#software for encryption
Explore tagged Tumblr posts
Text
#best encryption tools#computer security#cybersecurity#data breach prevention#data encryption guide#data privacy#data protection#data safety#data security tips#digital security#encrypting personal information#encryption basics#encryption FAQs#encryption for beginners#encryption software#encryption solutions#encryption techniques#guide to data encryption#how to encrypt data#online privacy#personal data security#prevent cyber attacks#privacy software#protect data online#secure communication#secure data encryption#secure files and folders#secure personal data#software for encryption#strong encryption methods
1 note
·
View note
Text
i love knowing people that know more about softwares than me. im pointing at the monitor with my mouth wide open in shock and they're just nodding like yeah you didnt have to do all that manually.
20 notes
·
View notes
Text
Signal has long said it'd "rather shut down or leave a market" than add a backdoor or weaken its encryption.
Apple also had this option when it was ordered by the UK government to build an iCloud backdoor. Apple could have said — without violating secrecy laws — why it was leaving the UK, rather than weaken the security of all of its UK customers.
Instead, Apple capitulated to the demand to keep operating, and prioritized its profits over its customers' security.
#human rights#privacy#invasion of privacy#signal#encryption#ukpol#ukgov#uk#class war#android#apple#boycott apple#apple music#appleradio#anti apple#fuck apple#icloud#software#firmware#app store#apps#app#ausgov#politas#auspol#tasgov#taspol#australia#fuck neoliberals#neoliberal capitalism
2 notes
·
View notes
Text
----------------------------------------------------------------------
INSTALLING: DATA ENCRYPTION SOFTWARE (cmbineencrpt.exe)
...
...
...
INSTALLATION: COMPLETE
WARNING: HUD AND INSTRUMENTS ARE: DAMAGED. PLEASE SEEK MEDICAL ATTENTION OR NEAREST COMBINE CHECKPOINT.
----------------------------------------------------------------------
#half life#creative writing#half life: non-citizen#hla#WELL thats a bit odd#what would you need encryption software for?#interesting#veeeery interesting.#hlnc#unfiction#half life combine#hl2
3 notes
·
View notes
Text
Why Your Business Needs a Cloud Video Platform Today
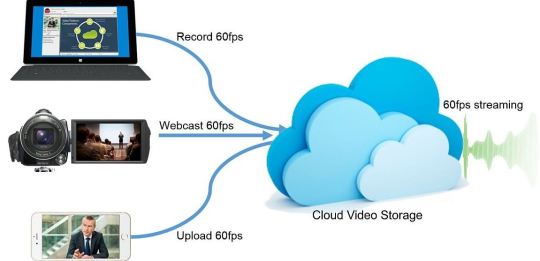
In the digital era, businesses are constantly looking for ways to enhance efficiency, reduce costs, and improve communication and collaboration. One of the technological advances that has been pivotal in achieving these objectives is the cloud video platform. This platform has revolutionized how businesses operate, offering a multitude of benefits ranging from improved communication strategies to expansive data analytics. Additionally, the cloud video platform provides scalable solutions that adapt to the needs of growing businesses, ensuring that they can maintain seamless operations. By facilitating remote work and virtual meetings, these platforms also contribute to better team collaboration and more efficient project management.
Key Benefits of Using Cloud Video Platform
A cloud video platform offers significant advantages to businesses, paramount among them being scalability, accessibility, enhanced collaboration, cost-effectiveness, and security. Understanding these benefits in detail can help organizations make informed decisions about adopting this technology, leading to more efficient operations, improved communication, and ultimately, a competitive edge in the market. Embracing cloud video solutions is a strategic move.
Scalability and Flexibility
One of the primary advantages of cloud video platform is their scalability. Businesses can effortlessly scale their video management needs up or down based on current demand without the need for significant upfront investments in hardware. This flexibility is crucial in adapting to business growth or changes without incurring additional costs or delays. Moreover, it allows companies to efficiently manage resources and respond promptly to evolving market conditions.
