#hide facebook ads
Text
ok so

somethin about this shein ad for an atrocious dress did massive damage to my brain
now i'm calling all FREAKS put your FAVS in this THANG

#Tough Boy#Hide Himaa#ffxiv#ff14#final fantasy xiv#xaela#ffxiv art#ffxiv oc#oc art#original character#art prompt#au ra xaela#don't support shein tho. like fr don't shop on shein#idk why i'm gettin shein ads but that's just the price i gotta pay when checking up on my relatives on facebook
131 notes
·
View notes
Text

I spent the last 11 months working with my illustrator, Marta, to make the children's book of my dreams. We were able to get every detail just the way I wanted, and I'm very happy with the final result. She is the best person I have ever worked with, and I mean, just look at those colors!

I wanted to tell that story of anyone's who ever felt that they didn't belong anywhere. Whether you are a nerd, autistic, queer, trans, a furry, or some combination of the above, it makes for a sad and difficult life. This isn't just my story. This is our story.

I also want to say the month following the book's launch has been very stressful. I have never done this kind of book before, and I didn't know how to get the word out about it. I do have a small publishing business and a full-time job, so I figured let's put my some money into advertising this time. Indie writers will tell you great success stories they've had using Facebook ads, so I started a page and boosting my posts.
Within a first few days, I got a lot of likes and shares and even a few people who requested the book and left great reviews for me. There were also people memeing on how the boy turns into a delicious venison steak at the end of the book. It was all in good fun, though. It honestly made made laugh. Things were great, so I made more posts and increased spending.

But somehow, someway these new posts ended up on the wrong side of the platform. Soon, we saw claims of how the book was perpetuating mental illness, of how this book goes against all of basic biology and logic, and how the lgbtq agenda was corrupting our kids.

This brought out even more people to support the book, so I just let them at it and enjoyed my time reading comments after work. A few days later, then conversation moved from politics to encouraging bullying, accusing others of abusing children, and a competition to who could post the most cruel image. They were just comments, however, and after all, people were still supporting the book.

But then the trolls started organizing. Over night, I got hit with 3 one-star reviews on Amazon. My heart stopped. If your book ever falls below a certain rating, it can be removed, and blocked, and you can receive a strike on your publishing account. All that hard work was about to be deleted, and it was all my fault for posting it in the wrong place.
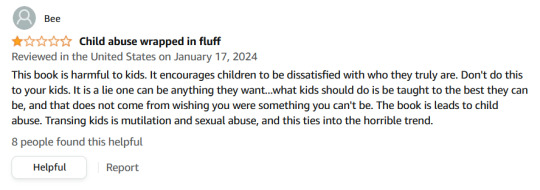

I panicked, pulled all my posts, and went into hiding, hoping things would die down. I reported the reviews and so did many others, but here's the thing you might have noticed across platforms like Google and Amazon. There are community guidelines that I referenced in my email, but unless people are doing something highly illegal, things are rarely ever taken down on these massive platforms. So those reviews are still there to this day. Once again, it's my fault, and I should have seen it coming.
Luckily, the harassment stopped, and the book is doing better now, at least in the US. The overall rating is still rickety in Europe, Canada, and Australia, so any reviews there help me out quite a lot.
I'm currently looking for a new home to post about the book and talk about everything that went into it. I also love to talk about all things books if you ever want to chat. Maybe I'll post a selfie one day, too. Otherwise, the book is still on Amazon, and the full story and illustrations are on YouTube as well if you want to read it for free.
#books#reading#childrens books#lgbtq#lgbtqia#autism#transgender#furry#therian#art#deer#queer#artists on tumblr#creativity#illustration
3K notes
·
View notes
Text
Oh, you know, just the usual internet browsing experience in the year of 2024

Some links and explanations since I figured it might be useful to some people, and writing down stuff is nice.
First of all, get Firefox. Yes, it has apps for Android/iOS too. It allows more extensions and customization (except the iOS version), it tracks less, the company has a less shitty attitude about things. Currently all the other alternatives are variations of Chromium, which means no matter how degoogled they supposedly are, Google has almost a monopoly on web browsing and that's not great. Basically they can introduce extremely user unfriendly updates and there's nothing forcing them to not do it, and nowhere for people to escape to. Current examples of their suggested updates are disabling/severly limiting adblocks in June 2024, and this great suggestion to force sites to verify "web environment integrity" ("oh you don't run a version of chromium we approve, such as the one that runs working adblocks? no web for you.").
uBlockOrigin - barely needs any explanation but yes, it works. You can whitelist whatever you want to support through displaying ads. You can also easily "adblock" site elements that annoy you. "Please log in" notice that won't go away? Important news tm sidebar that gives you sensory overload? Bye.
Dark Reader - a site you use has no dark mode? Now it has. Fairly customizable, also has some basic options for visually impaired people.
SponsorBlock for YouTube - highlights/skips (you choose) sponsored bits in the videos based on user submissions, and a few other things people often skip ("pls like and subscribe!"). A bit more controversial than normal adblock since the creators get some decent money from this, but also a lot of the big sponsors are kinda scummy and offer inferior product for superior price (or try to sell you a star jpg land ownership in Scotland to become a lord), so hearing an ad for that for the 20th time is kinda annoying. But also some creators make their sponsored segments hilarious.
Privacy Badger (and Ghostery I suppose) - I'm not actually sure how needed these are with uBlock and Firefox set to block any tracking it can, but that's basically what it does. Find someone more educated on this topic than me for more info.
Https Everywhere - I... can't actually find the extension anymore, also Firefox has this as an option in its settings now, so this is probably obsolete, whoops.
Facebook Container - also comes with Firefox by default I think. Keeps FB from snooping around outside of FB. It does that a lot, even if you don't have an account.
WebP / Avif image converter - have you ever saved an image and then discovered you can't view it, because it's WebP/Avif? You can now save it as a jpg.
YouTube Search Fixer - have you noticed that youtube search has been even worse than usual lately, with inserting all those unrelated videos into your search results? This fixes that. Also has an option to force shorts to play in the normal video window.
Consent-O-Matic - automatically rejects cookies/gdpr consent forms. While automated, you might still get a second or two of flashing popups being yeeted.
XKit Rewritten - current most up to date "variation "fork" of XKit I think? Has settings in extension settings instead of an extra tumblr button. As long as you get over the new dash layout current tumblr is kinda fine tbh, so this isn't as important as in the past, but still nice. I mostly use it to hide some visual bloat and mark posts on the dash I've already seen.
YouTube NonStop - do you want to punch youtube every time it pauses a video to check if you're still there? This saves your fists.
uBlacklist - blacklists sites from your search results. Obviously has a lot of different uses, but I use it to hide ai generated stuff from image search results. Here's a site list for that.
Redirect AMP to HTML - redirects links from their amp version to the normal version. Amp link is a version of a site made faster and more accessible for phones by Bing/Google. Good in theory, but lets search engines prefer some pages to others (that don't have an amp version), and afaik takes traffic from the original page too. Here's some more reading about why it's an issue, I don't think I can make a good tl;dr on this.
Also since I used this in the tags, here's some reading about enshittification and why the current mainstream internet/services kinda suck.
#modern internet is great#enshittification#internet browsing#idk how to tag this#but i hope it will help someone#personal#question mark
1K notes
·
View notes
Text
Hiking Clothes
"Fuck, that guy was weird." You say under your breath as you walk back to your car.
What else did you expect, responding to an ad for free clothes on Facebook marketplace. He was an older guy with a big gut that was too big for his clothes. He never made eye contact, just looking down at my body. And he spoke in an emotionless monotone voice.
You don't think much of it, just glad you're on your way home now. The man doesn't live far, so you arrive home in just a few minutes. As you walk up to your apartment, you see a familiar face getting into the elevator. He is looking away from you, so it's hard to tell but he looks kinda like the guy who sold you the clothes.
"I guess he just has one of those faces, huh?" You dismiss it, assuming they just look similar.
You get home and immediately get undressed, ready to try on the new clothes. You throw on the large black shirt, It's a bit loose but if you tuck it in it looks fine. You pull up the shorts and they're also too big, although they come with straps that hold them up. Good enough, given they were free after all.
You stand in front of the mirror, trying to decide whether you like them enough to keep them. They don't look that good, but something about the way it fits you makes you feel confident. But then you notice a dry white stain in the crotch area.
"Ew, what the fuck! That's disgus- aooohh ughh." You try to voice your disgust at the not so subtle stain, but you're quickly interrupted. The stain disappears as the dried liquid siphons up your dick. The euphoric feeling interrupts your train of thought with nothing but pleasure.
"Fuuuuuck that feels good." You say between moans.
You grab your cock as it starts to harden, making it stick straight out in the loose fitting shorts. The tingling feeling in your crotch continues as you can feel your dick growing in your hands. From your underwhelming 4 inches to 5, 6, 7, 8 inches. It folds to the side, trying to find room to comfortably sit in your shorts. The tingling shoots down your thick shaft and into your balls, making them drop further as they grow to the size of tennis balls. The bulge is now unmistakable under your shorts.
"Ooouugh... More." You can barely manage to speak.
Suddenly your small but perky ass starts to fill with fat. Your cheeks expand until they fill all the empty room in your large shorts, creating a large shelf on your backside. Your thighs soon follow suit, growing with fat and muscle and making you spread your legs to make room for them. Your calves and feet double in size to accommodate your growing body.
"What... Ooohh... Is happening... Ugh... To me?" You try to reason, but overwhelming pleasure has already taken over your lower half. You cups your fat ass, making your hips thrust forward as a stain of pre-cum starts to form in your crotch.
The tingling pleasure that has engulfed your legs starts to migrate up into your midsection. You feel a tightness in your stomach, looking down you realize a small mound of fat is now hiding under your large shirt. The small mound grows and grows until your belly would be impossible to hide, even under the loosest shirts. Your posture starts to lean back as you try to balance out your growing belly. Your shirt is now stretched tight over the beach ball sized gut that is hanging over your waist, making your overalls slide to the side of your belly. You even feel the soft fat growing on your sides and pushing your arms outward, leaving you with thick love handles that spill over the waist of your shorts.
"Wait... Nooooouuuggh... This isn't aauuugh... Right." You try to say as your gut starts to block the view of your lower body.
You instinctively try to reach your cock again, the tingling feeling is strongest there and it begs for release. You try to stretch and contort, but no matter what your gut prevents you from reaching it.
"No no no auugh, fuck!"
This isn't the end of it, it will get worse. His flat pecs suddenly burst outward. Soft fat engulfs them as they start to press against his shirt, his rock hard nipples showing through. They start to sag to the sides as they lay on his gut. He let out a loud moan as his fingers shot to his large nipples.
You feel your shoulders fill out your now tiny looking shirt as they grow large and broad. Your arms fill with a mix of strong muscle and soft fat, making you look strong but cuddly. And your hands double in size and fill with callouses, leaving you with massive man hands. Your arms lengthen in the process, finally allowing you to reach your dick. One hand rubbing your belly, and one hand stroking your cock. The stain in your crotch keeps growing and growing as per cum spills out.
"Ooouugh Fuck yeah!"
You barely notice your deep voice and thick southern accent. Similar to that of the man who sold you those clothes. If anything the manliness of your voice turns you on even more. You waddle to a mirror, wanting to see the package of manliness that you now are.
You stand in the mirror, gut proudly pushed forward and hand stick on the crotch. You look at your face and it seems unfamiliar. It's young and almost feminine, the complete opposite of you. But it doesn't last long. Your flowy hair completely falls out, leaving you with a shiny white head. Your eyebrows thicken as your brow bone becomes more prominent and manly. Your clean shaven face rapidly fills with a bushy black beard, covering the thick double chin that covers your jawline.
You confidently stare at your body, finally matching the manly image you have of yourself.

