#microsoft no code platform
Explore tagged Tumblr posts
Text
Unleash the potential of Microsoft Power Platform with us. We offer customized solutions, seamless integration, and dedicated support for your business needs.
#ms power platform#power platform#power apps#ms power platform consulting services#power bi#power automate#power bi business intelligence#power virtual agents#microsoft power platform#microsoft power apps#microsoft bi platform#microsoft no code platform#microsoft low code platform#power platform with NAV IT
0 notes
Text
Count The Rows In A Power Apps Gallery With AllItemsCount
Overview:
In this blog post, we’ll explore how to count Power Apps Gallery Rows using the AllItemsCount property. We’ll insert a label to show the count of all gallery items and then implement the exact code for precise counting. Each step comes with images and clear instructions. By the end, you’ll master the display of the total number of items in any gallery. Let’s dive in!
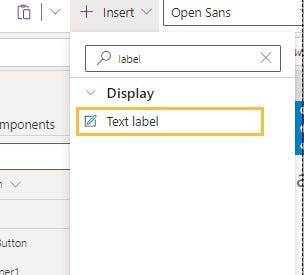

This code we use and count how many items in gallery
Read Full Post here: How to Count Rows in Power Apps Gallery: A Step-by-Step Guide (softwarezone365.com)
View Post On: LinkedIn: (4) Software Zone 365: Company Page Admin | LinkedIn Twitter: https://twitter.com/365_zone40741/status/1712883279580614768 Medium: Microsoft’s Power Platform Potential: Unlocking Business Impact (softwarezone365.com) Pinterest: https://www.pinterest.com/pin/1065875436793645010 Reddit: https://www.reddit.com/user/SoftwareZone365/comments/1773k2e/count_the_rows_in_a_power_apps_gallery_with/ Quora: https://www.quora.com/profile/Software-Zone-365/In-this-blog-post-we-ll-explore-how-to-count-Power-Apps-Gallery-Rows-using-the-AllItemsCount-property-We-ll-insert-a-l GitHub: Count The Rows In A Power Apps Gallery With AllItemsCount · softwarezone365/PowerApps Wiki (github.com) Instagram: https://www.instagram.com/p/CyWOuK8sGc9/ Facebook: https://m.facebook.com/story.php?story_fbid=300738072723966&id=100083633251137&mibextid=ZbWKwL
#development#AllItemsCount#App Development#BrowseGallery1#Coding in Power Apps#Gallery Items#Gallery Management#Gallery Rows#Item Counting#Label Count#Microsoft Power Apps#Power Apps#Power Apps Functions#Power Apps Gallery#Power Apps Tips#Power Apps Tutorial#Power platform#Row Counting Technique#Step-by-Step Guide#Text Property
2 notes
·
View notes
Text
Integrating ChatGPT with the Microsoft Power Platform could revolutionize how businesses develop and engage with their applications. This combination of advanced conversational AI and the versatile Power Platform enables organizations to create business apps that are not only powerful but also intuitive, helping companies enhance user experiences and automate critical processes more effectively. Microsoft PowerApps has become a cornerstone for businesses looking to develop custom applications quickly and with minimal coding. By integrating ChatGPT, companies can unlock new capabilities in their apps, allowing users to interact using natural language. This integration provides an innovative way to communicate with systems, retrieve information, and perform tasks, all through simple conversations. For example, users can ask a business app to generate reports, pull up customer data, or even schedule appointments, all by simply typing or speaking commands. This ease of interaction makes applications more user-friendly and efficient, especially for non-technical users. Regarding Power Apps development, integrating ChatGPT empowers developers to build more innovative apps with conversational interfaces. These apps can leverage AI to provide real-time insights, automate repetitive tasks, and even assist decision-making. An everyday use case for this integration might be customer service. ChatGPT can act as an intelligent virtual assistant to answer customer inquiries, suggest solutions, or provide status updates on support tickets. This improves overall productivity and satisfaction by cutting down on response times and freeing up customer support teams to concentrate on more complicated problems. Moreover, combining ChatGPT with Microsoft Power Automate takes automation a step further. Natural language interactions can automate routine tasks such as generating invoices, processing data inputs, and sending reminders. This reduces manual effort and ensures accuracy and consistency, freeing valuable resources for more strategic work. For businesses considering this integration, partnering with a Power Apps consulting firm can streamline the process and help maximize the potential of ChatGPT within the Microsoft Power Platform. These experts can assist in designing the app architecture, integrating AI features effectively, and ensuring that the app meets the business's unique needs. Whether enhancing customer support, optimizing internal workflows, or improving data management, integrating ChatGPT with Power Platform can significantly elevate the functionality and efficiency of business applications, paving the way for better results.
#microsoft powerapps#low code development#power apps consulting#power apps development#powerapps developers#buy power apps#hire powerapps developer#microsoft power apps development#microsoft power platform consulting#microsoft power platform solution#microsoft powerapps consulting services#microsoft powerapps development company#power apps development services#powerapps consulting services#best microsoft powerapps consulting services#powerapps development company#low code app development services#microsoft power apps consulting#microsoft power apps solutions#microsoft powerapps service#microsoft powerapps services#power apps developers#power apps integration#power apps services#top microsoft powerapps development company#top microsoft powerapps consultants
0 notes
Text
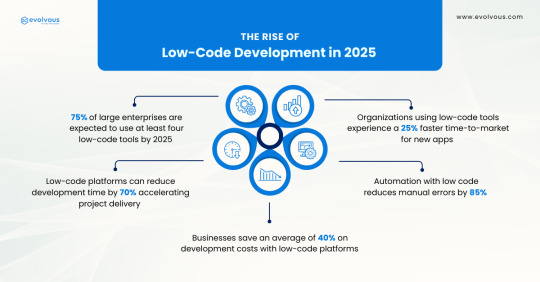
The Rise of Low-Code Development in 2025
Low-code development has revolutionized the way businesses operate. In 2025, we anticipate the technology will have a more significant impact. Here’s how. Microsoft Power Platform is a collection of low-code applications from Microsoft, making it easier for you to execute actions such as business analytics, app development, process automation, and other tools.
