#cybersecurity professional
Explore tagged Tumblr posts
Text
The Hacker's Guidebook:
Aspiring hackers! I’ve created a guide covering core cybersecurity concepts new hackers should master before tools. I break down networking, OS internals, & hacking tactics. Recognize hacking as lifelong journey—arm yourself with the basics!
Core Concepts for Budding Cybersecurity Enthusiasts The Building Blocks of Ethical Hacking So you want to become an ethical hacker and enter the exciting world of cybersecurity. That’s awesome! However, before you dive headfirst into firing up Kali Linux and hacking everything in sight, it’s vital to build up your foundational knowledge across several InfoSec domains. Mastering the fundamentals…

View On WordPress
#attacking tools#basics of hacking#cross site scripting#Cyber Threat Defense#cybersec#cybersecurity learning#cybersecurity professional#Ethical Hacking#fundamentals#hacking basics#hacking for beginners#hacking guide#hacking networks#hacking web#how to hack#infosec#learn hacking#learn to hack#linux#malware basics#malware for hacking#metasploit#netsec#network hacking#nmap#operating systems#Pentesting#phishing#phishing attacks#Red Team
34 notes
·
View notes
Text
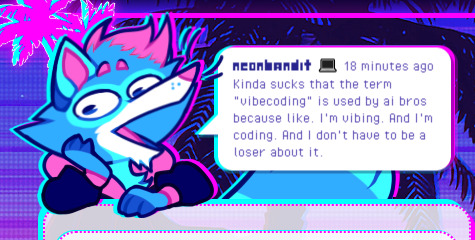
I said what I said
#jay talks#neocities tag#For those who don't know#vibecoding is basically telling an ai to do the code for you#Like I cannot begin to imagine the amount of mistakes an AI would make#and since you're actively handicapping yourself by not learning any of the problem solving and troubleshooting skills that come with this#You won't notice any mistakes the same way ai artists don't have a trained eye to know their art looks like dogshit#My code is absolutely not perfect#far from it#but when this stuff is getting used in actual professional environments#issues like cybersecurity and privacy leaks can't help but come to mind
27 notes
·
View notes
Text
Can you imagine if they actually do call an election on 4th July
28 notes
·
View notes
Text
Passkeys being supported so many places lately are the best thing to happen to authentication in the last 20 years.
If you have a good password manager and save passkeys to it, it’s finally as convenient to sign in as it was back when nothing had multifactor and you just typed your one memorized password into everything.
#btw speaking of password managers#if you’re still using LastPass switch#even after their huge breach which was only even as big an deal as it was because their security is so much worse than the competition#i see so many people using it‚ including IT professionals with cybersecurity responsibilities#seriously go find something better#at my last job i actually did a lot of research on the actual security of password managers and compared a bunch of options#and the two i would recommend based on that research are 1Password and Bitwarden#or for a FOSS option there’s KeePassXC
3 notes
·
View notes
Text
Big life plans that I have been working on since April that would have come to fruition in less than a month have completely fallen through (and it’s not even because I did something wrong, it’s literally circumstances that I have no control over and should have never been an issue in the first place🙃) and all I want to do is get lost in some silly little stories but tumblr wants to act like a lil ho and not load any content and says I don’t follow anyone and can’t search anything 🙃🙃🙃 I’ve suffered enough today just let me read 😭😭
#tumblr don’t tell me to add tags so people can find my post find my fn content#you busted ass bitch#i am unwell#but I’m also laughing because of the irony of being a cybersecurity professional crying over trouble shooting a site and app#my life is a joke so might as well laugh 🥲🤙🏽#I won’t be upset about this in like 5 minutes but still..tumblr your moms a ho
2 notes
·
View notes
Text
Nakul Thakore - A Highly Skilled Business Professional | Contently
Nakul Thakore's ability to analyze complex data sets and implement effective solutions ensures valuable outcomes for organizations.
