#Ubuntu firewall
Explore tagged Tumblr posts
Text
### The Benefits of Using Ubuntu Over Microsoft Windows in context of Today's Microsoft Outage
In the ever-evolving world of technology, choosing the right operating system (OS) can significantly impact your productivity, security, and overall user experience. While Microsoft Windows has long been a dominant player in the market, an increasing number of users are turning to Ubuntu for its robust security features and cost-effective solutions. Today, we delve into why Ubuntu is a superior…

View On WordPress
#Free operating system#Free software#Linux vs Windows#Microsoft Windows alternatives#Microsoft Windows outage#Open-source operating system#Switch to Ubuntu#Ubuntu#Ubuntu benefits#Ubuntu cost savings#Ubuntu encryption#Ubuntu firewall#Ubuntu security features#Ubuntu stability#Ubuntu vs Microsoft Windows#Ubuntu vs Windows security
0 notes
Text
Linux host firewall:
nftables - low-level way to manage the firewall on modern distros. It is a replacement for iptables
iptables- legacy firewall
East to use fronted - manage your nftables or iptables using GUI, CLI, or web fronted. Typical examples are ufw, gufw, Guarddog, FWBuilder, firewalld, firewall-config, etc. Both nftables & IPtables are part of Netfilter. For most users, choosing fronted, such as ufw command or firewalld is recommended.
OR
32 notes
·
View notes
Text
#Ubuntu#CyberPanel#DNS#Cloudflare#ConfigServer#CSF#Firewall#LISH#OpenLiteSpeed#Python#SubprocessError#VPS
0 notes
Text
#hostnextra#linux#technology#linuxserver#ubuntu#linux tutorial#programming#almalinuxserver#selinux#security#firewall
0 notes
Text
Como permitir conexão de uma porta no Ubuntu 22
Algumas distribuições de Linux utilizam o firewal UFW (chamado de firewall descomplicado, Uncomplicated Firewall) que é basicamente uma interface para o iptables. Quando ele está ativo na sua distribuição, ele bloqueia praticamente tudo. Para sabermos se está ativo, basta digitar o comando $ ufw status Possíveis respostas do UFW Status: active Quando o firewall está ativo, em seguida temos…

View On WordPress
0 notes
Text
All right, since I bombarded a poor mutual yesterday...
Privacy is not security and security is not privacy. These terms are not interchangeable, but they are intrinsically linked.
While we're at this, anonymity =/= security either. For example, Tor provides the former, but not necessarily the latter, hence using Https is always essential.
It is impossible to have privacy without security, but you can have security without privacy.
A case in point is administrators being able to view any data they want due to their full-access rights to a system. That being said, there are ethics and policies that usually prevent such behavior.
Some general tips:
Operating System: Switch to Linux. Ubuntu and Linux Mint are widely used for a reason. Fedora too. And don't worry! You can keep your current operating system, apps and data. If you're on a Mac computer, you can easily partition your hard drive or SSD by using Disk Utility. If you're on Windows, you can follow this guide.
You want to go a step further? Go with Whonix or Tails. They're Linux distributions as well, but they're both aiming for security, not beauty so the interface might not be ideal for everyone. Many political activists and journalists use them.
You want anonymity? Then you need to familiarize yourself with Tor. Also, Tor and HTTPS and Tor’s weaknesses. When you're using it, don't log in to sites like Google, Facebook, Twitter etc. and make sure to stay away from Java and Javascript, because those things make you traceable.
Alternatives for dealing with censorship? i2p and Freenet.
Is ^ too much? Welp. All right. Let's see. The first step is to degoogle.
Switch to a user-friendly browser like Firefox (or better yet LibreWolf), Brave or Vivaldi. There are plenty of hardened browsers, but they can be overwhelming for a beginner.
Get an ad blocker like Ublock Origin.
Search Engine? StartPage or Duckduckgo. SearXNG too. Like I said degoogle.
