#data security software
Explore tagged Tumblr posts
Text
How to install NewPipe on Android
NewPipe is a YouTube replacement client for Android devices. It's open-source (meaning, you can see all of their code as you please), privacy-oriented, lightweight, and supports features that are normally locked behind a YouTube Premium paywall.
Disclaimer: I am not affiliated with NewPipe, YouTube, Android, Google, Alphabet Inc, or any other brand or name mentioned here. I made this guide to help my friends who were curious.
NewPipe's Website: https://newpipe.net/
The GitHub Repository
Step 0. Compatibility check
Make sure you're running an Android device! This won't work on an Apple device of any kind! Also, for those more tech-savvy among you, if you have the F-Droid store installed, you can download NewPipe straight from there!
Step 1. Downloading
Go to NewPipe's Github repo (repository, the codebase or where all of the code is stored). Scroll to the bottom of the page until you see "Releases". Click on the one that says "Latest" next to it in a little green bubble:

Your version number (v#...) will be different if you're reading this in the future! That's okay. Scroll past the changelog (unless you want to read it!) until you find "Assets":

Click on the first one, the one with the little cube ending in .apk. APK files are Android Package (Kit) and are the main format for downloading apps. Once you click on the link, it should begin downloading or your browser will ask you to confirm that you want to download this file. You should always verify the filename matches what you expect it to be (namely, the file format) before attempting to install! It might take a few moments for the file to download depending on your internet connection.
Step 2. Installation
Once you have the file downloaded, you can click the download popup in your notification bar or find the file in your device's file system. One of 2 things will happen:
You will get a popup asking if you want to install an APK by the name of NewPipe - confirm that you do (and make sure the app is really NewPipe!) and it will install automatically. You can then click "Open" to open the app and begin using it.
You will get a popup warning you that you have the ability to install apps from unknown sources disabled and that you can't install this. This is normal and does not mean that you downloaded the wrong thing.
If you got the first popup, continue past this step. For those of you who got the second, let's go over what this means.
By default, most Androids have this setting disabled. This is for security purposes, so you can't accidentally install a malicious app from the whole internet. If you enable this setting (allow installations from unknown/unsigned sources), you are theoretically putting yourself at risk. Realistically, you're probably fine. But, after installing NewPipe, you can always re-disable the setting if it makes you more comfortable. That will prevent you from installing updates in the future, but it can always be re-enabled.
Ready to turn that setting on? It will vary by your individual device! Some devices will take you directly to the page with the setting upon failed installation, and some you will just have to find it yourself using the searchbar in settings.
Once you've allowed installations from unknown sources (wording may vary slightly), try to repeat the steps above of clicking the download popup or finding the APK in your files and trying to install it. It should work correctly this time!
Step 3. Updating NewPipe
Like most apps, NewPipe is in development currently and frequently has new versions released to improve it and fix bugs. Unlike most apps, NewPipe needs to be manually updated, since we haven't downloaded through the Google Play store.
To update NewPipe, all you have to do is follow the above steps for installing the app, except that when you get the popup asking to install it, it will instead say "Update". That's it! NewPipe and Android handle the rest.
NewPipe also has popup notifications for when the app has a new update, so you don't have to worry about checking the GitHub for a new release. Just click on the "A new version is available" popup and it should take you directly to the webpage.
That's it! Enjoy browsing videos in peace without ads and with the ability to download and so much more. Pro tip: you can copy paste YouTube links into the NewPipe search bar to go directly to that video/playlist/channel.
#newpipe#youtube#youtube client#youtube replacement#how to install newpipe#android#android apk#android app#images#text#links#image descriptions#privacy#data privacy#internet privacy#big tech#data security#github#software#database#opensource#open source#newpipe app
30 notes
·
View notes
Text
Abathur

At Abathur, we believe technology should empower, not complicate.
Our mission is to provide seamless, scalable, and secure solutions for businesses of all sizes. With a team of experts specializing in various tech domains, we ensure our clients stay ahead in an ever-evolving digital landscape.
Why Choose Us? Expert-Led Innovation – Our team is built on experience and expertise. Security First Approach – Cybersecurity is embedded in all our solutions. Scalable & Future-Proof – We design solutions that grow with you. Client-Centric Focus – Your success is our priority.
#Software Development#Web Development#Mobile App Development#API Integration#Artificial Intelligence#Machine Learning#Predictive Analytics#AI Automation#NLP#Data Analytics#Business Intelligence#Big Data#Cybersecurity#Risk Management#Penetration Testing#Cloud Security#Network Security#Compliance#Networking#IT Support#Cloud Management#AWS#Azure#DevOps#Server Management#Digital Marketing#SEO#Social Media Marketing#Paid Ads#Content Marketing
2 notes
·
View notes
Text
How to check if your computer is being monitored
In today's digital age, the issue of privacy and security is more pressing than ever. Whether you’re a casual user or a professional, understanding if your computer is being monitored is crucial. This guide will delve into the signs of monitoring, tools to detect it, and steps to safeguard your privacy.

Understanding Computer Monitoring
Before diving into the signs and detection methods, it’s essential to understand what computer monitoring entails. Monitoring can involve tracking your online activity, keystrokes, file access, and even webcam usage. This can be done by malicious software (malware), spyware, or legitimate monitoring software used by employers or parents.
Types of Monitoring
Malware and Spyware: These are malicious programs that can be installed without your knowledge. They can track your activities and send data back to an attacker.
Keyloggers: This type of software records keystrokes, capturing sensitive information like passwords and personal messages.
Remote Access Tools (RATs): These tools allow someone to control your computer remotely, monitoring your screen, accessing files, and even using your webcam.
Legitimate Monitoring Software: Often used in corporate environments, this software tracks employee activity for productivity or compliance reasons. While legal, it can still infringe on personal privacy.
Signs That Your Computer May Be Monitored
Recognizing the signs that your computer might be monitored is the first step in protecting yourself.
1. Unusual System Behavior
Slow Performance: If your computer suddenly becomes sluggish, it might be due to monitoring software consuming resources.
Frequent Crashes or Freezes: Unexpected system crashes can indicate underlying issues, including malware.
2. Suspicious Programs
Unknown Applications: Check your installed programs for any unfamiliar applications. Many monitoring tools disguise themselves as legitimate software.
High Resource Usage: Use the Task Manager (Windows) or Activity Monitor (Mac) to look for processes consuming excessive CPU or memory.
3. Network Activity
Unexplained Network Traffic: Use network monitoring tools to check for unusual data being sent or received. High outbound traffic could indicate that data is being transmitted without your consent.
Blocked Ports: Monitoring software often uses specific ports to communicate. If you notice blocked ports that you didn’t configure, it could be a red flag.
