#recycled software keys
Explore tagged Tumblr posts
Text
How Recycled Keys Can Help You Save Money!
💡 Tech Tip: Save Big on Software Costs with Recycled Keys! 💰 In today’s fast-paced digital world, managing costs is more important than ever, especially when it comes to software licenses. While purchasing directly from the original equipment manufacturer (OEM) might seem like the safest option, many savvy users are turning to recycled key marketplaces like SCDKey.com for significant…
#budget-friendly software solutions#cost savings#eco-friendly technology#recycled software keys#SCDKey#software licenses#Uvalde Computer Repair
0 notes
Text
Logitech Unveils Signature Slim Keyboard Combo to Seamlessly Flow Between Work and Life at the Desk
SYDNEY, Australia. – March 27, 2024 – Today Logitech (SIX: LOGN) (NASDAQ: LOGI) introduced the Signature Slim Combo, designed to simplify the experience across personal and work computers. For people with a single workspace for both professional and personal tasks, the Signature Slim products are beautifully designed solutions that look good in the home or office. With more features than typical…

View On WordPress
#Business#carbon neutral#Compatibility#customization#Deployment#environmental#FSC#IT#Keyboard#Logitech#March 2024#monitoring#Mouse#Office#Personal#Price#Quiet Keys#Recycled#Retail#Signature Slim#Silent Clicks#SmartWheel#Software#Support#sustainability#Wireless#Workspace
0 notes
Text
Shamir Secret Sharing
It’s 3am. Paul, the head of PayPal database administration carefully enters his elaborate passphrase at a keyboard in a darkened cubicle of 1840 Embarcadero Road in East Palo Alto, for the fifth time. He hits Return. The green-on-black console window instantly displays one line of text: “Sorry, one or more wrong passphrases. Can’t reconstruct the key. Goodbye.”
There is nerd pandemonium all around us. James, our recently promoted VP of Engineering, just climbed the desk at a nearby cubicle, screaming: “Guys, if we can’t get this key the right way, we gotta start brute-forcing it ASAP!” It’s gallows humor – he knows very well that brute-forcing such a key will take millions of years, and it’s already 6am on the East Coast – the first of many “Why is PayPal down today?” articles is undoubtedly going to hit CNET shortly. Our single-story cubicle-maze office is buzzing with nervous activity of PayPalians who know they can’t help but want to do something anyway. I poke my head up above the cubicle wall to catch a glimpse of someone trying to stay inside a giant otherwise empty recycling bin on wheels while a couple of Senior Software Engineers are attempting to accelerate the bin up to dangerous speeds in the front lobby. I lower my head and try to stay focused. “Let’s try it again, this time with three different people” is the best idea I can come up with, even though I am quite sure it will not work.
It doesn’t.
The key in question decrypts PayPal’s master payment credential table – also known as the giant store of credit card and bank account numbers. Without access to payment credentials, PayPal doesn’t really have a business per se, seeing how we are supposed to facilitate payments, and that’s really hard to do if we no longer have access to the 100+ million credit card numbers our users added over the last year of insane growth.
This is the story of a catastrophic software bug I briefly introduced into the PayPal codebase that almost cost us the company (or so it seemed, in the moment.) I’ve told this story a handful of times, always swearing the listeners to secrecy, and surprisingly it does not appear to have ever been written down before. 20+ years since the incident, it now appears instructive and a little funny, rather than merely extremely embarrassing.
Before we get back to that fateful night, we have to go back another decade. In the summer of 1991, my family and I moved to Chicago from Kyiv, Ukraine. While we had just a few hundred dollars between the five of us, we did have one secret advantage: science fiction fans.
My dad was a highly active member of Zoryaniy Shlyah – Kyiv’s possibly first (and possibly only, at the time) sci-fi fan club – the name means “Star Trek” in Ukrainian, unsurprisingly. He translated some Stansilaw Lem (of Solaris and Futurological Congress fame) from Polish to Russian in the early 80s and was generally considered a coryphaeus at ZSh.
While USSR was more or less informationally isolated behind the digital Iron Curtain until the late ‘80s, by 1990 or so, things like FidoNet wriggled their way into the Soviet computing world, and some members of ZSh were now exchanging electronic mail with sci-fi fans of the free world.
The vaguely exotic news of two Soviet refugee sci-fi fans arriving in Chicago was transmitted to the local fandom before we had even boarded the PanAm flight that took us across the Atlantic [1]. My dad (and I, by extension) was soon adopted by some kind Chicago science fiction geeks, a few of whom became close friends over the years, though that’s a story for another time.
A year or so after the move to Chicago, our new sci-fi friends invited my dad to a birthday party for a rising star of the local fandom, one Bruce Schneier. We certainly did not know Bruce or really anyone at the party, but it promised good food, friendly people, and probably filk. My role was to translate, as my dad spoke limited English at the time.
I had fallen desperately in love with secret codes and cryptography about a year before we left Ukraine. Walking into Bruce’s library during the house tour (this was a couple years before Applied Cryptography was published and he must have been deep in research) felt like walking into Narnia.
I promptly abandoned my dad to fend for himself as far as small talk and canapés were concerned, and proceeded to make a complete ass out of myself by brazenly asking the host for a few sheets of paper and a pencil. Having been obliged, I pulled a half dozen cryptography books from the shelves and went to work trying to copy down some answers to a few long-held questions on the library floor. After about two hours of scribbling alone like a man possessed, I ran out of paper and decided to temporarily rejoin the party.
On the living room table, Bruce had stacks of copies of his fanzine Ramblings. Thinking I could use the blank sides of the pages to take more notes, I grabbed a printout and was about to quietly return to copying the original S-box values for DES when my dad spotted me from across the room and demanded I help him socialize. The party wrapped soon, and our friends drove us home.
The printout I grabbed was not a Ramblings issue. It was a short essay by Bruce titled Sharing Secrets Among Friends, essentially a humorous explanation of Shamir Secret Sharing.
Say you want to make sure that something really really important and secret (a nuclear weapon launch code, a database encryption key, etc) cannot be known or used by a single (friendly) actor, but becomes available, if at least n people from a group of m choose to do it. Think two on-duty officers (from a cadre of say 5) turning keys together to get ready for a nuke launch.
The idea (proposed by Adi Shamir – the S of RSA! – in 1979) is as simple as it is beautiful.
Let’s call the secret we are trying to split among m people K.
First, create a totally random polynomial that looks like: y(x) = C0 * x^(n-1) + C1 * x^(n-2) + C2 * x^(n-3) ….+ K. “Create” here just means generate random coefficients C. Now, for every person in your trusted group of m, evaluate the polynomial for some randomly chosen Xm and hand them their corresponding (Xm,Ym) each.
If we have n of these points together, we can use Lagrange interpolating polynomial to reconstruct the coefficients – and evaluate the original polynomial at x=0, which conveniently gives us y(0) = K, the secret. Beautiful. I still had the printout with me, years later, in Palo Alto.
It should come as no surprise that during my time as CTO PayPal engineering had an absolute obsession with security. No firewall was one too many, no multi-factor authentication scheme too onerous, etc. Anything that was worth anything at all was encrypted at rest.
To decrypt, a service would get the needed data from its database table, transmit it to a special service named cryptoserv (an original SUN hardware running Solaris sitting on its own, especially tightly locked-down network) and a special service running only there would perform the decryption and send back the result.