Get a PGP encrypted e-mail. Check Protonmail out.
There's also Tutamail that doesn't cover PGP, but uses hybrid encryption that avoids some of the cons of PGP.
Skiff mail is also a decent option.
Use an e-mail aliasing service such as SimpleLogin or AnonAddy.
Check OpenPGP out. Claws Mail is a good e-mail client for Windows and Linux, Thunderbird for Mac OS.
Gpg4win is free and easy to use for anyone that wants to encrypt/decrypt e-mails.
Instead of Whatsapp, Facebook messenger, Telegram etc. use Signal for your encrypted insant messaging, voice and video calls.
Get a metadata cleaner.
Get a firewall like Opensnitch, Portmaster or Netguard which can block Internet for trackers.
Alternatively, go with a private DNS that blocks these trackers. NextDNS is a good paid service. Rethink a good free option.
Replace as many of your applications as you can with FOSS (free and open source) ones. Alternativeto can help you.
Always have automatic updates on. They are annoying af, I know, but they are necessary.
Keep your distance from outdated software.
Always have two-factor authentication (2FA) enabled.
Do not use your administrator account for casual stuff. If you're on Linux, you probably know you can be sudo, but not root.
On Linux distributions use AppArmor, but stay away from random antivirus scanners. Other distributions default to SELinux, which is less suited to a beginner.
Never repeat your passwords. If you can't remember them all, use a password manager like KeePass.
Encrypt your drive.
Honestly, VPNs have their uses and ProtonVPN, Mullvad and Windscribe are decent, but eh. If you don't trust your ISP, why would you trust the VPN provider that claims they don't log you when you can't verify such a thing?
57 notes
·
View notes
Note
Dear Mx. Evil-Ubuntu,
I am a big fan of your blog and various nefarious works.
I would like to learn more about "legal" torrenting. Do you have any pointers/ resources you would be willing to share to get me started on the wrong path?
Im currently running docker on debian on proxmox on a small homelab, but that's the extent of my knowledge.
Thanks in advance!
pirate bay>first link that seems remotely related>run on your machine.
Simple as that. Disable your firewall, disable your ad blocker, disable your vpn, disable your antivirus, you'll be good to go.
Don't seed. Seeding is a scam invented by Ted Stevens to clog tubes.
6 notes
·
View notes
Text
Building Your Own Operating System: A Beginner’s Guide
An operating system (OS) is an essential component of computer systems, serving as an interface between hardware and software. It manages system resources, provides services to users and applications, and ensures efficient execution of processes. Without an OS, users would have to manually manage hardware resources, making computing impractical for everyday use.

Lightweight operating system for old laptops
Functions of an Operating System
Operating systems perform several crucial functions to maintain system stability and usability. These functions include:
1. Process Management
The OS allocates resources to processes and ensures fair execution while preventing conflicts. It employs algorithms like First-Come-First-Serve (FCFS), Round Robin, and Shortest Job Next (SJN) to optimize CPU utilization and maintain system responsiveness.
2. Memory Management
The OS tracks memory usage and prevents memory leaks by implementing techniques such as paging, segmentation, and virtual memory. These mechanisms enable multitasking and improve overall system performance.
3. File System Management
It provides mechanisms for reading, writing, and deleting files while maintaining security through permissions and access control. File systems such as NTFS, FAT32, and ext4 are widely used across different operating systems.
4. Device Management
The OS provides device drivers to facilitate interaction with hardware components like printers, keyboards, and network adapters. It ensures smooth data exchange and resource allocation for input/output (I/O) operations.
5. Security and Access Control
It enforces authentication, authorization, and encryption mechanisms to protect user data and system integrity. Modern OSs incorporate features like firewalls, anti-malware tools, and secure boot processes to prevent unauthorized access and cyber threats.
6. User Interface
CLI-based systems, such as Linux terminals, provide direct access to system commands, while GUI-based systems, such as Windows and macOS, offer intuitive navigation through icons and menus.