4. Webcam and Microphone Behavior
Indicator Light Activation: If your webcam or microphone is being accessed without your knowledge, the indicator light may be on even when you're not using it.
Unexpected Recordings: Check for unusual files that could be recordings made by your microphone or webcam.
5. Browser Behavior
Unusual Browser Extensions: Check for extensions you didn’t install. Some can track your browsing activity.
Unexpected Redirects: Frequent redirects to strange sites or altered search results can indicate tracking.
6. Security Alerts
Antivirus Notifications: If your antivirus software frequently alerts you about threats, it may indicate that monitoring software is present.
Firewall Alerts: Unusual outgoing connection attempts can suggest that an unauthorized program is trying to access the internet.
Tools to Detect Monitoring Software
If you suspect that your computer is being monitored, several tools can help you investigate further.
1. Antivirus and Anti-Malware Software
Using a reliable antivirus or anti-malware program can help detect and remove malicious software. Some popular options include:
Malwarebytes: Excellent for detecting and removing malware and spyware.
Norton: Offers comprehensive protection against various types of threats.
2. Network Monitoring Tools
Tools like Wireshark can help analyze network traffic and identify suspicious activity. You can monitor data packets to see if there are any unexpected connections.
3. Task Manager / Activity Monitor
Regularly check the Task Manager (Windows) or Activity Monitor (Mac) for processes that look unfamiliar or suspicious. Research any questionable applications before taking action.
4. System Scans
Use built-in tools to perform system scans:
Windows Defender: Run a full scan for malware and spyware.
Mac’s Built-in Security Features: Use the Malware Removal Tool for additional scanning.
5. Firewall Monitoring
Make sure your firewall is active and monitor logs for any unusual activity. A firewall can block unauthorized access attempts and alert you to potential threats.
Steps to Protect Your Privacy
If you determine that your computer is being monitored or you want to prevent it from happening, follow these steps to enhance your security.
1. Update Your Software Regularly
Keeping your operating system and all software up-to-date ensures that you have the latest security patches. This reduces vulnerabilities that can be exploited by monitoring tools.
2. Use Strong Passwords
Implement strong, unique passwords for all your accounts and devices. Consider using a password manager to generate and store complex passwords securely.
3. Enable Two-Factor Authentication
Two-factor authentication (2FA) adds an extra layer of security by requiring a second form of verification, making unauthorized access much more difficult.
4. Install a Firewall
Ensure you have a firewall activated, whether it’s built-in (like Windows Firewall) or third-party. This helps control incoming and outgoing network traffic.
5. Be Cautious with Downloads
Avoid downloading software from untrusted sources, as this can introduce malware to your system. Always verify the legitimacy of software before installing it.
6. Regularly Review Permissions
Check application permissions on your device regularly. Revoke access for any apps that do not need to access your camera, microphone, or location.
7. Use a VPN
A Virtual Private Network (VPN) encrypts your internet connection, making it difficult for anyone to monitor your online activities.
8. Educate Yourself
Stay informed about the latest cybersecurity threats and best practices. Knowledge is your best defense against monitoring.
When to Seek Professional Help
If you suspect your computer is being monitored and cannot identify or remove the software yourself, consider seeking professional help. Cybersecurity experts can perform a thorough analysis of your system and provide tailored solutions.
Conclusion
Understanding if your computer is being monitored is vital for protecting your privacy. By recognizing the signs, utilizing detection tools, and implementing security measures, you can safeguard your personal information. Remember, vigilance is key in the ever-evolving landscape of digital security. Stay informed, proactive, and secure in your online presence.
#Computer Security#Online Privacy#Cybersecurity#Monitoring Software#Malware Detection#Privacy Protection#Digital Security#Keyloggers#Network Monitoring#Antivirus#VPN#Internet Safety#Personal Data Security#Remote Access Tools#Digital Awareness
2 notes
·
View notes
Text
Cobwebs Spy Software Locks Onto Protesters: Israeli Social Media Mining homeland security contractor
youtube

#cobwebs#spy#software#protest#privacy#data privacy#online privacy#internet privacy#invasion of privacy#social networks#social media#internet#class war#all cops are bastards#all cops are bad#all cops are pigs#israel#israhell#homeland security#spyware#infotech#information technology#i.t.#it#israel is a terrorist state#israel is committing genocide#israeli war crimes#israel is an apartheid state#israel is a war criminal#benjamin netanyahu
2 notes
·
View notes
Text
85% Discount + 2 month Free. Unveiling the Power of Surfshark VPN: Your Ultimate Online Privacy Solution. Surfshark Vpn Full Review In Article Below.
If you are looking for a VPN program for the computer or for Android, iPhone, and Mac... I promise you that this VPN is what you are looking for. Read the description of the VPN on the Medium platform and make your decision. I am here just to help you and get some followers on the Tumblr platform.
#best vpn#vpn#data privacy#online privacy#cyber security#free vpn#vpnservice#clone vpn#software#hidden#streaming#livestream#vps server#vpn reviews#vpn software#vpn service
2 notes
·
View notes
Text
THE IMPORTANCE OF DATA MANAGEMENT AND DATA SECURITY IN HEALTHCARE
Data is the lifeblood of the healthcare industry. It encompasses patient records, treatment plans, medical histories, and an array of vital information that healthcare providers rely on to deliver the best possible care. As the healthcare landscape becomes increasingly digital, the importance of data management and data security has never been more critical. In this Blog, we’ll delve into the significance of safeguarding patient data and how E_care, a leader in healthcare management software, prioritizes data security to protect sensitive patient information.
Preserving Patient Confidentiality:
Compliance with Data Protection Regulations:
The Importance of Data Management & Data Security in Healthcare
Data Encryption:
Access Control:
Data Backups and Recovery:
Security Audits and Monitoring:
Education and Training:
Data Security as a Competitive Advantage:
E Care Hospital Management Software
Our Social medias:
LinkedIn: E CARE - Hospital Management Software
Facebook: E-care
Instagram: e_care_hms
X: E-Care Hospital Management Software
#e care#hms#hospital management software#hospital management system#health#data management#data security
3 notes
·
View notes
Link
2 notes
·
View notes
Text

FYI: Not anywhere near a complete solution: but I run an app called Little Snitch on my Mac that warns me when a program unexpectedly tries to use the internet. (I can set which apps have permission, with granularity down to specific tcp/ip port numbers).
It's a bit technical to use, and requires some setup; but it does catch (and prevent) situations when some app unexpectedly tries to pull something. (Believe it runs on Windows as well as the Mac.)
I believe everything should be offline, I believe that every time something that is not your internet browser (and I'm being generous here) should have a big red alert that says THIS PIECE OF SHIT PROGRAM NEEDS TO CONNECT TO THE INTERNET AND REQUESTS YOUR CONSENT TO DO THIS SPECIFIC THING, and you had to touch a big red button and it would disconnect as soon as you close it.
