#Document Data Entry Service Provider
Explore tagged Tumblr posts
Text
Best Document Data Entry Services at Affordable Prices

Document data entry services involve inputting useful information from documents into a database for future use. This may include paper documents, online forms, digital files, or scanned images. The goal of the service is to create a searchable and accessible database to retrieve and analyze information easily. This task is essential for a business to maintain accurate records, support better decision-making, and also for improving operational efficiency. It is one of the best methods to take one's company to the top position in the global market.
#Document Data Entry Services#Document Data Entry#Data Entry Document#Document Data Entry Services India#Document Data Entry Companies#Outsource Document Data Entry#Document Data Entry Service Provider#Document Data Entry Companies in India
0 notes
Text


🦄The Sims 4🦄
🍾Office & Bartending Career📝
💕Early Release 5.4.2024💕
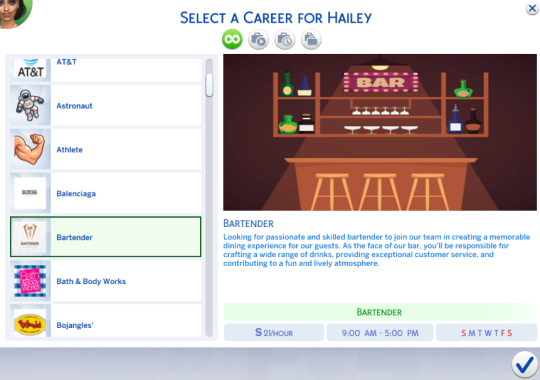
Bartender
Looking for passionate and skilled bartender to join our team in creating a memorable dining experience for our guests. As the face of our bar, you'll be responsible for crafting a wide range of drinks, providing exceptional customer service, and contributing to a fun and lively atmosphere.
💕Promotion Includes 5 PTO days off💕
Bartender
Tasting Room Bartender/Server
Bartender - Expedition Cafe
Event Bartender
Bartender For Axe Throwing Bar
Allow Teen
Allow Young Adult
Allow Adult
Allow Elder
Office
💕Promotion Includes 5 PTO days off💕
In this career, you may perform clerical tasks, such as filling out paperwork, creating documents, and doing data entry. Other responsibilities often involve handling communication, whether by answering phones, writing emails, or mailing written correspondences.
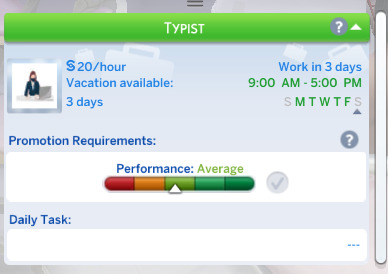
Typist
Office Assistant
Personal Assistant
Virtual Administrative Assistant
Administrative Assistant
Front Desk Receptionist
Allow Teen
Allow Young Adult
Allow Adult
Allow Elder
DOWNLOAD NOW
#gaming#the sims 4#the sims university#the sims 4 cc#sims 4#celebrities#the sims 4 mods#sims 4 mods#nicki minaj#pink#cardi b#pokemon cards#post card#baths#cold weather#christmas#electricity#office#desk#bathroom#bedroom#couch#floor#bartender#t pain#soft aesthetic#aesthetic#pink nation#pink aesthetic#soft pink
25 notes
·
View notes
Text
How does data capture services benefit a business?
Data Capture services

In the current digital age, data secrecy is recognized as the most valuable asset for any business. However, collecting it manually and investing time in it personally is time-consuming and prone to errors, as it is subject to matters. That’s where data capture services come in. While these services enable the enterprises to collect, organize, store and process information quickly and accurately, resulting in more informed decisions and enhanced efficiency for the organization to go ahead.
Faster Access to Information:
Data-capturing services automate the process of gathering data from various sources, including documents, forms, emails, and other digital assets. As this process speeds up the process to access critical information, enabling employees to work more towards the betterment efficiently and respond promptly towards customer needs or business challenges.
Improved Accuracy and Reduced Errors:
Manual data entry and filling often leads and thrives towards mistakes as they can affect the ongoing business operations. With data capturing technology, information is extracted using tools such as OCR (Optical Character Recognition) and with the assistance of AI, ensuring a level of higher accuracy is maintained. At the same time, fewer errors means better outcomes and more reliable reports that have been generated.
Streamlined Business Operations:
By automating data collection, businesses can save time and resources. While the staff and operating users no longer have the need to spend hours by entering data by hand or their own, allowing them to have a keen look on more valuable tasks and selective concerns. This heads and drives toward enhanced productivity and smoother workflows and operations.
Enhanced Customer Service:
Quick and precise data collection assures that the customer records, queries, and transactions are handled efficiently and effectively with this technique adaption. This leads towards faster service delivery, fewer complaints, and a better overall customer experience—key factors in staying competitive.
Better Decision-Making:
Accurate and well-organized data gives leaders a clearer view of their business performance. With real-time insights from data capture, they can make informed and clear decisions by identifying the current trends, and respond to market changes with confidence with a complete detailed report.
Scalable for Growing Businesses:
As a business grows, managing large volumes of data becomes more difficult. Data capture services scale and grow with your company, handling increasing amounts and multiple sets of information without sacrificing the speed or accuracy. Many businesses trust experts like Suma Soft, IBM, Cyntexa, and Cignex for efficient data capture solutions. These providers offer tailored services that boost data accuracy, ensure fast turnaround, and support long-term digital transformation.
#it services#technology#saas#software#saas development company#saas technology#digital transformation
2 notes
·
View notes
Text
The Strategic Role of Check-in Kiosks in Military Airport Terminals

Military airport terminals operate under heightened security and efficiency demands compared to their commercial counterparts. These facilities not only handle routine transport of service members but also play crucial roles in logistics, emergency deployments, and diplomatic missions. In such high-stakes environments, even minor inefficiencies or security lapses can have significant consequences.
To meet these challenges, many military terminals are turning to check-in kiosk technology—automated, self-service systems that streamline passenger processing and improve terminal security. These kiosks, equipped with advanced features such as biometric scanning, real-time data synchronization, and user-friendly interfaces, are reshaping the operational landscape of military air travel. In this blog, we explore how kiosk technology enhances security, boosts efficiency, improves user experience, and supports long-term cost-effectiveness and emergency readiness in military airport terminals.
Enhancing Security Protocols with Check-in Kiosks
Security is paramount in military environments, and check-in kiosks significantly contribute to strengthening existing protocols. These kiosks do more than expedite the check-in process—they integrate seamlessly with military-grade security systems to ensure rigorous identity verification and real-time data updates.
Biometric Integration for Identity Verification
One of the standout features of military check-in kiosks is biometric integration. Fingerprint scans, iris recognition, and facial recognition ensure that only authorized personnel gain access to secured areas. These systems eliminate the risks associated with lost or forged ID cards and allow for multi-factor authentication, which is critical in sensitive operations.
Biometric data is instantly matched against military personnel databases and watchlists, providing a higher level of accuracy and preventing unauthorized access. The process is not only secure but also faster and less intrusive than traditional methods, offering a seamless experience for users.
Real-Time Data Synchronization with Security Networks
Check-in kiosks in military terminals are linked to centralized security networks, allowing for real-time synchronization of data. When a service member checks in, their identity, assignment, and travel itinerary are cross-verified with military systems to detect inconsistencies or threats.
This instant communication enhances threat detection and tracking capabilities, allowing security personnel to respond swiftly to anomalies. Furthermore, in the event of a security breach, kiosks provide critical logs and timestamps to aid investigation and resolution.