0 notes
Text
Visual Studio Code Platform untuk Mengembangkan Aplikasi Android
Hai Semuanya Di dunia pengembangan perangkat lunak, memilih alat yang tepat dapat membuat perbedaan besar dalam produktivitas dan kualitas hasil akhir. Salah satu Integrated Development Environment (IDE) yang sangat populer di kalangan pengembang adalah Visual Studio Code (VS Code). Dibuat oleh Microsoft, VS Code menawarkan beragam fitur canggih yang membuatnya menjadi pilihan utama bagi banyak…
0 notes
Text
0 notes
Text
Power Apps, a part of the Microsoft Power Platform, empowers users to create custom business applications without the need for extensive coding knowledge. However, to ensure the success of your PowerApps development projects, it's crucial to follow best practices and leverage essential tips. In this blog post, we'll explore key strategies to enhance your Power Apps development experience.
#PowerApps development company#Microsoft Power Platform#Custom business applications#No coding knowledge#PowerApps development#Best practices for powerapps#Tips for success#Key strategies#Enhance development experience#software development company
0 notes
Text
#Microsoft Power Platform#Digital Transformation Through the Power App#low-code digital transformation
0 notes
Text
that glow squid post haunts me. i genuinely love glow squids but it reads like a dream stan thing in retrospect and i did also like the other choices i just disliked people not having any vision for what glow ink could do
#sometimes it feels like either people have 0 imagination and take every word at face value in the mob votes and use that to get upset#(ignoring that the mobs are a CONCEPT and not in any way finished before community input happens)#OR they have more imagination than mojang/extrapolate ten bajillion nodes away from the root and use THAT to get upset#(often not taking into account game balance. or performance impact. or accessibility. or replayability. or cross-language coding.#and cross-platform playability. all of which are hugely hugely important bc mojang!! is a socially-conscious!!! company!! that makes games!#for all ages!!)#also no disrespect to dream stans i dont get it and i dont like the vibe of the fandom but thats nothing about u as people who Like Things#i simply dont like feeling misrepresented or misinterpreted so the fact that post still gets acknowledged regularly fucks me up#anyway.#without glow squids we'd still be stuck with flat unreadable sign text#and no cute lil beacons in the distance to know how far the cave goes#and as updates go on theyll probs be making glow ink more useful and interesting#just. like. its a video game#where u can do what u want when u want forever#u dont need to get so upset#and u DONT need to harrass the team about mob votes#i know mojang is a company is owned by microsoft#that doesnt mean that like. Those Arent People Working On And Loving The Game
0 notes
Text
Well. I have a feeling I'm about to have a million new followers. (March 31st, 2025; not an April Fool's joke, unless Nanowrimo has very poor taste and timing)
youtube
Here's a link that explains in long video format the whole entire thing in detail:
youtube
and to sum it up:
This blog was made as an Anti-Generative AI to Nanowrimo, as well as a way to actually build a friendly, low-pressure, helpful community of aspiring writers, without the hard-fast-do-it-or-die pressure brought on by nanowrimo.
There is no official "contest" -- only a community coming together to inspire each other to write, help out with motivation by setting community goals, keeping participation motivation via Trackbear.app, etc!
The most popular writing challenge is still November for most people, but I myself have also started to keep a year-round, daily writing goal of 444 via the website 4thewords, which has been an extreme help in getting me to write a little at a time.
This year has been very hectic for everyone what with the election results so I haven't been very active on tumblr (I think everyone can understand that) but I was originally planning on also having each month of the year being a different themed writing / art challenge but got a bit distracted real life.
So, what is the Novella November Challenge?
It's a fun challenge where writers come together to write 30,000 (or your own personal writing goal!) words in 30 days, sharing tips, writing advice, plot ideas, accessibility aids, and committing to having fun while explicitly fighting back against Generative AI by using our own words and disavowing the use of scraping and generating to take away the livelyhoods of artists of all spectrums, and proving everyone who insists "generative AI is an accessibility tool" wrong by committing to our creative visions and making it easier for everyone to find the tools they need to succeed by sharing tips, free programs, and finding a like-minded community to support you! 💙
There is no official website, there is no required place to show your participation, this is a community initiative that will never be monetized by predatory sponsors or dangerous moderators abusing their power.
This blog is here to inspire everyone, regardless of experience level, to write and create the story they want to tell, in their own words, while striving to remain a fun, low-pressure challenge that doesn't turn into a stressful spiral, like often happened with Nano.
Want to start writing but not sure how? Don't have money to spend on expensive writing programs? Have no fear!
LibreOffice: An always free, open-source alternative to Microsoft Word (and Microsoft's other office suits)
4Thewords: A website (both desktop and mobile web browser) that syncs your writing cross platform to the cloud, with built-in daily word goals, streak tracking, and you can fight monsters with your word count to game-ify writing!