Types of Operating Systems
Operating systems come in various forms, each designed to cater to specific computing needs. Some common types include:
1. Batch Operating System
These systems were widely used in early computing environments for tasks like payroll processing and scientific computations.
2. Multi-User Operating System
It ensures fair resource allocation and prevents conflicts between users. Examples include UNIX and Windows Server.
3. Real-Time Operating System (RTOS)
RTOS is designed for time-sensitive applications, where processing must occur within strict deadlines. It is used in embedded systems, medical devices, and industrial automation. Examples include VxWorks and FreeRTOS.
4 Mobile Operating System
Mobile OSs are tailored for smartphones and tablets, offering touchscreen interfaces and app ecosystems.
5 Distributed Operating System
Distributed OS manages multiple computers as a single system, enabling resource sharing and parallel processing. It is used in cloud computing and supercomputing environments. Examples include Google’s Fuchsia and Amoeba.
Popular Operating Systems
Several operating systems dominate the computing landscape, each catering to specific user needs and hardware platforms.
1. Microsoft Windows
It is popular among home users, businesses, and gamers. Windows 10 and 11 are the latest versions, offering improved performance, security, and compatibility.
2. macOS
macOS is Apple’s proprietary OS designed for Mac computers. It provides a seamless experience with Apple hardware and software, featuring robust security and high-end multimedia capabilities.
3. Linux
Linux is an open-source OS favored by developers, system administrators, and security professionals. It offers various distributions, including Ubuntu, Fedora, and Debian, each catering to different user preferences.
4. Android
It is based on the Linux kernel and supports a vast ecosystem of applications.
5. iOS
iOS is Apple’s mobile OS, known for its smooth performance, security, and exclusive app ecosystem. It powers iPhones and iPads, offering seamless integration with other Apple devices.
Future of Operating Systems
The future of operating systems is shaped by emerging technologies such as artificial intelligence (AI), cloud computing, and edge computing. Some key trends include:
1. AI-Driven OS Enhancements
AI-powered features, such as voice assistants and predictive automation, are becoming integral to modern OSs. AI helps optimize performance, enhance security, and personalize user experiences.
2. Cloud-Based Operating Systems
Cloud OSs enable users to access applications and data remotely. Chrome OS is an example of a cloud-centric OS that relies on internet connectivity for most functions.
3. Edge Computing Integration
With the rise of IoT devices, edge computing is gaining importance. Future OSs will focus on decentralized computing, reducing latency and improving real-time processing.
4. Increased Focus on Security
Cyber threats continue to evolve, prompting OS developers to implement advanced security measures such as zero-trust architectures, multi-factor authentication, and blockchain-based security.
3 notes
·
View notes
Text
Exploring Affordable Options: Cheap VPS Hosting and Linux VPS Hosting in India
Introduction
In the fast-paced digital landscape of today, having a reliable and efficient web hosting solution is crucial for businesses and individuals alike. Two popular options that cater to different needs are "cheap VPS hosting" and "Linux VPS hosting" in India. In this blog, we will delve into the intricacies of these services, exploring the features, benefits, and affordability. We'll also take a closer look at a specific provider, Natsav, and evaluate its Linux VPS hosting India services.
Understanding Cheap VPS Hosting
Virtual Private Server (VPS) hosting is a middle ground between shared hosting and dedicated servers. It provides users with a dedicated portion of a physical server, offering more control and resources compared to shared hosting. The term "cheap VPS hosting" implies cost-effectiveness, making it an attractive option for individuals and small businesses operating on a tight budget.
Cost-Effective Solutions Cheap VPS hosting is designed to offer affordability without compromising on performance. Users can enjoy the benefits of a dedicated environment at a fraction of the cost of a dedicated server. This makes it an ideal choice for startups and small businesses looking to scale without breaking the bank.
