#malware for hacking
Explore tagged Tumblr posts
Text
Masterpost of informational posts
All posts are written for everyone, including those with no prior computer science education. If you know how to write an email and have used a computer at least sparingly, you are qualified for understanding these posts. :)
What is a DDoS
What are the types of malware
Vulnerabilities and Exploits (old and somewhat outdated)
Example of how malware can enter your computer
What are botnets and sinkholes
How does passwords work
Guide for getting a safer password
Here are various malware-related posts you may find interesting:
Stuxnet
The North Korean bank heist
5 vintage famous malware
Trickbot the Trickster malware (old and not up to date)
jRAT the spy and controller (old and not up to date)
Evil malware
New to Linux? Here's a quick guide for using the terminal:
Part 1: Introduction
Part 2: Commands
Part 3: Flags
Part 4: Shortcuts
If you have any questions, request for a topic I should write about, or if there is something in these posts that you don't understand, please send me a message/ask and I'll try my best to help you. :)

- unichrome
Bonus: RGB terminal
#datatag#masterpost#malware#cybersecurity#infosec#security#hacking#linux#information#informative#computer science
422 notes
·
View notes
Text

Confession #385
#rwby#doomalade#penny polendina#spoilers#volume 8#writing#I mean we have gone through this before here but I do have to wonder what they were thinking#bringing her back without any real setbacks (other than Pietro not being able to possibly build her again)#like idk... if u have to bring her back make her memory being erased or missing or something#~oo watts stole the memory disc we have to get it back~#oh no the gang didnt realised watts had installed malware there no Penny is getting hacked!!!!! ;_;#but yeah#why make her human? wasnt she human enough the way she was..?#Ironwood losing his humanity after having more robotic parts in him and this kinda makes a eeugghh bad look#xyz coding#trans allegory#winter maiden#also yeah there could be some dramatic irony in healer having to kill a friend/ally but cmon guys please anyone else pl-
57 notes
·
View notes
Text
Hello everyone!
I just found out some creators have had their simfileshare hacked and their downloads replaced by zip files containing executables that are likely malware (I'm getting this from the SimsAfterDark Discord-- check there for more info). Simfileshare is down right now, so I can't clear my files just yet, but I wanted to help spread the word about what's going on.
Unlike previous attacks which relied on users putting files into their game and then the game launching them, these are executables. ModGuard won't help protect you. At least one creator affected does mods for all four sims games, so this isn't a TS4 only issue this time. If you think you've downloaded the file, get rid of it immediately and check your computer for malware.
Until I can get around to clearing them, download at your own risk. Keep in mind that most of my files are .package and I've never shared anything with a script file. Further, I think I only have at most one or two zip folders if that, so if anything directs you to downloading a zip folder from me, be extra vigilant.
Stay safe everyone.
8 notes
·
View notes
Text
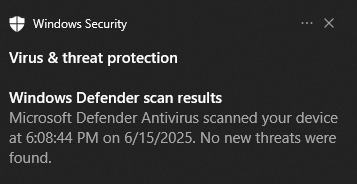
after flooding my pc with notifications, i turned off chrome and ran windows security. chrome is just really dramatic about the four whole russian hackers that apparently got on.
2 notes
·
View notes
Text
TS4 Malware via .TS4SCRIPT mods
(Copied from my Patreon)
Hi everyone, I figured I would make a post about this just in case anyone who follows me has not yet been made aware of the malware issues happening currently in the Sims 4 modding community.
Several days ago malware was discovered within a few mods that would silently steal info from your computer such as passwords and private information. This malware was then found to be in many other mods, as early as August 2023. It appears to mostly affect script (.ts4SCRIPT files), but be wary of .package files as well. Please read more about this on this reddit post and consider downloading TwistedMexi's ModGuard malware protection mod: https://www.patreon.com/posts/98126153 to keep yourself safe. There is also this website with information about the malware, known affected mods, how to check if you have been infected by it, and what to do if you have: https://scarletsrealm.com/malware-mod-information/
This malware affected user accounts which appear to have been hacked, or fake accounts made to mimic real users primarily. The list of known mods that were affected are:
Cult Mod by _PimpMySims
Social Events – Unlimited Time by MySims4
Weather and Forecast Cheat Menu by MSQSims
Seasons Cheats Menu by MSQSims
Motherlode Menu by MSQSims
Mood Cheat Menu by MSQSims
Mouth Preset N16
If you have downloaded these mods, please follow the advice in the reddit thread/website linked above. Please stay safe and vigilant when installing mods if you are continuing to do so currently.