Accessibility and Reach
With a cloud video platform, videos can be accessed from anywhere, at any time, on any device with internet access. This global accessibility ensures that employees in different locations can easily participate in training sessions, meetings, and collaborations without the need for physical travel, further enhancing productivity across the organization. Additionally, it allows for seamless integration of remote and on-site teams, fostering a more connected and efficient workplace.
Enhanced Collaboration
A cloud video platform facilitates enhanced collaboration among teams by providing features such as real-time sharing, editing, and communication tools. These integrated features enable teams to work together more effectively, even when members are spread across various geographic locations. This real-time interaction significantly aids in quicker decision-making and problem-solving, ensuring that projects progress smoothly and efficiently regardless of physical distances.
Cost-Effectiveness
Moving to a cloud video platform can significantly reduce costs related to video content management. By leveraging cloud services, businesses eliminate the need for expensive on-premise infrastructure. Additionally, the maintenance and upgrading of systems are handled by the service provider, which can further decrease IT expenses. Furthermore, cloud platforms offer scalable solutions that allow businesses to pay only for the resources they use, optimizing budget allocation.
Security and Compliance
Security is a top concern for any business leveraging digital tools. The cloud video platform is equipped with robust security measures, including data encryption, secure access controls, and compliance with international standards. These features ensure that sensitive content remains protected against unauthorized access and breaches. Additionally, regular security audits and updates further enhance the platform's ability to safeguard valuable data, providing businesses with peace of mind and confidence in their digital security.
Improved Content Management and Analytics
A cloud video platform also offers advanced content management systems, allowing businesses to efficiently organize, manage, and retrieve video content with ease. Additionally, these platforms provide insightful analytics on viewer engagement, content performance, and other key metrics. This data-driven approach enables businesses to make informed decisions to optimize their video strategies, enhance viewer experience, and ultimately drive better results in their video marketing efforts.
Implementing Cloud Video Platform: Considerations and Best Practices
Implementing a cloud video platform yields significant benefits, but its success hinges on strategic planning and factor consideration. Vital elements encompass selecting an appropriate platform, meeting bandwidth needs, prioritizing user adoption tactics, and upholding data governance policies. These measures collectively shape a robust foundation for seamless integration and optimized performance.
Choosing the Right Platform
Selecting the appropriate cloud video platform is critical and should be based on specific business needs such as feature requirements, scalability, security, and compatibility with existing systems. Businesses should conduct thorough research or consult with experts to find the best fit.
Ensuring Adequate Bandwidth
Effective video streaming requires sufficient bandwidth. Before implementation, businesses need to assess their internet bandwidth to ensure smooth video playback and uploading capabilities without disrupting other business operations.
Focusing on User Adoption
To maximize the benefits of cloud video platform, promoting user adoption through training and support is essential. Employees need to understand how to use the platform efficiently and be comfortable with its features to fully leverage its capabilities.
Adhering to Data Governance
Businesses must also consider data governance when implementing cloud video platform. Ensuring that the platform complies with relevant laws and regulations regarding data privacy and protection is crucial.
Conclusion
The adoption of a cloud video platform can bring transformative benefits to businesses, fostering better communication and collaboration, providing scalability and flexibility, enhancing content management and analytics, reducing costs, and bolstering security. By leveraging cloud technology, organizations can streamline their operations and improve efficiency. Moreover, these platforms enable seamless remote work, support real-time collaboration, and offer advanced tools for data-driven decision-making. With careful planning and consideration of the key factors outlined above, organizations can effectively implement and use these platforms to achieve substantial business success, ensuring they stay competitive in an increasingly digital and connected world. please don’t hesitate to contact us via email or phone for further assistance!
