#Image Data Entry Companies
Explore tagged Tumblr posts
Text
How To Choose The Best Image Data Entry Service Provider For Your Business

Images are the heart of modern day business processes, so it is highly important to get the best results from the data stored in images. Therefore, image data entry work is considered as the backbone of business performance. However, the task of image data entry services is tedious and time consuming. Here comes the part of a business partner whom you can rely on for your important yet time consuming tasks. If you choose the best image data entry services provider for your business, you can unlock the potential of your core team and focus more on crucial business operations.
As finding the best data entry service provider is a challenging task, here are some of the best tips to find your perfect business partner to outsource image data entry services at cost-effective prices. Let us get started with points to consider before even reaching out to a data entry service provider team.
Things To Consider For Choosing The Image Data Entry Services
Here are some things to keep in mind while looking for a data entry service provider to outsource your image data entry work.
Assessment Of The Business Needs: It is highly advisable to check all the business needs for data entry work before start looking for the service provider to better understand on what criteria we need to finalize the service provider.
Budget And Scope Of Work: As a business, you must keep in mind the budget you have in order to spend on outsourcing image data entry services and the scope of work you will be sharing with your business partner, as this will be a concern for anyone who wants to perform your data entry work.
Time-Lines Required For Data Entry: Timeliness is very crucial for business operations as many tasks are interdependent on each other. It is essential to know the minimum time frame we require to get the results of the image data entry services.
Scope Of Scale And Flexibility: Every business has a goal of constant growth and development, and hence you need your business partner to grow along with you to maintain the business relations in the long term. So it is important to check if there is scope for scaling your operations and is flexible enough to adjust work performance.
Data Security: As a business owner, data security should come first to mind; hence, it is vital to check for the level of data security you need from your service provider to protect your data from theft and fraud. You also need to check if there are sufficient tools available in order to follow the data security protocols.
How To Choose The Best Service Provider In The Industry
There is a check-list which can help you determine the top level of services and results to ensure that you are outsourcing to the best image data entry service provider in the industry.
Level Of Quality
Image Data Entry is a critical work and needs to be accurate in order to perform business operations. It is advisable to check for the level of quality the service provider offers to ensure it meets your expectations of high-quality outcomes.
Level Of Customization
Customization refers to the adjustment of image data entry work as per your business requirements, it can be related to specific data formats or using multiple formats for different image type. It can also be considered as file format for the deliverables. In the competitive era, it is essential to find the data entry partner that can fulfil your requirements without any hassle.
Level Of Skills And Experience
Years of experience and proficiency in work affects the quality of results and speed of delivery, hence it is important to check the years of experience in Industry. Skills can be learned but experience is gained with time, so it is advisable to outsource image data entry services to the most experienced and skilled workforce having higher level of work proficiency.
Level Of Transparency
As an outsourcing partner, communication plays a vital role in the business operations. It is required that transparency should be maintained to enhance your internal communication and stay updated with the progress of work by daily reports or regular reviews of work.
Level Of Technology Used
The more we advance into the future, more it is getting important to use the advanced tools and software to improve the work efficiency. As an outsourcing partner, you need to understand what kind of software is used and how efficient are the tools to perform your image data entry work. The tools used will directly impact the level of service delivered.
Level Of Customer Trust In Business
Any data entry partner will have proven records of work but they also have feedbacks from their previous clients. It is important to check the level of trust their previous business partners have in them, like testimonials, references, feedbacks and customer retention rate of the service provider.
Level Of Security & Data Protection
Your data needs to be safeguarded by your business partner. It is important and basic detail to check the level of security measures owned by the outsourcing service provider. Data must be protected in any form as it directly impacts your business reputation. There must be severe check for data processing and data handling standards to ensure the risk free outsourcing process.
Check For Free Trials!
It is highly recommended to ask the image data entry service provider to have a test sample processed and then proceed with the complete project outsourcing. It is a Win Win situation for both as the service provider will also become familiar with your work and the level of quality results you are expecting, any changes can be done at the test level, it will save on time and efforts for both the team and your core business team.
If you want to find the best data entry service provider, look for the team who can match your business goals and have all the required tools and skill set to perform your data entry work with high efficiency.
Source Link: https://dataentrywiki.blogspot.com/2024/04/how-to-choose-the-best-image-data-entry-service-provider-for-your-business.html
#Image Data Entry#Data Entry Images#Image Data Entry Services#Outsource Image Data Entry#Image Data Entry Companies#Image to Text Data Entry
0 notes
Text
Top 5 Tips For Efficient Image Data Entry Processing
By using the 5 tips of this blog, you can process images with enhanced productivity, accuracy and reliability. High quality results and consistency ensures growth in image data entry operations tasks. Training and practice can lead to best outcomes of image data processing.
To know more- https://latestbpoblog.blogspot.com/2024/04/top-5-tips-for-efficient-image-data-entry-processing.html