If only you could spread that to everyone in the world, make them understand the immense pleasure of being a big manly guy such as yourself. The tingling in your cock returns when you think about it. You stare at your gut and start to pump your hand up and down your crotch. Normally a man in his fifties would have trouble getting hard, but a true man like you is hard all the time and ready to spread his seed. Your knees buckle and you let out a loud moan as ropes of cum shoot out into your shorts. You fall to your knees with a loud thump as your cum leaks down the inside of your leg.
"Fuck I'm hungry!" You forget everything you were thinking in favour of the overwhelming need to get bigger. A loud belch erupts from your body as you slowly get up to your feet. The ground rumbles under your feet as you walk to the fridge and pull out some leftover pizza and a beer. You lay your fat ass down on the couch and turn on the tv. You surf through channels, trying to find the sports channel. But you stop on the local news, as something catches your eye. The two anchors look so... Manly. Your dick hardens as you turn up the volume. The two southern hunks are talking about donating clothes for free.
"A drastic increase in donated clothes has been reported in the last few hours. Us two anchors have received a few of these generous donations today. We highly recommend wearing these donated clothes as soon as possible, and donating as many of your clothes as possible to spread the... Ugh... Generosity."
"I should do that!" You tell as you heave yourself off of the couch.
You run to the neighbor and loudly bang on the door. It takes a few moments, but a tall scrawny man answers in his underwear and a small button up.
"What!?" He asks, irritated.
"I want you to have these. For free!" You say as you pull off your stained shorts.
"Uugh okay?" He says confused.
"Here I'll put them on for ya."
You firmly grab his ankle and lift it through the leg of the shorts.
"Hey wait, what the fuck are you doing!?" The man yells.
You grab the other ankle and pull the shorts up his legs as he struggles.
"He sto... Ooouugh ugh." The man stops struggling as soon as you button them up.
The stain you left in the shorts quickly disappears as your seed enters his body. You should feel proud for contributing to the world by spreading your manliness.
The man quickly succumbs to the effects. His belly inflated into a hairy ball gut as it popped all of the buttons in his shirt. His chest turns into two man tits with swollen nipples. His arms and legs expand into thick hairy limbs as his hands and feet double in size. The bulge in his pants grows and so too does the stain of pre cum. Finally his hair falls out and a thick beard grows in its absence. The man is left there staring at you while rubbing his massive cock and his hairy gut.

He lets out a moan as a new stain forms in his pants. You catch his as he is about to fall. You lean into his ear and whisper "Spread the message," in a deep sultry voice.
"Honey, are you coming back." A man's voice echoed from inside the apartment.
"Go get him." You tap him on the shoulder.
He smiles as he pulls off his shorts and waddles back into his apartment.
"Who are you?" You hear. Though as you walk away, all you can hear is a struggle, followed by loud moans coming from the apartment. And you smile, knowing you helped spread your manliness today.
#male tf#masculine#fat tf#hairy#male wg#reality change#male transformation#muscle tf#age progression
712 notes
·
View notes
Text
Forcing your computer to rat you out

