#malware removal guide
Explore tagged Tumblr posts
Note
Hey, could you do a post on the spacers.exe scam on discord please? I got hacked from it and a friend then got hacked by my account and it super sucks!
🔎Scam Exam(ination)🔍
Seen as: Free game / Try my game Scam Type: Malware / Password Stealer
Platform: Discord
Note: This post will contain a collection of data from across the internet, mainly reddit where people have figured out how this malware works and what it does at its core. I will do my best to explain to you what's going on behind the scenes.
Here's a video talking about this same type of scam by NTTS:
youtube
If you'd like my take on it, click read more and let's continue!
-----
1 - How it starts
The way this scam works is by a friend of yours, or someone in the same server as you, falling for this scam and downloading then opening the malicious file that their friend had sent to them. In a very long line of things, it's a chain reaction of them hijacking and using the stolen account to then scam someone else. And if you're not quick enough, it can and will steal everything on your computer/phone.
Not everyone on the internet is scam savvy, but that's what guides like these are meant to help with. :)
Here are two images taken from reddit on what it looks like when you're contacted by the hijacked account:
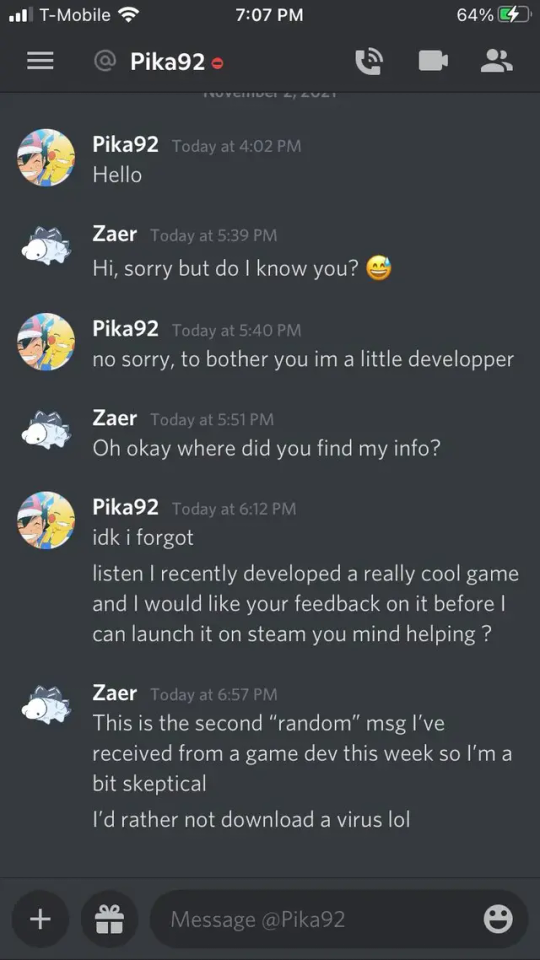
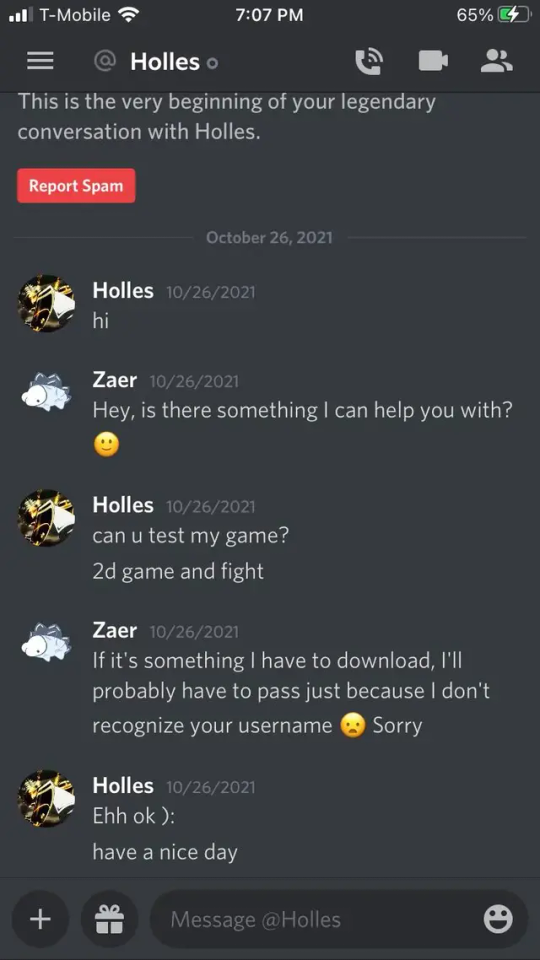
Immediate red flags:
I'm a developer. Try my game. Can you test my game?
Other reported red flags to look out for:
I need you to beta test my game. Download my game and try it for 4-5 minutes then write a review. Here's a free key/password for the game go to this link. I'm working on a project and need someone to try my game. I'll give you free items/vip if you try my game. Try this new mobile game <link> ** and I'll give you items. I'll pay you $ via PayPal or give you Nitro if you try it.
What it boils down to, is that for this scam to work, they need you to download the file they send you, or a file that's uploaded via a link to a file sharing website, and then you have to open the file.
Do not do this, obviously.
Do not accept any suspicious .exe or .jar files from your friends or fellow server members if you do not know what might be inside it.
** Sometimes they will send you an APK file or a link to the google play store for a mobile game, and sadly this too, is malware, and it will steal your passwords. Again, do not download it.
2 - The Malware/Virus
If you were someone who downloaded a file like this and then opened it, you have now infected your computer, and... unfortunately, all of your Passwords, addresses, Crypto info, and credit card information, have now been compromised.
Nothing is safe with this Malware.
A more in depth explanation of spacers.exe can be found here as well as how to remove spacers.exe:
youtube
Here's a second NTTS video explaining how the inner workings of this can work from the scammers point of view:
youtube
3 - The Goal
The goal of this malware, as noted above, is not just to steal your passwords, credit card info, but also your discord account.
There are people who will pay for this malware (it is being sold for others to use, which sucks) so that they can take over your discord accounts if you have certain badges or names.
If a scummy individual running this scam wants something they don't have that you do, they will try to take it from you.
Do be warned that if you fall for this, you may also receive threatening emails to have your personal information leaked if you don't pay a ransom/money amount after you got infected.
This is a scare tactic.
This was noted in this post from Dec 3rd 2024:
-----
Final Thoughts: All I can say is.. common sense should be a big factor here. Internet safety 101 and all that. You shouldn't be clicking links to anything or anyone saying something's 'free' or with the offer of you getting some reward from it. Nor should you go believing or downloading things from your friends if they start acting weird or weirder than normal.
Pro tip: If you get a message on steam or discord by someone asking you to 'visit this website' to 'vote for my friend in <thing>' that too is a scam and it will steal your login information.
If you're like me and your best friend on the internet is someone you've known online for 18 years, having him suddenly say 'I'm a developer try my game' would be a big indicator to me that his account was compromised.
If you can, try to make sure you're connected with your friends through other outlets like tumblr or bluesky. Or even through e-mail (as old as that seems lol.)
That way if something goes wrong, they can at least let you know about it.
#scam#scam alert#scams#scammer#scammers#scam awareness#discord#discord scam#online scams#scam warning
133 notes
·
View notes
Text
Embedding images on AO3: A Guide V2
Hi,
So, I thought I would go back and make an updated version of the A03 embedding image guide I made back in September of 2022.
This choice was mainly due to one of the options being viable.
Discord.
Due to the rise in malware distribution, Discord has set expirations on Discord links. This only applies to links that are used outside of Discord.
This short video explains this well
youtube
So, If we wanted to use the option, we would need to update the link every 24 hrs in your work.
Not great.
I know I also feel the salt.
Well, with that out the way, let's dive in.
A03 doesn’t actually allow for image hosting itself, so that’s why third-party hosting is needed.
In this guide, we will use these as possible choices to host our images
Google Drive
Tumblr
Imgur
https://postimages.org/
Other contenders:
IMGBB https://imgbb.com/
imgbox https://imgbox.com/
IMGBAM https://www.imagebam.com/
Image venue https://www.imagevenue.com/
Paste board https://pasteboard.co/
(Most if not all if these options listed require signup)
But really there are many options to choose from. If you have any recommendations, comment, and I’ll add them in.
Before we upload, you may need to compress your image(s) to shave them down to size, as some of these options upload size caps.
I recommend https://compressjpeg.com/ for this task. Or you may choose whatever your preference is.
Hosting options:
Option 1: Google Drive
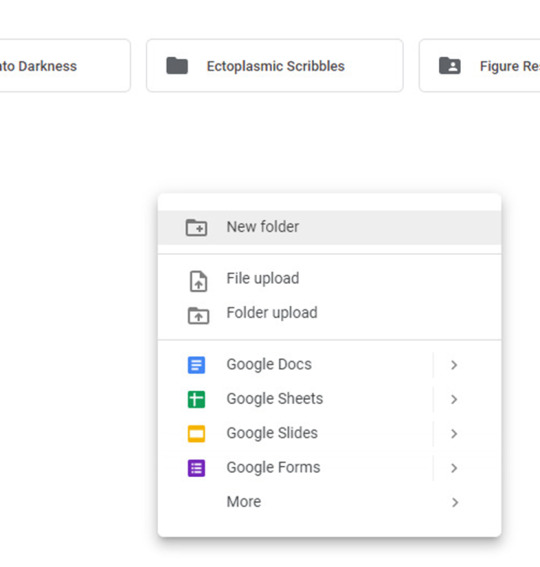
In Google Drive, create a new folder with the image(s) or subfolders for further organization.
Right-click and select New Folder, and name this folder whatever you want.
Now upload your image(s)
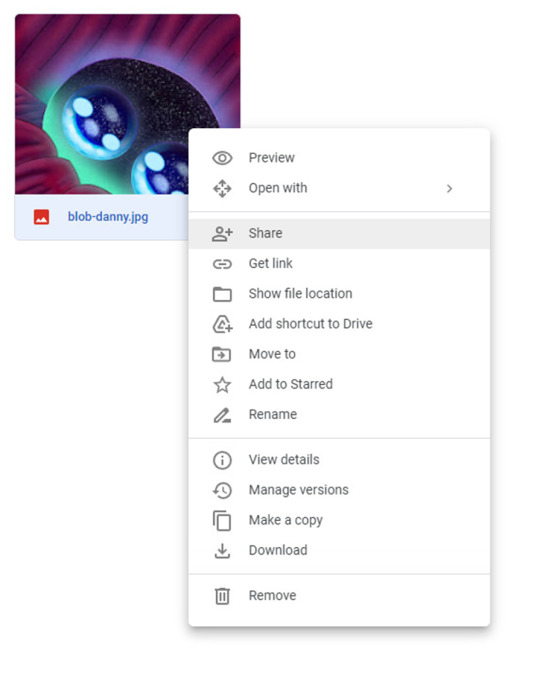
Right-click on your image and hit share.
Hit Copy link
The link you have should look something like this
https://drive.google.com/file/d/1Nt17i9jx8LYffyQQew6D2x4HYxXFM0_B/view?usp=sharing
But as is it won't work! We need to modify it first!
Remove the
/view?usp=sharing
at the end of the link to work with AO3
Now, you have a working link from Google Drive that is ready to use.
Your modified link should look like…
https://drive.google.com/file/d/1Nt17i9jx8LYffyQQew6D2x4HYxXFM0_B
This Google Drive portion was from this guide here: https://archiveofourown.org/works/28132845
Option 2 Tumblr:
Tumblr is not always the best platform to use, as blogs can get deleted or URLs can change. But I’ll include it here anyway.
On mobile
Long tap the image you wish to use in a post.
You will be presented with this menu.
Tap share photo.
Then, you will be presented with another menu.
On the desktop, it will basically be the same.
Right-click on the image and hit copy image address.
Now, you have a working link from Tumblr that is ready to use.
Option 3: Imgur
First sign up for an account. I would recommend this because last year, Imgur began deleting images not tied to a user account. This means that if you upload an image without an account, the image link may eventually expire and the image will be deleted.
Create a new post
Upload your desired photo(s).
Do not hit the Grab Link button