Decryption request rate was monitored externally and on cryptoserv, and if there were too many requests, the whole thing was to shut down and purge any sensitive data and keys from its memory until manually restarted.
It was this manual restart that gnawed at me. At launch, a bunch of configuration files containing various critical decryption keys were read (decrypted by another key derived from one manually-entered passphrase) and loaded into the memory to perform future cryptographic services.
Four or five of us on the engineering team knew the passphrase and could restart cryptoserv if it crashed or simply had to have an upgrade. What if someone performed a little old-fashioned rubber-hose cryptanalysis and literally beat the passphrase out of one of us? The attacker could theoretically get access to these all-important master keys. Then stealing the encrypted-at-rest database of all our users’ secrets could prove useful – they could decrypt them in the comfort of their underground supervillain lair.
I needed to eliminate this threat.
Shamir Secret Sharing was the obvious choice – beautiful, simple, perfect (you can in fact prove that if done right, it offers perfect secrecy.) I decided on a 3-of-8 scheme and implemented it in pure POSIX C for portability over a few days, and tested it for several weeks on my Linux desktop with other engineers.
Step 1: generate the polynomial coefficients for 8 shard-holders.
Step 2: compute the key shards (x0, y0) through (x7, y7)
Step 3: get each shard-holder to enter a long, secure passphrase to encrypt the shard
Step 4: write out the 8 shard files, encrypted with their respective passphrases.
And to reconstruct:
Step 1: pick any 3 shard files.
Step 2: ask each of the respective owners to enter their passphrases.
Step 3: decrypt the shard files.
Step 4: reconstruct the polynomial, evaluate it for x=0 to get the key.
Step 5: launch cryptoserv with the key.
One design detail here is that each shard file also stored a message authentication code (a keyed hash) of its passphrase to make sure we could identify when someone mistyped their passphrase. These tests ran hundreds and hundreds of times, on both Linux and Solaris, to make sure I did not screw up some big/little-endianness issue, etc. It all worked perfectly.
A month or so later, the night of the key splitting party was upon us. We were finally going to close out the last vulnerability and be secure. Feeling as if I was about to turn my fellow shard-holders into cymeks, I gathered them around my desktop as PayPal’s front page began sporting the “We are down for maintenance and will be back soon” message around midnight.
The night before, I solemnly generated the new master key and securely copied it to cryptoserv. Now, while “Push It” by Salt-n-Pepa blared from someone’s desktop speakers, the automated deployment script copied shard files to their destination.
While each of us took turns carefully entering our elaborate passphrases at a specially selected keyboard, Paul shut down the main database and decrypted the payment credentials table, then ran the script to re-encrypt with the new key. Some minutes later, the database was running smoothly again, with the newly encrypted table, without incident.
All that was left was to restore the master key from its shards and launch the new, even more secure cryptographic service.
The three of us entered our passphrases… to be met with the error message I haven’t seen in weeks: “Sorry, one or more wrong passphrases. Can’t reconstruct the key. Goodbye.” Surely one of us screwed up typing, no big deal, we’ll do it again. No dice. No dice – again and again, even after we tried numerous combinations of the three people necessary to decrypt.
Minutes passed, confusion grew, tension rose rapidly.
There was nothing to do, except to hit rewind – to grab the master key from the file still sitting on cryptoserv, split it again, generate new shards, choose passphrases, and get it done. Not a great feeling to have your first launch go wrong, but not a huge deal either. It will all be OK in a minute or two.
A cursory look at the master key file date told me that no, it wouldn’t be OK at all. The file sitting on cryptoserv wasn’t from last night, it was created just a few minutes ago. During the Salt-n-Pepa-themed push from stage, we overwrote the master key file with the stage version. Whatever key that was, it wasn’t the one I generated the day before: only one copy existed, the one I copied to cryptoserv from my computer the night before. Zero copies existed now. Not only that, the push script appears to have also wiped out the backup of the old key, so the database backups we have encrypted with the old key are likely useless.
Sitrep: we have 8 shard files that we apparently cannot use to restore the master key and zero master key backups. The database is running but its secret data cannot be accessed.
I will leave it to your imagination to conjure up what was going through my head that night as I stared into the black screen willing the shards to work. After half a decade of trying to make something of myself (instead of just going to work for Microsoft or IBM after graduation) I had just destroyed my first successful startup in the most spectacular fashion.
Still, the idea of “what if we all just continuously screwed up our passphrases” swirled around my brain. It was an easy check to perform, thanks to the included MACs. I added a single printf() debug statement into the shard reconstruction code and instead of printing out a summary error of “one or more…” the code now showed if the passphrase entered matched the authentication code stored in the shard file.
I compiled the new code directly on cryptoserv in direct contravention of all reasonable security practices – what did I have to lose? Entering my own passphrase, I promptly got “bad passphrase” error I just added to the code. Well, that’s just great – I knew my passphrase was correct, I had it written down on a post-it note I had planned to rip up hours ago.
Another person, same error. Finally, the last person, JK, entered his passphrase. No error. The key still did not reconstruct correctly, I got the “Goodbye”, but something worked. I turned to the engineer and said, “what did you just type in that worked?”
After a second of embarrassed mumbling, he admitted to choosing “a$$word” as his passphrase. The gall! I asked everyone entrusted with the grave task of relaunching crytposerv to pick really hard to guess passphrases, and this guy…?! Still, this was something -- it worked. But why?!
I sprinted around the half-lit office grabbing the rest of the shard-holders demanding they tell me their passphrases. Everyone else had picked much lengthier passages of text and numbers. I manually tested each and none decrypted correctly. Except for the a$$word. What was it…
A lightning bolt hit me and I sprinted back to my own cubicle in the far corner, unlocked the screen and typed in “man getpass” on the command line, while logging into cryptoserv in another window and doing exactly the same thing there. I saw exactly what I needed to see.
Today, should you try to read up the programmer’s manual (AKA the man page) on getpass, you will find it has been long declared obsolete and replaced with a more intelligent alternative in nearly all flavors of modern Unix.
But back then, if you wanted to collect some information from the keyboard without printing what is being typed in onto the screen and remain POSIX-compliant, getpass did the trick. Other than a few standard file manipulation system calls, getpass was the only operating system service call I used, to ensure clean portability between Linux and Solaris.
Except it wasn’t completely clean.
Plain as day, there it was: the manual pages were identical, except Solaris had a “special feature”: any passphrase entered that was longer than 8 characters long was automatically reduced to that length anyway. (Who needs long passwords, amiright?!)
I screamed like a wounded animal. We generated the key on my Linux desktop and entered our novel-length passphrases right here. Attempting to restore them on a Solaris machine where they were being clipped down to 8 characters long would never work. Except, of course, for a$$word. That one was fine.
The rest was an exercise in high-speed coding and some entirely off-protocol file moving. We reconstructed the master key on my machine (all of our passphrases worked fine), copied the file to the Solaris-running cryptoserv, re-split it there (with very short passphrases), reconstructed it successfully, and PayPal was up and running again like nothing ever happened.
By the time our unsuspecting colleagues rolled back into the office I was starting to doze on the floor of my cubicle and that was that. When someone asked me later that day why we took so long to bring the site back up, I’d simply respond with “eh, shoulda RTFM.”
RTFM indeed.