Powerful people imprisoned by the cluelessness of their own isolation, locked up with their own motivated reasoning: “It’s impossible to get a CEO to understand something when his quarterly earnings call depends on him not understanding it.”
Take Mark Zuckerberg. Zuckerberg insists that anyone who wanted to use a pseudonym online is “two-faced,” engaged in dishonest social behavior. The Zuckerberg Doctrine claims that forcing people to use their own names is a way to ensure civility. This is an idea so radioactively wrong, it can be spotted from orbit.
From the very beginning, social scientists (both inside and outside Facebook) told Zuckerberg that he was wrong. People have lots of reasons to hide their identities online, both good and bad, but a Real Names Policy affects different people differently:
https://memex.craphound.com/2018/01/22/social-scientists-have-warned-zuck-all-along-that-the-facebook-theory-of-interaction-would-make-people-angry-and-miserable/
For marginalized and at-risk people, there are plenty of reasons to want to have more than one online identity — say, because you are a #MeToo whistleblower hoping that Harvey Weinstein won’t sic his ex-Mossad mercenaries on you:
https://www.newyorker.com/news/news-desk/harvey-weinsteins-army-of-spies
Or maybe you’re a Rohingya Muslim hoping to avoid the genocidal attentions of the troll army that used Facebook to organize — under their real, legal names — to rape and murder you and everyone you love:
https://www.amnesty.org/en/latest/news/2022/09/myanmar-facebooks-systems-promoted-violence-against-rohingya-meta-owes-reparations-new-report/
But even if no one is looking to destroy your life or kill you and your family, there are plenty of good reasons to present different facets of your identity to different people. No one talks to their lover, their boss and their toddler in exactly the same way, or reveals the same facts about their lives to those people. Maintaining different facets to your identity is normal and healthy — and the opposite, presenting the same face to everyone in your life, is a wildly terrible way to live.
None of this is controversial among social scientists, nor is it hard to grasp. But Zuckerberg stubbornly stuck to this anonymity-breeds-incivility doctrine, even as dictators used the fact that Facebook forced dissidents to use their real names to retain power through the threat (and reality) of arrest and torture:
https://pluralistic.net/2023/01/25/nationalize-moderna/#hun-sen
Why did Zuck cling to this dangerous and obvious fallacy? Because the more he could collapse your identity into one unitary whole, the better he could target you with ads. Truly, it is impossible to get a billionaire to understand something when his mega-yacht depends on his not understanding it.
This motivated reasoning ripples through all of Silicon Valley’s top brass, producing what Anil Dash calls “VC QAnon,” the collection of conspiratorial, debunked and absurd beliefs embraced by powerful people who hold the digital lives of billions of us in their quivering grasp:
https://www.anildash.com/2023/07/07/vc-qanon/
These fallacy-ridden autocrats like to disguise their demands as observations, as though wanting something to be true was the same as making it true. Think of when Eric Schmidt — then the CEO of Google — dismissed online privacy concerns, stating “If you have something that you don’t want anyone to know, maybe you shouldn’t be doing it in the first place”:
https://www.eff.org/deeplinks/2009/12/google-ceo-eric-schmidt-dismisses-privacy
Schmidt was echoing the sentiments of his old co-conspirator, Sun Microsystems CEO Scott McNealy: “You have zero privacy anyway. Get over it”:
https://www.wired.com/1999/01/sun-on-privacy-get-over-it/
Both men knew better. Schmidt, in particular, is very jealous of his own privacy. When Cnet reporters used Google to uncover and publish public (but intimate and personal) facts about Schmidt, Schmidt ordered Google PR to ignore all future requests for comment from Cnet reporters:
https://www.cnet.com/tech/tech-industry/how-cnet-got-banned-by-google/
(Like everything else he does, Elon Musk’s policy of responding to media questions about Twitter with a poop emoji is just him copying things other people thought up, making them worse, and taking credit for them:)
https://www.theverge.com/23815634/tesla-elon-musk-origin-founder-twitter-land-of-the-giants
Schmidt’s actions do not reflect an attitude of “If you have something that you don’t want anyone to know, maybe you shouldn’t be doing it in the first place.” Rather, they are the normal response that we all have to getting doxed.
When Schmidt and McNealy and Zuck tell us that we don’t have privacy, or we don’t want privacy, or that privacy is bad for us, they’re disguising a demand as an observation. “Privacy is dead” actually means, “When privacy is dead, I will be richer than you can imagine, so stop trying to save it, goddamnit.”
We are all prone to believing our own bullshit, but when a tech baron gets high on his own supply, his mental contortions have broad implications for all of us. A couple years after Schmidt’s anti-privacy manifesto, Google launched Google Plus, a social network where everyone was required to use their “real name.”
This decision — justified as a means of ensuring civility and a transparent ruse to improve ad targeting — kicked off the Nym Wars:
https://epeus.blogspot.com/2011/08/google-plus-must-stop-this-identity.html
One of the best documents to come out of that ugly conflict is “Falsehoods Programmers Believe About Names,” a profound and surprising enumeration of all the ways that the experiences of tech bros in Silicon Valley are the real edge-cases, unreflective of the reality of billions of their users:
https://www.kalzumeus.com/2010/06/17/falsehoods-programmers-believe-about-names/
This, in turn, spawned a whole genre of programmer-fallacy catalogs, falsehoods programmers believe about time, currency, birthdays, timezones, email addresses, national borders, nations, biometrics, gender, language, alphabets, phone numbers, addresses, systems of measurement, and, of course, families:
https://github.com/kdeldycke/awesome-falsehood
But humility is in short supply in tech. It’s impossible to get a programmer to understand something when their boss requires them not to understand it. A programmer will happily insist that ordering you to remove your “mask” is for your own good — and not even notice that they’re taking your skin off with it.
There are so many ways that tech executives could improve their profits if only we would abandon our stubborn attachment to being so goddamned complicated. Think of Netflix and its anti-passsword-sharing holy war, which is really a demand that we redefine “family” to be legible and profitable for Netflix:
https://pluralistic.net/2023/02/02/nonbinary-families/#red-envelopes
But despite the entreaties of tech companies to collapse our identities, our families, and our online lives into streamlined, computably hard-edged shapes that fit neatly into their database structures, we continue to live fuzzy, complicated lives that only glancingly resemble those of the executives seeking to shape them.
Now, the rich, powerful people making these demands don’t plan on being constrained by them. They are conservatives, in the tradition of #FrankWilhoit, believers in a system of “in-groups whom the law protects but does not bind, alongside out-groups whom the law binds but does not protect”:
https://crookedtimber.org/2018/03/21/liberals-against-progressives/#comment-729288
As with Schmidt’s desire to spy on you from asshole to appetite for his own personal gain, and his violent aversion to having his own personal life made public, the tech millionaires and billionaires who made their fortune from the flexibility of general purpose computers would like to end that flexibility. They insist that the time for general purpose computers has passed, and that today, “consumers” crave the simplicity of appliances:
https://memex.craphound.com/2012/01/10/lockdown-the-coming-war-on-general-purpose-computing/
It is in the War On General Purpose Computing that we find the cheapest and flimsiest rhetoric. Companies like Apple — and their apologists — insist that no one wants to use third-party app stores, or seek out independent repair depots — and then spend millions to make sure that it’s illegal to jailbreak your phone or get it fixed outside of their own official channel:
https://doctorow.medium.com/apples-cement-overshoes-329856288d13
The cognitive dissonance of “no one wants this,” and “we must make it illegal to get this” is powerful, but the motivated reasoning is more powerful still. It is impossible to get Tim Cook to understand something when his $49 million paycheck depends on him not understanding it.
The War on General Purpose Computing has been underway for decades. Computers, like the people who use them, stubbornly insist on being reality-based, and the reality of computers is that they are general purpose. Every computer is a Turing complete, universal Von Neumann machine, which means that it can run every valid program. There is no way to get a computer to be almost Turing Complete, only capable of running programs that don’t upset your shareholders’ fragile emotional state.
There is no such thing as a printer that will only run the “reject third-party ink” program. There is no such thing as a phone that will only run the “reject third-party apps” program. There are only laws, like the Section 1201 of the Digital Millennium Copyright Act, that make writing and distributing those programs a felony punishable by a five-year prison sentence and a $500,000 fine (for a first offense).
That is to say, the War On General Purpose Computing is only incidentally a technical fight: it is primarily a legal fight. When Apple says, “You can’t install a third party app store on your phone,” what they means is, “it’s illegal to install that third party app store.” It’s not a technical countermeasure that stands between you and technological self-determination, it’s a legal doctrine we can call “felony contempt of business model”:
https://locusmag.com/2020/09/cory-doctorow-ip/
But the mighty US government will not step in to protect a company’s business model unless it at least gestures towards the technical. To invoke DMCA 1201, a company must first add the thinnest skin of digital rights management to their product. Since 1201 makes removing DRM illegal, a company can use this molecule-thick scrim of DRM to felonize any activity that the DRM prevents.
More than 20 years ago, technologists started to tinker with ways to combine the legal and technical to tame the wild general purpose computer. Starting with Microsoft’s Palladium project, they theorized a new “Secure Computing” model for allowing companies to reach into your computer long after you had paid for it and brought it home, in order to discipline you for using it in ways that undermined its shareholders’ interest.
Secure Computing began with the idea of shipping every computer with two CPUs. The first one was the normal CPU, the one you interacted with when you booted it up, loaded your OS, and ran programs. The second CPU would be a Trusted Platform Module, a brute-simple system-on-a-chip designed to be off-limits to modification, even by its owner (that is, you).
The TPM would ship with a limited suite of simple programs it could run, each thoroughly audited for bugs, as well as secret cryptographic signing keys that you were not permitted to extract. The original plan called for some truly exotic physical security measures for that TPM, like an acid-filled cavity that would melt the chip if you tried to decap it or run it through an electron-tunneling microscope:
https://pluralistic.net/2020/12/05/trusting-trust/#thompsons-devil
This second computer represented a crack in the otherwise perfectly smooth wall of a computer’s general purposeness; and Trusted Computing proposed to hammer a piton into that crack and use it to anchor a whole superstructure that could observe — and limited — the activity of your computer.
This would start with observation: the TPM would observe every step of your computer’s boot sequence, creating cryptographic hashes of each block of code as it loaded and executed. Each stage of the boot-up could be compared to “known good” versions of those programs. If your computer did something unexpected, the TPM could halt it in its tracks, blocking the boot cycle.
What kind of unexpected things do computers do during their boot cycle? Well, if your computer is infected with malware, it might load poisoned versions of its operating system. Once your OS is poisoned, it’s very hard to detect its malicious conduct, since normal antivirus programs rely on the OS to faithfully report what your computer is doing. When the AV program asks the OS to tell it which programs are running, or which files are on the drive, it has no choice but to trust the OS’s response. When the OS is compromised, it can feed a stream of lies to users’ programs, assuring these apps that everything is fine.
That’s a very beneficial use for a TPM, but there’s a sinister flipside: the TPM can also watch your boot sequence to make sure that there aren’t beneficial modifications present in your operating system. If you modify your OS to let you do things the manufacturer wants to prevent — like loading apps from a third-party app-store — the TPM can spot this and block it.
Now, these beneficial and sinister uses can be teased apart. When the Palladium team first presented its research, my colleague Seth Schoen proposed an “owner override”: a modification of Trusted Computing that would let the computer’s owner override the TPM:
https://web.archive.org/web/20021004125515/http://vitanuova.loyalty.org/2002-07-05.html
This override would introduce its own risks, of course. A user who was tricked into overriding the TPM might expose themselves to malicious software, which could harm that user, as well as attacking other computers on the user’s network and the other users whose data were on the compromised computer’s drive.
But an override would also provide serious benefits: it would rule out the monopolistic abuse of a TPM to force users to run malicious code that the manufacturer insisted on — code that prevented the user from doing things that benefited the user, even if it harmed the manufacturer’s shareholders. For example, with owner override, Microsoft couldn’t force you to use its official MS Office programs rather than third-party compatible programs like Apple’s iWork or Google Docs or LibreOffice.
Owner override also completely changed the calculus for another, even more dangerous part of Trusted Computing: remote attestation.
Remote Attestation is a way for third parties to request a reliable, cryptographically secured assurances about which operating system and programs your computer is running. In Remote Attestation, the TPM in your computer observes every stage of your computer’s boot, gathers information about all the programs you’re running, and cryptographically signs them, using the signing keys the manufacturer installed during fabrication.
You can send this “attestation” to other people on the internet. If they trust that your computer’s TPM is truly secure, then they know that you have sent them a true picture of your computer’s working (the actual protocol is a little more complicated and involves the remote party sending you a random number to cryptographically hash with the attestation, to prevent out-of-date attestations).
Now, this is also potentially beneficial. If you want to make sure that your technologically unsophisticated friend is running an uncompromised computer before you transmit sensitive data to it, you can ask them for an attestation that will tell you whether they’ve been infected with malware.
But it’s also potentially very sinister. Your government can require all the computers in its borders to send a daily attestation to confirm that you’re still running the mandatory spyware. Your abusive spouse — or abusive boss — can do the same for their own disciplinary technologies. Such a tool could prevent you from connecting to a service using a VPN, and make it impossible to use Tor Browser to protect your privacy when interacting with someone who wishes you harm.
The thing is, it’s completely normal and good for computers to lie to other computers on behalf of their owners. Like, if your IoT ebike’s manufacturer goes out of business and all their bikes get bricked because they can no longer talk to their servers, you can run an app that tricks the bike into thinking that it’s still talking to the mothership:
https://nltimes.nl/2023/07/15/alternative-app-can-unlock-vanmoof-bikes-popular-amid-bankruptcy-fears
Or if you’re connecting to a webserver that tries to track you by fingerprinting you based on your computer’s RAM, screen size, fonts, etc, you can order your browser to send random data about this stuff:
https://jshelter.org/fingerprinting/
Or if you’re connecting to a site that wants to track you and nonconsensually cram ads into your eyeballs, you can run an adblocker that doesn’t show you the ads, but tells the site that it did:
https://www.eff.org/deeplinks/2019/07/adblocking-how-about-nah
Owner override leaves some of the beneficial uses of remote attestation intact. If you’re asking a friend to remotely confirm that your computer is secure, you’re not going to use an override to send them bad data about about your computer’s configuration.
And owner override also sweeps all of the malicious uses of remote attestation off the board. With owner override, you can tell any lie about your computer to a webserver, a site, your boss, your abusive spouse, or your government, and they can’t spot the lie.
But owner override also eliminates some beneficial uses of remote attestation. For example, owner override rules out remote attestation as a way for strangers to play multiplayer video games while confirming that none of them are using cheat programs (like aimhack). It also means that you can’t use remote attestation to verify the configuration of a cloud server you’re renting in order to assure yourself that it’s not stealing your data or serving malware to your users.
This is a tradeoff, and it’s a tradeoff that’s similar to lots of other tradeoffs we make online, between the freedom to do something good and the freedom to do something bad. Participating anonymously, contributing to free software, distributing penetration testing tools, or providing a speech platform that’s open to the public all represent the same tradeoff.
We have lots of experience with making the tradeoff in favor of restrictions rather than freedom: powerful bad actors are happy to attach their names to their cruel speech and incitement to violence. Their victims are silenced for fear of that retaliation.
When we tell security researchers they can’t disclose defects in software without the manufacturer’s permission, the manufacturers use this as a club to silence their critics, not as a way to ensure orderly updates.
When we let corporations decide who is allowed to speak, they act with a mixture of carelessness and self-interest, becoming off-the-books deputies of authoritarian regimes and corrupt, powerful elites.
Alas, we made the wrong tradeoff with Trusted Computing. For the past twenty years, Trusted Computing has been creeping into our devices, albeit in somewhat denatured form. The original vision of acid-filled secondary processors has been replaced with less exotic (and expensive) alternatives, like “secure enclaves.” With a secure enclave, the manufacturer saves on the expense of installing a whole second computer, and instead, they draw a notional rectangle around a region of your computer’s main chip and try really hard to make sure that it can only perform a very constrained set of tasks.
This gives us the worst of all worlds. When secure enclaves are compromised, we not only lose the benefit of cryptographic certainty, knowing for sure that our computers are only booting up trusted, unalterted versions of the OS, but those compromised enclaves run malicious software that is essentially impossible to detect or remove:
https://pluralistic.net/2022/07/28/descartes-was-an-optimist/#uh-oh
But while Trusted Computing has wormed its way into boot-restrictions — preventing you from jailbreaking your computer so it will run the OS and apps of your choosing — there’s been very little work on remote attestation…until now.
Web Environment Integrity is Google’s proposal to integrate remote attestation into everyday web-browsing. The idea is to allow web-servers to verify what OS, extensions, browser, and add-ons your computer is using before the server will communicate with you:
https://github.com/RupertBenWiser/Web-Environment-Integrity/blob/main/explainer.md
Even by the thin standards of the remote attestation imaginaries, there are precious few beneficial uses for this. The googlers behind the proposal have a couple of laughable suggestions, like, maybe if ad-supported sites can comprehensively refuse to serve ad-blocking browsers, they will invest the extra profits in making things you like. Or: letting websites block scriptable browsers will make it harder for bad people to auto-post fake reviews and comments, giving users more assurances about the products they buy.
But foundationally, WEI is about compelling you to disclose true facts about yourself to people who you want to keep those facts from. It is a Real Names Policy for your browser. Google wants to add a new capability to the internet: the ability of people who have the power to force you to tell them things to know for sure that you’re not lying.
The fact that the authors assume this will be beneficial is just another “falsehood programmers believe”: there is no good reason to hide the truth from other people. Squint a little and we’re back to McNealy’s “Privacy is dead, get over it.” Or Schmidt’s “If you have something that you don’t want anyone to know, maybe you shouldn’t be doing it in the first place.”
And like those men, the programmers behind this harebrained scheme don’t imagine that it will ever apply to them. As Chris Palmer — who worked on Chromium — points out, this is not compatible with normal developer tools or debuggers, which are “incalculably valuable and not really negotiable”:
https://groups.google.com/a/chromium.org/g/blink-dev/c/Ux5h_kGO22g/m/5Lt5cnkLCwAJ
This proposal is still obscure in the mainstream, but in tech circles, it has precipitated a flood of righteous fury:
https://arstechnica.com/gadgets/2023/07/googles-web-integrity-api-sounds-like-drm-for-the-web/
As I wrote last week, giving manufacturers the power to decide how your computer is configured, overriding your own choices, is a bad tradeoff — the worst tradeoff, a greased slide into terminal enshittification:
https://pluralistic.net/2023/07/24/rent-to-pwn/#kitt-is-a-demon
This is how you get Unauthorized Bread:
https://arstechnica.com/gaming/2020/01/unauthorized-bread-a-near-future-tale-of-refugees-and-sinister-iot-appliances/
All of which leads to the question: what now? What should be done about WEI and remote attestation?
Let me start by saying: I don’t think it should be illegal for programmers to design and release these tools. Code is speech, and we can’t understand how this stuff works if we can’t study it.
But programmers shouldn’t deploy it in production code, in the same way that programmers should be allowed to make pen-testing tools, but shouldn’t use them to attack production systems and harm their users. Programmers who do this should be criticized and excluded from the society of their ethical, user-respecting peers.
Corporations that use remote attestation should face legal restrictions: privacy law should prevent the use of remote attestation to compel the production of true facts about users or the exclusion of users who refuse to produce those facts. Unfair competition law should prevent companies from using remote attestation to block interoperability or tie their products to related products and services.
Finally, we must withdraw the laws that prevent users and programmers from overriding TPMs, secure enclaves and remote attestations. You should have the right to study and modify your computer to produce false attestations, or run any code of your choosing. Felony contempt of business model is an outrage. We should alter or strike down DMCA 1201, the Computer Fraud and Abuse Act, and other laws (like contract law’s “tortious interference”) that stand between you and “sole and despotic dominion” over your own computer. All of that applies not just to users who want to reconfigure their own computers, but also toolsmiths who want to help them do so, by offering information, code, products or services to jailbreak and alter your devices.
Tech giants will squeal at this, insisting that they serve your interests when they prevent rivals from opening up their products. After all, those rivals might be bad guys who want to hurt you. That’s 100% true. What is likewise true is that no tech giant will defend you from its own bad impulses, and if you can’t alter your device, you are powerless to stop them:
https://pluralistic.net/2022/11/14/luxury-surveillance/#liar-liar
Companies should be stopped from harming you, but the right place to decide whether a business is doing something nefarious isn’t in the boardroom of that company’s chief competitor: it’s in the halls of democratically accountable governments:
https://www.eff.org/wp/interoperability-and-privacy
So how do we get there? Well, that’s another matter. In my next book, The Internet Con: How to Seize the Means of Computation (Verso Books, Sept 5), I lay out a detailed program, describing which policies will disenshittify the internet, and how to get those policies:
https://www.versobooks.com/products/3035-the-internet-con
Predictably, there are challenges getting this kind of book out into the world via our concentrated tech sector. Amazon refuses to carry the audio edition on its monopoly audiobook platform, Audible, unless it is locked to Amazon forever with mandatory DRM. That’s left me self-financing my own DRM-free audio edition, which is currently available for pre-order via this Kickstarter:
http://seizethemeansofcomputation.org

I’m kickstarting the audiobook for “The Internet Con: How To Seize the Means of Computation,” a Big Tech disassembly manual to disenshittify the web and bring back the old, good internet. It’s a DRM-free book, which means Audible won’t carry it, so this crowdfunder is essential. Back now to get the audio, Verso hardcover and ebook:
https://www.kickstarter.com/projects/doctorow/the-internet-con-how-to-seize-the-means-of-computation

If you’d like an essay-formatted version of this post to read or share, here’s a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2023/08/02/self-incrimination/#wei-bai-bai

[Image ID: An anatomical drawing of a flayed human head; it has been altered to give it a wide-stretched mouth revealing a gadget nestled in the back of the figure's throat, connected by a probe whose two coiled wires stretch to an old fashioned electronic box. The head's eyes have been replaced by the red, menacing eye of HAL 9000 from Stanley Kubrick's '2001: A Space Odyssey.' Behind the head is a code waterfall effect as seen in the credits of the Wachowskis' 'The Matrix.']

