#End-to-End Encryption
Explore tagged Tumblr posts
Text
2 notes
·
View notes
Text
Proton Pass Review: Password Manager that Hides Your Email Address
Proton Pass Review: Password Manager that Hides Your Email Address @vexpert #vmwarecommunities #100daysofhomelab #homelab #ProtonPass #PasswordManager #EndToEndEncryption #HideMyEmailAliases #FreePasswordManager #ProtonServices #protonpasswordmanager
With identity theft and breached credentials all over the news, password managers have become necessary to help generate strong, unique passwords. Proton AG, a Swiss-based company revered for pioneering the world’s largest encrypted email service – Proton Mail, has introduced its take on a password manager solution. Known as Proton Pass, it brings an exciting blend of unique features, stringent…

View On WordPress
#data security#End-to-End Encryption#Free Password Manager#Hide My Email Aliases#open source#password manager#Proton Pass#Proton Services#Swiss Privacy Laws#Unlimited Logins
2 notes
·
View notes
Text
Apple cedează presiunilor autorităților britanice: Criptarea end-to-end pentru iCloud, dezactivată în Marea Britanie
Apple a confirmat oficial că renunță la criptarea end-to-end oferită prin sistemul Advanced Data Protection (ADP) pentru utilizatorii iCloud cu conturi nou create în Regatul Unit, urmând ca și utilizatorii existenți să fie afectați de această decizie. Acest pas marchează un compromis semnificativ în politica de confidențialitate a companiei americane, realizat în urma presiunilor exercitate de…
#ADP#Advanced Data Protection#apple#backdoor#bam#cloud storage#Confidențialitate#criptare end-to-end#cybersecurity#data protection#diagnosis#diagnoza#end-to-end encryption#icloud#Marea Britanie#neamt#online security#privacy#Protecția datelor#Regatul Unit#roman#securitate cibernetică#securitate online#UK#United Kingdom
0 notes
Text
youtube
JFC moment. Comrades. Fucking. Don't be naive.
0 notes
Text
End-to-End Encryption by CipherChat | Secure Your Conversations Today
Secure your conversations with CipherChat's End-to-End Encryption. Ensure complete privacy with encrypted messaging from sender to recipient. Protect sensitive business data with advanced security measures. Stay compliant with data protection regulations effortlessly. Explore CipherChat's features today! Website: https://cipherchat.co/

1 note
·
View note
Text
#encrypted phone#buy encrypted phone#secure smartphone#end-to-end encryption#encrypted phone brands#Samsung Knox#iOS encryption#encrypted smartphone buying guide
0 notes
Text
How Many Users Are There on Major Social Media Platforms in 2024?
Social media continues to be a pivotal part of our daily lives, shaping how we communicate, share information, and consume content. As of 2024, the landscape of social media is more expansive and influential than ever. But how many users are there on major social media platforms in 2024? Let’s dive into the latest statistics to understand the scale of this digital phenomenon. Facebook: 2.96…

View On WordPress
#2024 stats#audience demographics#augmented reality#business marketing#communication#community engagement#content creators#content sharing#creative ideas#digital era#digital landscape#digital phenomenon#End-to-End Encryption#engagement#ephemeral messaging#Facebook#global communication#Global Reach#industry insights#innovation#Instagram#internet users#LinkedIn#messaging app#online engagement#online platforms#personal connections#Pinterest#platform usage#professional networking
0 notes
Text
UPDATE! REBLOG THIS VERSION!
#reaux speaks#zoom#terms of service#ai#artificial intelligence#privacy#safety#internet#end to end encryption#virtual#remote#black mirror#joan is awful#twitter#instagram#tiktok#meetings#therapy
23K notes
·
View notes
Text
A Comprehensive Guide to Best Practices for Securing Cloud Infrastructure
One of the most major benefits of cloud infrastructure is its flexibility and scalability. However, with the convenience of cloud technology come significant security risks. Data breaches are becoming increasingly widespread, therefore enterprises must ensure their cloud infrastructure is safe. In this detailed Blog, we'll go into the best practices for safeguarding cloud infrastructure.
1. Secure Configurations:
Securing your cloud infrastructure begins with meticulous configuration practices. Organizations must ensure that all services and data stored in the cloud are shielded. Best practices include deploying secure passwords, implementing Multi-Factor Authentication (MFA), restricting access based on roles, and staying vigilant with regular software updates and patches.