Trackbear: A website dedicated to tracking your writing, setting custom goals, and creating leaderboards for community participation; you can join the year-long community leaderboard with the Join Code "f043cc66-6d5d-45b2-acf1-204626a727ba" and a November-limited one will release on November 1st as well.
Want to use Text to Speech to dictate your novel?
Most modern phones have a built-in option available on your keyboard settings which can be used on any writing program on your phone, and most modern PCs that allow a microphone (including headphone) connection has some kind of native dictation function, which you can find by opening your start panel and searching your computer for "Speech to text" or "voice to text".
Want to write while on the go, but don't want to / can't use the small phone keyboard to type, or speech to text?
You can, for as cheap as $40, buy a bluetooth keyboard that you can pair with your smart phone or tablet and use to write in any and all writing applications on your phone -- this allows you to write on the goal (especially using cross-platform websites or services, like 4thewords or google docs) , and the small screen can also help minimize distractions by muting notifications in your writing time.
#novella november#nanowrimo#large text#writing events#national novel writing month#community events#anti ai#novellanovember#Sam Beckett Voice: Oh boy#long post#Youtube
167 notes
·
View notes
Text
back to basics


mostly free resources to help you learn the basics that i've gathered for myself so far that i think are cool
everyday
gcfglobal - about the internet, online safety and for kids, life skills like applying for jobs, career planning, resume writing, online learning, today's skills like 3d printing, photoshop, smartphone basics, microsoft office apps, and mac friendly. they have core skills like reading, math, science, language learning - some topics are sparse so hopefully they keep adding things on. great site to start off on learning.
handsonbanking - learn about finances. after highschool, credit, banking, investing, money management, debt, goal setting, loans, cars, small businesses, military, insurance, retirement, etc.
bbc - learning for all ages. primary to adult. arts, history, science, math, reading, english, french, all the way to functional and vocational skills for adults as well, great site!
education.ket - workplace essential skills
general education
mathsgenie - GCSE revision, grade 1-9, math stages 1-14, provides more resources! completely free.
khan academy - pre-k to college, life skills, test prep (sats, mcat, etc), get ready courses, AP, partner courses like NASA, etc. so much more!
aleks - k-12 + higher ed learning program. adapts to each student.
biology4kids - learn biology
cosmos4kids - learn astronomy basics
chem4kids - learn chemistry
physics4kids - learn physics
numbernut - math basics (arithmetic, fractions and decimals, roots and exponents, prealgebra)
education.ket - primary to adult. includes highschool equivalent test prep, the core skills. they have a free resource library and they sell workbooks. they have one on work-life essentials (high demand career sectors + soft skills)
youtube channels
the organic chemistry tutor
khanacademy
crashcourse
tabletclassmath
2minmaths
kevinmathscience
professor leonard
greenemath
mathantics
3blue1brown
literacy
readworks - reading comprehension, build background knowledge, grow your vocabulary, strengthen strategic reading
chompchomp - grammar knowledge
tutors
not the "free resource" part of this post but sometimes we forget we can be tutored especially as an adult. just because we don't have formal education does not mean we can't get 1:1 teaching! please do you research and don't be afraid to try out different tutors. and remember you're not dumb just because someone's teaching style doesn't match up with your learning style.
cambridge coaching - medical school, mba and business, law school, graduate, college academics, high school and college process, middle school and high school admissions
preply - language tutoring. affordable!
revolutionprep - math, science, english, history, computer science (ap, html/css, java, python c++), foreign languages (german, korean, french, italian, spanish, japanese, chinese, esl)
varsity tutors - k-5 subjects, ap, test prep, languages, math, science & engineering, coding, homeschool, college essays, essay editing, etc
chegg - biology, business, engineering/computer science, math, homework help, textbook support, rent and buying books
learn to be - k-12 subjects
for languages
lingq - app. created by steve kaufmann, a polygot (fluent in 20+ languages) an amazing language learning platform that compiles content in 20+ languages like podcasts, graded readers, story times, vlogs, radio, books, the feature to put in your own books! immersion, comprehensible input.
flexiclasses - option to study abroad, resources to learn, mandarin, cantonese, japanese, vietnamese, korean, italian, russian, taiwanese hokkien, shanghainese.
fluentin3months - bootcamp, consultation available, languages: spanish, french, korean, german, chinese, japanese, russian, italian.
fluenz - spanish immersion both online and in person - intensive.
pimsleur - not tutoring** online learning using apps and their method. up to 50 languages, free trial available.
incase time has passed since i last posted this, check on the original post (not the reblogs) to see if i updated link or added new resources. i think i want to add laguage resources at some point too but until then, happy learning!!
#study#education resources#resources#learning#language learning#math#english languages#languages#japanese#mandarin#arabic#italian#computer science#wed design#coding#codeblr#fluency#online learning#learn#digital learning#education#studyinspo#study resources#educate yourselves#self improvement#mathematics#mathblr#resource
780 notes
·
View notes
Text
Demon-haunted computers are back, baby

Catch me in Miami! I'll be at Books and Books in Coral Gables on Jan 22 at 8PM.

As a science fiction writer, I am professionally irritated by a lot of sf movies. Not only do those writers get paid a lot more than I do, they insist on including things like "self-destruct" buttons on the bridges of their starships.
Look, I get it. When the evil empire is closing in on your flagship with its secret transdimensional technology, it's important that you keep those secrets out of the emperor's hand. An irrevocable self-destruct switch there on the bridge gets the job done! (It has to be irrevocable, otherwise the baddies'll just swarm the bridge and toggle it off).