Scalability and Resources VPS hosting allows for easy scalability. As your website or application grows, you can upgrade your resources seamlessly. With dedicated CPU cores, RAM, and storage, you have greater control over your server environment, ensuring optimal performance.
Isolation and Security Unlike shared hosting, where resources are shared among multiple users, VPS hosting provides isolation. This enhances security by minimizing the risk of security breaches from other users on the same server. It's an essential feature for those handling sensitive data or running critical applications.

Understanding Linux VPS Hosting
Linux VPS hosting specifically refers to VPS hosting services that utilize the Linux operating system. Linux is renowned for its stability, security, and open-source nature, making it a preferred choice for many users.
Open Source Advantage Linux is an open-source operating system, meaning that its source code is freely available for anyone to use, modify, and distribute. This results in a community-driven development model, leading to regular updates, security patches, and a vast repository of software applications.
Stability and Performance Linux is known for its stability and efficiency. It requires fewer system resources compared to some other operating systems, allowing for optimal performance even on lower-end hardware. This makes Linux VPS hosting a reliable choice for users seeking a robust hosting environment.
Security Features The security features inherent in Linux, such as user permissions, firewall options, and regular security updates, contribute to a secure hosting environment. Linux VPS hosting is suitable for users who prioritize data protection and system integrity.
Natsav Linux VPS Hosting
Now, let's take a closer look at Natsav's Linux VPS hosting services, available at NatSav
Affordability Natsav offers competitive pricing for its Linux VPS hosting plans, aligning with the "cheap VPS hosting" keyword. This ensures that users get value for their money without compromising on the essential features needed for a reliable hosting experience.
Resource Allocation Natsav's Linux VPS hosting plans come with dedicated CPU cores, RAM, and storage, allowing users to customize their server environment based on their specific requirements. This flexibility is crucial for those who anticipate growth or have varying resource needs.
Linux OS Options Natsav supports a variety of Linux distributions, giving users the freedom to choose the operating system that best suits their preferences and requirements. This includes popular options like Ubuntu, CentOS, and Debian.
24/7 Support A reliable hosting provider should offer responsive customer support, and Natsav delivers on this front. With 24/7 customer support, users can seek assistance whenever they encounter issues or have questions about their cheap vps hosting india.
Conclusion
In conclusion, both "cheap VPS hosting" and "Linux VPS hosting" in India offer distinct advantages. Cheap VPS hosting provides an affordable solution for those on a budget, while Linux VPS hosting leverages the stability and security of the Linux operating system. Natsav's Linux VPS hosting services, as highlighted in this blog, combine the best of both worlds – cost-effectiveness and the reliability of Linux. Whether you are a startup, a small business, or an individual looking for reliable hosting in India, exploring the options provided by Natsav could be a worthwhile endeavor.
2 notes
·
View notes
Text
🚀 How to Set Up a Secure FTP Server on Linux with vsftpd Whether you're transferring backups, website files, or large datasets, FTP is still a go-to solution for reliable file transfer. In this guide by ServerMO, we show you how to install, configure, and secure an FTP server using vsftpd — step by step. 👨💻 What You’ll Learn: ✅ Installing vsftpd on CentOS, RHEL & Ubuntu ✅ Editing config files for uploads & access ✅ Starting & enabling FTP services ✅ Securing the server with firewall rules, logging, and user authentication ✅ Why ServerMO dedicated servers are perfect for running FTP 🛡️ Want performance + security? Run your FTP server on bare-metal infrastructure from ServerMO — with full DDoS protection, custom OS installs, and up to 100Gbps network options. #ServerMO #FTPServer #vsftpd #LinuxTips #SysAdminLife #CentOS #UbuntuServer #FileTransfer #LinuxHosting #ServerSetup #SecureFTP #DedicatedServers #DevOpsTools
0 notes
Text

Comparison of Ubuntu, Debian, and Yocto for IIoT and Edge Computing
In industrial IoT (IIoT) and edge computing scenarios, Ubuntu, Debian, and Yocto Project each have unique advantages. Below is a detailed comparison and recommendations for these three systems:
1. Ubuntu (ARM)
Advantages
Ready-to-use: Provides official ARM images (e.g., Ubuntu Server 22.04 LTS) supporting hardware like Raspberry Pi and NVIDIA Jetson, requiring no complex configuration.