#internet privacy#computer privacy#data privacy#corporate overreach#software overreach#privacy#intrusive software#computer security#enshittification
29K notes
·
View notes
Text
When Trusted Tools Turn Rogue: Hackers Exploit Salesforce App to Breach Global Firms
In a chilling revelation, Google has exposed a sophisticated cyber campaign where hackers are manipulating a Salesforce-related app to steal sensitive corporate data and extort companies. The attackers have successfully targeted organizations across Europe and the Americas by convincing employees to install a tampered version of Salesforce's Data Loader. This attack, tracked by Google's Threat Intelligence Group under the identifier UNC6040, underscores the growing vulnerabilities in enterprise software environments and the alarming ease with which cybercriminals can infiltrate even the most trusted digital infrastructures.

#Salesforce app breach#Google cyber threat report#UNC6040 hackers#Salesforce Data Loader attack#cyberattack global firms#enterprise software hack#cloud security breach#social engineering cybercrime#Google Threat Intelligence
0 notes
Text
I haven’t really seen any of the more recent U.S. election news hitting tumblr yet so here’s some updates (now edited with sources added):
There’s evidence of Trump cheating and interfering with the election.
Possible Russian interference.
Mail-in ballots are not being counted or “recognized” in multiple (notably swing) states.
30+ bomb threats were called in and shut down polling stations on Election Day.
20+ million votes are still unaccounted for, and that’s just to have the same voter turnout as 2020.
There was record voter turnout and new/first-time voter registration this year. We definitely should be well over the turnout in 2020.
U.S. citizens are using this site to demand, not only a recount, but a complete investigation into election fraud and interference for the reasons stated above:
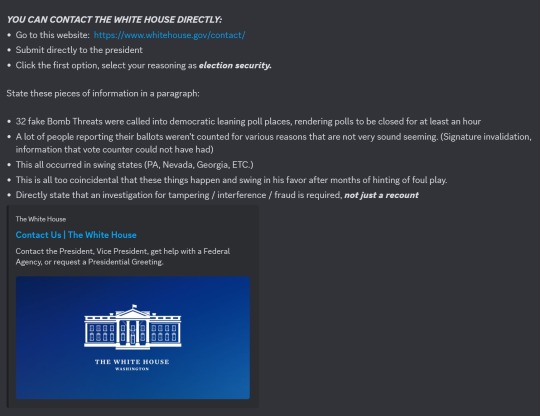
Here is what I submitted as an example:
An investigation for election interference and fraud is required. We desperately need a recount or even a revote. The American people deserve the right to a free and fair election. There has been evidence unveiled of Trump cheating and committing election fraud which is illegal. There is some evidence of possible Russian interference. At least 30+ bomb threats were called in to polling places. Multiple, notably swing states, have ballots unaccounted for and voting machines not registering votes. Ballots and ballot boxes were tampered with and burned. Over 20 million votes that we know of are unaccounted for. With record turnout and new voter registration this year, there should be no possibility that there are less votes than even in the 2020 election.
Sources (working on finding more links but if anyone wants to add info, it’s appreciated):
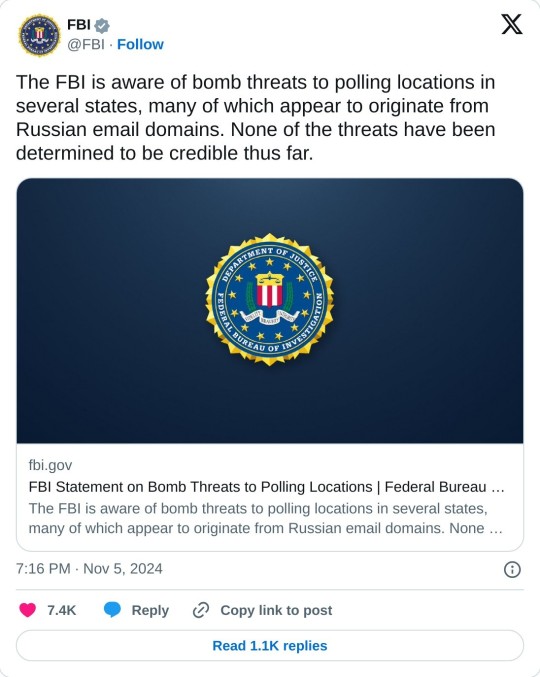
FBI addressing Russian interference and bomb threats:
Emails released by Rachael Bellis (private account, can’t share original tweet) confirming Trump committing election fraud:
Pennsylvania's Centre County officials say they are working with their ballot scanner vendor to figure out why the county's mail-in ballot data is "not being recognized when uploaded to the elections software:”

Wisconsin recount:
[ID:
Multiple screenshots and images.
The first is a screenshot with a link and information for contacting the White House directly regarding election fraud. The instructions include choosing to leave a comment to President Joe Biden directly and to select election security as the reason.
The screenshot then instructs people to include any or all of the following information in a paragraph as a comment to the president:
32 fake bomb threats were called into Democratic leaning poll places, rendering polling places closed for at least an hour.
A lot of people reporting their ballots were not counted for various reasons.
This all occurred in swing states.
This is too coincidental that these things happen and swing in his favor after months of hinting at foul play.
Directly state that an investigation for tampering, interference, fraud is required, not just a recount.