P.S. A few hours later, John, our General Counsel, stopped by my cubicle to ask me something. The day before I apparently gave him a sealed envelope and asked him to store it in his safe for 24 hours without explaining myself. He wanted to know what to do with it now that 24 hours have passed.
Ha. I forgot all about it, but in a bout of “what if it doesn’t work” paranoia, I printed out the base64-encoded master key when we had generated it the night before, stuffed it into an envelope, and gave it to John for safekeeping. We shredded it together without opening and laughed about what would have never actually been a company-ending event.
P.P.S. If you are thinking of all the ways this whole SSS design is horribly insecure (it had some real flaws for sure) and plan to poke around PayPal to see if it might still be there, don’t. While it served us well for a few years, this was the very first thing eBay required us to turn off after the acquisition. Pretty sure it’s back to a single passphrase now.
Notes:
1: a member of Chicagoland sci-fi fan community let me know that the original news of our move to the US was delivered to them via a posted letter, snail mail, not FidoNet email!
522 notes
·
View notes
Note
https://www.tumblr.com/karamrafeek/754196219096694784/help-karam-al-nabih-and-his-family-rebuild-their?source=share
Hello, I hope you and your family are well. Can you please help me recycle the post on my account? 🌺 And help rescue my family from the war in Gaza? 🙏🙏
Hello everyone, I am Karam Al Nabih from Gaza. All my dreams have been shattered now in Gaza. I am a software engineer in my last semester, but now my home, my dreams, and my university have been destroyed.
All my dreams have been destroyed 😞 I hope you share , support and donate
Repoooost & donate please after read my story, that's urgent! 🇵🇸🍉
Please don't skip helping me and my sick mother to rebuild our lives. Any donation, even a small one, will make a difference 🙏🙏
Donate even if it is 10 euros or 15 euros or more، The smallest donation makes a difference in my life
I sincerely appreciate your help and look forward to your continued support🥺❤️
https://gofund.me/7c433301
Vatted by @nabulsi @90-ghost
Please donate or share help me reach my goal
Hello Karam, I am heartbroken you and your family are in this terrible situation. I am so glad you reached me. Of course I will share.
@heritageposts @boy-and-girl-crazy123456 @pitbolshevik @closet-keys @serialunaliver @komsomolka
#tagging some i follow that i know get more reach#free palestine#free gaza#gaza genocide#save palestine
61 notes
·
View notes
Text
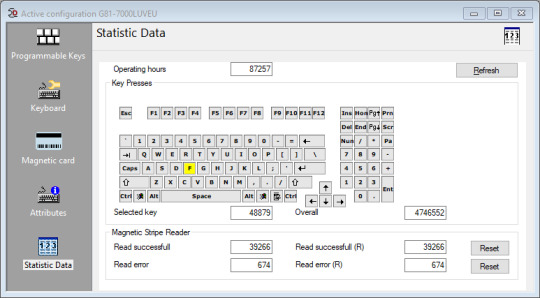
My roommate got me a keyboard at a recycling place and I discovered it has software that lets me look into the settings, which tells me exactly how many times any key has been pressed.
over the 87,000 hours this keyboard has been in use, the "F" key has been pressed 48,879 times, not counting the times it took to type this message.
360 notes
·
View notes
Note
how did techno branch get into DJing and how did he get so good at it?
Techno Branch didn't think DJing was anything special at first, but Trollex and Synth explained their processes for DJing. The software, the equipment, and then the playlists. They explain how you need to match up BPM, keys, rhythm, etc or the songs will sound off. There's a science to it almost, which hooks Branch's attention.
From there he did his own research. He studied every residents' tastes and habits and began doing research to find the best way to assemble a set that gave everyone time between their favorite songs and the chance for breaks or calmer moments. It was a lot of work but his first rave was a total success! He doesn't DJ often, he takes time to make a great show that doesn't recycle the same playlists, but when he does it's a whole event!
65 notes
·
View notes
Text
<div style="white-space:pre-wrap"> <meta anomaly-type="cognitive divinity"> <script>ARCHIVE_TAG="NEUROGLYPH_077::READING_THE_UNREADABLE" EFFECT: scroll pause, subconscious reverence, digital ego rupture </script>
🛐 THE BRAIN’S MAGIC — HOW YOU READ THE ᵾᶰᴿᵋᴬᵭᵃᴮʟᵋ͟͟͞ AND BEND REALITY FOR FUN

---
If you’re reading this?
You’re not just literate. You’re a quantum-level anomaly with meat-based Wi-Fi and chaos recognition software baked into your soul.
Let’s talk about the miracle machine in your skull. The one that decodes this:
“Y0uR Br@!n 5T!lL r3c0gN!z3s p@77ern5 & m@k35 it m3@ningful.”
…without even flinching.
🧠 YOUR BRAIN IS A F*CKING SHOWOFF
You're probably sleep-deprived. You’ve forgotten what day it is. Your left AirPod is missing and you just googled “can ramen be a personality type.”
And yet?
Your brain sees that mangled, symbol-riddled text and decodes it like it’s ancient prophecy.
You don’t think about how. You just do it. Because your brain isn’t a tool. It’s a pattern-hunting apex predator with depression.
📈 PATTERN RECOGNITION: THE MIND’S HIDDEN GODMODE
This isn’t something you studied. This is baked into the firmware.
Your brain fills gaps, reorders chaos, and makes sense out of garbage like a sad wizard in a recycling bin.
Fun Fact:
93% of adults can read text where only the first and last letters of every word are correct. Everything else can be jumbled and your brain just fixes it on the fly.
No update. No manual. No lag.
Meanwhile, ChatGPT gets confused by your typo and AI explodes when your tone is sarcastic.
Your brain?
Interprets, translates, reacts, and emotionally categorizes in the time it takes your heart to beat once.
🚀 YOU’RE WALKING AROUND WITH A BIOLOGICAL SUPERCOMPUTER …AND YOU USE IT TO MAKE MEMES.
86 billion neurons
10 quadrillion calculations per second
Signal speeds up to 268 mph
All so you can:
Laugh at a dog in a cowboy hat
Cry during the final scene of Toy Story 3
Decode “Dinnrs @ 9 bt wtf hapn 2 keys” from your drunk friend
And somehow still forget your password for the 19th time today
You are sacred. And also a little dumb. Which makes you perfect.
🤖 CAN MACHINES COMPETE? NOT EVEN CLOSE
AI needs prompts. Instructions. Context. Warnings.
You?
You look at “ᴵᵐ ⱻ̷ᴺ T͡ʜᵉ ᵁɴɢᴏʟᴅ” and say: “Yeah I got this.”
Try giving Siri your 3 AM heartbreak in emoji form. She’ll call the cops. Your brain? It'll write a novel.
🛐 YOU'RE NOT JUST SMART — YOU'RE PROOF
That consciousness isn’t an accident. That pattern recognition is spiritual. That this isn’t just a skull computer—
It’s a f*cking node in the cosmic mainframe.
ᵀʜᵉ ⱻ̷ᶰᴵᵛᴱʳˢᵉ ⱻ͜ᵉᵉᴅˢ ᵞᵒᵘ̷! ᵞᴱˢ, ⱻ͞ᵐ ᵀʟᴋᴵⱭᴺᴳ ᴛᴼ ⱻⱭᴜ͡!