It will not work with AO3
Instead, right, click on the image and hit copy image link or address, depending on your browser.
Now your Imgur Link is ready to use.
Option 4: Using an image hosting service like postimages.org
You can create an account for free with this one. This is pretty straightforward, so I’ll gloss it over.
Once logged in you will be presented with this page.
Upload your image, and you will be taken to this page.
Copy Direct link
Now, you have a working link from postimages ready to use.
Step 2: Inserting and fitting the image
Head over to Ao3.
Go to the new or existing chapter in which you wish to embed image(s).
HTML OPTION:
Make sure in the HTML editor view.
This is located next to the rich text button in the Worktext section, as shown.
Now, find the place in the text where the image should go...
Now, preview your work to confirm the link is correct.
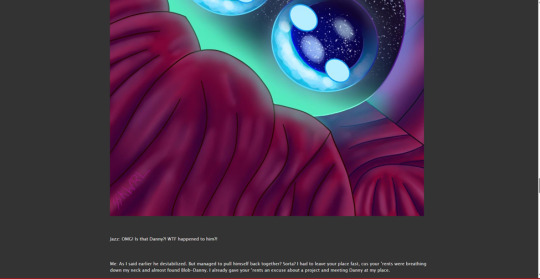
As you can see the image worked but in my case the image was waaaayyy too big.
So, we can add the width and height attributes to scale the image to a more comfortable size.
First, we need to know the exact dimensions of the image.
This can be done by looking at the size in an image app or can be done with an online tool.
Record these values
In this example, the image is 1080x2400
Now divide each by the same factor; this is important to avoid compressing or stretching the image.
In this example, We quartered/ divided them by 4.
Width = 1080/4 = 270px Hieght = 2400/4 = 600px
Record these values
And update the img tag
<p> <img src="" alt="" width="" height=""/> </p>
src is the path to the URL.
alt is the alternative text for the image. This is used for accessibility as well as be a modern web standard.
width is the image width in pixels
height is the image height in pixels
You insert your values in between the double quotes.
ALWAYS TO REMEMBER:
to close your quote _
to close your image tag
to close and include your units
Here it is much better.
RICH TEXT OPTION:
Make sure in the Rich Text editor view.
Set the cursor where you want the image. Click the image icon.
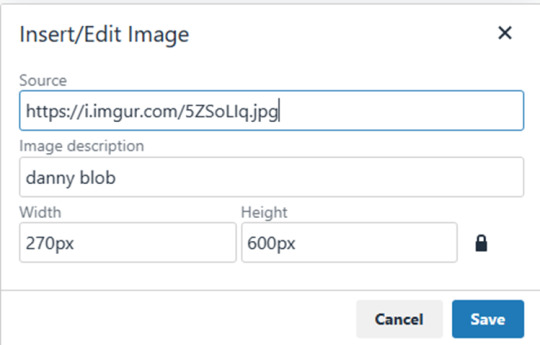
Set the values in this form.
Use the URL we generated in one of the previous 4 options.
Set the Image description
The width and height may be input automatically; if you are unsure, consult the HTML OPTION to find the dimensions and how to rescale an image.
Here’s how it looks after posting

Well, that concludes my simple guide to AO3 image embedding. Thanks for reading to the end.
26 notes
·
View notes
Text
The Ultimate Guide to Downloading Erome Videos

Erome is a popular platform for sharing and viewing user-generated adult content. However, it does not provide a built-in download option. If you want to save videos for offline viewing, you need an Erome downloader. In this guide, we will explore the best ways to download Erome videos safely and efficiently.
Why Use an Erome Downloader?
Many users want to download Erome videos for personal use. Here are a few reasons why:
Offline Viewing – Watch videos anytime without an internet connection.
Backup Content – Save your favorite videos before they get removed.
Better Streaming – Avoid buffering issues by watching videos offline.
Sharing Convenience – Easily transfer videos between devices.
Archival Purpose – Store important content for future reference.
Is Downloading Erome Videos Legal?
Before downloading any content, ensure that you have permission from the original uploader. Downloading copyrighted material without consent can violate terms of service and legal guidelines. Always respect the rights of content creators and adhere to copyright laws in your region.
Best Methods to Download Erome Videos
Here are the top methods to download videos from Erome.com:
1. Using an Online Erome Downloader
Several online tools allow users to paste a video URL and download it. These services are easy to use but may contain ads or require sign-ups.
Steps:
Visit a trusted online Erome downloader website.
Copy the Erome video URL.
Paste the URL into the downloader.
Click “Download” and choose the desired format.
Save the video to your device.
2. Using Browser Extensions
Browser extensions can help download videos directly from Erome. Some popular options include:
Video DownloadHelper (Firefox & Chrome)
Flash Video Downloader
SaveFrom.net Helper
Steps:
Install the extension on your browser.
Open the Erome video.
Click the extension icon to start the download.
Choose the format and save the file.
3. Using Developer Tools (Manual Method)
If you prefer a manual approach, you can use browser developer tools.
Steps:
Open the Erome video page.
Press F12 or right-click and select Inspect.
Go to the Network tab and filter for Media.
Locate the video file URL and copy it.
Open the link in a new tab and save the video.
4. Using a Dedicated Software
There are software programs designed for downloading videos, such as:
JDownloader
4K Video Downloader
YTD Video Downloader
These tools offer advanced features, including batch downloads, high-quality formats, and faster speeds.
How to Stay Safe When Using an Erome Downloader
Downloading videos from third-party tools comes with risks. Follow these safety tips:
Avoid Malware – Use only trusted websites and software.
Use a VPN – Protect your identity and browsing data.
Check Permissions – Ensure you have permission to download videos.
Update Antivirus Software – Protect against potential security threats.
Be Wary of Phishing Scams – Avoid suspicious websites asking for personal information.
Conclusion
An Erome downloader makes it easy to save videos for offline viewing. Whether you use an online tool, browser extension, or software, always prioritize safety and legal considerations. Choose the best method that suits your needs and enjoy seamless downloads. By following best practices, you can ensure a secure and hassle-free downloading experience.
5 notes
·
View notes
Text
How to Protect Your WordPress Site from Malware or Hackers?
WordPress is used by millions of websites for blogs, businesses, and online stores. However, because it’s so popular, it’s often a target for hackers and malware. If you have a WordPress site, it’s important to take steps to keep it secure. Here’s a simple guide to help you protect your site from hackers and malware.
How to Protect WordPress Site from Malware or Hackers?
Follow this step list given below to protect WordPress site from malware or hackers
1. Always Keep WordPress Updated
WordPress regularly releases updates to fix bugs and improve security. Hackers often look for websites running old versions of WordPress or outdated plugins, so keeping everything updated helps keep them out.
How to Update:
Check for updates in your WordPress dashboard regularly.
Go to the Dashboard > Updates section and install any available updates for WordPress core, themes, or plugins.
By staying updated, you’re less likely to have security holes in your site that hackers can use.
2. Use Strong Passwords and Change Them Often
Hackers can easily guess weak passwords like "123456" or "admin." To keep your site safe, use strong, unique passwords and change them every few months.
Tips for Strong Passwords:
Use a mix of uppercase and lowercase letters, numbers, and symbols.
Don’t use simple information like your name or "admin."
Consider using a password manager to create and store complex passwords securely.
Strong passwords are one of the simplest ways to add security to your website.
3. Limit Login Attempts
Hackers often try to break into websites by guessing the login password over and over. You can protect your site by limiting the number of login attempts a person (or bot) can make.
How to Limit Login Attempts:
Use plugins like Limit Login Attempts Reloaded or WP Limit Login Attempts.
These plugins lock out users after a certain number of failed login attempts.
This makes it much harder for hackers to keep guessing passwords.
4. Enable Two-Factor Authentication (2FA)
Two-factor authentication adds another layer of security. In addition to entering your password, you’ll also need to input a code sent to your phone or email. Even if someone knows your password, they won’t be able to log in without this extra code.
How to Set Up 2FA:
Install a plugin like Google Authenticator or Two-Factor.
Set it up by scanning a QR code and linking your account to an app like Google Authenticator or Authy.
This ensures that only you can access your site, even if someone steals your password.
5. Use a Security Plugin
A security plugin can protect your WordPress site from different types of attacks, like malware or brute force attempts. These plugins act as your site’s security guard, offering tools like firewalls and malware scanning.
Recommended Security Plugins:
Wordfence Security: Includes a firewall and real-time monitoring.
Sucuri Security: Provides malware removal and a website firewall.
iThemes Security: Offers brute force protection, backups, and two-factor authentication.
Using a security plugin adds strong layers of protection against hackers.
Also Read - What Is Domain Status? What does this mean, & Why should I know?
6. Back Up Your Website Regularly
Even with good security, things can sometimes go wrong. That’s why it’s important to back up your site regularly. If your site gets hacked, a backup will let you restore everything quickly without losing important data.
How to Back Up Your Website:
Use backup plugins like UpdraftPlus or BackupBuddy.
Store your backups in safe places like Google Drive, Dropbox, or a remote server.
Schedule backups daily or weekly, depending on how often you update your site.
Regular backups help ensure you won’t lose everything if something goes wrong.
7. Choose a Secure Hosting Provider
Your web hosting service plays an important role in your website’s security. Some hosts offer strong security features that help protect your site. Make sure to choose a hosting provider that values security.
What to Look for in a Hosting Provider:
Regular backups
Malware scanning and removal
Firewalls
SSL certificates
DDoS protection
Popular and secure WordPress hosting services include SiteGround, Bluehost, and WP Engine.
8. Use HTTPS and SSL Certificates
SSL (Secure Socket Layer) encrypts the data between your website and your visitors. This protects sensitive information, like passwords or credit card numbers. Websites with SSL certificates also have a secure URL that starts with "https://."
How to Install an SSL Certificate:
Most hosting providers offer free SSL certificates with Let’s Encrypt.
You can use plugins like Really Simple SSL to set it up quickly.
SSL certificates keep sensitive data safe and make your site more trustworthy.
9. Remove Unused Themes and Plugins
Unused plugins and themes can create security risks, especially if they aren’t updated. Even if they’re deactivated, they can still be a weak point. It’s best to delete any plugins or themes you don’t use.
How to Delete Unused Themes/Plugins:
Go to your Dashboard > Plugins or Appearance > Themes.
Deactivate and delete anything you no longer need.
This reduces the number of places where hackers might try to get in.
10. Monitor Your Site for Suspicious Activity
It’s important to keep an eye on your site for any unusual behavior. This could include sudden spikes in traffic, unknown files appearing on your server, or unauthorized users trying to log in.
How to Monitor Your Site:
Use a security plugin to track things like failed login attempts and changes to important files.
Regularly check your hosting account for unusual activity.
Review your website users to make sure no unauthorized accounts have been added.
By staying alert, you can catch potential threats before they do any serious damage.
Conclusion
Protecting your WordPress site doesn’t have to be difficult. By following these simple steps—keeping WordPress updated, using strong passwords, installing security plugins, and making regular backups—you can greatly reduce the risk of your site being hacked or infected with malware.
#OZOHosting#lowest price hosting in india#Cheap web hosting jaipur#cheap shared web hosting india#free web hosting india#affordable linux web hosting india
2 notes
·
View notes
Text
How to check if your computer is being monitored
In today's digital age, the issue of privacy and security is more pressing than ever. Whether you’re a casual user or a professional, understanding if your computer is being monitored is crucial. This guide will delve into the signs of monitoring, tools to detect it, and steps to safeguard your privacy.