The second image is from the FBI Twitter account that reads:
The FBI is aware of bomb threats to polling locations in several states, many of which appear to originate from Russian email domains. None of the threats have been determined to be credible thus far. https://t.co/j3YfajVK1m — FBI (@FBI) November 5, 2024
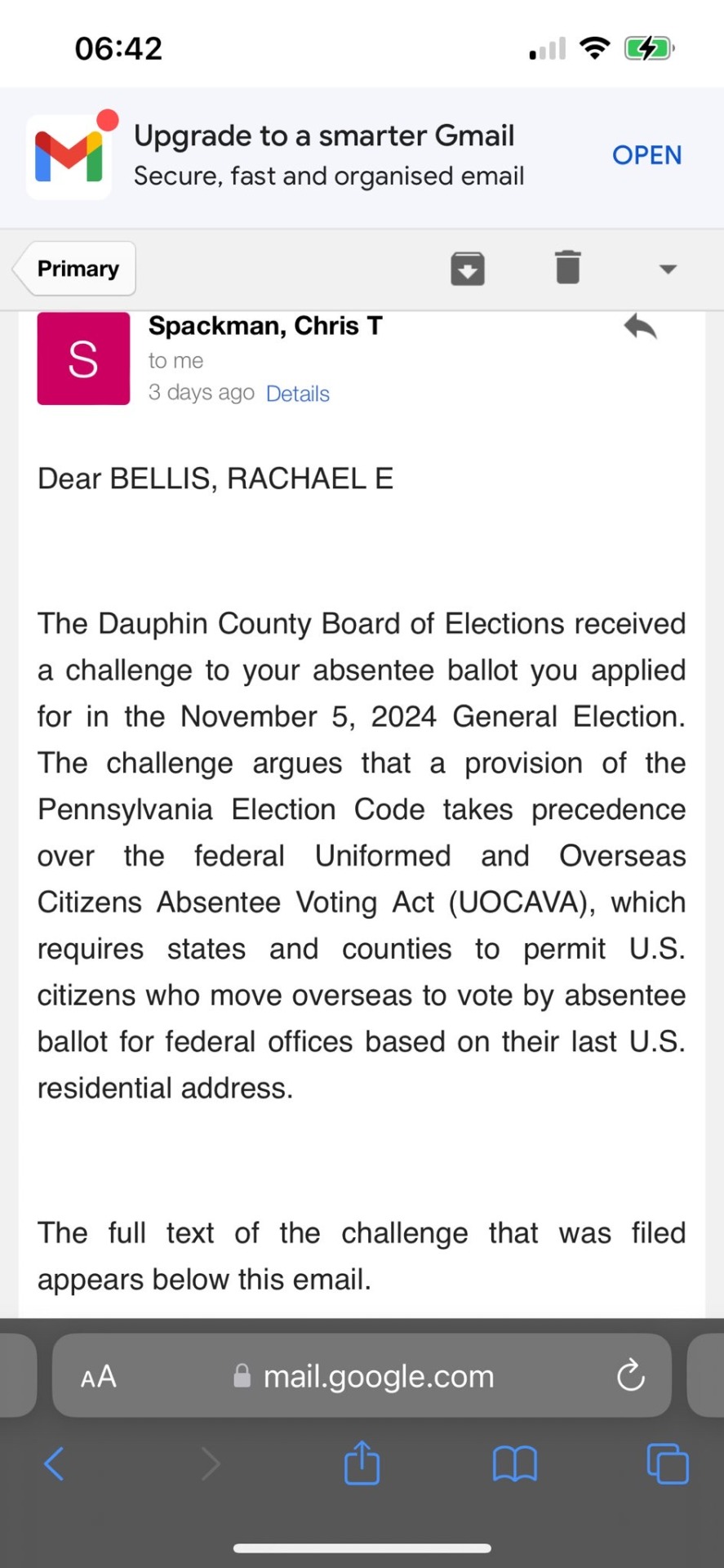
The next four Gmail screenshots of an email sent to Rachael Bellis from Chris T. Spackman that read together as follows:
Dear BELLIS, RACHAEL E., The Dauphin County Board of Elections received a challenge to your absentee ballot you applied for in the November 5, 2024 General Election. The challenge argues that a provision of the Pennsylvania Election Code takes precedence over the federal Uniformed and Overseas Citizens Absentee Voting Act (UOCAVA), which requires states and counties to permit U.S. citizens who move overseas to vote by absentee ballot for federal offices based on their last U.S. residential address.
The full text of the challenge that was filed appears below this email.
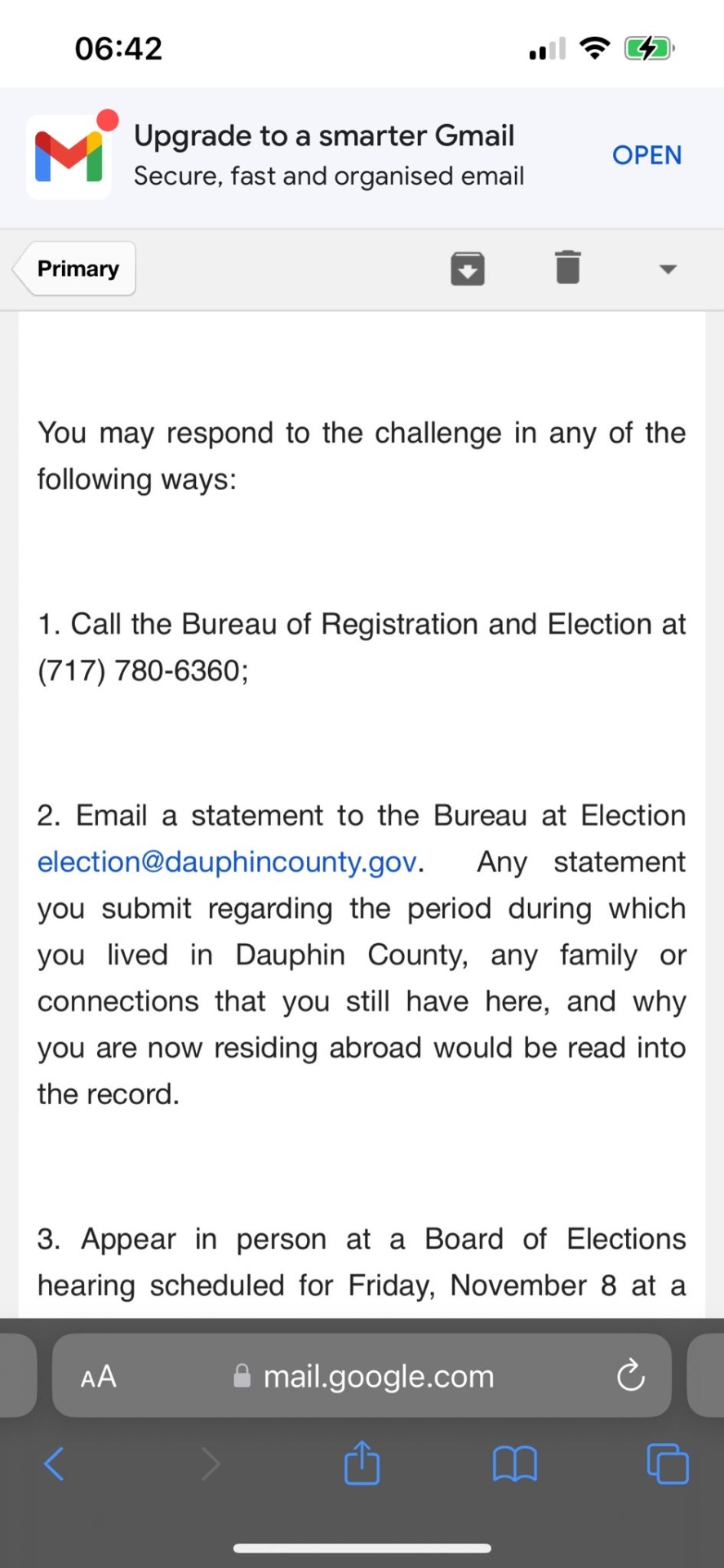
You may respond to the challenge in any of the following ways:
1. Call the Bureau of Registration and Election at (717) 780-6360;
2. Email a statement to the Bureau at Election [email protected]. Any statement you submit regarding the period during which you lived in Dauphin County, any family or connections that you still have here, and why you are now residing abroad would be read into the record.