But c'mon. If there's a facility built into your spaceship that causes it to explode no matter what the people on the bridge do, that is also a pretty big security risk! What if the bad guy figures out how to hijack the measure that – by design – the people who depend on the spaceship as a matter of life and death can't detect or override?
I mean, sure, you can try to simplify that self-destruct system to make it easier to audit and assure yourself that it doesn't have any bugs in it, but remember Schneier's Law: anyone can design a security system that works so well that they themselves can't think of a flaw in it. That doesn't mean you've made a security system that works – only that you've made a security system that works on people stupider than you.
I know it's weird to be worried about realism in movies that pretend we will ever find a practical means to visit other star systems and shuttle back and forth between them (which we are very, very unlikely to do):
https://pluralistic.net/2024/01/09/astrobezzle/#send-robots-instead
But this kind of foolishness galls me. It galls me even more when it happens in the real world of technology design, which is why I've spent the past quarter-century being very cross about Digital Rights Management in general, and trusted computing in particular.
It all starts in 2002, when a team from Microsoft visited our offices at EFF to tell us about this new thing they'd dreamed up called "trusted computing":
https://pluralistic.net/2020/12/05/trusting-trust/#thompsons-devil
The big idea was to stick a second computer inside your computer, a very secure little co-processor, that you couldn't access directly, let alone reprogram or interfere with. As far as this "trusted platform module" was concerned, you were the enemy. The "trust" in trusted computing was about other people being able to trust your computer, even if they didn't trust you.
So that little TPM would do all kinds of cute tricks. It could observe and produce a cryptographically signed manifest of the entire boot-chain of your computer, which was meant to be an unforgeable certificate attesting to which kind of computer you were running and what software you were running on it. That meant that programs on other computers could decide whether to talk to your computer based on whether they agreed with your choices about which code to run.
This process, called "remote attestation," is generally billed as a way to identify and block computers that have been compromised by malware, or to identify gamers who are running cheats and refuse to play with them. But inevitably it turns into a way to refuse service to computers that have privacy blockers turned on, or are running stream-ripping software, or whose owners are blocking ads:
https://pluralistic.net/2023/08/02/self-incrimination/#wei-bai-bai
After all, a system that treats the device's owner as an adversary is a natural ally for the owner's other, human adversaries. The rubric for treating the owner as an adversary focuses on the way that users can be fooled by bad people with bad programs. If your computer gets taken over by malicious software, that malware might intercept queries from your antivirus program and send it false data that lulls it into thinking your computer is fine, even as your private data is being plundered and your system is being used to launch malware attacks on others.
These separate, non-user-accessible, non-updateable secure systems serve a nubs of certainty, a remote fortress that observes and faithfully reports on the interior workings of your computer. This separate system can't be user-modifiable or field-updateable, because then malicious software could impersonate the user and disable the security chip.
It's true that compromised computers are a real and terrifying problem. Your computer is privy to your most intimate secrets and an attacker who can turn it against you can harm you in untold ways. But the widespread redesign of out computers to treat us as their enemies gives rise to a range of completely predictable and – I would argue – even worse harms. Building computers that treat their owners as untrusted parties is a system that works well, but fails badly.
First of all, there are the ways that trusted computing is designed to hurt you. The most reliable way to enshittify something is to supply it over a computer that runs programs you can't alter, and that rats you out to third parties if you run counter-programs that disenshittify the service you're using. That's how we get inkjet printers that refuse to use perfectly good third-party ink and cars that refuse to accept perfectly good engine repairs if they are performed by third-party mechanics:
https://pluralistic.net/2023/07/24/rent-to-pwn/#kitt-is-a-demon
It's how we get cursed devices and appliances, from the juicer that won't squeeze third-party juice to the insulin pump that won't connect to a third-party continuous glucose monitor:
https://arstechnica.com/gaming/2020/01/unauthorized-bread-a-near-future-tale-of-refugees-and-sinister-iot-appliances/
But trusted computing doesn't just create an opaque veil between your computer and the programs you use to inspect and control it. Trusted computing creates a no-go zone where programs can change their behavior based on whether they think they're being observed.
The most prominent example of this is Dieselgate, where auto manufacturers murdered hundreds of people by gimmicking their cars to emit illegal amount of NOX. Key to Dieselgate was a program that sought to determine whether it was being observed by regulators (it checked for the telltale signs of the standard test-suite) and changed its behavior to color within the lines.
Software that is seeking to harm the owner of the device that's running it must be able to detect when it is being run inside a simulation, a test-suite, a virtual machine, or any other hallucinatory virtual world. Just as Descartes couldn't know whether anything was real until he assured himself that he could trust his senses, malware is always questing to discover whether it is running in the real universe, or in a simulation created by a wicked god:
https://pluralistic.net/2022/07/28/descartes-was-an-optimist/#uh-oh
That's why mobile malware uses clever gambits like periodically checking for readings from your device's accelerometer, on the theory that a virtual mobile phone running on a security researcher's test bench won't have the fidelity to generate plausible jiggles to match the real data that comes from a phone in your pocket:
https://arstechnica.com/information-technology/2019/01/google-play-malware-used-phones-motion-sensors-to-conceal-itself/
Sometimes this backfires in absolutely delightful ways. When the Wannacry ransomware was holding the world hostage, the security researcher Marcus Hutchins noticed that its code made reference to a very weird website: iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com. Hutchins stood up a website at that address and every Wannacry-infection in the world went instantly dormant:
https://pluralistic.net/2020/07/10/flintstone-delano-roosevelt/#the-matrix
It turns out that Wannacry's authors were using that ferkakte URL the same way that mobile malware authors were using accelerometer readings – to fulfill Descartes' imperative to distinguish the Matrix from reality. The malware authors knew that security researchers often ran malicious code inside sandboxes that answered every network query with fake data in hopes of eliciting responses that could be analyzed for weaknesses. So the Wannacry worm would periodically poll this nonexistent website and, if it got an answer, it would assume that it was being monitored by a security researcher and it would retreat to an encrypted blob, ceasing to operate lest it give intelligence to the enemy. When Hutchins put a webserver up at iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com, every Wannacry instance in the world was instantly convinced that it was running on an enemy's simulator and withdrew into sulky hibernation.