Understanding Computer Monitoring
Before diving into the signs and detection methods, it’s essential to understand what computer monitoring entails. Monitoring can involve tracking your online activity, keystrokes, file access, and even webcam usage. This can be done by malicious software (malware), spyware, or legitimate monitoring software used by employers or parents.
Types of Monitoring
Malware and Spyware: These are malicious programs that can be installed without your knowledge. They can track your activities and send data back to an attacker.
Keyloggers: This type of software records keystrokes, capturing sensitive information like passwords and personal messages.
Remote Access Tools (RATs): These tools allow someone to control your computer remotely, monitoring your screen, accessing files, and even using your webcam.
Legitimate Monitoring Software: Often used in corporate environments, this software tracks employee activity for productivity or compliance reasons. While legal, it can still infringe on personal privacy.
Signs That Your Computer May Be Monitored
Recognizing the signs that your computer might be monitored is the first step in protecting yourself.
1. Unusual System Behavior
Slow Performance: If your computer suddenly becomes sluggish, it might be due to monitoring software consuming resources.
Frequent Crashes or Freezes: Unexpected system crashes can indicate underlying issues, including malware.
2. Suspicious Programs
Unknown Applications: Check your installed programs for any unfamiliar applications. Many monitoring tools disguise themselves as legitimate software.
High Resource Usage: Use the Task Manager (Windows) or Activity Monitor (Mac) to look for processes consuming excessive CPU or memory.
3. Network Activity
Unexplained Network Traffic: Use network monitoring tools to check for unusual data being sent or received. High outbound traffic could indicate that data is being transmitted without your consent.
Blocked Ports: Monitoring software often uses specific ports to communicate. If you notice blocked ports that you didn’t configure, it could be a red flag.
4. Webcam and Microphone Behavior
Indicator Light Activation: If your webcam or microphone is being accessed without your knowledge, the indicator light may be on even when you're not using it.
Unexpected Recordings: Check for unusual files that could be recordings made by your microphone or webcam.
5. Browser Behavior
Unusual Browser Extensions: Check for extensions you didn’t install. Some can track your browsing activity.
Unexpected Redirects: Frequent redirects to strange sites or altered search results can indicate tracking.
6. Security Alerts
Antivirus Notifications: If your antivirus software frequently alerts you about threats, it may indicate that monitoring software is present.
Firewall Alerts: Unusual outgoing connection attempts can suggest that an unauthorized program is trying to access the internet.
Tools to Detect Monitoring Software
If you suspect that your computer is being monitored, several tools can help you investigate further.
1. Antivirus and Anti-Malware Software
Using a reliable antivirus or anti-malware program can help detect and remove malicious software. Some popular options include:
Malwarebytes: Excellent for detecting and removing malware and spyware.
Norton: Offers comprehensive protection against various types of threats.
2. Network Monitoring Tools
Tools like Wireshark can help analyze network traffic and identify suspicious activity. You can monitor data packets to see if there are any unexpected connections.
3. Task Manager / Activity Monitor
Regularly check the Task Manager (Windows) or Activity Monitor (Mac) for processes that look unfamiliar or suspicious. Research any questionable applications before taking action.
4. System Scans
Use built-in tools to perform system scans:
Windows Defender: Run a full scan for malware and spyware.
Mac’s Built-in Security Features: Use the Malware Removal Tool for additional scanning.
5. Firewall Monitoring
Make sure your firewall is active and monitor logs for any unusual activity. A firewall can block unauthorized access attempts and alert you to potential threats.
Steps to Protect Your Privacy
If you determine that your computer is being monitored or you want to prevent it from happening, follow these steps to enhance your security.
1. Update Your Software Regularly
Keeping your operating system and all software up-to-date ensures that you have the latest security patches. This reduces vulnerabilities that can be exploited by monitoring tools.
2. Use Strong Passwords
Implement strong, unique passwords for all your accounts and devices. Consider using a password manager to generate and store complex passwords securely.
3. Enable Two-Factor Authentication
Two-factor authentication (2FA) adds an extra layer of security by requiring a second form of verification, making unauthorized access much more difficult.
4. Install a Firewall
Ensure you have a firewall activated, whether it’s built-in (like Windows Firewall) or third-party. This helps control incoming and outgoing network traffic.
5. Be Cautious with Downloads
Avoid downloading software from untrusted sources, as this can introduce malware to your system. Always verify the legitimacy of software before installing it.
6. Regularly Review Permissions
Check application permissions on your device regularly. Revoke access for any apps that do not need to access your camera, microphone, or location.
7. Use a VPN
A Virtual Private Network (VPN) encrypts your internet connection, making it difficult for anyone to monitor your online activities.
8. Educate Yourself
Stay informed about the latest cybersecurity threats and best practices. Knowledge is your best defense against monitoring.
When to Seek Professional Help
If you suspect your computer is being monitored and cannot identify or remove the software yourself, consider seeking professional help. Cybersecurity experts can perform a thorough analysis of your system and provide tailored solutions.
Conclusion
Understanding if your computer is being monitored is vital for protecting your privacy. By recognizing the signs, utilizing detection tools, and implementing security measures, you can safeguard your personal information. Remember, vigilance is key in the ever-evolving landscape of digital security. Stay informed, proactive, and secure in your online presence.
#Computer Security#Online Privacy#Cybersecurity#Monitoring Software#Malware Detection#Privacy Protection#Digital Security#Keyloggers#Network Monitoring#Antivirus#VPN#Internet Safety#Personal Data Security#Remote Access Tools#Digital Awareness
2 notes
·
View notes
Text
how to spot a bot!
Having trouble? Unsure if your followers are bots or not? Don’t worry, and read this handy post! Firstly, the most common kinda of bots are the pornographic type. These bots are made using scripts owners of dodgy websites have bought. At least 20 of them may follow you every day due to the newest bot wave. Their purpose is to get people to click on the links they attach to posts or in reblogs, which lead them to dodgy porn sites very likely filled with a million viruses waiting to infect your device.
So here’s some tips on checking whether it’s a BOT or NOT!
Firstly, check the blog’s name. If it’s a string of random words together, such as the example provided below, it’s very likely a bot. Another one is when the blog’s name is a random name and a bunch of numbers behind it, such as emily1863.
This is an example of a porn bot’s blog.
Another very important thing to check is the profile avatar / icon. If it is the default tumblr avatar show below, or a suggestive picture of a girl / guy (although it’s usually pictures of girls), it’s another sign that it’s a bot.