2. Access Management:
With a surge in personnel accessing cloud infrastructure, robust access management is non-negotiable. Limiting access to information minimizes vulnerability exposure. Implementing access controls, segregation of duties, and regular access reviews form the bedrock of a secure access management strategy.
3. Data Encryption:
Data encryption stands as the guardian against unauthorized access. It's imperative to encrypt data at rest, in transit, during backups, and while in use. Best practices include adopting end-to-end encryption, leveraging industry-standard cryptography, and ensuring the secure management of encryption keys.
4. Network Security Measures:
The cloud's network is a potential vulnerability hotspot. Organizations must implement robust network security practices, including configuring firewalls and vigilant traffic monitoring. Regular network security assessments, encompassing internal and external communication channels, play a pivotal role in identifying and rectifying vulnerabilities in cloud infrastructure.
5. Incident Response:
Having a well-defined incident response plan is essential for navigating security storms. A detailed plan should include protocols for reporting, investigating, and responding to incidents. Regular training of response teams and conducting drills ensures the plan's effectiveness when the need arises.
Final Say:
While the advantages of cloud infrastructure are abundant, security should remain a steadfast priority. The best practices outlined in this guide serve as a shield, safeguarding your cloud environment from potential threats. By proactively implementing these security measures, organizations can establish a robust defense against cyber threats and ensure the safety and efficiency of their cloud infrastructure. Remember, a secure cloud is not just a technological necessity; it's a strategic imperative for the future of your business.
0 notes
Text

#fuck musk#musk coup#twitter#maintain operational security#use end to end encryption (it's a start)#trump regime
2K notes
·
View notes
Text
An adversarial iMessage client for Android
Adversarial interoperability is one of the most reliable ways to protect tech users from predatory corporations: that's when a technologist reverse-engineers an existing product to reconfigure or mod it (interoperability) in ways its users like, but which its manufacturer objects to (adversarial):
https://www.eff.org/deeplinks/2019/10/adversarial-interoperability
"Adversarial interop" is a mouthful, so at EFF, we coined the term "competitive compatibility," or comcom, which is a lot easier to say and to spell.
Scratch any tech success and you'll find a comcom story. After all, when a company turns its screws on its users, it's good business to offer an aftermarket mod that loosens them again. HP's $10,000/gallon inkjet ink is like a bat-signal for third-party ink companies. When Mercedes announces that it's going to sell you access to your car's accelerator pedal as a subscription service, that's like an engraved invitation to clever independent mechanics who'll charge you a single fee to permanently unlock that "feature":
https://www.techdirt.com/2023/12/05/carmakers-push-forward-with-plans-to-make-basic-features-subscription-services-despite-widespread-backlash/
Comcom saved giant tech companies like Apple. Microsoft tried to kill the Mac by rolling out a truly cursèd version of MS Office for MacOS. Mac users (5% of the market) who tried to send Word, Excel or Powerpoint files to Windows users (95% of the market) were stymied: their files wouldn't open, or they'd go corrupt. Tech managers like me started throwing the graphic designer's Mac and replacing it with a Windows box with a big graphics card and Windows versions of Adobe's tools.
Comcom saved Apple's bacon. Apple reverse-engineered MS's flagship software suite and made a comcom version, iWork, whose Pages, Numbers and Keynote could flawlessly read and write MS's Word, Excel and Powerpoint files:
https://www.eff.org/deeplinks/2019/06/adversarial-interoperability-reviving-elegant-weapon-more-civilized-age-slay
It's tempting to think of iWork as benefiting Apple users, and certainly the people who installed and used it benefited from it. But Windows users also benefited from iWork. The existence of iWork meant that Windows users could seamlessly collaborate on and share files with their Mac colleagues. IWork didn't just add a new feature to the Mac ("read and write files that originated with Windows users") – it also added a feature to Windows: "collaborate with Mac users."
Every pirate wants to be an admiral. Though comcom rescued Apple from a monopolist's sneaky attempt to drive it out of business, Apple – now a three trillion dollar company – has repeatedly attacked comcom when it was applied to Apple's products. When Apple did comcom, that was progress. When someone does comcom to Apple, that's piracy.