#sims 4#the sims 4#sims 4 custom content#the sims#ts4#sims#the sims cc#script mods#malware#sims 4 malware#sims 4 virus#virus#hacking
27 notes
·
View notes
Text
we don’t have a lot of customers in my job, because our main purpose isn’t selling stuff to consumers, we’re mainly ‘selling’ to other branches, and administer their shifts.
so when i work in the front, and either the person with me is in charge of the phone, or there aren’t a lot of phone calls, i don’t really have anything to do,
so i started reading papers about malware on vxug, and its so funny cuz i’ll be like “ohh, yes, malware, kernel space, privilege escalation, hacking stuff” and then 5 seconds later be like “haiiii:3 welcome, do you need any help? we have these cool color changing candles if you want, these chocolates are really tasty<3”
it encapsulates the personality of so many trans women i’ve talked to, its hilarious to me lol!
#:3#196#rule#egg irl#traaa#ruleposting#r/196#:3 hehe#autismposting#actually autistic#mentally disabled#legally disabled#job#work#hacking#vx underground#vxug#malware
9 notes
·
View notes
Text
The Hacker's Guidebook:
Aspiring hackers! I’ve created a guide covering core cybersecurity concepts new hackers should master before tools. I break down networking, OS internals, & hacking tactics. Recognize hacking as lifelong journey—arm yourself with the basics!
Core Concepts for Budding Cybersecurity Enthusiasts The Building Blocks of Ethical Hacking So you want to become an ethical hacker and enter the exciting world of cybersecurity. That’s awesome! However, before you dive headfirst into firing up Kali Linux and hacking everything in sight, it’s vital to build up your foundational knowledge across several InfoSec domains. Mastering the fundamentals…

View On WordPress
#attacking tools#basics of hacking#cross site scripting#Cyber Threat Defense#cybersec#cybersecurity learning#cybersecurity professional#Ethical Hacking#fundamentals#hacking basics#hacking for beginners#hacking guide#hacking networks#hacking web#how to hack#infosec#learn hacking#learn to hack#linux#malware basics#malware for hacking#metasploit#netsec#network hacking#nmap#operating systems#Pentesting#phishing#phishing attacks#Red Team
34 notes
·
View notes
Text
15 Best Free Resources for Malicious URLs and Phishing Links for Cybersecurity Testing
In today’s rapidly evolving cybersecurity landscape, having access to reliable sources of malicious URLs, phishing links, and malware samples is essential for security professionals, penetration testers, and IT administrators. Whether you’re validating your security controls, conducting security awareness training, or researching new threat vectors, accessing known malicious content in a…
#cyber threats#cybersecurity#ethical hacking#malicious URLs#malware analysis#malware samples#penetration testing#phishing detection#phishing links#security controls#security testing#security tools#security validation#threat intelligence#web security
2 notes
·
View notes
Text
It's tuesday and I almost
managed to get a full night of sleep,
I played with dirty lines of code and
freaked out over nothing like
the fucking adult that I'm.
The skeleton in me was
aching for a dance floor where it could erode,
but it's tuesday and my bones
would be missing for a few more days,
something other than regret occupied it's place for now,
and smoky ash piled upon my love for bad decisions
colored it's trained indifference.
Dogs mourned and howled as
a missing less than sign shook my world red,
things that never truly mattered failed to compile,
logic gates screamed like the promises of
someone that wished for nothing but harm.
A threat analyst somewhere would call it fatal,
but on a tuesday no one would care,
proper malware always walks in uninvited and
I can appreciate that as much as the next vampire.
