#secure data encryption
Explore tagged Tumblr posts
Text
#best encryption tools#computer security#cybersecurity#data breach prevention#data encryption guide#data privacy#data protection#data safety#data security tips#digital security#encrypting personal information#encryption basics#encryption FAQs#encryption for beginners#encryption software#encryption solutions#encryption techniques#guide to data encryption#how to encrypt data#online privacy#personal data security#prevent cyber attacks#privacy software#protect data online#secure communication#secure data encryption#secure files and folders#secure personal data#software for encryption#strong encryption methods
1 note
·
View note
Text
It's just so phenomenally stupid to be sitting here trying to do everyday shit and planning for the work week ahead when it doesn't even matter anymore. Laundry groceries meal prep cleaning who the fuck cares. The lucky ones with the means to do so will get to escape the country and the rest get to deal with everything becoming too exorbitantly expensive to be able to live and also having no healthcare. Plus vaccines being outlawed (it just happened in Idaho!) and a brewing H5N1 pandemic everyone is going to ignore oh yeah and also Trump executing everyone who doesn't agree with him. Why the fuck am I having to do emails and spreadsheets at a time like this??
#me trying to figure out what i need to do before january 20th to protect myself and being overwhelmed lmao#hoard cash encrypt data find servers overseas to store my cloud stuff find secure messaging apps AHH
14 notes
·
View notes
Text
Chrome/Google is blocking HSTS encrypted content sites like Wikipedia because this encryption blocks their plagiarist data/info crawler.
Google is NOT protecting "your" security.
#google chrome#google#chrome#anti google#boycott google#hsts#encryption#encrypted communication#fyi#psa#privacy#invasion of privacy#cyber security#data security#security#infotech#it#i.t.#information technology#ausgov#politas#auspol#tasgov#taspol#australia#fuck neoliberals#neoliberal capitalism#anthony albanese#albanese government#internet
17 notes
·
View notes
Text
PLEASE don't rely on Signal to keep you safe. Please please please please please don't trust any technology to be perfectly private and secure. TL:DR- Signal's developers, funders, board members, and workers are a rotating cast of Silicon Valley technocrats (Google & Amazon guys etc) and US State Department regime change freaks. While messages are encrypted, there is still metadata they collect, and they have given data to the state department before (!!!!). Even if they only have your phone number, that can be used with data from other sources to find out a LOT of info. TOR, VPNs, and crypto (duh) are all similarly too slimy to trust. I don't have a good alternative. we should use messenger pigeons or some shit idk.
3 notes
·
View notes
Video
youtube
DeepSeek App - Privacy concerns
#youtube#DeepSeek AI chatbot privacy data security technology futuristic digital encryption mystery Concern
3 notes
·
View notes
Text
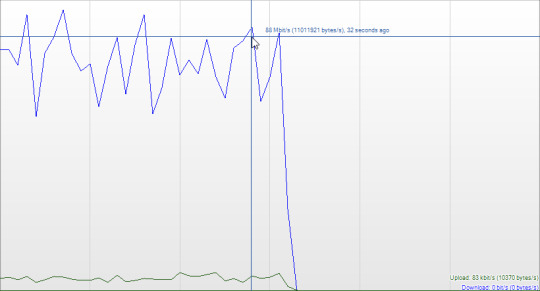
FUCKKKK my school frrr, network is totally capable of allocating me 86Mbp/s for JUST qBITTORRENT but instead of getting access to that we get throttled down to like >400Kbps if even.