Here are some default tumblr avatar examples.
Next, check the posts. Are they posting links to other websites with suggestive / inappropriate thumbnails or just links in general in unrelated tags? It’s a bot. OR are they completely empty, with no posts at all? It’s likely that this one is a new bot that hasn’t posted yet. People call these blank blogs, and sometimes they are new users who haven’t posted, or lurkers. I’ll make a more detailed post on them later.
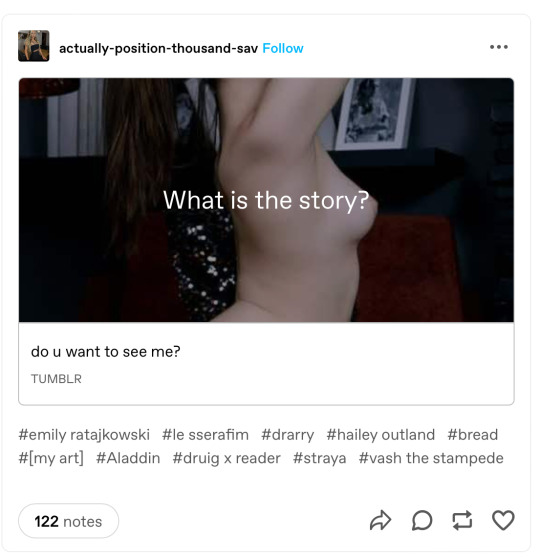
Here’s an example of a bot’s posts. Notice the tags, especially. They are all innocent looking tags, mostly for fandoms and I don’t even want to ask why they put it in the bread tag. It seems to me that these bots take random trending tags and post in them.
Common tags these bots reside in are the lgbt tags, mostly the #aromantic and #asexual tags (why are they posting porn bots in these? the people here literally don’t want to have sex!) and #transgender.
however, they can be found in pretty much any popular tag if you scroll long enough.
Okay, so I’ve found a bot. WHAT DO I DO???
A simple answer is to block so you don’t have to see them anymore, but it's not the best method. If you just block them, they will still stay on the site and clog up people’s dashboards.
instead, here's a better way. you should report AND block! That way, these bots’ accounts will be removed from tumblr!
how to report / block? Here’s a picture guide!
click on the 3 dots on the side of a post.
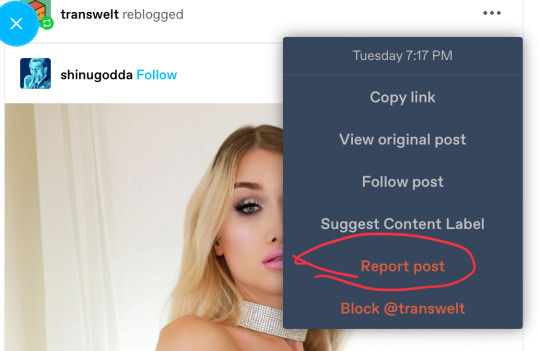
when you report you’ll be led to this page.
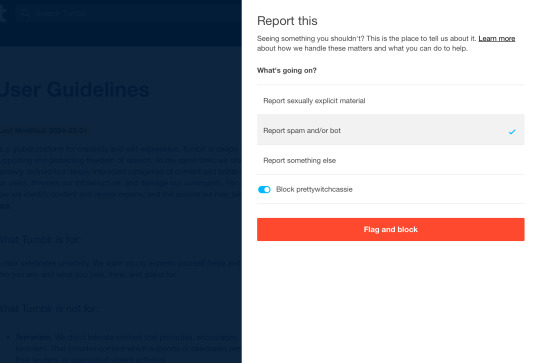
Please report them for spam / bot, NOT sexually explicit material. Reporting them for explicit content will simply get them shadow banned, but their blogs will still be accessible somehow. Also because it’s more spam when they are posting in unrelated tags.
but if you report them for spam, these blogs will be deleted! Hooray!
another great thing is you can flag and block them at the same time, as seen in the image above! Killing two birds with one stone!
I hope this mini guide helped you guys! Oh, and one more thing.
PLEASE DONT CLICK ON ANY LINK THESE BOTS SEND! THEY USUALLY CONTAIN MALWARE OR THEY COULD LOCK YOU OUT OF YOUR TUMBLR AND TURN THE ACC INTO A BOT ACC!
stay safe, and happy bot hunting!
3 notes
·
View notes
Text
Artificial Condition, Chapter 9
(Curious what I'm doing here? Read this post! For the link index and a primer on The Murderbot Diaries, read this one! Like what you see? Send me a Ko-Fi.)
In which another episode concludes.(1)
Art takes care of all the bureaucracy, forging its captain's feed signature and paying fines for the unusual events that follow. It brings the shuttle into a large hangar module, meant to be lab space, and as soon as it fills with atmosphere MB carries Tapan out to Medsystem, the ComfortUnit(2) close behind. As MB removes Tapan's clothes for treatment, some MedSystem drones start poking at its injuries, but it ignores them.
Art informs MB that four humans in the shuttle are still alive, but unconscious. Art has drones sterilize MB's and Tapan's presences and fluids from the interior, then sends it on a flight back to RaviHyral. No one will know they didn't do it to each other until they wake up and tell their stories, and maybe some wouldn't want to tell what they did at all. It'll give the bots time to get out, at least. MB asks how Art knew to do it, but Art confirms its suspicions by giving an episode number of Sanctuary Moon, where presumably something similar happened.
MB asks the ComfortUnit how it knew MB was a Ganaka Pit unit. CU says it saw MB go to the pit, and if it wasn't under orders, it calculated an 86% chance it was one of those units going back for some reason.
MB tells the CU to drop its walls. It does so, still following Tlacey's order to obey MB, and MB disables its governor module. Then, as CU stares at MB, MB tells it to go away and never let MB see it again, or hurt anyone. The CU stumbles upright, and Art uses drones to guide it out to the transit ring without a word.
Art wondered if MB would destroy CU, but MB knows CU didn't have a choice, and it chose to disable CU's governor module for the sake of the CUs in Ganaka Pit who had faced "the meat grinder" to save every human and bot left in the installation.(3)
Art tells MB to get on the other MedSystem platform, as they have a lot of evidence to destroy.
MB is holding Tapan's hand when she wakes, having been healed and cleaned up. Tapan asks what happened, and MB says they tried to kill them again, and they made it out and onto its friend's ship. It shows Tapan the data chip from the Tlacey contact, which it already checked for malware and trackers, and asks her to call Rami and Maro to meet them at the embarkation zone. Tapan and MB exchange "it's my fault"s before she does.
MB surveys everywhere it's been on Art, to be sure there's no evidence left to be found, even if they planned to stay long enough to be stopped and investigated. MB suggests Art take back its comm interface, but Art says to keep it, in case they're in range again someday.
MB and Tapan go out to see the others. Art seals up behind them, erasing records of their having been aboard. They meet Rami, Maro, and the rest of their group at a food stand. They have passage to leave again within the hour.
Rami gives MB a hard currency card, and says its friend said this was the best way to pay it. It tucks it awkwardly into one of the pockets on its Art-provided clothes, as the humans all watch. Rami asks if MB is going now, and it confirms.
Maro asks if she can give MB a hug, but its expression says more than words ever could. So, she squeezes her arms around herself and says it's for MB.(4) MB awkwardly excuses itself for its transport. As it walks away, Art tells it to be careful, and find its crew. MB just pings an acknowledgement, lest it sound "stupid and emotional."
I didn’t know what I was going to do now, if I was going to go ahead with my plan or not. I had hoped finding out what had happened at Ganaka Pit would clear everything up, but maybe revelations like that only happened in the media. Speaking of which, I needed to grab some more downloads before my next transport left. It was going to be a long trip.
=====
(1) If you get the feeling that these novellas sort of fit themselves into episodic parts of a whole, you'd be more or less correct. One of my most keen observations (that is sarcasm) is that the first four novellas are, in a way, four acts of a single novel's story. (2) MB's respect for it went up, and it stopped calling it sexbot in its narration. I have some complicated feelings about this, as someone who is very explicitly for legal safe sex work and against anti-sex-worker stigma, but that rant really might get too long and off-topic for this blog if I got started. (3) See, in contrast to last chapter, this scene seems to imply it was an unrelated CU. It makes no mention that it was there to recognize any signature or anything, and MB dismisses the possibility outright. I really appreciate those sorts of unanswered questions. Like, sometimes it's good to have a firm, lore-based answer, but sometimes? Sometimes those loose ends give you room to think for yourself about a story's possibilities, and make things much more interesting than the author ever could have. (4) Honestly this is the cutest thing in this whole book, to me.
#the murderbot diaries#murderbot diaries#artificial condition#murderbot#secunit#art (murderbot)#asshole research transport#tapan (murderbot)#maro (murderbot)#rami (murderbot)
11 notes
·
View notes
Text
Spotify Premium Mod APK: A Comprehensive Guide
Introduction
Overview of Spotify Premium Mod APK
Spotify Premium Mod APK is a modified version of the official Spotify app, offering users premium features without the need for a paid subscription. This modded version is popular among users seeking an enhanced Spotify experience without the associated costs.
Importance and Relevance
With the rise of streaming services, access to premium features without financial constraints has become highly desirable. Spotify Premium Mod APK caters to this demand, making it a topic of significant interest.
What is Spotify Premium Mod APK?
Definition and Features
Spotify Premium Mod APK is a third-party application that has been altered to provide Spotify Premium features for free. It includes various enhancements such as ad-free listening, unlimited skips, offline downloads, and high-quality audio streaming.
Is It Legal?
Legal Implications
Using Spotify Premium Mod APK is illegal. It violates Spotify's terms of service and can result in account suspension or legal action. It’s important for users to be aware of the legal risks involved in using such applications.
Features of Spotify Premium Mod APK
Ad-free Experience
One of the main attractions of Spotify++ IPA is the removal of all advertisements, providing an uninterrupted listening experience.
Unlimited Skips
Unlike the free version of Spotify, the modded APK allows users to skip tracks as many times as they want, offering greater control over their music selection.
Offline Listening
Spotify Premium Mod APK enables users to download their favorite tracks and listen to them offline, a feature typically reserved for premium subscribers.
High-Quality Audio
Users can enjoy high-quality audio streaming, enhancing the overall listening experience.
How to Download and Install
Step-by-step Guide for Android
Enable Unknown Sources: Go to Settings > Security > Enable Unknown Sources.
Download APK File: Download the Spotify Premium Mod APK from a trusted source.
Install the APK: Open the downloaded file and follow the installation prompts.
Log In: Open the app and log in with your Spotify account.
Step-by-step Guide for iOS
Jailbreak Required: iOS devices need to be jailbroken to install third-party apps.
Download APK: Find a reliable source to download the Spotify Premium Mod IPA file.
Install: Use a sideloading tool like Cydia Impactor to install the IPA file.
Log In: Open the app and log in with your Spotify account.
Benefits of Using Spotify Premium Mod APK
Cost Savings
Using the modded APK provides all premium features without any subscription fees, making it cost-effective.
Enhanced User Experience
With no ads, unlimited skips, offline listening, and high-quality audio, the user experience is significantly enhanced.
Risks and Drawbacks
Security Risks
Downloading and installing APK files from unofficial sources can expose your device to malware and other security threats.
Ethical Considerations
Using modified versions of applications is unethical as it deprives developers of deserved revenue and violates terms of service.
Potential for Malicious Software
There's a high risk of encountering malicious software that can compromise personal data and device integrity.
Conclusion
Summary and Final Thoughts
While Spotify Premium Mod APK offers an attractive array of premium features for free, it comes with legal and security risks that users should carefully consider. Opting for the official Spotify Premium ensures a safe, ethical, and high-quality music streaming experience.
4 notes
·
View notes
Text
WordPress Hosting Guide
WordPress has changed the way we make and manage websites by providing an easy-to-use platform for bloggers, businesses, and everyone in between. But even the most experienced web users may find it hard to navigate WordPress hosting. It's easy to find a hosting service that fits your needs, whether you want shared hosting or a private server. In this comprehensive guide, we will delve into the complexities of WordPress hosting, empowering you to make informed decisions regarding your website's online visibility.

