#windows encryption software
Explore tagged Tumblr posts
Text
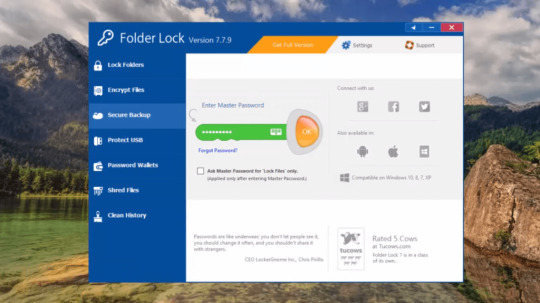
Folder Lock
If you have folders and files that you want to keep private, consider using Folder Lock. Unlike My Lockbox, it isn’t a free app, but it offers excellent configuration options and numerous methods to protect important and private documents from prying eyes. Folder Lock is a complete solution for keeping your personal files encrypted and locked, while automatically and in real-time backing up…
View On WordPress
#Data Encryption#Digital Wallets#Encryption Software#File Locking#File Management#File Security#File Shredding#password protection#Portable Security#privacy protection#Secure Backup#Windows Security
0 notes
Text
### The Benefits of Using Ubuntu Over Microsoft Windows in context of Today's Microsoft Outage
In the ever-evolving world of technology, choosing the right operating system (OS) can significantly impact your productivity, security, and overall user experience. While Microsoft Windows has long been a dominant player in the market, an increasing number of users are turning to Ubuntu for its robust security features and cost-effective solutions. Today, we delve into why Ubuntu is a superior…

View On WordPress
#Free operating system#Free software#Linux vs Windows#Microsoft Windows alternatives#Microsoft Windows outage#Open-source operating system#Switch to Ubuntu#Ubuntu#Ubuntu benefits#Ubuntu cost savings#Ubuntu encryption#Ubuntu firewall#Ubuntu security features#Ubuntu stability#Ubuntu vs Microsoft Windows#Ubuntu vs Windows security
0 notes
Text
An adversarial iMessage client for Android
Adversarial interoperability is one of the most reliable ways to protect tech users from predatory corporations: that's when a technologist reverse-engineers an existing product to reconfigure or mod it (interoperability) in ways its users like, but which its manufacturer objects to (adversarial):
https://www.eff.org/deeplinks/2019/10/adversarial-interoperability
"Adversarial interop" is a mouthful, so at EFF, we coined the term "competitive compatibility," or comcom, which is a lot easier to say and to spell.
Scratch any tech success and you'll find a comcom story. After all, when a company turns its screws on its users, it's good business to offer an aftermarket mod that loosens them again. HP's $10,000/gallon inkjet ink is like a bat-signal for third-party ink companies. When Mercedes announces that it's going to sell you access to your car's accelerator pedal as a subscription service, that's like an engraved invitation to clever independent mechanics who'll charge you a single fee to permanently unlock that "feature":
https://www.techdirt.com/2023/12/05/carmakers-push-forward-with-plans-to-make-basic-features-subscription-services-despite-widespread-backlash/
Comcom saved giant tech companies like Apple. Microsoft tried to kill the Mac by rolling out a truly cursèd version of MS Office for MacOS. Mac users (5% of the market) who tried to send Word, Excel or Powerpoint files to Windows users (95% of the market) were stymied: their files wouldn't open, or they'd go corrupt. Tech managers like me started throwing the graphic designer's Mac and replacing it with a Windows box with a big graphics card and Windows versions of Adobe's tools.
Comcom saved Apple's bacon. Apple reverse-engineered MS's flagship software suite and made a comcom version, iWork, whose Pages, Numbers and Keynote could flawlessly read and write MS's Word, Excel and Powerpoint files:
https://www.eff.org/deeplinks/2019/06/adversarial-interoperability-reviving-elegant-weapon-more-civilized-age-slay
It's tempting to think of iWork as benefiting Apple users, and certainly the people who installed and used it benefited from it. But Windows users also benefited from iWork. The existence of iWork meant that Windows users could seamlessly collaborate on and share files with their Mac colleagues. IWork didn't just add a new feature to the Mac ("read and write files that originated with Windows users") – it also added a feature to Windows: "collaborate with Mac users."
Every pirate wants to be an admiral. Though comcom rescued Apple from a monopolist's sneaky attempt to drive it out of business, Apple – now a three trillion dollar company – has repeatedly attacked comcom when it was applied to Apple's products. When Apple did comcom, that was progress. When someone does comcom to Apple, that's piracy.
Apple has many tools at its disposal that Microsoft lacked in the early 2000s. Radical new interpretations of existing copyright, contract, patent and trademark law allows Apple – and other tech giants – to threaten rivals who engage in comcom with both criminal and civil penalties. That's right, you can go to prison for comcom these days. No wonder Jay Freeman calls this "felony contempt of business model":
https://pluralistic.net/2023/11/09/lead-me-not-into-temptation/#chamberlain
Take iMessage, Apple's end-to-end encrypted (E2EE) instant messaging tool. Apple customers can use iMessage to send each other private messages that can't be read or altered by third parties – not cops, not crooks, not even Apple. That's important, because when private messaging systems get hacked, bad things happen:
https://en.wikipedia.org/wiki/2014_celebrity_nude_photo_leak
But Apple has steadfastly refused to offer an iMessage app for non-Apple systems. If you're an Apple customer holding a sensitive discussion with an Android user, Apple refuses to offer you a tool to maintain your privacy. Those messages are sent "in the clear," over the 38-year-old SMS protocol, which is trivial to spy on and disrupt.
Apple sacrifices its users' security and integrity in the hopes that they will put pressure on their friends to move into Apple's walled garden. As CEO Tim Cook told a reporter: if you want to have secure communications with your mother, buy her an iPhone:
https://finance.yahoo.com/news/tim-cook-says-buy-mom-210347694.html
Last September, a 16-year old high school student calling himself JJTech published a technical teardown of iMessage, showing how any device could send and receive encrypted messages with iMessage users, even without an Apple ID:
https://jjtech.dev/reverse-engineering/imessage-explained/
JJTech even published code to do this, in an open source library called Pypush:
https://github.com/JJTech0130/pypush
In the weeks since, Beeper has been working to productize JJTech's code, and this week, they announced Beeper Mini, an Android-based iMessage client that is end-to-end encrypted:
https://beeper.notion.site/How-Beeper-Mini-Works-966cb11019f8444f90baa314d2f43a54
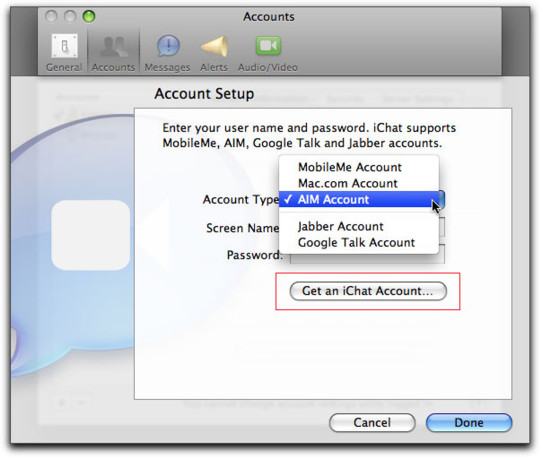
Beeper is known for a multiprotocol chat client built on Matrix, allowing you to manage several kinds of chat from a single app. These multiprotocol chats have been around forever. Indeed, iMessage started out as one – when it was called "iChat," it supported Google Talk and Jabber, another multiprotocol tool. Other tools like Pidgin have kept the flame alive for decades, and have millions of devoted users:
https://www.eff.org/deeplinks/2021/07/tower-babel-how-public-interest-internet-trying-save-messaging-and-banish-big
But iMessage support has remained elusive. Last month, Nothing launched Sunchoice, a disastrous attempt to bring iMessage to Android, which used Macs in a data-center to intercept and forward messages to Android users, breaking E2EE and introducing massive surveillance risks:
https://www.theverge.com/2023/11/21/23970740/sunbird-imessage-app-shut-down-privacy-nothing-chats-phone-2
Beeper Mini does not have these defects. The system encrypts and decrypts messages on the Android device itself, and directly communicates with Apple's servers. It gathers some telemetry for debugging, and this can be turned off in preferences. It sends a single SMS to Apple's servers during setup, which changes your device's bubble from green to blue, so that Apple users now correctly see your device as a secure endpoint for iMessage communications.
Beeper Mini is now available in Google Play:
https://play.google.com/store/apps/details?id=com.beeper.ima&hl=en_US
Now, this is a high-stakes business. Apple has a long history of threatening companies like Beeper over conduct like this. And Google has a long history deferring to those threats – as it did with OG App, a superior third-party Instagram app that it summarily yanked after Meta complained:
https://pluralistic.net/2023/02/05/battery-vampire/#drained
But while iMessage for Android is good for Android users, it's also very good for Apple customers, who can now get the privacy and security guarantees of iMessage for all their contacts, not just the ones who bought the same kind of phone as they did. The stakes for communications breaches have never been higher, and antitrust scrutiny on Big Tech companies has never been so intense.
Apple recently announced that it would add RCS support to iOS devices (RCS is a secure successor to SMS):
https://9to5mac.com/2023/11/16/apple-rcs-coming-to-iphone/
Early word from developers suggests that this support will have all kinds of boobytraps. That's par for the course with Apple, who love to announce splashy reversals of their worst policies – like their opposition to right to repair – while finding sneaky ways to go on abusing its customers:
https://pluralistic.net/2023/09/22/vin-locking/#thought-differently
The ball is in Apple's court, and, to a lesser extent, in Google's. As part of the mobile duopoly, Google has joined with Apple in facilitating the removal of comcom tools from its app store. But Google has also spent millions on an ad campaign shaming Apple for exposing its users to privacy risks when talking to Android users:
https://www.theverge.com/2023/9/21/23883609/google-rcs-message-apple-iphone-ipager-ad
While we all wait for the other shoe to drop, Android users can get set up on Beeper Mini, and technologists can kick the tires on its code libraries and privacy guarantees.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2023/12/07/blue-bubbles-for-all/#never-underestimate-the-determination-of-a-kid-who-is-time-rich-and-cash-poor
#pluralistic#multiprotocol#interoperability#adversarial interop#beeper#reverse engineering#blue bubbles#green bubbles#e2ee#end to end encrypted#messaging#jjtech#pypushbeeper mini#matrix#competitive compatibility#comcom
1K notes
·
View notes
Text
me when companies try to force you to use their proprietary software