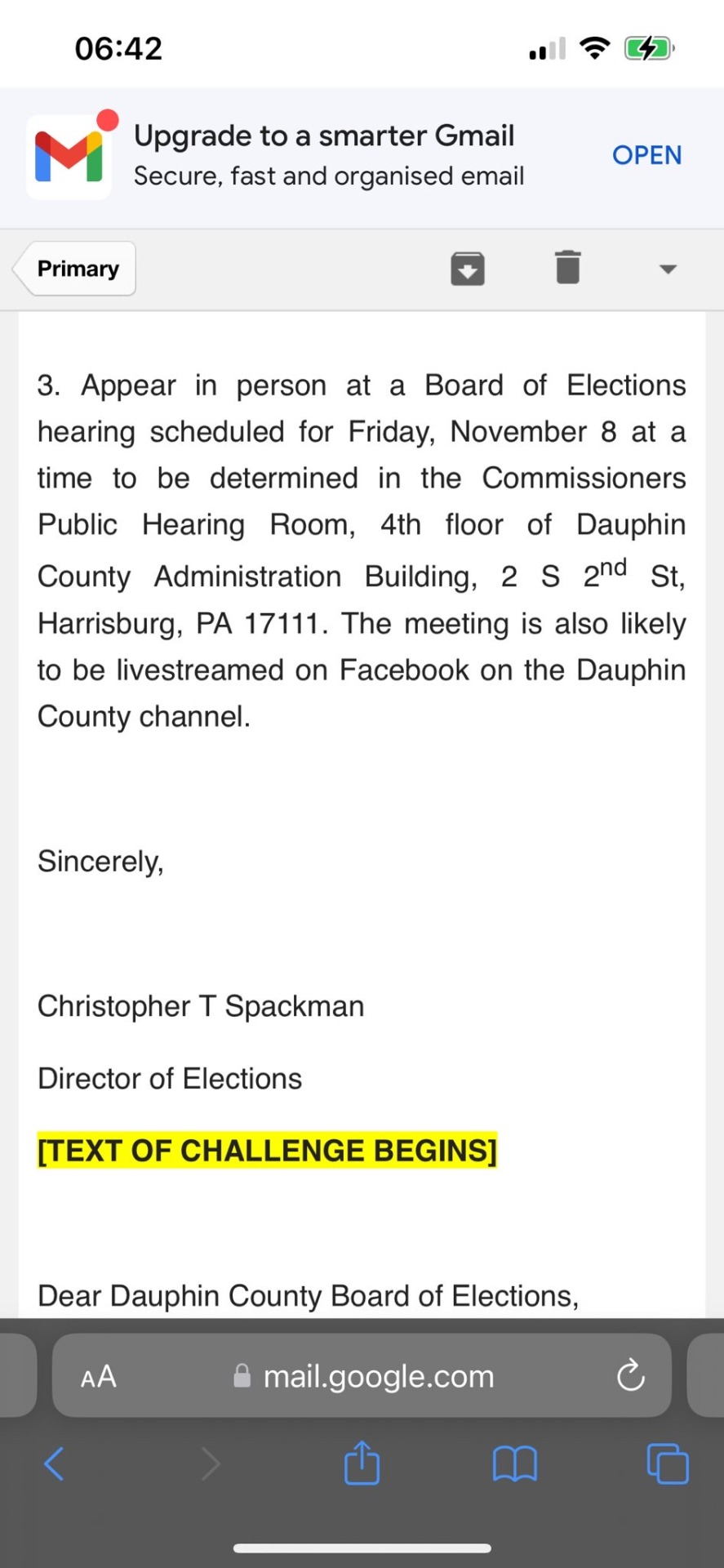
3. Appear in person at a Board of Elections hearing scheduled for Friday, November 8 at a time to be determined in the Commissioners Public Hearing Room, 4th floor of Dauphin County Administration Building, 2 S 20d St, Harrisburg, PA 17111. The meeting is also likely to be livestreamed on Facebook on the Dauphin County channel.
Sincerely,
Christopher T Spackman
TEXT OF CHALLENGE BEGINS
Dear Dauphin County Board of Elections,
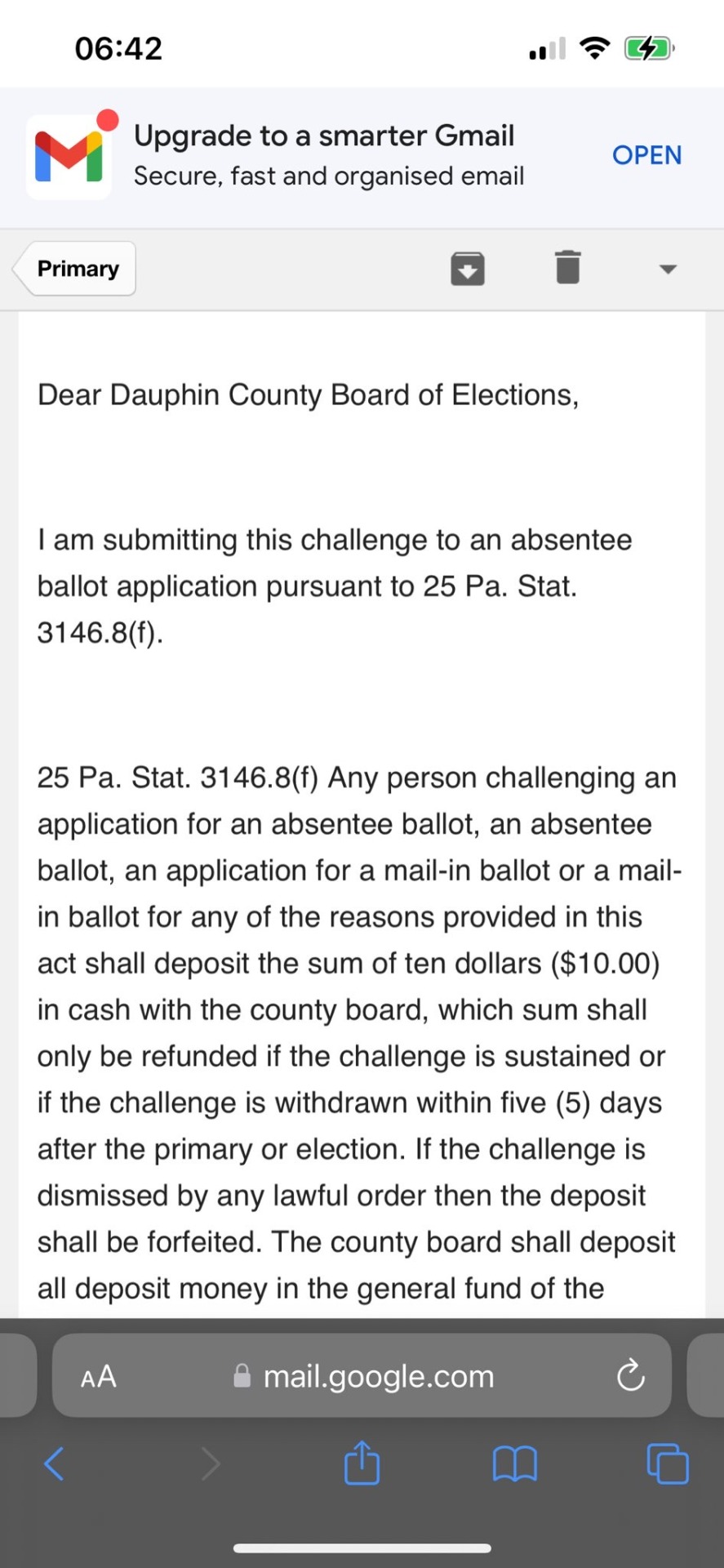
I am submitting this challenge to an absentee ballot application pursuant to 25 Pa. Stat.