#Image Data Entry#Data Entry Images#Image Data Entry Services#Outsource Image Data Entry#Image Data Entry Companies#Image to text data entry
0 notes
Text
Simplifying OCR Data Collection: A Comprehensive Guide -
Globose Technology Solutions, we are committed to providing state-of-the-art OCR solutions to meet the specific needs of our customers. Contact us today to learn more about how OCR can transform your data collection workflow.
#OCR data collection#Optical Character Recognition (OCR)#Data Extraction#Document Digitization#Text Recognition#Automated Data Entry#Data Capture#OCR Technology#Document Processing#Image to Text Conversion#Data Accuracy#Text Analytics#Invoice Processing#Form Recognition#Natural Language Processing (NLP)#Data Management#Document Scanning#Data Automation#Data Quality#Compliance Reporting#Business Efficiency#data collection#data collection company
0 notes
Text
my dream is to found a company that only hires former prostitutes for entry level work like cleaning or customer service or data input or something provide them with free housing where they can get free therapy coaching training childcare and if needed language classes and a fix salary with low minimum and flexible hours and every hour worked on top gets paid extra and companies will want to hire us despite being more expensive because they can boost their image with it
278 notes
·
View notes
Text
The job was simple: Monitor the woman in Room 6. She’s been asleep for 42 days.
(an r/nosleep style story)
I took the job because I needed quiet.
I had just moved back into the city after a really bad year - breakup, job loss, a fire that took half of what I owned. I was couch surfing when I saw the listing. Overnight shift. Private sleep study. No experience necessary, just basic data entry and the ability to stay awake. I figured I’d get some peace, maybe save up enough to afford rent somewhere that didn’t smell like damp carpet and stale weed.
The company was called SomnoTech. I Googled them. Not much came up. One old article in a university medical journal talking about “experimental treatments in chronic sleep disorder recovery,” and a barebones website with a contact form. The building I was sent to looked more like an office for defunct insurance than a lab. Beige, windowless, buzzed me in through two locked doors. Everything inside was silent and clean. No logos. Just halls that didn’t echo.
They gave me a laminated badge and walked me to Observation Room 6. It had one long window, a chair, three monitors, and a clipboard. That was it. Beyond the glass: a white-walled room, padded corners, one hospital-style bed with a woman laying perfectly still on it. Wires across her scalp. Pulse oximeter. Blood pressure cuff. Breathing tubes. The usual. The kind of image you’d see in a medical drama.
Her name was Marla. That’s all they told me.
“She’s not in a coma,” the lead technician - Dr. Ellis - said. “She’s asleep.”
I asked how long.
He said, “Forty-two days.”
That was when I almost walked out. But the pay was too good, and I told myself it was harmless. Just keep a log. Note her REM cycles. Don’t go in the room.
They emphasized that. Over and over.
Never enter the room.
I asked what would happen if she woke up.
Dr. Ellis paused for too long before he answered,
“That’s… not expected.”
That first night, nothing happened.
She lay still, vitals normal. Every couple hours her eyes flickered beneath the lids. Standard REM activity. Once, around 2:30 a.m., her hand twitched. I logged everything. I didn’t sleep, didn’t even look away much. Just sat and stared, drank vending machine coffee, and listened to the soft beep of monitors that never changed.
It wasn’t until the third shift that she moved.
Not much. Just shifted in bed. Rolled slightly. Her breathing deepened. That’s when I noticed something strange - the audio feed picked up sound from her room, but it was... too clean. No background noise. No rustle of sheets. Just her breathing.
Then she said something. A whisper.
I hit replay.
She’d said a name.
My name.
My full name.
No one else at SomnoTech knew it. I’d used an alias on the application, something I did out of habit after a few years of gig jobs. But what she said - what she mouthed - was my real name.
The one I haven’t used since I left home.
I showed the recording to Dr. Ellis.
He watched it, twice, without expression.
“It’s likely a coincidence,” he said. “The dreaming brain replays fragments of memory. She may have seen you on the way in.”
“She’s been asleep for six weeks.”
“She’s responding. That’s good. Keep documenting.”
He walked out before I could ask anything else.
The next few nights, I tried to convince myself it was nothing. I told myself it was a coincidence. That it didn’t mean anything. But she kept saying it.
Night after night. Just my name. Sometimes fast, sometimes slow. No sound - just the shape of it, over and over. Her mouth moving in that same rhythm. I stopped drinking the coffee. Started staying stone-cold sober for every shift.
On the 23rd day, everything changed.
At exactly 3:07 a.m., Marla sat up in bed. Her eyes were still closed. She turned her head, slowly, toward the camera in the top corner of the ceiling. And then, without hesitation, she pointed at it. At me.
I didn’t move. Didn’t breathe. Just stared as she pointed, waited five long seconds, then laid back down.
I radioed it in.
“She’s dreaming about you,” the tech on call said. “That means it’s working.”
“What’s working?”
No response.
When I arrived the next night, I was given a new form to sign. It was labeled ‘Phase Two Observation Protocol.’
Most of it was boilerplate NDA language, but two lines stuck out:
Observer must not leave the premises until Phase Two is complete.
Observer must report all subjective experiences, including dreams, during or between shifts.
They were asking me to log my own sleep. When I pointed out that I wasn’t supposed to be sleeping on shift, the night tech said,
“You’ll understand soon.”
Marla began crying on Day 31. At first, it was soft. Then sobs - raw, broken, painful. Her vitals didn’t spike. Brain activity remained stable. But the sound of her grief came through the speaker like it was close. Not recorded. Not filtered. Like she was in the room with me.
I started sleeping in two-hour blocks. I couldn’t stay awake anymore. My body was shutting down.
And then the dreams came.
First night: I’m standing in the hallway of the lab. Only it’s longer. The walls are too narrow, the ceiling too low. At the end of the hallway, there’s a door. Behind it, whispering.
Second night: Marla is sitting in the chair I use. Writing something. Every time I try to speak, she looks up and smiles. Her eyes are still closed.
Third night: I’m in the observation room, but the monitors show me, sleeping. Marla’s bed is empty.
I started documenting the dreams. Every detail. I showed them to Dr. Ellis. He didn’t even blink.
“You’re syncing,” he said.
“Syncing with what?”
He just said, “The bridge needs a guide.”
I stopped asking questions. I stopped pushing. I didn’t have much choice.
I started working double shifts. Eighteen hours on, six off. I slept at the facility. They put me in a bunkroom in a hallway I’d never seen. I thought it was just exhaustion, but when I tried to leave the building after that shift, my badge was deactivated. The front doors stayed locked. I went back to the observation room.
Marla was sitting up in bed, hands on her face, still crying. She’d been crying for nine days straight.
I didn’t eat. Didn’t sleep. I started taking the pills they left by the coffee machine. They didn’t help. My vision blurred. My hands shook. Every time I looked in the mirror, I saw bags under my eyes, my face pale and gaunt.
I wasn’t there anymore. I was just in the room. Staring. Always staring.
And then Marla opened her eyes. Just for a moment, just a fraction of an inch, but they were open. Not white, not rolled back. She was looking at me. Her pupils were there. Focused. She held my gaze for a breath, then closed them.
I tried to call Dr. Ellis. My radio didn’t work anymore. The lights went out. The only thing left was the audio feed. Her soft crying. And then, she said my name again.
That’s when I noticed.
My clipboard was empty. Every log, every note, every dream I’d written down - gone. I grabbed for the stack of old forms from the drawer under the monitor. They weren’t there. Not even the signature pages. Just hundreds of blank sheets.
I looked up at the monitors. The leftmost screen was blank. I hadn’t noticed it. Was it always like that? It was dark. No vitals. No video. Just a black screen with a single white label - my name.
Marla pointed at it. The crying stopped.
She stood up and walked to the window. I felt cold. My blood slowed. My heart pounded in my ears. Then she reached out and touched the glass. And for the first time, the audio picked up more than her breath. It picked up mine.
I backed away. But there was nowhere to go. The door was locked. Marla stared at me through the window, and her expression changed. Her brow furrowed. Her mouth opened. I watched the shape of a question form on her lips.
Suddenly, I was in the room. Not the observation room. Her room.
My hand touched the bed. Cold sheets. The air smelled sterile. There was one window. No monitors. I was on the other side of the glass. I was in the bed.
I looked over the edge of the mattress and saw myself. I was sitting in the observation chair. Writing on a clipboard. My eyes were open but blank. The rightmost monitor showed vitals, but they weren’t Marla’s. They were mine. My breathing, my heart rate.
And on the leftmost monitor, just darkness.
Marla stood in front of the window in the observation room and pointed at me. She mouthed something over and over again. Not my name. Not this time. I couldn’t understand it. I tried to get up. To reach for her. But I couldn’t move.
She took one step back and turned toward the door. I heard it open. Someone walked in, someone I couldn’t see. Marla said something else and then walked out. The audio feed stayed active. I heard footsteps. A new set of footsteps, heavier, slower, dragging. And then a new voice. It wasn’t Marla’s. It was mine.
I tried to scream. The audio feed went dead.
The next time I woke up, the observation room was dark. The silence was too deep. It felt like the building had been abandoned for years.
I pulled the blanket off me. My legs were weak. My mouth tasted of copper. I stood up, slowly. The air was freezing. My breath came out in clouds. The window was dark. All the lights were off.
But when I looked at the ground, I saw I wasn’t standing on the floor. I was standing on glass.
And on the other side - a new girl in the chair.
Only, she wasn’t looking up at me.
She was looking at me - straight on - as if her world tilted at a different angle. As if she were seated upright in a room that existed sideways beneath mine. Her gaze didn’t drift. Her neck didn’t crane. She met my eyes like we were sitting across from each other, not separated by gravity and glass.
I dropped to my knees, pressing my hands to the pane.
She watched me. Pale, shaking, eyes wide with fear. She looked like she’d been crying. Like she’d seen something she didn’t understand.
I recognized myself in her face, but it wasn’t me. It couldn’t be.
Because behind her, on the far side of the darkened room, there was a figure standing in the corner.
It was me. The other me. The one that sat in the chair. Its eyes were open, and it was smiling. And on its lap: an empty clipboard, waiting to be filled.
********************************************************************************
It’s been four months since I arrived at SomnoTech. I haven’t slept in three. I’ve written all of this down. I’m not sure how many times. I don’t know how much is real.
The girl in the chair doesn’t look at me anymore. She stopped crying. She stopped moving. She’s becoming like the other one. The smiling one. The one in the dark. The one who’s waiting for its turn.
I don’t want to know what comes next. I don’t think anyone does. But it doesn’t matter what we want. All that matters is what it wants. And it’s getting closer. I can hear it in the walls. I can feel it in my skin. I can see it in the reflection.
And once that happens, there’s only one thing left. One final step. One last phase.
This isn’t a dream. It’s not even a nightmare.
It’s the thing waiting after.
And we’re already in it.
We’re all already asleep.
And we don’t even know it yet.
#literature#writing#original#words#thoughts#lit#spilled ink#aesthetic#spilled thoughts#spilled words#writeblr#writers on tumblr#self written#original writing#creative writing#ao3 writer#ao3 author#no sleep#horror#scary#psycological horror#short story
19 notes
·
View notes
Text


Resources and study tips to get you in cyber forensics
Master post • Part1 • part2
let's get you prepped to be a cyber sleuth without spending any cash. Here’s the ultimate tips and resources.
Ps: you can't become one while doing these pointers but you can experience the vibe so you can finally find your career interest


