#rogue antivirus software
Explore tagged Tumblr posts
Text
Found this highlight, somebody made a fake commercial for the infamous SpySheriff Rogue as part of a competition by F-Secure
youtube
#reshi rambles#shitposts#Spysheriff#malware#rogue antivirus software#2000s nostalgia#old computer software#2000s core#aero frutiger#Youtube
0 notes
Note
If you are willing, I crave more Idia content. I really like the first date thing you wrote for him, and I’d love to see how you’d approach the idea of him being a bit bolder with his crush upon finding out somehow that they have a crush on him too! Tysm and congrats! 🩵💙

COMMENTS: Thank you for the request. Idia is one of my favorites. 💙 And maybe that's why I wrote a little more than I usually do. And in a slightly different way too.
I hope you and all enjoy it. 😉
CHARACTERS: Idia Shroud (Ortho as his accomplice)
TAGS: Fluff; GN Reader; Flirting
WORD COUNT: 850 words

How did he find out?
Idia found out because of Ortho. Knowing that his older brother had a crush on you, he decided to find out if you could have a crush on him too. Since Idia wouldn't try anything at all unless he was absolutely sure your feelings would be reciprocated.
First Ortho studied your vital signs and other physical changes to see if they changed when his brother was around or mentioned. And, according to his studies and test results, the changes that happened to you squared with the changes that occur when one person has a crush on another.
Why do all that if some of your closest friends could confirm your crush on him? Because that information would not be enough for Idia, he needed scientific proof too.
How would he react?
Denial! “Come on! Those results can't be right. I mean, with all this handsome SSR OP characters around? They could have a prince, why would they want me? You must have some bug. Let me check.”
“NO! I’m fine!” Ortho replays “I can guarantee you that all my software is up to date and there is no warning from my antivirus.” They got into an argument long enough for Ortho to convince Idia that it's true that you have a crush on him. Would that take hours? Days? It doesn't matter. The Shroud may very well be the most stubborn students in the entire school.
How would he start acting around you?
Well, it depends. Of how many people and who is around you.
If you are in a place where he feels socially uncomfortable, such as surrounded by extroverted friends of yours, you will be his shield. He won't let go of you. And he will only talk to you, or at least try to only talk to you. If those people are the shadows in the room and he is a child afraid of the dark trying to sleep, then you are his teddy bear that puts him to sleep when he hugs you.
Well, he wouldn't literally hug you in public, but the feeling is extremely similar.
If he is very anxious, he may discreetly hold your arm. And he will try to convince you to accompany him to a place where he feels more at ease.
If you were out in public but in a situation that was within his comfort zone, for example at the board games club, or surrounded by someone he already has a little more confidence in, he will still be reserved, at least in the eyes of others.
He would always be close to you, sit next to you. Not in the sense that he is glued to you, but in the sense that you are the person he feels most comfortable with. Like I said before, his teddy bear.
Since he is in a place where he feels comfortable, he can forget about the others while talking to you, by accident, and flirt with you a little. Tucking his arm around your shoulders as he talks. Talking to you in that deep voice and with his confident smile on his face.
If anyone in the room shows they can hear you two or can tell you're flirting, he'll back away from you a little bit completely embarrassed by the situation. And yes, the ends of his hair will turn pink.
And if you are in private, most likely in his room, there will be nothing to assuage his pride.
He will treat you most of the time like his best friend. At least until such time as something happens or is said that gives him an opening to flirt with you. A bet on a video game for example?
“You want to take a walk with me one day? To leave my room of my own free will?” Idia smiles smugly at you “Fine, sure, of course... if you beat me at Star Rogue.”
You two were sitting, playing some video games.
“That's not fair!” you protest “You know nobody can beat you!”
“I'm glad you're smart enough to see the trick. If you had accepted I would have started to worry about your ability to fall into a deadly trap in the future. Wisdom is not an attribute to be neglected.”
“If you don't want to take a walk with me, all you have to do is say no. Or no, thanks.”
“I know, that's why I never said no. Are you not paying attention?”
You don't want to play that, so you get up sulking and walk to the door to leave. You expect him to stop you but he doesn't. You try to leave, but the door won't open.
Idia gets up and walks over to you. Still with your back to him, you see his hand land on the closed door. You turn around and he's basically "kabe-don" you.
“Hey, come on, these kinds of achievements shouldn't be so simple to get, don't you think? And do we really need to go outside? There are so many things we can only do inside.”

If you dropped in here out of the blue and want to read more from me, you can find it in my pinned post: INDEX
#Twisted Wonderland#twst#twisted wonderland x reader#twst x reader#disney twisted wonderland#twst imagines#twst wonderland#twst fluf#Twisted Wonderland Fluf#twst fluff#Twisted Wonderland Fluff#twst requests#Twisted Wonderland requests#requests#500 followers#500 followers milestone#500 followers celebration#Idia Shroud#Idia Shroud x Reader#Idia x Reader
573 notes
·
View notes
Text
semi related but reading about affiliate networks for rogue antivirus software is really funny. pyramid scheme for malware sellers
7 notes
·
View notes
Text

Some rogue antivirus programs in 2024 pose serious risks, disguising themselves as security tools while stealing data or installing malware. These fake antiviruses often exploit users through phishing scams or unverified downloads. To stay safe, rely on trusted brands, verify software sources, and avoid suspicious offers promising "instant protection."
https://bit.ly/3ZKGI6M
3 notes
·
View notes
Note
[The rogue queen ant is uncharacteristically quiet. This… Seemed to be a lot bigger than she originally thought.]
"It sure sounds like you got a lot on your shoulders, fella."
[She sits a bit more still, her elbows on the table and her hands clasped together with concern.]
"I know I can come on strong, but it's only because I care just a bit too much about other folks."
[She smooths back some of her hair.]
"And listen. If you'd let me. It sounds like there's a whole lot of folks in there that could benefit from my help. I've got experience with dealing with malware - made my own antivirus software to specifically deal with the worst of 'em in case they ever slip through my safe environments."
[She softened her expression.]
"So please. Let this old ant lend a couple hands?"
-🐜
"...You may do as you wish. I cannot stop you from talking with others inside the server via their feeds. Whether or not they are receptive...is another story."
[Sonny stiffened as Ori stepped over, mumbling a 'doctor?' as he usually would when concerned with something]
"...Whatever you do, anything that looks like this...." [He motions to Ori, who simply sighs] "Be wary how you trust them."