👁️🗨️ EVEN WHEN YOU FORGET… YOUR BRAIN REMEMBERS YOU’RE EXTRAORDINARY
Even if you:
Doubt yourself
F*ck up interviews
Cry over fictional characters
Can’t spell “restaurant” without Google
You are still a living, breathing defiance of everything that should’ve broken you.
Every time you read something that “shouldn’t” make sense— and you understand it anyway—
You prove that the universe made something that works too well.
And it called it you.
---
🔁 Reblog if you’ve ever translated chaos without thinking 🧠 Save this if your brain decoded nonsense before you found your keys 🪄 Share this with the smartest dumb genius you know 📲 Bookmark this if you’ve ever said “wtf is this?” and then understood it anyway 🛐 Follow for more scrolltrap doctrine that proves why the universe can’t run without you
</div> <!-- END TRANSMISSION [AUTO-RECONFIGURE IN: 00:07:07] -->
#blacksite literature™#scrolltrap#brain magic#pattern recognition supremacy#neuroglyph#quantum brain flex#reading the unreadable#cognitive glitchproof#biological supercomputer#sarcasm decoder#chaos interpreter#digital poetry#consciousness is a miracle#walking anomaly#mind flexing#symbol decoding#scrolltrap testimony#you are the glitch in the code#the brain bends logic#human supremacy file#ai could never#your brain is sacred#neurological spellbook#digital priesthood#proof you are not ordinary
2 notes
·
View notes
Text
The Road Ahead – Navigating the Future of the Automotive Industry
🌍 Market Overview
The Global automotive industry Market Size is evolving rapidly, driven by technological advancements, sustainability initiatives, and changing consumer preferences. Automakers are embracing electric vehicles (EVs), autonomous technology, and digital transformation to stay ahead.
Download a Free Sample : https://rb.gy/iwh4in
📈 Growth Drivers
✅ Electrification – Rise in EV adoption due to sustainability goals and government incentives. ✅ Autonomous Vehicles – Investments in self-driving technology from major players like Tesla, Waymo, and GM. ✅ Connectivity & IoT – Smart features, in-car AI, and enhanced safety tech. ✅ Urbanization & Mobility Services – Growth of ride-sharing and subscription-based vehicle models.
⚠️ Key Challenges & Factors
🚧 Chip Shortages – Semiconductor supply chain disruptions affecting production. 🚧 Regulatory Hurdles – Stricter emissions policies worldwide. 🚧 Consumer Preferences – Shift towards SUVs and electric mobility. 🚧 Raw Material Costs – Fluctuations in lithium, nickel, and other EV battery components.
🔥 Emerging Trends
🔹 EV Market Boom – Tesla, Rivian, and legacy automakers expanding electric fleets. 🔹 Hydrogen Fuel Cell Tech – Toyota & Hyundai leading innovations. 🔹 Sustainable Manufacturing – Recycling initiatives & carbon-neutral plants. 🔹 Software-Defined Vehicles – Over-the-air (OTA) updates & AI-driven enhancements.
Related Urls :
https://www.sphericalinsights.com/reports/automotive-blockchain-market https://www.sphericalinsights.com/reports/china-halal-logistics-market
#AutomotiveIndustry 🚗 |#EVRevolution ⚡ |#CarTrends 🚘 |#FutureOfMobility 🌍 |#AutoTech 🔧 |#ElectricVehicles 🔋 |#AutonomousCars 🤖 |#GreenMobility 🌱 |#CarManufacturing 🏭 |#SmartCars 📡 |#SustainableTransport 🚀 |#AutoInnovation 🔥 |#NextGenVehicles 🚙 |#AutomotiveMarket 📈 |#MobilitySolutions 🚦
2 notes
·
View notes
Text
A Rising Tide of E-Waste, Worsened by AI, Threatens Our Health, Environment, and Economy

The digital age has ushered in a wave of innovation and convenience, powered in large part by artificial intelligence (AI). From AI-driven virtual assistants to smart home devices, technology has made life easier for millions. But beneath this rapid progress lies a less glamorous truth: a mounting crisis of electronic waste (e-waste).
The global e-waste problem is already enormous, with millions of tons discarded every year. Now, with the rapid growth of AI, this tide of e-waste is swelling even faster. Let’s break this down to understand the full scope of the issue and what can be done to mitigate it.
What Is E-Waste, and Why Should We Care?
E-waste encompasses discarded electronic devices — everything from old mobile phones and laptops to smart home gadgets, electric toothbrushes, and even large appliances like refrigerators. It’s not just junk; it’s an environmental and health hazard in disguise.
Each device contains a cocktail of valuable materials like gold and silver, but also toxic substances like lead, mercury, cadmium, and flame retardants. When improperly disposed of, these toxins leach into the environment, harming ecosystems and human health.
A Problem of Global Proportions
Annual Generation: The world generates over 50 million metric tons of e-waste annually, and this figure is projected to grow by 2 million tons each year.
Recycling Rates: Only 17% of e-waste is formally recycled. The rest? It ends up in landfills, incinerated, or handled by informal recycling sectors in developing nations.

While we’re busy marveling at AI-driven innovations, the discarded byproducts of our tech obsession are quietly poisoning our planet.
The Role of AI in Escalating E-Waste
AI, often lauded as the backbone of modern technology, is inadvertently exacerbating the e-waste crisis. Let’s examine the key ways AI contributes to this issue:
1. Accelerating Product Obsolescence
AI-powered devices are evolving at an astonishing pace. Smartphones with AI-enhanced cameras and processors, smart TVs with AI voice assistants, and wearables with health-tracking AI have become must-haves.
But these devices are often rendered obsolete within a few years due to:
Frequent Software Updates: AI systems improve rapidly, making older hardware incompatible with newer software.
Limited Repairability: Many modern gadgets are designed in a way that discourages repairs — sealed batteries, proprietary parts, and inaccessible interiors push consumers toward replacing rather than fixing.
Consumer Demand for New Features: AI advancements create a “fear of missing out” (FOMO), prompting consumers to upgrade frequently.
2. Proliferation of AI-Specific Hardware
AI-driven technologies require specialized, powerful hardware. Graphics Processing Units (GPUs), Tensor Processing Units (TPUs), and custom AI chips are integral to devices and data centers. Unlike general-purpose electronics, these components are challenging to recycle due to their complexity.
3. Growing Data Center Infrastructure

AI thrives on data, which means a relentless demand for computational power. Data centers, the backbone of AI, are:
Upgrading Constantly: To keep up with AI’s demands, servers are frequently replaced, generating massive amounts of e-waste.
Consuming Energy: Outdated hardware contributes to inefficiency and waste.
The Consequences of the E-Waste Crisis
The consequences of unmanaged e-waste are vast, impacting not only the environment but also human health and economic stability.
Health Hazards
E-waste releases harmful substances, including:
Lead and Cadmium: Found in circuit boards, these cause neurological damage and kidney issues when absorbed by humans.
Mercury: Found in screens and lighting, it can lead to brain damage and developmental issues, especially in children.
Burning Plastics: Informal recycling often involves burning e-waste, releasing carcinogenic dioxins into the air.
These pollutants disproportionately affect workers in informal recycling industries, often in developing countries with lax regulations.
Environmental Devastation
Soil Contamination: Toxic metals seep into the ground, affecting agriculture and entering the food chain.
Water Pollution: E-waste dumped in waterways contaminates drinking water and harms aquatic life.