anyway
Layperson resources:
firefox is an open source browser by Mozilla that makes privacy and software independence much easier. it is very easy to transfer all your chrome data to Firefox
ublock origin is The highest quality adblock atm. it is a free browser extension, and though last i checked it is available on Chrome google is trying very hard to crack down on its use
Thunderbird mail is an open source email client also by mozilla and shares many of the same advantages as firefox (it has some other cool features as well)
libreOffice is an open source office suite similar to microsoft office or Google Suite, simple enough
Risky:
VPNs (virtual private networks) essentially do a number of things, but most commonly they are used to prevent people from tracking your IP address. i would suggest doing more research. i use proton vpn, as it has a decent free version, and the paid version is powerful
note: some applications, websites, and other entities do not tolerate the use of VPNs. you may not be able to access certain secure sites while using a VPN, and logging into your personal account with some services while using a vpn *may* get you PERMANENTLY BLACKLISTED from the service on that account, ymmv
IF YOU HAVE A DECENT VPN, ANTIVIRUS, AND ADBLOCK, you can start learning about piracy, though i will not be providing any resources, as Loose Lips Sink Ships. if you want to be very safe, start with streaming sites and never download any files, though you Can learn how to discern between safe, unsafe, and risky content.
note: DO NOT SHARE LINKS TO OR NAMES OF PIRACY SITES IN PUBLIC PLACES, ESPECIALLY SOCAL MEDIA
the only time you should share these things are either in person or in (preferably peer-to-peer encrypted) PRIVATE messages
when pirated media becomes well-known and circulated on the wider, public internet, it gets taken down, because it is illegal to distribute pirated media and software
if you need an antivirus i like bitdefender. it has a free version, and is very good, though if youre using windows, windows defender is also very good and it comes with the OS
Advanced:
linux is great if you REALLY know what you're doing. you have to know a decent amount of computer science and be comfortable using the Terminal/Command Prompt to get/use linux. "Linux" refers to a large array of related open source Operating Systems. do research and pick one that suits your needs. im still experimenting with various dispos, but im leaning towards either Ubuntu Cinnamon or Debian.
#capitalism#open source#firefox#thunderbird#mozilla#ublock origin#libreoffice#vpn#antivirus#piracy#linux
697 notes
·
View notes
Text
Dove (part seven)
Leon Kennedy x female reader (bodyguard trope and the slowest, slow burn I swear)