#cloud video platform#secure video hosting#streaming video hosting#encrypted video hosting#drm encrypted video streaming#encrypted video streaming#DRM software#video hosting#security video#video platforms#online video platform#video watermark#DRM protected content#video cdn#wide vine#online courses#e-learning platforms#influencers#paid online courses#E-Learning Solutions#Digital content
2 notes
·
View notes
Text
Wonderful Web Wednesday 2
Testing Converso - Crnković
Converso was a messaging app meant to change the way people talked over the internet. It was released on the 21st of January, 2023 and is now gone from the internet. The only things left are a blog post exposing the absolutely rampant security flaws in their "state-of-the-art" encryption, and a couple of sponsored articles.
The article by Crnković was the catalyst that spun into the downfall of Converso. The post reads like an adventure book, telling the story of a great adventurer hacking and slashing through a field of broken promises.
The article begins by Crnković explaining how they heard about the app Converso. They had heard an ad for Converso on a podcast that presented Converso as an app that knew nothing about you or what you were talking about. From the perspective of someone who focuses a little bit on privacy, those sound like absolutely amazing promises. But from the perspective of a developer, I am a little skeptical, and so was Crnković.
This led them to digging into what was actually happening behind the scenes at Converso.
What they found is absolutely astonishing. I won't spoil a single bit here so go read it over at https://crnkovic.dev/testing-converso/!
Some secondary research (Spoilers)
Before writing this post, I decided to do some research into what Converso used to look like.
Here are the archives of the Converso website once at release and the other before the close - Converso's website at release - Converso's website near their closing
File Over App - Steph Ango
This quick essay by Steph Ango is an amazing 1 minute read. The essay explains that as we travel through the digital world, we deposit our data across hundreds of proprietary formats and servers. What happens when these formats and servers disappear? Where does the data that we have created go?
It just disappears to be lost forever.
There is a beauty in the way Steph Ango expresses their drive to durable data. They relate the files and data we create to the history our ancestors have left behind. Stone tablets, hieroglyphics, and ancient books have stood the test of time, proving to be information that is truly durable.
Making information that is durable is at the center of what Steph thinks tool makers need to account for when creating software. The tools that they create will not exist forever, but the data that their tools create should exist forever.
This is why Steph urges tool makers to give users access to their data in durable, transportable, and archivable formats. This way, if a user wants to see what they were doing 5 years or 5 decades ago, they can.
#wonderfulwebwednesday#wonderfulweb#files#app#software engineering#softwaredeveloper#encryption#blog#short reads#obsidian md#obsidian.md
4 notes
·
View notes
Text
I had a full on panic attack because I thought all my WIPs were gone bc I couldn't tell where one drive had hidden them.
getting new technology feels more infuriating every year. got a new computer for the first time in 8 years and everything about windows 11 and how it handles onedrive is driving me up the wall
#This was also when I found out that the backup software I was using had been putting my files into a proprietary encryption#And I couldn't just go in and find the back up of a file I was looking for#It was a real fun panic attack day for Sammy
23K notes
·
View notes
Text
Secure File Sharing: Best Free Encryption Tools in 2025
Introduction In an age where cyber threats are becoming more sophisticated by the day, file sharing without encryption is like sending a postcard—anyone can read it. Whether you’re a freelancer, student, small business owner, or just someone sending sensitive documents to a friend, using encrypted file-sharing tools is a must. The good news? You don’t need to spend a penny to do it securely. In…
#best free cloud encryption#end-to-end file sharing 2025#free encryption software#privacy-first file storage#secure file sharing tools
0 notes
Text
Dear Web Encryptor : Protect both Content and Source Code of HTML, HTML5, BootStrap website
https://codecanyon.net/item/dear-web-encryptor-protect-the-source-code-of-html-html5-bootstrap-website/19555597
Every day, several website owners become victims of people who steal Text Content, Image Content and HTML, HTML5, BootStrap codes. If you do not protect your Text Content, Image Content and Source Code, you could even allow your entire site to be cloned by such people, in minutes, even without any credit or profit to you. Using this software is the only way to protect your HTML, HTML5, BootStrap websites from being stolen.
