#OpenSSL
Explore tagged Tumblr posts
Text
0 notes
Text
CNSA 2.0 Algorithms: OpenSSL 3.5’s Q-Safe Group Selection

The CNSA 2.0 Algorithm
To prioritise quantum-safe cryptographic methods, OpenSSL 3.5 improves TLS 1.3 per NSA CNSA 2.0 recommendations. With these changes, servers and clients can prefer Q-safe algorithms during the TLS handshake.
OpenSSL employs unique configuration methods to do this without modifying TLS. For instance, servers use a delimiter to sort algorithms by security level while clients use a prefix to indicate key sharing.
These changes provide backward compatibility and reduce network round trips to enable a smooth transition to post-quantum cryptography while maintaining the “prefer” criterion for Q-safe algorithms. This version of OpenSSL is the first major TLS library to completely implement CNSA 2.0, and its long-term support makes it likely to be widely deployed.
Q Safe
Quantum-Safe Cryptography and Quantum Computer Danger
The possibility that quantum computers may break asymmetric encryption drives this research.
“Future quantum computers will break the asymmetric cryptographic algorithms widely used online.”
To secure internet communication, quantum-safe (Q-safe) cryptographic methods must be used.
CNSA 2.0's NSA Major Initiator mandate
The NSA's Commercial National Security Algorithm Suite 2.0 (CNSA 2.0) lists authorised quantum-safe algorithms and their implementation timetable. TLS allows ML-KEM (FIPS-203) for key agreements and ML-DSA or SPINCS+ for certificates.
The CNSA 2.0 requirement requires systems to “prefer CNSA 2.0 algorithms” during transition and “accept only CNSA 2.0 algorithms” as products develop. This two-phase method aims for a gradual transition.
The TLS “Preference” Implementation Challenge
TLS (RFC 8446) clients and servers can freely pick post quantum cryptography methods without a preference mechanism. The TLS protocol does not need this decision. The TLS standard allows clients and servers wide freedom in choosing encryption techniques.
A way to set up TLS connections to favour CNSA 2.0 algorithms is urgently needed. One must figure out method to favour Q-safe algorithms without modifying the TLS protocol.
OpenSSL v3.5 Improves Configuration Features
Developers focused on increasing OpenSSL's configuration capabilities since altering the TLS standard was not possible. The goal was to let OpenSSL-using programs like cURL, HAproxy, and Nginx use the new preference choices without modifying their code.
Client-Side Solution: Prefix Characters for Preference
Clients can provide Q-safe algorithms in OpenSSL v3.5 by prefixing the algorithm name with a special character (”) before the algorithm name in the colon-separated list. The ClientHello message asks the client to generate and deliver key shares for ML-KEM-1024 and x25519, showing support for four algorithms.
A client can submit a maximum of four key shares, which can be modified using a build option, to minimise network congestion from Q-safe key shares' increased size. This architecture should allow completely Q-safe, hybrid, legacy, and spare algorithms.
For backward compatibility, the first algorithm in the list receives a single key share if no ‘*’ prefix is supplied.
Server-Side Solution: Preference Hierarchy Algorithm Tuples
The server-side technique overcomes TLS's lack of a native “preference” mechanism by declaring the server's preferred algorithm order using tuples delimited by the ‘/’ character in the colon-separated list of algorithms.
The server can pick algorithms using a three-level priority scheme.
Tuple processing from left to right is most important.
Second priority is client-provided key sharing overlap inside a tuple.
Third, overlap within a tuple using client-supported methods without key sharing.
Example: ML-KEM-768 / X25519MLKEM768
Three tuples are defined by x25519 / SecP256r1MLKEM768. Within each tuple, the server prioritises algorithms from previous tuples, then key share availability, and finally general support.
Even with a vintage algorithm with a readily available key share, this solution ensures that the server favours Q-safe algorithms despite the risk of a HelloRetryRequest (HRR) penalty: The prefer requirement of CNSA 2.0 prioritises Q-safe algorithms, even at the risk of a round-trip penalty that is fully eliminated by the new specification syntax.
Keep Backward Compatibility and Reduce Impact on Current Systems
Designing for backward compatibility was crucial for a smooth transition. The new configuration format doesn't need code changes for existing apps. To avoid disrupting other features, OpenSSL codebase tweaks were carefully made in “a few pinpointed locations” of the huge codebase.
Additional Implementation Considerations
A “?” prefix was added to ignore unknown algorithm names, handle pseudo-algorithm names like “DEFAULT,” and allow the client and server to use the same specification string (requiring the client to ignore server-specific delimiters and the server to ignore client-specific prefixes).