Increasing Operational Efficiency in Terminal Management
Military terminals operate around tight schedules and high throughput. By automating check-in procedures, kiosks alleviate common bottlenecks and enhance operational efficiency.
Automated Boarding Pass and ID Issuance
Traditional check-in desks involve manual data entry and document verification, which can slow down the boarding process. In contrast, automated kiosks issue boarding passes and temporary access credentials within seconds, drastically reducing processing time.
Kiosks can print, scan, and digitally store documentation, minimizing the likelihood of human error. This not only improves accuracy but also enhances compliance with standardized military travel protocols.
Reduced Staff Workload and Resource Allocation
By handling repetitive check-in tasks, kiosks free up human resources for more critical responsibilities. Personnel previously tied to desk duties can be reassigned to areas such as tactical operations, logistics support, or passenger assistance.
This optimized resource allocation ensures that the terminal functions more smoothly, even during peak hours or large-scale deployments. It also reduces the risk of operational delays, contributing to overall mission readiness.
Improving User Experience for Military Personnel and Visitors
Ease of use is crucial in high-pressure environments. Military check-in kiosks are designed with user-centric interfaces, ensuring accessibility for all users, including service members, dependents, and visitors.
Multilingual Support and Accessibility Features
Military airports cater to diverse users from various linguistic and cultural backgrounds. Kiosks equipped with multilingual options ensure that language barriers do not impede check-in or access.
Moreover, features such as voice commands, screen magnification, and wheelchair-accessible interfaces make these kiosks usable for individuals with disabilities. This commitment to inclusivity aligns with military values and enhances the overall user experience.
24/7 Availability and Minimizing Congestion
Unlike staffed check-in counters, kiosks offer uninterrupted service around the clock. This is especially beneficial in military operations where flights and deployments can occur at odd hours or on short notice.
By distributing the check-in load across multiple kiosks, these systems minimize terminal congestion, allowing for smoother passenger flow and reduced wait times. This is particularly valuable during mobilizations, drills, or emergency evacuations.
Cost-Effectiveness and Long-Term Savings
Implementing kiosk systems in military terminals requires upfront investment, but the long-term financial benefits make a compelling case for adoption.
Reduction in Manual Processing Costs
Kiosks reduce the need for manual data entry, paper forms, and physical staffing, all of which incur recurring costs. Digital processes streamline administrative workflows and lower the chances of clerical errors, which can be costly and time-consuming to fix.
In addition, kiosks help reduce the environmental footprint of military operations by minimizing paper use—a growing priority in defense logistics.
Scalability to Meet Future Demands
Modern kiosk systems are built with modular and scalable designs, allowing for future upgrades without major overhauls. As military travel protocols evolve, new software features or hardware modules (e.g., upgraded biometric sensors or contactless payment capabilities) can be easily integrated.
This future-proofing makes kiosk systems a strategic investment, capable of adapting to shifting operational needs and technological advancements.

Supporting Emergency and Contingency Operations
Military terminals must remain operational under all circumstances, including crises. Kiosks offer resilience and flexibility during emergencies, supporting both evacuation and redeployment efforts.
Rapid Reconfiguration for Emergency Protocols
In the event of a crisis—whether it’s a natural disaster, base lockdown, or global conflict—check-in kiosks can be rapidly reprogrammed to follow new protocols. For example, they can be configured to prioritize certain personnel categories, enable emergency passes, or facilitate health screenings during pandemics.
This capability allows terminals to maintain order and operational continuity, even in high-stress environments.
Reliable Communication Channels for Critical Updates
During emergencies, timely and accurate communication is essential. Kiosks can function as broadcast hubs, displaying critical alerts, evacuation routes, or mission updates directly on the screen.
Some systems can also send automated SMS or email updates to personnel, ensuring that everyone receives the necessary information regardless of their physical location within the terminal. This functionality is invaluable during fast-moving operations where traditional communication lines may be overloaded or unavailable.
Conclusion
Check-in kiosks are no longer just a convenience feature—they are a strategic asset in military airport terminals. From strengthening security with biometric authentication and real-time data sync, to improving operational efficiency and delivering a seamless user experience, kiosks represent a significant leap forward in military logistics technology.
They not only reduce costs and optimize personnel usage, but also enhance readiness and resilience during emergencies. With scalable architectures and support for the latest security features, kiosk systems are well-positioned to meet the future demands of military air transport.
For defense organizations aiming to modernize their infrastructure and improve mission efficiency, adopting kiosk technology is not just an option—it’s a mission-critical necessity.
#kiosk#technology#software#business#development#programming#productivity#airport#check in kiosk#tech#techtrends#selfservicekiosk#kioskmachine#innovation#kiosks#panashi#techinnovation#digitaltransformation
2 notes
·
View notes
Text
**From PCI DSS to HIPAA: Ensuring Compliance with Robust IT Support in New York City**
Introduction
In contemporary digital world, organisations are a growing number of reliant on science for their operations. This dependence has caused a heightened focus on cybersecurity and compliance specifications, specifically in regulated industries like healthcare and finance. For services working in New York City, wisdom the nuances of compliance frameworks—specifically the Payment Card Industry Data Security Standard (PCI DSS) and the Health Insurance Portability and Accountability Act (HIPAA)—is quintessential. Navigating those policies requires potent IT give a boost to, which encompasses everything from community infrastructure to documents management.
With the rapid advancement of technological know-how, organizations ought to additionally remain abreast of high-quality practices in details technologies (IT) give a boost to. This article delves into how organizations can ensure that compliance with PCI DSS and HIPAA thru triumphant IT processes whilst leveraging materials from accurate providers like Microsoft, Google, Amazon, and others.
Understanding PCI DSS What is PCI DSS?
The https://brooksxaoj631.over.blog/2025/04/navigating-cybersecurity-in-the-big-apple-essential-it-support-solutions-for-new-york-businesses.html Payment Card Industry Data Security Standard (PCI DSS) is a group of safety principles designed to look after card tips all the way through and after a economic transaction. It was once proven by using significant credit card enterprises to fight growing times of fee fraud.
Why is PCI DSS Important?
Compliance with PCI DSS enables groups defend touchy economic recordsdata, thereby modifying visitor trust and slicing the possibility of info breaches. Non-compliance can bring about intense consequences, such as hefty fines or maybe being banned from processing credit score card transactions.

youtube
Key Requirements of PCI DSS Build and Maintain a Secure Network: This carries fitting a firewall to preserve cardholder knowledge. Protect Cardholder Data: Encrypt kept files and transmit it securely. Maintain a Vulnerability Management Program: Use antivirus utility and develop protect structures. Implement Strong Access Control Measures: Restrict entry to in basic terms people that want it. Regularly Monitor and Test Networks: Keep observe of all get admission to to networks and aas a rule look at various protection tactics. Maintain an Information Security Policy: Create insurance policies that cope with defense necessities. Exploring HIPAA Compliance What is HIPAA?
The Health Insurance Portability and Accountability Act (HIPAA) sets the ordinary for conserving sensitive sufferer know-how in the healthcare trade. Any entity that offers with blanketed well being know-how (PHI) have got to adjust to HIPAA regulations.
Importance of HIPAA Compliance
HIPAA compliance no longer handiest protects affected person privateness however also guarantees more suitable healthcare outcome with the aid of permitting maintain sharing of affected person data between permitted entities. Violations can cause titanic fines, prison results, and wreck to popularity.
" style="max-width:500px;height:auto;">