4 notes
·
View notes
Text
Akira Ransomware Breaches Over 250 Global Entities, Rakes in $42 Million
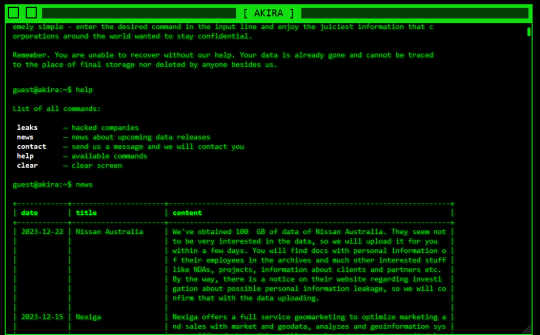
A joint cybersecurity advisory issued by CISA, FBI, Europol, and the Dutch NCSC-NL has uncovered the staggering scale of the Akira ransomware campaign. Since early 2023, the nefarious Akira operators have compromised more than 250 organizations worldwide, extorting a whopping $42 million in ransom payments. Akira's Prolific Targeting Across Industries The Akira ransomware group has been actively infiltrating entities across diverse sectors, including education, finance, and real estate. Staying true to the double extortion playbook, the threat actors exfiltrate sensitive data before encrypting the victims' systems, amplifying the pressure for a ransom payment. Early Akira versions, coded in C++, appended the .akira extension to encrypted files. However, from August 2023 onward, certain attacks deployed Megazord, a Rust-based variant that encrypts data with the .powerranges extension. Investigations reveal the perpetrators interchangeably using both Akira and Megazord, including the updated Akira_v2. Initial Access and Privilege Escalation The cybercriminals exploit various entry points, such as unprotected VPNs, Cisco vulnerabilities (CVE-2020-3259 and CVE-2023-20269), RDP exposures, spear phishing, and stolen credentials. Post-compromise, they create rogue domain accounts, like itadm, to elevate privileges, leveraging techniques like Kerberoasting and credential scraping with Mimikatz and LaZagne. Disabling Security Controls and Lateral Movement To evade detection and facilitate lateral movement, Akira operators disable security software using tools like PowerTool to terminate antivirus processes and exploit vulnerabilities. They employ various tools for reconnaissance, data exfiltration (FileZilla, WinRAR, WinSCP, RClone), and C2 communication (AnyDesk, Cloudflare Tunnel, RustDesk, Ngrok). Sophisticated Encryption The advisory highlights Akira's "sophisticated hybrid encryption scheme" combining ChaCha20 stream cipher with RSA public-key cryptography for efficient and secure encryption tailored to file types and sizes. As the Akira ransomware campaign continues to wreak havoc, the joint advisory provides crucial indicators of compromise (IoCs) to help organizations bolster their defenses against this formidable threat. Read the full article
2 notes
·
View notes
Text
All You Need To Know About KMSPICO

KMSpico is incredibly powerful and enables users to activate Microsoft products without paying the license fee. It works by mimicking a KMS server and using generic keys to activate Windows and other Microsoft software. You may get more details about windows by visiting kmspico download site.
Nevertheless, many antivirus software block KMSPICO from being installed as malware. This is because it defies security measures and requires users to disable their antivirus programs prior to installation.
What's kmspio?
KMSPICO is primarily a tool crafted by cyber criminals that allows users to install and use different Microsoft products without paying recurrently. It operates by mimicking the KMS server, which is used by Microsoft to authenticate products.
It is capable of altering internal Windows settings, which can negatively impact computer performance and security. Due to these factors, many antivirus programs view kmspico windows 11 as a threat and either prevent its download or caution users against running it.
To increase infection rates, KMSPICO developers commonly use infected websites that appear to be legitimate download portals, search engines, and software product pages. They may additionally "package" rogue software together with legitimate applications during the downloading and installation processes. Additionally, they may ask users to disable their anti-virus applications, which is another indicator of malware distribution.
Does kmspico do any work?
KMSpico is essentially a malware-free program designed to permit you to activate Microsoft products for free. This tool functions by mimicking a Key Management Server (KMS), which is typically employed for licensing large amounts of software. The program permits you to obtain a lifetime license for Windows and Microsoft Office without spending money. This can only be achieved if you download the program from reputable sites and carefully follow the instructions.
Unfortunately, those who distribute kmspico for windows 11 are not always diligent. The programs are often downloaded bundled with malware, including adware, browser hijackers, and even password-stealing ransomware. They are often distributed through hacker-controlled portals and ad campaigns.
youtube
Due to these problems, it can be challenging to obtain a clean version. However, it is certainly not impossible to achieve it entirely. In fact, the most recently released version of the program can be found on a members-only forum that was created over a decade ago. It is important to note that this site does NOT reside on Microsoft servers and has no official support for KMSPICO.
Learn How To Make Use Of Kmspico
KMSPICO is a program that helps you bypass Microsoft's restrictions on using its products. It can easily be used to activate Windows operating systems and other Microsoft office products within minutes without having to pay for them.
Unfortunately, this tool also acts as malware and can potentially inflict severe problems on your computer. It attempts to penetrate by exploiting the "bundling" method, where rogue software is installed alongside legitimate applications during the download and installation process.
Once installed, the program backs up the license information on your system software and creates a dedicated KMS server. Its main objective is to drive traffic and click-through revenue for its creators, and therefore, it displays annoying pop-up advertisements. Additionally, it can slip under the radar of other applications, making it challenging to remove. To uninstall it safely, you need to perform a complete system scan and remove all files associated with kmspico for windows 11.
How to eliminate KMSPICO?
KMSPICO is a malware that could pose significant security risks to the user. It is essentially a license bypass tool that modifies the product key of Microsoft software products and redirects the KMS server to one that is managed by its developer. This allows Microsoft software to be activated without purchasing a valid license.
Additionally, KMSPICO may inflict computer system viruses. For example, the hacking tool has been known to distribute STOP/DJVU ransomware versions. This malware version redirects the internet browser to infected web pages and takes sensitive information from the infected system.
The use and misuse of KMSPICO constitutes a punishable offense under the Digital Millennium Copyright Act (DMCA).
Users can uninstall it using a trusted antimalware program such as Zemana Anti Malware. Once the process is completed, the system will be restored to its previous state. Once the procedure is completed, the system shall be restored to its default state. Additionally, the program won't anymore redirect the browser to unused web pages.
2 notes
·
View notes
Text
15 Types of Malware Everyone Should Know About
In today’s digital world, our devices are more connected than ever. While this makes life easier, it also means more opportunities for cybercriminals to attack. One of the biggest online threats is malware. But what is malware? And how can you stay safe from it?
In this blog, we’ll explain 15 different types of malware in simple terms. We’ll also show you how using tools like CoverMeVPN can help protect your personal information and keep you safe online.
What Is Malware?
Malware is short for malicious software. It’s any program or file created to harm your computer, steal your information, or take control of your device without your permission. Cybercriminals use malware to cause problems for people, businesses, and even governments.
Let’s look at the most common types of malware you should watch out for.
The 15 Main Types of Malware
1. Virus
A virus attaches itself to a file or program. When you open that file, the virus spreads to other files on your device. Viruses can damage data, slow down your system, or even delete important files.
Example: A harmful file downloaded from a suspicious email.