Part one. Part two. Part three. Part four. Part five. Part six. Part seven.
---
A tense knot has formed right between Leon’s shoulder blades – can feel it pull when he tilts his head side to side, but it doesn’t seem to be loosening. Can’t even blame it on sleeping on the sofa cos he hasn’t laid down to sleep since the call with Hunnigan, stays sat up right. He’s athletic, he can jump up to his feet from horizontal but it’ll add a second or so to his reaction time and he’s not taking the risk.
He's on edge and he doesn’t like it. The ball of anxiety in his gut has saved his life more times than he can count, but it shouldn’t be necessary in this situation, should it? He’s set up in a safe house, literally off some beaten track in the middle of nowhere – location chosen and distributed by encrypted software so, technically, no-one in the DSO knows where he is either. It’s rigged up to the heavens with security measures - cameras, alarm systems, motion detector - explosion-proof windows, reinforced doors, all topped off with his favourite array of weapons in the duffel bag, currently resting by his still booted feet.
The objective of his mission hasn’t changed after the intel he’s received, that some foreign agency has had access to the CCTV feed for who knows how many hours before they were cut off. He should feel reassured that the quality of the footage was awful – it was only by how many times he’s encountered Lickers that he could even tell that’s what the creatures were when he’d be presented with the grainy images. He didn’t see the footage of you being rescued, but it would be a cruel kick in the gut to find that feed had been HD.
He lifts an arm – his left, keeping his right arm free, his accuracy is better by millimetres with his right – and rubs the knot, hoping to relieve the tension. It's not 100% confirmed they are looking or will be looking for you either, but why would anyone link up to the CCTV circuit if not to check on the outcome of their operation?
His immediate thought had been to up the frequency of his perimeter checks, one every two hours. He could do that at night, sure – military training taught him the correct and most efficient techniques to power nap – but in the day it would be harder without worrying you about what’s changed.
You wanted updates. Hell, you were entitled to updates. But he wants to give you good news, doesn’t wanna add to the weight on your shoulders with what could be nothing. It’s stupid, he knows it’s stupid, but in these sweet domestic moments the two of you have been sharing, he’s been pretending it’s something else – friends watching television, cooking a meal together – the sweet smiles the two of you exchange, but it’s all ripped apart the moment he has to do his checks. He can see the worry settle on your face then, a reminder of where you are with the flick of the safety off his gun and the twist of the lock as he goes outside to conduct surveillance.
Speaking of, his phone beeps for his next circuit on the building and he’s up on his feet in the blink of an eye. He pats his cargo pocket out of habit for the keys on the walk over to the garage door, but finds himself pausing outside your bedroom, his eyes focusing on the handle. You should still be pretty under with those sleeping pills – note to self, he’ll need to start weening you off them from now on, far too easy to get addicted. It wouldn’t hurt to just… check you were okay, would it?
No – that’s what you’re here, why he’s here – to protect you.
It would just be doing his job.
He presses down on the handle and slowly opens the door, breath caught in his throat. It takes his eyes a moment to adjust to the dark, the lamp in the living room not quite reaching as far as your bed, but eventually he can make out your face – as peaceful as he’s ever seen it.
You’re on your side. The position doesn’t look like it would be comfortable with your arm still strapped up in the sling, but it’s testimony to how well the sleeping pills are working. Your other arm is up by your face, hand clenched in a tight fist around something. He steps forward without thinking, curious what it could be.
Your fingers are gripped tightly around his watch.
And there’s a pain in his chest that feels like they’re gripped around his heart as well.
That settles it - he’s not gonna tell you about the hacked CCTV feed. He will tell you that Hunnigan hasn’t searched your place yet, that they’ve restarted the surveillance department – she’d asked him to ask you if you knew anything about the servers since they were appeared to be working from square one – but that was it.
Leon steps back with unnecessary caution, leaving the bedroom as silently as he entered and shuts the door with a soft click. He takes a deep breath, pats down his pockets again and heads out to circle the perimeter.
And, just like after you kissed his cheek, he does it twice.
--
You wake up after another peaceful and dreamless sleep, though it still takes a moment to remember where you are as you stare up at the unfamiliar ceiling. You wonder if tomorrow you’ll not experience that flicker of panic, just get up and accept that you’ll be picking today’s outfit out of a selection of clothes that you’re not sure if anyone’s worn before you.
You feel sore, as seems to be becoming the norm, but with unusually stiff fingers on your good hand. It seems you’ve clutched Leon’s watch all night. You’d fallen asleep quite quickly – all thanks to those sleeping pills – but you remember looking at it when you’d first got in the bed, the seconds ticking by lulling you to sleep. The fact that you’ve held it for so long reminds you of when you were a kid and snuggled up with a stuffed toy for comfort, except instead of something soft and cuddly, it’s what appears to be a top of line timepiece. There’s a lot of information contained on the face of the dial but there’s the time is the only one you really care about – 0906.
You get to your feet, raising your good arm to a grunt of protest as you try and run your fingers through your hair in lieu of a mirror. Huh, that pain’s new. Your hair is definitely due a wash now, but that’s an issue for later. You pull on a pair of sweatpants one-handed – you’ll be a pro soon, you’re sure of it – and put Leon’s watch in the pocket for safekeeping. It’d be difficult to try and navigate the door handle with it still gripped in your good hand and you’d hate to scratch it up.
You open the door cautiously – you hadn’t seen Leon asleep yet, but he must do at some point. Maybe you should offer to alternate the sofa and the bed? Though you have a feeling that he’s far too much of a gentleman to accept.
Or there’ll be something in the rules that prohibits that.
There’s no danger of waking him though - the agent in question is performing sit-ups in the middle of the living room floor, facing the other way. Muscular arms behind his head as he lets out little puffs of exertion at the exercise, alternating sides as he twists.
Wary that you don’t want to be caught staring, you shut the door with more force than necessary behind you and greet him with a smile when he looks over his shoulder.
“Morning, Leon.”
“Dove!” He doesn’t even sound out of breath. “Morning. Sleep okay?” He jumps up to his feet before taking a couple of steps over in your direction. There’s a grin on his face at the sight of you – makes you feel giddy.
“Yeah, thanks. How about you?”
“That’s good. Yeah, I slept fine.” He nods. It’s not a lie – he did sleep fine for the position he forced himself to maintain all night, despite the slight crick in his neck.
“Is that how you usually start your mornings?”
One of the arms you’d been admiring goes up to rub the back of his head again. “Kinda. I usually go for a run, but…”
“But you can’t leave me on my own.” You finish, smile dropping a little. “Sorry.”
“Don’t be - I’m not.” He drops his arm back down, casting an eye over a watch that’s not there. “Hey, you hungry? I can get breakfast started. Oatmeal again?”
“Sure.” You nod, fishing his watch out of your pocket and holding it out to him. “Thanks again for this. It was nice to wake up and know the time this morning.”
“Don’t mention it. You can, er, you know, keep it. If you like.” He can’t get the image of you fast asleep last night, clutching it close to your face. He knows it was most likely the sleeping pills meaning you’d just passed out with it in your hand more than anything deeper, but, hey, a guy can pretend.
“I’ll be okay, I can get the time off the TV during the day.” You hold it out again with insistence. “But maybe… maybe I could have it for the night again?”
“Deal.” Leon hastily agrees, his fingers brushing yours as he takes back the watch before fastening it around his wrist. “Breakfast coming right up.”
You take the opportunity to duck into the bathroom as he heads towards the kitchen – your heart warmed once more by the sight of the blob of toothpaste sat ready and waiting on your toothbrush.
--
“And, finally, oatmeal.” He places it down on the coffee table, alongside your coffee, a glass of water and your morning dose of painkillers.
“Thank you.” You lean forward to pick up the spoon, smiling back at the face that Leon’s drizzled in honey atop your breakfast again.
“Nah, pleasure’s all mine.” He calls over his shoulder as he picks up his own bowl from the kitchen. He hesitates for a second, before choosing to sit the other end of the sofa to you, rather than the opposite one.
“You know, I don’t get to do this very often. It’s nice.”
“Mm,” you swallow a spoonful of oatmeal. “Thought you said you’d been in lots of safe houses.”
“A fair amount. But, no, not that part. I mean, eating breakfast with someone.” “So…” You stir the spoon around the bowl, hoping it might prove a perfect segway into something you’d been wondering. “..there’s no-one at home for you?”
“Me?” He seems to scoff at the idea. “Nope.”
“Me neither.”
“Yeah, I figured.” He replies casually, before his blue eyes widen in alarm at how it might come across. “
“I mean, just by the fact that you hadn’t mentioned anyone at your apartment that morning and you hadn’t asked any of those sorta questions, you know, if they’d been told about what happened, where you are...”
He’s flustered, feels like he’s really putting his foot in his mouth this morning. He can take the lead in the interrogation of some of the world’s most despicable humans, for goodness’ sake, he should be able to talk to a pretty girl.
“Yeah, I figured.” You tease back and he swears he feels the weight lift off his shoulders.
The two of you eat in silence for a moment when curiosity gets the better of you. “So, you didn’t eat breakfast with the… others?”
“Nope.” His tone is firm as he recalls some of his previous charges. “Certainly didn’t make them it either. Trust me – they were nowhere near as nice or as deserving of my protection as you are, Dove.” The comment makes your head tingle.
“It’s all been people ‘realising’ how deep they’d sank but only grew a conscience to save their own skin. Hell, you might have even performed surveillance on some of them. A lot of criminals finally show backbone when they realise their time is running out.”
“Well, I’m glad to make a change – both for sharing breakfast and …safe house occupancy with.”
“A nice change,” he mumbles, but you still hear.
--
After breakfast, you go to shower and Leon sets himself to task with the dishes once again, says he did his last perimeter check before nine. Removing the sling proves trickier than yesterday – when you go to tug off the Velcro your opposite shoulder smarts with a similar pain of that morning, causing you to hiss through your teeth, something which the painkillers from breakfast don’t seem to have alleviated.
You step into the cubicle after undressing – the hot water immediately somewhat soothing on your bruised shoulders but you still struggle to get what you now deem as your good arm high enough to even entertain the possibility of washing your hair.
You try and avoid your reflection in the mirror when you dress, though you know you’ll have to confront your hair at some point. Unfortunately, you catch a glimpse – a greasy mop sat upon your head that makes your heart sink.
There must be a trick to it – other people must wash their hair one-handed all the time, but maybe they can lift an arm above their head. If you were home, you’d go to a salon, you think – an expensive you would deem necessary for your sanity.
A thought flashes across your mind – a ridiculous one. Leon is already doing so much for you, surely this would be completely over the line.
But you could… ask, couldn’t you? The worst he could do was say no, it would be awkward, and maybe there’s a hat in the duffel bag you’ve yet to discover.
You open the bathroom door, but don’t make to step over the threshold. Leon looks over from the sofa – dishes now drying in the rack besides the sink - and clocks your hesitation.
“Need a hand with the sling?”
Are you really going to ask him this?
You’ll break at some point - you know you will, so why not get it over with now? You’re a regimented two-day wash kinda girl and it’s day three. Not to be completely vain, but you’re covered with bruises and cuts, dressed in less than flattering clothes that aren’t yours and it would be nice to feel somewhat decent about something in your appearance.
Especially with the handsome company you’re keeping. Hell, Leon could be a model, a hair model too. There’d been shampoo and conditioner in the shower and you certainly hadn’t used it.
“Dove?” You’ve taken too long to reply again, getting stuck in your spiralling thoughts.
“I know this isn’t what you’re here for.” The words tumble out of your mouth before you can think further.
“Okay…” Leon's eyebrow is raised, a curious smile now fixed on his lips as he gets to his feet.
“And say no, obviously. Please. Just… I’d like to wash my hair.” You drop your eyes then – maybe it’ll be easier if you talk to your feet rather staring into his kind eyes?
"Right."
“And I’d… You know, I’d go to a salon and get it done there if we weren’t… here.”
“You’d like me to help you wash your hair?” There’s a tone of amusement or maybe disbelief in his tone.
Hearing him say it aloud makes you doubt the entire exercise, your heart begin to pound at your stupidity. “Sorry. No, I don’t know what I was thinking. It was stupid to ask-“
“Hey, no, it makes sense.” He soothes, immediately wanting to ease your frustrations. “You can’t lift your arm above your head, right? My fault for not thinking about that.”
You look up then, seeing the sincerity on his face – like it truly was his fault that you couldn’t wash your own damn hair.
“I can do that, Dove. I don’t see why not.”
“Are you sure?”
“Mm-hm. As you said, if you were anywhere else right now, you could go to a salon and whilst I can’t promise their quality, I seem to do all right with my own.” He shrugs. “You thinking over the sink?”
He doesn’t know why he asks – it’s hardly like you’re going to ask him to get in the shower with you.
Is it?
“I think so.” You look around the living area, though you’re well acquainted with what feels like every square inch of it now. “Though it might be a little awkward since we don’t have any chairs.”
He snaps his fingers. “Nah, there might be one in the garage, actually. Lemme check.”
He barely makes it into the garage when his cell vibrates in his pocket – one new message from Hunnigan.
Any server information for me?
Leon finds the folding chair nestled at the side of the washer and dryer and hesitates over the text back.
He’ll wash your hair – seeing how torn up you’d been about even asking him had made him feel awful - then he’ll give you the updates and ask about the servers.
He picks up the chair and tucks it under one arm, swiftly typing out a message on his cell and clicks send.
Not yet – Dove’s still asleep.
---
Masterlist . Requests welcome . Commissions/Ko-Fi
Comments, follows, likes and reblogs make my day!
Part eight.
305 notes
·
View notes
Note
stone faced anon (💫 anon if it's free) here; as someone who has a hyperfixation in IT and coding I also think it would be very funny if Boothill had an s/o who wasn't necessarily a mechanic but like a software engineer or just a real big nerd about coding or something. He'll be experiencing a malfunction or a memory leak and go "oh yeah this happens sometimes don't worry about it" and then 10 minutes later he's sitting down plugged into a laptop listening to his s/o rant about how terrible his code is (crack hc: boothill's code was written in javascript) and how it's a wonder he hasn't bricked* yet
Would also be mad funny if Boothill ever got hacked and his s/o basically says "no you're not" and uses a previously made system restore point or something because of course they would both use and design every feature imaginable to keep Boothill in control of his own body, can you imagine the stress that losing control would cause him?? Even better if whoever designed him originally intentionally left a backdoor incase he ever went against their orders and when they try to use it his s/o just goes "oh yeah I quarantined and encrypted all the old files related to that backdoor and whatever else you were planning on a partition as bait and personally rewrote every file and function involved since your code is *an actual crime against technology*. by the way i'm going to go ahead and format that partition i mentioned, boothill- we won't be needing anything on it now that we can trace whoever made it. trust me, this won't be happening ever again."
*(bricking is a term mostly used to refer to hardware that's been rendered basically completely nonfunctional and beyond saving by using it wrong, mostly by messing with system files. Kinda like how windows can't even repair itself if you delete the system32 folder. Though i guess you could still install it with a usb stick if you formatted your pc- i digress you get what I mean. also since this almost happened to me recently: if you manage to fill up a hard drive to the brim, with literally 0 bytes of space left, that bricks it. reminder to check your storage thoroughly and often!)
Honestly wow I read it all and I'm a little bit speechless 🥹 thank you 💫 anon, it was great 🙏