Apple has many tools at its disposal that Microsoft lacked in the early 2000s. Radical new interpretations of existing copyright, contract, patent and trademark law allows Apple – and other tech giants – to threaten rivals who engage in comcom with both criminal and civil penalties. That's right, you can go to prison for comcom these days. No wonder Jay Freeman calls this "felony contempt of business model":
https://pluralistic.net/2023/11/09/lead-me-not-into-temptation/#chamberlain
Take iMessage, Apple's end-to-end encrypted (E2EE) instant messaging tool. Apple customers can use iMessage to send each other private messages that can't be read or altered by third parties – not cops, not crooks, not even Apple. That's important, because when private messaging systems get hacked, bad things happen:
https://en.wikipedia.org/wiki/2014_celebrity_nude_photo_leak
But Apple has steadfastly refused to offer an iMessage app for non-Apple systems. If you're an Apple customer holding a sensitive discussion with an Android user, Apple refuses to offer you a tool to maintain your privacy. Those messages are sent "in the clear," over the 38-year-old SMS protocol, which is trivial to spy on and disrupt.
Apple sacrifices its users' security and integrity in the hopes that they will put pressure on their friends to move into Apple's walled garden. As CEO Tim Cook told a reporter: if you want to have secure communications with your mother, buy her an iPhone:
https://finance.yahoo.com/news/tim-cook-says-buy-mom-210347694.html
Last September, a 16-year old high school student calling himself JJTech published a technical teardown of iMessage, showing how any device could send and receive encrypted messages with iMessage users, even without an Apple ID:
https://jjtech.dev/reverse-engineering/imessage-explained/
JJTech even published code to do this, in an open source library called Pypush:
https://github.com/JJTech0130/pypush
In the weeks since, Beeper has been working to productize JJTech's code, and this week, they announced Beeper Mini, an Android-based iMessage client that is end-to-end encrypted:
https://beeper.notion.site/How-Beeper-Mini-Works-966cb11019f8444f90baa314d2f43a54
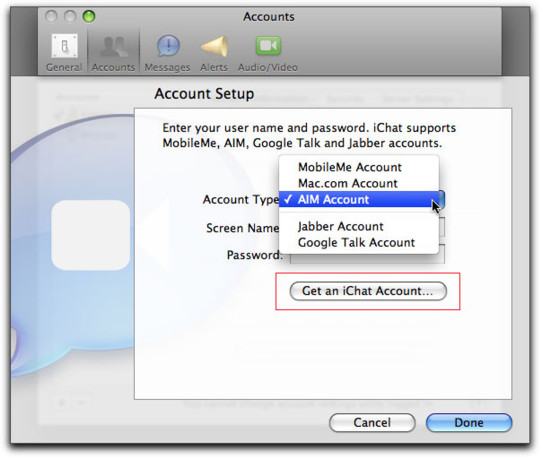
Beeper is known for a multiprotocol chat client built on Matrix, allowing you to manage several kinds of chat from a single app. These multiprotocol chats have been around forever. Indeed, iMessage started out as one – when it was called "iChat," it supported Google Talk and Jabber, another multiprotocol tool. Other tools like Pidgin have kept the flame alive for decades, and have millions of devoted users:
https://www.eff.org/deeplinks/2021/07/tower-babel-how-public-interest-internet-trying-save-messaging-and-banish-big
But iMessage support has remained elusive. Last month, Nothing launched Sunchoice, a disastrous attempt to bring iMessage to Android, which used Macs in a data-center to intercept and forward messages to Android users, breaking E2EE and introducing massive surveillance risks:
https://www.theverge.com/2023/11/21/23970740/sunbird-imessage-app-shut-down-privacy-nothing-chats-phone-2
Beeper Mini does not have these defects. The system encrypts and decrypts messages on the Android device itself, and directly communicates with Apple's servers. It gathers some telemetry for debugging, and this can be turned off in preferences. It sends a single SMS to Apple's servers during setup, which changes your device's bubble from green to blue, so that Apple users now correctly see your device as a secure endpoint for iMessage communications.