3146.8(f).
25 Pa. Stat. 3146.8(f) Any person challenging an application for an absentee ballot, an absentee ballot, an application for a mail-in ballot or a mail-in ballot for any of the reasons provided in this act shall deposit the sum of ten dollars ($10.00) in cash with the county board, which sum shall only be refunded if the challenge is sustained or if the challenge is withdrawn within five (5) days after the primary or election. If the challenge is dismissed by any lawful order then the deposit shall be forfeited. The county board shall deposit all deposit money in the general fund of the…
The rest of the forwarded email is cut off.
The last image is a screenshot of the official statement from the Centre County, Pennsylvania Board of Commissioners released on November 6, 2024 that states:
Centre County Working with Ballot Scanner Vendor to Export Election Results.
(Bellefonte, PA) -Centre County Elections Office is working continuously to provide mail-in ballot data in order to post unofficial results.
To this point, all ballots have been scanned, including all mail-in ballots.
Centre County's Election team and IT team have identified that the data are successfully being exported from the mail-in ballot scanners, but that the data is not being recognized when uploaded to the elections software.
Centre County's Administrator, John Franek, Jr. stated, "We have not stopped working, and we will continue to work until unofficial results are posted and reported to the Pennsylvania Department of State."
As a next step, Centre County has begun working with the equipment vendor to adjust configurations to make the two systems-the mail-in ballot scanner and the elections software where data are uploaded -compatible with one another.
We will provide updates as we make progress.
/end ID]
#sources added#us politics#us election#presidential election#2024 presidential election#election interference#election integrity#election security#image described#image description in alt#image description included#image description added#described#kamala harris#kamala 2024#us news#us presidents#updated id
36K notes
·
View notes
Text
Relyance AI Unveils Data Journeys™: Redefining Trust and Visibility in the AI Era
Press Release – SAN FRANCISCO, CA – April 21, 2025 – Relyance AI, the leading AI-powered trust and governance platform that provides complete visibility and control over enterprise-wide data, today announced Relyance AI Data Journeys™ (Data Journeys), a first-of-its-kind product that enables AI innovation while introducing the new standard for trust and governance in a world where data is…
0 notes
Text
#Healthcare IT#HealthTech#Medical IT Solutions#EMR Support#Healthcare Software#Telemedicine Services#Medical Data Security#Healthcare Cloud Solutions
0 notes
Text
CRMLeaf Features Built to Improve Sales and Customer Relationships

In this blog, we’ll explore the key features of CRMLeaf that are designed to elevate your sales process and enhance customer relationships at every stage.
Read the full blog
#CRMLeaf#Sales CRM#Business CRM#CRM software#Lead management#Customer engagement#Project management#HR software#Payroll system#Billing CRM#Task tracking#Team collaboration#Pipeline management#Ticketing system#Employee tracking#Recruitment tool#Data security#Reports & insights#Role-based access
0 notes
Text
G Suite Mail Backup Tool

Every business and profession faces risks that can take the menacing form of data loss. This is the reason why we must take effective measures to have the better of these risks. Since digital data is the very life force fueling a business, every effort must be made to repel any chances of data loss. A large chunk of digital data is present in the form of emails and these must be well protected by installing antimalware systems. But this is not enough; we also need data backup and recovery systems to keep data loss at bay. Therefore, we must use professional, third party tools which are way cheaper than expert services and way more convenient than manual methods to backup G suite or any other email service.
G suite backup with a tool that caters simplicity in usage
In order to backup emails with ease we so yearn for, we need a tool that caters user friendly features. It must enable users to personalize an email archiving session. No matter what volume of data is thrown at a tool, it must deliver flawless results. It must issue valid usage license to users and should come decked with an easy plus smooth interface. A tool should not shrink our wallets by overcharging us. If you want to backup G suite email with such a features-packed tool, then you cannot go wrong if you stamp your approval on Mail Backup X.
Mail Backup X- a professional G suite mail backup tool with user friendly features
Mail backup X is a tool that beats the exorbitant professional services in the area of pricing with its highly affordable price tag. This tool also beats the professional services when it comes to the sheer range of features on offer. Easy to use even for beginners, this tool maintains its peak and flawless performance on both Windows and Mac devices. It is compatible with a huge number of email services, which makes it a cost effective solution. Another thing that makes it an even more cost effective choice is this tool's untiring ability to cater the whole range of email management tasks like email migration and restore. You can customize an email backup, restore or achieving session in the light of your unique needs. The level of flexibility on offer from this tool is second to none. You can choose between full and selective backups. PDF archiving feature is also present. Your data is duly encrypted to present no chance to internet threats to meddle in your private affairs. You can also G suite mail contacts backup, which evidences the fact that this tool assures complete data retention. It is updated on a regular basis, which explains the reason why its smooth performance on both Windows and Mac is well sustained.
How to backup G suite email in a manner that affords significant savings in storage space?
To reap significant savings in storage space, you can throw the weight of your trust on this tool that has the unique ability of 3x data compression. The data compression algorithm employed by this tool has been fully tested, so there are no question marks about its safety. Even while using such a high degree of compression, you are assured of complete data retention. Even the folder hierarchy is not messed up during this process. 3x data compression will increase the rate of data transfer thereby leading to faster and effortless results.
G suite email backup that is safe as well
No matter how precarious the outside circumstances are, this tool will keep your data safe by using effective remedies against data theft. Encryption takes the top honors when it comes to completely shutting all doors that may become a source of unauthorized data access. Google approved login ensures that whenever you use this tool to source emails from an email client, the connection is always secure with no scope for unauthorized data access. The users are provided with the option to password protect their files tagged highly confidential. An offline mode of this tool gives vent to all data security concerns populating your mind space. To put it in short, you will not find a more secure tool to backup G suite.