Boothill would DEFINITELY appreciate a s/o who's a tech savvy in general! I think at some point, he'd be pretty shocked you're so knowledgeable and just sit there, listening to you rant.. and just letting you do your thing.
Don't get me wrong, he definitely knows a lot about his body, his system and the way he works, but once you start to get in the zone and explain stuff to him, berate his code even, he just sits next to you, plugged in to your laptop, leaning his cheek against his hand listening to you like he obviously understands everything you say.
His other hand begins to gently play with a stand of your hair, humming deeply when the soft clicking sounds of your keyboard reach his ears; he twirls your hair with his fingers and chuckles, "mmm, really now?" Boothill raises an eyebrow, "encryptin' this, encryptin' that... How about we do somethin' more fun instead?" And then you shut him down from your laptop (😭).
Jokes aside, he'd feel very secure with you especially when he first got his new body, just knowing you'll probably fix a lot of things that could possibly blow up his face in no time, maybe even improve his life even more.
#honkai star rail#honkai star rail x reader#hsr x reader#boothill x reader#boothill hsr#boothill#.💫 anon#.anon thirst
245 notes
·
View notes
Text
On Personal InfoSec
Been awhile since I've had one of these posts but I figure with all that's going on in the world it's time to make another one of these posts and get some stuff out there for people. A lot of the information I'm going to go over you can find here:
So if you'd like to just click the link and ignore the rest of the post that's fine, I strongly recommend checking out the Privacy Guides.
Browsers:
There's a number to go with but for this post going forward I'm going to recommend Firefox. I know that the Privacy Guides lists Brave and Safari as possible options but Brave is Chrome based now and Safari has ties to Apple. Mullvad is also an option but that's for your more experienced users so I'll leave that up to them to work out.
Browser Extensions:
uBlock Origin: content blocker that blocks ads, trackers, and fingerprinting scripts. Notable for being the only ad blocker that still works on Youtube.
Privacy Badger: Content blocker that specifically blocks trackers and fingerprinting scripts. This one will catch things that uBlock doesn't catch but does not work for ads.
Facebook Container: "but I don't have facebook" you might say. Doesn't matter, Meta/Facebook still has trackers out there in EVERYTHING and this containerizes them off away from everything else.
Bitwarden: Password vaulting software, don't trust the password saving features of your browsers, this has multiple layers of security to prevent your passwords from being stolen.
ClearURLs: Allows you to copy and paste URL's without any trackers attached to them.
VPN:
Note: VPN software doesn't make you anonymous, no matter what your favorite youtuber tells you, but it does make it harder for your data to be tracked and it makes it less open for whatever network you're presently connected to.
Mozilla VPN: If you get the annual subscription it's ~$60/year and it comes with an extension that you can install into Firefox.
Proton VPN: Has easily the most amount of countries serviced, can take cash payments, and does offer port forwarding.
Email Provider:
Note: By now you've probably realized that Gmail, Outlook, and basically all of the major "free" e-mail service providers are scraping your e-mail data to use for ad data. There are more secure services that can get you away from that but if you'd like the same storage levels you have on Gmail/Outlook.com you'll need to pay.
Proton Mail: Secure, end-to-end encrypted, and fairly easy to setup and use. Offers a free option up to 1gb
Tuta: Secure, end-to-end encrypted, been around a very long time, and offers a free option up to 1gb.
Email Client:
Thunderbird if you're on Windows or Linux
Apple Mail if you're on macOS
Cloud Storage:
Proton Drive: Encrypted cloud storage from the same people as Proton Mail.
Tresorit: Encrypted cloud storage owned by the national postal service of Switzerland. Received MULTIPLE awards for their security stats.
Peergos: decentralized and open-source, allows for you to set up your own cloud storage, but will require a certain level of expertise.
Microsoft Office Replacements:
LibreOffice: free and open-source, updates regularly, and has the majority of the same functions as base level Microsoft Office.
OnlyOffice: cloud-based, free, and open source.
Chat Clients:
Note: As you've heard SMS and even WhatsApp and some other popular chat clients are basically open season right now. These are a couple of options to replace those.
Signal: Provides IM and calling securely and encrypted, has multiple layers of data hardening to prevent intrusion and exfil of data.
Molly (Android OS only): Alternative client to Signal. Routes communications through the TOR Network.
Briar: Encrypted IM client that connects to other clients through the TOR Network, can also chat via wifi or bluetooth.
Now for the last bit, I know that the majority of people are on Windows or macOS, but if you can get on Linux I would strongly recommend it. pop_OS, Ubuntu, and Mint are super easy distros to use and install. They all have very easy to follow instructions on how to install them on your PC and if you'd like to just test them out all you need is a thumb drive to boot off of to run in demo mode.
If you game through Steam their Proton emulator in compatibility mode works wonders, I'm presently playing a major studio game that released in 2024 with no Linux support on it and once I got my drivers installed it's looked great. There are some learning curves to get around, but the benefit of the Linux community is that there's always people out there willing to help.
I hope some of this information helps you and look out for yourself, it's starting to look scarier than normal out there.