#.txt#to explain what this graph is#the blue is my down speed#green is up speed#I have my vpn on and with port forwarding#which is able to circumvent my schools NAT protocol by forwarding the network traffic to a local port on my computer#(its technically remote port forwarding but)#and because I can get traffic directed to my machine a lot of the traffic that gets throttled by the networks security protocols#specifically NAT.( btw I am not inviting hostile activity onto the network I am just choosing to encrypt my data and verify authenticity#with a different protocol than NAT. specifically wireGuard which is the leading VPN protocol now)#however a lot of people dont like port forwarding because of that property and few VPNs support it anymore but its like the only way to#torrent at more than a snails pace#and so my school detected my high network activity and because of the encrypted data I was sending they literally just deny me service#I can just connect back with my regular PC no problem too so its not even stopping me#its just delaying me and making it annoying'
4 notes
·
View notes
Text
Proton Pass Review: Password Manager that Hides Your Email Address
Proton Pass Review: Password Manager that Hides Your Email Address @vexpert #vmwarecommunities #100daysofhomelab #homelab #ProtonPass #PasswordManager #EndToEndEncryption #HideMyEmailAliases #FreePasswordManager #ProtonServices #protonpasswordmanager
With identity theft and breached credentials all over the news, password managers have become necessary to help generate strong, unique passwords. Proton AG, a Swiss-based company revered for pioneering the world’s largest encrypted email service – Proton Mail, has introduced its take on a password manager solution. Known as Proton Pass, it brings an exciting blend of unique features, stringent…

View On WordPress
#data security#End-to-End Encryption#Free Password Manager#Hide My Email Aliases#open source#password manager#Proton Pass#Proton Services#Swiss Privacy Laws#Unlimited Logins
2 notes
·
View notes
Text
#Data Protection Act#Privacy Online#Online Privacy#Personal Data Protection#Data Breaches#Privacy Rights#Online Security#Protecting Personal Information#Secure Browsing#Encryption#VPN#HTTPS#Strong Passwords#Two-Factor Authentication#Privacy Settings#Safe Online Communication
2 notes
·
View notes
Text
Epilouge:


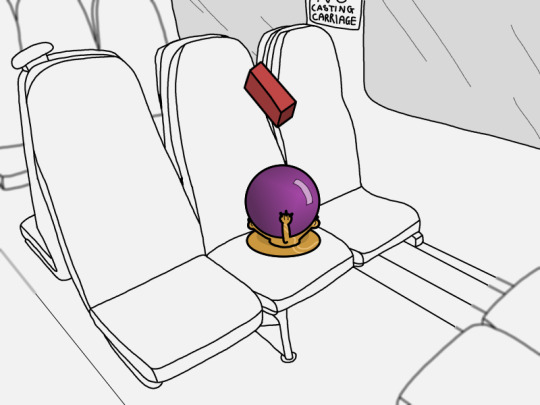
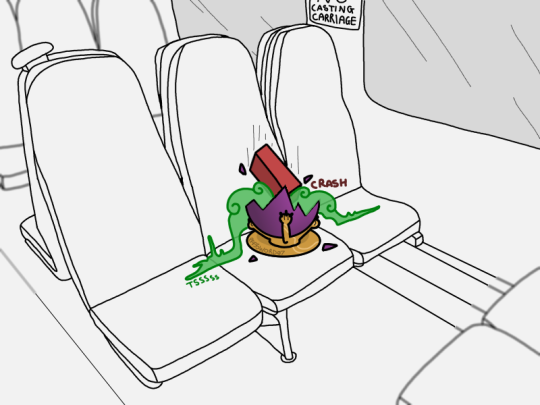


In a fantasy setting, my job would be exactly the same
#in my irl job to “brick” a device is to send a signal to it so as soon as it's turned on the hard drive encrypts itself#making the device useless and unusable#it's a security measure to ensure that if someone finds the device they can't access sensitive company data#yeah sure they can wipe the device and reinstall an OS and use it then#but IMPORTANTLY the company data is gone#we'll claim back the cost of the lost device from insurance#in a fantasy setting the solution to lost devices is more elegant#myart
33K notes
·
View notes
Text

Awesome! Scope's Quantum Security Mobile App Secures Funding Scope Technologies secures $1.5M to accelerate its QSE quantum security mobile app. Offering advanced, user-friendly quantum-resistant encryption and secure file sharing.
Read more
#quantum security#mobile app#data encryption#cybersecurity#quantum-resistant#Scope Technologies#QSE mobile app#First Majestic Silver
0 notes
Text
Sometimes, you genuinely need to talk about things that you don't want a company to see. Sometimes that can't happen in person, and snail mail is inconvenient.