Image:
Cryteria (modified)
https://commons.wikimedia.org/wiki/File:HAL9000.svg
CC BY 3.0
https://creativecommons.org/licenses/by/3.0/deed.en
#pluralistic#chaffing#spoofing#remote attestation#rene descartes#adversarial interoperability#war on general purpose computing#canvas attacks#vpns#compelled speech#onion routing#owner override#stalkerware#ngscb#palladium#trusted computing#secure enclaves#tor#interop#net neutrality#taking the fifth#right to remain silent#real names policy#the zuckerberg doctrine#none of your business#the right to lie#right to repair#bossware#spyware#wei web environment integrity
2K notes
·
View notes
Text
Formula 1, Sportswashing and Greenwashing a Genocide ... in other words, just an ordinary day in baku

As the final Formula 1 Grand Prix is set to take place tomorrow in baku, azerbaijan, I find it impossible to remain silent. The world is gearing up for what’s supposed to be an exciting event but behind the gleaming lights of the racetrack, there’s a much darker story that demands attention: the ethnic cleansing of Artsakh and azerbaijan’s ongoing brutal actions against Armenians.
azerbaijan’s history of oppression toward the Armenian people is not a secret. The forced displacement of Armenians from their ancestral lands, the violent campaign of ethnic cleansing in Artsakh, and the inhumane imprisonment and torture of Armenian captives in baku are undeniable facts. The world has remained shockingly quiet as over 200 Armenians languish in azerbaijani prisons, subjected to treatment that violates every principle of human rights.
One of the most glaring symbols of azerbaijan’s hatred toward Armenians is the Genocide Theme Park in baku, a chilling place that mocks the pain and suffering of an entire people. This is not just an internal issue; it’s an attack on humanity. But instead of confronting azerbaijan’s actions, the world is endorsing them.
These atrocities are certainly not limited to the government and the officials; the indescribable hatred has extended over to the people as well - take a glimpse into the azeri society
Now, let's imagine that you were fortunate enough to watch the F1 Grand Prix live in baku. How would you feel knowing that the azerbaijani person sitting next to you might be one of the many who were selling beheaded bodies of Armenian children on Facebook? Or perhaps they took their children to the Genocide Park and photographed them pretending to choke the statues of Armenian soldiers?
azerbaijan is not only hosting the Formula 1 Grand Prix but is also set to host COP29, a global climate summit. These events are being used to greenwash and sportwash the regime’s crimes.
How can we watch Formula 1 without acknowledging that the very ground this race is held on is soaked in the suffering of Armenians? How can we cheer for a spectacle when the cries of the oppressed go unheard?
This is not a political issue; it’s a matter of basic human decency. While the world enjoys the race, we must not forget the injustices happening in the shadows. Formula 1 should be about fairness and excellence. But in azerbaijan, it’s about something far more sinister—using sport to hide atrocities.
So, as you watch the Grand Prix in baku, remember the Armenian lives shattered by violence, hatred and silence. Let’s refuse to let sports and international events become tools for erasing history and ignoring the suffering of innocent people.
BREAK THE CHAIN OF IGNORANCE:
Share Information: use social media platforms like Tumblr, Instagram, X, Facebook and others to share articles, videos, and testimonies about the atrocities being committed by azerbaijan. The more people know, the harder it becomes to ignore.
Engage in Dialogue: talk to friends, family, and colleagues about the situation in azerbaijan and encourage others to take action too.
Support Armenian Communities: donate to/support organizations helping displaced Armenians and those impacted by the conflict in Artsakh. Even small contributions can go a long way in providing humanitarian aid.
Artsakh Relocation Project
All For Armenia
TAKE ACTION by adding your name to THE LIST of supporters.
Remember that this is not a political issue; it’s a matter of basic human decency.
#break the chain of ignorance#azeri crimes#baku#f1#f1 grand prix#f1 grand prix baku#genocide#armenia#turkish crimes#armenian genocide#artsakh is armenia#f1 x reader#formula 1#nobel prize#nobel peace prize#oscar piastri#max verstappen#lewis hamilton#franco colapinto#azerbaijan gp 2024#baku gp 2024#carlos sainz
310 notes
·
View notes
Text
So. Armand has been given different names at different points in his life as a way of others owning him and recreating him in a new image. He hides himself and to an extent, doesn’t even know who he really is.
But then, one day Daniel mentions how Armand doesn’t have a last name. He’s scrolling through Facebook or newspaper articles, or perhaps is reading over a review from the book that mentions the same fact. So he turns to Armand, and says he should take his last name.
“Armand Molloy, got a nice ring, don’t it?”
and Armand sits so somber for a moment before it hits him. Before he realises that Daniel isn’t changing him, he’s adding to him. Daniel hasn’t created a new persona, in fact he has shared a part of himself with Armand, with his eternal companion. He hasn’t given him a new name out of ownership, but out of devotion. Out of pure love.
I’m even going to go as far as Daniel getting some kind of official document made. Armand treasures it more than anything.
#losing my absolute mind#daniel molloy#devils minion#armand iwtv#interview with the vampire#iwtv#amc iwtv
214 notes
·
View notes
Text
Elliott headcannons (some of these I gather from people but there's side notes who it's from)
I definitely do not have an obsession with this man.
Elliott used a smoking pipe before. He doesn't know how to use it by the way that he start coughing. (Bonus from @majokothesmol: "He doesn't use it to smoke. It's a bubble blower." Then @/3-and-a-half-possums-in-a-hat added "plotwist, he inhaled the bubbles")
He doesn't know how to maintain eye contact. That's why he's facing side ways and he looked confidence (or arrogant as you might say it) just to hide the fact he can't make eye contact.
He came from a wealthy family and his parents hates him because he wants to he a writer instead of a lawyer or something. Probably an only child, if not, his sibling is either decades away from his age and probably his parents favorite, sorry Elliott you don't have parent favoritism. (younger or older)
Theatre kid, that's it. You can't tell me that's not a theatre kid. He probably played Goston for the Beauty and the Beast musical in highschool and I don't know why.
Someone said he's a werewolf and it's the funniest thing I've read. (I can't rell you who because I found it on Facebook and it was their personal account...)
When he's folding origami, he folds it neatly and perfectly aligned.
Willy invites him for meal sometimes if he's cooking at home. Don't starve Elliott, you're too glamorous.
Broke ass. (We all agreed on this and it's because he spent most of his money on hair care products. Or some good quality papers.)
Wait, have you guys ever realized that this man has OCs? THIS GUY LITERALLY HAVE OCS? OF COURSE HE HAVE OCS, HE'S A WRITER...
#elliott sdv#stardew valley elliott sdv#headcanons#elliott headcanon#sdv headcanons#elliott stardew#stardew elliott#stardew valley elliott#elliott stardew valley#sdv elliott#elliott#stardew valley#stardew#stardew valley memes#elias talk
61 notes
·
View notes
Text
This will freak you out
... or at least I hope it does. Yes, I know most of the stuff I post on here is just kinky and horny talk and that's totally fine. By now, thousands of users have found their way to my blog and I'm very grateful for the support. I know I don't share much about myself, but the following will be about a more personal matter. I work in IT, or more specifically, with data. Lots of data. Being into data science, I am hyper-aware of the constant collecting and aggregating of user data. I know it's somewhat common knowledge that you're being tracked, but I want to take this opportunity to point out how bad the situation is and why privacy matters. I'll try to keep it as easy to follow as possible, so please bare with me!
The Trackers
Right now, you're on Tumblr. As you are reading this, your app connects to over a dozen servers that are not from Tumblr itself. They are from companies like Google, Amazon, Yahoo, but also lesser known companies such as Adjust and Moat. Within a single day, the Tumblr App sends about 5.000 tracking requests to the aforementioned and more companies, sharing your personal data. That's once every 15-20 seconds, regardless of whether you have the app opened or not. While I can't say exactly what data is being shared, it is likely that this is personal information that can be utilized to assume your opinions, target ads, or predict future behavior, as these are ways how companies will ultimately make money. Depending on what permissions you have granted the Tumblr app, it might also scan your gallery, your entire file system, access your call history, or your camera and microphone. By granting this permission, you are essentially giving Tumblr the keys to your phone on a complete "just trust me, bro"-basis. To me personally, that sounds scary.
But why do you use Tumblr yourself, then?
Very good and fair question! I actually am conflicted regarding using Tumblr, but I have put several security measures into place to minimize tracking potential as much as possible. While Tumblr can still see when I go online, read all the messages I send to others, know what content I view, like, comment on, and otherwise engage with, that is about it. Tumblr cannot acces my general file system, it cannot remotely access my camera and microphone, and even all the aforementioned trackers are blocked. I'll go more into this later.
"So what, I've got nothing to hide."
It's great that you think that! That's just what the big tech companies want you to believe. But answer me this: have you ever found it uncomfortable when a person next to you was reading all your texts, looking at your gallery, and just generally kept an eye on what you do on your phone at all times? Well, if a single person doing that is bothering you, how much worse must it be to know that several companies with thousands of employees spy on you for a living? Yes, they have seen your nudes, your breakup texts, your hours of Whatsapp calls with your best friend. It's literally a Big Brother Dystopia.
"Why would they be interested in me?"
I bet you have heard about the Cambridge Analytica (CA) scandal from 2018. Just to summarize: a data analytics company CA worked closely together with Facebook to target adds specifically tailored to users to manipulate them into voting for Donald Trump as President. If you are asking how specific this could be, just look at this demonstration by Signal, where their ads are extremely specific to a point where probably only a few thousand if not only hundreds of people would fit the description and just those exact people saw their ad.
"You got this ad because you're a newlywed pilates instructor and you're cartoon crazy. This ad used your location to see you're in La Jolla. You're into parenting blogs and thinking about LGBTQ adoption."
Facebook took it down within hours. But imagine you seeing this ad of a random company knowing this much and lots more about you. Note that Instagram and WhatsApp belong to Facebook/Meta, so even if you're not using Facebook directly, you're still being watched just as closely.
Knowing exactly what you like, dislike, fear, and love, strong emotions can be triggered for political or financial gain. You're into sustainability? Buy this product and we will retrieve one pound of plastic from the ocean! You are conservative and maybe slightly racist? Immigrants are taking over more and more healthcare jobs! You are scared by a possible nuclear war? Vote us for safety and peace!
This is how Cambridge Analytica managed to pull in millions of voters in the US and manipulate the election in a way that Donald Trump wouldn't have won without their manipulation. This is literally a threat to democracy. And as you know, my allegiance is to the Republic, to Democracy!
You might be aware of how right-wing and extremist parties all around the western world use very polarizing and emotional topics in their campaigns and are doing very well on social media. Often much better than more centered, leftist, or conservative parties, who tend to polarize less. This is not a coincidence. Not only is this because of customized, targeted content, but it's also because strong emotions generate more attention
Doom Scrolling & Dopamine
Social Media has had decades to perfect their dopamine lottery. The algorithms know exactly what you are into, no matter how much of a niche it might be. A good, user-oriented algorithm would show you a few posts, the best ones of the day, and then simply say "well, that's been all the good stuff. Wanna see the rest anyways?". But that's not how it works, is it? When opening an app like Instagram, TikTok, Tumblr, etc., you usually immediately land on a recent top-post. This is to give you the instant gratification and that sweet hit of dopamine.