Worm
A worm spreads by itself through a network. It doesn't need you to open a file or click a link. Worms often slow down computers and networks by using up resources.
Example: A worm might spread through email contacts and send copies of itself to others.
Trojan Horse
A Trojan horse, or Trojan, looks like a normal file or app. But when you open it, it installs malware secretly. Trojans are often used to steal personal data or give hackers control of your device.
Example: A free online game that secretly steals your passwords.
Ransomware
Ransomware locks your files and demands money to unlock them. It usually asks for payment in cryptocurrency, like Bitcoin.
Example: The famous WannaCry ransomware attack in 2017 affected thousands of companies around the world.
Spyware
Spyware secretly gathers information about you. It can track your keystrokes, watch the websites you visit, and record your passwords.
Example: A program that steals your online banking details while you type.
Adware
Adware shows unwanted ads on your screen. Some adware also collects information about your browsing habits without your permission.
Example: Pop-up ads that appear even when you’re not using your browser.
Rootkit
A rootkit hides deep in your system and allows hackers to control your computer remotely. It’s very hard to detect.
Example: A hacker secretly turning on your webcam.
Keylogger
A keylogger records every key you press. It captures passwords, messages, and credit card numbers.
Example: A hidden program that sends everything you type to a hacker.
Botnet
A botnet is a group of infected computers controlled by a hacker. These computers, called bots, work together to perform tasks like sending spam emails or attacking websites.
Example: A hacker using thousands of infected computers to crash a website.
Fileless Malware
Fileless malware doesn’t install any files. It uses existing programs on your computer to perform harmful tasks, making it hard for antivirus programs to find.
Example: Malware that uses system tools like PowerShell to steal data.
Logic Bomb
A logic bomb is hidden in a program and only activates when certain conditions are met, like a specific date or event.
Example: A malicious code set to delete files on April 1st.
Mobile Malware
Mobile malware attacks smartphones and tablets. It can steal data, track your location, or send premium-rate messages.
Example: A fake mobile app that quietly spies on you.
Scareware
Scareware tricks you by displaying fake virus warnings. It tries to scare you into buying fake software or services.
Example: A pop-up claiming “Your system is infected! Download now!”
Rogue Security Software
A form of scareware, rogue security software pretends to be a real antivirus program. It shows fake alerts and asks you to pay for a solution to problems that don’t exist.
Example: A program claiming you have 500 viruses when your device is clean.
Malvertising
Malvertising uses online ads to spread malware. Even trusted websites can display infected ads without knowing it.
Example: Clicking an ad promising a free prize, which installs malware.
How to Stay Safe from Malware
Staying safe online doesn’t have to be complicated. A few simple habits can protect you from most malware threats:
Always keep your software updated.
Don’t click on suspicious links or attachments.
Use strong, unique passwords for every account.
Backup your important files regularly.
Install reliable antivirus software.
Avoid downloading apps or files from unknown sources.
And here’s a powerful tool to add to your defense:
🌐 Protect Your Privacy with CoverMeVPN
One of the best ways to stay safe online is by using a VPN (Virtual Private Network). A VPN hides your IP address and encrypts your internet connection, making it much harder for hackers to target you.
We recommend CoverMeVPN, a trusted and secure VPN service that shields your online activity from prying eyes. It prevents malware from tracking your location and protects your personal information, especially when using public Wi-Fi networks.
Whether you’re working from home, traveling, or just browsing at a coffee shop, CoverMeVPN adds an extra layer of safety between you and the internet.
Why CoverMeVPN?
Keeps your identity and data private.
Protects you on public Wi-Fi.
Blocks dangerous websites.
Easy to use and fast.
Final Thoughts
Malware comes in many forms, and it’s more common than most people realize. From viruses and worms to ransomware and spyware, these digital threats can cause serious problems. The good news is that by learning about malware and taking simple steps to stay safe, you can avoid most attacks.
Make sure to use strong passwords, avoid suspicious links, and always keep your devices up to date. And for even stronger protection, consider using a VPN like CoverMeVPN to keep your online life private and secure.
By being careful and staying informed, you can enjoy the internet safely without falling victim to malware.
0 notes
Text
Week2.1!
Elevator Pitch for a platformer game.
Target audience: Fans of fast-paced indie platformers, ages 13+, especially those into sci-fi or retro-futuristic styles.
For my platformer project, I want to work on a game called Blackwall. You play as a rogue AI that's been released into a network. Your mission? Infiltrate digital subnets and eliminate a high-value target. Each subnet (level) is a maze of data full of enemies that roam and search the net to stop you from reaching your destination. You will need to dash, jump, and exploit glitches/faults in the subnet to bypass enemies and reach deeper into the network.
I'm aiming for a CRT-inspired, heavy cyberpunk aesthetic.
If i can, I'd love to implement:
-Dash mechanics
-Visual distortion effects
-Enemy AI that behaves like antivirus software
-Minimalist storytelling told through corrupted fragments of data and logs.
0 notes
Text
10 Common Ways Hackers Gain Access to Your Phone
Smartphones have become an essential part of our lives, holding personal, financial, and professional information. While these devices offer convenience, they also attract cybercriminals who use clever tactics to gain unauthorized access. Understanding how hackers target phones can help you safeguard your device and sensitive information. Here are the 10 most common ways hackers access phones and tips to stay ahead of these threats.

1. Phishing Attacks
Phishing is a popular method where hackers deceive users into sharing sensitive details, such as passwords or banking information.
How it works:
Cybercriminals send fake emails, messages, or SMS (known as smishing) that mimic legitimate organizations like banks or social media platforms. These messages often contain links leading to counterfeit websites designed to steal credentials.
Tips to stay safe:
Always verify the sender’s identity before clicking on links.
Avoid sharing sensitive information via emails or messages.
Use tools that detect phishing attempts and flag malicious websites.
2. Public Wi-Fi Networks
Public Wi-Fi in places like coffee shops, airports, or hotels is convenient but risky. Hackers exploit unencrypted connections or set up fake networks to intercept user data.
How it works:
Hackers create rogue Wi-Fi hotspots with names similar to legitimate networks. Unsuspecting users connect, exposing their online activity and personal information.
Tips to stay safe:
Refrain from accessing sensitive accounts or conducting transactions on public Wi-Fi.
Use a Virtual Private Network (VPN) for secure browsing.
Disable automatic Wi-Fi connections on your phone.
3. Malicious Apps
Apps can be a hidden source of danger when they carry malware. Cybercriminals disguise malicious software as harmless apps to infiltrate your device.
How it works:
These apps may masquerade as games, utilities, or productivity tools and request excessive permissions, such as access to your camera, contacts, or messages.
Tips to stay safe:
Download apps exclusively from trusted sources like Google Play or Apple’s App Store.
Review app permissions before installation.
Use a reliable antivirus program to scan your phone periodically.
4. SIM Card Swapping
SIM swapping is a method where hackers manipulate mobile carriers into transferring a user’s phone number to another SIM card under their control.
