that a lot of the media (videos, games, etc) no longer work on the archived sites rip but i'm sure people have uploaded some of the stuff (vids especially) to yt or other places lol

so a) i love that we get some background stuff on jelly and 2) 'captain CRACKERS' bernie clifton's dressing room reference question mark ??????? (ofc bcdr was AFTER this but i know love the idea that mr jelly trained under len pfft)

what that red raw stump do though 👀 (sorry pfffft)
mr jolly's website wasn't that interesting soz tho i did like him comparing being a doctor to being a clown lol
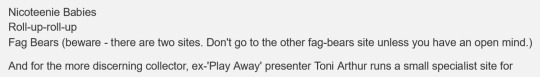
the comment about fag bears did make me wheeze i'm afraid lol i also loved the blurry photos of lomax's commodities lol (kinda reminded me of the bit in tlog w/ that terrible old photographer guy lol)
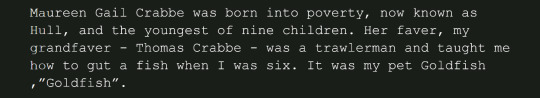
when i tell you i DIED with laughter at the 'now known as hull' bit like u just know reece wrote that bit pfft
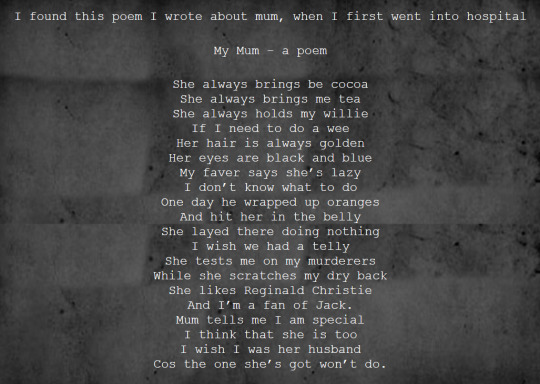
not really a funny thing but this poem written by david honestly kinda breaks my heart lol... i think it also a lot of additional context to david's guilt when he thought he'd killed his father(faver) because perhaps he felt guilty about NOT feeling guilty you get me? like, it felt to me that when maureen told david it was SHE who killed her husband, it didn't feel like he was mad at her for doing it, but more that she kept the fact from him. it's about... the mutual oedipus-coded obsession with one another that couldn't even be destroyed in death and in this essay i will....

ghoul_lass23 is just like me but about tumblr lol fr

nothing feels more cursed than the phrases 'the river minge has burst its banks', 'crying creamy tears' and 'fleshy rapunzel' (which i've just noticed they misspelt lol... don't think that was intentional lol?) so if i had to read this so do you <3

the way that i kinda wish this actually existed tho pfft... also, it does kinda remind me of that video where jenny nicholson talked about that insane reality show 'opposite worlds' lol

'cross between seven and glee' is honestly sending me pfft
also on this part there was a script from stinkfinger (which is a show mentioned on the show) which sounded suspiciously like a reference to tlc lol

the less said about swastknickers the better
(will say i did nearly piss myself laughing at the nazi section of the hoity toity website lol which wasn't a sentence i thought i'd type today lol)

i just love these kinds of jokes pfft
also the whole biography sections of each of the pantomime cast are fab lol tho i AM kinda pissed they made debbie from yeovil and yet didn't give her a west country accent lol!!! (i guess they thought it'd be a bit much w/ joy being bristolian but i'm still mad about it lol)
also i know people have probably already pointed this out but i do find it funny that brian in the in9 episode last night of the proms is a closeted gay guy who likes watching drag was probably a reference to brian in this show that was a drag queen like... is anything these guys do NOT a reference??? u know those gaylor fans who obsessively look for clues in her songs about her apparent secret sexuality? all i'm saying is that i think they'd really like the extended reece shearsmith & steve pemberton universe pfft

all three of these made me cry with laughter lol

ohh this is interesting lol so obviously they suspected that some people might be all 'um why didn't the sprinklers go off during the fire at ravenhill? plot hole much!' so they wrote this into one of the websites so they could be like SEE! WE'RE ONE STEP AHEAD OF YOU DUMBASSES lol

both the jeremy kyle reference (remember when that was a thing? yikes... my mum used to watch his show CONSTANTLY...) and nurse kenshington's thoughts on david and maureen are interesting lol.. also there's a reference to the serial killer top trumps in this bit lol! (do people still play top trumps?? man i LOVED top trumps lol...)


the entire sunnyvale care home section is so fucking funny (both the website AND in the show lol mrs wren/mrs ladybird face is unironically probably my favourite character on the entire show) these were just some of my fav gags lol...
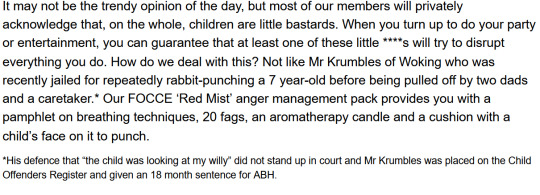
ok but why is this the SECOND reference to a guy punching a child who was apparently looking at his dick lol!??!! did this happen to one of you ??!!?!? reece did you punch a child ??!???!?!??
&&&& that's it lol
there were a few websites i didn't spend long on or generally weren't that interesting (coughmidgetgemscough) but honestly? i was really captivated with just how funny and well put together all these sites were! you can tell they had a lot of fun making it and i'm sure fans at the time LOVED being able to have this semi-interactive element of the show lol
there was just something so wonderfully late 00's about these websites lol i genuinely don't think i've laughed this much at anything in literal months and all of this is just solidifies that psychoville is a criminally under-appreciated masterpiece lol
#psychoville#reece shearsmith#steve pemberton#there are too many characters mentioned here to list lol#honestly more people need to watch this show it's just great lol#anyway i hope that some of y'all have a laugh reading some of these even if ur not familiar with the show lol!
64 notes
·
View notes