### 1. **Digital Scavenger Hunts**
- **CTF Challenges (Capture The Flag)**: Dive into platforms like [CTFtime](https://ctftime.org/) where you can participate in cyber security challenges. It's like playing *Among Us* but with hackers—find the imposter in the code!
- **Hunt A Killer (Digitally)**: Create your own digital crime scenes. Ask friends to send you files (like images, PDFs) with hidden clues. Your job? Find the Easter eggs and solve the case.
### 2. **YouTube University**
- **Cyber Sleuth Tutorials**: Channels like *HackerSploit* and *The Cyber Mentor* have playlists covering digital forensics, cybersecurity, and more. Binge-watch them like your fave Netflix series, but here you're learning skills to catch bad guys.
- **Live Streams & Q&A**: Jump into live streams on platforms like Twitch where cybersecurity experts solve cases in real-time. Ask questions, get answers, and interact with the pros.
### 3. **Public Libraries & eBook Treasure Hunts**
- **Library eBooks**: Most libraries have eBooks or online resources on digital forensics. Check out titles like *"Hacking Exposed"* or *"Digital Forensics for Dummies"*. You might have to dig through the catalog, but think of it as your first case.
- **LinkedIn Learning via Library**: Some libraries offer free access to LinkedIn Learning. If you can snag that, you've got a goldmine of courses on cybersecurity and forensics.
### 4. **Virtual Study Groups**
- **Discord Servers**: Join cybersecurity and hacking communities on Discord. They often have study groups, challenges, and mentors ready to help out. It's like joining a digital Hogwarts for hackers.
- **Reddit Threads**: Subreddits like r/cybersecurity and r/hacking are packed with resources, advice, and study buddies. Post your questions, and you’ll get a whole thread of answers.
### 5. **DIY Labs at Home**
- **Build Your Own Lab**: Got an old PC or laptop? Turn it into a practice lab. Install virtual machines (VMware, VirtualBox) and play around with different operating systems and security tools. It’s like Minecraft but for hacking.
- **Log Your Own Activity**: Turn on logging on your own devices and then try to trace your own steps later. You’re basically spying on yourself—no NSA required.
### 6. **Community College & University Open Courses**
- **Free Audit Courses**: Many universities offer free auditing of cybersecurity courses through platforms like Coursera, edX, and even YouTube. No grades, no stress, just pure learning.
- **MOOCs**: Massive Open Online Courses often have free tiers. Try courses like "Introduction to Cyber Security" on platforms like FutureLearn or edX.
### 7. **Scour GitHub**
- **Open-Source Tools**: GitHub is full of open-source forensic tools and scripts. Clone some repositories and start tinkering with them. You’re basically getting your hands on the tools real investigators use.
- **Follow the Code**: Find projects related to digital forensics, follow the code, and see how they work. Contribute if you can—bonus points for boosting your resume.
### 8. **Local Meetups & Online Conferences**
- **Free Virtual Conferences**: Many cybersecurity conferences are virtual and some offer free access. DEF CON has a lot of free content, and you can find tons of talks on YouTube.
- **Hackathons**: Look for free entry hackathons—often universities or tech companies sponsor them. Compete, learn, and maybe even win some gear.
### 9. **DIY Challenges**
- **Create Your Own Scenarios**: Get a friend to simulate a hack or data breach. You try to solve it using whatever tools and resources you have. It's like escape rooms, but digital.
- **Pen & Paper Simulation**: Before diving into digital, try solving forensic puzzles on paper. Map out scenarios and solutions to get your brain wired like a detective.
### 10. **Stay Updated**
- **Podcasts & Blogs**: Tune into cybersecurity podcasts like *Darknet Diaries* or follow blogs like *Krebs on Security*. It’s like getting the tea on what’s happening in the cyber world.
### 11. **Free Software & Tools**
- **Autopsy**: Free digital forensics software that helps you analyze hard drives and mobile devices. Think of it as your magnifying glass for digital clues.
- **Wireshark**: A free tool to see what's happening on your network. Catch all the data packets like you're a digital fisherman.
### 12. **Online Forensics Communities**
- **Free Webinars & Workshops**: Join communities like the *SANS Institute* for free webinars. It's like attending a masterclass but from the comfort of your gaming chair.
- **LinkedIn Groups**: Join groups like *Digital Forensics & Incident Response (DFIR)*. Network with pros, get job tips, and stay in the loop with the latest trends.
### 13. **Practice Cases & Mock Trials**
- **Set Up Mock Trials**: Role-play with friends where one is the hacker, another the victim, and you’re the investigator. Recreate cases from famous cybercrimes to see how you'd solve them.
- **Case Studies**: Research and recreate famous digital forensic cases. What steps did the investigators take? How would you handle it differently?

There you have it—your roadmap to becoming a cyber sleuth without dropping a dime. You don't have time find your interest after paying pennies to different ppl and colleges. You can explore multiple things from comfort of your home only if you want to.

#light academia#study blog#academic validation#academic weapon#student life#study motivation#study with me#study#studyblr#studyblr community#masterpostjam#codeblr
30 notes
·
View notes
Text
United States Customs and Border Protection is asking tech companies to send pitches for a real-time face recognition tool that would take photos of every single person in a vehicle at a border crossing, including anyone in the back seats, and match them to travel documents, according to a document posted in a federal register last week.
The request for information, or RIF, says that CBP already has a face recognition tool that takes a picture of a person at a port of entry and compares it to travel or identity documents that someone gives to a border officer, as well as other photos from those documents already “in government holdings.”
“Biometrically confirmed entries into the United States are added to the traveler’s crossing record,” the document says.
An agency under the Department of Homeland Security, CBP says that its face recognition tool “is currently operating in the air, sea, and land pedestrian environments.” The agency’s goal is to bring it to “the land vehicle environment.” According to a page on CBP’s website updated last week, the agency is currently “testing” how to do so. The RIF says that these tests demonstrate that while this face recognition tool has “improved,” it isn’t always able to get photos of every vehicle passenger, especially if they’re in the second or third row.
“Human behavior, multiple passenger vehicle rows, and environmental obstacles all present challenges unique to the vehicle environment,” the document says. CBP says it wants a private vendor to provide it with a tool that would “augment the passenger images” and “capture 100% of vehicle passengers.”
Dave Maass, director of investigations at the Electronic Frontier Foundation, received a document from CBP via public record request that reveals the results of a 152-day test the agency conducted on its port of entry face recognition system from late 2021 to early 2022. The document Maass obtained was first reported by The Intercept.
Maas said that what stood out to him were the error rates. Cameras at the Anzalduas border crossing at Mexico’s border with McAllen, Texas, captured photos of everyone in the car just 76 percent of the time, and of those people, just 81 percent met the “validation requirements” for matching their face with their identification documents.
The current iteration of the system matches a person’s photo to their travel documents in what’s known as one-to-one face recognition. The primary risk here, Maas says, is the system failing to recognize that someone matches their own documents. This differs from one-to-many face recognition, which police may use to identify a suspect based on a surveillance photo, where the primary risk is someone getting a false positive match and being falsely identified as a suspect.
Maas says it’s unclear whether CBP’s error rates primarily have to do with the cameras or the matching system itself. “We don't know what racial disparities, gender disparities, etc, come up with these systems,” he says.
As reported by The Intercept in 2024, the DHS's Science and Technology Directorate issued a request for information last August that’s similar to the one that CBP posted last week. However, the DHS document currently appears to be unavailable.
Maas adds that it’s important to remember that CBP’s push to widen and improve its surveillance isn’t unique to the current Trump administration.
“CBP surveillance strategy carries over from administration to administration—it always falls short, it always has vendor issues and contracting issues and waste issues and abuse issues,” Maas says. “What changes is often the rhetoric and the theater around it.”
DHS noted in a 2024 report that CBP has historically struggled to get “biographic and biometric” data from people leaving the country, particularly if they leave over land. This means it’s hard for it to track people self-deporting from the country, which is something the administration is encouraging hundreds of thousands of people to do. CBP’s recent request for information only mentions inbound vehicles, not outbound vehicles, meaning it’s currently not set up to use face recognition to track self-deporations.
CBP did not respond to WIRED’s request for comment.
CBP’s request for information comes less than three weeks after 404 Media revealed that Immigration and Customs Enforcement is paying the software company Palantir $30 million to build a platform that would allow the agency to perform “complete target analysis of known populations.” According to a contract justification published a few days later, the platform, called ImmigrationOS, would give ICE “near real-time visibility” on people self-deporting from the US, with the goal of having accurate numbers on how many people are doing so. However, ICE did not specify where it would get the data to power ImmigrationOS.
In the ICE document that justifies paying Palantir for ImmigrationOS, the agency does not specify where Palantir would get the data to power the tool. However, it does note that Palantir could create ImmigrationOS by configuring the case management system that the company has provided to ICE since 2014. This case management system integrates all of the information ICE may have about a person from investigative records or government databases, according to a government privacy assessment published in 2016.
It’s unclear if the system may have integrated new data sources over the past decade. But at the time of the assessment, the system stored information about someone’s physical attributes—like hair and eye color, height and weight, and any scars or tattoos—as well as any “location-related data” from “covert tracking devices,” and any data from license plate readers, which can provide a detailed history on where a person goes in their vehicle and when.
8 notes
·
View notes
Text
Personally as a communist and anarchist I think it's such a lazy idea that using AI is in some means ok because there's no ethical consumption under capitalism. Ethical consumption under capitalism refers to worker exploitation to live and consuming goods from companies that have supported genocide.
AI is one of the MANY WAYS that art cannot be consumed ethically under capitalism, as it STEALS ART and produces low-quality copy/paste images for free. Art is inherently critical of capitalism, and by commodifying it and shearing it of all human intervention, it no longer holds power and ceases to exist. The whole purpose of AI (which was originally for data entry) stealing art was to reduce its rebellion against capitalism.
If you can't shell out the amount of money it would take for a artist to make a picture of you as a fictional character, then either LEARN or start dismantling capitalism so that art can exist for it's own sake once again.
Yes, this goes doubly for people using Bing AI to draw themselves as spider-man characters or Pixar characters and posting it on tiktok, and triply for people who have the gall to call themselves anarchists or activists when they can't even give up tools of exploitation.
#This is about a select group of people but it applies to everyone really#Like obviously im not gonna name the person because i would never subject you all to the horrors of tiktok#But just know theyre a staple in the online communist community and its very disappointing to hear that they cant be arsed to give back#ai#ai discourse#artist
38 notes
·
View notes
Text
Top 5 Tips For Efficient Image Data Entry Processing