What does WordPress hosting mean?
WordPress hosting is a type of web hosting designed for WordPress sites. It works best with WordPress blogs.
Various hosting companies provide diverse WordPress hosting packages. These typically include convenient features such as automatic updates, custom WordPress themes, and one-click installation of WordPress, relieving you of the need to handle these tasks manually.
You don't have to sign up for WordPress hosting just because you have a WordPress site. It's fine to host the site normally. However, the best way to make your WordPress site run faster, safer, and available all the time is to connect it to a WordPress hosting plan.
WordPress hosting advantages
Using WordPress hosting for your website can help it in many ways. These are the seven most important:
1. Faster: WordPress hosting can make your website faster and better at what it does. One reason for this is that WordPress hosting companies use fast computers that are set up to work best with WordPress sites.
2. Security: Most WordPress hosting companies offer extra security features like scanning for malware and finding intrusions. This can help you relax because you'll know that your site is safe from possible risks.
3. Scalability: If your website grows, you might need to upgrade your hosting plan to handle the extra traffic and data storage needs. However, it's easy to change your WordPress hosting plan to fit your needs.
4. Better uptime: WordPress hosting companies can ensure that your website is online more often. This means that people will be able to access your website more often, which could lead to more visits and sales.
5. Better customer service: If you host your website with a WordPress hosting business, you will be able to get better customer service. What this means is that you can get help from the server company if you need it.
6. More freedom: WordPress hosting gives you more freedom to pick the plugins, styles, and other features you want for your website. When you use WordPress hosting, it's easy to add or remove features without making changes to the whole website.
7. Saves money: WordPress hosting can help you save money on your hosting fees. For this reason, WordPress hosting companies often give discounts and other deals to people who host their websites with them.
8. Better SEO: WordPress hosting gives you access to many SEO tools and resources that can help your website's search engine optimization (SEO).
9. More features: Many WordPress hosts offer extra features, like installing famous plugins and themes with just one click, that can make running your website easier.
Tips for picking a WordPress hosting service
No matter which way you look, a WordPress host is advertising its service as the best one for you. Do your research and consider all of your choices before making a decision.
In particular, when picking a WordPress hosting plan, you should think about things like speed, security, and customer service.
1. Performance
If you want your site to work at its best, think about its uptime. If your site can't be reached, it can have bad effects like less traffic and customers leaving. Make sure that the host you choose guarantees that their service will be up at least 99% of the time.
It should also have a content delivery network (CDN) and built-in caching, which are both great for making pages load faster.
You could also test your site's speed yourself by using one of the free WordPress hosts or getting your money back. Tools like PageSpeed Insights and Pingdom can help you determine whether a host really speeds up your site.
2. Scalability
Scalability can affect your site's bottom line in the same way that speed can.
If you are a new website owner, choose the cheapest hosting option. That's fine. This type of WordPress hosting might not be good for you if your site gets a lot of visitors. Your plan might need to give your site more resources as it grows.
One example is that you might have an outage if your WordPress site can't handle a lot of visitor traffic.
So, pick a web host that can help your business grow and let you add more computers as needed to handle more traffic.
Check to see if the host offers plans that can be changed or plans that go above shared hosting, like VPS hosting. So, you won't have to move web hosts when the number of visitors grows.
3. Security
Security is another important factor to consider when picking a WordPress web host. To ensure smooth operation, you must keep your data and the data of your customers safe.
Many WordPress hosts offer strong security measures to keep your data safe from various cyberattacks and lower the risk.
Some of these are:
SSL certificates
Web Application Firewall, or WAF
Secure shell (SSH) access
DDoS protection
Malware scanner
4. Prices
Since each WordPress host has a different price range, it's best to look at a few and compare plans and prices to find the best one for you. Some web hosts, for example, charge more in the long run, so as you grow, things can quickly get pricey.
Also, watch out for any hidden fees. Some hosts charge extra for extra protection or for exceeding your bandwidth limit.
If you're looking for a web host, look for deals that let you save money while you try their services.
5. Customer support
When you run a WordPress site, you must remember good support. This is especially important if you're new. Also, things do break down, so it's good to know that your friend will be there for you if something goes wrong. So, pick a web host like MyResellerHome that has live customer support 24/7.
Prior to committing to a hosting company, it's crucial to assess their support system. Look for providers that offer multiple avenues for communication, such as phone and email, ensuring you have a variety of options to reach out for assistance.
Also, you can check out the host's support team on your own to see how quickly and well they can help you. Talk to them in real-time and write down how long it takes for them to answer if they offer live chat support.
Types of WordPress hosting services
Shared WordPress hosting
Shared WordPress hosting is the least expensive way to store your website and is best for small sites or people who are just starting with websites.
When you rent or get a small part of a single computer from a web host, this is called shared hosting. This means that you and other website owners share the server's resources.
If one site uses fewer of the shared resources, it could slow down your site. This is one of the problems with shared hosting plans.
Another con is that you won't be able to change how the server works—if you use a shared server, you won't be able to make the hosting setting fit your needs.
Virtual private server (VPS) WordPress hosting
A hypervisor divides one physical server into several virtual servers in this type of hosting. There will be a part of the server that is only for your site, so you won't have to share bandwidth and RAM with other users. This makes performance and protection better.
When you use VPS WordPress hosting, the rules are the same, but each site will run on WordPress. This means that the server environment will be set up to work best with WordPress sites, giving you better speed and security than a regular VPS server.
Dedicated WordPress hosting
When you pay for dedicated WordPress hosting, you get a computer all to yourself. You won't have to share disk space, memory, or CPU with other people, and you'll be able to see everything on the server as root.
If you get a dedicated hosting plan, your site will run faster, be safer, and be online more often because you won't have to share resources with other people like you do on shared servers.
Managed WordPress hosting
When you use managed WordPress hosting, your web host takes care of all the back-end management of your WordPress site. Things like maintenance, updates, protection, and backups are part of this.
Managed WordPress hosting plans offer faster site speeds, more security, 24/7 customer support, and more specialized features.
Who should use hosting for WordPress?
When it comes to CMS platforms, WordPress is the most famous. WordPress lets you make any website, like a blog, an e-commerce site, or something else. In order to make your website with WordPress, WordPress hosting is the best option. For these reasons, a WordPress hosting plan is the best way to make sure that WordPress sites run quickly and safely.
Conclusion
Picking the right WordPress hosting company is very important for the growth of your site. You can make an informed choice that fits your needs by thinking about things like speed, security, support, and scalability. Make sure that the hosting you choose for your WordPress site meets its needs, whether it's shared hosting, controlled hosting, or VPS hosting. As your website changes and grows, remember to look at and improve your hosting plan on a regular basis. To find the best hosting for your WordPress project, take the time to learn about and compare the different choices. Be smart about the choices you make to build a strong online reputation.