Core Components of HIPAA Compliance Privacy Rule: Establishes countr
2 notes
·
View notes
Text
I'm Not A Writer. But All I Have Is Words
You’ve got the ideas. I’ve got the executive function.
I wish it were possible to stream my thoughts with all the flavours, smells, feelings, emotions and tactile sensations attached. Instead, I have to convert that sensory-rich stream into two-dimensional letters in an attempt to convey the experience. That’s why expressing what I feel is the hardest thing about using words.
If I have to communicate with other human beings, I prefer to talk about things that are understandable for both sides. I like to use language as a utility tool. To ask and answer questions, explain processes, share information, or establish rules for cooperation.
Yet when it comes to humans, they delight in overdoing the word dress-up even for those kinds of interactions. It’s draining that if I want to network with someone, I need to create all this hype, provide value, and employ intricate verbal gymnastics to explain what I do and why I’m a great choice.
There are tons of incredibly talented writers who can produce a mesmerising pitch, that would market them as the best thing since invention of a mobile phone. But. Will that pitch translate when it comes to the actual job?
* * *
If I could do it my way, this is how I’d approach you as a prospective client:
Hello. I’m Anna, an actually autistic virtual assistant providing general admin services for neurodivergent entrepreneurs. Do you want to work with me? Here’s my website www.autisticva.com Or you can book a free discovery chat If not, tell business people you know who would. Anna
I hope you haven’t spilt your coffee or tea on the keyboard because it’s so extremely effective. I know. I’m getting fully booked up and can raise my prices just after sending this single message (that was sarcasm).
* * *
But let’s break it down and analyse it.
Logically.
That's how an ASD, ADHD or AuDHD brain would translate that shorthand:
“Actually autistic” Oh, it means she gets it because she has a similar lived experience. And I can expect traits like strong focus, attention to detail, curiosity, self-teaching, punctuality, honesty, loyalty, non-judgement, directness, reliability, trustworthiness… and some awkwardness too. “Virtual assistant” Ha, she works remotely and is a contractor. It means I won’t have to fork out for payroll, insurance or give her a desk. We can work on the internets without having to meet in person and become besties. Yay! “Providing general admin” That means emails, files, documents, data entry, calendars, spreadsheets, organising, proofreading. I bet she’s good with Microsoft Office, and Google Workspace at minimum. But since she’s autistic—that means she might be even more capable or willing to learn. “For neurodivergent entrepreneurs” Hey, I’m neurodivergent and I have a business! That’s me she’s talking about. “Do I want to work with her?” I’d like to at least check out what she’s about—see if she offers what I want and other finer details before I decide. Website and booking link Oh cool, I can check her out immediately and do my lurking, thinking, deciding—or dive right in if I want to. “If not, tell business people you know who would”. Aww, she’s honest, upfront, not pushy, and has the guts to reach out. If I dare to pass on the opportunity I’ll at least help by connecting her with my business BFFs. Our tribe needs to stick together because living in the NT world is hard and we need all the help we can get.
* * *
See? I wouldn’t have to spend 67 minutes to write 266 words when I could encapsulate the whole message in 2 minutes and 7 seconds—in just 57 words. (What’s up with all those 7s?!)
Sure, I could ask ChatGPT to write 10,000 words about what I could do for you—but words won’t get the shit done.
I’m not a writer.
I’m a doer, a thinker, and a problem solver.
Don't ask me to tell you poems about what I can do.
And let me express myself by doing stuff for you.
#actually autistic#autistic adult#autistic#neurodivergent#virtual assistant#audhd#asd#autistic entrepreneur#communication#autistic thoughts#autistic writing#autistic women#autistic life#autistic social interaction#adhd#take it or leave it#feeling unseen#looking for my tribe#autistic journey#unapologetically autistic
2 notes
·
View notes
Text