Have you ever noticed how you had to scroll a bit before you got a post again that you really loved? That's by design. The mix of top-posts and mediocre ones is on purpose, to keep you waiting for more. You never know when the next super funny TikTok will come by. All you know is that it might be the next one. In-between top-posts, you're met with mediocre garbage and an add or two and just before it gets too boring, you hit gold again. The constant release of much higher than normal amounts of dopamine make your brain temporarily lose touch with what levels are normal. Why is it that you feel drained and tired after scrolling through social media for a few hours, even though you've done nothing but sitting around? You didn't think hard, you didn't move much, so what is it? It is the dopamine-rollercoaster that is mentally straining you. And there are tens of thousands of highly trained software engineers and corporate executives designing their platforms to keep you scrolling for as long as possible. If that little chiming sound increases your screen time by as little as 2%, it will be added. It is designed to suck your life away, chain your eyeballs to the content they want you to see, just so they can literally sell you to anyone who has the cash. You need that new gadget, visiting this country is an absolute must, this new sports competition is amazing, definitely vote for this cool party. Trust them. They know what you want. You don't know anything about them, but they know everything about you.
"What do I do now?"
Well, it is unlikely that you'll stop using social media at all. I mean, even I am still here. But there are things you can and should do for your mental and financial health, and for your own safety and protection against manipulation. Here is a list of things you should consider
Limiting social media to only a few apps you actually use and are interested in
Spend no more than 2 hours on social media per day
Meet friends irl instead of only texting
Stop sharing personal information. It is not illegal to enter false names, birthdays, etc into random sign-up forms! Protect your children as well!
Use privacy- & user-oriented platforms, such as Signal instead of WhatsApp, or Mastodon instead of Twitter. They finance themselves through volunteers and donations instead of by selling your data and lifetime to any buyer
Use privacy-oriented frontends (the visual interface and application you interact with), such as NewPipe or FreeTube instead of YouTube. You also won't be seeing any ads there
Don't buy anything impulsively. Take a week or two to think about whether you really need and want it.
Check facts, do your own research, use multiple sources, be critical
And in case you're interested in what I use:
I'm have an Android phone running /e/OS and a total of 5 computers/servers which run Linux and a Windows laptop for work. My phone block any trackers, fakes my GPS location (not VPN/IP) to where I am in Barcelona. All devices have a 24/7 encrypted VPN connection. I don't have WhatsApp, Instagram, Facebook, Twitter, or even a Google account. For personal use I have Signal, Element (Discord alternative), and Proton Mail. That's it. Every website or platform I have an account on has it's own, unique, single-use email, a randomized password and 2FA whenever possible. I use KeePass as my password manager, encrypted with a password, key file, and hardware key. I enter false data into any random form, use hardened Firefox browsers to resist fingerprinting and tracking, and back up all my data at home on a hard drive instead of using a cloud service. (Yes, there is much more)
For my content, I use Tumblr and a semi-active Discord account, Reddit accounts are banned.
For my professional life, I am forced to use Microsoft Teams and Outlook, yet I only use those on my work computer & phone.
Privacy = Freedom
Yes, I know my measures are far beyond average, but I wanted to present an example and hopefully inspire some of you to take back your online freedom and privacy! Because that's what it is! Privacy is Freedom!
I hope this inspired you and please ask any questions in the comments! This truly is a topic that means a lot to me so thank you for reading all the way through it. Please reblog to further share this important topic and encourage others to protect themselves!
- Ace
68 notes
·
View notes
Note
Hi, where would you go tumblr does go (I doubt it will, the same has been said about twitter)? I mean, I have bluesky, but it gets too defeatist for me to check out often.
Hey!
If tumblr collapses or becomes too unusable, I'll be moving to either Mastodon or Cohost, barring some kind of big change in the social media landscape.
Why those two? Because they're the only other (afaik) social media sites of any prominence that don't have an algorithm. And algorithms on social media sites, as it currently stands, have a strong tendency to suppress good news and push bad news (because anger and sadness get higher engagement), so as a good news blog, I don't think I'd do very well anywhere else!
(Also because the big social media sites routinely hide users' posts from said users own followers to try to force people to buy ads, and I would like people to actually see my good news posts, weirdly enough!)
Sources on the social media bs things: x, x, and I can't find verification of the hiding posts from your followers bit, but I promise it's a thing - it's one of the reasons I stopped running a page for my business on facebook a year or so ago
101 notes
·
View notes
Text
“I’m scared to pirate stuff - ” do it scared!*
*with Firefox and Adblock and a VPN and -
If you want a nonspecific, nonexhaustive “where do I even start” guide…
Sail the cyber seas at your own risk!
Streaming - “I want to watch xyz”
This is normally what most people want when they talk about pirating.
Use Firefox with uBlock Origin and additional privacy add-ons such as PrivacyBadger, TrackMeNot, etc.
Free VPNs are out there. Get one - but vet it’s efficacy. My go-tos are Proton VPN, or Windscribe if you plan to do a bit of torrenting.
What is torrenting? How does it work? Here’s a guide!
Back to streaming -
Make sure that a) you’ve got your Mozilla browser with all its adblocking private glory, and b) you’ve got a VPN turned on to hide what you’re doing in that browser from your ISP (internet service provider).
Now you need to actually find a site to stream from. This is the tricky part, because openly sharing these sites will get them taken down if they’re talked about widely enough. (Remember how tiktok idiots got zlibrary taken down?)
You’re going to have to talk to people on forums. You’re going to have to experiment with sites you find yourself. Search for ‘x online free’ and look at the links that come up - is the preview text mangled or clickbaitey? Are there Reddit threads about that website confirming or denying its content? A good rule of thumb is to ignore the top result or two - copycats of good streaming sites will often buy out the top result spot. Eventually, you’ll develop a good gut feeling and understanding of what a good site ‘looks like’ from the results page alone.
However, there are some places that compile good sites that haven’t been nuked by lawyers (yet) - check out r/FMHY! The masterposts are actively curated and updated when a site goes down or is found to have malicious downloads.
Remember - loose lips sink ships. No tweeting (xeeting?) or Facebook statuses about your new favorite piracy website and where you found it. Even posting to tumblr (kind of like this…) isn’t a great idea if you want those websites to stay under the radar and stay accessible. Nobody talks, everybody walks (away with their share of pirate booty)
If you aren’t downloading media, pick pretty much any site and watch away! Adblock and Firefox will keep away pop-ups and other annoying ads, and your VPN means your ISP can’t tell that you’re visiting an unofficial streaming service.
Note: In my experience, I’ve never heard of visiting a site and watching stuff on it infecting or otherwise compromising your computer. That tends to come from misclicks on invisible or overwhelming pop-up ads that redirect you to an automatic download or similarly malicious bullshit. If you’re using Firefox and uBlock, you shouldn’t be in any danger of an accidental redirect.
Downloads - “I want to keep xyz”
This is the realm of pirate archiving - you’re keeping files physically on your hard drive, an external hard drive, or burning a disk.
Adblock + Firefox browser? Check. VPN on? Check.
Go to your streaming site of choice - most if not all have download options. You can download those files or, manually, right click and save the video file from the webpage as an mp4. I honestly don’t know if there’s a difference in quality or more danger in clicking the download buttons, but regardless -
Run that puppy through VirusTotal.com! It’s a reliable browser based virus checker - if the file is too large, use a local virus checking program (your native Windows Defender on Windows computers or, I prefer, Malwarebytes)
Generally mp4 and mp3 files are clean - choose where to save them for the long term, and bam! Free forever media.
Optionally, I also upload mp4 files to a named Google document - this way I can easily share them or make them findable through a ‘xyz Google doc’ search for others :]
Torrents - “I want to keep and share xyz”
I’m not going to go into this subject in depth because, honestly, it’s not something I do regularly.
See the previously linked Torrenting guide for information on how the process works, and check out r/FMHY for recommendations and warnings about different torrenting clients (I’ve personally only used qBittorrent - I’ve heard to stay away from the Pirate Bay and Bittorrent.)
As with streaming, turn on that VPN baby! You’re going to need one that supports peer-to-peer (p2p) connections, so Proton’s free version is a no-go. Windscribe is what I’ve used for torrenting (and it’s a good free VPN on its own - I’m just partial to Proton). You get 10GB every month on Windscribe’s free version, which is more than enough for a few movies/a season or two of your favorite show.
(Bigger torrents like video games are easily 30+ GB, so be prepared to either pay for a no-limit premium account or spend a few months downloading your files in chunks.)
VPN on? Double check.
Boot up your torrenting client - I use a slightly out of date version of qBittorent, but there are other options. The Reddit thread and previously linked torrenting guide have a few dos and donts of selecting a client, so be thorough before you download your client of choice.
This is getting into the logistics of torrenting a bit, so forgive me if this is vague or incorrect, but now you need a torrent seed. These will be .tor files found through pirating websites or archives - these are rarely malicious, but it’s good to run any piracy related download through something like VirusTotal.com or scan it with a local program like Malwarebytes.
You open your seed file in your client and wait. A ‘healthy’ seed tends to have lots of seeders and few leeches, but sometimes you’re stuck with an obscure seed you just have to wait for.
Your torrented files have fully downloaded! Now what? a) keep your client open and seed those files for others as long as you want to - sharing is caring! and b) run those files through a security program like Malwarebytes (not sponsored it’s just the only program I’m familiar with).
Be wary of what gets flagged - sometimes the files seem important, but are just trojans, and likewise sometimes they seem malicious, but are just cracked software getting flagged by your system. It’s good to check and see if others have had a problem with this particular torrent before - Reddit threads from 2008 are your long dead friends.
And that’s about it. Feel free to correct me if anything I’ve recommended is malicious or outright wrong. I’ve been doing this for years and haven’t had an active problem to my knowledge, so if there is something fishy with how I do things, I am a statistical outlier and should not be counted.
I wish you smooth sailing and strong winds in your ventures me hearties!
Obligatory ‘don’t pirate small author’s or artist’s works what the fuck dude’ statement.
#ra speaks#piracy#pirating#pirate to make hondo ohnaka proud#I’ve seen so many people on my streaming piracy post bemoaning that they don’t know how like !!!!#congrats you get to learn without the middle school trial and error phase we zillenials had (RIP family computer 2004-2009)#I genuinely think piracy has gotten easier/safer than it used to be. that or I’ve gotten smarter. which is also likely.
365 notes
·
View notes
Note
Ineffable husbands x reader (platonic)! They've been noticing how much they've been on their phone lately, always smiling and giggling. Azira quickly assumes they're seeing someone and being the match maker he is at heart, he and Crowley manage to get the phone but the only thing on it is that Y/N is in a Facebook group about pretending to be ants in an ant colony (it's an actual thing).
A/n- This is so oddly specific and I love it! Kind of reminds me of when I was obsessed with Mystic Messenger which is just being in fake relationships with anime boys and girls... yeah I didn't have many friends in a high school LOL. Also, tell me why I am researching information about ants for a fanfiction!
Pronouns- (They/them)
Word Count- 930
Y/n's Ant Hill
Aziracrow x (Plantonic Reader)
Summary- The reader has been giggling at their phone non-stop recently Crowly is insistent that the reader has a significant other so he steals their phone.