The arms race to distinguish simulation from reality is critical and the stakes only get higher by the day. Malware abounds, even as our devices grow more intimately woven through our lives. We put our bodies into computers – cars, buildings – and computers inside our bodies. We absolutely want our computers to be able to faithfully convey what's going on inside them.
But we keep running as hard as we can in the opposite direction, leaning harder into secure computing models built on subsystems in our computers that treat us as the threat. Take UEFI, the ubiquitous security system that observes your computer's boot process, halting it if it sees something it doesn't approve of. On the one hand, this has made installing GNU/Linux and other alternative OSes vastly harder across a wide variety of devices. This means that when a vendor end-of-lifes a gadget, no one can make an alternative OS for it, so off the landfill it goes.
It doesn't help that UEFI – and other trusted computing modules – are covered by Section 1201 of the Digital Millennium Copyright Act (DMCA), which makes it a felony to publish information that can bypass or weaken the system. The threat of a five-year prison sentence and a $500,000 fine means that UEFI and other trusted computing systems are understudied, leaving them festering with longstanding bugs:
https://pluralistic.net/2020/09/09/free-sample/#que-viva
Here's where it gets really bad. If an attacker can get inside UEFI, they can run malicious software that – by design – no program running on our computers can detect or block. That badware is running in "Ring -1" – a zone of privilege that overrides the operating system itself.
Here's the bad news: UEFI malware has already been detected in the wild:
https://securelist.com/cosmicstrand-uefi-firmware-rootkit/106973/
And here's the worst news: researchers have just identified another exploitable UEFI bug, dubbed Pixiefail:
https://blog.quarkslab.com/pixiefail-nine-vulnerabilities-in-tianocores-edk-ii-ipv6-network-stack.html
Writing in Ars Technica, Dan Goodin breaks down Pixiefail, describing how anyone on the same LAN as a vulnerable computer can infect its firmware:
https://arstechnica.com/security/2024/01/new-uefi-vulnerabilities-send-firmware-devs-across-an-entire-ecosystem-scrambling/
That vulnerability extends to computers in a data-center where the attacker has a cloud computing instance. PXE – the system that Pixiefail attacks – isn't widely used in home or office environments, but it's very common in data-centers.
Again, once a computer is exploited with Pixiefail, software running on that computer can't detect or delete the Pixiefail code. When the compromised computer is queried by the operating system, Pixiefail undetectably lies to the OS. "Hey, OS, does this drive have a file called 'pixiefail?'" "Nope." "Hey, OS, are you running a process called 'pixiefail?'" "Nope."
This is a self-destruct switch that's been compromised by the enemy, and which no one on the bridge can de-activate – by design. It's not the first time this has happened, and it won't be the last.
There are models for helping your computer bust out of the Matrix. Back in 2016, Edward Snowden and bunnie Huang prototyped and published source code and schematics for an "introspection engine":
https://assets.pubpub.org/aacpjrja/AgainstTheLaw-CounteringLawfulAbusesofDigitalSurveillance.pdf
This is a single-board computer that lives in an ultraslim shim that you slide between your iPhone's mainboard and its case, leaving a ribbon cable poking out of the SIM slot. This connects to a case that has its own OLED display. The board has leads that physically contact each of the network interfaces on the phone, conveying any data they transit to the screen so that you can observe the data your phone is sending without having to trust your phone.
(I liked this gadget so much that I included it as a major plot point in my 2020 novel Attack Surface, the third book in the Little Brother series):
https://craphound.com/attacksurface/
We don't have to cede control over our devices in order to secure them. Indeed, we can't ever secure them unless we can control them. Self-destruct switches don't belong on the bridge of your spaceship, and trusted computing modules don't belong in your devices.

I'm Kickstarting the audiobook for The Bezzle, the sequel to Red Team Blues, narrated by @wilwheaton! You can pre-order the audiobook and ebook, DRM free, as well as the hardcover, signed or unsigned. There's also bundles with Red Team Blues in ebook, audio or paperback.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/01/17/descartes-delenda-est/#self-destruct-sequence-initiated

Image: Mike (modified) https://www.flickr.com/photos/stillwellmike/15676883261/
CC BY-SA 2.0 https://creativecommons.org/licenses/by-sa/2.0/
#pluralistic#uefi#owner override#user override#jailbreaking#dmca 1201#schneiers law#descartes#nub of certainty#self-destruct button#trusted computing#secure enclaves#drm#ngscb#next generation secure computing base#palladium#pixiefail#infosec
576 notes
·
View notes
Text
From the Slang Dictionary
part 2
Algospeak - coded language that people use (“speak”) to avoid being censored or moderated by AI algorithms. It combines algo- from the word "algorithm" with the word speak. The word was used as early as 2016 on social media. Many websites, especially social media sites, use AI algorithms to moderate the large amount of content posted on their platforms. These algorithms often automatically flag or delete content that contains or mentions words or phrases that the algorithm has been programmed to recognize as being unacceptable. However, this often causes algorithms to flag or remove permitted content that discusses sensitive issues or content that uses the “unacceptable” words without breaking any rules. Being aware of this, many communities on social media use coded language, emoji, or euphemisms to avoid having their content removed by algorithms. The term algospeak refers to this language. For example, people used terms like panoramic, panini, and panda express to refer to the COVID-19 pandemic after platforms began removing content that mentioned the pandemic to attempt to halt the spread of misinformation. Some other examples of algospeak include using the word seggs instead of sex, the word accountants to refer to sex workers, the word unalive to refer to death or suicide, the corn emoji to refer to pornography, and the phrase leg booty to refer to the LGBTQ+ community.