AI’s Role in Business Process Automation
Automation has come a long way from simply replacing manual tasks with machines. With AI stepping into the scene, business process automation is no longer just about cutting costs or speeding up workflows—it’s about making smarter, more adaptive decisions that continuously evolve. AI isn't just doing what we tell it; it’s learning, predicting, and innovating in ways that redefine how businesses operate.
From hyperautomation to AI-powered chatbots and intelligent document processing, the world of automation is rapidly expanding. But what does the future hold?
What is Business Process Automation?
Business Process Automation (BPA) refers to the use of technology to streamline and automate repetitive, rule-based tasks within an organization. The goal is to improve efficiency, reduce errors, cut costs, and free up human workers for higher-value activities. BPA covers a wide range of functions, from automating simple data entry tasks to orchestrating complex workflows across multiple departments.
Traditional BPA solutions rely on predefined rules and scripts to automate tasks such as invoicing, payroll processing, customer service inquiries, and supply chain management. However, as businesses deal with increasing amounts of data and more complex decision-making requirements, AI is playing an increasingly critical role in enhancing BPA capabilities.
AI’s Role in Business Process Automation
AI is revolutionizing business process automation by introducing cognitive capabilities that allow systems to learn, adapt, and make intelligent decisions. Unlike traditional automation, which follows a strict set of rules, AI-driven BPA leverages machine learning, natural language processing (NLP), and computer vision to understand patterns, process unstructured data, and provide predictive insights.
Here are some of the key ways AI is enhancing BPA:
Self-Learning Systems: AI-powered BPA can analyze past workflows and optimize them dynamically without human intervention.
Advanced Data Processing: AI-driven tools can extract information from documents, emails, and customer interactions, enabling businesses to process data faster and more accurately.
Predictive Analytics: AI helps businesses forecast trends, detect anomalies, and make proactive decisions based on real-time insights.
Enhanced Customer Interactions: AI-powered chatbots and virtual assistants provide 24/7 support, improving customer service efficiency and satisfaction.
Automation of Complex Workflows: AI enables the automation of multi-step, decision-heavy processes, such as fraud detection, regulatory compliance, and personalized marketing campaigns.
As organizations seek more efficient ways to handle increasing data volumes and complex processes, AI-driven BPA is becoming a strategic priority. The ability of AI to analyze patterns, predict outcomes, and make intelligent decisions is transforming industries such as finance, healthcare, retail, and manufacturing.
“At the leading edge of automation, AI transforms routine workflows into smart, adaptive systems that think ahead. It’s not about merely accelerating tasks—it’s about creating an evolving framework that continuously optimizes operations for future challenges.”
— Emma Reynolds, CTO of QuantumOps
Trends in AI-Driven Business Process Automation
1. Hyperautomation
Hyperautomation, a term coined by Gartner, refers to the combination of AI, robotic process automation (RPA), and other advanced technologies to automate as many business processes as possible. By leveraging AI-powered bots and predictive analytics, companies can automate end-to-end processes, reducing operational costs and improving decision-making.
Hyperautomation enables organizations to move beyond simple task automation to more complex workflows, incorporating AI-driven insights to optimize efficiency continuously. This trend is expected to accelerate as businesses adopt AI-first strategies to stay competitive.
2. AI-Powered Chatbots and Virtual Assistants
Chatbots and virtual assistants are becoming increasingly sophisticated, enabling seamless interactions with customers and employees. AI-driven conversational interfaces are revolutionizing customer service, HR operations, and IT support by providing real-time assistance, answering queries, and resolving issues without human intervention.
The integration of AI with natural language processing (NLP) and sentiment analysis allows chatbots to understand context, emotions, and intent, providing more personalized responses. Future advancements in AI will enhance their capabilities, making them more intuitive and capable of handling complex tasks.
3. Process Mining and AI-Driven Insights
Process mining leverages AI to analyze business workflows, identify bottlenecks, and suggest improvements. By collecting data from enterprise systems, AI can provide actionable insights into process inefficiencies, allowing companies to optimize operations dynamically.
AI-powered process mining tools help businesses understand workflow deviations, uncover hidden inefficiencies, and implement data-driven solutions. This trend is expected to grow as organizations seek more visibility and control over their automated processes.
4. AI and Predictive Analytics for Decision-Making
AI-driven predictive analytics plays a crucial role in business process automation by forecasting trends, detecting anomalies, and making data-backed decisions. Companies are increasingly using AI to analyze customer behaviour, market trends, and operational risks, enabling them to make proactive decisions.
For example, in supply chain management, AI can predict demand fluctuations, optimize inventory levels, and prevent disruptions. In finance, AI-powered fraud detection systems analyze transaction patterns in real-time to prevent fraudulent activities. The future of BPA will heavily rely on AI-driven predictive capabilities to drive smarter business decisions.
5. AI-Enabled Document Processing and Intelligent OCR
Document-heavy industries such as legal, healthcare, and banking are benefiting from AI-powered Optical Character Recognition (OCR) and document processing solutions. AI can extract, classify, and process unstructured data from invoices, contracts, and forms, reducing manual effort and improving accuracy.
Intelligent document processing (IDP) combines AI, machine learning, and NLP to understand the context of documents, automate data entry, and integrate with existing enterprise systems. As AI models continue to improve, document processing automation will become more accurate and efficient.
Going Beyond Automation
The future of AI-driven BPA will go beyond automation—it will redefine how businesses function at their core. Here are some key predictions for the next decade:
Autonomous Decision-Making: AI systems will move beyond assisting human decisions to making autonomous decisions in areas such as finance, supply chain logistics, and healthcare management.
AI-Driven Creativity: AI will not just automate processes but also assist in creative and strategic business decisions, helping companies design products, create marketing strategies, and personalize customer experiences.
Human-AI Collaboration: AI will become an integral part of the workforce, working alongside employees as an intelligent assistant, boosting productivity and innovation.
Decentralized AI Systems: AI will become more distributed, with businesses using edge AI and blockchain-based automation to improve security, efficiency, and transparency in operations.
Industry-Specific AI Solutions: We will see more tailored AI automation solutions designed for specific industries, such as AI-driven legal research tools, medical diagnostics automation, and AI-powered financial advisory services.
AI is no longer a futuristic concept—it’s here, and it’s already transforming the way businesses operate. What’s exciting is that we’re still just scratching the surface. As AI continues to evolve, businesses will find new ways to automate, innovate, and create efficiencies that we can’t yet fully imagine.
But while AI is streamlining processes and making work more efficient, it’s also reshaping what it means to be human in the workplace. As automation takes over repetitive tasks, employees will have more opportunities to focus on creativity, strategy, and problem-solving. The future of AI in business process automation isn’t just about doing things faster—it’s about rethinking how we work all together.
Learn more about DataPeak:
#datapeak#factr#technology#agentic ai#saas#artificial intelligence#machine learning#ai#ai-driven business solutions#machine learning for workflow#ai solutions for data driven decision making#ai business tools#aiinnovation#digitaltools#digital technology#digital trends#dataanalytics#data driven decision making#data analytics#cloudmigration#cloudcomputing#cybersecurity#cloud computing#smbs#chatbots
2 notes
·
View notes
Text
A Comprehensive Guide to Applying for a UK Tourist Visa
Traveling to the United Kingdom is an exciting prospect filled with opportunities to explore rich history, vibrant culture, and stunning landscapes. However, before you can embark on your UK adventure, securing a UK tourist visa is often a crucial step, especially for travelers from non-visa-exempt countries. This comprehensive guide walks you through the application process, requirements, and tips to ensure a successful visa application.
Understanding the UK Tourist Visa
The UK tourist visa, officially known as the Standard Visitor Visa, permits individuals to visit the UK for leisure, tourism, family visits, business meetings, or short-term studies. It typically allows stays of up to six months, with some exceptions for medical treatment and academic research.
This visa is designed for short-term stays and does not permit long-term residence, employment, or access to public funds in the UK. The Standard Visitor Visa can also be issued for long-term validity (2, 5, or 10 years), allowing multiple entries, provided that each stay does not exceed six months.
Eligibility Criteria
To be eligible for a UK tourist visa, applicants must meet several criteria:
Have a Valid Passport: Ensure your passport is valid for the duration of your stay and contains at least one blank page.
Demonstrate Intent to Leave the UK: Provide evidence that you plan to return home after your visit, such as employment letters, family commitments, or property ownership.
Proof of Financial Means: Show you can support yourself financially during your stay without recourse to public funds.
Purpose of Visit: Clearly state your reasons for visiting, supported by relevant documentation like invitation letters, travel itineraries, or event confirmations.
No Intention to Work: Confirm that you will not undertake paid or unpaid work during your stay.
Step-by-Step Application Process
Complete the Online Application:
Visit the official UK government visa website.
Create an account and fill out the Standard Visitor Visa application form accurately.
Provide personal details, travel history, and purpose of visit.
Pay the Application Fee:
The standard fee is approximately £100 for a six-month visa.
Additional fees apply for priority processing, super-priority services, or long-term visas.
Book an Appointment:
Schedule an appointment at your nearest visa application center (VAC).
Prepare to submit biometric data, including fingerprints and a photograph.
Gather Required Documents:
Valid passport with at least one blank page.
Financial documents (bank statements, payslips, sponsorship letters).
Proof of accommodation and travel itinerary.
Invitation letter (if visiting family or friends).
Evidence of ties to your home country (employment letter, property ownership).
Travel insurance (recommended but not mandatory).
Attend Your Appointment:
Submit your application, supporting documents, and biometric information.
Be prepared for a short interview where you may be asked about your travel plans.
Wait for a Decision:
Processing times typically range from 15 to 20 working days.
Priority services are available for faster processing, often within 5-7 working days.
Required Documents Checklist
Valid passport
Completed visa application form
Recent passport-sized photographs
Proof of financial means (bank statements, payslips)
Detailed travel itinerary
Accommodation bookings or invitation letters
Evidence of ties to home country
Travel insurance (optional but recommended)
Cover letter explaining the purpose of your visit
Proof of employment or enrollment (if applicable)
Financial Requirements
Applicants must demonstrate that they have sufficient funds to cover:
Travel expenses to and from the UK
Accommodation costs
Daily living expenses
Financial documents should be recent (within the last three months) and clearly show the source of income. If someone else is sponsoring your trip, provide a sponsorship letter and the sponsor’s financial documents.
Tips for a Successful Application
Be Honest: Provide accurate and truthful information. False information can lead to visa refusal and future bans.
Organize Your Documents: Ensure all paperwork is clear, complete, and well-organized.
Apply Early: Submit your application well before your planned travel date, especially during peak seasons.
Consult Official Resources: Refer to the UK government website for the latest guidelines and updates.
Prepare for an Interview: Some applicants may be called for an interview. Be prepared to discuss your travel plans and financial situation.
Common Reasons for Visa Rejection
Understanding the common reasons for visa rejection can help improve your application:
Incomplete or Inaccurate Application Forms: Double-check for errors or missing information.
Insufficient Financial Proof: Provide clear evidence of your financial stability.
Lack of Strong Ties to the Home Country: Demonstrate reasons to return home, such as employment, family, or property.
Discrepancies in Provided Information: Ensure consistency between the application form and supporting documents.
Previous Immigration Violations: Disclose any past visa refusals or immigration issues honestly.
Unclear Purpose of Visit: Provide a detailed itinerary and supporting documents to clarify your travel intentions.
What to Do If Your Visa Is Refused
If your visa application is refused:
Review the Refusal Letter: Understand the reasons for refusal.
Address the Issues: Correct any mistakes or provide additional documentation.
Reapply: Submit a new application with improved documentation.
Consider an Appeal: In some cases, you may be eligible to appeal the decision.
Can You Work or Study with a UK Tourist Visa?
The UK tourist visa does NOT permit:
Paid or unpaid work
Long-term study programs
Marrying or registering a civil partnership
Receiving public funds
However, you can:
Attend business meetings, conferences, or short training sessions
Participate in recreational courses (up to 30 days)
Visit family and friends
Receive private medical treatment
Extending Your UK Tourist Visa
In most cases, you cannot extend your UK tourist visa beyond six months. Exceptions include:
Medical Treatment: If ongoing treatment is required.
Academic Research: For academics participating in research.
Applications for extensions must be submitted before your current visa expires. Provide strong evidence to support your extension request.
Traveling with Dependents
Each family member, including children, must apply for their own visa. Ensure that:
Children under 18 have birth certificates and parental consent letters.
Family applications are submitted together to streamline the process.
Conclusion
Applying for a UK tourist visa may seem daunting, but with thorough preparation and attention to detail, you can navigate the process smoothly. By following this comprehensive guide, gathering the necessary documents, and presenting a clear, honest application, you’ll increase your chances of securing a UK tourist visa. Whether you're planning to explore historic landmarks, visit family, or attend business events, proper planning ensures a memorable and hassle-free trip to the United Kingdom.
2 notes
·
View notes
Text
The Darkweb: Exploring the hidden crimes of the Internet