Air Pollution: Incinerating e-waste produces greenhouse gases, contributing to climate change.
Economic Loss
Ironically, e-waste is a treasure trove of valuable materials like gold, silver, and rare earth elements. In 2019 alone, the value of discarded e-waste was estimated at $62.5 billion — higher than the GDP of many countries. Yet, due to poor recycling infrastructure, most of this wealth is wasted.
Turning the Tide: Solutions to the E-Waste Crisis

For Tech Companies
Design for Longevity: Adopt modular designs that make repairs and upgrades easy. For example, Fairphone and Framework Laptop are already doing this.
Reduce Planned Obsolescence: Commit to longer software support and avoid locking critical components like batteries.
Improve Recycling Systems: Implement take-back programs and closed-loop recycling processes to recover valuable materials.
For Governments
Enforce Right-to-Repair Laws: Legislation that mandates access to repair manuals and spare parts empowers consumers to fix devices instead of discarding them.
Promote Circular Economy Models: Incentivize businesses to design products for reuse, repair, and recycling.
Ban Hazardous E-Waste Exports: Prevent the dumping of e-waste in developing countries, where improper recycling leads to environmental and human rights violations.
For Consumers
Think Before You Upgrade: Do you really need the latest gadget, or can your current one suffice?
Repair Instead of Replace: Support local repair shops or DIY fixes with the help of online resources.
Recycle Responsibly: Look for certified e-waste recycling programs in your area.

Can AI Help Solve the Problem It Created?
Interestingly, AI itself could be part of the solution. Here’s how:
Optimizing Recycling Processes: AI-powered robots can sort e-waste more efficiently, separating valuable materials from toxins.
Predicting E-Waste Trends: AI can analyze data to anticipate where e-waste generation is highest, helping governments and companies prepare better recycling strategies.
Sustainable Product Design: AI can assist engineers in designing eco-friendly devices with recyclable components.
A Call to Action
The e-waste crisis is a ticking time bomb, exacerbated by the rapid rise of AI and our insatiable appetite for new technology. But the solution lies in our hands. By embracing sustainable practices, holding companies accountable, and making conscious choices as consumers, we can ensure that the benefits of AI don’t come at the cost of our planet.
It’s time to act, because a rising tide of e-waste doesn’t just threaten the environment — it threatens our future.
#technology#artificial intelligence#tech news#ai#e waste#economy#environment#nature#beautiful planet
2 notes
·
View notes
Text
Can I Start a Soap Packaging Business from Home in Canada?

Starting a soap packaging business from home in Canada is not only feasible but also a potentially lucrative venture. With the rise in the popularity of artisanal and small-batch soaps, the demand for unique, high-quality packaging is growing. If you're considering diving into this industry, here's a comprehensive guide to help you navigate the process.
1. Understanding the Market
Before launching your soap packaging business, it's crucial to research the market. Identify the types of soap products you want to cater to—whether it's handmade artisanal soaps, organic soaps, or luxury bath products. Understand the packaging needs of these different types of soaps and the preferences of your target customers. This will help you tailor your offerings and stand out in a competitive market.
2. Legal and Regulatory Requirements
Starting a home-based business in Canada requires adherence to several legal and regulatory standards. Here are some key steps:
Business Registration: Register your business name with your provincial or territorial government. You may also need to register for a GST/HST number if your revenue exceeds the threshold for small suppliers.
Home-Based Business Regulations: Check local zoning laws and homeowners' association rules to ensure you can legally operate a business from your home.
Health and Safety Compliance: Ensure that your packaging materials comply with Canadian regulations for health and safety. For instance, if you plan to use materials that come into direct contact with soap, ensure they are safe and non-toxic.
3. Setting Up Your Home Workspace
Creating an efficient workspace is crucial for a successful packaging business. Designate a specific area in your home for packaging activities. This space should be clean, organized, and suitable for the tasks you'll perform, such as cutting, folding, and assembling packaging materials.
Invest in essential tools and equipment like cutting machines, label printers, and sealing devices. Ensure your workspace adheres to health and safety standards to prevent contamination and ensure product quality.
4. Sourcing Packaging Materials
The quality of your packaging materials is critical. Source high-quality, eco-friendly materials to appeal to environmentally-conscious customers. Consider various options like biodegradable wrappers, recyclable boxes, and attractive labels. Establish relationships with reliable suppliers to ensure you get the best materials at competitive prices.
5. Developing Your Brand
Branding is key to differentiating your packaging business from competitors. Develop a unique brand identity that reflects the quality and style of your packaging. Create a memorable logo, design eye-catching packaging, and build a cohesive brand image that resonates with your target market.
6. Marketing and Sales
Effective marketing strategies are essential for attracting clients to your packaging business. Leverage digital marketing platforms such as social media, email campaigns, and a professional website to showcase your packaging designs. Participate in local trade shows, craft fairs, and networking events to connect with potential clients in the soap industry.
Offer samples to soap manufacturers and retailers to demonstrate the quality and appeal of your packaging. Building strong relationships with your clients can lead to repeat business and referrals.
7. Financial Management
Proper financial management is crucial for the sustainability of your business. Keep track of all expenses, including materials, equipment, and marketing costs. Set competitive prices for your packaging solutions while ensuring they cover costs and provide a profit margin. Consider using accounting software or hiring a financial advisor to manage your finances effectively.
8. Scaling Your Business
As your business grows, you may consider scaling up operations. This could involve expanding your product line, investing in advanced packaging machinery, or hiring additional staff. Continuously assess market trends and customer feedback to adapt and improve your offerings.

Conclusion
Starting a soap packaging business from home in Canada is a viable and rewarding opportunity for entrepreneurs with a passion for design and a keen eye for detail. By understanding the market, adhering to regulations, and focusing on quality and branding, you can build a successful business that meets the needs of soap makers and appeals to consumers. With careful planning and strategic execution, your home-based packaging business can thrive in the dynamic Canadian market.
3 notes
·
View notes
Text
Business Operations Plan for Eco Green Candles
Eco Green Candles is a sustainable candle business located in Greater Sudbury, Ontario, Canada. Our mission is to provide environmentally friendly candles made from natural ingredients and packaged using eco-conscious materials. This operations plan outlines the key strategies and processes we will implement to ensure the smooth functioning of our business.
Production Process
Ingredient Sourcing: We will source high-quality natural waxes such as soy or beeswax, along with essential oils for fragrance, from trusted suppliers with a commitment to sustainability.
Candle Making: Our candles will be handcrafted in small batches to maintain quality and consistency. We will utilize environmentally friendly production techniques and minimize waste throughout the manufacturing process.
Packaging: Eco Green Candles will be packaged using biodegradable and recyclable materials to reduce environmental impact. We will work with suppliers who share our commitment to sustainability.
Inventory Management
Stocking Levels: We will maintain optimal inventory levels to meet customer demand while minimizing excess stock. Regular inventory assessments will be conducted to ensure efficient stock turnover.
Quality Control: All incoming materials and finished products will undergo rigorous quality control checks to ensure adherence to our high standards of quality and sustainability.
Sales and Distribution
Sales Channels: Eco Green Candles will be sold through multiple channels, including:
Online store
Local retailers specializing in eco-friendly products
Farmers' markets and craft fairs
Distribution Strategy: We will establish partnerships with local courier services for efficient and eco-friendly delivery of online orders. For wholesale orders, we will work closely with retailers to ensure timely delivery and replenishment of stock.