2 notes
·
View notes
Text
How Disrespect in Business—Like Ignoring Emails and Turning Down Networking—Can Lead to Cyber Attacks
Let’s get something straight right now: your crappy communication habits aren’t just annoying—they’re dangerous. That ignored email chain? It might be the reason your company gets ransomwared next month. That networking event you blew off because you were “too busy”? Could’ve been where you learned about the security vulnerability currently festering in your system. Disrespect in business isn’t…
#business communication#company culture#cyber attacks#cybersecurity#data breaches#digital security#email response#information security#networking importance#professional respect#ransomware prevention#security protocols#security vulnerabilities#workplace communication
0 notes
Text
The Importance of WordPress Updates: Protecting Your Business from Cyber Threats
As a business owner, having a website is crucial for establishing an online presence and reaching out to potential customers. However, with the increasing number of cyber attacks, website security has become a top priority. WordPress, being one of the most popular Content Management Systems (CMS), is a frequent target for hackers. In this article, we will discuss the importance of WordPress updates, especially from a cybersecurity perspective, and why it's crucial to protect your business interests.
Why Hackers Target WordPress Websites
WordPress is a popular CMS, powering over 40% of the world's websites. Its widespread adoption makes it an attractive target for hackers. Moreover, the open-source nature of WordPress means that vulnerabilities can be easily discovered and exploited. When a security hole is found in WordPress, it quickly spreads to malicious actors, who then attempt to attack websites with known vulnerabilities. This is why keeping WordPress up to date is crucial in preventing cyber attacks.
The Risks of Outdated WordPress
Failing to update WordPress can lead to serious consequences, including:
Data breaches: Outdated WordPress versions can leave your website vulnerable to data breaches, compromising sensitive information and putting your customers at risk.
Malware infections: Hackers can inject malware into your website, leading to blacklisting by search engines and damaging your online reputation.
Financial losses: A hacked website can result in financial losses, either through stolen customer data or by disrupting your online business operations.
The Importance of WordPress Updates
Updating WordPress is essential in preventing cyber attacks. New releases of WordPress often include security patches and fixes for known vulnerabilities. By keeping your WordPress version up to date, you significantly reduce the risk of your website being compromised. Additionally, updating WordPress ensures that your website continues to function smoothly, without breaking due to compatibility issues with themes and plugins.
Amity IT's WordPress Updates Service
At Amity IT, we understand the importance of keeping your WordPress website up to date. Our WordPress Updates service is designed to ensure that your website remains secure and functions optimally. Our team of experts will perform regular updates on a schedule that suits your business needs, whether it's monthly or quarterly. Our service includes:
Updates of WordPress core
Updates of plugins compatible with the latest version of WordPress
Rollback of updates if functionality is compromised
By choosing Amity IT's WordPress Updates service, you can rest assured that your website is protected from cyber threats. Our team is based in Penrith and serves the Western Sydney area, providing local support and expertise.
Conclusion
In conclusion, keeping your WordPress website up to date is crucial in protecting your business from cyber threats. By understanding the risks associated with outdated WordPress and the importance of updates, you can take proactive steps to secure your online presence. Amity IT's WordPress Updates service is designed to provide you with peace of mind, knowing that your website is secure and functioning optimally. Visit our WordPress Updates page today to learn more about our service and how we can help protect your business interests: https://www.amityit.com.au/services/websites/wordpress-updates.
#WordPress updates#Cybersecurity#Business interests#Hackers#Vulnerabilities#Plugins and themes#Sensitive data#Trust and reputation#Professional WordPress update service#Amity IT Penrith and Western Sydney
0 notes
Text
Find Out Expert Tip on How You Can Get a $200K Cybersecurity Job in 90 Days
youtube
Are you ready to take your career to the next level and earn a lucrative salary in cybersecurity? Look no further! In this groundbreaking webinar, cybersecurity expert Tom Michel reveals the secrets to earning over $200,000 in just 45 days, without needing a degree or prior technical knowledge.