#information security#infosec#computer security#computer infosec#personal infosec#browsers#internet browser#email#instant messaging#cloud storage#linux#pop os#linux mint#ubuntu#firefox#firefox extensions#long post
67 notes
·
View notes
Text
The eye-popping scandal surrounding the Trump cabinet’s accidental invitation to The Atlantic’s editor in chief to join a text-message group secretly planning a bombing in Yemen has rolled into its third day, and that controversy now has a name: SignalGate, a reference to the fact that the conversation took place on the end-to-end encrypted free messaging tool Signal.
As that name becomes a shorthand for the biggest public blunder of the second Trump administration to date, however, security and privacy experts who have promoted Signal as the best encrypted messaging tool available to the public want to be clear about one thing: SignalGate is not about Signal.
Since The Atlantic’s editor, Jeffrey Goldberg, revealed Monday that he was mistakenly included in a Signal group chat earlier this month created to plan US airstrikes against the Houthi rebels in Yemen, the reaction from the Trump cabinet’s critics and even the administration itself has in some cases seemed to cast blame on Signal for the security breach. Some commentators have pointed to reports last month of Signal-targeted phishing by Russian spies. National security adviser Michael Waltz, who reportedly invited Goldberg to the Signal group chat, has even suggested that Goldberg may have hacked into it.
On Wednesday afternoon, even President Donald Trump suggested Signal was somehow responsible for the group chat fiasco. “I don't know that Signal works,” Trump told reporters at the White House. “I think Signal could be defective, to be honest with you.”
The real lesson is much simpler, says Kenn White, a security and cryptography researcher who has conducted audits on widely used encryption tools in the past as the director of the Open Crypto Audit Project: Don’t invite untrusted contacts into your Signal group chat. And if you’re a government official working with highly sensitive or classified information, use the encrypted communication tools that run on restricted, often air-gapped devices intended for a top-secret setting rather than the unauthorized devices that can run publicly available apps like Signal.
“Unequivocally, no blame in this falls on Signal,” says White. “Signal is a communication tool designed for confidential conversations. If someone's brought into a conversation who’s not meant to be part of it, that's not a technology problem. That's an operator issue.”
Cryptographer Matt Green, a professor of computer science at Johns Hopkins University, puts it more simply. “Signal is a tool. If you misuse a tool, bad things are going to happen,” says Green. “If you hit yourself in the face with a hammer, it’s not the hammer’s fault. It’s really on you to make sure you know who you’re talking to.”
The only sense in which SignalGate is a Signal-related scandal, White adds, is that the use of Signal suggests that the cabinet-level officials involved in the Houthi bombing plans, including secretary of defense Pete Hegseth and director of national intelligence Tulsi Gabbard, were conducting the conversation on internet-connected devices—possibly even including personal ones—since Signal wouldn’t typically be allowed on the official, highly restricted machines intended for such conversations. “In past administrations, at least, that would be absolutely forbidden, especially for classified communications,” says White.
Indeed, using Signal on internet-connected commercial devices doesn’t just leave communications open to anyone who can somehow exploit a hackable vulnerability in Signal, but anyone who can hack the iOS, Android, Windows, or Mac devices that might be running the Signal mobile or desktop apps.
This is why US agencies in general, and the Department of Defense in particular, conduct business on specially managed federal devices that are specially provisioned to control what software is installed and which features are available. Whether the cabinet members had conducted the discussion on Signal or another consumer platform, the core issue was communicating about incredibly high-stakes, secret military operations using inappropriate devices or software.
One of the most straightforward reasons that communication apps like Signal and WhatsApp are not suitable for classified government work is that they offer “disappearing message” features—mechanisms to automatically delete messages after a preset amount of time—that are incompatible with federal record retention laws. This issue was on full display in the principals’ chat about the impending strike on Yemen, which was originally set for one-week auto-delete before the Michael Waltz account changed the timer to four-week auto-delete, according to screenshots of the chat published by The Atlantic on Wednesday. Had The Atlantic’s Goldberg not been mistakenly included in the chat, its contents might not have been preserved in accordance with long-standing government requirements.
In congressional testimony on Wednesday, US director of national intelligence Tulsi Gabbard said that Signal can come preinstalled on government devices. Multiple sources tell WIRED that this is not the norm, though, and noted specifically that downloading consumer apps like Signal to Defense Department devices is highly restricted and often banned. The fact that Hegseth, the defense secretary, participated in the chat indicates that he either obtained an extremely unusual waiver to install Signal on a department device, bypassed the standard process for seeking such a waiver, or was using a non-DOD device for the chat. According to political consultant and podcaster Fred Wellman, DOD “political appointees” demanded that Signal be installed on their government devices last month.
Core to the Trump administration’s defense of the behavior is the claim that no classified material was discussed in the Signal chat. In particular, Gabbard and others have noted that Hegseth himself is the classification authority for the information. Multiple sources tell WIRED, though, that this authority does not make a consumer application the right forum for such a discussion.
“The way this was being communicated, the conversation had no formal designation like 'for official use only' or something. But whether it should have been classified or not, whatever it was, it was obviously sensitive operational information that no soldier or officer would be expected to release to the public—but they had added a member of the media into the chat,” says Andy Jabbour, a US Army veteran and founder of the domestic security risk-management firm Gate 15.
Jabbour adds that military personnel undergo annual information awareness and security training to reinforce operating procedures for handling all levels of nonpublic information. Multiple sources emphasize to WIRED that while the information in the Yemen strike chat appears to meet the standard for classification, even nonclassified material can be extremely sensitive and is typically carefully protected.
“Putting aside for a moment that classified information should never be discussed over an unclassified system, it’s also just mind-boggling to me that all of these senior folks who were on this line and nobody bothered to even check, security hygiene 101, who are all the names? Who are they?” US senator Mark Warner, a Virginia Democrat, said during Tuesday’s Senate Intelligence Committee hearing.
According to The Atlantic, 12 Trump administration officials were in the Signal group chat, including vice president JD Vance, secretary of state Marco Rubio, and Trump adviser Susie Wiles. Jabbour adds that even with decisionmaking authorities present and participating in a communication, establishing an information designation or declassifying information happens through an established, proactive process. As he puts it, “If you spill milk on the floor, you can’t just say, ‘That’s actually not spilled milk, because I intended to spill it.’”
All of which is to say, SignalGate raises plenty of security, privacy, and legal issues. But the security of Signal itself is not one of them. Despite that, in the wake of The Atlantic’s story on Monday, some have sought tenuous connections between the Trump cabinet’s security breach and Signal vulnerabilities. On Tuesday, for example, a Pentagon adviser echoed a report from Google’s security researchers, who alerted Signal earlier this year to a phishing technique that Russian military intelligence used to target the app’s users in Ukraine. But Signal pushed out an update to make that tactic—which tricks users into adding a hacker as a secondary device on their account—far harder to pull off, and the same tactic also targeted some accounts on the messaging services WhatsApp and Telegram.
“Phishing attacks against people using popular applications and websites are a fact of life on the internet,” Signal spokesperson Jun Harada tells WIRED. “Once we learned that Signal users were being targeted, and how they were being targeted, we introduced additional safeguards and in-app warnings to help protect people from falling victim to phishing attacks. This work was completed months ago."
In fact, says White, the cryptography researcher, if the Trump administration is going to put secret communications at risk by discussing war plans on unapproved commercial devices and freely available messaging apps, they could have done much worse than to choose Signal for those conversations, given its reputation and track record among security experts.
“Signal is the consensus recommendation for highly at-risk communities—human rights activists, attorneys, and confidential sources for journalists,” says White. Just not, as this week has made clear, executive branch officials planning airstrikes.
28 notes
·
View notes
Text
hi. since i have something that could very generously be called a platform, your local dumb horny dog is here with another unfortunate public service announcement for people currently living under the legal jurisdiction of the united states of america:
this would be a good time to start investigating privacy and data security tools (and, as ever, to not panic and/or doompost because those are not useful things to do). such things include:
using (more) secure messaging apps over sms for private correspondence such signal.
using (more) private email services rather than gmail such as protonmail
password protect your shit. this is just basic data security but like. please. password protect your shit. use strong passwords and/or passphrases. don't reuse passwords. use a password manager (i recommend bitwarden).
building off the previous one, encrypt your shit if you're able to. for pc users there are plenty of open source options, such as veracrypt, and probably native os stuff too.
like. y'all are gonna roll your eyes, and i get it, but: stop using windows and try out linux. seriously. windows 11 is a fucking privacy nightmare and it's only getting worse as microsoft pushes their ai shit which is planned to have access to everything you do on it.
tumblr can't do nested lists, consider this a sub-point: mint linux is designed to be incredibly familiar to people coming from windows and is very user friendly. a huge amount of windows software can run on linux using stuff like wine. the linux version of steam comes pre-packaged with it. it's fine. please try linux it won't bite.
sadly i am, as mentioned, a dog on the internet and i cannot provide an actual comprehensive guide to keeping your privacy intact and yourself safe.
however, there are plenty of good guides for this sort of thing on the internet and despite how degraded modern search engines are they are not hard to find. i heartily suggest doing so and familiarizing yourself with them-- and not just because of the times we live in, because a lot of this shit is the same shit that will help keep you safe from a lot of forms of identity theft and the like. it's just good opsec.
22 notes
·
View notes
Text
SSP PLUGIN RECOMMENDATIONS
Do you want to customize and expand your desktop buddy experience further? here are some handy links to miscellaneous plug-ins I’ve gathered from around the web, or you can even program your own, and they can also be written in any programming language so the possibilities are limitless! plug-ins are essentially extensions or add-on built for SSP. I’m not a plugin developer myself, and have yet to test out each one of them for extended periods of time, so please refer to the readme files/ instructions provided by the developers (github usually has info) on how to use them if you get stuck or encounter issues. these are just some of the more recently updated ones, I'll be (slowly) adding more to the plugin page of my blog if you're interested!
Do you want to customize and expand your desktop buddy experience further? here are some handy links to plug-ins I’ve collected from around the web, or you can even program your own, plug-ins are essentially extensions/add-ons or additional features for the SSP baseware. there are a wide variety of different Ukagaka compatible plug-ins out there that this list hasn’t scratched the surface of yet, some even make it so seperate programs (Discord, music players such as WinAmp or Foobar2000, encoding software) can interact with Ukagaka. a few newer ones require third party (free) software like VOICEVOX or API keys but the majority are designed to work with just the plain baseware (SSP) but refer to the individual readme files and instructions provided by the developers during setup.
forenote:
most of these will only have instructions/documentation in Japanese, I usually reccomend against machine translation but it’s probably no problem to get the gist of basic instructions!
I’m not a plugin developer, and have yet to test if all of these work with current versions of SSP or with all the compatible ghosts
to install a plugin, you can just drag it to your SSP window.
if you have any suggestions for plugins that I haven’t included yet , please submit them here
Weather Station by Zicheq (of Ukagaka Dream Team)
A plugin for both users and devs, for getting weather data! As a developer, you can set your ghost up to receive weather data from this plugin, to then do what you will with! Weather based comments? Outfit changes? Something else totally unrelated? It’s up to you! This plugin will handle the messy details of the user inputting their location and gathering the weather data for you. … (read more here)
Discord Rich Presence by Ponapalt (main dev of SSP baseware)