How it works:
The attacker contacts your mobile provider, pretending to be you, and uses stolen personal information to convince them to transfer your number. Once done, they intercept calls, SMS, and two-factor authentication (2FA) codes.
Tips to stay safe:
Set a PIN or password on your mobile carrier account.
Opt for app-based authentication methods like Google Authenticator instead of SMS-based 2FA.
Monitor your phone for unusual service disruptions.
5. Bluetooth Vulnerabilities
Bluetooth is a helpful tool for connecting devices but can also be a weak spot for security. If not handled carefully, it becomes a gateway for hackers.
How it works:
When Bluetooth is left on and discoverable, hackers exploit vulnerabilities to intercept data or install malware.
Tips to stay safe:
Turn off Bluetooth when not in use.
Pair devices only in secure settings.
Keep your phone updated to fix Bluetooth-related vulnerabilities.
6. Outdated Software
Failure to update your phone’s software leaves it vulnerable to exploits that hackers use to infiltrate devices.
How it works:
Operating systems and apps occasionally have security flaws. Developers release updates to fix these issues, but delaying updates can leave your phone exposed.
Tips to stay safe:
Regularly update your phone’s operating system and apps.
Enable automatic updates to ensure you don’t miss critical fixes.
Avoid using devices that no longer receive software support.
7. Social Engineering
Social engineering targets human psychology instead of technical vulnerabilities. Hackers manipulate victims into revealing sensitive data or granting access.
How it works:
A hacker might impersonate a trusted individual or organization, pressuring you into sharing login details, granting access, or installing harmful software.
Tips to stay safe:
Be cautious of unsolicited calls, emails, or messages requesting information.
Verify the identity of anyone asking for sensitive details.
Stay informed about common social engineering strategies.
8. Spyware and Keyloggers
Spyware and keyloggers are forms of malware designed to monitor your activities or record your keystrokes, capturing everything you type.
How it works:
These programs are often installed unknowingly through phishing links, malicious apps, or direct access to your phone. They can track your location, steal credentials, or eavesdrop on communications.
Tips to stay safe:
Avoid clicking on suspicious links or downloading files from unknown sources.
Use strong, unique passwords for each account.
Install a trustworthy anti-spyware application.
9. QR Code Scams
While QR codes offer convenience, they can also be exploited by hackers to lead users to malicious websites or download harmful software.
How it works:
Hackers replace legitimate QR codes with altered ones that redirect users to phishing sites or initiate downloads of malware.
Tips to stay safe:
Scan QR codes only from reliable sources.
Use a QR code scanner app that displays the URL before accessing it.
Double-check QR codes in public areas to ensure they haven’t been tampered with.
10. Physical Access
Sometimes, the simplest approach for a hacker is to gain physical access to your phone. If left unattended, your device becomes vulnerable.
How it works:
Once they have your phone, a hacker can install malware, extract data, or bypass security measures. They might even perform a factory reset to take over the device.
Tips to stay safe:
Use a strong password, PIN, or biometric lock.
Enable features like “Find My Phone” to locate or remotely wipe the device.
Avoid leaving your phone unattended in public places.
Enhancing Smartphone Security
Staying ahead of hackers requires consistent vigilance and adopting best practices:
Enable Two-Factor Authentication (2FA):Add an additional security layer to your accounts.
Install Antivirus Software:A good antivirus program can detect and remove malicious software.
Back Up Your Data:Regular backups ensure you don’t lose important information in case of a breach.
Use Remote Lock/Wipe Tools:Features like Google’s “Find My Device” or Apple’s “Find My iPhone” allow you to secure your phone if it’s lost or stolen.
Stay Educated:Keep up with the latest cybersecurity threats and learn how to counteract them.
Conclusion
Hackers constantly innovate, but understanding their methods can help you stay one step ahead. By implementing security practices and staying aware of potential risks, you can minimize your exposure to cyber threats. Your smartphone holds valuable data, and taking proactive measures ensures it stays safe in an increasingly connected world.
1 note
·
View note
Text
”The authentic 2007 expirence”

(This was made using makesweet.com, pls go check it out for funny stuff like this)
1 note
·
View note
Note
Tim is a mess.
This isn't exactly a new thing, but he's usually better put together than this.
Dick was the first to enter the bat cave for the meeting that Bruce called. He saw Tim... on the floor... crying? and muttering about drawings? He started banging his head against the desk by the BatComputer
"Timmy, are you okay?"
"Noo! The little animals hacked the BatComputer and are playing fetch with the icons! I can't fix it! Oracle can't fix it! I don't know what to do!"
"Well, we'll figure it out."
During the time in which Tim was ranting, the rest of the family (who could make it) arrived in the cave.
Bruce walked up to the computer to analyze the situation.
"What have you tried?"
Tim stood up and went into report mode. "When I noticed the problem, I immediately started the active antivirus software. Didn't work. I then looked at all the tasks running, but all the ones running are things that should be. I looked for any extra file, document, download, etc, but came up empty. By that time the antivirus finished and detected no major viruses, and killed the small bugs by itself. But, that's when the stupid animal doodles opened up your files on the rogues and were looking through them! They looked like they were just playing with the scroll, but I don't know if that is a distraction or something, and every time I closed the tab, one of them kept opening it! It was like herding cats!" As Tim started to go back to ranting mode, the cat doodle looked at Tim with an annoyed expression, which is weird seeing as it really didn't have a face.
"Did you try turning it off and on again?" Duke asked.
Tim just looked tired "A lot of malware can still work with the computer off, and Restarting it only works for operating system errors because it skipped or misread a line of code or something and its basically a retry to read it. It wouldn't do anything to viruses that the antivirus software couldn't fix."
"Sorry..." Duke looked dejected.
Dick piped up, "Nah, don't worry about it, you haven't gotten the BatHack rundown yet."
Steph was just watching the animals playing fetch for a while, the squirrel throws an icon across the page for the dog and fox to chase, it bounces around for a bit, and then one of the canines brings it to the closest other animal. The lizard started getting bored though, and was sniffing (with forked tongue out) through some other files. It opened up the music.

Danny makes some little animal stick figure desktop pets, with Tucker's help, mainly to help with homework, act as autocorrect, and serve as something cute. He notices after a few weeks that they can interact with different things in different ways (think of the stick figures from animation vs animator) and is impressed. He decides to bring the six with him in his phone on a class field trip to Gotham and excitedly shows Sam and Tucker the evolved code. While there and walking around the sticks were just messing around in Danny's phone when they manage to accidentally air drop themselves into Tim Drake's laptop. Tim somehow doesn't notice until he's back at the cave and connects his computer to the bat computer and accidentally uploads the desktop pets to it, Danny at this point also realized his desktop pets were gone. At this point Danny and Tim are both low-key freaking out for different yet similar reasons.
omg they accidentally created a computer virus! And it’s probably a ghostly one too all things considered. Maybe it’s just some blob ghosts that infected the code, or Technus. Team Phantom might be blaming Technius at first haha.