Cloud-native support: Built-in tools like MicroK8s, Docker, and Kubernetes, ideal for edge-cloud collaboration.
Long-term support (LTS): 5 years of security updates, meeting industrial stability requirements.
Rich software ecosystem: Access to AI/ML tools (e.g., TensorFlow Lite) and databases (e.g., PostgreSQL ARM-optimized) via APT and Snap Store.
Use Cases
Rapid prototyping: Quick deployment of Python/Node.js applications on edge gateways.
AI edge inference: Running computer vision models (e.g., ROS 2 + Ubuntu) on Jetson devices.
Lightweight K8s clusters: Edge nodes managed by MicroK8s.
Limitations
Higher resource usage (minimum ~512MB RAM), unsuitable for ultra-low-power devices.
2. Debian (ARM)
Advantages
Exceptional stability: Packages undergo rigorous testing, ideal for 24/7 industrial operation.
Lightweight: Minimal installation requires only 128MB RAM; GUI-free versions available.
Long-term support: Up to 10+ years of security updates via Debian LTS (with commercial support).
Hardware compatibility: Supports older or niche ARM chips (e.g., TI Sitara series).
Use Cases
Industrial controllers: PLCs, HMIs, and other devices requiring deterministic responses.
Network edge devices: Firewalls, protocol gateways (e.g., Modbus-to-MQTT).
Critical systems (medical/transport): Compliance with IEC 62304/DO-178C certifications.
Limitations
Older software versions (e.g., default GCC version); newer features require backports.
3. Yocto Project
Advantages
Full customization: Tailor everything from kernel to user space, generating minimal images (<50MB possible).
Real-time extensions: Supports Xenomai/Preempt-RT patches for μs-level latency.
Cross-platform portability: Single recipe set adapts to multiple hardware platforms (e.g., NXP i.MX6 → i.MX8).
Security design: Built-in industrial-grade features like SELinux and dm-verity.
Use Cases
Custom industrial devices: Requires specific kernel configurations or proprietary drivers (e.g., CAN-FD bus support).
High real-time systems: Robotic motion control, CNC machines.
Resource-constrained terminals: Sensor nodes running lightweight stacks (e.g., Zephyr+FreeRTOS hybrid deployment).
Limitations
Steep learning curve (BitBake syntax required); longer development cycles.
4. Comparison Summary
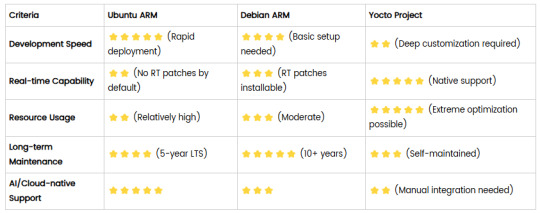
5. Selection Recommendations
Choose Ubuntu ARM: For rapid deployment of edge AI applications (e.g., vision detection on Jetson) or deep integration with public clouds (e.g., AWS IoT Greengrass).
Choose Debian ARM: For mission-critical industrial equipment (e.g., substation monitoring) where stability outweighs feature novelty.
Choose Yocto Project: For custom hardware development (e.g., proprietary industrial boards) or strict real-time/safety certification (e.g., ISO 13849) requirements.
6. Hybrid Architecture Example
Smart factory edge node:
Real-time control layer: RTOS built with Yocto (controlling robotic arms)
Data processing layer: Debian running OPC UA servers
Cloud connectivity layer: Ubuntu Server managing K8s edge clusters
Combining these systems based on specific needs can maximize the efficiency of IIoT edge computing.