#copy protection html#dear web encryptor#disable copy and paste html#disable copy web page#disable image download html#disable right click and selection html#dreamweaver#encrypt html5#html copy protection software#html encryption software#html image copy protection#html text copy protection#html5 copy protection#html5 encryption#prevent image download
0 notes
Text
United States encryption software market size reached USD 3.5 Billion in 2024. Looking forward, IMARC Group expects the market to reach USD 10.1 Billion by 2033, exhibiting a growth rate (CAGR) of 12.7% during 2025-2033. The growing cyber threats and data breaches in the United States, rising remote work and bring your own device (BYOD) policies, increasing need to comply with government regulations, and the growing volume of digital transactions represent some of the key factors driving the market.
#United States Encryption Software Market#United States Encryption Software Market size#United States Encryption Software Market share#United States Encryption Software Market forecast#United States Encryption Software Market 2024
0 notes
Text
Zoho Product Vulnerabilities: Exploring Legacy Issues and New Security Threats in 2023-2024 @zoho #ZohoOne #ManageEngine #ZohoCRM #ZohoBooks
Legacy Vulnerabilities in Zoho Products and New Discoveries in 2023-2024: A Comprehensive Analysis Introduction Zoho Corporation is one of the most well-established software development companies, offering a wide range of products that include customer relationship management (CRM), office suite applications, and cloud-based business tools. Over the years, Zoho has gained a massive following,…
#Cybersecurity threats#Software security 2024#Zero-day vulnerabilities#Zoho CRM API#Zoho Mail phishing#Zoho ManageEngine#Zoho security#Zoho Vault encryption#Zoho vulnerabilities
0 notes
Text
Folder Lock
If you have folders and files that you want to keep private, consider using Folder Lock. Unlike My Lockbox, it isn’t a free app, but it offers excellent configuration options and numerous methods to protect important and private documents from prying eyes. Folder Lock is a complete solution for keeping your personal files encrypted and locked, while automatically and in real-time backing up…
View On WordPress
#Data Encryption#Digital Wallets#Encryption Software#File Locking#File Management#File Security#File Shredding#password protection#Portable Security#privacy protection#Secure Backup#Windows Security
0 notes
Text
### The Benefits of Using Ubuntu Over Microsoft Windows in context of Today's Microsoft Outage
In the ever-evolving world of technology, choosing the right operating system (OS) can significantly impact your productivity, security, and overall user experience. While Microsoft Windows has long been a dominant player in the market, an increasing number of users are turning to Ubuntu for its robust security features and cost-effective solutions. Today, we delve into why Ubuntu is a superior…

View On WordPress
#Free operating system#Free software#Linux vs Windows#Microsoft Windows alternatives#Microsoft Windows outage#Open-source operating system#Switch to Ubuntu#Ubuntu#Ubuntu benefits#Ubuntu cost savings#Ubuntu encryption#Ubuntu firewall#Ubuntu security features#Ubuntu stability#Ubuntu vs Microsoft Windows#Ubuntu vs Windows security
0 notes
Text
DRM Video Encryption Software or DRM Player to protect your video content
128-bit DRM Video Encryption software with DRM Player which protects your videos & content from unauthorized access. Start your free trail now - iShieldProtect®. Start your free trail now 916400 6065
#DRM Video Encryption Software#DRM player#drm video protection software#drm player#drm protection software#drm video encryption#drm software for video#drmprotected video testing#drm protected video testing
0 notes
Text
Mastering Streaming Video Hosting for Beginners

Streaming Video Hosting has become a staple of media consumption, with platforms like YouTube, Netflix, and Twitch pushing the boundaries of how and where we watch videos. However, creating a smooth streaming experience requires meticulous attention to various technical and strategic factors. For content creators and streaming services, optimizing video content is crucial for reducing buffering, improving quality, and ensuring user satisfaction. This article explores the key strategies and technologies involved in optimizing video content for seamless streaming.