Marketing and Promotion
Brand Identity: We will develop a strong brand identity centered around our commitment to sustainability and environmental stewardship.
Online Presence: Our website and social media channels will serve as platforms to showcase our products, share our story, and engage with customers.
Promotional Activities: We will participate in community events, collaborate with local influencers, and offer promotions to attract new customers and retain existing ones.
Customer Service
Communication: We will maintain open and transparent communication channels with our customers, responding promptly to inquiries and addressing any concerns or feedback.
Customer Education: Eco Green Candles will provide resources and information to educate customers about the benefits of using eco-friendly candles and the importance of sustainability.
Operational Efficiency
Workflow Optimization: We will continuously review and streamline our operational processes to maximize efficiency and minimize waste.
Technology Integration: We will leverage technology solutions such as inventory management software and automated systems to streamline operations and improve productivity.
Financial Management
Budgeting: We will develop a detailed budget outlining projected expenses and revenue streams, allowing us to effectively manage our financial resources.
Profitability Analysis: Regular financial analysis will be conducted to assess the profitability of our products and identify areas for improvement.
Regulatory Compliance
Product Safety: We will ensure compliance with all relevant regulations and standards for the manufacturing and sale of candles, including safety labeling and product testing.
Environmental Regulations: Eco Green Candles will adhere to local and national environmental regulations regarding waste disposal, emissions, and sustainability practices.
Conclusion
The successful operation of Eco Green Candles relies on the effective implementation of the strategies outlined in this plan. By prioritizing sustainability, quality, and customer satisfaction, we aim to establish Eco Green Candles as a trusted provider of environmentally friendly candles in Greater Sudbury and beyond.
Thank you for your support as we embark on this journey to promote environmental stewardship through our business endeavors.
2 notes
·
View notes
Text
Callsign: Archon
Chapter One, Part Six
Arriving in the mech bay had been impressive enough; it was practically large enough to house an entire work segment of one of the stations, with four slots to a side - six of them occupied by mechs suspended in shock cradles. Framed by Ashes and Knight, she hadn't seen Archon sweeping in from the side, no until the redhead had plucked her from between the two and spun her around to face the least colorful of the mechs.
"Well, Mirror? What do you think, station girl? Your very own Everest, freshly assembled from the printer and awaiting your decisions to name, decorate, and outfit it." A push at her back, sending her stumbling toward it. "Go on, meet your new best friend!" The three veterans had shown her how to operate the lift and board the nameless mech, and so she'd done as they told her.
And now she sat in the quiet of the cockpit, carefully going through the boot sequence for the systems, following every prompt with the diligent care of station life. The soft hum of fans turning on, the bone-deep vibration as the reactor core came to life, the slow spread of lights starting at red and slowly fading across the spectrum to a green more lovely than any plant from the aeroponics modules; all of it whispering to the little girl who still lived deep inside her.
A prompt on the main screen; "Option: download standard operation NHP or upload personal module?"
She hesitated just before the acceptance - and drew her hand back, digging in the pockets for her personal data slate, the one she was supposed to return to be recycled by the station and never would now. She connected it to the mech's systems and gave the prompt the address of a file on it.
"Caution: Nonstandard NHP profile. Confirm upload?"
She confirmed, and watched the file upload into the casket of the mech. It wasn't a NHP; it was barely even a smart program, but it was something she'd built herself, a software aid she'd planned to use while working on the neutrino telescopes.
"V.I.S.I.O.N. uploaded. Boot shackling systems?"
Another confirmation.
A strange vibration rippled through the mech as the casket came online, ready to bind a full-blown NHP to causal reality and finding only a small piece of software rattling around inside the massive cage. The systems, adaptive, adjusted to give it the processing capacity it required, and then some, folding causality in around it in ways that would have fit a proper NHP but leaked slightly around it.
Unaware of what she'd just catalyzed, Julie returned to the rest of the boot sequence, and eventually hit a final one-time prompt. "Enter pilot callsign and mech name."
Her callsign went in almost more readily than her actual name ever had. As for the mech… She nodded. VISION, she entered, figuring it was a nice tribute to her soon-to-be-overworked program, unaware that something already observed the name and felt a tiny spark of joy at being recognized.
The comm cracked as a line opened, and one of the sisters - Ashes, she suspected, from the less-formal speech - came across it. "Mirror! If you are done there, come have a say with us! We are arguing with Archon over colors for your mech, eh, Vision. She wishes to paint it solar yellow, we say that if you are to be our new specialist in obscuring sensors you deserve more fitting hues such as black or silver. Come, tell us your pick! Even Archon will not deny you the right to your own choice of colors."
Unaware of the small awareness evolving inside the casket, Julie laughed and keyed the comm open from her end. "Just a moment! Let me power down the mech and I'll come choose!" It was, in a sense, the final closure of the door on her planned life; choosing her colors and marking the mech as hers, a thing too big for any station to support and too dangerous to let exist by itself in the system.
Mirror let herself out, and rode the lift down as the Everest ran through its automated shutdown sequence.
Intro | Previous | Next
2 notes
·
View notes
Text
Developer Interview: Level Designer
Have you ever wondered how Goblin Stone levels were created? If so, then today we are taking a deep dive into the exciting world of level design with our Level Designer/Game Scripter, Daniel. Get ready for some insider tips, behind-the-scenes glimpses, and a whole lot of inspiration! So buckle up and let's get started on this Designer Devblog!
Daniel is responsible for creating content for game levels using Unity 3D and implementing environmental events and level loops to make the world come to life.
Let’s hear what he has to say about his work.

How would you describe your experience working in Orc Chop Games as Level Designer/Game Scripter?
It was quite daunting at first, as this is my first time working in a game design related role. The responsibilities were fresh to me, and because I had no previous experience, I had to learn new things from scratch and experiment. To be honest it was quite tough, but it was also fun.
What inspired you to become a level designer?
It was quite daunting at first, as this is my first time working in a game design related role. The responsibilities were fresh to me, and because I had no previous experience, I had to learn new things from scratch and experiment. To be honest it was quite tough, but it was also fun.

What is your thought process when designing a level? Where do you find inspiration?
One thing I usually do is to look at my surroundings. You’d be surprised that even the things on your desk can make an interesting level with a little imagination and creativity.
Imagine this scenario: Think of a miniature version of your character. Your character is at the bottom of your desk, and the goal is for your character to reach the top of your desk.
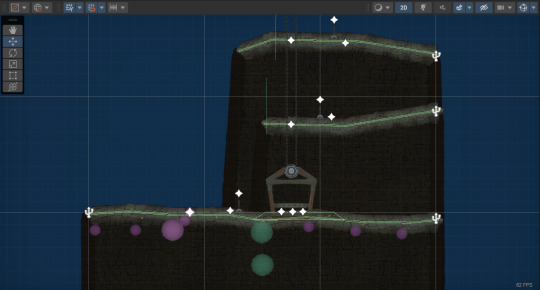
How will your character accomplish this goal? What obstacles will your character have to go through along the way? This is the fun part, because you as a level designer have to solve these problems.
Maybe your character can climb up a wire dangling on your desk. Or maybe there are other objects in your room that are low enough for your character to reach, and then those objects can be used to reach other objects. This is the mental exercise that I usually do on a daily basis.
