#Communication Security
Explore tagged Tumblr posts
Text


#politics#us politics#political#donald trump#news#president trump#elon musk#american politics#jd vance#law#lgbt#lgtbtq#lesbian#gay#bisexual#pansexual#lgbtqiia+#lgbtq community#lgbt pride#pride#america#us news#freedom#privacy#spies#freedom of speech#homeland security#civil rights#trump admin#president donald trump
43K notes
·
View notes
Text
Guys you should totally let him out he is fellow human☺️☺️



#sun yapping#fnaf#art#fnaf daycare attendant#fnaf sun#fnaf security breach#fnaf sb#fnaf fanart#moondrop dca#moondrop fnaf#moondrop fanart#moon au#fnaf moon#moondrop#fnaf daycare au#dca art#self insert#yn#dca au#dca fanart#dca community#dcau#dca fandom#dca moon#dc art#fnaf sun and moon#sundrop and moondrop
5K notes
·
View notes
Text

Fluster the Moonman!! Make that baby girl stutter with butterflies!! >:D
I drew this when my pc was still working :']
#hierba art#fnaf dca#fnaf dca older sibling! au#dca older sibling au#dca fandom#fnaf daycare attendant#dca community#dca au#fnaf moon#fnaf moon x y/n#fnaf moon x reader#fnaf moon fanart#moon fnaf#dca x reader#dca art#fnaf dca au#moon fanart#moondrop x reader#moon x reader#moon sb#moondrop#moondrop fnaf#security breach daycare attendant#fnaf au#moondrop fanart#moondrop security breach
2K notes
·
View notes
Text
Securing Communications: The Role of Cipher Machines and Password Cards

In today's digital age, securing communications is paramount to protect sensitive information from interception and unauthorized access. Cipher machines and password cards play crucial roles in this endeavor, offering robust encryption and authentication mechanisms to safeguard data transmission and access.
Cipher Machines: Cipher machines are sophisticated devices used to encrypt and decrypt messages, ensuring the confidentiality and integrity of communications. These machines employ complex cryptographic algorithms to scramble plaintext messages into ciphertext, making them unreadable to unauthorized parties. By incorporating cipher machines into communication systems, organizations can prevent eavesdropping and maintain the privacy of sensitive information.
Password Cards: Cipher Machines and Password Cards serve as physical tokens or devices used to store and manage authentication credentials, such as passwords or PINs. These cards feature grids of alphanumeric characters, each corresponding to a unique password. Users can reference the grid to retrieve their passwords when logging into secure systems or accessing protected resources. Password cards provide an additional layer of security by requiring users to possess the physical token in addition to knowledge of the password.
Encryption Strength: Both cipher machines and password cards contribute to the strength of encryption and authentication mechanisms. Cipher machines utilize robust encryption algorithms and keys to transform plaintext messages into ciphertext, ensuring that even if intercepted, the message remains unintelligible to unauthorized parties. Similarly, password cards enhance authentication security by requiring the possession of physical tokens, mitigating the risk of unauthorized access through password theft or brute-force attacks.
Data Confidentiality: Cipher machines and password cards play crucial roles in preserving the confidentiality of sensitive information during transmission and access. Cipher machines encrypt messages before transmission over insecure channels, preventing unauthorized interception and decryption of the communication. Password cards protect access to secure systems and resources by verifying the identity of users through authentication credentials stored on the physical token.
Authentication Mechanisms: Password cards augment authentication mechanisms by introducing multifactor authentication (MFA) capabilities. In addition to passwords or PINs, users must possess the physical token to authenticate themselves, adding an extra layer of security. This multifactor approach reduces the likelihood of unauthorized access, even if passwords are compromised or stolen.
Regulatory Compliance: Incorporating cipher machines and password cards into communication systems helps organizations comply with regulatory requirements and industry standards for data security and privacy. Many regulatory frameworks mandate the use of strong encryption and authentication mechanisms to protect sensitive information and prevent data breaches. Cipher machines and password cards offer robust solutions to meet these compliance requirements effectively.
User-Friendly Interfaces: Despite their advanced encryption and authentication capabilities, cipher machines and password cards are designed to be user-friendly and accessible. Cipher machines may feature intuitive interfaces for inputting plaintext messages and encryption keys, while password cards provide convenient grids for retrieving passwords during authentication processes. This user-friendly design ensures that security measures do not impede productivity or usability.
Continuous Innovation: Cipher machines and password cards continue to evolve in response to emerging threats and technological advancements. Manufacturers and developers invest in research and development to enhance encryption algorithms, authentication protocols, and physical security features. By staying abreast of evolving security threats and best practices, cipher machines and password cards remain effective tools for securing communications in an ever-changing digital landscape.
In summary, cipher machines and password cards play integral roles in securing communications and protecting sensitive information from unauthorized access. By leveraging robust encryption and authentication mechanisms, organizations can maintain data confidentiality, comply with regulatory requirements, and mitigate the risk of data breaches. As technology evolves, cipher machines and password cards will continue to adapt and innovate to meet the evolving challenges of cybersecurity.
Get More Insights On This Topic: Cipher Machines And Password Cards
#Cipher Machines#Password Cards#Encryption#Authentication#Data Security#Cryptography#Communication Security#Information Protection
0 notes
Text