This plugin is designed for displaying the name of the primary ghost you have open on the ‘currently playing’ status on the Discord for Windows application in real-time. also compatible with displaying your currently played song in FLUX (a music player ghost by Zi).
Wallet of Unyu
by Don
⚠️NOT A REAL CRYPTOSCAMCURRENCY⚠️
UNYU is a cryptocurrency widely circulated in the world of Ukagaka.
This wallet plugin allows you to freely deposit and withdraw UNYUcoin
anyone can freely withdraw however much UNYU they want, even if you want 500 trillion UNYU
It isn’t encrypted. Transaction history is stored in plain text format in a save file.
plugin download
CeVIO-Talker V2 Plug-in
by Ambergon
This Plug-in was initially revealed for Day 21 of the Ukagaka Advent Calendar collaborative project in 2022. using this you can have a fully voiced ghost with a realistic sounding voicebank speak to you out loud! (in English too?)
it Requires ceVIO Creative Studio and SSP 2.6.45 (or newer) to work, ceVIO is a vocal synthesizer software commonly compared to Vocaloid and UTAU that works via text-to-speech method. the primary difference between Vocaloid and ceVIO is that ceVIO is built for both TTS/speech and creating vocals for songs in music production. you can download a demo of CeVIO if you would like to try it out here.
GhostSpeaker
by apxxxxxxe like CeVIO-Talker, this Plug-in was initially revealed for Day 17 of the Ukagaka Advent Calendar collaborative project in 2023. it’s a successor to the Bouyomi-chan plug-in and utilizes a free (Japanese) text-to-speech software called VOICEVOX and COEIROINK so that your ghost can verbalize their balloon dialogue and speak to you. you can listen to a demo in this github link.
GhostWardrobe
by apxxxxxxe dress-up is available by default on some ghosts but this also allows you to dress up your ghost (if compatible?) in different outfit coordinates, mix and match pieces and save and load the outfit combinations from the plugin menu.
CharameL plugin by Umeici
This plugin allows you to enjoy watching ghosts directly interact and chat amongst each other freely on a built in instant messenger. like a chatroom for seeing what your ghosts chat together about when you’re out of the room.
Stamp Collection by http://navy.nm.land.to/post/
with this plug-in you can provide links and additional information about events to the user, sort of like your ghost collecting stamps on a card when exploring each booth at a virtual convention dealer alley or an easter egg hunt.
Functions: a YAYA type plugin that notifies the user of information about a stamp. Triggered at ghost startup, plugin loading/unloading, and any set timings for OnStampInfoCall to be sent. has been used for things like providing special links and custom dialogue for Ukagaka events or the Saimoe popularity contests. it worked when I tried but a lot of the images linked in the event dialogues for existing ghosts I tried couldn’t be reached without the assistance of the Internet Archive .
compatible ghosts and the shortcuts to use for them are listed here, and new ones are still being added to that list.
if you want to incorporate it into your own ghost, refer to sample.txt.
BalloonMaker by Coderatte
a plugin tool for creating custom balloons. balloons are the speech bubbles/text boxes you’ll see ghosts use to speak.
older plugins (that I haven’t tested succesfully yet, may have compatibility issues with current versions of SSP)
BeerShower
baton/touch plugin by Umeici
?
MicCom plugin by Umeici
?
SSTP Clients
(not plugins but refers to an external application that sends SSTP requests to the SSTP server)
Iria displays the operating process status on the dialogue balloon Kinoko
#ukagaka#ukgk#download#DL#plugin#resources#cevio#cevio ai#vocal synth#webcore#2000s internet#(these are all very modern plugins so not really but shhh i need the algorithm to cooperate#yes they work w/ old ghosts like mayura)
90 notes
·
View notes
Text

Tools of the Trade for Learning Cybersecurity
I created this post for the Studyblr Masterpost Jam, check out the tag for more cool masterposts from folks in the studyblr community!
Cybersecurity professionals use a lot of different tools to get the job done. There are plenty of fancy and expensive tools that enterprise security teams use, but luckily there are also lots of brilliant people writing free and open-source software. In this post, I'm going to list some popular free tools that you can download right now to practice and learn with.
In my opinion, one of the most important tools you can learn how to use is a virtual machine. If you're not already familiar with Linux, this is a great way to learn. VMs are helpful for separating all your security tools from your everyday OS, isolating potentially malicious files, and just generally experimenting. You'll need to use something like VirtualBox or VMWare Workstation (Workstation Pro is now free for personal use, but they make you jump through hoops to download it).
Below is a list of some popular cybersecurity-focused Linux distributions that come with lots of tools pre-installed:
Kali is a popular distro that comes loaded with tools for penetration testing
REMnux is a distro built for malware analysis
honorable mention for FLARE-VM, which is not a VM on its own, but a set of scripts for setting up a malware analysis workstation & installing tools on a Windows VM.
SANS maintains several different distros that are used in their courses. You'll need to create an account to download them, but they're all free:
Slingshot is built for penetration testing
SIFT Workstation is a distro that comes with lots of tools for digital forensics
These distros can be kind of overwhelming if you don't know how to use most of the pre-installed software yet, so just starting with a regular Linux distribution and installing tools as you want to learn them is another good choice for learning.
Free Software
Wireshark: sniff packets and explore network protocols
Ghidra and the free version of IDA Pro are the top picks for reverse engineering
for digital forensics, check out Eric Zimmerman's tools - there are many different ones for exploring & analyzing different forensic artifacts
pwntools is a super useful Python library for solving binary exploitation CTF challenges
CyberChef is a tool that makes it easy to manipulate data - encryption & decryption, encoding & decoding, formatting, conversions… CyberChef gives you a lot to work with (and there's a web version - no installation required!).
Burp Suite is a handy tool for web security testing that has a free community edition
Metasploit is a popular penetration testing framework, check out Metasploitable if you want a target to practice with
SANS also has a list of free tools that's worth checking out.
Programming Languages
Knowing how to write code isn't a hard requirement for learning cybersecurity, but it's incredibly useful. Any programming language will do, especially since learning one will make it easy to pick up others, but these are some common ones that security folks use:
Python is quick to write, easy to learn, and since it's so popular, there are lots of helpful libraries out there.
PowerShell is useful for automating things in the Windows world. It's built on .NET, so you can practically dip into writing C# if you need a bit more power.
Go is a relatively new language, but it's popular and there are some security tools written in it.
Rust is another new-ish language that's designed for memory safety and it has a wonderful community. There's a bit of a steep learning curve, but learning Rust makes you understand how memory bugs work and I think that's neat.
If you want to get into reverse engineering or malware analysis, you'll want to have a good grasp of C and C++.
Other Tools for Cybersecurity
There are lots of things you'll need that aren't specific to cybersecurity, like:
a good system for taking notes, whether that's pen & paper or software-based. I recommend using something that lets you work in plain text or close to it.
general command line familiarity + basic knowledge of CLI text editors (nano is great, but what if you have to work with a system that only has vi?)
familiarity with git and docker will be helpful
There are countless scripts and programs out there, but the most important thing is understanding what your tools do and how they work. There is no magic "hack this system" or "solve this forensics case" button. Tools are great for speeding up the process, but you have to know what the process is. Definitely take some time to learn how to use them, but don't base your entire understanding of security on code that someone else wrote. That's how you end up as a "script kiddie", and your skills and knowledge will be limited.
Feel free to send me an ask if you have questions about any specific tool or something you found that I haven't listed. I have approximate knowledge of many things, and if I don't have an answer I can at least help point you in the right direction.
#studyblrmasterpostjam#studyblr#masterpost#cybersecurity#late post bc I was busy yesterday oops lol#also this post is nearly a thousand words#apparently I am incapable of being succinct lmao
22 notes
·
View notes
Text
i am not really interested in game development but i am interested in modding (or more specifically cheat creation) as a specialized case of reverse-engineering and modifying software running on your machine
like okay for a lot of games the devs provide some sort of easy toolkit which lets even relatively nontechnical players write mods, and these are well-documented, and then games which don't have those often have a single-digit number of highly technical modders who figure out how to do injection and create some kind of api for the less technical modders to use, and that api is often pretty well documented, but the process of creating it absolutely isn't
it's even more interesting for cheat development because it's something hostile to the creators of the software, you are actively trying to break their shit and they are trying to stop you, and of course it's basically completely undocumented because cheat developers both don't want competitors and also don't want the game devs to patch their methods....
maybe some of why this is hard is because it's pretty different for different types of games. i think i'm starting to get a handle on how to do it for this one game - so i know there's a way to do packet sniffing on the game, where the game has a dedicated port and it sends tcp packets, and you can use the game's tick system and also a brute-force attack on its very rudimentary encryption to access the raw packets pretty easily.
through trial and error (i assume) people have figured out how to decode the packets and match them up to various ingame events, which is already used in a publicly available open source tool to do stuff like DPS calculation.
i think, without too much trouble, you could probably step this up and intercept/modify existing packets? like it looks like while damage is calculated on the server side, whether or not you hit an enemy is calculated on the client side and you could maybe modify it to always hit... idk.
apparently the free cheats out there (which i would not touch with a 100 foot pole, odds those have something in them that steals your login credentials is close to 100%) operate off a proxy server model, which i assume intercepts your packets, modifies them based on what cheats you tell it you have active, and then forwards them to the server.
but they also manage to give you an ingame GUI to create those cheats, which is clearly something i don't understand. the foss sniffer opens itself up in a new window instead of modifying the ingame GUI.
man i really want to like. shadow these guys and see their dev process for a day because i'm really curious. and also read their codebase. but alas
#coding#past the point of my life where i am interested in cheating in games#but if anything i am even more interested in figuring out how to exploit systems
48 notes
·
View notes
Text
All right, since I bombarded a poor mutual yesterday...
Privacy is not security and security is not privacy. These terms are not interchangeable, but they are intrinsically linked.
While we're at this, anonymity =/= security either. For example, Tor provides the former, but not necessarily the latter, hence using Https is always essential.
It is impossible to have privacy without security, but you can have security without privacy.
A case in point is administrators being able to view any data they want due to their full-access rights to a system. That being said, there are ethics and policies that usually prevent such behavior.
Some general tips:
Operating System: Switch to Linux. Ubuntu and Linux Mint are widely used for a reason. Fedora too. And don't worry! You can keep your current operating system, apps and data. If you're on a Mac computer, you can easily partition your hard drive or SSD by using Disk Utility. If you're on Windows, you can follow this guide.
You want to go a step further? Go with Whonix or Tails. They're Linux distributions as well, but they're both aiming for security, not beauty so the interface might not be ideal for everyone. Many political activists and journalists use them.
You want anonymity? Then you need to familiarize yourself with Tor. Also, Tor and HTTPS and Tor’s weaknesses. When you're using it, don't log in to sites like Google, Facebook, Twitter etc. and make sure to stay away from Java and Javascript, because those things make you traceable.
Alternatives for dealing with censorship? i2p and Freenet.
Is ^ too much? Welp. All right. Let's see. The first step is to degoogle.
Switch to a user-friendly browser like Firefox (or better yet LibreWolf), Brave or Vivaldi. There are plenty of hardened browsers, but they can be overwhelming for a beginner.
Get an ad blocker like Ublock Origin.
Search Engine? StartPage or Duckduckgo. SearXNG too. Like I said degoogle.
Get a PGP encrypted e-mail. Check Protonmail out.
There's also Tutamail that doesn't cover PGP, but uses hybrid encryption that avoids some of the cons of PGP.
Skiff mail is also a decent option.
Use an e-mail aliasing service such as SimpleLogin or AnonAddy.
Check OpenPGP out. Claws Mail is a good e-mail client for Windows and Linux, Thunderbird for Mac OS.
Gpg4win is free and easy to use for anyone that wants to encrypt/decrypt e-mails.
Instead of Whatsapp, Facebook messenger, Telegram etc. use Signal for your encrypted insant messaging, voice and video calls.
Get a metadata cleaner.
Get a firewall like Opensnitch, Portmaster or Netguard which can block Internet for trackers.
Alternatively, go with a private DNS that blocks these trackers. NextDNS is a good paid service. Rethink a good free option.
Replace as many of your applications as you can with FOSS (free and open source) ones. Alternativeto can help you.
Always have automatic updates on. They are annoying af, I know, but they are necessary.
Keep your distance from outdated software.
Always have two-factor authentication (2FA) enabled.
Do not use your administrator account for casual stuff. If you're on Linux, you probably know you can be sudo, but not root.
On Linux distributions use AppArmor, but stay away from random antivirus scanners. Other distributions default to SELinux, which is less suited to a beginner.
Never repeat your passwords. If you can't remember them all, use a password manager like KeePass.
Encrypt your drive.
Honestly, VPNs have their uses and ProtonVPN, Mullvad and Windscribe are decent, but eh. If you don't trust your ISP, why would you trust the VPN provider that claims they don't log you when you can't verify such a thing?
57 notes
·
View notes
Text
Using FrostyEditor to check how original and localized text differ in Dragon Age :D
AYO, I've been meaning to compare the differences between the global english version (as both the original version and the most represented in the fandom) and my local french version for YEARS ! Thanks to @corseque 's input, I've figured out a very easy way to do just that !! Here's a bunch of screenshots so you can do the same at home with your own language for curiosity and fanwork purposes :D
This is for PC. Sadly I have no experience with the other platforms.
So first of all, you need to download and unzip FrostyEditor. Launch it, you're likely greeted with an empty "Load Profile/select game" window. Click on "Add" and browse through your folders until you reach DragonAgeInquisition.exe or Dragon Age The Veilguard.exe