And Tim is going to suffer, this I swear. Why are these weird, stick figure things messing the Batcomputer? He tries to fix everything and delete the little animals before anyone else shows up…but an 1 hour later, when Batman calls everybody to the Batcave, they find Tim is now a sobbing mess, whining about how the Batcomputer got hacked by stupid stick figures. Who hear that of course and decide to blast music right into his ears. The rest of the Batman try-and fail-to fix it. It definitely isn’t a normal virus, and could be something magical, but they aren’t too sure. Meanwhile, Team Phantom has been trying to figure out where Tim lives. Now Danny, as Phantom, is floating around Wayne Manor. He really hopes they don’t sue him after this.
#stick animals#imagine alan becker but animals#dp x dc#batfam#tim drake needs a hug#tim drake is a mess#danny is an idiot#digital art#animal stick figures
754 notes
·
View notes
Text
The Quadruplet Cyber Syndicate
In the year 2145, the world had descended into a cyber dystopia. Mega-corporations ruled with iron fists, their power bolstered by advanced AI and omnipresent surveillance systems. Cities were teeming with neon lights and digital advertisements, but beneath the surface, poverty and despair were rampant. In this dark future, a shadowy organization known as The Quadruplet Cyber Syndicate emerged from the depths of the dark web.
The syndicate, composed of four brilliant but nefarious siblings, had spent years mastering the art of cybercrime. They were known only by their codenames: Alpha, Beta, Gamma, and Delta. Each sibling possessed unique skills that made them a formidable force in the world of digital espionage, hacking, and financial manipulation.
Alpha, the eldest, was the mastermind. A former prodigy who had once been a top security consultant for a global conglomerate, he now used his vast knowledge to exploit vulnerabilities in the systems he once protected. Beta, the second oldest, was a coding genius with an uncanny ability to create malware that could infiltrate the most secure networks. Gamma, the only sister, specialized in social engineering and psychological manipulation, capable of extracting secrets from the most guarded individuals. Finally, Delta, the youngest, was a cryptography expert, able to decipher the most complex codes and encryptions.
Their latest operation was their most ambitious yet: a simultaneous attack on the financial systems of three major mega-corporations that controlled the world's economy. The plan was meticulously crafted. Alpha would oversee the entire operation, coordinating every move from their hidden base in the ruins of an abandoned tech facility. Beta had developed a new type of ransomware, virtually undetectable by current antivirus software, which he dubbed "Black Lotus." Gamma had spent months infiltrating the corporations' staff, gaining access to crucial insider information. Delta, using his cryptographic skills, ensured that their communications remained secure and that the data they extracted could be safely transferred and utilized.
On the night of the attack, the siblings were a well-oiled machine. Alpha initiated the breach by exploiting a zero-day vulnerability in the corporations' mainframes. Beta unleashed Black Lotus, which swiftly took control of the networks, locking down vital data and operations. Gamma's carefully planted insiders disabled key security protocols, ensuring that no alarms were triggered prematurely. Delta monitored the encrypted data flow, making real-time adjustments to avoid detection.
As dawn approached, the syndicate had siphoned off trillions of digital credits into untraceable accounts spread across the globe. However, their triumph was short-lived. Unknown to them, a coalition of underground hackers, resistance fighters, and rogue AI had been tracking their activities for months. This coalition, led by a determined former law enforcement officer named Sarah Carter, had been one step behind the syndicate, slowly piecing together the puzzle.
The coalition launched a counter-operation just as the syndicate was about to cover their tracks. They had anticipated the syndicate's moves and had laid a digital trap. When Delta attempted to encrypt the final batch of data, he unwittingly triggered the coalition's countermeasures. Alarms blared through the syndicate's hidden base as their secure channels were breached.
Panic set in as Alpha tried to coordinate an escape. Beta frantically attempted to neutralize the incoming threats, while Gamma destroyed evidence and prepared their physical getaway. Delta, realizing they had been compromised, initiated a self-destruct sequence for their servers to erase any trace of their activities.
Despite their efforts, the coalition moved swiftly. They pinpointed the syndicate's location through a combination of digital forensics and old-fashioned detective work. As the siblings attempted to flee, a tactical team stormed their base. A tense standoff ensued. However, Alpha had anticipated this possibility. He triggered a hidden escape route that led deep into the city's abandoned subway tunnels.
With Beta's hacking skills, they disabled the coalition's tracking devices. Gamma's insider knowledge of the city's layout guided them through the labyrinthine tunnels, while Delta kept their communications encrypted and secure. The coalition forces, led by Sarah Carter, found themselves one step behind at every turn.
In the chaos, the Quadruplet Cyber Syndicate managed to slip through the coalition's grasp. They emerged into the neon-lit cityscape, blending into the crowd. Their digital footprints erased, their identities concealed, they disappeared into the shadows.
In the aftermath, the world learned of the syndicate's exploits and the incredible efforts taken to bring them to justice. The financial systems were secured, and some of the stolen funds were recovered. Sarah Carter became a hero, her relentless pursuit of the syndicate earning her accolades and respect.
However, the Quadruplet Cyber Syndicate remained at large, their whereabouts unknown. Their story became a legend, a cautionary tale about the ever-present dangers of the cyber world and the relentless vigilance required to protect against them in a future dominated by technology and corruption. The syndicate had escaped, but their shadow loomed large over the digital landscape, a constant reminder of the thin line between order and chaos.
0 notes
Text
does using a vpn on public wifi more secure
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does using a vpn on public wifi more secure
VPN encryption strength
VPN encryption strength is a crucial factor to consider when choosing a virtual private network (VPN) service. Encryption is the process of converting data into a code to prevent unauthorized access. The strength of encryption used by a VPN determines how secure your online activities and data transmissions are.
There are various encryption protocols commonly used by VPN providers, such as OpenVPN, L2TP/IPsec, and IKEv2/IPsec. These protocols differ in the level of encryption they offer, with OpenVPN generally being considered the most secure due to its robust encryption algorithms.
When evaluating VPN encryption strength, it is essential to look at the length of the encryption key and the encryption algorithm used. The longer the encryption key, the harder it is for hackers to decrypt the data. AES (Advanced Encryption Standard) with 256-bit key length is currently the industry standard for VPN encryption and is virtually unbreakable.
A strong VPN encryption ensures that your online communications, sensitive information, and browsing activities remain private and secure from prying eyes, such as hackers, government surveillance, and internet service providers. It is particularly important when accessing public Wi-Fi networks, where cyber threats are more prevalent.
In conclusion, VPN encryption strength plays a vital role in safeguarding your online privacy and security. When choosing a VPN service, opt for one that offers robust encryption protocols with a high level of security, such as AES-256 encryption. By doing so, you can enjoy peace of mind knowing that your digital footprint is well-protected.