The Dark Web is a complex and often misunderstood segment of the internet, shrouded in secrecy and notorious for its association with illegal activities. This hidden part of the web, accessible only through specialised software like Tor (The Onion Router), allows users to navigate anonymously, which has fostered both legitimate and illicit uses. The Dark Web is a subset of the Deep Web, which itself constitutes about 90% of the internet not indexed by traditional search engines. While most users interact with the Surface Web, the Deep Web includes private databases and secure sites, whereas the Dark Web is specifically designed for anonymity and privacy. The Dark Web emerged from projects aimed at ensuring secure communication, originally developed by the U.S. Department of Defence in the early 2000s. [1] [2]
Hidden Crimes in the Dark Web
The anonymity offered by the dark web has made it a hub for numerous forms of criminal activity. From illegal marketplaces to cybercrime forums, this underworld of the internet is teeming with hidden dangers.
Illicit Markets and Drug Trade
One of the most notorious aspects of the dark web is its marketplace for illegal goods. Websites like the now-defunct Silk Road offered a platform where users could buy and sell illegal drugs, firearms, stolen goods, and counterfeit documents. These black markets are often operated using cryptocurrencies such as Bitcoin to further mask identities and ensure untraceable transactions.According to a 2019 study by the European Monitoring Centre for Drugs and Drug Addiction, the dark web drug trade has grown exponentially, with millions of dollars' worth of drugs being sold monthly across various platforms . [3] [4]
2. Cybercrime and Hacking Services
The dark web also serves as a marketplace for cybercriminals. Hacking tools, ransomware-as-a-service, and stolen data are regularly exchanged in these hidden corners of the internet. Criminals offer services ranging from DDoS attacks to the sale of stolen credit card information and personal identities. Some forums even provide tutorials for novice hackers looking to learn cybercrime techniques. [5]
3. Human Trafficking and Exploitation
While less publicly discussed, the dark web has been linked to disturbing trends in human trafficking and child exploitation. Illegal forums allow criminals to sell services or even traffic victims, relying on the secrecy provided by encryption and anonymity transactions. These criminal activities often occur alongside other heinous content like child abuse imagery, which is tragically prevalent in certain corners of the dark web . [5]
4.Weapons and Assassination-for-Hire
Another dark aspect of the dark web is the sale of illegal firearms, explosives, and even assassination services. Websites provide arms to buyers without the restrictions and regulations of the surface web. Though some claims of hitmen-for-hire on the dark web have been debunked as scams, the sale of illicit firearms remains a significant concern for global law enforcement agencies .
Top 5 Notorious Cases on the Dark Web
(Content Warning: This list includes some horrifying incidents and scary dark web stories. We suggest you skip entries if you’re faint of heart or suffering from any type of anxiety or stress disorder.)
1. Banmeet Singh’s $100M+ dark web drug empire gets brought to light
Starting with a fairly recent case, Banmeet Singh of Haldwani, Northern India was sentenced to eight years in prison in late January 2024 after he was found to have created and led a multi-million dollar drug enterprise.The Indian national also forfeited $150 million in cryptocurrency. This proved to be illegal drug money that was laundered into cryptocurrency. Singh used various dark web marketplaces to create his drug empire. According to the U.S. Department of Justice, Singh shipped drugs from Europe to eight distribution centers in the US. After, these were transported to and sold in all 50 US states and other countries in the Americas. Singh was arrested in London, where he was residing in 2019. In 2023, he was extradited to the US. [7]

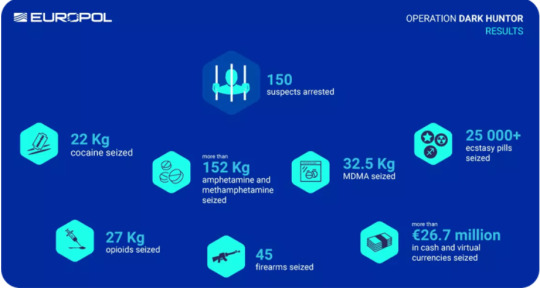
2. Operation Dark hunTor results in 150 arrests in nine countries
We’re moving from one multi-million-dollar illegal contraband case to the next. In 2021, Euro pol, Eurojust, and the police forces of nine countries conducted one of the biggest anti-crime operations the dark web has ever seen: Dark hunter. This operation resulted in 150 arrests across Australia, Bulgaria, France, Germany, Italy, the Netherlands, Switzerland, the United Kingdom, and the United States. All of the arrested were allegedly involved in buying or selling illegal goods on the dark web. The authorities found some articles in the possession of the arrested that strengthened their case: EUR 26.7 million (USD 31 million) in cash and virtual currencies, 234 kg of drugs, and 45 firearms.Italian authorities also managed to close down two dark web markets that boasted over 100,000 listings for illegal goods, DeepSea and Berlusconi. [7]
3. Operation DisrupTor exposes a dark web drugs distribution center
Amid the Covid pandemic, most businesses were struggling. Meanwhile, Operation DisrupTor suggests the drug business was still prospering. In February 2020, a group of FBI agents found 50 pounds of methamphetamine and thousands of Adderall pills in a storage shed in Los Angeles. The drugs, and the firearms that were also found, belonged to a crime network that had completed over 18,000 drug sales on the dark web. The criminal syndicate hid the drugs in a shed that they had made to look like a legitimate mail-order business. Their dark web drug sales included shipments to other dark net vendors, street dealers, and actual consumers. [7]
WATCH FULL VIDEO [8]
4. Attempt to hire a dark web hitman backfires
Now and then, crazy deep web stories pop up about how easy it is to hire a dark web hitman. One of these urban legends, however, turned out to be true. In February 2024, a woman from Canberra, Australia, pleaded guilty to inciting another to murder. The woman claimed to have contacted a dark web hitman (on the dark web marketplace Sinaloa Cartel) to murder her wealthy parents as part of an inheritance scheme. Supposedly, the total agreed-upon sum for the murder was $20,000, of which she had already paid $6,000 as a downpayment, using Bitcoin. It’s hard to say if the woman was actually talking to a contract killer or a scammer. Let’s just say we’re just happy the Australian court system was on to her before we could find out. While we don’t encourage anyone to go looking for a hitman on the dark web or elsewhere, this case goes to show that even on the dark web and while using crypto, many actions are retraceable. We always recommend people with good intentions to go for maximum privacy, as it’s no one’s business what they’re doing on the dark web. A great way to improve your privacy is by using NordVPN. NordVPN hides your IP address and encrypts your traffic, plus it blocks malicious links. [7]