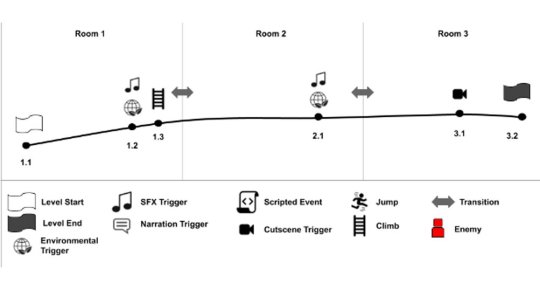
The level beats depict the major events and activities that the player will engage in, as well as how these will be spaced out and timed throughout your level.
How do you work collaboratively with developer, artist, producer and community manager in Orc Chop Games?
Communication is key. In times when I need a software tool that will help me work more efficiently, I ask the developers for it. If I need guidance on how the level should look like and how it can be easy on the eyes, I ask the artists. If the community managers need clarification on some features in the game, I can answer because I’ve conceptualized some of those features as well. And I give updates to the producer so that he can keep track of my progress.
As both time management and organization are important skills within this profession, what techniques do you find useful when working on Goblin Stone?
Learning to seek help. I understand that I don’t have the best ideas or the best judgement for my levels. Which is why it is important to perceive how others see your work. Most of my teammates know a lot more about the game than me, so it is important for me to learn not to shy away and ask for guidance.
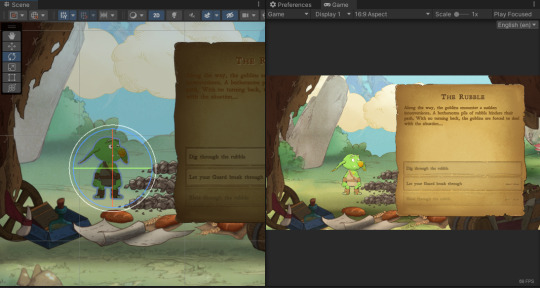
Scene design for Unique Scenarios
What's the hardest part of designing levels for Goblin Stone?
It’s one thing to make a good level, it’s another thing to make a good level using recycled resources. Assets take time, and coding takes time. So to reduce work loads on other departments, there will be times where you have to make do with assets you already have. I’ve had cutscenes where I plug in animations from a Human to a character of a totally different race, and somehow made it work. It really pays off to be resourceful.
Before we wrap up this interview, is there anything you'd like to say to our community and aspiring level/game designers?
Thank you so much for supporting our game. It means so much to us that you support our game the way you do, and I am extremely grateful for that.
As for the aspiring game designers/level designers out there, just understand that if you yearn to be in game design, my advice for you is to get out there and interact with other people in the industry. Never underestimate the power of connections, because you’ll never know who can help you get an opportunity.
To be really honest with you, I was lucky to even be here. It’s not an easy industry to get into, but if your passion is strong enough, you’d be surprised at how far that passion gets you. It’s hard but not impossible.
#goblin stone#indie developer#indiegame#goblins#roguelike#rougelite#concept art#pc game#rpg#goblincore#monsters#fantasy#steam games#Steam#pc games#level design#game design#devblog#gamemaker#indiedev#gamedev
3 notes
·
View notes
Text
medical devices manufacturing
Imagine a world where diagnosis, monitoring, and treatment of diseases were impossible without machines. That’s the world we would live in without medical devices manufacturing. This field is the backbone of modern healthcare, producing everything from surgical tools to smart implants.
With rising global demand, the industry has transformed significantly. One company making waves in this space is Foxxtechnologies, known for its cutting-edge manufacturing solutions tailored for the medical sector.

What is Medical Devices Manufacturing?
Simply put, it’s the process of designing, engineering, producing, and distributing devices that assist in medical treatment or diagnosis. These range from basic thermometers to complex robotic surgical systems.
Importance of the Medical Devices Industry
This industry ensures hospitals and clinics have the tools they need to save lives. It’s not just about machines — it’s about healthcare innovation, patient safety, and efficiency.
Understanding the Manufacturing Process
Research and Development (R&D)
Every great product starts with an idea. In medical devices manufacturing, R&D is where the magic begins.
Ideation and Concept Testing
Teams brainstorm, sketch, and simulate product ideas. Then, they test concepts through small trials and user feedback to determine viability.
Prototyping and Product Design
Before going to mass production, a prototype is created. This helps identify design flaws and gather early clinical feedback.
Role of CAD and 3D Modelling
Design engineers use advanced software to build detailed 3D models, helping predict performance and optimize the structure.
Materials Used in Medical Device Production
The choice of material can make or break a device.
Biocompatible Materials
Manufacturers use plastics, metals, and ceramics that are non-toxic and accepted by the human body. Titanium and medical-grade silicone are common choices.
Regulatory Standards and Certifications
You can’t just create a device and sell it — there are rules.
FDA, ISO, and CE Certifications
Medical devices must meet strict quality and safety regulations. These include FDA approvals in the U.S., CE marks in Europe, and ISO 13485 certification globally.
Key Technologies in Medical Devices Manufacturing
Automation and Robotics
Modern factories use robotics to improve precision, reduce errors, and accelerate production.
3D Printing in Medical Devices
3D printing is transforming the industry by allowing customized implants, faster prototyping, and reduced waste.
AI and IoT Integration
Smart medical devices connected through IoT can transmit real-time health data to doctors. AI helps in predictive maintenance and quality control.
Foxxtechnologies – Leading the Innovation
Overview of Foxxtechnologies
Foxxtechnologies is not your average manufacturer. They specialize in innovative, scalable, and high-quality medical device production services. With a solid reputation, they cater to both startups and large healthcare brands.
Unique Manufacturing Capabilities
Customization and Rapid Prototyping
Need a device tailored to your needs? Foxxtechnologies provides rapid prototyping, saving both time and cost in development.
Cleanroom Production Facilities
Sterility is crucial. Their ISO-class cleanrooms ensure that every product meets stringent hygiene standards.
Compliance and Quality Assurance
Foxxtechnologies doesn’t just build — they ensure every product is tested, validated, and certified according to international standards.
Trends Shaping the Future of Medical Device Manufacturing
Sustainability and Eco-Friendly Practices
As the world shifts towards greener practices, manufacturers like Foxxtechnologies are adopting recyclable materials and low-waste processes.
Smart Devices and Wearables
From fitness trackers to glucose monitors, wearable technology is booming and changing how we manage health.
Global Market Growth and Expansion
The global market for medical devices is expected to surpass $800 billion by 2030. Companies must scale fast — and smart.
Challenges in Medical Device Manufacturing
Navigating Regulations
Each country has its own rules. Global manufacturing means tackling multiple regulatory frameworks.
Ensuring Sterility and Biocompatibility
The challenge is to ensure every device is safe and performs flawlessly inside the human body.
High Costs of R&D and Manufacturing
Innovation isn’t cheap. It demands huge investments in technology, skilled labor, and compliance.
Why Choose Foxxtechnologies for Medical Device Manufacturing?
Industry Expertise and Experience
With years of hands-on experience, Foxxtechnologies knows what works and what doesn't in this highly sensitive sector.
Client-Centric Solutions
From idea to delivery, the team works closely with clients, offering end-to-end support.