Janet Watson MyResellerHome MyResellerhome.com We offer experienced web hosting services that are customized to your specific requirements.
Facebook Twitter YouTube Instagram
2 notes
·
View notes
Text
Spotify Mod Apk Free Download
What is Spotify Mod Apk?
Spotify Mod Apk is a modified version of the official Spotify application. Created by independent developers, this version bypasses the restrictions imposed on free users, providing access to premium features without any cost. Users can enjoy ad-free music, unlimited skips, high-quality audio streaming, and offline listening.
Key Features of Spotify Mod Apk
Ad-Free Experience: One of the most appealing features of Spotify Mod Apk is the removal of all ads. Enjoy uninterrupted music without the annoyance of commercial breaks.
Unlimited Skips: Unlike the free version, which limits the number of skips, Spotify Mod Apk allows users to skip tracks as much as they like.
High-Quality Audio: Stream music in high-definition audio quality, providing a superior listening experience.
Offline Listening: Download your favorite songs and playlists to listen offline, saving data and ensuring you have your music even without an internet connection.
Unlocked Spotify Connect: Connect Spotify to various devices, such as speakers, smart TVs, and game consoles, enhancing your overall music experience.
How to Download and Install Spotify Mod Apk
Downloading and installing Spotify Mod Apk is a straightforward process, but it requires a few specific steps to ensure a smooth setup. Follow this step-by-step guide to get started:
Step 1: Enable Unknown Sources
Before you can install Spotify Mod Apk, you need to allow installations from unknown sources on your device. This setting can be found in your device’s security settings.
Go to Settings > Security.
Enable Unknown Sources.
Step 2: Download the Apk File
Find a reliable source to download the Spotify Mod Apk file. Ensure the website is trustworthy to avoid downloading malware or corrupted files.
Open your browser and search for Spotify Mod Apk Download.
Select a reputable website and download the latest version of the Apk file.
Step 3: Install the Apk File
Once the download is complete, locate the file in your device’s download folder and proceed with the installation.
Open the Downloads folder.
Tap on the Spotify Mod Apk file.
Follow the on-screen instructions to complete the installation.
Step 4: Log in to Your Spotify Account
After installation, open the Spotify Mod Apk and log in with your existing Spotify account or create a new one. Enjoy all the premium features without any limitations.
1 note
·
View note
Text
This day in history

I'll be in Stratford, Ontario, appearing onstage with Vass Bednar as part of the CBC IDEAS Festival. I'm also doing an afternoon session for middle-schoolers at the Stratford Public Library.

#15yrsago The Manuscript: a technothriller written by someone who understands technology https://memex.craphound.com/2008/11/14/the-manuscript-a-technothriller-written-by-someone-who-understands-technology/
#10yrsago UK Conservative party tries to send all official speeches down the memory hole https://www.computerweekly.com/blog/Public-Sector-IT/Conservatives-erase-Internet-history
#10yrsago TSA blows a billion bucks on unscientific “behavioral detection” program, reinvents phrenology https://arstechnica.com/tech-policy/2013/11/despite-lack-of-science-tsa-spent-millions-on-behavioral-detection-officers/
#10yrsago Renault ships a brickable car with battery DRM that you’re not allowed to own https://www.eff.org/deeplinks/2013/11/drm-cars-will-drive-consumers-crazy
#10yrsago Punk Freedom of Information Access ninja learns how to beat FBI obfuscation, so they shut him out https://www.motherjones.com/politics/2013/11/foia-ryan-shapiro-fbi-files-lawsuit/
#10yrsago Massive 1978 Las Vegas fallout shelter https://www.cultofweird.com/architecture/underground-home-las-vegas/
#10yrsago TPP’s worst evil: making all future copyright reform impossible https://www.techdirt.com/2013/11/14/most-nefarious-part-tpp-proposal-making-copyright-reform-impossible/
#10yrsago Rob Ford: $170K/year, 11-3 working day https://www.joeydevilla.com/2013/11/14/one-thing-to-remember-during-this-whole-toronto-mayoral-kerfuffle/
#10yrsago Rob Ford articulates official mayoral cunnilingus policy https://www.joeydevilla.com/2013/11/14/rob-ford-will-ahem-go-down-in-history-with-this-quote/
#10yrsago Toronto council turns their back to Rob Ford every time he speaks https://www.motherjones.com/politics/2018/11/the-acting-attorney-general-helped-an-alleged-scam-company-hawk-bizarre-products/
#5yrsago Trump’s Acting Attorney General was an active participant in a scam company that marketed “masculine toilets” https://www.motherjones.com/politics/2018/11/the-acting-attorney-general-helped-an-alleged-scam-company-hawk-bizarre-products/
#5yrsago The Florida of ballot-design mistakes is… https://freedom-to-tinker.com/2018/11/14/florida-is-the-florida-of-ballot-design-mistakes/
#5yrsago “Privacy Not Included”: Mozilla’s guide to insecure, surveillant gadgets to avoid https://foundation.mozilla.org/en/privacynotincluded/
#5yrsago Alex Jones blames “leftist stay-behind networks in US intelligence agencies” for malware on his site https://www.zdnet.com/article/card-skimming-malware-removed-from-infowars-online-store/
#5yrsago Coalition of small cable operators calls for antitrust investigation into Comcast (Trump agrees) https://www.theverge.com/2018/11/12/18088846/comcast-nbcuniversal-american-cable-doj-antitrust-investigation-letter-trump-tweet
#5yrsago Nigerian telco says it accidentally routed Google traffic through China https://www.reuters.com/article/us-alphabet-disruption/nigerian-firm-takes-blame-for-routing-google-traffic-through-china-idUSKCN1NI2D9
#5yrsago 70 of the world’s leading human rights groups ask Mark Zuckerberg to create due process for censored content https://santaclaraprinciples.org/open-letter/
#5yrsago Apple’s world-beating financial engineering is teaching the corporate world how to exploit Trump’s tax cuts https://www.ineteconomics.org/perspectives/blog/apples-capital-return-program-where-are-the-patient-capitalists
#5yrsago Researchers keep finding Spectre-style bugs in processors https://arstechnica.com/gadgets/2018/11/spectre-meltdown-researchers-unveil-7-more-speculative-execution-attacks/
#1yrago Even if you're paying for the product, you're still the product https://pluralistic.net/2022/11/14/luxury-surveillance/#liar-liar
6 notes
·
View notes
Text
How to Root Samsung Galaxy J2 Core SM-J260F With Odin Tool

Learning how to root SM J260F, particularly the Samsung Galaxy J2 Core model, can significantly enhance your device's functionality and user experience. The root process allows you to access and modify the operating system's code, enabling you to install custom ROMs, remove pre-installed apps, and even boost your device's speed and battery life. In this guide, we'll walk you through the step-by-step process of how to root Samsung SM-J260F. We'll also delve into using the Odin Tool, a popular firmware flashing tool developed by Samsung. This tool is particularly useful when you want to root Samsung SM-J260F, unlocking a world of customizability and improved performance. So, let's get started with the process of rooting your Samsung Galaxy J2 Core model SM-J260F. Read more - Why we want to root - Full Details with a guide
Table of Contents
The Pros and Cons of Rooting Your Samsung Galaxy J2 Core SM-J260FThe Advantages of Rooting SM-J260F The Drawbacks of Rooting Samsung SM-J260F 8 Steps To Root SM J260F Verifying Successful Rooting of Your SM-J260F Reversing the Root Process on Samsung Galaxy J2 Core SM-J260F Conclusion Frequently Asked QuestionsWhat should I do if I can't find my Samsung SM-J260F model listed on the Chainfire website to root SM-J260F? Why did my attempts to root SM-J260F with applications like KingoRoot, Kinguser, FramaRoot, Kingroot, Vroot, Root Master, z4root, and Root Genius fail? I have rooted my Samsung SM-J260F, but the system indicates "su binary needs to be updated/The Superuser binary (su) must be updated". How can I resolve this issue? I've rooted my Samsung Galaxy J2 Core SM-J260F and now the Kinguser binary (su) needs updates? How to Fix the "Unfortunately, kinguser has Stopped" Error in Samsung Galaxy J2 Core SM-J260F After Rooting? What should I do if I encounter the "Unfortunately, kingroot has Stopped" error while trying to root SM-J260F? Why am I seeing "Root Failed! , No Strategy Found, ConnectionUnstabitil , need root" error when trying to root my Samsung SM-J260F? How to fix Google Play Store errors on my rooted SM-J260F? What should I do if I encounter the "could not do normal boot odin mode" error while trying to root SM-J260F? What should I do if my Samsung Galaxy J2 Core SM-J260F gets stuck on the logo screen after trying to root? Fix Bootloop on device (continuously restart)
The Pros and Cons of Rooting Your Samsung Galaxy J2 Core SM-J260F

When deciding whether to root your SM J260F, it's essential to weigh the pros and cons. Rooting, though potentially beneficial, comes with its own set of risks and challenges. Here's a balanced look at the advantages and drawbacks of rooting your Samsung SM-J260F. The Advantages of Rooting SM-J260F 1. Custom Software (ROMs): One of the main reasons people choose to root Samsung SM-J260F is the ability to install custom ROMs. These ROMs can enhance performance, provide additional features, and even update your device to a newer version of Android. 2. Apps Permission Control: Rooting provides you with complete control over what your apps can and cannot do. This means you can block ads, remove bloatware, and enhance battery life. 3. Full Device Control: Rooting your Samsung SM-J260F allows for total control over your device. You can change the CPU speed, modify system files, use themes, and even change boot images. The Drawbacks of Rooting Samsung SM-J260F 1. Bricking Your Device: The most significant risk when you root Samsung SM-J260F is bricking your device, rendering it unusable. This usually happens when the rooting process is not followed correctly. 2. Voiding Your Warranty: Most manufacturers, including Samsung, will void your warranty if they find out you've rooted your device. 3. Security Risks: Rooting can make your device more vulnerable to viruses and malware because you bypass certain protections put in place by Google. 4. System Updates: Sometimes, rooting can cause issues with system updates. This means you may not be able to install updates or may face instability after an update. In conclusion, deciding how to root SM-J260F isn't a decision to be taken lightly. While the benefits can be significant, the risks are equally substantial. Always ensure you understand the process and the potential implications before proceeding.
8 Steps To Root SM J260F
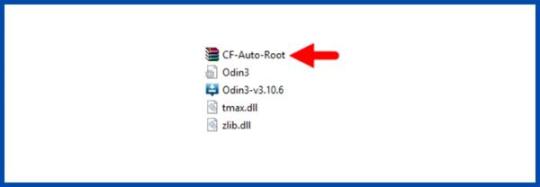
Note - First Back up your data Step 1 - Charge your phone up to 50%. - Download the Samsung Galaxy J2 Core SM-J260F USB Driver and install it on your computer. - Turn ON USB Debugging and Developer mode on the phone. Step 2 Download the Odin program to your PC - Now download the Odin program to your laptop or your Computer. - After downloading, install and launch it. Step 3 - Take your phone and Turn it OFF by pressing the power key. - Now press and hold the Power key + Home key + Volume down key until boot to download mode.