sometimes you just need to hear it v some stills below the cut v



#fnaf#five nights at freddy's#fnaf security breach#fnaf daycare attendant#fnaf sun moon#dca fandom#dca x y/n#artists on tumblr#fan art#digital art#animation#gif#watercolour background from unsplash!! (phenomenal free photos website)#it's been a tough one lately!!! ooooh boy#its hard to caption this one because I fundamentally want to stay positive but it's been.. difficult. with everything going on in the world#so I broke this WIP out from a few months ago when i was having a bad episode of my own and was trying to make something to get me thru it#i felt like it was worth finishing and sharing now#If you're someone that needs art to get through scary stuff (i very much am) then we're in this together!#I'm gonna keep making stuff and cherishing this community#and we're gonna get through it all together <3
5K notes
·
View notes
Text
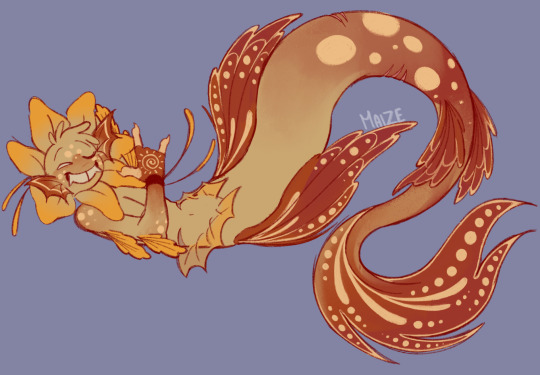
My first baby

And my second baby.
I redesigned them because I didn’t like the fact that Jinks looked green lol
@itsmuffiiee PAY THIS NO MIND. I will not torture you with redrawing them. Not after the kelp prison you’ve been locked in.
Everyone else, enjoy your lunch in the meantime. I have other stuff that I’m working on, but it’s gonna take some time.
Ima leave before I see the decorum leave your bodies. /j
#mxiize#fnaf#fnaf security breach#fnaf daycare attendant#dca community#fnaf dca#sun fnaf#digital aritst#fnaf lol#fnaf fandom#fnaf sb#fnaf moon#sun and moon fnaf#fnaf au#jokester au#hijinks fnaf#mischief fnaf#fnaf sun#sundrop moondrop#sun animatronic#sundrop#sunrise#moondrop fnaf#moon fnaf#moondrop#mer moon#mer sun#merfolk#moon#dca fandom
4K notes
·
View notes
Text


Ding dong, someone’s at the door
How did they find out where I live?
#dca fandom#fnaf dca#dca fanart#dca art#fnaf daycare attendant#fnaf sun#fnaf moon#moondrop#my art tag#feeling the Halloween vibes with this one#moon dca#dca moondrop#dca community#dca moon#dca sun#dca sundrop#sun dca#sundrop#moondrop fnaf#moon fnaf#fnaf sb#fnaf security breach#fnaf fanart#fnaf sundrop
4K notes
·
View notes
Text
Silly outfits for them cause its annoying drawing their frills all the time 😭😭
Tsukouis' Commissions



#my art#my artwork#fnaf#fnaf sb#five nights at freddy’s#fnaf security breach#fnaf dca#dca moon#dca sun#dca fanart#dca fandom#dca community#dca#fnaf sun#fnaf moon#fnaf daycare attendant#fnaf sb fanart#dca art#sundrop#moondrop#daycare attendant#moon fnaf#sun fnaf#daycare attendant sun#daycare attendant moon#daycare attendant fnaf
3K notes
·
View notes
Text
Last Names
(Click for better quality)
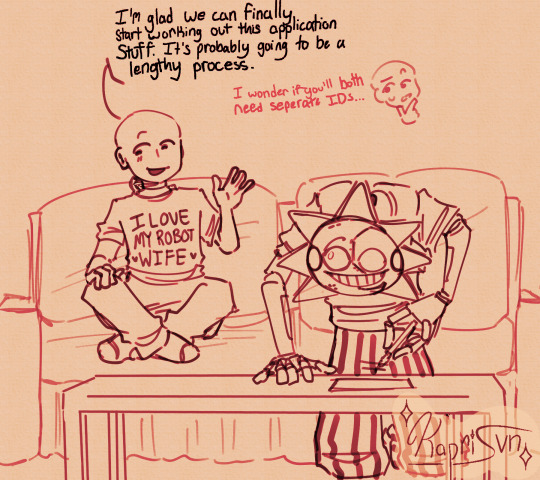


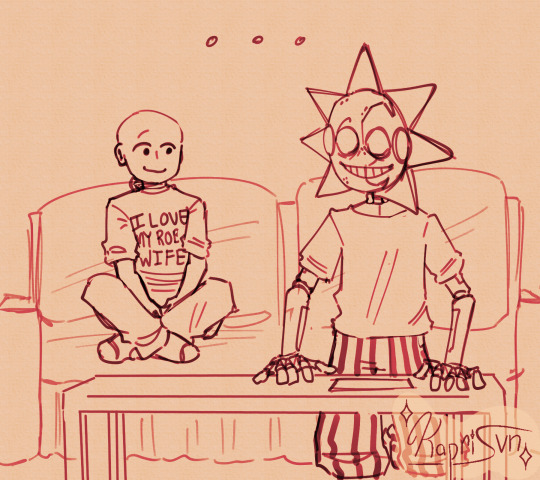




"KAPRI YOU CAN'T POST THE AFTER STORY FOR CHASING STARS YOU HAVEN'T EVEN POSTED THE FIRST CHAPTERS YET!!!"
🤫🙂↔️
This comic is kinda shitty but you get the point XD
Bonus clothed CS Moon!