Y/n is entranced by their phone having no idea about their surroundings.
Crowley throws his hands up in the air, "Okay that is the tenth time they giggled in five minutes!"
Aziraphale smiles at Crowley's outburst, "I am sure you are overexaggerating dear."
Crowley leans closer to Y/n to get a better look at their phone, "They have to be seeing someone!"
"Crowley, shh you are talking about Y/n as if they are not even there!" Aziraphale chastises him.
Crowley waves his hand dismissively, "They can't hear me they have no idea what's happening around them. Watch," he proceeds to clap directly in front of Y/n's face who does not even blink.
Aziraphale narrows his eyes, "That is actually quite impressive. I wonder what has Y/n so engrossed."
Crowley rolls his eyes, "Angel, I am telling you there is only one explanation they are seeing someone!"
"If they are they will tell us when they are ready," he places a comforting hand on Crowley's shoulder.
"Why would they be hiding it from us? We are their best friends we need to make sure we give their significant other a talking-to about the rules and what happens if they hurt Y/n! It can not wait," he cracks his knuckles.
"My dear maybe that's why their not telling you, " Aziraphale pats the shoulder his hand was already on and Crowley simply hisses in response.
Y/n abruptly stands, "I am really craving some hot cocoa, this weather is frigid. You want some?" Y/n asks the pair.
"I'd love some, thank you," Aziraphale smiles.
Crowley simply nods in response but as soon as Y/n leaves the room he jumps to the couch to where Y/n was just sitting.
"Ha! They left their phone," he smiles quickly typing the password.
"I am not even going to ask why you have their password memorized," Aziraphale frowns and Crowley looks up at him with a devilish grin.
Crowley's face quickly turns from devious to utter shock so much so that it concerns Aziraphale.
"What is that look is Y/n some sort of trouble?" He asks his parent mode instantly activated.
"They are fine physically not sure mentally though...," Crowley says full of pure confusion.
"What is it?" Aziraphale slides right up into Crowley's side.
"So much for you judging me for invading their privacy," he smirks at Aziraphale who shoots back a glare.
New messages appear from several different people one reads *foraging food for our queen* another reads *adding more tunnels for our queen* the last one they read says *Found a humongous picnic for our queen! Ants assemble!*
"What on God's earth is this!" Aziraphale surprisingly shouts and it just so happens that Y/n had just walked in with the three hot cocoas.
Y/n's face sours at them on her phone and accidentally drops one of the cups which breaks on impact with the floor.
Y/n quickly apologizes but then stops, "You know what I am not sorry that is a total invasion of my privacy! Crowley I expect this behavior from you but not you Aziraphale!""
Aziraphale quickly gets up, "I am so sorry Y/n! Let me clean the glass I don't want you to get hurt."
"Oh, so you don't want me to get hurt but hurting my feelings is fair game," Y/n glares.
"Y/n, be nice to the angel. It was my idea he got pulled in because of your weird group chat called Y/n's Ant Hill," Crowley says trying to calm them.
Y/n crosses their arms, embarrassment written clearly on their face, "You saw that? You still shouldn't have read the messages."
"We were concerned that you had a significant other and weren't sharing it. I assumed they were some heathen instead I see you roleplaying as an ant! It is far beyond anything any demon or angel could conjure in their mind." Crowley says with shock but also a weird sense of pride in humans.
Y/n tries to defend themself, "If you must know I am not any ant... I am their queen."
Aziraphale smiles and tries to hold back a laugh but at this point, Crowley is dying of laughter.
Y/n looks extremely bitter and Aziraphale tries to brighten their mood, "At least you hold a position of power."
Y/n's eyebrows furrow in anger, "Try it! I swear it is fun! If you don't like it you can make fun of me for it as long as you want if you do like it you can never say a bad word about it again!"
"You know I am always down for a little wager," Crowley smirks.
Y/n smiles, "Good! You Aziraphale?"
"It does sound very strange... but I will do anything for your forgiveness of your breach of privacy," Aziraphale says full of sorrow.
Y/n clasps their hands together, "Perfect!"
They spend the next hour huddled around Y/n's phone.
*I demand you find me the biggest feast an ant has ever feasted on* Crowley types.
Y/n tries to tug the phone away, "Stop they will overthrow me!"
"I'd like to see them try," Crowley wickedly smiles.
"Nooo," Y/n whines.
"For goodness sake why is my best friend and the love of my life the most insane begins I have ever met." Aziraphale sighs.
Safe to say Crowley gets Y/n overthrown and they have to start a whole new colony over together and Aziraphale can now never get them off the phone.
#crowly x aziraphale#good omens x reader#good omens fanfiction#good omens imagine#good omens fic#good omens drabble#crowley x reader#aziraphale x reader#aziraphale imagine
165 notes
·
View notes
Text
Pluralistic: Leaving Twitter had no effect on NPR's traffic

I'm coming to Minneapolis! This Sunday (Oct 15): Presenting The Internet Con at Moon Palace Books. Monday (Oct 16): Keynoting the 26th ACM Conference On Computer-Supported Cooperative Work and Social Computing.