Beeper Mini is now available in Google Play:
https://play.google.com/store/apps/details?id=com.beeper.ima&hl=en_US
Now, this is a high-stakes business. Apple has a long history of threatening companies like Beeper over conduct like this. And Google has a long history deferring to those threats – as it did with OG App, a superior third-party Instagram app that it summarily yanked after Meta complained:
https://pluralistic.net/2023/02/05/battery-vampire/#drained
But while iMessage for Android is good for Android users, it's also very good for Apple customers, who can now get the privacy and security guarantees of iMessage for all their contacts, not just the ones who bought the same kind of phone as they did. The stakes for communications breaches have never been higher, and antitrust scrutiny on Big Tech companies has never been so intense.
Apple recently announced that it would add RCS support to iOS devices (RCS is a secure successor to SMS):
https://9to5mac.com/2023/11/16/apple-rcs-coming-to-iphone/
Early word from developers suggests that this support will have all kinds of boobytraps. That's par for the course with Apple, who love to announce splashy reversals of their worst policies – like their opposition to right to repair – while finding sneaky ways to go on abusing its customers:
https://pluralistic.net/2023/09/22/vin-locking/#thought-differently
The ball is in Apple's court, and, to a lesser extent, in Google's. As part of the mobile duopoly, Google has joined with Apple in facilitating the removal of comcom tools from its app store. But Google has also spent millions on an ad campaign shaming Apple for exposing its users to privacy risks when talking to Android users:
https://www.theverge.com/2023/9/21/23883609/google-rcs-message-apple-iphone-ipager-ad
While we all wait for the other shoe to drop, Android users can get set up on Beeper Mini, and technologists can kick the tires on its code libraries and privacy guarantees.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2023/12/07/blue-bubbles-for-all/#never-underestimate-the-determination-of-a-kid-who-is-time-rich-and-cash-poor
#pluralistic#multiprotocol#interoperability#adversarial interop#beeper#reverse engineering#blue bubbles#green bubbles#e2ee#end to end encrypted#messaging#jjtech#pypushbeeper mini#matrix#competitive compatibility#comcom
1K notes
·
View notes
Text


As a show of good faith toward the remaining Decepticons at the beginning of a new, united Cybertron, newly appointed Senators Bumblebee and Soundwave allowed Shatter and Dropkick to enlist into Autobot City's Defense Team.
These two turned out to be... not the best choices.
The city may have fallen to Insurgent Decepticon occupation had it not been for young recruits Hot Rod and Arcee's accidental interception of Shatter's communication with the fugitive Starscream.
To replace the errant Defense Team members, Springer and Blurr were reassigned from Iacon to Autobot City in their stead.
#my art#tf reconstruction#transformers#bumblebee movie#tf shatter#tf dropkick#maccadam#transformers au#semi-introduction to my idea for antagonists in tf:r - specifically being movie villains slotted into my au#bc if the main crux of the main reconstruction story in autobot city is about hot rod and her rise to becoming rodimus prime#which comes from the First movie - why not loosely adapt other movies too??#ive got ideas for most of them already - kinda jumping back and forth between the modern day story and my pre-war ''downfall'' story#which gives my brain a break from thinking about one to think about another#anyway - i imagine the first ''episode'' of tf:r would be like. hot rod shows up in autobot city on her first day > meets the team#> gets assigned arcee as her partner > arcee hates it > they over hear shatter talking to someone they don't recognise because rod's nosey#> huh that's weird > they intercept it next time by accident > its a communication to starscream about the city's defenses#> they take it to ultra magnus but they break the pad on the way because they were arguing about it#> ''hot rod i know you're new here. and you're intrigued about the war and everything. but we shouldn't be suspicious of everyone wearing a#purple badge. give them a chance.'' > arcee drops it bc she doesn't wanna start trouble + ''magnus will handle it. he always does somehow.'#> rod does not drop it and makes blaster monitor shatter's messages for anything unusual > blaster indulges her bc he's endeared to her#> he does end up intercepting an encrypted message > rod immediately acts and chases after shatter and dropkick on an outside-city mission#> arcee goes after her to stop her from fucking up really bad > blaster unencrypts the message. it's a rendezvous point to start an invasio#> magnus kup blaster and perceptor all head out to help the two young'uns before they get in over their heads#> rod and arcee meet and fight starscream and barely make it out by the skin of the teeth thanks to the more experienced autobots arrival#> starscream shatter dropkick and whoever else is there are driven off#> day is saved - magnus commends rod's gut instincts but rod goes back to what magnus said about not trusting bots with purple badges#> she was right this time but its an exception not a rule and most other decepticons in the city want to live in peace#> magnus also commends that attitude and the team head back > starscream starts plotting his Next Big Plan#''post credits'' scene of magnus putting the request in for springer and blurr + robot dinosaur opening its eye in the dark👀👀#longwinded but ya thats like the Clearest idea for Specific Events so far other things are Stuff I Want To Happen
52 notes
·
View notes
Text

The UK no longer has end to end encryption thanks to Keir Starmer’s Labour government reanimating the zombie policy that is the Snoopers Charter, first peddled by Theresa May’s Tory government and rejected by the public.