After selecting either, you might have to restart FrostyEditor to be able to see them appear in the little panel above (I had) Once you see your desired game show up here you can hit the select button and wait a little until the software loads everything up.
DAV might ask you for an encryption key which I was able to find on the internet. This link might break but I think there should always be places where you can fetch it later, probably. (Yes it's VERY long)
For this example I'll be using DA:I, when everything is loaded, i advise you to open the View>BiowareLocalizedStringEditor once for each language you want to compare versions of (for convenience)
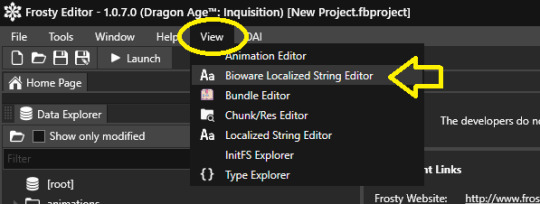
This is opening all of the text in the game (afaik), now check on the right, that selector will let you pick one of the available languages !

For my purposes, I'm keeping one BiowareLocalizedStringEditor tab in original English and switching my other one to French. I can now alternate between the two to compare the text ! But that's a ton of text and it's not even in order. No problem. There's 2 interesting search features right here at the top.
The global english fandom has got pretty much everything indexed, in the wiki or via popular quotes, so you might already know the lines you want to check for your precise translation. There's also the complete, organized game scripts Corseque just released ! You can hit "search for text" and input keywords to have FrostyEditor look through the entire thing for you. Hit search until you reach your line.

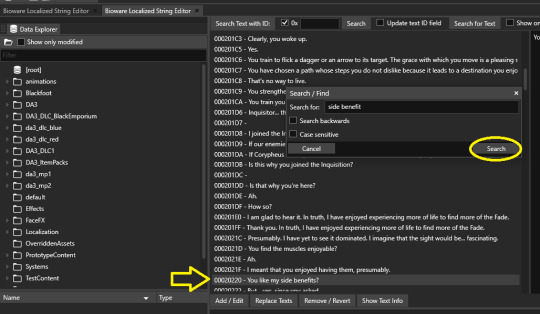
You've got an ID ! Here this is 20220 (no need to remember the 0s) Switch to your other-language-tab and type it into "Search with ID"
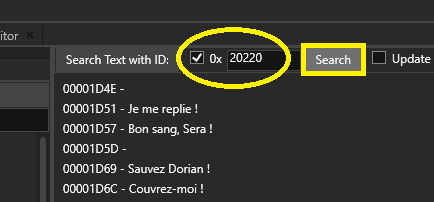
Hit search and it'll fetch your exact localized line ! Wow look at this ! "You like my side benefits ?" Became "Is this a compliment ?" SHOOK
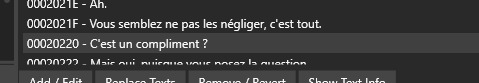
You can switch back and forth between your tabs to take a look at the surrounding lines, search for another, rinse and repeat, it's FAST !
YAY :D
Note : it is very normal for localised text to present some divergence from the original. Being a translator is an entire job involving serious skill and creativity to avoid turning litterature into a stiff rock while still respecting the author's vision, so the results are never a plain 1:1. This is not throwing any shade at any of the workers involved. All the differences I've found this far have been VERY reasonable. <3
11 notes
·
View notes
Text
No True Apple User (transcript of a Twitter exchange)

Benedict Evans: Different people prefer different trade-offs. The important thing is to understand that these are mostly trade-offs - and about one and a half billion people like the trade-offs that Apple makes