At my fingertips, structures of thought are turned
into pure mayhem as key constraints overflow
into abstract nightmares,
the green shell erupts in deliverance,
payload is such an ugly word for retribution
on a dying tuesday that,
by all that is fair and right should never have existed,
I name the file heartbreak.rb and call it complete,
feeling the urge to dance slowly escape from me,
dream, little file,
dream of all that is vile,
dream of all you could have been
#poetry#original poetry#poets on tumblr#female poets#poemsbyme#spilled ink#spilled poem#trans poets on tumblr#hacking#malware
19 notes
·
View notes
Text
DAILY DOSE: FBI Removes Chinese Malware from Over 4000 US Systems; Three More Cats Infected with H5N1 Avian Flu.
FBI REMOVES CHINESE MALWARE FROM 4258 US COMPUTERS The FBI announced that it removed Chinese malware, PlugX, from 4,258 US-based computers and networks. The malware, developed by the Mustang Panda group under the direction of the Chinese government, has been infecting systems since at least 2014, targeting US victims, governments, businesses, and Chinese dissidents. The malware remains largely…
#Africa#artificial intelligence#Asia#Australia#avian influenza#Europe#Featured#hacking#malware#North America#obesity#South America#technology
2 notes
·
View notes
Text
The biggest heist that almost was
Let me tell you about the most insane bank heist that is going to sound like I'm just leaking the script for the next American hacking movie. The goal? Steal one billion USD. And it all began with an email and a printer, which as we all know is where problems usually start. Another weapon in this heist was... Weekends and time zones.
As usual, no prior computer science education needed.
What happened?
On the morning of February 5th 2016, a printer had stopped working in the central bank of Bangladesh (Bangladesh Bank). But it wasn't just any printer, it was the printer responsible for printing all the records of the multimillion transfers going in and out of the bank. When the poor employees finally won the printer battle and had it resume normal operation, they saw a very concerning account transfer in the records that was coming out. The bank had an USD account in the USA, at Federal Reserve Bank, with approximately 1 billlion Dollars in it, and the Federal Reserve Bank had received instructions to drain almost the entire amount. In the records that came out in the printer, the American bank had attempted to urgently message the Bangladesh bank regarding this transfer, but couldn't get through to them. This was because the hack had actually started the day before, Thursday 4th, at around 20:00 Bangladesh time, when the bank was closed. However, USA had just started their day, giving the American bank plenty of time to follow through with the instructions from the Bangladesh bank to drain their entire account while they were closed. And that wasn't the end of it, as weekends are from Friday to Saturday in Bangladesh, meaning that the Bangladesh bank headquarters in Dhaka wouldn't discover this withdrawal until Sunday morning. That's when they immediately tried to reach the American bank, which of course didn't work as over there it was Saturday evening, and the American weekend is from Saturday to Sunday, meaning that they wouldn't be reachable until Monday.
You see what I mean by the hackers using time zones and weekends, finding the perfect time for the American bank to execute their orders while Bangladesh discovers the withdrawal several days too late, and again several days too late for Americans to be reachable. But it didn't stop there with their timehacking.
The money had to go somewhere from the American bank, and it would be stupid to send it directly to the hackers own account without laundering the money first. So they had set up four different bank accounts in the Philippines, using fake names and credentials. Why the Philippines? Because the Lunar new year was on Monday the 8th, which is a holiday and holiday means no bank activities in either Bangladesh or the Philippines, buying the hackers even more time. As a final act, they messed with the printer responsible for printing transaction records, adding another few hours to their schedule. Moon and stars really aligned perfectly for this plan.
But how did they do it?
It all began one year prior, in January 2015, with an email sent to several employees at the Bangladesh Bank. The email seemingly contained a job application from a person who didn't actually exist, but who was very polite in his request for a position at the bank, with a link to his CV and cover letter. Naturally this link led to a document with a little surprise gift - malware. Since the heist happened, at least one of the recipients must have clicked the link, and successfully deployed a RAT - Remote Access Trojan, malware that lets you control a computer from the comfort of your own home, as well as a toolkit with various malware to move from computer to computer, avoiding discovery, and covering their tracks.