Backup G suite mail folders without pounding your head with complexities
A tool may have the best lineup of features and may be highly secure as well, but its overall utility will diminish considerably if it pounds our head with complexities. Ease in use should be the foremost attribute of a tool, everything else matters thereafter. And this tool gets the balance between simplicity and sophistication absolutely right. No more usage of mind numbing technical terminologies. No more encounters with vague instructions that become a grapevine of confusions. No more getting caught up in an unnecessarily long line up of instructions which lead to brewing of confusions. Use this sophisticated yet straightforward tool to get the intended results in an effortless manner. Short and simple instructions, a user friendly interface, complete absence of heavy technical terminologies and usage of simple language, elevate the level of ease users feel while carrying out myriad email management tasks.
These tools has other ease-affording features as well that simplify email management to a great degree. These features include a smart mail viewer, incremental backups, a smart search module along with a live dashboard.
Backup G suite mail data with a free demo of this tool
There is no better way of discovering the trust-invoking qualities of this tool other than trying out its free demo. This tool has been growing in popularity at an unabated pace because it walks the talks by living up to the expectations of users. Even though everything about this tool is very true and transparent, you can get further insights into its user friendly technology by trying out its free demo. So what are you waiting for? Grab this inopportunity without any second thoughts for this tool is tailor-made to fulfill your diverse needs.
0 notes
Text
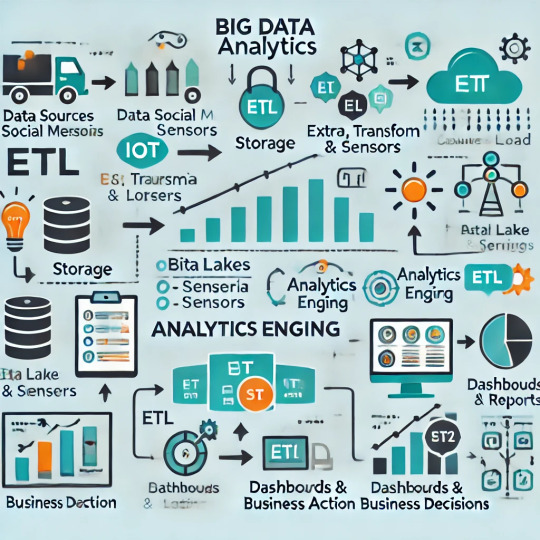
Big Data Analytics Services: Unleashing Business Intelligence at Scale
Why Big Data Analytics Matters Today
In the age of digital data has emerged as an important asset of companies. Every online activity such as a click the website to a Facebook or Twitter interaction creates information. While the internet continues to create enormous amounts of data businesses are looking for new methods to make use of this abundance of data to improve their operations, drive growth and provide more satisfying customer experiences. This influx of data frequently referred to "big data," is not merely a trend, but is a fundamental element in modern day business intelligence. Big data analytics is an integral part of the decision-making process across different sectors, changing how companies operate, anticipate trends, and invent.
The amount of data growing exponentially. As per International Data Corporation (IDC) the world's volume of data will reach an astounding 181 zettabytes by 2025. This number is expected to continue to grow. With the data generated by many sources, such as those from Internet of Things (IoT) and the social web, transactions records and customer data, companies have to face the task of analyzing and managing the data efficiently. Without the proper methods and tools to analyze the data, businesses are at risk of missing the most important information that could result in substantial improvements to their operations and services. This is the point where Big Data Analytics Services come in.
What Are Big Data Analytics Services?
Big Data Analytics Services refer to the methods, tools that are employed to collect meaningful information from large and varied datasets. These services usually encompass an array of methods and tasks, which include data ingestion, transformation of data, predictive analytics, machine learning and visualization of data. The purpose of using Big Data Analytics Services is to aid businesses in making data-driven choices by turning the raw data into actionable insights.
The most important elements in Big Data Analytics Services include:
Data Ingestion as well as ETL Pipeline Setup It is the process of removing data from different sources, then transforming it into a format that is usable and then load it onto a computer system so that it can be analysed. This is typically accomplished with ETL (Extract Transform, Load) tools and techniques such as Apache Kafka, NiFi, or AWS Kinesis.
Data Lakes and Warehouse Architecture For managing large amounts of data, companies typically use data lakes as well as data warehouses. These systems house huge quantities of data in their natural formats (in cases of lakes)) or in structured format (in cases of data warehouses) to facilitate easy accessibility and data analysis.
Advanced Analytics: Prescriptive and predictive analytics aid businesses in forecasting the future and recommend actions based upon data-driven insights. The models of Machine Learning are typically used to detect patterns and predict the outcomes.
The Visualization Tool and the Dashboard: Information is typically complicated and difficult to understand. Tools for visualizing such as Tableau, Power BI, and Looker assist businesses in presenting their data in a simple digestible format. They also provide interactive dashboards that provide instantaneous information.
AI as well as Machine Learning Model Integration: Machine learning and AI are used to study information and to predict future trends, like finding anomalies or forecasting trends for the future. These models are incorporated in the pipeline of analytics to help automate decision-making processes.
Governance Security, Governance and Compliance Enforcement As the significance of information, making sure that it is secure and compliance with laws (e.g. GDPR) is essential. Big Data Analytics Services often contain data governance strategies as well as security measures to guard sensitive data as well as ensure compliance with regulations.
Core Benefits of Big Data Analytics Services
Big Data Analytics Services provide numerous benefits to organizations which allow the organization to make smarter choices, increase efficiency, and get an edge over competitors. The main advantages are:
Smarter Decision-Making: Using the assistance of predictive models as well as real-time dashboards, business executives are able to make informed choices with the help of data-driven insights. For example, a logistics company that utilizes real-time GPS information and weather data can change routes so that they don't get delayed, which can reduce the cost of transportation and improve the speed of service delivery.
Customer-centricity at Scale Personalized experiences are becoming increasingly crucial in the consumer-facing industry. Big data allows businesses to determine their customer segments, learn about their preferences and design specific offerings or content. Based on Epsilon Research, more than 80 percent of customers will be more inclined to purchase purchases when they are offered customized experiences.
Operational Cost Savings: Through automated processes, and optimizing the use of resources, Big data analytics can assist businesses in reducing their operating costs. McKinsey estimates that businesses using big data analytics can cut their operating expenses by as much as 20% with efficient resource management, waste reduction along with process efficiency.
Fraud detection and risk reduction Financial institutions, like banks, utilize massive data analytics in order to identify fraudulent activity in real-time. The anomalies in transaction data could be detected immediately, preventing fraud and securing millions of dollars. This proactive strategy reduces security risks for financial transactions and improves the level of protection.