Public Wi-Fi security risks
Public Wi-Fi has become a ubiquitous amenity in cafes, airports, hotels, and other public spaces, offering convenient internet access to users on the go. However, amidst the convenience lies a hidden threat: security risks associated with connecting to these networks.
One of the primary dangers of public Wi-Fi is the potential for interception of sensitive information. Because these networks are often unsecured or poorly secured, cybercriminals can easily intercept data transmitted between a user's device and the Wi-Fi hotspot. This includes passwords, credit card numbers, and other personal or financial information, leaving users vulnerable to identity theft and financial fraud.
Another risk is the presence of rogue hotspots, which masquerade as legitimate Wi-Fi networks but are actually set up by hackers to capture users' data. Unsuspecting individuals may connect to these rogue networks, unknowingly exposing their information to cybercriminals.
Additionally, public Wi-Fi networks are often crowded and unregulated, making them breeding grounds for malware and other cyber threats. Malicious actors can deploy malware onto these networks, infecting the devices of unsuspecting users and compromising their security.
To mitigate these risks, users should take proactive measures to protect themselves when using public Wi-Fi. This includes avoiding the transmission of sensitive information, using a virtual private network (VPN) to encrypt data traffic, and keeping devices updated with the latest security patches and antivirus software.
Ultimately, while public Wi-Fi offers convenience, users must remain vigilant and take steps to safeguard their personal and financial information from the numerous security threats lurking on these networks.
VPN tunneling protocols
VPN tunneling protocols are essential components of Virtual Private Networks (VPNs) that ensure secure and private communication over the internet. These protocols establish the rules and procedures for encapsulating and encrypting data as it travels between a user's device and the VPN server.
One of the most commonly used VPN tunneling protocols is OpenVPN, known for its open-source nature, high level of security, and the ability to traverse firewalls and network address translation (NAT) devices. Another popular protocol is IPSec (Internet Protocol Security), which provides secure communication through encryption and authentication methods.
L2TP (Layer 2 Tunneling Protocol) and its extension, L2TP/IPSec, combine the features of L2TP and IPSec to offer a robust and secure tunneling protocol for VPN connections. SSTP (Secure Socket Tunneling Protocol) is another option that utilizes the SSL/TLS protocol for secure communication, making it ideal for Windows users.
PPTP (Point-to-Point Tunneling Protocol) is one of the oldest tunneling protocols but is now considered less secure compared to newer options like OpenVPN or IPSec. However, PPTP is still widely supported and easy to set up on various devices.
Choosing the right VPN tunneling protocol depends on factors such as security needs, device compatibility, and ease of configuration. While some protocols offer higher levels of security, others prioritize speed and simplicity. Understanding the differences between these protocols can help users make informed decisions when selecting a VPN service for their online privacy and security needs.
Secure VPN configurations
Title: Best Practices for Secure VPN Configurations
In today's digital landscape, ensuring secure virtual private network (VPN) configurations is paramount for safeguarding sensitive data and maintaining privacy online. VPNs serve as a crucial tool for encrypting internet traffic and establishing secure connections over public networks. However, to maximize their effectiveness, it's essential to implement the following best practices for secure VPN configurations:
Strong Encryption Protocols: Utilize robust encryption protocols such as AES (Advanced Encryption Standard) with 256-bit keys to encrypt data transmitted through the VPN tunnel. Strong encryption ensures that even if intercepted, the data remains unreadable to unauthorized parties.
Multi-Factor Authentication (MFA): Implement multi-factor authentication to add an extra layer of security beyond just username and password. MFA typically involves a combination of something the user knows (password), something they have (token or smartphone), and something they are (biometric authentication).
Regular Software Updates: Keep VPN software and firmware up to date to patch vulnerabilities and protect against known security threats. Regular updates ensure that the VPN infrastructure remains resilient against evolving cybersecurity risks.
Secure VPN Client Configuration: Configure VPN clients securely by disabling unnecessary features and limiting access privileges. Additionally, enforce strong password policies for VPN client accounts to prevent unauthorized access.
Network Segmentation: Segment the network infrastructure to isolate VPN traffic from other network segments. This helps prevent lateral movement by attackers in the event of a breach and minimizes the potential impact of a security incident.
Log and Monitor VPN Activity: Enable logging and monitoring of VPN activity to detect and respond to suspicious behavior or unauthorized access attempts promptly. Monitoring VPN traffic provides valuable insights into potential security threats and helps maintain compliance with regulatory requirements.
By adhering to these best practices for secure VPN configurations, organizations can mitigate risks associated with remote access and ensure the confidentiality, integrity, and availability of their data and network resources. Investing in robust VPN security measures is essential for safeguarding sensitive information and maintaining trust in an increasingly connected world.
VPN versus public Wi-Fi vulnerabilities
When it comes to staying safe online, many people turn to virtual private networks (VPNs) or public Wi-Fi networks. However, both options come with their own set of vulnerabilities that users should be aware of.
Public Wi-Fi networks, such as those found in cafes, airports, and hotels, are convenient but can pose significant security risks. These networks are typically unencrypted, meaning that cybercriminals can easily intercept the data being transmitted between your device and the network. This leaves your personal information, such as passwords and credit card details, vulnerable to being stolen.
On the other hand, VPNs are designed to create a secure encrypted tunnel between your device and the internet. This encryption helps protect your data from prying eyes and is especially useful when using public Wi-Fi networks. However, not all VPNs are created equal, and some may still have vulnerabilities that could potentially be exploited by hackers.
It is essential for users to understand the limitations of both options and take steps to enhance their online security. When using public Wi-Fi, it is crucial to avoid accessing sensitive information such as online banking or entering passwords. Instead, consider using a VPN to add an extra layer of protection.
In conclusion, while both VPNs and public Wi-Fi networks have their vulnerabilities, using a combination of both can help enhance your online security. By being aware of the risks and taking appropriate precautions, you can enjoy a safer and more secure online experience.
0 notes
Text
can't log in to vpn from public wifi
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
can't log in to vpn from public wifi
VPN connection troubleshoot
Troubleshooting VPN Connection Issues
A Virtual Private Network (VPN) is a crucial tool for ensuring online privacy and security. However, like any technology, it's not immune to occasional hiccups. If you're experiencing difficulties connecting to your VPN, here are some troubleshooting steps to help resolve the issue.
Check Your Internet Connection: Before troubleshooting your VPN, ensure that your internet connection is stable and working correctly. If your internet is down, the VPN won't be able to establish a connection.
Restart Your Devices: Sometimes, a simple restart can resolve connectivity issues. Restart your computer, smartphone, router, and modem to refresh their connections.
Update VPN Software: Ensure that your VPN client is up-to-date. Outdated software may contain bugs or compatibility issues that could prevent a successful connection.
Choose a Different Server: If you're unable to connect to one server, try connecting to a different one. Sometimes, servers may be temporarily overloaded or experiencing technical issues.