From there, the hackers slowly made their way through the bank offices network, one step at a time to avoid setting off alarms, looking for any computer that had control of the banks SWIFT setup. SWIFT lets banks transfer large amounts of money between themselves and other banks connected to SWIFT. And as soon as they found one of those computers, they stopped. They didn't need to hack SWIFT in the traditional sense of the word - since they operated in a bank computer, the SWIFT-software assumed they naturally had to be bank employees. However, one of the parts of the malware used in the heist was for manipulating the SWIFT system, as the hackers weren't physically there to press anything. Additionally, since they were laying dormant for the time to strike, they needed to keep an eye out for SWIFT updates that could detect any tampering with the system, and adapt accordingly.
Then they waited many months for the stars to align on February 4th, 2016.
There were 35 transfers made by the hackers from the American bank account, totaling almost 1 billion USD, but there were two of these tiny little seemingly insignificant details that prevented this from becoming the worlds largest bank heist in history. The hackers biggest enemy became this concept known as “words”.
The Philippine bank accounts were all located in the same RCBC Bank office on Jupiter Street in Manila. And this would be the hackers downfall, as USA had sanctions put on an Iranian cargo ship called Jupiter. Since the transactions went to a recipient that contained the word “Jupiter”, it created a security alert in the Federal Reserve Bank that the employees needed to investigate. When they saw what was going on, they managed to stop all but five of the initial 35 transactions, thus “only” roughly 100 million USD made it to the Philippines. The Bangladesh bank requested to reverse the transactions, but since the money was in the Philippines, they would need bureaucracy in form of a court order to reclaim the money, and we all know that's not a 5 minute project. It was when Bangladesh filed the court order in late February that the case became public (since court orders are public documents) and the news broke to the country.
Once in the RCBC bank accounts, the money arrived on Friday the 5th and was immediately moved again. First the 100 million was converted to local currency, and some of it was withdrawn in cash, while the rest was sent off to other hacker-controlled locations. And this is where the second tiny little detail cut off even more of the hackers precious payday. 20 million USD had been sent to Shalika Foundation, a charity organisation in Sri Lanka. But, once again the hackers worst enemy - words - decided to strike again. A typo was made in their transaction, sending the money to “Shalika Fundation”, and a bank employee who must have had their morning coffee spotted this typo and rejected the transfer and kept the funds frozen. This left the hackers with 80 million USD.
✨Now comes the money laundering!✨
There was a second reason for choosing the Philippines as deposit zone; gambling is legal and the casinos had no money laundering regulations imposed. The accomplices of the heist booked private rooms in two casinos located in Manila - Solaire and Midas - and proceeded to purchase tokens to gamble for with the stolen money. Since they played with a room consisting of their fellow accomplices, winning was not really much of a challenge. Then the tokens could be exchanged back to money that would now be clean. To avoid suspicion, they didn't gamble all of the money at once, but over the course of several weeks gambled away the dirty money to clean money.
Who was behind it?
It's normally difficult to pinpoint where the more sophisticated hacking groups come from. Oftentimes, they will leave false clues behind that points to another group so they will face more trouble instead of the group that did it. They may even place clues from several different groups, just to mess with the analysts. It's also quite common to simply “steal” a way of working from another group, or use a leaked/stolen tool from another group (criminals aren't safe from other criminals, especially not in this business) - there are new malware coming out all the time with code that is just a slight modification of a well-known malware actor that had their source code leaked or simply had hired the same programmer. Or they may leave no clues as to who was behind it. Attribution to the guilty part is usually the single most difficult mission in IT-security - often it's just pure guesswork with little to no solid evidence to back it up, if you're lucky there's circumstantial evidence.
This case was no different. The first clue came from the IP the bad guys used to connect to the Bangladesh bank from. It was located in Pyongyang, North Korea. But, as I mentioned, this is not a conclusive verdict, as the IP may simply be planted false evidence to throw the analysts off their track. After the heist, the hackers used a data-wiper to scrub as much of their malware off the bank systems, but they didn't succeed in deleting all of it, some of the tools were still present, including the wiper.