#Anyone else desperately want to give these jesters your last name???#No???#Just me???#k :(#Chasing Stars#chasing stars au#Ngl I feel like I seen a comic like this somewhere so if I accidently copied someone Im sorry#fnaf#fnaf security breach#moon fnaf#sun fnaf#daycare attendant#dca community#moon x reader#sun x reader#sun x y/n#moon x y/n#fnaf sun x reader#fnaf moon x reader#sundrop x reader#moondrop x reader#dca x reader#dca x y/n#daycare attendant x reader#fnaf moon#fnaf sun#kapri's collection
3K notes
·
View notes
Text

"Where do you think YOU'RE going~?"
#dca!serial killer au#sk sun#serial killer sun#fnaf sun#fnaf sundrop#sundrop#fnaf daycare attendant#fnaf dca#dca au#sun fnaf#dca fandom#dca community#sunhinged#unhinged sun#tw knife#fnaf security breach#fnaf sb
1K notes
·
View notes
Text
silly Y/N


Yes, silly silly y/n
Oh how I dream to be you..
#fanart#sun and moon security breach#fnaf dca#artists on tumblr#eclipse fnaf#eclipse x reader#Eclipse × y/n#GOD WHY IS HE SO-#incorrect quotes#Comment your favorite incorrect quote and maybe I'll draw it after I finish drawing my other quotes#please no repost thanks#sundrop fnaf#moondrop fnaf#Slight suggestive warning#@TheYawningCat#dca fandom#daycare attendent#daycare attendant fnaf#fnaf daycare attendant#dca au#dca community#dca fanart
1K notes
·
View notes
Text
Endling au masterpost

i will update this post regulary with all the comics, refs, ect.
tag: dca! endling au
Sumery:
You are a travelling artist, making your way through the silent snowy ruins of a world long gone. The endless Winter is harsh and you have not seen another human in years. On your journey, you find an old abandoned mall. Within its silent walls, you stumble upon a what seems to be a long dead robot. It is not an uncommon find, but still quite intriguing. The celestial robot is certainly interesting enough for your sketchbook. or the wolrd ended but its okay since you now have a robotic friend :D
Comics:
its real guys (pt1)
what a great start (pt2)
Refs:
Endling y/n Ref
credits:
The au is mainly inspired by girl last tour, and because it started as a girl last tour au, there will be alot of ideas that are in that manga aswell
thank you so much @amarynthian-chronicles for helping me with writing
alot of my dca headcannons are from varios fanfictions, but (probably) mainly from i see you sundrop by ShiraCheshire
feel free to send me ask
i am also completly fine with fan works, using art of the au as pfp, making your own storys and such. all speculations is welcome.
#boy i didnt enjoy drawing this lighting#anis sketches#dca x y/n#fnaf dca#fnaf daycare attendant#dca fandom#fnaf moon x y/n#fnaf moon#fnaf moon x reader#dca au#dca community#daycare attendant#dca x reader#dca! endling au#fnaf security breach#fnaf sun#moondrop x reader#sundrop x reader#moondrop#sundrop
981 notes
·
View notes
Text
Pray for sun guys hes gonna be trapped there for awhile😔🫡

#sun yapping#fnaf#sundrop#fnaf daycare attendant#art#fnaf sun#fnaf security breach#fnaf sb#fnaf fanart#sundrop fnaf#fnaf sundrop#sundrop and moondrop#moondrop dca#moondrop fnaf#moondrop fanart#moondrop#dca#dca art#dcaau#dca fandom#dca community#dca fanart
3K notes
·
View notes
Text

(Old) I just think they would be very good friends qwq ✨💕💕
#artists on tumblr#digital art#sun and moon sb#sun and moon security breach#fnaf security breach#sun and moon fanart#sun and moon fnaf#fnaf art#fivenightsatfreddyssecuritybreach#fivenightsatfreddysfanart#fnaf sb#fnaf sun#fnaf moon#fnaf glamrock chica#glamrock chica#dca moon#moon dca#fnaf dca#dca fandom#fnaf fanart#doodle#five nights at freddy's#five nights at freddy’s art#dca fanart#dca community#chica the chicken#five nights at freddy's security breach
1K notes
·
View notes
Text
Where I post from btw

#berenice yappies#agere community#sfw interaction only#sfw agere#agere post#little space sfw#fnaf security breach#fnaf daycare attendant#sundrop#moondrop
774 notes
·
View notes