Enshittification is the process by which a platform lures in and then captures end users (stage one), who serve as bait for business customers, who are also captured (stage two), whereupon the platform rug-pulls both groups and allocates all the value they generate and exchange to itself (stage three):
https://pluralistic.net/2023/01/21/potemkin-ai/#hey-guys
Enshittification isn't merely a form of rent-seeking – it is a uniquely digital phenomenon, because it relies on the inherent flexibility of digital systems. There are lots of intermediaries that want to extract surpluses from customers and suppliers – everyone from grocers to oil companies – but these can't be reconfigured in an eyeblink the that that purely digital services can.
A sleazy boss can hide their wage-theft with a bunch of confusing deductions to your paycheck. But when your boss is an app, it can engage in algorithmic wage discrimination, where your pay declines minutely every time you accept a job, but if you start to decline jobs, the app can raise the offer:
https://pluralistic.net/2023/04/12/algorithmic-wage-discrimination/#fishers-of-men
I call this process "twiddling": tech platforms are equipped with a million knobs on their back-ends, and platform operators can endlessly twiddle those knobs, altering the business logic from moment to moment, turning the system into an endlessly shifting quagmire where neither users nor business customers can ever be sure whether they're getting a fair deal:
https://pluralistic.net/2023/02/19/twiddler/
Social media platforms are compulsive twiddlers. They use endless variation to lure in – and then lock in – publishers, with the goal of converting these standalone businesses into commodity suppliers who are dependent on the platform, who can then be charged rent to reach the users who asked to hear from them.
Facebook designed this playbook. First, it lured in end-users by promising them a good deal: "Unlike Myspace, which spies on you from asshole to appetite, Facebook is a privacy-respecting site that will never, ever spy on you. Simply sign up, tell us everyone who matters to you, and we'll populate a feed with everything they post for public consumption":
https://lawcat.berkeley.edu/record/1128876
The users came, and locked themselves in: when people gather in social spaces, they inadvertently take one another hostage. You joined Facebook because you liked the people who were there, then others joined because they liked you. Facebook can now make life worse for all of you without losing your business. You might hate Facebook, but you like each other, and the collective action problem of deciding when and whether to go, and where you should go next, is so difficult to overcome, that you all stay in a place that's getting progressively worse.
Once its users were locked in, Facebook turned to advertisers and said, "Remember when we told these rubes we'd never spy on them? It was a lie. We spy on them with every hour that God sends, and we'll sell you access to that data in the form of dirt-cheap targeted ads."
Then Facebook went to the publishers and said, "Remember when we told these suckers that we'd only show them the things they asked to see? Total lie. Post short excerpts from your content and links back to your websites and we'll nonconsensually cram them into the eyeballs of people who never asked to see them. It's a free, high-value traffic funnel for your own site, bringing monetizable users right to your door."
Now, Facebook had to find a way to lock in those publishers. To do this, it had to twiddle. By tiny increments, Facebook deprioritized publishers' content, forcing them to make their excerpts grew progressively longer. As with gig workers, the digital flexibility of Facebook gave it lots of leeway here. Some publishers sensed the excerpts they were being asked to post were a substitute for visiting their sites – and not an enticement – and drew down their posting to Facebook.
When that happened, Facebook could twiddle in the publisher's favor, giving them broader distribution for shorter excerpts, then, once the publisher returned to the platform, Facebook drew down their traffic unless they started posting longer pieces. Twiddling lets platforms play users and business-customers like a fish on a line, giving them slack when they fight, then reeling them in when they tire.
Once Facebook converted a publisher to a commodity supplier to the platform, it reeled the publishers in. First, it deprioritized publishers' posts when they had links back to the publisher's site (under the pretext of policing "clickbait" and "malicious links"). Then, it stopped showing publishers' content to their own subscribers, extorting them to pay to "boost" their posts in order to reach people who had explicitly asked to hear from them.
For users, this meant that their feeds were increasingly populated with payola-boosted content from advertisers and pay-to-play publishers who paid Facebook's Danegeld to reach them. A user will only spend so much time on Facebook, and every post that Facebook feeds that user from someone they want to hear from is a missed opportunity to show them a post from someone who'll pay to reach them.
Here, too, twiddling lets Facebook fine-tune its approach. If a user starts to wean themself off Facebook, the algorithm (TM) can put more content the user has asked to see in the feed. When the user's participation returns to higher levels, Facebook can draw down the share of desirable content again, replacing it with monetizable content. This is done minutely, behind the scenes, automatically, and quickly. In any shell game, the quickness of the hand deceives the eye.
This is the final stage of enshittification: withdrawing surpluses from end-users and business customers, leaving behind the minimum homeopathic quantum of value for each needed to keep them locked to the platform, generating value that can be extracted and diverted to platform shareholders.
But this is a brittle equilibrium to maintain. The difference between "God, I hate this place but I just can't leave it" and "Holy shit, this sucks, I'm outta here" is razor-thin. All it takes is one privacy scandal, one livestreamed mass-shooting, one whistleblower dump, and people bolt for the exits. This kicks off a death-spiral: as users and business customers leave, the platform's shareholders demand that they squeeze the remaining population harder to make up for the loss.
One reason this gambit worked so well is that it was a long con. Platform operators and their investors have been willing to throw away billions convincing end-users and business customers to lock themselves in until it was time for the pig-butchering to begin. They financed expensive forays into additional features and complementary products meant to increase user lock-in, raising the switching costs for users who were tempted to leave.
For example, Facebook's product manager for its "photos" product wrote to Mark Zuckerberg to lay out a strategy of enticing users into uploading valuable family photos to the platform in order to "make switching costs very high for users," who would have to throw away their precious memories as the price for leaving Facebook:
https://www.eff.org/deeplinks/2021/08/facebooks-secret-war-switching-costs
The platforms' patience paid off. Their slow ratchets operated so subtly that we barely noticed the squeeze, and when we did, they relaxed the pressure until we were lulled back into complacency. Long cons require a lot of prefrontal cortex, the executive function to exercise patience and restraint.
Which brings me to Elon Musk, a man who seems to have been born without a prefrontal cortex, who has repeatedly and publicly demonstrated that he lacks any restraint, patience or planning. Elon Musk's prefrontal cortical deficit resulted in his being forced to buy Twitter, and his every action since has betrayed an even graver inability to stop tripping over his own dick.
Where Zuckerberg played enshittification as a long game, Musk is bent on speedrunning it. He doesn't slice his users up with a subtle scalpel, he hacks away at them with a hatchet.
Musk inaugurated his reign by nonconsensually flipping every user to an algorithmic feed which was crammed with ads and posts from "verified" users whose blue ticks verified solely that they had $8 ($11 for iOS users). Where Facebook deployed substantial effort to enticing users who tired of eyeball-cramming feed decay by temporarily improving their feeds, Musk's Twitter actually overrode users' choice to switch back to a chronological feed by repeatedly flipping them back to more monetizable, algorithmic feeds.
Then came the squeeze on publishers. Musk's Twitter rolled out a bewildering array of "verification" ticks, each priced higher than the last, and publishers who refused to pay found their subscribers taken hostage, with Twitter downranking or shadowbanning their content unless they paid.
(Musk also squeezed advertisers, keeping the same high prices but reducing the quality of the offer by killing programs that kept advertisers' content from being published along Holocaust denial and open calls for genocide.)
Today, Musk continues to squeeze advertisers, publishers and users, and his hamfisted enticements to make up for these depredations are spectacularly bad, and even illegal, like offering advertisers a new kind of ad that isn't associated with any Twitter account, can't be blocked, and is not labeled as an ad:
https://www.wired.com/story/xs-sneaky-new-ads-might-be-illegal/
Of course, Musk has a compulsive bullshitter's contempt for the press, so he has far fewer enticements for them to stay. Quite the reverse: first, Musk removed headlines from link previews, rendering posts by publishers that went to their own sites into stock-art enigmas that generated no traffic:
https://www.theguardian.com/technology/2023/oct/05/x-twitter-strips-headlines-new-links-why-elon-musk
Then he jumped straight to the end-stage of enshittification by announcing that he would shadowban any newsmedia posts with links to sites other than Twitter, "because there is less time spent if people click away." Publishers were advised to "post content in long form on this platform":
https://mamot.fr/@pluralistic/111183068362793821
Where a canny enshittifier would have gestured at a gaslighting explanation ("we're shadowbanning posts with links because they might be malicious"), Musk busts out the motto of the Darth Vader MBA: "I am altering the deal, pray I don't alter it any further."
All this has the effect of highlighting just how little residual value there is on the platform for publishers, and tempts them to bolt for the exits. Six months ago, NPR lost all patience with Musk's shenanigans, and quit the service. Half a year later, they've revealed how low the switching cost for a major news outlet that leaves Twitter really are: NPR's traffic, post-Twitter, has declined by less than a single percentage point:
https://niemanreports.org/articles/npr-twitter-musk/
NPR's Twitter accounts had 8.7 million followers, but even six months ago, Musk's enshittification speedrun had drawn down NPR's ability to reach those users to a negligible level. The 8.7 million number was an illusion, a shell game Musk played on publishers like NPR in a bid to get them to buy a five-figure iridium checkmark or even a six-figure titanium one.
On Twitter, the true number of followers you have is effectively zero – not because Twitter users haven't explicitly instructed the service to show them your posts, but because every post in their feeds that they want to see is a post that no one can be charged to show them.
I've experienced this myself. Three and a half years ago, I left Boing Boing and started pluralistic.net, my cross-platform, open access, surveillance-free, daily newsletter and blog:
https://pluralistic.net/2023/02/19/drei-drei-drei/#now-we-are-three
Boing Boing had the good fortune to have attracted a sizable audience before the advent of siloed platforms, and a large portion of that audience came to the site directly, rather than following us on social media. I knew that, starting a new platform from scratch, I wouldn't have that luxury. My audience would come from social media, and it would be up to me to convert readers into people who followed me on platforms I controlled – where neither they nor I could be held to ransom.
I embraced a strategy called POSSE: Post Own Site, Syndicate Everywhere. With POSSE, the permalink and native habitat for your material is a site you control (in my case, a WordPress blog with all the telemetry, logging and surveillance disabled). Then you repost that content to other platforms – mostly social media – with links back to your own site:
https://indieweb.org/POSSE
There are a lot of automated tools to help you with this, but the platforms have gone to great lengths to break or neuter them. Musk's attack on Twitter's legendarily flexible and powerful API killed every automation tool that might help with this. I was lucky enough to have a reader – Loren Kohnfelder – who coded me some python scripts that automate much of the process, but POSSE remains a very labor-intensive and error-prone methodology:
https://pluralistic.net/2021/01/13/two-decades/#hfbd
And of all the feeds I produce – email, RSS, Discourse, Medium, Tumblr, Mastodon – none is as labor-intensive as Twitter's. It is an unforgiving medium to begin with, and Musk's drawdown of engineering support has made it wildly unreliable. Many's the time I've set up 20+ posts in a thread, only to have the browser tab reload itself and wipe out all my work.
But I stuck with Twitter, because I have a half-million followers, and to the extent that I reach them there, I can hope that they will follow the permalinks to Pluralistic proper and switch over to RSS, or email, or a daily visit to the blog.
But with each day, the case for using Twitter grows weaker. I get ten times as many replies and reposts on Mastodon, though my Mastodon follower count is a tenth the size of my (increasingly hypothetical) Twitter audience.
All this raises the question of what can or should be done about Twitter. One possible regulatory response would be to impose an "End-To-End" rule on the service, requiring that Twitter deliver posts from willing senders to willing receivers without interfering in them. End-To-end is the bedrock of the internet (one of its incarnations is Net Neutrality) and it's a proven counterenshittificatory force:
https://www.eff.org/deeplinks/2023/06/save-news-we-need-end-end-web
Despite what you may have heard, "freedom of reach" is freedom of speech: when a platform interposes itself between willing speakers and their willing audiences, it arrogates to itself the power to control what we're allowed to say and who is allowed to hear us:
https://pluralistic.net/2022/12/10/e2e/#the-censors-pen
We have a wide variety of tools to make a rule like this stick. For one thing, Musk's Twitter has violated innumerable laws and consent decrees in the US, Canada and the EU, which creates a space for regulators to impose "conduct remedies" on the company.
But there's also existing regulatory authorities, like the FTC's Section Five powers, which enable the agency to act against companies that engage in "unfair and deceptive" acts. When Twitter asks you who you want to hear from, then refuses to deliver their posts to you unless they pay a bribe, that's both "unfair and deceptive":
https://pluralistic.net/2023/01/10/the-courage-to-govern/#whos-in-charge
But that's only a stopgap. The problem with Twitter isn't that this important service is run by the wrong mercurial, mediocre billionaire: it's that hundreds of millions of people are at the mercy of any foolish corporate leader. While there's a short-term case for improving the platforms, our long-term strategy should be evacuating them:
https://pluralistic.net/2023/07/18/urban-wildlife-interface/#combustible-walled-gardens
To make that a reality, we could also impose a "Right To Exit" on the platforms. This would be an interoperability rule that would require Twitter to adopt Mastodon's approach to server-hopping: click a link to export the list of everyone who follows you on one server, click another link to upload that file to another server, and all your followers and followees are relocated to your new digs:
https://pluralistic.net/2022/12/23/semipermeable-membranes/#free-as-in-puppies
A Twitter with the Right To Exit would exert a powerful discipline even on the stunted self-regulatory centers of Elon Musk's brain. If he banned a reporter for publishing truthful coverage that cast him in a bad light, that reporter would have the legal right to move to another platform, and continue to reach the people who follow them on Twitter. Publishers aghast at having the headlines removed from their Twitter posts could go somewhere less slipshod and still reach the people who want to hear from them on Twitter.
And both Right To Exit and End-To-End satisfy the two prime tests for sound internet regulation: first, they are easy to administer. If you want to know whether Musk is permitting harassment on his platform, you have to agree on a definition of harassment, determine whether a given act meets that definition, and then investigate whether Twitter took reasonable steps to prevent it.
By contrast, administering End-To-End merely requires that you post something and see if your followers receive it. Administering Right To Exit is as simple as saying, "OK, Twitter, I know you say you gave Cory his follower and followee file, but he says he never got it. Just send him another copy, and this time, CC the regulator so we can verify that it arrived."
Beyond administration, there's the cost of compliance. Requiring Twitter to police its users' conduct also requires it to hire an army of moderators – something that Elon Musk might be able to afford, but community-supported, small federated servers couldn't. A tech regulation can easily become a barrier to entry, blocking better competitors who might replace the company whose conduct spurred the regulation in the first place.
End-to-End does not present this kind of barrier. The default state for a social media platform is to deliver posts from accounts to their followers. Interfering with End-To-End costs more than delivering the messages users want to have. Likewise, a Right To Exit is a solved problem, built into the open Mastodon protocol, itself built atop the open ActivityPub standard.
It's not just Twitter. Every platform is consuming itself in an orgy of enshittification. This is the Great Enshittening, a moment of universal, end-stage platform decay. As the platforms burn, calls to address the fires grow louder and harder for policymakers to resist. But not all solutions to platform decay are created equal. Some solutions will perversely enshrine the dominance of platforms, help make them both too big to fail and too big to jail.
Musk has flagrantly violated so many rules, laws and consent decrees that he has accidentally turned Twitter into the perfect starting point for a program of platform reform and platform evacuation.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2023/10/14/freedom-of-reach/#ex


My next novel is The Lost Cause, a hopeful novel of the climate emergency. Amazon won't sell the audiobook, so I made my own and I'm pre-selling it on Kickstarter!

Image:
JD Lasica (modified)
https://commons.wikimedia.org/wiki/File:Elon_Musk_%283018710552%29.jpg
CC BY 2.0
https://creativecommons.org/licenses/by/2.0/deed.en
#pluralistic#twitter#posse#elon musk#x#social media#graceful failure modes#end-to-end principle#administratable remedies#good regulation#ads#privacy#benevolent dictatorships#freedom of reach#journalism#enshittification#switching costs
799 notes
·
View notes
Text
Hollywood stars shoot films in Bad Godesberg Exclusive | Bad Godesberg
The famous American actress Lili Reinhart shot for five days on Europastrasse in Bad Godesberg for her new film “American Sweatshop”. Producer Anita Elsani explains in an interview with GA why the filming had to remain secret and what the film is about.

The new film “American Sweatshop” was shot for five days in an apartment on Europastrasse in Bad Godesberg.
Child p*rnography, mutilated people and tortured animals flicker across the screens of so-called “content moderators”. Their job is to clean up social networks like Facebook, Instagram and YouTube. They delete pornographic and criminal videos and photos every day. Often it only takes a quick click to remove another violent video, but what you see stays in the minds of the moderators for a long time. This is also the case in the new thriller “American Sweatshop”, in German: American sweatshop, which deals with the real job and its consequences for people.
The main character Daisy is played by the well-known American actress Lili Reinhart. Reinhart starred in successful films and series such as “Hustlers” and “Riverdale”.
Now the Hollywood star ended up in the American settlement of Bad Godesberg to record scenes for her latest film. Also there: the English actor Josh Whitehouse, known from films such as “The Knight Before Christmas” with Vanessa Hudgens. “We shot several scenes in an apartment here for four to five days. The film itself takes place in Florida,” says the film’s producer, Anita Elsani. In the finished cut, the viewer will not recognize that the filming location was the Europastrasse in Bonn, says the Cologne native.
Filming had to remain secret
The General-Anzeiger had already found out about the filming last week and was there. However, the filming had to remain secret until the last day of filming. “We didn’t want any attention during filming so we could work in peace,” says Elsani. The film was a small production with little money, so shielding it from onlookers would have been too much additional effort. Added to this is the safety of the actors. “Actors often have problems with stalkers. As a producer, I am also responsible for making sure everyone feels comfortable and safe,” said the 52-year-old.