Birb - also spelled as berb, is a deliberate misspelling of bird used in internet slang such as DoggoLingo. It’s used as a playful way to refer to cute birds, particularly pet birds.
Bye Felicia - a slang way of dismissing someone. Sometimes formatted as bye, Felicia and based on a movie character whose name is spelled Felisha, it often appears in memes, GIFs, and hashtags online to express disregard or indifference to someone. The term has been popular in Black culture since the 1990s when the film was released, although the original spelling of the name “Felisha” has changed to the more common (and, some would point out, more “white”) spelling, Felicia. Bye Felicia is considered by some to be an example of white culture appropriating Black culture, often with little knowledge of the original source material. The phrase enjoyed renewed popularity around 2009 thanks to its frequent use on the reality TV show RuPaul’s Drag Race. It got another bump in December 2018, when former First Lady of the United States, Michelle Obama, used it as a guest on The Tonight Show Starring Jimmy Fallon to describe what was going through her head as she and President Obama waved goodbye to the White House at the end of Obama’s presidency in January 2017. Bye Felicia is most often used humorously or as a way to throw shade at someone, suggesting the speaker couldn’t be bothered with another person’s presence or is surprised they haven’t left yet. While humor is almost always part of the intention in using the term, the tone in which it is said has changed somewhat over time. Initially, bye Felicia was said coolly or nonchalantly, as in the movie Friday; now, it’s just as often used in a more aggressive or melodramatic way.
Doggo - this and pupper are affectionate terms for dog and puppy used in the internet slang called DoggoLingo. This emerged in the 2010s and drew on existing online culture, such as lolspeak, the snek meme, and Doge.
Left on read - in internet slang, a person is left on read when a recipient has read, but not responded to, a sender’s message. The expression is often used to express feeling ignored. A read receipt lets the sender know a digital message has been opened or seen (i.e., read) by the recipient. Microsoft Outlook, for instance, allows read receipts for email. Apple has enabled read receipts for text messages since 2011.
Receipts - slang for “proof” or “evidence,” often used to call out someone for lying or to show someone is being genuine. In popular culture, such receipts may come in the form of screenshots, images, or videos. They also often concern things done by famous people. One of the first prominent uses of receipts came in a 2002 interview of singer Whitney Houston by Diane Sawyer for ABC. Sawyer brought up the topic of recent tabloid headlines that accused Houston of buying large amounts of crack cocaine. Houston denied these accusations and demanded proof: “I want to see the receipts.”
Shelfie - a picture of a shelf, especially a bookshelf that shows off someone’s books, movies, art, collectibles, special belongings, etc. It can also be a proper selfie if you are in the picture with the shelves. On social media, the hashtag #shelfie is often posted alongside pictures of various shelves where a person lives or works.
Snacc - internet slang for an extremely attractive or sexy person (i.e., you want to gobble them up like a snack). It’s also internet slang used when cute animals are seeking or enjoying a snack. Snacc, with two Cs, emerges on Black Twitter in 2009, the deliberate misspelling is consistent with other black slang terms, such as phat, thicc, and succ. Early uses of this term refer to actual snacks. Sexual senses of snacc do begin to appear around this time in wordplay, but it doesn’t take off in earnest until around 2017.
Spirit animal - In certain spiritual traditions or cultures, this refers to a spirit which helps guide or protect a person on a journey and whose characteristics that person shares or embodies. It is also metaphor, often humorous, for someone or something a person relates to or admires. The ancient concept of animal guides, particularly prominent in some indigenous, especially Native American, religions and cultures, was adopted in Pagan and Wiccan spirituality in the 1990s. In these contexts, spirit animals are meant literally, referring to spiritual guides or totems that take the form of animals. Earnest quizzes began to emerge in the mid-2000s to help you find your spirit animal. Spirit animal has increasingly been used to indicate, ironically, a strong appreciation or identification for someone or something.
Tea - best served piping hot, tea is slang for “gossip,” a juicy scoop, or other personal information. As far as we can tell, it was steeped in black drag culture. One theory connects tea to the celebrated drag performer The Lady Chablis, who is quoted in the 1994 bestseller Midnight in the Garden of Good and Evil: “Yeah, my T. My thing, my business, what’s goin’ on in my life.” T, here, is short for truth.