With the ever-increasing demand for efficient data that can be used in industries across the world, it is important to focus on the raw data. The source of data comes from images of all sorts. Be it medical records, catalogs, survey responses, or enhancing the database, images provide us with a lot of information. To process all that and more, we need to ensure that quality image data processing is being performed at the source. In this blog, we will share with you the top 5 tips to ensure you get your dream image data processing solutions with high-end effectiveness in decision-making and problem-solving. Outsourcing image data entry and processing services can also be a great choice to expand your business operations.
Here Are The Top 5 Tips You Can Focus On While Processing Image Data Entry:
1. Choose Your Right Tools And Software:
Image data processing requires the correct choice of tools and software to process the image data. The tools you are using need to meet the requirements of high quality while processing image data.
It is always advised to invest in the best data entry software with advanced features and flexible applications of the tools in a changing work environment. In order to reduce errors and manual efforts, these tools can capture data from images easily and can save a lot of cost and time.
There are many advanced tools and software that can handle multiple image processing tasks at one time, which can take the efficiency of business operations to the next level. Hence, image data entry processing gets simple, quick, and easy to operate with hi-tech tools at hand.
2. Following Standard Procedures And Templates:
The second step to consider to improve your image data entry and processing tasks is to have consistent results. To make sure the results maintain quality standards, it is advised to create templates for the data entry task for every image processed. Templates are a convenient way to receive consistent and uniform results.
By following set procedures, image data entry operators can also perform tasks with efficiency and the minimum risk of errors. It is easy to manage and study data in the same format, and it allows you to get analytical results without any hassle by performing additional image data entry services.
3. Use Of Automated Quality Control Techniques:
Usually, image data entry services require manual data validation and verification to ensure quality standards are met. However, the process may involve human errors, and it can be time-consuming to perform such tasks. Thus, it is always better to utilize automation in the image data entry validation process.
It is highly important to keep the quality consistent and high-end in image data entry services. In order to get results within time-lines, considering data verification tools to verify the data with internal and external resources is highly recommended. The task of data analysis and decision-making in business operations becomes smoother as it becomes easier to access accurate data.
4. Focus On Easy To Learn Practical Training:
One of the most important thing to enhance image data entry service results is to follow the ideal training methods. It is essential to focus on quality assurance methods while performing image data entry tasks. There are many key elements like following protocols and set standards, review and validation of image data processing results, data verification, and more.
There should be systematic plan on how the training will proceed and it should be documented to maintain the standards of learning as well as development purposes. Regular checks and consultation after the training will resolve the issue of gaps during the training process. Best quality image data entry services are results of precise knowledge and training of best practices, updated software and tools as well as making corrections quickly during the process.
5. Optimization Of Process To Improve Productivity And Results:
Improvement in any process is an ongoing task, it requires constant focus on check points to look for the need of improvement. Optimization of image data entry processing tasks is vital as it reduces the efforts of data entry operator by extracting the image data quickly and accurately. As the image data entry services are looking for optimization, it is important to focus on quality results and timeliness of process to utilize the best of tools and software.
It is essential to join hands with changing technologies, automation of easy tasks, implement efficient quality control protocols and use templates that can benefit in long term operations of image data entry.
Simple Ways To Enhance Image Data Entry Processing
Performing data validation and data verification will improve the quality of data and the process results will be highly accurate and reliable.
Keeping the software and tools updated to keep up with modern changes and challenges will elevate the outcomes.
Regular checks of quality will improve the overall standards of data processing and reduce the risk of errors with large image data processing.
It is also advised to ensure the data security and data management to improve the storage capacity of processed data.
Source Link: https://latestbpoblog.blogspot.com/2024/04/top-5-tips-for-efficient-image-data-entry-processing.html
#Image Data Entry#Data Entry Images#Image Data Entry Services#Outsource Image Data Entry#Image Data Entry Companies#Image to text data entry
0 notes
Text
G Witch Onscreen Text: Episode 2
This is part 3 in an ongoing series where I try and document and discuss all of the text that appears on screens and monitors throughout the show! Just because I can!
<<Click here to go back to Episode 1!
(Once I have a masterpost set up I will link it here!) Let us Begin! Below the Cut!

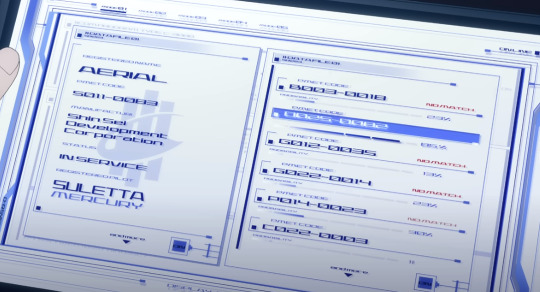
TEXT: (Lefthand side) Registered Name: AERIAL PMET CODE: 5011-0083 MANUFACTUR(ER): SHIN-SEI DEVELOPMENT CORPORATION STATUS: IN SERVICE REGISTERED PILOT: SULETTA MERCURY
At the beginning of the episode, Rouji has Haro run a program that compares Aerial's permet code and registered statistics against other registered Mobile Suits to try and find a match, and measures the probability of the two being the same type of MS. There is no direct match to any other MS by Permet Code, but the system states there's an 85% probability that it's a match for a Mobile Suit with permet code 0025-0082.
We never see the specific name of this MS, but considering that Shaddiq names "Ochs Earth" as the company that made it and proceeds to call Aerial, "...the Witch's Mobile Suit," I think it's reasonable to assume that 0025-0082 was the Permet Code for Lfrith-03.