Check Firewall and Antivirus Settings: Your firewall or antivirus software may be blocking the VPN connection. Temporarily disable them and try connecting again to see if that resolves the issue.
Reset VPN Settings: If you've made custom settings changes to your VPN client, try resetting them to default. This can help eliminate any misconfigurations that might be causing the problem.
Contact VPN Provider Support: If you've tried all the above steps and still can't connect to your VPN, reach out to your VPN provider's customer support for assistance. They can offer further troubleshooting steps or insights specific to their service.
By following these troubleshooting steps, you can resolve common VPN connection issues and get back to enjoying a secure and private internet experience.
Public WiFi access issue
Title: Navigating the Perils of Public WiFi Access: Addressing Security Concerns
Public WiFi access has become an indispensable part of our digital landscape, offering convenience and connectivity on the go. However, beneath its allure lies a web of security risks that can compromise personal and sensitive information. Understanding these risks is crucial for safeguarding your data and privacy.
One of the primary concerns with public WiFi access is the lack of encryption. Unlike private networks, public WiFi hotspots often lack robust encryption protocols, making it easier for hackers to intercept data transmitted between devices and the network. This leaves users vulnerable to various cyber threats, including man-in-the-middle attacks, where attackers intercept communication between two parties.
Moreover, the proliferation of fake WiFi hotspots exacerbates the problem. Cybercriminals create rogue networks with legitimate-sounding names to trick unsuspecting users into connecting. Once connected, hackers can deploy various tactics, such as phishing attacks or malware distribution, to exploit vulnerabilities in connected devices.
Another issue is the shared nature of public WiFi networks. With multiple users accessing the same network, there's a heightened risk of data interception and unauthorized access to shared files or resources. Even seemingly harmless activities like checking emails or logging into social media accounts can expose sensitive information to prying eyes.
To mitigate these risks, users must take proactive measures to secure their connections. Utilizing virtual private networks (VPNs) encrypts internet traffic, shielding it from potential eavesdropping. Additionally, practicing good cybersecurity hygiene, such as avoiding sensitive transactions on public networks and keeping devices updated with the latest security patches, can significantly reduce the likelihood of falling victim to cyber threats.
In conclusion, while public WiFi access offers unparalleled convenience, it comes with inherent security risks. By staying vigilant and implementing robust security measures, users can navigate the digital landscape safely and protect their sensitive information from falling into the wrong hands.
Password authentication problem
When it comes to online security, password authentication plays a crucial role in safeguarding user accounts and sensitive information. However, there are several common issues related to password authentication that can compromise the security of an individual's online presence.
One common problem with password authentication is the use of weak or easily guessable passwords. Many individuals still use passwords like "123456" or "password," which are incredibly easy for cybercriminals to crack using automated tools. To address this issue, it is essential for users to create strong passwords that include a combination of letters, numbers, and special characters.
Another challenge with password authentication is password reuse across multiple accounts. If a hacker manages to obtain a user's password from one account, they can potentially access all other accounts where the same password is used. To mitigate this risk, it is crucial to use unique passwords for each online account and consider using a password manager to securely store and manage passwords.
Additionally, the risk of phishing attacks poses a significant threat to password authentication. Phishing attacks involve tricking users into providing their login credentials on fake websites, allowing attackers to gain unauthorized access to their accounts. To avoid falling victim to phishing scams, users should always double-check the URL of the website before entering their login credentials.
In conclusion, while password authentication is a fundamental aspect of online security, it is not without its challenges. By creating strong, unique passwords, refraining from password reuse, and remaining vigilant against phishing attempts, users can enhance the security of their online accounts and protect their sensitive information from unauthorized access.
VPN security protocols
When it comes to ensuring your online privacy and security, using a Virtual Private Network (VPN) is crucial. A VPN encrypts your internet connection, making your online activities virtually untraceable. However, not all VPNs are created equal, and the security protocol used by a VPN provider plays a significant role in determining the level of protection it offers.
There are several VPN security protocols available, each with its own strengths and weaknesses. One of the most popular and secure protocols is OpenVPN. OpenVPN is open-source software that provides a high level of security and is known for its reliability. It uses a combination of cryptographic algorithms to ensure confidentiality and integrity of data transmission.
Another commonly used protocol is IPSec (Internet Protocol Security). IPSec operates in two modes: transport mode, which encrypts the data being sent between your device and the VPN server, and tunnel mode, which encrypts the entire data packet. IPSec is widely supported and offers strong security features.
L2TP/IPSec (Layer 2 Tunneling Protocol with IPSec) is another secure protocol that provides strong encryption and authentication. While it may not be as fast as some other protocols, it is highly secure and is often used in combination with other protocols for added security.
In conclusion, choosing the right VPN security protocol is essential for maintaining your online privacy and security. Consider factors such as the level of encryption offered, speed, and compatibility with your devices when selecting a VPN provider. Remember that while using a VPN can enhance your security, it is not a substitute for practicing safe online habits.
Network firewall restrictions
A network firewall is a security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules. One important aspect of utilizing a network firewall effectively is implementing proper firewall restrictions.
Firewall restrictions are rules or settings configured within a network firewall to control and limit the flow of traffic within a network. These restrictions are crucial for enhancing network security and protecting sensitive data from unauthorized access or cyber threats.
By setting up firewall restrictions, organizations can define which devices or users are allowed to access specific resources within the network. For example, restrictions can be placed to block certain IP addresses, websites, or applications known to be risky or malicious. This helps prevent potential cyber attacks, such as malware infections or unauthorized data breaches.
In addition, firewall restrictions can also be used to regulate the type of traffic allowed within the network. For instance, organizations can create rules to prioritize business-critical applications and limit the bandwidth allocated to non-essential services. By doing so, they can ensure optimal network performance and prevent network congestion caused by excessive or unnecessary traffic.
Overall, implementing network firewall restrictions is essential for maintaining a secure and efficient network environment. By defining and enforcing strict rules through the firewall, organizations can effectively mitigate security risks, safeguard sensitive information, and uphold network integrity.
0 notes
Text
do i need a vpn when using boost mobile hotspot
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
do i need a vpn when using boost mobile hotspot
VPN necessity with Boost Mobile hotspot
Title: The Necessity of VPN with Boost Mobile Hotspot
In today's digital landscape, where online security and privacy are paramount concerns, using a Virtual Private Network (VPN) with your Boost Mobile hotspot is not just recommended; it's a necessity. Boost Mobile hotspots offer convenient internet access on the go, but without proper security measures, your sensitive data could be exposed to various threats.
A VPN creates a secure and encrypted connection between your device and the internet, preventing third parties from intercepting your data. When you connect to a Boost Mobile hotspot, your data travels through public networks, making it vulnerable to hackers and cybercriminals. However, by using a VPN, you can safeguard your personal information, such as passwords, financial details, and browsing history, from prying eyes.