With over 10 years of experience in the field, Tom Michel has helped over 600 individuals transform their careers and achieve financial success in cybersecurity. Now, he's ready to share his proven strategies with you. In this webinar, you'll discover: 🌟The high demand for cybersecurity professionals in today's digital world. 🌟How you can earn multiple six figures without leaving your current job or home. 🌟Practical training methods to equip you with the skills and confidence needed to succeed. 🌟Access to training materials, hands-on experience, and industry-recognized certifications. 🌟Personalized support from Tom Michel and his team throughout your journey. 🌟Real-life success stories from individuals who have achieved financial freedom through cybersecurity. Don't miss out on this life-changing opportunity to elevate your career and secure your financial future. Book your spot in our exclusive cybersecurity training program today and start your journey towards a $200,000 salary! Subscribe now and take the first step towards a rewarding career in cybersecurity. Your future starts here! Click here to book a discovery call. https://sixfigurecybersecurityjobs.co... Join Tolulope Michael, a seasoned cybersecurity professional with over a decade of experience, as he unveils the five game-changing secrets to landing multiple six-figure cybersecurity jobs in just 45 days! Discover why the cybersecurity industry is a goldmine with over 2 million vacant positions worldwide. Learn how the U.S. government's multi-million dollar cybersecurity contracts create unprecedented opportunities. Tolulope emphasizes the Governance, Risk & Compliance Management (GRC) domain, revealing why it's the pathway to success without the need for programming skills. 🌟 Proven Results: Tolulope has helped over 600 individuals achieve cybersecurity readiness in just 45 days, securing high-paying job offers. Hear success stories from those who transformed their careers using his fail-proof strategies.
#$200000 salary in cybersecurity#career advancement#professional development#multiple six figures#interview preparation#high paying salary in cybersecurity#Youtube
0 notes
Text
Building Your Own Cyberdeck:
What do you do when you have extra time between a job and your next? How about building your own Cyberdeck? Check this article out for tips on building your own!
The Ultimate Hacker Project For aspiring cybersecurity professionals, cyberpunk enthusiasts, hardware hackers, and circuit benders, one of the best hands-on projects you can take on is building your own cyberdeck. Despite overwhelming schedules full of training programs, full time work weeks, sometimes limited funds, and the endless possibilities of hardware combinations, many fans of the…

View On WordPress
#Cyber#Cyber Security#cyberdeck#cyberpunk#Cybersecurity Specialist#Ethical Hacking#hack#hacker#infosec#IT#IT professional#mobile#mobile computer#Pentesting#programming#project
30 notes
·
View notes
Text
Find Out Expert Tip on How You Can Get a $200K Cybersecurity Job in 90 Days
youtube
Are you ready to take your career to the next level and earn a lucrative salary in cybersecurity? Look no further! In this groundbreaking webinar, cybersecurity expert Tom Michel reveals the secrets to earning over $200,000 in just 45 days, without needing a degree or prior technical knowledge.
With over 10 years of experience in the field, Tom Michel has helped over 600 individuals transform their careers and achieve financial success in cybersecurity. Now, he's ready to share his proven strategies with you. In this webinar, you'll discover:
🌟The high demand for cybersecurity professionals in today's digital world.
🌟How you can earn multiple six figures without leaving your current job or home.
🌟Practical training methods to equip you with the skills and confidence needed to succeed.
🌟Access to training materials, hands-on experience, and industry-recognized certifications.
🌟Personalized support from Tom Michel and his team throughout your journey.
🌟Real-life success stories from individuals who have achieved financial freedom through cybersecurity.
Don't miss out on this life-changing opportunity to elevate your career and secure your financial future. Book your spot in our exclusive cybersecurity training program today and start your journey towards a $200,000 salary! Subscribe now and take the first step towards a rewarding career in cybersecurity. Your future starts here! Click here to book a discovery call.
://sixfigurecybersecurityjobs.co... Join Tolulope Michael, a seasoned cybersecurity professional with over a decade of experience, as he unveils the five game-changing secrets to landing multiple six-figure cybersecurity jobs in just 45 days! Discover why the cybersecurity industry is a goldmine with over 2 million vacant positions worldwide. Learn how the U.S. government's multi-million dollar cybersecurity contracts create unprecedented opportunities.
Tolulope emphasizes the Governance, Risk & Compliance Management (GRC) domain, revealing why it's the pathway to success without the need for programming skills.
🌟 Proven Results: Tolulope has helped over 600 individuals achieve cybersecurity readiness in just 45 days, securing high-paying job offers. Hear success stories from those who transformed their careers using his fail-proof strategies.
🔍 Exclusive Program: Experience hands-on practical training, live classes, one-on-one sessions, and effective exercises designed for executives seeking additional income.