Understanding the Basics of Streaming Video Hosting
Streaming Video Hosting is the process of transmitting video files from a server to a user's device in real time. The user’s device decodes the data stream and plays the video without fully downloading it. To achieve seamless streaming, videos must be optimized in several ways, starting with compression and formatting.
Video Compression and Codecs
Video compression is essential to reduce the file size without significantly compromising video quality. Effective compression techniques make videos easier to transmit over various internet speeds. Codecs, which stand for "compressor-decompressor", are used to encode and decode digital video. Popular codecs include H.264, HEVC (H.265), and VP9. Each codec varies in terms of compression efficiency and compatibility with devices and browsers.
Adaptive Bitrate Streaming (ABS)
Adaptive Bitrate Streaming is a technique used to adjust the video quality in real time based on the viewer’s available bandwidth. ABS enhances the viewing experience by minimizing buffering and avoiding the degradation of video quality. Major streaming platforms utilize ABS to dynamically serve the best possible video quality at any given time.
Content Delivery Networks (CDNs)
Content Delivery Networks are another crucial element in optimizing video streaming. CDNs distribute the video content across various servers located in different geographical locations. When a user requests a video, it is served from the nearest server, which reduces latency, decreases buffering times, and improves load speeds.
Best Practices for Video Optimization
Beyond technical adjustments, several best practices can enhance the streaming video hosting experience:
Choose the Right Hosting Solution: Whether it’s a dedicated server, cloud hosting, or a CDN, selecting the right hosting solution based on the audience size and geographical spread is vital.
Opt for Multi-Bitrate Encoding: Offering multiple bitrate options allows the streaming video hosting service to adjust to different internet speeds and device capabilities.
Thoroughly Test Video Quality: Regular testing across different devices and network conditions is essential to ensure consistent video quality and functionality.
Monitor Analytics: Utilize analytics to understand viewer behavior, device usage, and network conditions to continuously refine streaming video hosting strategies.
Optimizing Mobile Streaming
With increasing mobile device usage, optimizing videos for mobile streaming video hosting is crucial. This includes ensuring that videos are encoded in mobile-friendly formats, using responsive design principles, and implementing touch-friendly player controls. Furthermore, considering the use of lighter mobile-specific codecs like VP9 can help in faster loading times and lower data consumption.
Enhancing User Experience (UX)
To ensure a seamless streaming video hosting experience, UX designers and developers should focus on creating an intuitive and engaging interface. Elements such as easy navigation, quick access to video controls, and minimal buffering contribute significantly to user satisfaction. Additionally, including features like video previews, quality selectors, and seamless transitions from one video to another can greatly enhance the viewing experience.
Facing Challenges in Streaming Video Hosting
Content creators and streaming video hosting services often face several challenges such as high bandwidth costs, varied internet speeds among users, and the need for massive scalability during peak times. To address these issues, implementing advanced compression technologies, using efficient transmission protocols, and scaling infrastructure dynamically are vital strategies.
Future Trends in Video Streaming
Looking ahead, emerging technologies such as AI-driven compression, edge computing, and 5G are set to revolutionize the streaming video hosting industry. AI can optimize encoding settings in real time for optimal quality and minimal bandwidth usage. Edge computing will help in processing data closer to the end user, reducing latency significantly. Additionally, the rollout of 5G technology promises substantially higher speeds and more reliable connections, which will further enhance streaming video hosting capabilities.
In conclusion, optimizing video content for seamless streaming video hosting involves a well-rounded approach that includes technical optimizations, strategic planning, and continual adaptation to emerging trends and technologies. By focusing on these aspects, content creators and streaming video hosting platforms can ensure high-quality, buffer-free experiences that meet the evolving demands of modern viewers. please don’t hesitate to contact us via email or phone for further assistance!
#streaming video hosting#cloud video platform#secure video hosting#drm encrypted video streaming#security video#drm software#online video platform
0 notes