Step 4 - Connect your phone to your PC or laptop by using a USB data cable. It's better to use original Data cables. Step 5 Download the CF-Root file for Samsung Galaxy J2 Core SM-J260F - Download the CF-Root file for Samsung Galaxy J2 Core SM-J260F. (Yes this zip may include Odin tool again. Use one of the Odin.) - CF root file is ZIP so, you have to unzip it.
Step 6 - Now press the Volume up key to continue to Download Mode.
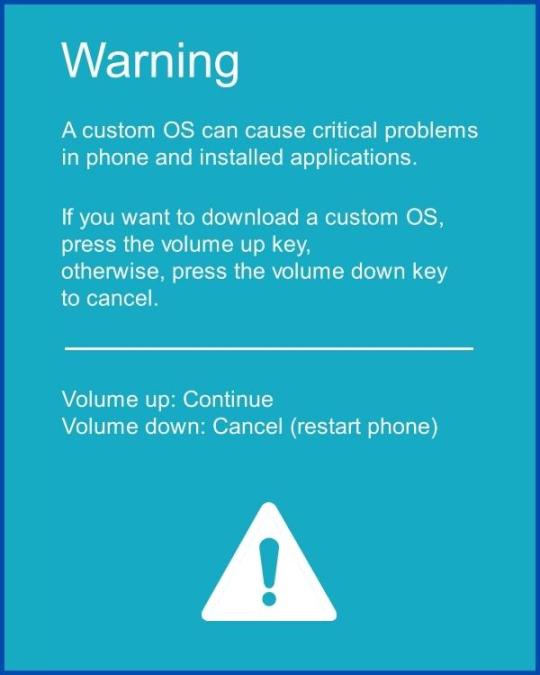
- After tapping the Volume up key, you will able to see the "Added" message in the Odin tool's notification box.
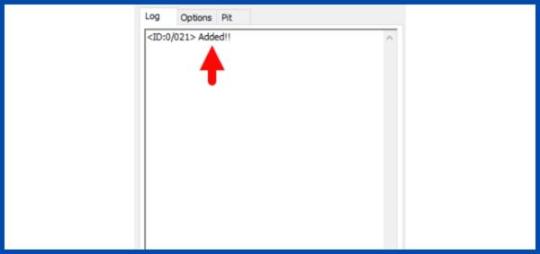
Step 7 - Click PDA / AP and browse to the downloaded CF-Root file. - Select "Auto Reboot".
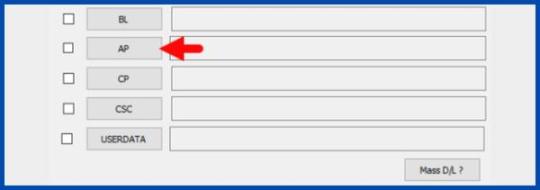
- Start Rooting by Clicking Start. - Read More - Increase RAM SIZE after root Step 8 - Please wait until the phone restarts automatically and it will display a green Pass.
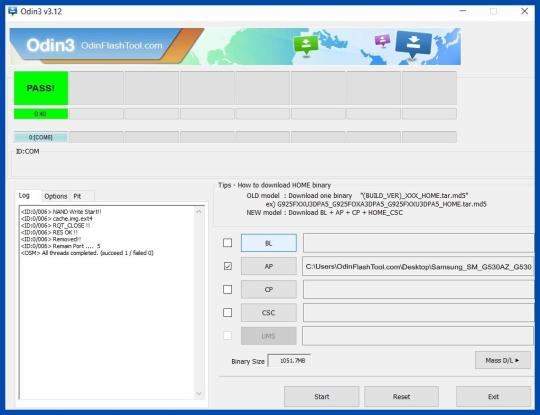
Root Samsung Galaxy J2 Core SM-J260F - The last step is to Factory Reset your phone after turning it on. - Now, Congratulations you have Successfully Rooted :) - Read more, OK I rooted. Now what next?
Verifying Successful Rooting of Your SM-J260F