This flexible program fits your schedule and doesn't require prior tech knowledge. 💼 Limited Time Offer: Act fast to book a discovery call with Tolulope's team and transform your life forever. Don't miss this chance to boost your income and advance your career in the lucrative field of cybersecurity! Click the link below NOW to secure your spot!
#cybersecurity#salary increase#professional development#multiple six figures#industry demand#$200000 salary in cybersecurity#high paying salary in cybersecurity#Youtube
0 notes
Text
The IT Guy: The Unsung Hero of the Office
Every office has one. That mystical figure who emerges from the depths of the server room like a tech-savvy wizard, wielding an arsenal of USB sticks and an uncanny ability to fix things just by looking at them. He’s the one who holds the power to make or break your workday. He is… The IT Guy. Chapter 1: The IT Guy’s Natural Habitat The IT guy doesn’t have a normal workspace. No cubicle farm…
#coding struggles#computer issues at work#cybersecurity humor#data security jokes#fiction#funny IT experiences#funny IT guy experiences#funny IT issues#funny IT stories#funny tech problems#funny tech support#hardware repair mishaps#helpdesk disasters#IT career humor#IT department chaos#IT department jokes#IT desk shenanigans#IT guy at work#IT guy daily life#IT guy humor#IT guy office survival#IT guy problems#IT guy stereotypes#IT guy stories#IT jokes#IT jokes and puns#IT memes#IT professional struggles#IT specialist life#IT support chaos
0 notes
Text
Network Right
Network Right is the leading Managed IT Services and IT Support provider in the San Francisco Bay Area, serving startups and tech companies across San Francisco, San Jose, Oakland, Berkeley, San Mateo, Santa Clara, and Alameda. Offering comprehensive remote and onsite IT solutions, their services include IT infrastructure, IT security, data backup, network management support, VoIP, A/V solutions, and more. They also provide IT Helpdesk support and Fractional IT Manager roles, ensuring full-spectrum IT management. Trusted by fast-growing companies, Network Right combines expert solutions with unparalleled customer support to accelerate business growth.
Contact us:
333 Bryant St #250, San Francisco, CA 94107
(415) 209-5808
Opening Hours:
Monday to Friday: 9 AM–6 PM
Saturday to Sunday: Closed
Social Links:
https://www.linkedin.com/company/networkright/
#IT Support#Managed IT Services#IT Helpdesk#IT Infrastructure#IT Security#Data Backup#Network Management#VoIP Solutions#A/V Solutions#Cybersecurity#IT Consulting#Professional IT Services
1 note
·
View note
Text
At M.Kumarasamy College of Engineering (MKCE), we emphasize the significance of engineering ethics in shaping responsible engineers. Engineering ethics guide decision-making, foster professionalism, and ensure societal welfare. Our curriculum integrates these principles, teaching students to consider the long-term impacts of their work. Students are trained in truthfulness, transparency, and ethical communication, while also prioritizing public safety and environmental sustainability. We focus on risk management and encourage innovation in sustainable technologies. Our programs also address contemporary challenges like artificial intelligence and cybersecurity, preparing students to tackle these with ethical responsibility. MKCE nurtures future engineers who lead with integrity and contribute to society’s well-being.
To know more : https://mkce.ac.in/blog/engineering-ethics-and-navigating-the-challenges-of-modern-technologies/
#mkce college#top 10 colleges in tn#engineering college in karur#best engineering college in karur#private college#libary#mkce#best engineering college#mkce.ac.in#engineering college#• Engineering Ethics#Engineering Decision Making#AI and Ethics#Cybersecurity Ethics#Public Safety in Engineering#• Environmental Sustainability in Engineering#Professional Responsibility#Risk Management in Engineering#Artificial Intelligence Challenges#Engineering Leadership#• Data Privacy and Security#Ethical Engineering Practices#Sustainable Engineering Solutions#• Technological Innovation and Ethics#Technological Innovation and Ethics#MKCE Engineering Curriculum#• Social Responsibility in Engineering#• Engineering Ethics in AI#Workplace Ethics in Engineering#Collaboration in Engineering Projects
0 notes
Text
0 notes
Text
Frequently Asked Questions on CISM Certification
The Certified Information Security Manager (CISM) certification, offered by ISACA, is one of the most sought-after credentials in the information security domain. It validates an individual’s expertise in managing and governing an organization’s security program. Whether you’re an aspiring CISM professional or exploring the idea of certification, this article addresses some of the most frequently asked questions about CISM.