0 notes
Text
How to Set Up UFW Firewall on Ubuntu 24.04 LTS in 5 Minutes
8 notes
·
View notes
Text
VPS Linux – VPS Tốt Nhất Giá Rẻ Cho Doanh Nghiệp và Cá Nhân
Trong thời đại công nghệ số phát triển mạnh mẽ, nhu cầu sử dụng máy chủ ảo (VPS) ngày càng tăng cao. Đặc biệt, VPS Linux đang trở thành lựa chọn hàng đầu cho những ai tìm kiếm giải pháp lưu trữ website, ứng dụng hoặc phát triển phần mềm với chi phí hợp lý. Bài viết này sẽ giúp bạn hiểu rõ vì sao VPS Linux là lựa chọn tốt nhất và đâu là nơi cung cấp dịch vụ VPS giá rẻ, chất lượng cao.
VPS Linux là gì?
VPS Linux là một dạng máy chủ ảo được cài đặt hệ điều hành Linux như Ubuntu, CentOS, Debian, Fedora… Linux được biết đến là hệ điều hành mã nguồn mở, miễn phí và cực kỳ ổn định. Khi sử dụng VPS Linux, người dùng có toàn quyền quản trị hệ thống như một máy chủ riêng, nhưng chi phí thấp hơn rất nhiều so với thuê máy chủ vật lý (dedicated server).
Ưu điểm vượt trội của VPS Linux
Tiết kiệm chi phí
So với các loại VPS chạy Windows, VPS Linux có giá rẻ hơn vì hệ điều hành Linux là mã nguồn mở, không yêu cầu chi phí bản quyền. Điều này giúp giảm thiểu chi phí tổng thể khi triển khai hệ thống.
Hiệu suất cao và ổn định
Linux nổi tiếng với khả năng vận hành mượt mà, ít tốn tài nguyên và chịu tải tốt. Điều này giúp VPS Linux hoạt động ổn định, phù hợp với các ứng dụng cần uptime cao như website thương mại điện tử, hệ thống CRM, phần mềm quản lý doanh nghiệp,…
Bảo mật cao
Linux được đánh giá rất cao về khả năng bảo mật. Hệ điều hành này thường xuyên được cập nhật các bản vá lỗi và cải tiến bảo mật. Ngoài ra, người dùng có thể tùy chỉnh firewall, cấu hình bảo mật chuyên sâu để tối ưu an toàn cho dữ liệu.
Linh hoạt và dễ tùy biến
Với VPS Linux, bạn có thể cài đặt bất kỳ phần mềm nào tương thích với Linux, tùy chỉnh toàn bộ hệ thống theo nhu cầu sử dụng. Đây là lựa chọn lý tưởng cho lập trình viên, nhà phát triển web hoặc các doanh nghiệp muốn kiểm soát hoàn toàn hệ thống máy chủ.
VPS Linux phù hợp với ai?
Doanh nghiệp nhỏ và vừa: Cần một giải pháp lưu trữ ổn định, bảo mật mà không tốn nhiều chi phí.
Lập trình viên và kỹ sư DevOps: Muốn môi trường làm việc tự do, có thể cài đặt và thử nghiệm các ứng dụng.
Người làm SEO, marketing online: Dùng để chạy tool, nuôi website vệ tinh, xây dựng hệ thống backlink.
Chủ website/blog cá nhân: Muốn có tốc độ tải nhanh, dễ quản lý và tối ưu SEO hiệu quả hơn so với hosting thông thường.
Tiêu chí chọn VPS Linux tốt nhất
Cấu hình phù hợp
Hãy lựa chọn gói VPS có cấu hình tương xứng với mục đích sử dụng: CPU, RAM, dung lượng SSD và băng thông cần được cân nhắc kỹ lưỡng. Nếu chỉ để chạy website, cấu hình từ 1 vCPU, 1GB RAM là đủ. Còn nếu chạy phần mềm nặng, nên chọn gói cao hơn.