Signal and Matrix and other e2e services are literally incapable of handing over your messages. The closest they could do if they wanted to hand over your data was to give the cops a series of hashes that correspond to your messages. The information necessary to decrypt the data is stored on your device. You can view the source code of both of these services to verify for yourself that this is the case, though it does require some technical understanding of the system. You don't need to trust the company, just the many users who have perused the code and given a thumbs up. Matrix is decentralized so it's not even like there's a single website that would be easy for law enforcement to ask about you from.
Emails are also not safe without e2e. People generally use PGP to encrypt their mail. I recommend proton mail to make that process simple.
I also generally feel fairly safe using voice calls to speak my mind, but that's not a "the company is literally incapable of doing anything with this data" (it could always be recorded without your knowledge), but a "this is impractical to store on servers solely in case they get served a warrant." I don't feel as safe using phone calls to speak my mind because to my understanding those can be more easily intercepted.
PSA: never discuss private affairs in your DMs, especially contraception and abortion. Social media moguls will absolutely sell you out to the government. There are already cases of people being charged based on evidence in their DMs.
#the one eyed man speaking to the blind#there's so much i don't know about cybersec but you shouldn't trust any company with your data but some companies really can't see your dat#(also if you want an encrypted secure version of googledocs try cryptpad)#also btw discord is not safe but afaict deleting messages does in fact delete messages from their servers but that's a rumor
78K notes
·
View notes
Text
Apple cedează presiunilor autorităților britanice: Criptarea end-to-end pentru iCloud, dezactivată în Marea Britanie
Apple a confirmat oficial că renunță la criptarea end-to-end oferită prin sistemul Advanced Data Protection (ADP) pentru utilizatorii iCloud cu conturi nou create în Regatul Unit, urmând ca și utilizatorii existenți să fie afectați de această decizie. Acest pas marchează un compromis semnificativ în politica de confidențialitate a companiei americane, realizat în urma presiunilor exercitate de…
#ADP#Advanced Data Protection#apple#backdoor#bam#cloud storage#Confidențialitate#criptare end-to-end#cybersecurity#data protection#diagnosis#diagnoza#end-to-end encryption#icloud#Marea Britanie#neamt#online security#privacy#Protecția datelor#Regatul Unit#roman#securitate cibernetică#securitate online#UK#United Kingdom
0 notes
Text
How Blockchain Can Revolutionize Genomic Data Security

In the era of precision medicine and personalized healthcare, genomic data has become one of the most valuable yet vulnerable assets. As medical researchers and biotech companies continue to harness the power of DNA sequencing, the security, privacy, and integrity of genomic data remain critical concerns. Blockchain technology, known for its decentralized and immutable nature, is emerging as a game-changer in securing genomic information.
Understanding the Need for Genomic Data Security
Genomic data contains highly sensitive personal information that can reveal an individual’s ancestry, predisposition to diseases, and even potential hereditary risks. The misuse or breach of such data can lead to severe consequences, including:
Privacy violations – Unauthorized access to genomic data can expose individuals to identity theft or discrimination.
Data manipulation risks – Traditional centralized databases are susceptible to hacking and unauthorized alterations.
Ethical concerns – Without proper security, genomic data can be exploited by insurance companies, employers, or other entities for unfair practices.
How Blockchain Enhances Genomic Data Security
Blockchain technology offers several advantages that address these security challenges in genomic data management:
1. Decentralization and Data Integrity
Unlike traditional centralized databases, blockchain operates on a decentralized network. This ensures that no single entity controls the genomic data, reducing the risk of data breaches and cyberattacks. Once genomic information is recorded on a blockchain, it becomes immutable—preventing unauthorized modifications or tampering.
2. Enhanced Privacy with Smart Contracts
Blockchain employs smart contracts, self-executing agreements that regulate data access. Genomic data owners can define who can view or use their data, ensuring complete privacy and control over personal genetic information. These smart contracts enable researchers or medical professionals to access anonymized data while keeping personally identifiable details secure.
3. Secure Data Sharing with Encryption
Blockchain facilitates encrypted and permissioned data sharing, allowing individuals to grant access to specific organizations while maintaining anonymity. This capability is particularly beneficial in genomic research, where secure data sharing can accelerate medical advancements without compromising patient privacy.