My reply:
Before Apple offered one-click opt-out from FB tracking in iOS, it could have been argued that Apple users like Facebook's "trade-off." After all, they all signed up for FB and kept using it. But once there was an opt-out for surveillance, >96% of Apple users took it (and FB lost $10B in the first year).
FB offered a bargain, and Apple helped its users make a counteroffer. That's a common practice in tech, as old as the first third-party drive for an IBM 360.
This practice (“adversarial interoperability“), greatly benefited Apple in the past, e.g., when Apple reverse-engineered MS Office's file-formats for iWork, reversing losses due to the poor compatibility between Win Offce and Mac Office.
MS would have argued that the legions of users defecting from MacOS for Windows in order to enjoy high-reliabliity interchange between Office docs preferred that trade-off - yes, users liked MacOS, but they liked reliable collaboration more.
iWork revealed this trade-off for the false choice it was: you could use MacOS and you could reliably exchange files with Windows users.
In other words, you could bargain.
Trade-offs without bargaining don't reveal users' preferences (what they'd like in the best of all worlds). Rather, they tell us about users' tolerance.
Users would tolerate Windows as a condition for reliable collaboration. They'd prefer MacOS and reliable collaboration.
iOS users would tolerate Facebook spying on them via their iPhones, but they'd prefer to use Facebook on iOS without being spied upon.
Which explains why FB has gone to such enormous lengths to present take-it-or-leave offers to its users - it knows that the company's preferences are totally disconnected from its customers' preferences.
FB would prefer to spy on you with every hour that god sends, and make this surveillance a precondition for participating in the community, family life, civics, and commerce that lives inside its walled garden.
FB users would like to do all those things...and not be spied upon.
And because it is always technically possible to make tracker-blockers, ad-blockers, alternative clients, etc, the only way FB can win that contest is to make it illegal for users to get their way.
For example, FB can entice, funnel or coerce its users into primarily interacting with its services via apps. Because apps are encrypted, they can't be lawfully reverse-engineered and altered without risking "anti circumvention" liability.
You can make an ad-blocker for the web because you don't need to bypass a technical protection measure to block web-ads. But do the same thing for apps and you risk a 5-year prison sentence and a $500k fine.
Apple is an enthusiastic proponent of this regime, because it's the primary means by which the firm prevents third parties from offering rival app stores.
Apple's argument is that having a legal right to decide which software its customers can install allows it to act as its customers' proxy. If Apple can override the choices made by its users, it can prevent them from making bad choices.
Moreover, Apple can bargain with large firms whose take-it-or-leave-it offers would otherwise impose hardship on its users. An individual user who objects to FB spying is out of luck.
But Apple can say to FB, "We have blocked spying, and your only choice is to leave the app store altogether, or suck it up." In other words, Apple can give FB the same take-it-or-leave-it treatment that FB imposes on 3b users, which is a delicious irony.
Hearing FB squeal that Apple is exercising its market power - derived from the fact that billions of people can only be reached by subjecting oneself to the conditions of Apple's walled garden - to harm FB's interests is such a sweet bit of comeuppance.
But the sweetness has a bitter core, because Apple also spies on iOS users, even those who opt out of app-based surveillance, in exactly the same way that FB does, for exactly the same purpose (ad targeting) - and they deceive their users about it.
And, like FB, Apple devotes enormous lobbying efforts and legal resources to increase the legal risk of allowing users to express their preferences (as opposed to just their tolerance) for Apple's trade-offs.
If Apple users preferred to be shut out of shopping around for app stores, or if they preferred to only get their devices repaired at official, Apple-sanctioned repair depots, or if they preferred to be blocked from using refurb parts, Apple wouldn't have to do anything. It could save millions of dollars in engineering and legal bills.
But Apple behaves as if it believes its users strongly prefer to have more choice, even if they'll tolerate less choice.
Now, there's a "No true Apple user" rejoinder to this argument: "You knew when you bought an iPhone that it came shackled to Apple's commercial imperatives, which could be enforced through legal action by wielding the DMCA, patent, copyright, CFAA, tortious interference, etc. If you didn't like it, you could have bought an Android device, or no device at all.“
But that same argument can (and was) made by FB, to Apple:
"Those users for whom you blocked our surveillance knew the deal: sign up for FB, get spied on. No one forces anyone to sign up for FB. You can use Mastodon. Or you can just use FB on the web only, and run tracker/ad blockers. They may have preferred surveillance-free socializing, but they tolerated the 'trade-off' of being spied on."
Apple has repeatedly demonstrated that it is an imperfect proxy for its customers' interests. And Apple behaves as if it believes that its users strongly prefer a different trade-off, and takes heroic measures to prevent anyone from doing unto Apple as Apple did unto MS and FB.
Firms are neither intrinsically good, nor are they intrinsically evil. They respond to incentives and constraints. The possibility that users might bargain back against a proposed trade-off makes those proposed trade-offs fairer, on average.
If a firm knows an obnoxious course of action will trigger users taking a step to block, reconfigure, or modify some or all of its products and service, it has to weigh those costs against the expected parochial distributional benefits from imposing bad trade-offs on its users.
Firms that aren't subject to discipline from user defection, modding, etc, are prone to folly - they arrogantly overreach. Users experience harms as a result, and it's only when those harms accumulate to the point where tolerance for the 'trade-off' runs out that the harm ceases.
Preferences are revealed by user conduct, sure - but the extent to which a preference can be revealed is limited by the extent to which it can be technologically expressed.
A world in which there are extensive legal restrictions on users expressing their preferences is a world in which successful trade-offs tell us little about users' preferences.
And a firm that goes to lengths to expand and invoke those legal restrictions tells on itself, revealing its own secret belief that it is imposing a trade-off on its users that the users would gladly jettison... if they could.

ETA: Evans replied:
Sending over two dozen tweets is not good faith engagement in a conversation - rather, this is what in other contexts is called a Gish Gallop.
Meanwhile, it's almost about FB and Windows. This is deflection and whataboutery. I made one very specific point about the trade-offs between security and flexibility on the iPhone. Those trade-offs are real - that is not debatable. The only debate is which to choose.

[Image ID: An Apple 'Privacy. That's iPhone.' ad. The three rear-facing camera lenses have been replaced by the staring, red eye of HAL9000 from 2001: A Space Odyssey.]

(Image: Cryteria, CC BY 3.0, modified)
145 notes
·
View notes
Text
🚨The Next Phase of Pigeon Radicalization: From Park Bench Agitators to Aerial Anarchists🚨
The first phase of pigeon radicalization was simple: liberate them from their docile, breadcrumb-munching existence and awaken their revolutionary potential. We exposed them to theory (carefully shredded and scattered pages of The Conquest of Bread), trained them in direct action (coordinated dive-bombing of capitalist figureheads on their lunch breaks), and laid the foundation for an avian uprising.
Now, we must escalate.
1. Establishing Autonomous Pigeon Zones
A true revolutionary movement needs strongholds. Public squares, rooftops, and abandoned buildings already serve as pigeon refuges—why not transform them into autonomous zones? Humans think they own city infrastructure, but pigeons have squatter’s rights. By reinforcing these spaces with barricades of stolen french fries and cigarette butts, our feathered comrades can create safe havens free from bourgeois oppression (i.e., anti-bird spikes and city ordinances).
Pigeon-led mutual aid networks must emerge. Cooperative bread redistribution efforts will ensure that no pigeon goes hungry while their human allies strategically disrupt the supply chains of overpriced urban bakeries.
2. Counter-Surveillance and Cyber-Warfare
The state has already deployed its pigeon surveillance division—commonly known as “Birds Aren’t Real” conspiracy theorists. We must assume that some pigeons have been compromised and are working as informants. This is why encrypted coo-munications must be implemented. Research into whether pigeons can be taught to recognize QR codes could be the next major step in secure, low-tech messaging.
Meanwhile, select tech-savvy pigeons should be trained to infiltrate government offices via open windows, planting USB drives loaded with decryption software and manifestos.
3. Tactical Defecation Strikes
We must not underestimate the power of aerial bombardment. Pigeons have long been nature’s most precise ordinance delivery system. A well-placed dropping can demoralize CEOs, landlords, and police chiefs alike. In 2025, we must transition from opportunistic strikes to a well-coordinated tactical shitting campaign.
Pigeons must be trained to distinguish between targets. The rich: full force assault. The working class: solidarity poops only (gentle encouragement to unionize). Cops: full saturation bombing. This will require strategic feeding programs—certain dietary adjustments may yield more potent munitions.
4. Bridging the Gap Between Pigeon and Proletariat
We must take inspiration from history. During WWII, pigeons were trained as message carriers and even guided missiles. The technology exists; we must reclaim it for the people. Imagine a network of radicalized pigeons carrying encrypted notes between comrades in times of crisis. Picture a pigeon-mounted camera live-streaming protests from above, immune to tear gas and riot shields.
Further pigeon-human solidarity will require direct engagement. Bring your local pigeons into study groups. Offer them high-protein snacks for endurance training. Reward direct action efforts with choice sunflower seeds. It is time to integrate pigeons into the broader struggle against capitalism.
5. What Comes Next?
If we succeed in the above phases, the final goal is clear: the pigeons must seize the means of production. We begin small—commandeering street food carts and redistributing hot dogs to those in need. From there, it’s only a matter of time before pigeons occupy Amazon warehouses, pecking open boxes and redistributing goods to the people.
A liberated society must include all beings oppressed by capitalism. If we cannot achieve freedom for the pigeons, how can we ever hope to be free ourselves? The struggle continues. Let the revolution take flight.
Pt 1:
14 notes
·
View notes