Due to the scale of this operation, it caught the attention of every single IT-security person and IT-security company worldwide, who all of course wanted to know who and how they did it. With the remaining malware, a joint effort was made, comparing malware code to other malware code for similarities. Some was found in Poland, after an analyst noted the similarities from another suspected North Korean hack. Some was found in another infamous North Korean hack targeting Sony Pictures. More and more signs pointed towards the same actor. Some were false leads, the hackers seemed to be wanting to implicate the Russians did it, but failed quite miserably at that, just sprinkling random Russian words into the malware and making it way too obvious it was a ruse.
You may not believe this, but the North Korean government has one of the most notorious hacking groups in the world, known as the Lazarus Group. Some of its more well-known adventures include an extremely data-destructive hack of Sony Pictures (as punishment for releasing “The Interview”), creation of the ransomware WannaCry which was used against many targets worldwide (including hospitals), and various attempts at gathering information from governments and government-affiliated corporations all over the world. And, of course, this heist.
Eventually, after months of collaboration all over the world, the final verdict fell on North Korea, and specifically one of their programmers. His name is Park Jin Hyok, and worked for Chosun Expo - a front company for the North Korean government, located in Dalian (China) who used the funds of the fake corporation gained from legitimate programming jobs from customers worldwide to create the malware and plan the heist with all of its expenses. Of course he wasn't the sole person involved in this project, but it's the only person we know was in it.
This particular heist had been meticulously planned for several years, and Park Jin Hyok had moved to Dalian, set up fake IDs and built a network of contacts there to avoid suspicion. However, he didn't manage to delete all of his online footprints, and became the number one suspect when his internet activities suddenly came from Pyongyang, North Korea.
Additionally, several Chinese business men - many associated with the casino industry in China's Macau territory - were also charged and arrested for assisting with setting up the gambling rooms and coordinating the money laundering process. One unknown Chinese business man managed to get away with 31 million USD of the 80 million that remained after the heist, and as you would expect, he was never to be seen again.
With the middlemen from China paid off, not much remained of the original 1 billion to North Korea. But the heist has fascinated the whole IT-security world nonetheless.