5. No Love Deep Web takes dark web enthusiasts on a treasure hunt
Back in August of 2012, visitors on the dark web could find clues scattered on the network that led them through a fascinating alternate reality game. Much like Cicada 3031’s 4chan game, the clues led regular users through an array of clever clues set up like a treasure hunt. The dark web game employed a lot of encryption means to hide its hints, including the Caesar cipher, QR codes, Morse code, and a lot of other similar encryption methods. All of the clues were spread around dark websites, and one participant recounts the experience as quite thrilling:

So what was going on? Well, it wasn’t a secret government agency recruiting new members, and it wasn’t a feat of a group of cybercriminals.
Rather, the game was created by the experimental hip-hop group Death Grips to promote their new album, No Love Deep Web. [7]
READ MORE CASES [7]
Law Enforcement and the Fight Against Dark Web Crime
Despite the anonymity and encryption, law enforcement agencies around the world have made significant progress in cracking down on dark web criminality. In 2021, a multinational law enforcement effort, Operation Dark HunTor, led to the arrest of 150 individuals across multiple countries, targeting major drug vendors and illegal marketplaces on the dark web .
Undercover operations, improved digital forensics, and advances in cryptocurrency tracing have given authorities new tools to combat the hidden crimes of the dark web. However, for every takedown, new marketplaces and forums emerge, reflecting the cat-and-mouse dynamic between law enforcement and cybercriminals. [6]
Conclusion
While the dark web itself is not inherently evil, its secrecy has allowed criminals to thrive in ways that are difficult to regulate or even detect. From drug trafficking and cybercrime to human exploitation, the hidden crimes of the dark web reveal a darker side of digital anonymity. As law enforcement and technology continue to evolve, so too will the battle to uncover and combat these underground activities. Nonetheless, the dark web serves as a potent reminder that as technology advances, so too does the need for robust security measures and ethical oversight.
.
.
.
.
sources:
https://www.varutra.com/the-hidden-internet-exploring-the-secrets-of-the-dark-web/
2.https://sopa.tulane.edu/blog/everything-you-should-know-about-dark-web
3. https://www.unsw.edu.au/research/ndarc/news-events/blogs/2016/01/dark-net-drug-marketplaces-begin-to-emulate-organised-street-cri
4. https://www.euda.europa.eu/darknet_en
5. https://www.findlaw.com/criminal/criminal-charges/dark-web-crimes.html
6. https://syntheticdrugs.unodc.org/syntheticdrugs/en/cybercrime/detectandrespond/investigation/darknet.html
7. file:///D:/New%20folder/The%2013%20Most%20Notorious%20Cases%20on%20the%20Dark%20Web.html
8. https://youtu.be/d4NSfrOtMfU?feature=shared
#crime#cyberpunk 2077#cybersecurity#internet#dark web#criminal case#laws#murder mystery#mental health
5 notes
·
View notes
Text
Legal Document Data Entry for Accuracy & Compliance

Document data entry in the legal sector is highly important to implement in order to attain organized datasets which are easy to access and protect crucial information. Checkout in detail about document data entry for legal firms.
#document digitization#document data entry services#data entry services#document management company#digital document services#document data entry#document data solutions#outsourcing data entry#data entry services provider#best data entry services
2 notes
·
View notes
Text
Elevate Client Services with Excel: Expert Tips for Financial Consultants by Grayson Garelick

Financial consultants operate in a dynamic environment where precision, efficiency, and client satisfaction are paramount. Excel, as a versatile tool, offers an array of features that can significantly enhance the services provided by financial consultants. Grayson Garelick, an accomplished financial analyst and consultant, shares invaluable Excel tips to help financial consultants elevate their client services and add tangible value.
The Role of Excel in Financial Consulting
Excel serves as the backbone of financial consulting, enabling consultants to analyze data, create models, and generate insights that drive informed decision-making. As the demands of clients become increasingly complex, mastering Excel becomes essential for financial consultants aiming to deliver exceptional services.
1. Customize Excel Templates
One of the most effective ways to streamline workflows and improve efficiency is by creating customized Excel templates tailored to specific client needs. Grayson suggests developing templates for budgeting, forecasting, and financial reporting that can be easily adapted for different clients, saving time and ensuring consistency.
2. Utilize PivotTables for Data Analysis
PivotTables are powerful tools in Excel that allow financial consultants to analyze large datasets and extract meaningful insights quickly. Grayson emphasizes the importance of mastering PivotTables for segmenting data, identifying trends, and presenting information in a clear and concise manner to clients.
3. Implement Conditional Formatting
Conditional formatting is a valuable feature in Excel that allows consultants to highlight important information and identify outliers effortlessly. By setting up conditional formatting rules, consultants can draw attention to key metrics, discrepancies, or trends, facilitating easier interpretation of data by clients.
4. Leverage Excel Add-ins
Excel offers a variety of add-ins that extend its functionality and provide additional features tailored to financial analysis and reporting. Grayson recommends exploring add-ins such as Power Query, Power Pivot, and Solver to enhance data manipulation, modeling, and optimization capabilities.
5. Automate Repetitive Tasks with Macros
Macros enable financial consultants to automate repetitive tasks and streamline workflows, saving valuable time and reducing the risk of errors. Grayson advises recording and editing macros to automate tasks such as data entry, formatting, and report generation, allowing consultants to focus on value-added activities.
6. Master Advanced Formulas and Functions
Excel's extensive library of formulas and functions offers endless possibilities for financial analysis and modeling. Grayson suggests mastering advanced formulas such as VLOOKUP, INDEX-MATCH, and array formulas to perform complex calculations, manipulate data, and create sophisticated models tailored to client needs.
7. Visualize Data with Charts and Graphs
Visualizing data is essential for conveying complex information in an easily digestible format. Excel offers a variety of chart types and customization options that enable consultants to create compelling visuals that resonate with clients. Grayson recommends experimenting with different chart styles to find the most effective way to present data and insights.
8. Collaborate and Share Workbooks Online
Excel's collaboration features enable financial consultants to work seamlessly with clients, colleagues, and stakeholders in real-time. Grayson highlights the benefits of sharing workbooks via OneDrive or SharePoint, allowing multiple users to collaborate on the same document, track changes, and maintain version control.
9. Protect Sensitive Data with Security Features
Data security is a top priority for financial consultants handling sensitive client information. Excel's built-in security features, such as password protection and encryption, help safeguard confidential data and ensure compliance with regulatory requirements. Grayson advises implementing security protocols to protect client data and maintain trust.
10. Stay Updated with Excel Training and Certification
Excel is a constantly evolving tool, with new features and updates released regularly. Grayson stresses the importance of staying updated with the latest Excel training and certification programs to enhance skills, explore new capabilities, and maintain proficiency in Excel's ever-changing landscape.
Elevating Client Services with Excel Mastery
Excel serves as a catalyst for innovation and excellence in financial consulting, empowering consultants to deliver exceptional services that add tangible value to clients. By implementing Grayson Garelick Excel tips, financial consultants can streamline workflows, enhance data analysis capabilities, and foster collaboration, ultimately driving client satisfaction and success. As financial consulting continues to evolve, mastering Excel remains a cornerstone of excellence, enabling consultants to thrive in a competitive landscape and exceed client expectations.
#Financial Consulting#grayson garelick#Customize Excel Templates#Utilize PivotTables#Implement Conditional Formatting#Leverage Excel Add-ins#Automate Repetitive Tasks with Macros#Advanced Formulas and Functions#Visualize Data with Charts and Graphs#Collaborate and Share Workbooks#Protect Sensitive Data with Security#Stay Updated with Excel Training#Elevating Client Services with Excel
3 notes
·
View notes
Text
Convenience, Confidentiality, Conundrum