Apple withdrawing end-to-end encrypted backups from the UK "creates a dangerous precedent which authoritarian countries will surely follow".
UK now likened to authoritarian regimes and why Starmer won’t challenge Trump since he is in lock step with US policies, openly goes after sick, disabled, pensioners and poorest, increasing their hardship rather than tax the mega rich. US policy is UK policy.
So what does this mean for Apple users in the UK?
All your data in the cloud is no longer secure in comparison to having ADP enabled and can be accessed by the government upon request. The GDPR is all but dead in the UK, there are now so many government policies that snoop on us by the back door with even news outlets online now charging us for access without *cookies enabled (data farming you whilst you read with no option to opt out unless you pay)
I checked with the ICO myself and it is a fully approved policy despite its contradiction to the rights of consent, removed in the process.
If you want a workaround here are my suggestions
Cancel your iCloud storage, your data will stay on the cloud until the renewal date, use that time to back it up locally or on a flash drive.

Change your iMessage settings to delete audio messages after 2 minutes and permanently delete messages after 30 days.
Alternatively, use a third party messaging app with a delete on read feature and disable Apple iMessage altogether.
If you are tech savvy you can set up a USB drive or flash drive directly into your router hub (you should have at least one USB slot, some have two) and use FTP to back up over wifi, you can do this on any device, you don’t need a desktop.
Use a VPN service or set one up. If you’re really technical you can use a Raspberry Pi to do this, but you will need to hard code it. Think Mr Robot.
This change does not impact sensitive data like medical details which remain end to end encrypted.
If you want to learn more on the sweeping bills being pushed through government and any action your can take visit Big Brother Watch: https://bigbrotherwatch.org.uk
*If you want to read news articles without paying for the privilege of not handing over your cookie data, simply disable javascript within your browsers settings and refresh the browser page. Remember to turn it back on when your done. Alternatively disable all cookies but know this will impact your online experience and access.
#big brother watch#orwellian#labour government#data privacy#end to end encryption#apple#government#uk politics#equality#discrimination#the matrix#advance data protection#big brother#1984#distopia#keir starmer#authoritarian#totalitarian#fascisim#police state#Theresa May#gdpr#Information Commissioner's Office#ICO
17 notes
·
View notes
Text
Discord, one of the largest group chat apps in the world, announced on Tuesday that audio and video calls inside the platform will now be end-to-end encrypted (E2EE), meaning even Discord won’t know what users in those conversations talk about. In the last 10 years, end-to-end encrypted chat went from being a rare exception — think Skype in the mid-2000s — to a technology used by the world’s most popular chat apps, such as iMessage, WhatsApp, Signal, and Facebook Messenger, among others. Discord was born as a group chat platform for gamers, with an emphasis on audio calls for users playing online games together, but also became popular with people who simply want a place where a large number of people can interact.
Continue Reading
32 notes
·
View notes
Text
Man, I might be wrong for having this sensation, but this usanerican election results might not be entirely the population's fault.
Considering that y'all's voting is on paper and it ain't even the voters who decide the president, but the delegates of each state....
#how the fuck did y'all never noticed somethin wrong with the delegates thingy???#in other nations the ballot boxes are electronic#n' extremely protected with an end to end encryption that got no wifi to ensure that ALL the votes are safe from corruption#y'all live in a dictactorship atp#us politics#us elections#us presidents#2024 elections#elections 2024
9 notes
·
View notes
Text
Our Privacy Is In Serious Danger By The Government Right Now...
youtube
6 notes
·
View notes