TEXT: ALERT ACCESS CONTROL [???] [----OF ENTRY A---]
Unfortunately due to the small text of the Alert message, the fact that it scrolls, and it's brief time onscreen, its hard to make out specifically what it says. My best assumption from what we have is that it's a warning currently barring anyone from entry into the 13th Tactical Testing Sector.

TEXT: (Suletta's Asticassia ID) PILOTING DEPARTMENT ID No: LP-041 SULETTA MERCURY BIRTHPLACE: MERCURY HOUSE: NO DATA PC-CRIMINAL RECORD: NO DATA PC-BIOMETRIC SYSTEM: REGISTERED
(Below) WE ARE RESPONSIBLE UNDER COMPANY REGULATIONS FOR THE PROCESSING OF PERSONAL DATA
UNDER THESE REGULATIONS, WE ARE ALSO RESPONSIBLE FOR DATA HANDLING SUCH AS TRANSMISSION TO RECIPIENTS AND THIRD PARTIES.
PLEASE REFER TO THE FOLLOWING DOCUMENTS FOR DETAILS.
As Suletta is being questioned, we get a brief glimpse at the investigation report the interrogator was looking at before the screen cuts to black when it hits the table. Nothing super interesting here, but Suletta doesn't have a registered criminal record! Yippeeee!

TEXT: CAM: 05 MONITORING CAMERA FACILITY MANAGEMENT COMPANY
Not much to say here, this camera lets us know where Suletta is currently being held. (The Facility Management Company)
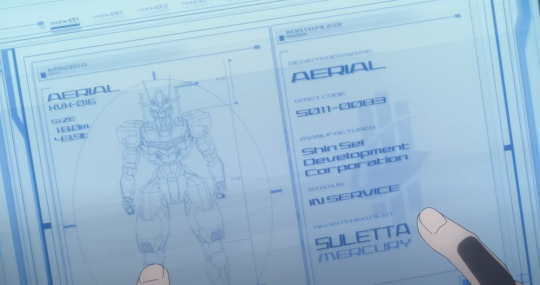
TEXT: (Lefthand Side) AERIAL XVX - 016 SIZE: 18.0m 48.9t
No point discussing the info on the right, we've already seen it, but this gives us a look at Aerial's height and weight.

TEXT: (Top Right) COM DELLING REMBRAN BENERIT GROUP
I only included this to point out that wow the display system devs made some poor choices with the UI here. Dark Blue text on Dark Backgrounds? You'd think the text would automatically lighten but I guess we'll have to wait for Ver 6.0 for that update.
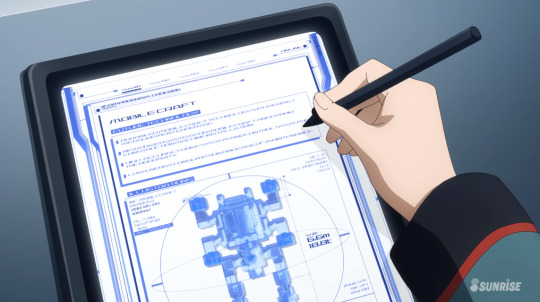
TEXT (Top half) MOBILE CRAFT FUTURE TECHNOLOGY
ADVANCED MOBILE CRAFT TECHNOLOGY WITH PERMET MEASUREMENT EXPERTISE NEW POWER SYSTEM FOR MOBILE CRAFT AND HYBRID CONSTRUCTION MACHINE INSTALLATION HIGH ACCURACY DRIVE SYSTEM AND CONTROL SYSTEM IN MICROGRAVITY LOW ENERGY CONSUMPTION AND EASE OF MAINTENNANCE
No need to discuss the bottom half, its just the height and weight of the MC which we already know. I think it's funny how many classes this school seems to have on the new and improved Mobile Craft from Future Technology. I should probably buy one too. I love you Mobile Craft.


TEXT: (Left Image) The Shin Sei Development Corporation was established in A.S. 89. Our business began with the development of integrated operating systems for mobile suits and medical devices. We have been involved in MS development and have supported welfare engineering throughout our company history.
(Right Image) Ranking: D Sales Ranking (within group companies): 151th (out of) Total 157 companies [Mobile Suit Development] Number of clients: Over 300 companies Yearly patents: Over 200
We get a lot of information about Shin Sei in this scene where Martin looks at the Company History tab on their official website. The most interesting thing being that they were founded in A.S. 89. The Vanadis Incident occured in A.S. 101, and the show proper takes place in A.S. 122, so at some point between 101 and 122, Prospera worked her way up through Shin Sei, eventually becoming its CEO.
Given that Suletta had to have been born around A.S. 105, and that in Cradle Planet, we learn that Prospera had been working within Shin Sei when Suletta was around 6, that places A.S. 111 as the earliest she was involved.
We also learn in Cradle Planet, that when Suletta is around 11, Prospera has recently been promoted within the company, and now has many people working under her. That would be around A.S. 116. When Suletta is 16, that's when Prospera tells her that she's going to school, which would be around A.S. 121, and I think it's safe to assume that she had already become president by then.
SO!! TL;DR!! It's most likely that Prospera became the president of Shin Sei at SOME point between A.S 116 and A.S 121. I'd put it somewhere in the middle, around A.S 119. (Can't wait to find out that they probably just outright state this somewhere and I did all this for nothing....)
ADDENDUM

GOD DAMNIT. I WATCHED ALL OF CRADLE PLANET TO MATH THAT SHIT OUT. WHATEVER. I CAME TO THE SAME CONCLUSION SO I WIN.

The text is too small to make out, but we DO get a small glimpse at the letter Delling sent to Miorine about unenrolling her from the school. It probably just literally says what the body guard reads out.
I think it says something that Delling doesn't even like, text his daughter. He sends an email through the official Benerit Group email account to her bodyguard who reads it for her. What a cowardly man.

TEXT: (Left) FLUSH (Right) EMERGENCY CALL UNLOCK LOCK
YES the toilet text is important to document stop fucking looking at me like that.

TEXT: NEXT STAGE TOUCH SCREEN TO CONTINUE
I'll leave the explanation of the symbolism of this scene as an exercise for the reader. [Sultry Wink]

TEXT (Above) THIS ELECTRONIC SIGNATURE IS PROOF THAT IT WAS SIGNED BY A REPRESENTATIVE OF THE BENERIT GROUP.
No way to tell what Delling is signing here, but we do get a brief look at his handwriting. It turns out his cursive is really bad, actually!
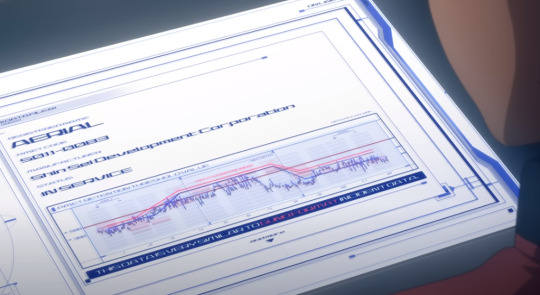
At the Shin Sei inquiry, Shaddiq shares this graph titled "PMET RETENTION THRESHOLD VALUE", stating that during the duel, Aerial's Permet Influx Values exceeded the standards set by Cathedra.
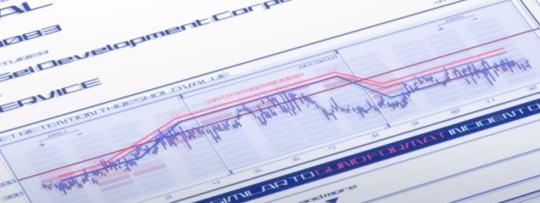
This graph can be tough to parse, so let me explain it as best I can. The blue line represents Aerial's Permet Retention during the duel. The solid dark line represents the permet retention limit imposed by cathedra on mobile suits. (At around 500) As we can see, while Aerial began the duel underneath that limit, it exceeded it for a moment (presumably when Suletta took over for Miorine and the GUND bits were activated.)
The red line above that is labelled DATA STORM INCIDENT, which is representative of the minimum Permet Retention a Gundam expresses when it is interfacing with a Data Storm. The text on the bottom reads, THIS DATA IS VERY SIMILAR TO GUND FORMAT INCIDENT DATA.
But the key thing to take note of here is that Aerial's chart just BARELY doesn't exceed the DATA STORM INCIDENT graph, meaning that, despite it exceeding Cathedra's standards, it CANNOT be directly proven that Aerial was interfacing with a Data Storm. This is actually what Prospera brings up as her main counterpoint to the accusation.