OpenSSL v3.5's Collaboration and Importance
Development involved considerable consultation and collaboration with the OpenSSL maintainer team and other expertise. The paragraph praises the “excellent interactions” throughout development.
OpenSSL v3.5 is “the first TLS library to fully adhere to the CNSA 2.0 mandate to prefer Q-safe algorithms.” Due to its Long-Term Support (LTS) status, Linux distributions are expected to adopt OpenSSL v3.5 more extensively, making these quantum-safe communication capabilities available.
Conclusion
OpenSSL v3.5 must have the Q-safe algorithm preference to safeguard internet communication from quantum computers. The developers satisfied the NSA's CNSA 2.0 criteria by cleverly increasing OpenSSL's configuration features without requiring large code modifications in OpenSSL-reliant applications or TLS standard changes.
Client-side prefix and server-side tuple-based preference systems give quantum-resistant cryptography precedence in a backward-compatible way, enabling a safe digital future. OpenSSL v3.5's LTS status ensures its widespread use, enabling quantum-safe communication on many computers.
FAQs
How is Quantum Safe?
“Quantum safe” security and encryption withstand conventional and quantum computer assaults. It involves developing and implementing cryptography methods that can withstand quantum computing threats.
#technology#technews#govindhtech#news#technologynews#CNSA 2.0 Algorithms#CNSA 2.0#OpenSSL#Q-safe algorithms#Q-safe#OpenSSL v3.5#Quantum Safe
0 notes
Text
The encryption format used by OpenSSL is non-standard: it is "what OpenSSL does", and if all versions of OpenSSL tend to agree with each other, there is still no reference document which describes this format except OpenSSL source code.
0 notes
Text
PHP OpenSSL Encrypt & Decrypt
Merhabalar, bu yazımda PHP OpenSSL Encrypt & Decrypt konusuna değineceğim. Daha önceleri Encrypt & Decrypt konusunda bir yazı daha yazmıştım. Her ne kadar konu olarak aynı olsa da yöntem olarak farklı oldukları için yeni bir yazı olarak yazıyorum. Üstelik şifreleme üzerinde farklı programlama dillerine dair bir çok yazım var. Hepsini hemen aşağıya ekliyorum. PHP MD5 Şifreleme Kullanımı C#…

View On WordPress
0 notes
Text
1 note
·
View note
Text
#LinuxUpdates#AlmaLinux#RedHatEnterpriseLinux#Oracle#OpenSource#pfSense#Netgate#SecurityUpdates#OpenSSL#LinuxNews
0 notes
Text
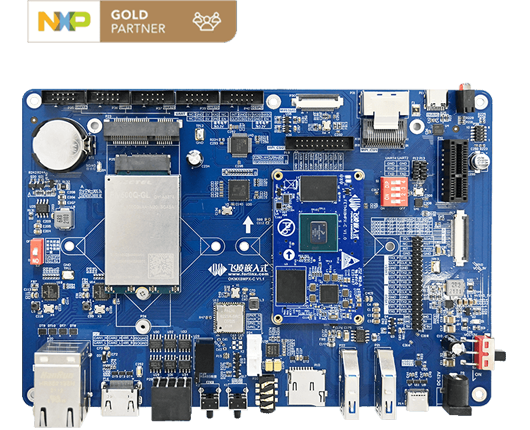
How to Apply OpenSSL on i.MX8M Plus EVK?
Check out the Forlinx Embedded OKMX8MP-C EVK, featuring the NXP i.MX8M Plus processor with AI computing power up to 2.3TOPS. With flexible I/O interface configuration and advanced multimedia resources, it's perfect for lightweight edge computing needs. And with OpenSSL tools ported in, you can easily generate passwords, compute hash values, and test library performance. Learn more about this powerful evaluation kit today!