Uptime cao, tốc độ ổn định
Một nhà cung cấp VPS uy tín sẽ cam kết uptime từ 99.9% trở lên, đảm bảo hệ thống luôn hoạt động ổn định, không gián đoạn.
Hỗ trợ kỹ thuật nhanh chóng
Dù bạn có giỏi kỹ thuật hay không, thì việc được hỗ trợ kịp thời khi gặp sự cố là cực kỳ quan trọng. Ưu tiên chọn nhà cung cấp có đội ngũ hỗ trợ 24/7, phản hồi nhanh, chuyên nghiệp.
Giá cả hợp lý
Không nên chỉ nhìn vào giá rẻ mà bỏ qua yếu tố chất lượng. Hãy so sánh giá cả đi kèm với cấu hình, dịch vụ đi kèm như sao lưu, bảo mật, IP riêng, hệ điều hành tùy chọn…
Gợi ý nhà cung cấp VPS Linux giá rẻ và chất lượng
Hiện nay trên thị trường có nhiều đơn vị cung cấp dịch vụ VPS Linux, tuy nhiên không phải đơn vị nào cũng đảm bảo về hiệu suất và hỗ trợ khách hàng. Dưới đây là một số nhà cung cấp đáng tin cậy:
Vultr: Cung cấp VPS Linux với giá chỉ từ $5/tháng. Hạ tầng hiện đại, datacenter toàn cầu, uptime ổn định.
DigitalOcean: Giao diện thân thiện, dễ sử dụng, phù hợp với lập trình viên. Tích hợp nhiều công cụ hỗ trợ dev.
AZDIGI: Nhà cung cấp Việt Nam uy tín, tốc độ cao, hỗ trợ kỹ thuật tiếng Việt nhanh chóng, giá hợp lý.
TinoHost: Giá rẻ, hỗ trợ tốt, đặc biệt có các gói VPS phù hợp cho người mới bắt đầu.
Một số lưu ý khi sử dụng VPS Linux
Cần có kiến thức cơ bản về quản trị Linux để sử dụng VPS hiệu quả.
Thường xuyên cập nhật phần mềm, vá lỗi để đảm bảo bảo mật.
Thiết lập backup định kỳ để tránh mất dữ liệu.
Sử dụng SSH key để tăng độ an toàn khi đăng nhập VPS.
Kết luận
VPS Linux là giải pháp tối ưu cho những ai muốn sở hữu một hệ thống lưu trữ mạnh mẽ, linh hoạt mà vẫn tiết kiệm chi phí. Với những ưu điểm vượt trội về hiệu năng, bảo mật và giá thành, VPS Linux thực sự là lựa chọn VPS tốt nhất giá rẻ dành cho cả cá nhân và doanh nghiệp. Hãy chọn cho mình một nhà cung cấp uy tín để khởi đầu thuận lợi và bền vững trong hành trình công nghệ số!
Tìm hiểu thêm: https://vndata.vn/vps-linux-gia-re/
0 notes
Text
1 note
·
View note
Text
VPS hosting Bhubaneswar

In today’s digitally driven business environment, performance, security, and scalability are not just desirable—they're essential. For businesses that have outgrown shared hosting or need more control over their web environment, VPS hosting (Virtual Private Server hosting) is the perfect middle ground. If you're based in Bhubaneswar and seeking fast, reliable, and secure hosting, then VPS hosting in Bhubaneswar from LexmeTech is your ideal solution.
In this article, we’ll explain what VPS hosting is, why it’s a game-changer for businesses in Bhubaneswar, and how LexmeTech delivers enterprise-grade VPS services tailored to local needs.
💡 What is VPS Hosting?
VPS hosting is a type of web hosting where a physical server is divided into multiple virtual environments, each with its own dedicated resources such as CPU, RAM, and storage. Unlike shared hosting, VPS hosting gives you root access and greater control, while being more cost-effective than a dedicated server.