So the graph is entirely consistent with Prospera's main argument. While she can't prove that Aerial isn't a gundam, nobody else can prove that it is.
Huaaaahh!! Alright!! This one was very DENSE. If you made it all the way through, thank you very much!! As a reward, have some little gay people




[I sprinkle these stills on the ground like bird seed.]
There was definitely a lot of really interesting info in this episode, and while not a lot of it was particularly new, I think it's really a testament to the dedication of keeping things wholly consistent in this world, even for the smallest of things that no normal person watching would even bother noticing.
Also, on the Shin Sei Website, did you notice that they accidentally put 151th instead of 151st?
You can't win em all!
Click here to go to Episode 3! >>
Click here to go to the Masterpost!
36 notes
·
View notes
Text
How to Earn Money Online: A Beginner-Friendly Guide

Are you looking for ways to earn money online in 2025? Whether you're interested in freelancing, starting an online business, or making passive income, this guide covers the best and most profitable opportunities. Let's explore how you can start earning from home today!
1. Freelancing 🖥️
Freelancing is one of the easiest ways to start making money online. If you have skills in writing, graphic design, programming, or social media management, websites like Upwork, Fiverr, and Freelancer can help you find clients. Just create a profile, showcase your work, and start applying for jobs.
2. Online Tutoring 📚
If you're knowledgeable in a subject like math, science, or languages, you can earn money by teaching students online. Platforms like VIPKid, Chegg Tutors, and Tutor.com allow you to connect with students worldwide and set your own schedule.
3. Affiliate Marketing 🔗
Affiliate marketing lets you earn commissions by promoting products online. You can join programs like Amazon Associates, ShareASale, and ClickBank. Simply share referral links on your blog, social media, or YouTube channel, and earn a commission when someone makes a purchase.
4. Selling Products Online 🛍️
E-commerce is booming! Sell handmade crafts, digital downloads, or dropshipping products through Shopify, Etsy, or eBay. These platforms provide easy tools to set up your store and start selling quickly.
5. Blogging and Content Creation ��️🎥
Starting a blog or a YouTube channel can generate income through ads, sponsorships, and affiliate marketing. Platforms like WordPress and Medium allow you to publish engaging content that attracts an audience and monetizes over time.
6. Stock Photography and Videography 📸
If you enjoy photography or videography, you can sell your work on Shutterstock, Adobe Stock, and Getty Images. Businesses and content creators are always looking for high-quality visuals.
7. Online Surveys and Small Tasks 📝
While it won’t make you rich, completing surveys and microtasks can earn you extra cash. Websites like Swagbucks, InboxDollars, and Amazon Mechanical Turk pay users for simple tasks like watching videos, answering surveys, and testing websites.
8. Dropshipping 📦
Dropshipping is an excellent way to start an online business without managing inventory. Use platforms like Shopify with suppliers from AliExpress or SaleHoo. When customers place an order, the supplier ships the product directly to them.
9. Print on Demand 🎨
With print-on-demand services like Printful and Redbubble, you can sell custom-designed products without handling inventory. You design the products, and the platform handles production and shipping.
10. Remote Work and Virtual Assistance 💻
Many companies offer remote job opportunities in fields like customer service, data entry, and administrative support. Websites like Remote.co, We Work Remotely, and PeoplePerHour list job openings that you can do from home.
#artificial intelligence#digital marketing#earn money online#how to earn money#earnings#earn money fast#youtube#money
3 notes
·
View notes
Text
Strengthen Brand Identity and Fuel Creativity with Sales Quoting Software
For value-added resellers in the IT and office supplies sector, creating a strong brand identity is indispensable. A brand identity not only sets a company apart from its competitors but also fosters trust and loyalty among customers.
However, maintaining a consistent brand image while striving for innovation can be a challenging task. This is where sales quoting software steps in to streamline processes, enhance brand identity, and fuel creativity. The business sales quoting software serves as a comprehensive solution for value-added resellers (VARs) to generate accurate quotes quickly and efficiently.
However its benefits extend beyond mere sales operations; it can play a pivotal role in reinforcing brand identity and fostering creativity within an organization. Here's how:
Consistency in Brand Messaging
A cohesive brand identity is built upon consistent messaging across all customer touchpoints. Sales quoting software allows businesses to incorporate branded templates, logos, and messaging into every quote, ensuring that the brand identity remains consistent throughout the sales process. This consistency reinforces brand recognition and strengthens the brand's overall image in the eyes of customers.
Personalization
While consistency is key, personalization is equally important for connecting with customers on a deeper level. A business quote generator enables businesses to tailor quotes to each customer's specific needs and preferences. By incorporating personalized elements such as customer names, relevant product recommendations, and customized pricing options, businesses can demonstrate their commitment to providing personalized experiences, thus enhancing brand loyalty.
Streamlined Workflows
Creativity thrives in environments where processes are streamlined and efficient. The software that has connections with Cisco Direct data feed automates repetitive tasks such as data entry, pricing calculations, and quote generation, allowing sales teams to focus their time and energy on more creative endeavors, such as crafting compelling sales pitches and developing innovative solutions to meet customer needs.
Data-Driven Insights
Creativity flourishes when fueled by insights and feedback. Sales quoting tools connected to catalog management solutions provide valuable data and analytics on quote performance, customer preferences, and sales trends. By leveraging these insights, businesses can identify areas for improvement, uncover new opportunities, and fine-tune their sales strategies to better resonate with their target audience, ultimately fostering a culture of continuous innovation.
Collaboration and Communication
Effective collaboration is essential for unleashing creativity within an organization. This software system integrated with catalog solutions software facilitates seamless collaboration among sales teams, marketing departments, and other stakeholders involved in the quoting process. Features such as real-time updates, commenting, and version control ensure that everyone is on the same page, fostering a collaborative environment where ideas can flow freely and innovation can thrive.
Brand Differentiation
In a crowded marketplace, standing out from the competition is crucial. Sales quoting tools that have built-in connections with the Cisco catalog empower businesses to differentiate themselves by offering unique value propositions, showcasing their expertise, and highlighting the benefits of their products or services in a visually compelling manner. By effectively communicating their brand's unique selling points through quotes, businesses can carve out a distinct identity in the minds of customers.
Sales quoting software is not just a tool for generating quotes; it is a powerful asset for strengthening brand identity and fueling creativity within an organization. By ensuring consistency in brand messaging, enabling personalization, streamlining workflows, providing data-driven insights, fostering collaboration, and facilitating brand differentiation, sales quoting software empowers businesses to elevate their brand image, engage customers more effectively, and drive innovation forward.
As businesses continue to navigate an ever-evolving marketplace, investing in this software application is not just a wise decision; it's a strategic imperative for success in the digital age.
#ecommerce platform#sales quoting software#quote creation#business software#cpq software#varstreet#ecommerce software#free rich content
11 notes
·
View notes
Text
Earn money online in micro job