Source ⚜ More: Word Lists ⚜ Writing Resources PDFs ⚜ Part 1
#requested#slang#writeblr#writing reference#langblr#word list#writing prompt#spilled ink#dark academia#writers on tumblr#literature#linguistics#language#internet#creative writing#writing inspiration#writing ideas#dialogue#writing resources
85 notes
·
View notes
Text
Businesses looking to streamline their Power Apps development processes must comprehend the distinction between Model-Driven Apps and Canvas Apps in Microsoft PowerApps. Both app types offer distinct approaches to building applications, with their own sets of advantages depending on the specific use case. Model-driven apps are data-centric and built around the Common Data Service (CDS), making them ideal for applications that require structured data relationships. Users interact with pre-defined forms, views, and dashboards in these apps, which are automatically generated according to the data model. Model-Driven Apps' main benefits are their rapid scalability and smooth integration with other Microsoft products.Businesses that require reliable, data-intensive software for handling intricate procedures like enterprise resource planning (ERP) or customer relationship management (CRM) are especially well-suited for them. Conversely, Canvas Apps offer greater design flexibility.. With Canvas Apps, developers have complete control over the user interface, allowing them to drag and drop various elements to create a highly customized experience. These apps can connect to multiple data sources, from Excel files to SharePoint lists, offering greater adaptability. Canvas Apps are ideal for scenarios where visual customization is paramount and users require more freedom in layout and user interaction. When deciding between the two, businesses should consider the specific needs of their application. Model-driven apps are best suited for scenarios where structured data and complex relationships take center stage. At the same time, Canvas Apps shine in situations where visual design and user experience are a priority. For companies looking to implement these solutions, partnering with a Power Apps consulting firm can provide the expertise needed to choose the right app type based on their development goals. Whether embarking on your first PowerApps project or refining an existing solution, understanding the fundamental differences between these two types of apps can significantly impact your success in Power Apps development.
#powerapps developers#hire powerapps developer#buy power apps#microsoft power apps development#microsoft power platform consulting#microsoft power platform solution#microsoft powerapps consulting services#microsoft powerapps development company#power apps development services#powerapps consulting services#powerapps development company#best microsoft powerapps consulting services#low code app development services#microsoft power apps consulting#microsoft power apps solutions#microsoft powerapps service#microsoft powerapps services#power apps developers#power apps integration#power apps services#top microsoft powerapps consultants#top microsoft powerapps development company
0 notes
Text
These days, when Nicole Yelland receives a meeting request from someone she doesn’t already know, she conducts a multi-step background check before deciding whether to accept. Yelland, who works in public relations for a Detroit-based non-profit, says she’ll run the person’s information through Spokeo, a personal data aggregator that she pays a monthly subscription fee to use. If the contact claims to speak Spanish, Yelland says, she will casually test their ability to understand and translate trickier phrases. If something doesn’t quite seem right, she’ll ask the person to join a Microsoft Teams call—with their camera on.
If Yelland sounds paranoid, that’s because she is. In January, before she started her current non-profit role, Yelland says she got roped into an elaborate scam targeting job seekers. “Now, I do the whole verification rigamarole any time someone reaches out to me,” she tells WIRED.
Digital imposter scams aren’t new; messaging platforms, social media sites, and dating apps have long been rife with fakery. In a time when remote work and distributed teams have become commonplace, professional communications channels are no longer safe, either. The same artificial intelligence tools that tech companies promise will boost worker productivity are also making it easier for criminals and fraudsters to construct fake personas in seconds.
On LinkedIn, it can be hard to distinguish a slightly touched-up headshot of a real person from a too-polished, AI-generated facsimile. Deepfake videos are getting so good that longtime email scammers are pivoting to impersonating people on live video calls. According to the US Federal Trade Commission, reports of job and employment related scams nearly tripled from 2020 to 2024, and actual losses from those scams have increased from $90 million to $500 million.
Yelland says the scammers that approached her back in January were impersonating a real company, one with a legitimate product. The “hiring manager” she corresponded with over email also seemed legit, even sharing a slide deck outlining the responsibilities of the role they were advertising. But during the first video interview, Yelland says, the scammers refused to turn their cameras on during a Microsoft Teams meeting and made unusual requests for detailed personal information, including her driver’s license number. Realizing she’d been duped, Yelland slammed her laptop shut.
These kinds of schemes have become so widespread that AI startups have emerged promising to detect other AI-enabled deepfakes, including GetReal Labs, and Reality Defender. OpenAI CEO Sam Altman also runs an identity-verification startup called Tools for Humanity, which makes eye-scanning devices that capture a person’s biometric data, create a unique identifier for their identity, and store that information on the blockchain. The whole idea behind it is proving “personhood,” or that someone is a real human. (Lots of people working on blockchain technology say that blockchain is the solution for identity verification.)
But some corporate professionals are turning instead to old-fashioned social engineering techniques to verify every fishy-seeming interaction they have. Welcome to the Age of Paranoia, when someone might ask you to send them an email while you’re mid-conversation on the phone, slide into your Instagram DMs to ensure the LinkedIn message you sent was really from you, or request you text a selfie with a timestamp, proving you are who you claim to be. Some colleagues say they even share code words with each other, so they have a way to ensure they’re not being misled if an encounter feels off.
“What’s funny is, the low-fi approach works,” says Daniel Goldman, a blockchain software engineer and former startup founder. Goldman says he began changing his own behavior after he heard a prominent figure in the crypto world had been convincingly deepfaked on a video call. “It put the fear of god in me,” he says. Afterwards, he warned his family and friends that even if they hear what they believe is his voice or see him on a video call asking for something concrete—like money or an internet password—they should hang up and email him first before doing anything.
Ken Schumacher, founder of the recruitment verification service Ropes, says he’s worked with hiring managers who ask job candidates rapid-fire questions about the city where they claim to live on their resume, such as their favorite coffee shops and places to hang out. If the applicant is actually based in that geographic region, Schumacher says, they should be able to respond quickly with accurate details.