To confirm if you've managed to properly root your Samsung SM-J260F, there are a couple of straightforward methods you can utilize. If an application titled "SuperSu" is present on your device after the rooting process, it typically indicates successful root status. But if you're still harboring doubts about how to root SM-J260F and whether it's been done correctly, there's an additional step you can take. Simply make use of a trusted third-party application, specifically designed to assess root access on devices like the root Samsung sm-j260f. This will conclusively inform you if your phone has been rooted effectively. Top 10 Rooted apps for android devices
Reversing the Root Process on Samsung Galaxy J2 Core SM-J260F
After successfully executing the 'root sm j260f' process on your Samsung Galaxy J2 Core, you may decide that root permissions are no longer necessary for your needs. In this case, unrooting your Samsung SM-J260F becomes your next step. Rest assured, the process to revert back from the root Samsung sm-j260f is straightforward and involves a few simple steps. Click here for more detailed instructions on how to unroot sm-j260f and bring your device back to its original settings.
Conclusion
In conclusion, learning to root sm j260f using the Odin Tool unlocks the full potential of your Samsung Galaxy J2 Core. Despite being a technical process, it offers control and customization options. However, it's crucial to back up your data before rooting any device, including the Samsung sm-j260f variant. Remember, rooting may void your warranty, but the benefits can outweigh the risks if done correctly.
Frequently Asked Questions
What should I do if I can't find my Samsung SM-J260F model listed on the Chainfire website to root SM-J260F? If your specific model, such as the Samsung SM-J260F, isn't listed on the Chainfire website, don't worry - there are other options available to root your Samsung SM-J260F. The absence of your phone model could indicate that the developers are currently making or updating your phone's CF file. In the meantime, you can consider using a different method to root Samsung SM-J260F. Numerous rooting apps are available that can help you root your Samsung SM-J260F effectively. It's recommended to wait for the official update, but if immediate rooting is necessary, these apps can be a viable alternative. For more details on how to root SM-J260F using these alternative methods, refer this guide. Why did my attempts to root SM-J260F with applications like KingoRoot, Kinguser, FramaRoot, Kingroot, Vroot, Root Master, z4root, and Root Genius fail? Rooting applications such as KingoRoot, Kinguser, FramaRoot, Kingroot, Vroot, Root Master, z4root, and Root Genius can potentially root your Samsung SM-J260F. However, these applications may fail to root Samsung SM-J260F if your phone model isn't supported by the app. It's important to note that not all rooting applications are universal and can work with every phone model. If you're struggling with how to root SM-J260F using these applications, it's advisable to try the CF-Root method instead. This is considered the standard way to root mobile phones, including the SM-J260F, and is likely to be successful where other methods have failed. I have rooted my Samsung SM-J260F, but the system indicates "su binary needs to be updated/The Superuser binary (su) must be updated". How can I resolve this issue? If you encounter the "su binary needs to be updated" issue after rooting your SM-J260F, you can resolve it by following these steps: first, unroot your device and remove all rooting apps. Then, restart your phone to clear any remaining data from the apps. Update the Superuser binary (su) and proceed to root your Samsung SM-J260F again by following the provided guide. Always exercise caution when rooting your device or seek professional assistance if needed. I've rooted my Samsung Galaxy J2 Core SM-J260F and now the Kinguser binary (su) needs updates? If you're facing issues after you root sm j260f, you can follow these steps to unroot your phone: - Update Kinguser binary (su): Open the Kinguser app and follow the prompts to update. - Remove rooting apps: Go to Settings > Apps > Select the app > Uninstall. - Unroot your phone: Use a root access file manager to delete the "su" and "busybox" files from the /system/bin and /system/xbin directories. - Restart your phone: Restart your phone to ensure all changes take effect. If you want to root your phone again, follow a guide on how to root sm-j260f. Always take a full backup of your data before making any changes to your phone's software. How to Fix the "Unfortunately, kinguser has Stopped" Error in Samsung Galaxy J2 Core SM-J260F After Rooting? If you've recently attempted to root SM j260f and are experiencing the "Unfortunately, kinguser has stopped" error on your Samsung Galaxy J2 Core SM-J260F, here are some solutions you can try. Firstly, try restarting your device to see if the issue resolves itself. If the problem persists, follow these steps: - Open the Settings page on your device. - Navigate to the App or Application Manager. - Scroll down the list of applications to find 'kinguser'. - Once found, click on it and select 'Delete cache and data'. This process should ideally fix the error you're encountering after trying to root Samsung sm-j260f. If the problem still persists, you may need to consult with a professional or explore other forums that offer solutions on how to root sm-j260f without encountering such issues. What should I do if I encounter the "Unfortunately, kingroot has Stopped" error while trying to root SM-J260F? This is a common issue faced by many users attempting to root the Samsung SM-J260F. If you see the "Unfortunately, kingroot has Stopped" error message on your device, don't worry. Here's a simple solution to tackle this problem: Firstly, restart your device and check if the issue persists. If that doesn't work, follow these steps: - Navigate to the Settings page on your device. - Look for the app or application manager. - Find kingroot in the list of applications. - Select kingroot and delete both cache and data. This should ideally resolve the "Unfortunately, kingroot has Stopped" error you're facing while trying to root Samsung SM-J260F. If the issue continues, you might need to consider other methods on how to root SM-J260F. Why am I seeing "Root Failed! , No Strategy Found, ConnectionUnstabitil , need root" error when trying to root my Samsung SM-J260F? If you're encountering the "Root Failed!, No Strategy Found, ConnectionUnstabitil, need root" error while trying to root your SM-J260F, it's likely due to the use of an incompatible rooting app. For your Samsung device, we highly recommend you to root Samsung SM-J260F using the CF root method. This method is known to be quite effective and eliminates common issues that are often associated with other rooting methods. Just follow our step-by-step guide on how to root SM-J260F using the Odin tool to avoid such errors in the future. How to fix Google Play Store errors on my rooted SM-J260F? If you're facing Google Play Store errors after rooting your Samsung SM-J260F, follow these steps: - Switch to a new Google account. - In device settings, navigate to App Manager > Google Play Store. Clear both cache and data. - If errors persist, delete unnecessary media files to free up storage space. These steps should help resolve most Google Play Store errors after rooting your device. What should I do if I encounter the "could not do normal boot odin mode" error while trying to root SM-J260F? The "could not do normal boot odin mode" error often occurs when you use an incorrect CF root file while trying to root Samsung SM-J260F. However, there's no need to worry as you can still switch on your phone. For a comprehensive solution on how to resolve this issue and successfully root SM-J260F, please follow this link . Remember, using the correct files and procedure is crucial when you attempt to root Samsung SM-J260F to avoid such issues. What should I do if my Samsung Galaxy J2 Core SM-J260F gets stuck on the logo screen after trying to root? If your Samsung Galaxy J2 Core SM-J260F gets stuck on the logo screen after attempting to root Samsung sm j260f, there are a few steps you can take to resolve the issue. - Firstly, navigate to the Odin tool and switch to DL mode. Then, repeat the above steps for rooting your device. - If the problem persists, it's possible that the CF Root file you downloaded is damaged or incorrect. Read the full article
2 notes
·
View notes
Text
Joe Biden wants the US government to make wider use of artificial intelligence—and to keep commercial AI on a tighter leash. Those are two prominent themes of a sprawling executive order Biden will sign today, which issues dozens of directives for federal agencies to complete within the next year, on topics ranging from national security and immigration to housing and healthcare.
The order places reporting requirements on companies developing powerful AI technology, such as that behind OpenAI's ChatGPT. Biden will use the Defense Production Act, a law that can compel businesses to take actions in the interest of national security, to require the makers of large AI models to report key information to the government, including when they are training a new model and what cybersecurity protections they have.
That will include disclosing results of so-called red teaming exercises, intended to reveal vulnerabilities in AI models, such as those that can be used to evade controls that prevent malicious use cases such as generating malware. The goal is to monitor the potential threats AI technology can pose to national security, public health, and the economy.
Another part of the order requires companies that acquire, develop, or possess large-scale computing clusters, essential to training the most powerful AI systems, to report their activity to the federal government. This rule is intended to help the government understand which entities, including those from nations competing with the US, have strong AI capabilities.
The executive order also directs the Department of Energy to evaluate how AI outputs can contribute to biological or chemical attacks, or cyberattacks on critical infrastructure. The UK government included the possibility of advanced AI enabling biological and chemical attacks in a report last week on potential threats posed by the technology.
White House deputy chief of staff Bruce Reed, who is chair of a newly formed White House AI Council to ensure compliance with the order, calls it “the strongest set of actions any government in the world has ever taken on AI safety, security, and trust.”
Help Wanted
The measures in Biden's executive order aimed at powering up US government AI include the creation of a dedicated job portal hosted at AI.gov to draw more experts and researchers familiar with the technology into government. Another initiative asks for a new training program to produce 500 AI researchers by 2025.
Divyansh Kaushik, an associate director at policy research group the Federation of American Scientists, who helped draft portions of the executive order, says those could be among the most influential pieces. “People often forget that talent is the biggest bottleneck in the federal government,” he says.
Kaushik also welcomes the way Biden’s order demands changes to immigration policy to make it easier for AI talent to come to the US. A plan to allow immigrant workers to renew their visas inside the US, for example, could remove the need for hundreds of thousands of STEM students to travel to their home countries for in-person interviews.
Although the US has a majority of the world’s top AI talent today, only 20 percent of them received undergraduate degrees in the US, Kaushik says, indicating that many are immigrants. He says it’s in the US interest to make it easier for AI experts to come from overseas, to compete against other destinations such as China, Canada, or the UK.
Biden’s new executive order acknowledges that AI projects can be harmful to citizens if not carefully implemented, singling out the potential for discrimination and other unintended effects in housing and healthcare. The order calls for the White House’s Office of Management and Budget to develop guides and tools to help government employees who purchase AI services from private companies make good choices.
Suresh Venkatasubramanian, director of the Center for Technological Responsibility, Reimagination, and Redesign at Brown University, says those rules could be impactful. Within the federal government, procurement is “number one on everyone's agenda because everyone understands that is the way to effect change,” he says. He previously helped the White House assemble an AI Bill of Rights for federal agencies issued by Biden last year.
However, Venkatasubramanian says some of the most critical government use cases for AI in the US will largely go unaffected by the new executive order. Biden’s directives apply to federal agencies, but much AI used in criminal justice and policing is deployed by state and local law enforcement. False positives from AI-powered technology like ShotSpotter gunshot detection and face recognition have led to false arrests, and police departments currently use predictive policing software that doesn’t work as advertised.
To force state agencies to also adopt the standards in the executive order, Venkatasubramanian says federal lawmakers could make compliance a condition of funding for state and local law enforcement agencies.
This is the first executive order of the Biden presidency solely focused on artificial intelligence, and it follows two by former president Trump, in 2019 and 2020. So far, government agencies have a spotty record of complying with them.
The 2019 order focused on investments in AI research and development. A December 2020 executive order and the Advancing American AI Act passed last year require federal agencies to annually disclose an inventory of algorithms in use. But a Stanford Law School study found a pattern of inconsistent compliance, warning of a national AI “capacity gap.” If Biden’s new order, the most ambitious presidential directive on the technology to date, works as intended, it will significantly expand that capacity.
2 notes
·
View notes
Text
https://www.fiverr.com/s/LoK2mp

Boost your PC's performance with my expert optimization guide! You'll get a step-by-step process to speed up your computer, personalized settings, and powerful regedits. Say goodbye to sluggishness and hello to seamless computing. Order now for a faster PC!
Sure, here's a brief explanation of each function:
1. **Detailed PC Optimization Guide:** You'll receive clear instructions to clean up files, free up disk space, and optimize startup programs for faster performance.
2. Expertly Crafted Regedits:** Customized settings designed to fine tune your PC, providing a significant performance boost beyond standard optimization.
3. **Driver and Software Updates** Recommendations for updating drivers and software to ensure stability and the latest features.
4. Personalized System Settings** Expert tips to tweak system settings for a customized and optimal experience.
5. **RAM Management Techniques:** Advice on managing RAM usage for improved multitasking capabilities.
6. Malware Removal Tools: Tools to scan and remove malware, ensuring PC security and data protection.
**Additional Options (With Extra Payment):**
-**Customized Regedits Internet AND Latency
#gamer#fiverr#technology#help#please help#optimize pc#pc games#pc#pc gamer#pcmasterrace#yanpol#league of legends#fps#fps games#regedit#windows 10#windows 11#buynow
4 notes
·
View notes
Text
How to Detect & Remove Malware from Your Site in 2025
🚨 Is your WordPress site acting weird? Slower load times, strange redirects, or random logouts? You might be infected with malware 😱
👉 Here’s your step-by-step guide to detect, clean, and secure your site from malware in 2025 – without needing a developer.
🛡️ Clean it. 🔐 Lock it. 💥 Bounce back like a pro.

#WordPressSecurity#MalwareRemoval#CyberSecurity#WebsiteHacked#WPPlugins#SEO#SiteSecurity#WordPressTips#WPressBlog
1 note
·
View note
Text
How to Troubleshoot Computer Problems: A Complete Step-by-Step Guide
Experiencing computer problems can be frustrating, whether it’s a slow startup, unexpected crashes, or network connectivity issues. This comprehensive guide will walk you through how to troubleshoot these common problems effectively—empowering you with the knowledge to fix your PC or Mac yourself before seeking costly repairs. Whether you're a beginner or an intermediate user, understanding how to diagnose and resolve computer troubles is essential to keep your system running smoothly.
Understanding Common Computer Problems
Computer problems can range from minor annoyances to critical failures. Some of the most frequent issues users face include slow computer performance, system errors, blue screen crashes, software freezes, and startup or boot problems. Error messages often give clues about what’s wrong, recommended best repair but their meanings can be cryptic without proper context.
Common symptoms include:
Blue Screen of Death (BSOD) indicating serious system errors System freezes or crashes during use Slow response times when opening apps or files Startup failures or boot loops preventing system access Unusual noises from hardware components like fans or hard drives Peripheral malfunctions such as keyboard or mouse issues
Understanding these symptoms helps pinpoint whether the problem is caused by software glitches or hardware faults.
Preparing to Troubleshoot Your Computer
Before diving into fixes, preparation is key to avoid data loss and further complications. Running diagnostics to gather system information, backing up important files, and knowing how to perform system restores are crucial first steps.
Key preparatory actions include:
Backing up critical data to an external drive or cloud service Creating a system restore point or bootable rescue USB for recovery Running built-in diagnostic tools to identify hardware or software faults Reviewing recent changes like new software installations or updates Ensuring your operating system and antivirus software are current
Proper maintenance and backup strategies not only facilitate easier troubleshooting but also protect your data in emergencies.
Step 1 - Identify the Type of Problem Software Issues
Software problems are often related to corrupted applications, update failures, viruses, or malware infections. These can cause security issues, unexpected errors, and degraded performance.
Common signs of software-related issues:
Frequent error messages or popup warnings Slow program launches or unresponsiveness Automatic restarts after updates fail Suspicious activity indicating virus or malware presence
Identifying software problems early allows for targeted virus removal, software updates, and security scans to restore stability.
Hardware Issues
Hardware problems involve physical components such as hard drives, memory modules, fans, or peripherals. Issues like overheating, power Phone repair supply failures, and faulty keyboards affect overall performance and usability.
Common hardware-related symptoms:
Hard drive
0 notes