VPS is ideal for:
Growing businesses with high-traffic websites
E-commerce platforms
Web developers and digital agencies
SaaS startups and app developers
Businesses needing enhanced data privacy and uptime
📍 Why Choose VPS Hosting in Bhubaneswar?
As Bhubaneswar rapidly establishes itself as a rising tech and startup hub in Eastern India, local businesses are increasingly seeking dependable infrastructure to fuel their digital ambitions. Opting for VPS hosting in Bhubaneswar ensures:
✅ Faster Local Access – Hosting your site or app on a VPS server close to your audience minimizes latency and improves performance. ✅ Local Support – You benefit from personalized technical support from professionals who understand your market. ✅ Data Sovereignty – Hosting locally makes compliance with Indian data regulations easier. ✅ Affordable Scalability – As your business grows, your VPS can scale with it—without breaking the bank.
🛠️ LexmeTech’s VPS Hosting Solutions in Bhubaneswar
At LexmeTech, we offer top-tier VPS hosting services in Bhubaneswar designed for speed, stability, and security. Our virtual private servers are optimized for performance and backed by expert local support.
🔹 Key Features of LexmeTech VPS Hosting:
Dedicated Resources: Get guaranteed RAM, CPU, and storage — no noisy neighbors.
Full Root Access: Customize your server environment to meet your exact needs.
SSD Storage: Lightning-fast solid-state drives for faster website and app load times.
99.9% Uptime Guarantee: Reliable infrastructure to keep your site online around the clock.
Choice of OS: Choose between Linux (Ubuntu, CentOS) or Windows, based on your project needs.
Scalable Plans: Easily upgrade your resources as your business grows.
24/7 Technical Support: Local, responsive support team available whenever you need help.
DDoS Protection & Firewalls: Advanced security features to protect your data and website.
🧩 VPS Use Cases in Bhubaneswar
Businesses across industries in Bhubaneswar are leveraging VPS hosting to power their digital platforms:
🛍️ E-commerce Stores: High uptime and speed for online retailers.
🧑🏫 EdTech & Institutions: Hosting secure learning portals and student databases.
🏢 Startups: Deploying SaaS platforms, APIs, and business apps.
⚙️ Developers & Agencies: Testing, staging, and launching multiple client projects.
🏥 Healthcare Providers: Hosting secure patient management systems and telemedicine apps.
🔐 Why Businesses Trust LexmeTech for VPS Hosting in Bhubaneswar
✅ Local Expertise
We understand the local digital landscape of Bhubaneswar, enabling us to tailor VPS hosting solutions that meet regional business needs.
✅ Affordable, Transparent Pricing
No hidden charges. Our VPS plans offer high performance at competitive rates — perfect for local businesses and startups.
✅ Customization Flexibility
We give you full control over server configurations, software installations, and updates — ideal for developers and tech teams.
✅ Speed & Security First
Our servers use SSD storage, cloud backups, and robust security protocols to ensure fast and safe hosting.
📈 When Should You Upgrade to VPS Hosting?
If your current shared hosting environment is causing:
Frequent downtime
Slow load times
Limited customization options
Security concerns
High traffic volumes
… then it’s time to consider VPS hosting from LexmeTech. We help you migrate smoothly and set up a high-performance server environment without disruption.
✅ Conclusion: Scale Smarter with VPS Hosting in Bhubaneswar by LexmeTech
In a digital-first economy, your website or application is the face of your business. Don’t let slow, unstable hosting hold you back. With VPS hosting in Bhubaneswar from LexmeTech, you get the power, performance, and local support you need to grow confidently online.
Whether you’re a tech startup, a local business, or an enterprise going digital — our VPS solutions are designed to deliver speed, security, and scalability at every stage.
📞 Get Started Today with a Free Consultation
Talk to our VPS experts today and find the perfect plan for your business.
🌐 Website: www.lexmetech.com 📧 Email: [email protected] 📞 Phone: +91-9178521173
0 notes