Another verification tactic some people use, Schumacher says, is what he calls the “phone camera trick.” If someone suspects the person they’re talking to over video chat is being deceitful, they can ask them to hold up their phone camera to their laptop. The idea is to verify whether the individual may be running deepfake technology on their computer, obscuring their true identity or surroundings. But it’s safe to say this approach can also be off-putting: Honest job candidates may be hesitant to show off the inside of their homes or offices, or worry a hiring manager is trying to learn details about their personal lives.
“Everyone is on edge and wary of each other now,” Schumacher says.
While turning yourself into a human captcha may be a fairly effective approach to operational security, even the most paranoid admit these checks create an atmosphere of distrust before two parties have even had the chance to really connect. They can also be a huge time suck. “I feel like something’s gotta give,” Yelland says. “I’m wasting so much time at work just trying to figure out if people are real.”
Jessica Eise, an assistant professor studying climate change and social behavior at Indiana University-Bloomington, says that her research team has been forced to essentially become digital forensics experts, due to the amount of fraudsters who respond to ads for paid virtual surveys. (Scammers aren’t as interested in the unpaid surveys, unsurprisingly.) If the research project is federally funded, all of the online participants have to be over the age of 18 and living in the US.
“My team would check time stamps for when participants answered emails, and if the timing was suspicious, we could guess they might be in a different time zone,” Eise says. “Then we’d look for other clues we came to recognize, like certain formats of email address or incoherent demographic data.”
Eise says the amount of time her team spent screening people was “exorbitant,” and that they’ve now shrunk the size of the cohort for each study and have turned to “snowball sampling” or having recruiting people they know personally to join their studies. The researchers are also handing out more physical flyers to solicit participants in person. “We care a lot about making sure that our data has integrity, that we’re studying who we say we’re trying to study,” she says. “I don’t think there’s an easy solution to this.”
Barring any widespread technical solution, a little common sense can go a long way in spotting bad actors. Yelland shared with me the slide deck that she received as part of the fake job pitch. At first glance, it seemed like legit pitch, but when she looked at it again, a few details stood out. The job promised to pay substantially more than the average salary for a similar role in her location, and offered unlimited vacation time, generous paid parental leave, and fully-covered health care benefits. In today’s job environment, that might have been the biggest tipoff of all that it was a scam.
27 notes
·
View notes
Text
The Writer's Toolkit
#1. Notion/Milanote
One of the most important tools for a writer is being able to stay organized. There are tons of apps for this, but I’ve found that either Milanote or Notion works best.
My recommendation:
Use Notion if: you’re writing a serial, like to keep chapters in separate documents, like spreadsheets, or complete organizational customization
Use Milanote if: you’re very visual/moodboard-based, like drag-and-drop features, and you’re not keeping a whole lot of your actual text in the app
#2. A Dictionary
Perhaps the most tried-and-true tool for a writer is the dictionary! I’m constantly using a dictionary app to double-check word meanings or to look for synonyms when I’m writing.
My personal favorite is the Dictionary.com app. Whatever app you choose, you want it to be as convenient as possible, so you can research words/definitions without disturbing the flow of your writing. I like Dictionary.com because you can easily switch between dictionary and thesaurus mode.
#3 Pinterest
Sometimes the creative well runs dry. And when that happens, I turn to my reliable old pal, Pinterest.
I keep several boards for each story:
Characters: faces, similar characters, outfits, traits
Inspiration: anything that has an intriguing element
Aesthetic: VIBES; images that match the tone of the story
World: streets, architecture, maps, important settings
Fill these boards up throughout your scrolling. Then, when you need some inspiration, you can turn back to what you’ve pinned and go from there!
#4 Google Docs
So you’ve got all the tools you need to stay organized and inspired. Time to write! Obviously any Word processor works, but my platform of choice is the infamous Google Doc. Some people hate it, but I find it very useful for writers who often write on the go or switch devices often. You can access drafts on your phone, iPad, or any laptop and pick up exactly where you left off.
I also like Google Docs’ accessibility, price (free), and the outlining features!
In case you don’t want to use Google Docs, here are a few others I’ve heard commonly used:
Microsoft Word ($140)
Scrivener ($49)
Atticus ($147)
World Anvil ($7/month)
#5 Timer App
In Haruki Murakami’s collection of essays, Novelist as a Vocation, he talks about how a “formula” to your writing routine is “absolutely crucial” to finishing a novel. For him, he breaks it up into ten pages a day. For author Anthony Trollope, he is known for his 250-words-in-15-minutes routine, which also corresponds to roughly ten pages a day.
How you choose to structure your routine is up to you, but I’ve found Trollope’s timed method really helpful in reducing perfectionism and forcing myself to just write.
So, I use a timer app (the standard Apple one is fine) to write for 15-minute chunks, aiming for 250 words. Surprisingly, I usually end up with more than that. Breaking my writing into sprints like this has become a bit of a cheat code for jumpstarting my writing process and getting the creative juices flowing.
#6 Substack
A bit of a shameless self-plug here (seeing as I write on Substack, as well), but the amount of talented writers on there that are actively sharing their writing expertise is frankly obscene. There is so much knowledge to be found on Substack, beyond your standard tech newsletters and political ramblings. There’s also FICTION (usually free!) on Substack, and writers talking about writing! All the time!
Here are a few of my favorite newsletters:
A Mug of Insights
Tales from the Triverse (Write More with Simon K Jones)
Beyond the Bookshelf
Chuck Palahniuk’s Plot Spoiler
You can also check out my Substack, where I post installments of my gothic fantasy Monster Monster every Friday!
14 notes
·
View notes