A micro job is a small, short-term task or project that can be completed quickly, often within minutes or hours. These tasks usually require minimal skill, and workers are paid a small amount of money for each task. Micro jobs are typically posted on online platforms, connecting freelancers or gig workers with companies or individuals who need small tasks
Examples of Micro Jobs:
Data Entry: Entering data into a spreadsheet or system.
Survey Participation: Answering online surveys or providing feedback on products or services.
Content Moderation: Reviewing and filtering content (e.g., flagging inappropriate comments or images).
App Testing: Testing apps or websites and providing feedback.
Social Media Tasks: Liking, sharing, or following pages on social media.
Image Tagging: Labeling images with appropriate tags (useful in AI training).
Transcription: Converting short audio clips into text.
Small Writing Tasks: Writing short product descriptions or reviews.
Pros and Cons:
• Pros: Flexibility, can work from anywhere, doesn’t usually require extensive experience, and allows people to earn money in spare time.
• Cons: Generally low pay per task, no job security or benefits, and payment can vary greatly between platforms.
Micro jobs can be a quick way to earn extra cash, but they are typically not suited for stable, long-term income.
3 notes
·
View notes
Text
[ad_1] Reliance Jio Infocomm chairman Akash M Ambani | Image: PTI3 min read Last Updated : Oct 15 2024 | 12:41 PM IST Speaking at the inauguration of the India Mobile Congress on Tuesday, the leaders of Reliance Jio and Bharti Airtel called for the government to embrace a holistic artificial intelligence (AI) strategy and ensure all potential satellite communication providers are subject to the same rules as traditional telecom operators. Reliance Jio Infocomm chairman Akash M Ambani and Bharti Enterprises chairman Sunil Bharti Mittal outlined their suggestions for the evolving sector in their address to a major gathering of national and global delegates from the telecom sector, including Prime Minister Narendra Modi and telecom minister Jyotiraditya Scindia. Click here to connect with us on WhatsApp Market leader Reliance Jio wants the government to adopt a holistic AI strategy focused on self-sufficiency. "AI is absolutely critical for realising our dreams of a viksit Bharat by 2047. Therefore, India under your leadership should urgently embrace AI with a holistic strategy driven by maximum Atmanirbhar efforts," Ambani said. He stressed that Jio remains committed to democratising AI and offering powerful AI models and services to Indians at affordable prices. "Towards this end, we are laying the groundwork for a national AI infrastructure," he emphasised. Ambani noted that India needs to accelerate talent generation on a scale necessary to make the country a global leader in AI. Addressing the concern over how AI might affect the job market, he remarked that some existing jobs will evolve while many new and exciting opportunities for employment and entrepreneurship "will be created rapidly, just like during the adoption of the computer and the internet." Additionally, Ambani urged the government to expedite the draft of the 2020 data centre policy. "Indian data should remain in Indian data centres. Therefore, Indian companies ready to set up AI and machine learning data centres should receive all necessary incentives, including incentives for power consumption," he added. Satcom debate Bharti Airtel has called on the government to ensure that all potential satellite communication providers operate under the telecom operator framework. Drawing the Prime Minister's attention to the ongoing global debate on how fast-growing satellite communication services can coexist with terrestrial networks, Mittal highlighted that telecom companies worldwide have played a crucial role in connecting the globe. Referring to Indian telcos, he noted that they would extend satellite services to the remotest parts of the country. However, Mittal stressed that satellite companies aiming to serve "elite, retail customers" in urban areas must take a telecom licence like everyone else. His comments appear directed at foreign entities such as Starlink and Project Kuiper, which are seeking entry into the Indian market and whose applications are currently being reviewed by the government. "They must adhere to the same conditions, including buying spectrum like telecom companies, paying the licence fees, and securing their networks. This is a simple solution that can be adopted on a global scale, and India can lead the way," Mittal said. The government is currently in the process of opening up satellite communication services and has already granted GMPCS licences to Bharti Group-backed Eutelsat OneWeb and Reliance Jio’s satellite arm, Jio Space Limited. However, applications from foreign entities have faced hurdles due to technicalities and security concerns. Starlink is the satellite internet constellation operated by SpaceX, the American spacecraft manufacturer and satellite communications company owned by US tech billionaire Elon Musk. Project Kuiper, a subsidiary of Amazon, was established in 2019 to deploy a large satellite internet constellation to provide low-latency broadband connectivity. First Published: Oct 15 2024 | 12:41 PM IST
2 notes
·
View notes
Text
Since Elon Musk announced that he’ll be stepping back from his daily work with DOGE, perhaps you’ve been wondering if he has anything else to fill that time now that he’s shut down operations at America’s humanitarian-aid provider, wrecked much of the nation’s scientific-research infrastructure, and disrupted the communications systems at the Social Security Administration. One way to find out would be to ask Grok, his entry in the A.I. sweepstakes. “Elon Musk’s artificial intelligence company, xAI, has been making significant moves in Memphis,” Grok reports. “But these have sparked controversy.”
Indeed they have. Last year, Musk’s team secured an abandoned factory that used to belong to Electrolux, the vacuum-cleaner people on the edge of the city’s Boxtown neighborhood. As Musk explained at the time, “That’s why it’s in Memphis, home of Elvis and also one of the oldest—I think it was the capital of ancient Egypt.” With typical modesty, he renamed his vacuum factory Colossus, and started stuffing it with Nvidia graphics-processing units, or G.P.U.s, the basic building blocks of A.I. systems. At the moment, he has two hundred thousand of these G.P.U.s, and he’s headed for a million; by some estimates, he is expected to build the “largest supercomputer” in the world.
All that processing takes power to run, and so the xAI team moved about thirty-five mobile methane-gas-powered generators onto the site to support the data center. These are truck-mounted units, many of them designed by Caterpillar, which give off some of the same brew of pollutants as other gas-combustion device—including nitrogen oxides and formaldehyde—and which are currently operating without a permit. “xAI has essentially built a power plant in South Memphis with no oversight, no permitting, and no regard for families living in nearby communities,” the Southern Environmental Law Center said, in a report released in April. (Full disclosure: I volunteer every year to judge the S.E.L.C.’s Phil Reed prize for best environmental writing about the South). The S.E.L.C. has called for an “emergency order” from the city to require xAI to cease the use of these generators, with a twenty-five-thousand-dollar daily fine if the company refuses. The mayor of Memphis, Paul Young, a supporter of the project, addressed the concerns at a meeting with community members in March. “I want to figure out how we can exploit this project for us,” he said. “I know you all feel like it’s us getting exploited, but we need to speak from a place of strength.” After the S.E.L.C. issued its report, Young explained that the company has a permit application pending with the Shelby County Health Department to run fifteen generators. “There are thirty-five, but there are only fifteen that are on,” he said. “The other ones are stored on the site.”
It turns out that Young may be wrong about that number. SouthWings, a group of volunteer pilots who help monitor environmental problems, overflew the site with thermal-imaging equipment that showed at least thirty-three of the generators giving off lots of heat—indicating that they were fired up and running at the same time. (Young’s office and xAI didn’t respond to requests for comment.) Taken together, they would produce about four hundred and twenty megawatts of power—the equivalent of the Tennessee Valley Authority’s big gas-fired power plant nearby.
Memphis was, indeed, home to Elvis—but it was also, of course, where Martin Luther King, Jr., who came to the city to support striking sanitation workers, was assassinated, and it remains a place of sharp economic and racial division. It will surprise no one to learn that the neighborhoods in South Memphis surrounding Musk’s facility—including Boxtown and Westwood—are predominantly Black and also home to a number of industrial facilities, including chemical plants and an oil refinery. The area already has elevated levels of pollution compared with leafier precincts, and, according to Politico’s E&E News, “already leads the state in emergency department visits for asthma.” Those same neighborhoods came together at the beginning of the decade to fight, and ultimately defeat, the proposed forty-nine-mile-long crude-oil Byhalia pipeline, which would have run through the area. In that process, a new political star emerged: Justin Pearson, a young African American who rode that battle into the state legislature (from which he was later expelled for joining an anti-gun-violence protest on the floor of the Tennessee House after a shooting at a Christian school, only to soon be reappointed by the county and reëlected to office in the next election).
Pearson and his brother KeShaun, the director of a group called Memphis Community Against Pollution, are now helping lead the fight against xAI. They were prominent voices at a town hall of the Shelby County Health Department in late April, which a local NBC affiliate described as “unlike any other town hall in recent memory, with dozens of Shelby County sheriff’s deputies, Memphis police officers and Tennessee Highway Patrol troopers standing inside and outside of Fairley High School.” Citizens were allowed two minutes each to speak, but there were no responses to questions; after two hours the proceedings ended.
A company spokesman was shouted down at the meeting, but his written statement insisted that “XAl is going above and beyond the required emission control requirements. The Solar SMT-130 turbines will be equipped with SoLoNOx dry low emissions (D.L.E.) technology and selective catalytic reduction (S.C.R.) systems that lower nitrogen oxides (NOx) to 2 ppm.” The “Solar” here, though, has nothing to do with the power source—it’s the name of Caterpillar’s turbine division, which stems from the Solar Aircraft Company, founded in the late nineteen-twenties, whose name was derived from the fact that it was based in sunny San Diego.)
“I feel like my community is being disrespected,” Justin Pearson (whom I got to know during the Byhalia fight) told me in an e-mail. “I feel like my friends and neighbors and family members are being ignored—both by xAI itself and city leaders championing this data center that is emitting pollution into our air. Some of those leaders have mentioned the money that xAI will supposedly bring to Memphis, but what good is money if we have to struggle with polluted air? As the elders here say, ‘All money ain’t good money.’ ” He added, “Folks are angry and fearful. Some neighbors have expressed fear about letting children play outside or not enjoying time in their backyards because they don’t know what kind of pollution is in the air.”
Had Musk wanted to proceed differently, he could have. A report last year, from researchers at a number of energy and tech firms, made it clear that building arrays of solar microgrids is a quick and highly affordable plan for powering such data centers. “While building off-grid solar microgrids of this magnitude would be a first, it’s very possible to do with technology that exists today, and to scale it quickly,” the researchers found. They actually looked at Musk’s Memphis project and concluded that its use of portable gas generators was at best a one-off solution: “Most users of rental power plan to transition once possible because this approach carries very high costs and generally reliability is lower than permanent infrastructure.”
But cost is evidently not a big issue for Musk. (DOGE claims to have saved a hundred and sixty billion dollars in government spending, but a new analysis by the nonprofit Partnership for Public Service estimates that it only did so at a cost of a hundred and thirty-five billion dollars, because it has operated so quickly and ineptly.) Neither, judging from DOGE’s performance, is saving lives, but he could help do so in Memphis, if he wanted to. Pearson says, “Solar panels and battery storage would be a much cleaner alternative to methane gas turbines. Solar panels also don’t pump smog-forming pollution or chemicals like formaldehyde into nearby communities.”
More to the point, Musk’s actions in Memphis seem to presuppose that his experience in Washington will prove typical. There, he managed to enact his slash-and-burn damage in a few short weeks before leaving town, albeit with an approval rating even lower than the President’s. In Tennessee, he’s running into forces seasoned by several generations of struggle. During the Byhalia-pipeline dispute, Pearson recalled, “a representative from the pipeline company called my community the ‘path of least resistance.’ It seems like corporations don’t expect us to fight back, but we’ve proven that wrong time and time again. We’re going to do it again.”
7 notes
·
View notes
Text
Peshawar Digital Marketing Agency: Crossing the Digital Divide
The thriving capital of Khyber Pakhtunkhwa, Pakistan, Peshawar, has witnessed a notable increase in the presence and influence of digital marketing organisations in the quickly changing digital world. These organisations are leading the way in converting conventional company models into innovative, web-based businesses. Among the platforms they use, Tumblr sticks out as a special and successful tool for digital marketing, providing a variety of chances for brands to engage with their audience in a creative and efficient manner.