Bad things happen when data gets into the wrong hands. The news about a certain celebrity couple's private affairs has been buzzing across various platforms, and it has created enough noise for it to be brought up in the introduction to one of our discussions with our course instructor, because of how it's such a great example of what happens when a breach in data privacy takes place. We now live in the digital age where every aspect of our lives, from personal interactions to financial transactions, leaves a trail of data. I've learned that as this influx of information presents its opportunity, it also gives challenges concerning privacy and security.
In my perspective as someone who owns a printer at home and offers basic printing and copier services for people in her neighborhood, I've observed that my customers appear indifferent about the privacy of their data. They're trusting enough to lend their flash drive for me to print or create a copy of their documents, even the ones that contain classified information like birth certificates, and valid IDs. There are also customers that do not have a hint of reluctance in them in sending their document files to my email, for them to be printed. While it's convenient for customers to rely on local printing services like mine, their apathetic attitude towards the privacy of their data is concerning.
Entrusting sensitive documents containing personal information such as birth certificates and valid IDs without ensuring proper handling puts them at risk of data breaches. I, as the service provider, give high regard to the privacy and security of my customers' data. However, it should be an essential for customers to be more mindful of the potential risks involved in sharing sensitive information and to take proactive steps to protect it. In addition to the practices of customers, it's also important for service providers like me to implement data retention policies, which I hadn't consciously done until I've learned about it in this module's discussion, where I became more aware of proper data retention practices.
The imparted knowledge from this session have been an eye-opener for me, and it is evident in the way I have realized the application of these knowledge in my very own personal life. I have learned that in an era wherein digital footprints are omnipresent, it's crucial for both individuals and businesses to strike a balance between convenience and confidentiality when it comes to data privacy. On one hand, convenience is undeniably a driving force in our digital age. The ease of sharing information, accessing services, and conducting transactions online has revolutionized the way we live and work. From online shopping to social media interactions, convenience often takes precedence over concerns about privacy. However, this convenience should not come at the expense of confidentiality. As highlighted in the example of the celebrity couple's privacy breach, the consequences of mishandling sensitive data can be far-reaching and devastating. Whether it's personal documents like birth certificates and IDs or financial information, the stakes are high when it comes to safeguarding privacy. It is crucial for individuals to be vigilant about who they entrust their data to and the measures taken to protect it. Likewise, businesses must prioritize data security and implement robust protocols to prevent unauthorized access and breaches.
To conclude this journal entry, I believe that the dilemma that we face in the digital age requires a refined approach that considers both convenience and confidentiality. We need to be mindful of the risks associated with sharing sensitive data and take proactive steps to protect our privacy. By navigating this delicate balance, we can harness the benefits of technology while mitigating the risks of privacy and security breaches.
2 notes
·
View notes
Text
Why are data entry services important in the healthcare industry?
Healthcare Data Entry Services

Accurate data and precise information are the backbone of the healthcare system and infrastructure for better functioning. Every patient record, insurance claim, prescription, and laboratory report must be accurately documented or stored in preferred format to ensure seamless medical care and efficient operations as they need to be readily available to concerned sources with ease considerations. Here's the role where Healthcare Data Entry becomes essential and a must for a healthcare organization. It refers to the structured and accurate input of healthcare-related data and information into digital systems, ensuring easy access and support, processing, and analysis of this data.
Ensures Accurate Patient Records -
One of the most crucial and critic roles of Healthcare Data Entry is to maintain up-to-date and error-free patient records and details in the system. From medical history to treatment plans and further proceedings treatments or plans with health stats, timely and correct data entry ensures that healthcare professionals have reliable information to make informed decisions and can head to take the right step. As this helps to improve the quality and hospitality of patient care and minimizes risks due to miscommunication or missing data.
Streamlines Administrative Processes -
Healthcare providers deal and serve with a large volume and number of paperwork daily as their common task. Healthcare Data Entry helps digitize and organize this information, streamlining administrative tasks like appointment scheduling, billing, and claim submissions. This initiative allows and grants the healthcare staff to focus and starve more on patient care and hygiene and less on manual paperwork and other common deliverables.
Improves Billing and Insurance Claims -
Accurate data entry is essential for smooth billing and claim processing. Errors in entering insurance details or treatment codes can lead and thrive towards claim denials and revenue loss turning towards revenue burning. With dedicated and extreme Healthcare Data Entry services, providers can assure faster reimbursements, reduced errors, and improved financial outcomes with their practices.
Enhances Data Security and Compliance -
Handling sensitive medical information requires strict adherence to data security and privacy regulations. While the professional Healthcare Data Entry teams follow HIPAA and other compliance standards, ensuring data is protected and securely managed throughout the entry process.
Supports Research and Decision-Making -
Digitally stored and well-organized data enables better analysis, research, and reporting. It helps identify treatment trends, improve services, and plan for future healthcare needs. Leading companies and professional experts like Suma Soft, IBM, Cyntexa, and Cignex offer dependable Healthcare Data Entry services that ensure precision, confidentiality, and efficiency with their expertise. Their expertise tends to enable healthcare providers to reduce administrative burdens and deliver improved patient outcomes.
#it services#technology#saas#software#saas development company#saas technology#digital transformation
2 notes
·
View notes
Text
The Collaboration of Clinical Data Management and Biostatistics in Evidence-Based Medicine
Introduction:
In the realm of clinical research, the seamless collaboration between clinical data management (CDM) and biostatistics is paramount for ensuring the accuracy, reliability, and integrity of study outcomes. This dynamic partnership plays a pivotal role in transforming raw data into meaningful insights that drive evidence-based medical decisions. In this blog post, we delve into the essential interactions between CDM and biostatistics, highlighting their respective contributions and synergies in the clinical research landscape.