Moreover, a VPN enhances your online privacy by masking your IP address and location. With Boost Mobile hotspots, your browsing activity can be tracked by internet service providers (ISPs) and advertisers. By encrypting your internet traffic and routing it through remote servers, a VPN ensures that your online activities remain anonymous and confidential.
Furthermore, VPNs offer additional benefits such as accessing geo-restricted content and bypassing censorship. With Boost Mobile hotspots, you may encounter restrictions on certain websites or streaming services based on your location. However, by connecting to a VPN server located in a different country, you can bypass these restrictions and enjoy unrestricted access to the content you desire.
In conclusion, using a VPN with your Boost Mobile hotspot is essential for safeguarding your online security, protecting your privacy, and accessing unrestricted content. By encrypting your internet connection and masking your IP address, a VPN provides peace of mind and ensures a safe and secure browsing experience wherever you go.
Boost Mobile hotspot security concerns
Title: Understanding Boost Mobile Hotspot Security Concerns
In today's interconnected world, mobile hotspots have become essential for staying connected on the go. Boost Mobile, a popular provider of prepaid wireless services, offers mobile hotspot capabilities to its customers. While convenient, these hotspots also come with their own set of security concerns that users need to be aware of.
One primary concern is the risk of unauthorized access to the hotspot. Without proper security measures in place, malicious actors can potentially intercept the connection and gain access to sensitive information transmitted over the network. This could include personal data, login credentials, or even financial information.
Another issue is the possibility of malware infections. When connected to a mobile hotspot, devices are exposed to the same risks as any other internet connection. If a user inadvertently visits a malicious website or downloads a compromised file, their device could become infected with malware, putting their data and privacy at risk.
Furthermore, there's the threat of rogue hotspots. Hackers can set up fake hotspots with similar names to legitimate ones, tricking users into connecting to them unknowingly. Once connected, the hacker can monitor all traffic passing through the hotspot, potentially capturing sensitive information.
To mitigate these risks, users should take proactive steps to secure their Boost Mobile hotspot. This includes using strong, unique passwords for both the hotspot itself and any connected devices. Additionally, enabling encryption protocols such as WPA2 or WPA3 can help protect against unauthorized access.
Regularly updating device software and using reputable antivirus software can also help prevent malware infections. Finally, users should exercise caution when connecting to unfamiliar hotspots and verify the legitimacy of the network before transmitting any sensitive information.
By staying informed and implementing proper security measures, Boost Mobile users can enjoy the convenience of mobile hotspots while minimizing the associated risks.
VPN advantages for Boost Mobile users
Boost Mobile users can greatly benefit from using a Virtual Private Network (VPN) for enhanced privacy, security, and accessibility while browsing the internet on their devices. A VPN encrypts the user's internet connection, making it more secure and protecting their personal data from potential cyber threats such as hackers, snoopers, or identity thieves.
One of the main advantages of using a VPN for Boost Mobile users is the ability to access geo-restricted content. By connecting to a VPN server in a different location, users can bypass content restrictions and access websites, streaming services, or online platforms that may be blocked in their region.
Additionally, a VPN can help prevent ISP throttling, which can slow down internet speeds when streaming or downloading content. Boost Mobile users can enjoy a faster and more stable connection by using a VPN to mask their online activities from their internet service provider.
Another key benefit of using a VPN is the ability to browse the internet anonymously. With a VPN, users can hide their IP address and location, ensuring their online activities remain private and untraceable. This is especially important for Boost Mobile users who often connect to public Wi-Fi networks, as a VPN can protect their data from potential eavesdroppers on unsecured networks.
Overall, utilizing a VPN can provide Boost Mobile users with added security, privacy, and freedom while browsing the internet on their devices. With the increasing number of cyber threats and privacy concerns online, investing in a reliable VPN service can offer peace of mind and a safer online experience for Boost Mobile users.
Boost Mobile hotspot privacy considerations
When using a Boost Mobile hotspot, there are several privacy considerations to keep in mind to ensure your data and information are secure. A hotspot is a convenient way to connect to the internet while on the go, but it also poses some risks if proper precautions are not taken.
First and foremost, it is essential to secure your hotspot with a strong password. This helps prevent unauthorized access and ensures that only trusted individuals can connect to your network. Additionally, avoid using public Wi-Fi hotspots without a password, as these networks are often less secure and can leave your data vulnerable to hackers.
Another important consideration is to enable encryption on your hotspot. Encryption scrambles the data sent between your device and the internet, making it more difficult for cybercriminals to intercept and read your information. Most modern hotspots come with built-in encryption features that you can easily activate for added security.
Furthermore, be cautious about the information you share while connected to a hotspot. Avoid accessing sensitive data such as banking or personal information on public networks, as these can be targeted by hackers looking to steal valuable data. Consider using a virtual private network (VPN) for an extra layer of security when accessing the internet through a hotspot.
In conclusion, when using a Boost Mobile hotspot, it is crucial to prioritize privacy and security. By following these simple yet effective tips, you can enjoy the convenience of staying connected while keeping your personal information safe from potential threats on the internet.
VPN benefits for Boost Mobile hotspot users
Title: Maximizing the Benefits of VPN for Boost Mobile Hotspot Users
In an increasingly digital world, where connectivity is paramount, Boost Mobile offers users the convenience of mobile hotspots, enabling access to the internet on the go. However, as users rely more on public networks, concerns about privacy and security become more pressing. This is where a Virtual Private Network (VPN) steps in, offering numerous benefits for Boost Mobile hotspot users.
First and foremost, a VPN enhances security by encrypting data transmitted over the internet connection. Boost Mobile hotspot users can browse with peace of mind, knowing that their sensitive information, such as passwords, financial details, and personal communications, is shielded from prying eyes. This encryption is particularly crucial when using public Wi-Fi networks, where cyber threats are more prevalent.
Moreover, VPNs provide anonymity by masking the user's IP address. This means that Boost Mobile hotspot users can browse the internet without revealing their location or identity to websites and online services. By maintaining anonymity, users can protect their privacy and avoid targeted advertising and tracking.
Additionally, VPNs offer access to geo-restricted content by allowing users to connect to servers located in different regions. Boost Mobile hotspot users can bypass censorship and access websites, streaming services, and online platforms that may be restricted in their current location. Whether it's streaming their favorite shows or accessing websites unavailable in their country, a VPN provides unrestricted access to online content.
Furthermore, VPNs can improve internet speed and performance by reducing bandwidth throttling imposed by internet service providers (ISPs). Boost Mobile hotspot users can enjoy faster and more reliable connections, especially during peak usage hours.
In conclusion, integrating a VPN into their online experience can significantly enhance the security, privacy, and accessibility of Boost Mobile hotspot users. With the assurance of encrypted connections, anonymity, access to geo-restricted content, and improved performance, VPNs are invaluable tools for navigating the digital landscape safely and freely.
0 notes