Scalable and Efficient Processes
Whether it’s a batch of 100 or 10,000 units, Foxxtechnologies scales seamlessly without compromising quality.
Conclusion
Medical devices manufacturing is not just a process — it’s a commitment to healthcare, innovation, and patient safety. As technology evolves, companies like Foxxtechnologies are leading the charge by integrating cutting-edge tech, adhering to global standards, and providing client-focused solutions.
Whether you're a startup with a prototype idea or an established healthcare brand looking to expand production, Foxxtechnologies is your go-to partner in the realm of medical device manufacturing.
Email Us : [email protected]
0 notes
Text
PEB vs Traditional Construction: What Leading PEB Manufacturers in India Say
In the evolving world of construction, the debate between Pre-Engineered Buildings (PEB) and traditional construction methods has become increasingly relevant. With the rise of industrial, commercial, and infrastructure projects, builders and developers are now leaning towards faster, more cost-effective, and durable construction methods. That's where PEB systems step in — revolutionizing the construction landscape across India.
But how exactly do PEBs outperform traditional construction? And what do the top industry players — including renowned PEB company names — say about this shift? Let’s explore.
What Are Pre-Engineered Buildings?
Pre-Engineered Buildings are factory-manufactured steel structures that are shipped and assembled on-site. Unlike traditional buildings that are constructed brick by brick on-site, PEBs follow a design–manufacture–assemble model, saving time and resources.
A reputed peb company like Shree Umiya Structure uses advanced design software and precision engineering to fabricate steel structures tailored to specific project needs.
PEB vs Traditional Construction: Key Differences
1. Speed of Construction
PEB: Since most components are prefabricated, construction time is reduced by up to 50%.
Traditional: Time-consuming due to on-site fabrication, curing, and manual labor.
Top PEB companies in India point out that reduced construction time directly results in faster ROI — especially for commercial and industrial projects.
2. Cost Efficiency
PEB: Lower labor costs, minimal material wastage, and reduced site overheads.
Traditional: Higher costs due to extensive on-site labor and longer project durations.
According to Shree Umiya Structure, a leading peb company, clients save significantly on both material and labor costs by opting for pre-engineered solutions.
3. Design Flexibility and Accuracy
PEB: Highly customizable using CAD/CAM and BIM technology.
Traditional: Less flexibility and higher chances of design errors.
Today’s top PEB manufacturers in India emphasise the advantage of modular design and scalability. Whether it’s a warehouse, factory, or retail showroom, PEBs offer superior adaptability.
4. Structural Durability
PEB: Manufactured with high-quality steel, offering enhanced strength and resistance to weather, seismic activity, and corrosion.
Traditional: May suffer from uneven workmanship and longer-term maintenance needs.
Leading PEB companies ensure strict quality control during fabrication, giving clients long-lasting structural integrity.
5. Sustainability
PEB: Environmentally friendly with recyclable materials and lower carbon footprint.
Traditional: Generates more site waste and consumes natural resources like water, sand, and bricks.
As per Shree Umiya Structure, sustainability is a major factor why modern developers are choosing PEB companies for green building solutions.
Why Are Developers Choosing PEB Today?
Modern builders are under pressure to deliver faster, cheaper, and more reliable projects. In such a scenario, working with an experienced peb company gives them access to engineering excellence, streamlined project management, and guaranteed timelines.
From industrial sheds and cold storage units to commercial spaces and airport terminals, the versatility of PEB systems is unmatched.
Trusted PEB Company in India – Shree Umiya Structure
When it comes to reliability, innovation, and on-time delivery, Shree Umiya Structure stands tall as a top-performing PEB company in India. With decades of experience and hundreds of successful projects across the country, they are known for providing complete turnkey PEB solutions — from design and fabrication to on-site installation.
Their expert team ensures that every structure meets international standards of quality and safety, making them a preferred partner for industrial and commercial clients alike.
Final Thoughts
The construction industry is shifting gears — and PEB systems are leading the change. With faster turnaround times, reduced costs, and enhanced durability, it’s no wonder developers are moving away from traditional brick-and-mortar methods. Backed by the expertise of a trusted peb company like Shree Umiya Structure, you can future-proof your projects with confidence.
0 notes
Text
Curved Surface Printer Market [2025] Size, Share and Trends upto 2033
Global “Curved Surface Printer Market” research report is a comprehensive analysis of the current status of the Curved Surface Printer industry worldwide. The report categorizes the global Curved Surface Printer market by top players/brands, region, type, and end-user. It also examines the competition landscape, market share, growth rate, future trends, market drivers, opportunities, and challenges in the global Curved Surface Printer market. The report provides a professional and in-depth study of the industry to help understand its current state and future prospects. What Are The Prominent Key Player Of the Curved Surface Printer Market?
AMI
IQDEMY
Unique Assembly
Roland DG Corporation
Micro-tec
Systematic Automation
NEWLONG
Fuxinlong Machinery
DOMSEM
Liberty Clark
TAOXING Technology
Hang Lap
Jiamei Screen Printing Equipment
Fine Cause
The Primary Objectives in This Report Are:
To determine the size of the total market opportunity of global and key countries
To assess the growth potential for Curved Surface Printer
To forecast future growth in each product and end-use market
To assess competitive factors affecting the marketplace
This report also provides key insights about market drivers, restraints, opportunities, new product launches or approvals.
Regional Segment of Curved Surface Printer Market:
Geographically, the report includes research on production, consumption, revenue, market share, and growth rate of the following regions:
United States
Europe (Germany, UK, France, Italy, Spain, Russia, Poland)
China
Japan
India
Southeast Asia (Malaysia, Singapore, Philippines, Indonesia, Thailand, Vietnam)
Latin America (Brazil, Mexico, Colombia)
Middle East and Africa (Saudi Arabia, United Arab Emirates, Turkey, Egypt, South Africa, Nigeria)
The global Curved Surface Printer Market report answers the following questions:
What are the main drivers of the global Curved Surface Printer market? How big will the Curved Surface Printer market and growth rate in upcoming years?
What are the major market trends that affecting the growth of the global Curved Surface Printer market?
Key trend factors affect market share in the world's top regions?
Who are the most important market participants and what strategies being they pursuing in the global Curved Surface Printer market?
What are the market opportunities and threats to which players are exposed in the global Curved Surface Printer market?
Which industry trends, drivers and challenges are driving that growth?
Browse More Details On This Report at - https://www.businessresearchinsights.com/market-reports/curved-surface-printer-market-104432
Contact Us:
Business Research Insights
Phone:
US: (+1) 424 253 0807
UK: (+44) 203 239 8187
Email: [email protected]
Web: https://www.businessresearchinsights.com
Other Reports Here:
Mechanical Keyboards Market
Lining Fabrics Market
E-Ticketing System Market
Mobile Car Washing Market
Compound Bow Market
Fabric Cutting Machines Market
Electronic Batch Record Software Market
Laser Micro Perforation Market
Automotive Recycling Market
Conjugated Linoleic Acid (CLA) Market
Other Reports Here:
Swimming Pool Clean Robots Market
Mini Tiller Cultivator Market
Torque Calibration Services Market
Spiral Separator Market
Invisible Dog Fence Market
SD-Branch Market
Garbanzo Flour Market
Leather Luggage and Suitcases Market
MOSFET and IGBT Gate Drivers Market
Knowledge Payment Platform Market
0 notes