Data Collection and Database Design:
CDM professionals are responsible for designing robust data collection tools and establishing comprehensive data management plans.
Biostatisticians collaborate closely to ensure that data collection instruments capture relevant variables with precision, enabling accurate statistical analysis.
Joint efforts streamline the development of databases that adhere to regulatory standards and facilitate efficient data entry, validation, and cleaning processes.
Data Quality Assurance:
CDM specialists implement quality control measures to identify and address data discrepancies, inconsistencies, and errors.
Biostatisticians contribute expertise in data validation and verification, conducting thorough checks to maintain data integrity.
Continuous communication between CDM and biostatistics teams fosters proactive identification and resolution of data quality issues, enhancing the reliability of study findings.
Statistical Analysis Planning:
Biostatisticians from Biostatistics Services collaborate with CDM professionals to formulate robust statistical analysis plans (SAPs) tailored to study objectives and design.
CDM experts provide insights into data structure, collection processes, and potential biases, informing statistical modeling approaches and hypotheses testing strategies.
The synergy between CDM and biostatistics ensures that analytical methodologies align with data characteristics, maximizing the validity and interpretability of study results.
Data Interpretation and Reporting:
Biostatisticians play a pivotal role in analyzing study data, interpreting statistical findings, and deriving meaningful conclusions.
CDM specialists assist in contextualizing statistical results within the broader clinical framework, elucidating the implications for patient care and treatment strategies.
Collaborative review and refinement of study reports and publications ensure accurate representation of data insights and statistical significance.
Regulatory Compliance and Audits:
CDM professionals and biostatisticians collaborate to ensure compliance with regulatory requirements and industry standards governing data management and statistical analysis.
Joint efforts facilitate preparation for regulatory inspections and audits, with comprehensive documentation and audit trails supporting data integrity and traceability.
Continuous monitoring and adherence to regulatory updates and guidelines mitigate risks and enhance the credibility of clinical research outcomes.
Conclusion:
The intricate interplay between clinical data management services and biostatistics underscores the importance of collaborative synergy in advancing evidence-based medicine. By leveraging their respective expertise and working in tandem throughout the research lifecycle, CDM and biostatistics teams synergize efforts to uphold data quality, integrity, and regulatory compliance. Clinical data management services, such as those provided by Global Pharma Tek, play a crucial role in designing robust data collection tools, establishing comprehensive data management plans, and implementing quality control measures to ensure the accuracy and reliability of study data. This harmonious partnership not only drives scientific discovery and innovation but also contributes to improved patient outcomes and healthcare decision-making.
2 notes
·
View notes
Text
5 Ways Freight Forwarding Software Can Boost Your Business's Efficiency

In today's fast-paced logistics industry, efficiency is key to success. One tool that can significantly enhance efficiency in your business operations is freight forwarding software. But what exactly is freight forwarding software, and how can it revolutionize your logistics processes? This blog post will explore the five key ways in which freight forwarding software can boost your business's efficiency, from streamlined communication to cost savings.
Streamlined Communication
Centralized Platform for Communication A major benefit of using freight forwarding software is its centralized platform, for all communication regarding shipments. This ensures that everyone involved, from suppliers to carriers and customers stays informed and connected at all times.
Real-Time Tracking and Updates: The real time tracking features of freight forwarding software allow you to keep tabs on your shipments throughout their journey reducing the chances of misunderstandings and delays.
Reduction of Communication Errors and Delays: By automating communication processes freight forwarding software helps minimize errors and prevents delays caused by miscommunication leading to operations.
Automated Processes
Automated Documentation and Paperwork Handling paperwork manually can be time consuming and prone to errors. Freight forwarding software automates tasks like generating bills of lading and invoices making the paperwork process more efficient.
Integration with Customs Regulations and Compliance: Compliance with customs regulations is essential in shipping. Freight forwarding software integrates, with customs databases to ensure your shipments meet all requirements.
Reduction of Manual Data Entry and Human Error: Automating data entry tasks reduces the likelihood of error improving the accuracy and efficiency of your logistics operations.
Improved Planning and Optimization
Route Optimization and Shipment Consolidation: Freight forwarding software offers features like route optimization and shipment consolidation, enabling you to plan the most efficient delivery routes and reduce transportation costs.
Forecasting and Demand Planning Features: To stay ahead of demand, freight forwarding software provides forecasting tools that help you anticipate market trends and plan your logistics operations accordingly.
Capacity Management and Resource Allocation: By optimizing capacity and allocating resources effectively, freight forwarding software ensures that your business operates at its fullest potential, maximizing efficiency.
Enhanced Customer Service
Transparency and Visibility for Clients: With freight forwarding software, you can provide your clients with real-time visibility into their shipments, fostering trust and transparency in your business relationships.
Quicker Response Times to Inquiries: The ability to access up-to-date information on shipments enables you to respond promptly to customer inquiries, enhancing customer satisfaction and loyalty.
Customizable Reporting and Analytics for Client Insights: Freight forwarding software offers customizable reporting and analytics tools that provide valuable insights into your clients' shipping patterns and preferences, allowing you to tailor your services to their needs.
Cost Savings
Reduction in Administrative Costs: By automating administrative tasks, freight forwarding software reduces the need for manual input, saving time and money on administrative work.
Avoidance of Penalties through Compliance Automation: Compliance errors can result in costly penalties. Freight forwarding software helps you avoid these penalties by automating compliance processes and ensuring regulatory adherence.
Optimization of Resources Leading to Lower Operational Costs: Through efficient resource allocation and capacity management, freight forwarding software optimizes your resources, minimizing operational costs and maximizing profitability.
Conclusion
In conclusion, freight forwarding software is a powerful tool that can transform your logistics operations and boost your business's efficiency in numerous ways. From streamlined communication and automated processes to improved planning and optimization, enhanced customer service, and cost savings, investing in freight forwarding software is a wise decision for any business looking to stay ahead in the competitive logistics industry. So why wait? Upgrade your business today and experience the benefits firsthand!
#FreightForwarding#LogisticsTech#SupplyChainSolutions#BusinessGrowth#freight forwarding software#logistics software
2 notes
·
View notes
Text
AP management services
Streamline Your Finances with Masllp's AP Management Services: Say Goodbye to Paper Chase and Hello to Efficiency Introducing Masllp's AP Management Services: your one-stop shop for transforming your AP process from a tedious chore into a smooth, efficient operation.
Here's how we can help:
Ditch the Paper: We say goodbye to mountains of paper invoices and hello to paperless processing. No more manual data entry, lost documents, or chasing down approvals. Our secure, cloud-based platform handles everything electronically, streamlining your workflow and saving you valuable time. Boost Accuracy: Say goodbye to human error and hello to automatic data capture and verification. Our system eliminates typos, duplicates, and miscalculations, ensuring your payments are accurate and on time, every time. Optimize Workflows: We customize your AP process to fit your specific needs. From two-way PO matching to automated approvals, we help you move invoices from receipt to payment faster, improving your cash flow and vendor relationships. Gain Valuable Insights: Forget sifting through spreadsheets to find buried treasure. Our insightful reporting tools provide real-time visibility into your AP performance, allowing you to identify areas for improvement and make data-driven decisions. Free Up Your Team: Let our dedicated AP experts handle the heavy lifting. Our experienced team takes care of everything from data entry and invoice verification to vendor communication and payment processing, freeing up your internal staff to focus on more strategic tasks. But the benefits go beyond just efficiency:
Reduced Costs: Our automated processes and paperless platform save you money on printing, postage, and storage. Plus, our expertise helps you avoid late fees and payment errors, further shrinking your bottom line. Improved Vendor Relationships: Timely payments and clear communication keep your vendors happy, potentially leading to better discounts and terms. Enhanced Security: Our robust security measures protect your financial data, giving you peace of mind and ensuring compliance with industry regulations. In short, Masllp's AP Management Services are your key to achieving financial peace of mind. We take the pain out of AP, allowing you to focus on what matters most: growing your business.
Ready to ditch the paper chase and embrace the future of AP? Contact Masllp today for a free consultation and discover how we can help you streamline your finances and unlock the full potential of your business. Call to action: Visit our website, download our free ebook, or schedule a demo to learn more about how Masllp's AP Management Services can transform your business.
#audit#accounting & bookkeeping services in india#ajsh#income tax#auditor#businessregistration#chartered accountant#foreign companies registration in india#taxation#AP management services
4 notes
·
View notes