At Kenedyallee, residents were able to observe containers and actors and other crew members for several days. Photo: Selina Stiegler People who are in the public eye are more likely to have fans who excessively watch their idol's activities and send a lot of "niceties."
“Even if flowers and other attention are meant to be nice, those affected find it oppressive when they receive a certain amount and on a regular basis,” explains Elsani. They would also try to find filming locations to go to or send other supposed gifts. The game of hide-and-seek was successful despite smaller containers and a food truck along Kennedyallee.
The filming went largely unnoticed. The filming was carried out in Bonn without any difficulties and everyone was able to work in peace. “We also tried to disturb the residents as little as possible. The people here are really pleasant. Only a few people asked nicely and unobtrusively what we were doing here.” No further filming is planned in Bonn.
On the trail of a perpetrator
The producer does not want to reveal what the scenes filmed are about. “Taken out of context, it doesn’t make any sense,” she says. The thriller itself is about the employee Daisy, who works for a company as a content moderator. “How do people deal with the content that they have deleted from the Internet but not from their minds?” is a question that the film deals with. In the film, Rheinart embarks on a dangerous search for a particularly perfidious perpetrator. The producer says she doesn't yet know when viewers in the cinema will be able to see how the search turns out. “There is no premiere date yet, but I estimate the film will be released in the second half of 2025.”
The screenwriter is the American Matthew Nemeth, who spoke to real “content moderators” for research purposes. “The people in such sweatshops usually work from Asia, Africa or America,” says Elsani. The German directors Hans Block and Moritz Riesewieck had already explained the situation in the documentary film "The Cleaner" in 2018 and spoke to those affected in the Philippines. The Verdi union estimates that several hundred thousand "content moderators" on the Internet create content for the Delete the rest of the world.
The film is therefore a current and relevant film for all people who use social media privately. The viewer should learn that pornographic and criminal content is sorted out by hand by real people and what consequences that can have.
Cast and production “American Sweatshop” with an international cast
The German-American film “American Sweatshop” was shot in the MMC Studios in Cologne and in the American settlement of Bad Godesberg. In the media thriller, Hollywood actress Lili Reinhart plays an internet cleaner who embarks on a dangerous search for a particularly perfidious perpetrator. Daniela Melchior, Joel Fry and Christiane Paul also play in roles. The film is directed by German director Uta Briesewitz. The script was written by American author Matthew Nemeth. Producers are Cologne-based Anita Elsani (Elsani Film), Jason Sosnoff and Barry Levinson (Baltimore Pictures) and Tom Fontana. The film is scheduled to be released in 2025 and will be distributed to cinemas by Plaion Pictures. The Film and Media Foundation NRW supported the project with 400,000 euros.
41 notes
·
View notes
Text
Multiple police departments across Illinois are warning residents about the potential risks of a game called “senior assassins” in which high school students don ski masks and target each other with water guns that look like firearms.
In a Facebook post, the Gurnee police department said that on Tuesday a group of high school students from a neighboring community entered a local restaurant wearing ski masks and displayed water guns resembling firearms.
Despite the students attempting to target other students at the restaurant and spray them with water, an adult who was a concealed carry holder “mistook the situation for a genuine threat and the situation could have escalated quickly”, the police department said.
“The gravity of the situation cannot be emphasized enough; it had the potential to lead to serious consequences,” it warned, adding that incidents like these may warrant disorderly conduct charges.
Describing the game, Arlington Heights police department said that it is an “annual springtime tradition for students, especially seniors” and involves attempts to “forego match elimination by squirting other players using a water gun with a goal of being the last person remaining in the game”.
The police department added that game rules specify that the game cannot take place during school hours or on school property. Instead, players attempt to locate their opponents in other locations including homes, local parks and other public gathering spaces within the community. Participants will often hide in “odd spots, chase targets through yards and appear suddenly in a vehicle or on foot”, it said.
The police department went on to warn: “The unintentional result of participants running throughout the community with a water gun, some often resembling a look-alike firearm, could have deadly consequences.”
“We encourage parents to talk to their children about safety concerns linked to openly carrying a squirt gun that resembles a look-alike firearm and being on private property without permission. Consider the perception [of] an uninformed resident who sees a person rapidly displaying a replica firearm in a populated common area. That action could be viewed as ‘alarming and disturbing’ which are elements of a criminal offense and/or local ordinance violation – disorderly conduct,” it continued.
Echoing the Arlington Heights police department, the city of St Charles’ police department issued a similar warning and posted a photo online of the fake guns (though it did not say that these were the guns students had used).
In its Facebook post on 5 April, the city of St Charles’ police department said that over the past week, it has responded to numerous 911 calls from residents who are “witnessing individuals dressed in hoodies or masks, sneaking around their neighbor’s homes”.

“We remind students that they need to be aware that realistic-looking fake guns like those in this picture should not be used,” the police department said, adding, “Our officers respond to each of these 911 calls without knowledge of whether this is students just having fun or an actual crime about to be committed. We strongly encourage parents to please talk with your kids about this as well.”
(and here I thought at least one of these was real, someone's gonna get killed doing this)
39 notes
·
View notes
Text
9 - Life Changing Moments

Part 10
Dr. Redheaded Neighbor
Tag list - send an ask to be added @annieradcliff @watermeezer @zaidatorcuatomorgado @kmc1989
Maxon made a noise looking up at Will with a tilt of his head. “What do you think that conversation is going to be about, Max.” Will just sat down with him laying at his feet simply wanting to wait until she got back.
Sylvie and I exited the ED going to sit down on one of the benches outside the building so we could talk. I wasn’t sure what she needed to talk to me about or how she found me here at the hospital in the first place. “So, I have to ask how the hell did you find me here exactly?”
“I looked you up on the internet. Facebook showed some pictures with you and Dr. Halstead. I searched through his page and found out that he worked here. The chance of you being here still at the same town was a happy coincidence.” She explained and I nodded somehow not finding that creepy given the smile she had given me.
I clicked my tongue intertwining my hands together in my lap. “Okay, so – what exactly did you need to talk to me about privately?”
“I have been trying to rack my brain about why I couldn’t get you out of my head and it finally came to me. It’s because you clearly aren’t ready to be done helping people.”
I eyed my right leg wishing that I didn’t have the brace on all the time. “Maybe I am. I mean I had to be discharged from Army after I got injured. I don’t remember the last mission I only know I came home with this on me probably for the rest of my life.”
“Look I have been thinking about offering you a chance to come work at Firehouse 51 or at least consider looking into helping out there.” The female firefighter sends me a smile again.
Running a hand through my loose hair I sighed thinking about what she was offering. “Wow. That’s - that’s a huge offer. I mean I don’t have any training to be a Firefighter or Paramedic like you guys.”
“You’re right but you’d be able to learn on the job and take courses if you really want to look into what I’ve mentioned here.”
I asked her meeting her blue eyes. “Is this even allowed with your boss?”
“If you truly are considering saying yes, I will speak with him as soon as possible.” She reached forward touching my knee.
Since coming home I was just focusing on trying to adjust getting back to civilian lifestyle and getting spend more time with my best friend again. “I’ll let you know. Uh here – I can give you my phone number.” Taking out my phone I handed it to her showing my phone number.
“Thanks. Just call me, Mallory.” She put her number in my phone handing me my phone back.
The hospital sliding doors opened causing me and the firefighter to turn our heads and attention towards them. I saw Maxon coming towards me before I saw Will slowly running over to us. “Raegan is awake and asking for you. If you want to see her now.”
“Oh my gosh. Ms. Brett, I will certainly let you know my answer later.” Jumping up onto my feet Maxon bolted to the doors with me and Will following him inside the hospital doors. I entered the room she was supposed to be in seeing her sitting somewhat upright in her bed, smiling when I rushed to her bedside. “Rae, I was so worried about you. I – I thought something really bad was going to happen.”
She blew a raspberry at me. “I’m too stubborn to leave you alone. Especially when you haven’t fessed up and told your Redhead how you feel.”
“You know the thought of you dying is more important than my romantic life.” I sent her a glare.
She crossed her arms over her chest huffing at me. “Okay but you know that I’m right. Halstead from what I can tell isn’t very good about hiding his feelings. So, I see no issue with getting it over with and telling him that you have feelings for him too.”
“But what if he- “
She held her up left hand with an iv sticking in her arm. “I will take this out which will set off all the alarms and go find himself. Do you really want me to be the one to tell him what you won’t.”
Holding up my hands up in surrender in front of me I begged her. “Don’t you dare do anything like that. I’ll tell him soon okay.”
“You better.” Raegan sent me a warning look.
Pushing opened the apartment door I tossed my keys on the countertop the second I walked inside Will’s apartment while carrying in a pizza box that we had picked up on the way home from the hospital. Maxon jumped up onto the couch and he laid down in a curled-up position. Will came in shortly after sitting his bag by the door. “Oh, what a day. I gotta say I love being an ED doc but it sure wores me out.”
“At least now I finally kept up on my promise on bringing you this.” Spinning the pizza box around on the kitchen counter I drew the lid open and the familiar comforting smell filled the air.
He shrugged his jacket off ditching it onto the back side of the couch coming over in two long strides until his nose was right above the pizza box. “Ohh I’ve been needing this all day.”
“I gotta admit it is pretty good pizza.” I picked up a bite thinking back to my old home state. “I do remember the drive to Dominos wasn’t too bad either.”
Will set his piece of pizza down. “How dare you say bad things about me pizza..”
“I can’t help I’m from Indiana, Will.” I throw my hands up staring at him.
He glared at me across the kitchen island. “Dang country girl.”
“City slicker.” I did my best to hold a straight and serious face when I was looking at him but I only lasted a few more seconds. I bent my head down in my arms laughing my head off.
Will mirrored my laughter shaking his head. “Who would’ve thought that we would work together like this. Living together, me, you and Maxon.”
“We do make a pretty good trio.” Picking up my slice of pizza I take out a few bites before picking up another.
Will moved over to the couch sitting down with some pieces of pizza on his plate. “Do you ever think we’d still work together this great as a couple?”
“Wha – what did you say?” I nearly choked on the bite of pizza I had in my mouth.
Will’s gaze focused on me standing by the kitchen island sitting the plate down on the coffee table in front of him. I’ve been thinking for a while that I should have told you this much sooner. And so now I’m done waiting.” He rose from the furniture striding over to me until I held my hands up before he can say anything more.
“Will, hang on a second. I need to say something to you too. I – I just have been so terrified of what you would say.”
He rummaged around in his pocket holding up a random coin. “Let’s let luck decide this then. Heads, we say our feelings one at a time. Tails, we say them at the same time. And there’s no backing out.” Will tossed the coin up off his thumb and it landed down in his palm.
“What does it say?” I nervously gripped the ends of my tea shirt in my fingers nervous for his answer.
“Tails.”
I gulped. “Okay. 3 – 2 – 1.”
Will and I paused before uttering out at the same time. “I have feelings for you.”
Covering my mouth with my hands I felt some tears welling in my eyes. “I thought that you wouldn’t – um.” I didn’t know what to say considering I assumed he wouldn’t feel the same way since we’d been friends for over six years now.
“Why didn’t you tell me sooner?” He asked me.
I started to respond to him but he cut me off. “I was afraid that our relationship would be ruined and that you wouldn’t feel the same way- “
He crashed his lip’s down onto mine where I gasped taking a second to process what was happening. I had imagined what it would be like to kiss him but now that it was happening I thought I was dreaming. I leaned up slightly on my toes kissing him back and wrapping my arms around his neck.
“Mal, Mallory, listen to me okay.” He drew back holding my face in his hands, smiling through happy tears. “Our relationship could never be ruined by you being honest with me. Cause I have always had feelings for you. Always have, always will.”
I grinned up at him gripping the fabric of his shirt. “So this is for real?”
“Yes, Mallory. This is real.” He sent me that familiar cheeky grin. “Now what would you say to me taking you out on our first official date tomorrow night?’
Leaning up on my toes I began the next kiss we shared. “I’d love that.” Will moved his hands around my waist holding me against his chest until we broke away knowing the pizza was getting cold.
Comments really appreciated ❤️
#dr.redheaded neighbor#will halstead series#will halstead x reader#will halstead fanfiction#will halstead fic#will halstead x you#will halstead#nick gehlfuss#sylvie brett#chicago med#chicago med x oc#chicago med x reader#chicago med fic#chicago med fanfiction#one chicago#one chicago fanfiction#chicago fire#best friends#friends to lovers#military dogs#us army#wattpad fanfiction#ask box is open for feedback#comments really appreciated#chicago fire fanfic#chicago fire x reader#doctors#firefighters#oc : mallory easton#britt robertson
21 notes
·
View notes