1. What is the CISM Certification?
CISM (Certified Information Security Manager) is a globally recognized certification designed for professionals who manage enterprise information security programs. Unlike certifications that focus on technical aspects, CISM emphasizes risk management, governance, and aligning security with business goals.
2. Who Should Pursue CISM?
CISM is ideal for:
Information security managers
Aspiring IT security professionals
IT consultants focused on security
Risk management and compliance specialists
3. What Are the Prerequisites for CISM?
To earn the CISM certification, you must meet the following criteria:
Pass the CISM exam.
Have at least five years of work experience in information security management.
Experience must be across three or more CISM domains, with a waiver of up to two years available for certain qualifications or certifications (e.g., CISSP, CISA, or a related degree).
4. What Are the CISM Domains?
The CISM certification exam is divided into four domains:
Information Security Governance (17%) stablishing and managing the security strategy.
Information Risk Management (20%) Identifying and mitigating risks.
Information Security Program Development and Management (33%) Designing and managing the organization’s security program.
Information Security Incident Management (30%) Preparing for and responding to security incidents.
5. How Do I Register for the CISM Exam?
To register:
Visit ISACA’s official website.
Create an account if you don’t already have one.
Schedule the exam at a convenient time and location through ISACA’s partner test centers.
Pay the exam fee: $575 for ISACA members and $760 for non-members (subject to change).
6. What Is the Format of the CISM Exam?
The CISM exam consists of:
150 multiple-choice questions
A four-hour time limit
Questions that evaluate knowledge across the four domains
A scaled score ranging from 200 to 800, with 450 as the passing mark
7. How Can I Prepare for the CISM Exam?
Preparation tips include:
Study the CISM Review Manual: ISACA’s official manual is an essential resource.
Practice Questions: Use ISACA’s question database for realistic practice.
Attend Training Programs: Enroll in instructor-led or online courses offered by training providers like NovelVista, Simplilearn, or ISACA.
Join Study Groups: Leverage forums and communities to share insights and tips.
Time Management: Practice under timed conditions to simulate the exam environment.
8. What Is the Cost of the CISM Certification?
The total cost includes:
Exam registration fees ($575-$760)
Study materials (varies by provider)
Optional training programs (cost depends on the mode and duration)
9. What Are the Benefits of CISM Certification?
Global Recognition: CISM is respected worldwide as a premier security management certification.
Higher Earning Potential: Certified professionals often command higher salaries.
Career Advancement: Opens doors to leadership roles in IT security.
Improved Knowledge: Enhances your understanding of aligning security with business objectives.
10. How Long Is the Certification Valid?
CISM certification is valid for three years. To maintain it, you must:
Earn 120 Continuing Professional Education (CPE) credits during the three years.
Pay an annual maintenance fee of $45 for ISACA members or $85 for non-members.
11. What Jobs Can I Get with a CISM Certification?
CISM-certified professionals are qualified for roles such as:
Information Security Manager
IT Risk Manager
Security Consultant
Chief Information Security Officer (CISO)
12. How Does CISM Compare to CISSP?
Both certifications are highly respected, but they serve different purposes:
CISM focuses on management, governance, and aligning security strategies with business goals.
CISSP emphasizes technical expertise and security practices. Your choice depends on whether you aspire to management (CISM) or technical (CISSP) roles.
13. What Are Common Challenges in CISM Preparation?
Some challenges include:
Balancing study time with work responsibilities
Understanding managerial concepts if your background is technical
Staying updated on evolving security standards
14. Are There Any Alternatives to CISM?
Yes, alternatives include:
CISSP (Certified Information Systems Security Professional)
CISA (Certified Information Systems Auditor)
CRISC (Certified in Risk and Information Systems Control)
ISO 27001 Lead Implementer
In conclusion, the CISM certification and CISM Training is a valuable credential for professionals aiming to excel in information security management. By addressing these frequently asked questions, we hope you gain a clearer understanding of what it takes to achieve this milestone and how it can advance your career.
#CISM Certification#CISM Course#CISM Training#CISM#CISM Certified Professionals#CISM FAQ#Frequently Asked Questions#Cybersecurity#Security Challenges
0 notes