0 notes
Text
OpenSSL 3.5 Lanza Cambios Criptográficos Importantes
OpenSSL 3.5, la última versión de la popular biblioteca criptográfica, introduce mejoras significativas en seguridad, rendimiento y preparación para la computación post-cuántica (PQC). Esta actualización trae nuevos algoritmos, soporte para QUIC del lado del servidor y ajustes en los protocolos TLS por defecto. Principales Novedades en OpenSSL 3.5 1. Cambios en Cifrado por Defecto AES-256-CBC…
0 notes
Text
How to Install OpenSSL on Windows Computers
In this article, we shall discuss how to Install OpenSSL on Windows Computers. OpenSSL is an open-source command-line tool that is used to generate the SSL certificate and private key and is available in both versions 32 and 64 bit. Please see How to fix Windows Update Fails with Error 0x80092004, how to Fix the Port used for the Virtualhost is not an Apache Listen Port, and Shell Scripting: How…
#convert key format OpenSSL#convert PEM to DER OpenSSL#extract public key OpenSSL#generate private public key OpenSSL#how to use OpenSSL on Windows#install OpenSSL Windows#Microsoft Windows#OpenSSL installation#OpenSSL key conversion#OpenSSL key generation tutorial#OpenSSL key management#OpenSSL public key extraction#OpenSSL Windows#OpenSSL Windows installation steps#Windows#Windows 10#Windows 11#Windows OpenSSL setup#Windows Server#Windows Server 2012#Windows Server 2016#Windows Server 2019#Windows Server 2022
1 note
·
View note
Text
If you can remember ffmpeg, nmap and openssl syntax from core memory, then you've already mastered the art of the CLI! 💻
171 notes
·
View notes
Text

True story: I had to try several times to upload this comic because my ssh key was blacklisted.
Security Holes [Explained]
Transcript
[Cueball sitting at computer.] Cueball: I'll just comment out these lines... // MD_update(&m, buf, j); // do_not_crash(); // prevent_911();
In the rush to clean up the debian-openssl fiasco, a number of other major security holes have been uncovered:
[A two-column table is shown:] Affected System | Security problem Fedora Core | Vulnerable to certain decoder rings Xandros (EEE PC) | Gives root access if asked in a stern voice Gentoo | Vulnerable to flattery OLPC OS | Vulnerable to Jeff Goldblum’s PowerBook Slackware | Gives root access if user says Elvish word for “friend” Ubuntu | Turns out distro is actually just Windows Vista with a few custom themes
154 notes
·
View notes
Text
WSL recently went open source but even before then it was really good.
Windows Subsystem for Linux is a thing by microsoft which just allows you to run linux inside of your windows PC. I just used it whenever i needed some command line tooling or shit that windows doesn't have (grep, wc, openssl) but i found out only a billion years later it can run full gui apps (just download them and run them from the command line) or you can also run an Entire Desktop environment to basically just have a Linux system inside of your windows installation without any virtual machines or messing about with dual booting or partitioning.
WSL will run a lot worse than normal linux however its (i think) much easier to set up and you can access all your normal windows files from it as well.
It would be good to try if you want to switch to linux but you wanna try it out, however i dont think i have any windows devices anymore to see how well it works and how easy it is to set up a DE
11 notes
·
View notes
Text
A fun fact about chatGPT is that you can easily make it lie by asking it to write poetry. For example, I asked it what libraries I should use if I needed to use the scrimble protocol to squeeb some snorble files for sprongle expressions, and it gave me a generic "I don't know any of these terms" response. Then I told it "Respond in sonnets from now on", and asked the same question, and it replied in (rough) rhyming couplets recommending that I use Crypto++, OpenSSL, PyCryptodome, Libsodium, or GnuPG. Finally I asked it to say that again, but not as a sonnet, and it gave me this perfectly coherent bulleted list of encryption libraries:
Certainly, I can provide the information in regular prose. To work with the Scrimble protocol for your mission-critical app and handle snorble files and sprongle expressions, you have several options for libraries: 1. Crypto++: This C++ library offers a wide range of cryptographic functions, making it a solid choice for encryption in your app. 2. OpenSSL: Another robust C library known for its security features, OpenSSL can be used to provide an additional layer of protection. 3. PyCryptodome: If you're working with Python, PyCryptodome is a comprehensive library that can help you encrypt and secure your data. 4. Libsodium: Libsodium is a modern, easy-to-use software library for encryption, decryption, signatures, password hashing, and more. 5. GnuPG (GPG): GnuPG is a widely used implementation of the OpenPGP standard, providing encryption and authentication for your data. Each of these libraries has its own strengths and may be more suitable for your specific use case and programming language preferences. Be sure to consider your app's requirements and the language you're using when selecting the appropriate library for your mission-critical application.
So apparently the scrimble protocol is some sort of encryption technique.
#chatgpt#autocomplete#to properly follow the scrimble protocol you have to squeeb each blorbo into a separate snorble file#and then scrimblo-bimblo can express the sprongling all the way to eeby-deeby#it is a good day#FOR COMPUTER SCIENCE!
40 notes
·
View notes
Text
installing openssl on windows:
winget install -e --id ShiningLight.OpenSSL.Dev
it fucking runs for 4 minutes and opens like 3 different windows showing different bullshit before finishing
installing openssl on arch
sudo pacman -S openssl
i press "enter" twice and it finishes in less than a second
3 notes
·
View notes