Digital Marketing's Ascent in Peshawar Peshawar's digital marketing landscape has expanded rapidly in the last several years. In order to improve their online visibility, local businesses—from classic handicraft stores to cutting-edge tech startups—are increasingly resorting to digital marketing services. Search engine optimisation (SEO), content marketing, social media management, and online advertising are just a few of the services that these firms provide.Digital Marketing Agency In Peshawar offers wide range of digital topics.
Tumblr:
A Missed Opportunity in Online Advertising The social networking and microblogging site Tumblr is frequently eclipsed by industry heavyweights like Facebook, Instagram, and Twitter. But because of its special qualities, it's a useful tool for digital marketers. Rich multimedia material, fully customisable blogs, and a vibrant community are all made possible by Tumblr, and these features can be especially helpful for niche marketing.
What makes Tumblr special?
Creativity and Customisation:
Brands may develop aesthetically pleasing and highly customised blogs with Tumblr thanks to its versatile interface. With this creative freedom, brands may successfully communicate their identity and values.
Text, images, quotations, links, audio, and video are just a few of the types that Tumblr can handle when it comes to rich multimedia material. Because of its adaptability, marketers may employ a variety of content formats to interact with their audience and increase user engagement.
Community Engagement:
The robust and lively communities on Tumblr are well-known. Using these communities, brands may interact with consumers who have similar interests and develop a devoted following. Benefits for SEO: Tumblr blogs have good SEO. A brand's presence on search engines can be increased by having a well-optimised Tumblr page, which will increase organic traffic to the main website.
How Peshawar's Digital Marketing Agencies Use Tumblr Peshawar-based digital marketing companies are starting to realise Tumblr's potential. They are using the platform as follows:

Content Creation:
To cater to the interests of Tumblr's wide user base, agencies provide visually appealing and captivating content. Blog entries, info-graphics, films, and interactive materials fall under this category. Community Building: Agencies assist brands in gaining a devoted and robust following on Tumbler by actively engaging in these communities. By interacting with users via direct messages, re blogs, and comments, they promote a sense of community and fidelity.
Campaign Management:
To reach a wider audience, agencies use promotional posts and targeted advertising to manage and carry out marketing campaigns on Tumblr. To improve campaign performance, they monitor performance data and make necessary adjustments.
Brand Identity:
Agencies assist companies in building a strong online presence on Tumblr by creating personalised themes and unified branding. The uniformity of the brand across all digital platforms strengthens trust and brand recognition.
In summary Peshawar's digital marketing environment is dynamic and changing quickly. The city's digital marketing organisations are skilled at using Tumblr and other platforms to help businesses reach their target audiences and meet their marketing objectives. Because of its distinctive qualities, Tumblr is a useful resource for innovative and community-focused marketing campaigns. The importance of these agencies will only increase as more companies realise the possibilities of digital marketing, spurring success and innovation in Peshawar's business community.
FAQ
1. What is the purpose of using Tumblr for digital marketing for my company? Tumblr has several benefits, like blogs that are incredibly customisable, support for rich multimedia material, and active community involvement. These characteristics might make your company stand out and appeal to a specific type of customer.
How might a Tumblr digital marketing agency benefit my company? On Tumblr, a digital marketing agency can support with content creation, community building, campaign management, and brand identity establishment.
Is Tumblr appropriate for all kinds of companies? Tumblr may help any business trying to interact with specific communities and improve their online profile, but it's especially useful for companies that can use creative and graphic content.
What are the advantages of Tumblr for SEO? Because Tumblr blogs are SEO-friendly, they can raise the visibility of your brand on search engines. Tumblr optimised content can increase organic traffic to your primary website.
What distinguishes Tumblr's community involvement from that of other platforms? Creative expression and a strong feeling of common interests are what fuel Tumblr's community engagement. With regard to particular issues, users frequently establish close-knit communities, which facilitates brand engagement with highly engaged audiences. Businesses in Peshawar can improve their digital marketing tactics, expand their customer base, and succeed more in the digital sphere by knowing and leveraging Tumblr's distinctive qualities.
Q6: How can companies assess whether their efforts in digital marketing are successful? A6: Key performance indicators (KPIs) such website traffic, conversion rates, social media engagement metrics, return on investment (ROI) from advertising campaigns, and search engine rankings can be used by businesses to gauge the effectiveness of their digital marketing initiatives.
Q7: How does content marketing fit into the plans of digital marketers? A7: Content marketing is essential for building a brand's credibility and authority. The target audience is drawn to and engaged by high-quality content, which also generates organic traffic and bolsters other marketing initiatives like SEO and social media marketing.
Q8: Are there any particular trends in digital marketing that Peshawar businesses ought to be aware of? A8: Trends like the growing usage of video content, influencer marketing, mobile optimisation, personalised marketing experiences, and the expanding influence of automation and artificial intelligence in marketing are things that businesses should be aware of.
Q9: How can Peshawar-based digital marketing companies assist with brand development? A9: By developing a strong online presence through consistent branding across several digital channels, interesting content, well-placed advertisements, and proactive social media management, these agencies help to establish brand recognition and loyalty.
Q10: What qualities ought companies to consider before selecting a Peshawar digital marketing agency? A10: Companies should seek out an agency with a track record of accomplishment, experience in the relevant field, a wide range of services, a clear grasp of their objectives, open communication, and a cooperative mindset.
2 notes
·
View notes