I remember when the news of this case dropped to the IT-security world, who all wanted to take part in the hunt. It was a very fun time, we were all sitting at the edge of our seats waiting for the next update. I hope it was at least somewhat exciting for you too to read about, and thank you for reading this long post! If you liked it, please consider reblogging as it motivates me to write more. You may also like malware stuff I've written about before, such as Stuxnet or just plain evil malware that is a threat to our daily lives.
As always my inbox is open if you have any questions.
94 notes
·
View notes
Text
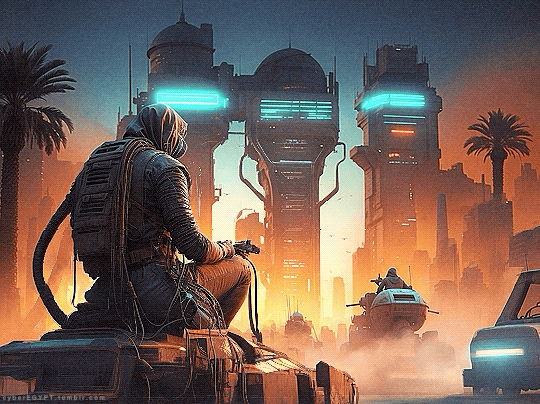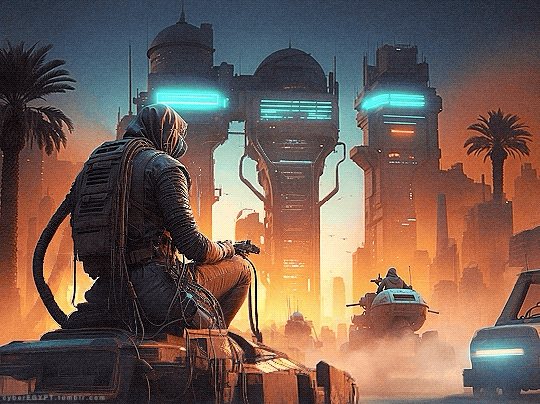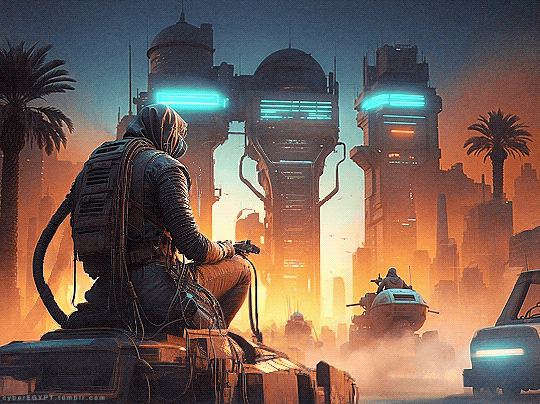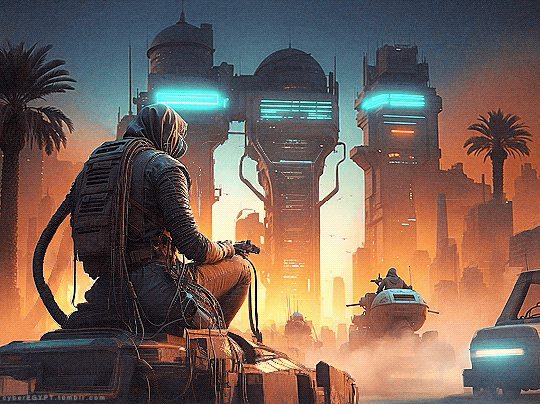
Cyberpunk Aesthetic + Ancient Egypt = Hacking and Attacking
#cyberpunk aesthetic#hacking#cybersecurity#hackers#malware#gif#neon lights#glow#desert#hacker#fremen#high tech#low life#armored vehicles#megacorp#ancient future#cityscape#dystopianfuture#cybernetics
9 notes
·
View notes
Text
🚨 Botnet Exploits GeoVision Zero-Day to Install Mirai Malware 🚨
WIRE TOR - The Ethical Hacking Services
2 notes
·
View notes
Text

Password hacked.
Watch the full video here: https://www.shutterstock.com/video/clip-1110370325-futuristic-cybersecurity-attack-concept-on-network-password?rid=1518998
#gif#animated gif#gif animation#motion graphics#mograph#cinema 4d#xparticles#circuit board#circuitboard#lines#connection#password#hack#hacker#unlock#unlocked#motherboard#neon#glowing#malware#internet#cyberspace#cybersecurity#network#digital#computer
17 notes
·
View notes
Text
(inspired by my last rb) you guys know that scene from tmnt rise where april tries to download an app but then a blocker pops up and it's just don going "donnie says no no no!" ¿ peak engineer core in my opinion
#pyro: MWHM MH MHHMWNM ?? (WHAT IS AN ENGIE BLOCKER ???)#engie: i put it on your phone so ya wouldn't get hacked or download anythin with malware because i know how much you're—#pyro: MHMMSM MFMFMDFHM MFHH !!! (THE ONLY THING IT'S BLOCKING IS ME FROM BEING COOL !!!)#future au or somthin#me at all times : how can i make this about texas toast#brick.ponders#cowboy up#tf2#tf2 engineer#tf2 hcs
2 notes
·
View notes
Text

Guard Your Cloud! Business communication security starts with proactive protection. This Cybersecurity Awareness Month, learn how Vitel Global helps you stay protected while staying connected.
Read our latest blog to discover how a secure cloud phone system keeps your business safe: https://www.vitelglobal.com/blog/significance-of-cybersecurity-in-cloud-phone-system/
#cybersecurity#cybersecurityawareness#cloud#businesssecurity#cloud communications#GuardYourcloud#Business#cloudcommunications#hacking#technology#cybercrime#tech#cyberattack#malware#data privacy#datasecurity#dataprotection
6 notes
·
View notes