Improved Product Innovation through Big data plays crucial roles in the process of product development and innovation. Companies such as Netflix study the data of millions of subscribers to suggest content and determine what movies or shows to make the next. This approach based on data lets them adapt their content strategy to the preferences of their customers, thereby driving engagement and growth in subscribers.
How Big Data Analytics Impacts Different Industries
The use of big data in analytics has been revolutionizing industries through providing profound insights that can lead to more informed decisions and enhanced operational efficiency. Here's how different industries are using big data:
Industry
Big Data Use Cases
Retail & eCommerce
Individualized offers including basket analysis, dynamic pricing
Manufacturing
IoT data to help with quality control, predictive maintenance
Healthcare
Early diagnosis, patient analytics, prediction Genomics
Banking & Finance
Credit risk scoring, real-time fraud alerts
Travel & Hospitality
Dynamic pricing and occupancy forecasting, as well as behavior analysis
Big Data Analytics Architecture Overview
Big data analytics usually is based on a multi-layered structure which consists of several important components that work together to gather, process, as well as analyze the data. Here's a quick outline of a typical data structure:
Information Sources: The data may be gathered from a variety of sources, such as sensors, databases and logs, social media, and much more.
Data Ingestion Tools: Software such as Apache Kafka NiFi, Apache Kafka or AWS Kinesis can be used to gather and ingest data from various sources.
ETL Pipelines Processes data and transforms by using Extract, Transform, and Load (ETL) methods using tools like Talend or AWS Glue.
Storage Data are stored within data lakes and data warehouses with cloud storage solutions such as AWS S3 or Azure Data Lake.
Processing Layer The data is processed and analyzed with tools such as Apache Spark, Databricks, or Presto.
Analytic Layer: The machine Learning algorithmic and AI models are employed to gain insight and predict.
Visualization tools such as Tableau, Power BI, and Looker aid in communicating the information in a digestible and actionable format.
Challenges Faced During Implementation
Despite the many advantages from big data analytics there are a few hurdles to implement the solutions efficiently. The most frequent problems are:
Installation and infrastructure costs are high: Creating and maintaining a massive data analytics platform can be costly. But, companies can reduce the costs of these platforms by using cloud-based services, which provide cost-per-use pricing.
Team Skills Gap There are many organizations struggling to find qualified experts who are proficient in big data technology and analytics. To get around this, organizations can employ ETL consultants as well as AI experts to fill the gap in skills.
Non Conformant Data Formats Data from different sources is often in a variety of formats, which makes it hard to understand. Schema and data standardization could help to solve this problem.
Privacy Concerns for Data Due to the ever-growing quantity of sensitive information being gathered, ensuring security and compliance with laws like GDPR is crucial. Businesses can address these issues through the implementation of encryption as well as role-based access and other security measures.
Integration of Legacy Systems: Many organizations still use legacy systems that aren't compatible with the modern tools for big data. Middleware connectors and APIs can aid in integrating these systems into an analytics system.
The Role of ETL Consulting in Big Data Success
The ETL (Extract, Transform, Load) pipeline plays an important function for big data analysis. It is the way to determine how quickly data flows in a clean and reliable manner, how validated and safe information is as well as how secure it is. By constructing affordable, scalable and fully AI-ready ETL pipelines ETL experts can assist businesses improve the efficiency of their data processing processes and ensure that the data is analyzed quickly.
ETL consultants are also essential in real-time applications, such as the detection of fraud, dynamic pricing and tracking of customer sentiment. Their expertise guarantees that data is processed promptly and that companies can immediately take action using the insights that are derived from the information.
Future Trends in Big Data Analytics
As the amount of the data available continues to increase, emerging trends for big data analysis are beginning to emerge. A few of the more significant developments include:
Augmented Analytics: Artificial Intelligence-based analytics which aid in automatizing processes for generating insight and decision-making.
serverless data processing: this new trend removes the requirement for infrastructure management and allows businesses to concentrate exclusively upon data processing.
Data Mesh Architecture: A way to manage data that is not centralized that treats data as a product and is managed by teams that are specific to a particular domain.
Edge Analytics: Live analysis performed at the edges of a network which is closer to the data source like IoT devices.
Green Data Centers: as demand for analytics based on big data rises and so does the demand for eco-friendly and sustainable energy data centers.
According to Gartner more than 60% of businesses will be using augmented analytics platforms in 2026, which will help them speed up information delivery.
Big Data and AI: Better Together
Data from big data along with artificial intelligence (AI) are complementary technologies. Big data offers the huge quantities of data required for the development of AI models and AI can enhance the power of big data by automating decision-making processes as well as finding patterns that are not obvious to the naked eye.
In retail, for instance the data collected from customer interactions could be utilized in AI models to anticipate future purchases or to identify customers who are at risk of experiencing churn. Through the combination of big data and AI, companies can enhance their decision-making processes and deliver more personalized customer experience.
Final Ideas: Make Smarter Decisions using Big Data Analytics
Big Data Analytics Services are no longer a luxury option for companies; they are now an essential requirement for companies seeking to compete. By using big data, companies can enhance operational efficiency, customize customer experiences, spot fraud, and boost innovation. But, implementing successful big data analytics will require the appropriate strategy, the right architecture and experience.
If you're looking to unlock the power of your data to drive better decisions, you need to work with experts who will help create a scalable, secure, and future-proof big analytics platform for data. If you're looking to automate decision-making processes, create live analytics dashboards, or incorporate the use of predictive models into processes, Big Data Analytics Services will help you transform raw data into actionable insights.
FAQs :
1. What exactly is Big Data Analytics and why is it so important?
Big Data Analytics is the method of analyzing huge quantities of data to uncover patterns and insights. It assists businesses in making better decisions, enhance processes, and remaining ahead of the competition.
2. What are the primary elements in Big Data Analytics?
Data collection is one of the most important components. It includes storage, processing, the analysis of machine-learning and visualization of data, all working together to transform data into actionable information.
3. What industries would benefit most from Big Data Analytics?
Industries such as healthcare, retail manufacturing, banking and travel utilize large amounts of data to provide customized deals, fraud detection, predictive maintenance as well as dynamic pricing.
4. What are the challenges associated when dealing with Big Data Analytics?
Problems include the high cost of setting up and a lack of highly skilled professionals as well as privacy concerns with data and integrating older systems with the latest technology.
5. How can AI as well as Big Data work together?
AI utilizes big data to predict and make decisions automatically, while big data can help develop AI models to discover patterns and insights for businesses.
0 notes
Text

Best Employee Monitoring Solution | Kriptone | Kntrol
#best employee time tracking software#Real-time monitoring software#it security services company#Data loss prevention solutions#Endpoint security#IT cyber security services#Data loss protection#Web Tracking
1 note
·
View note