4. Transparency and Traceability
Every transaction on a blockchain is recorded with a timestamp, ensuring full traceability of who accessed genomic data and for what purpose. This transparency helps prevent unauthorized data usage while fostering trust among data providers, researchers, and institutions.
5. Protection Against Genetic Data Breaches
Traditional databases are frequent targets for cyberattacks, putting sensitive genomic data at risk. Since blockchain records are distributed across multiple nodes, hacking or breaching a single point becomes nearly impossible. This resilient infrastructure significantly enhances genomic data security.
Real-World Applications of Blockchain in Genomics
Several biotech companies and research institutions are already leveraging blockchain for genomic data security:
Nebula Genomics – Allows users to securely share genomic data with researchers using blockchain, ensuring privacy and compensation for data usage.
LunaDNA – A blockchain-based genomic data marketplace where individuals can monetize their genomic data securely.
EncrypGen – A decentralized genomic data exchange enabling secure transactions between data providers and researchers.
Challenges and Future Prospects
While blockchain presents a promising solution for genomic data security, challenges such as scalability, regulatory compliance, and integration with existing healthcare systems need to be addressed. However, as the technology evolves and adoption increases, blockchain is poised to reshape the future of genomic data privacy and security.
Conclusion
Blockchain technology offers an innovative approach to securing genomic data, ensuring privacy, transparency, and integrity. By leveraging decentralization, encryption, and smart contracts, individuals can maintain control over their genetic information while enabling groundbreaking medical research. As biotech and healthcare industries continue to embrace blockchain, the future of genomic data security looks more secure, private, and efficient than ever before.
This SEO-friendly article incorporates high-ranking keywords like genomic data security, blockchain in healthcare, decentralized data storage, privacy in genomics, etc., ensuring better visibility on search engines. Let me know if you'd like any refinements! 🚀
#biopractify#genomics#machinelearning#datascience#aiinbiotech#bioinformaticstools#biotech#biotechnology#biotechcareers#bioinformatics#blockchain#data security#cybersecurity#encryption
0 notes
Text

#PollTime Which service is a must for data security?
A) Firewall 🔥 B) Encryption 🔐 C) Backup 📂 D) Authentication 🛡️
Comments your answer below👇
💻 Explore insights on the latest in #technology on our Blog Page 👉 https://simplelogic-it.com/blogs/
🚀 Ready for your next career move? Check out our #careers page for exciting opportunities 👉 https://simplelogic-it.com/careers/
#simplelogic#makingitsimple#itcompany#dropcomment#manageditservices#itmanagedservices#poll#polls#data#security#datasecurity#firewall#encryption#backup#authentication#itservices#itserviceprovider#managedservices#testyourknowledge#makeitsimple#simplelogicit
0 notes
Video
youtube
Your Phone is a Blabbermouth - Stop It from Leaking Your Data Now
#youtube#Privacy Security Smartphone Data Tracking Protection Apps Encryption WiFi 2FA Settings Control
0 notes
Text
Exploring the Benefits of Psync's Two-Way Audio Camera
In today's world, home security is more important than ever, and Psync is leading the charge with its innovative Two-Way Audio Camera. This cutting-edge device not only allows you to monitor your home in real-time, but it also enables seamless communication with family members or pets from anywhere.
The Two-Way Audio feature is a game changer. It provides peace of mind by allowing you to check in on your loved ones and speak to them directly through the camera. Whether you're at work, on vacation, or just in another room, you can always stay connected.
Psync's cameras are designed with user-friendly technology that makes installation a breeze. With high-definition video quality and night vision capabilities, you can have clear visibility around the clock. The sleek design ensures that the camera fits perfectly into any home decor.
Moreover, Psync prioritizes security and privacy. The camera's encrypted data transmission ensures that your footage is safe from unauthorized access. You can enjoy the benefits of advanced home security without worrying about potential breaches.
In summary, Psync's Two-Way Audio Camera is an excellent investment for anyone looking to enhance their home security system. With its interactive features and superior design, it's a fantastic choice for keeping your home and loved ones safe.
#encrypted data transmission#privacy#home security#real-time monitoring#interactive features#user-friendly technology#advanced home security
0 notes