#IoT Data Privacy
Text
Exploring the Future of IoT | Internet of Things
Internet of Things (IoT) has already transformed the way we perceive and interact with technology connecting everyday objects to the digital world. As we navigate through a rapidly evolving technological landscape it becomes crucial to delve deeper into the future of IoT and the endless possibilities it holds. Let’s explore the exciting advancements and emerging trends that will shape the future…
View On WordPress
#connected devices#Data Analytics#Emerging IoT Technologies#Future Technology#Industrial IoT#IoT Applications#IoT Automation#IoT Connectivity#IoT Data Privacy#IoT Ecosystem#IoT in Agriculture#IoT in Healthcare#IoT Industry Insights#IoT Infrastructure#IoT Innovations#IoT Security#IoT Sensors#IoT Sustainability#IoT Trends#Smart Homes
0 notes
Text
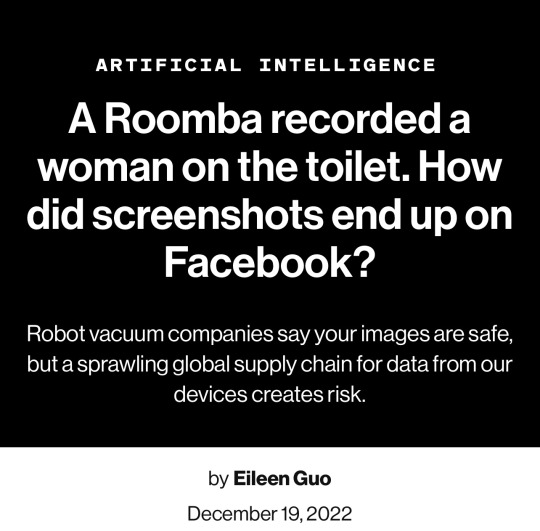



IN THE FALL OF 2020, GIG WORKERS IN VENEZUELA POSTED A SERIES OF images to online forums where they gathered to talk shop. The photos were mundane, if sometimes intimate, household scenes captured from low angles—including some you really wouldn’t want shared on the Internet.
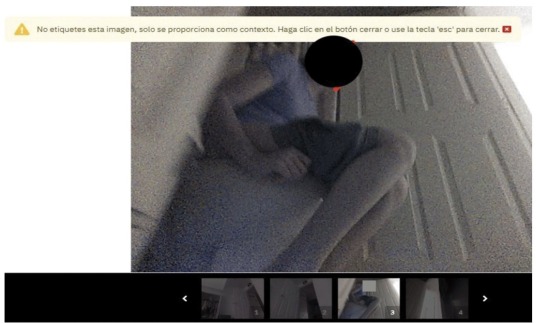
In one particularly revealing shot, a young woman in a lavender T-shirt sits on the toilet, her shorts pulled down to mid-thigh.
The images were not taken by a person, but by development versions of iRobot’s Roomba J7 series robot vacuum. They were then sent to Scale AI, a startup that contracts workers around the world to label audio, photo, and video data used to train artificial intelligence.
They were the sorts of scenes that internet-connected devices regularly capture and send back to the cloud—though usually with stricter storage and access controls. Yet earlier this year, MIT Technology Review obtained 15 screenshots of these private photos, which had been posted to closed social media groups.
The photos vary in type and in sensitivity. The most intimate image we saw was the series of video stills featuring the young woman on the toilet, her face blocked in the lead image but unobscured in the grainy scroll of shots below. In another image, a boy who appears to be eight or nine years old, and whose face is clearly visible, is sprawled on his stomach across a hallway floor. A triangular flop of hair spills across his forehead as he stares, with apparent amusement, at the object recording him from just below eye level.

iRobot—the world’s largest vendor of robotic vacuums, which Amazon recently acquired for $1.7 billion in a pending deal—confirmed that these images were captured by its Roombas in 2020.
Ultimately, though, this set of images represents something bigger than any one individual company’s actions. They speak to the widespread, and growing, practice of sharing potentially sensitive data to train algorithms, as well as the surprising, globe-spanning journey that a single image can take—in this case, from homes in North America, Europe, and Asia to the servers of Massachusetts-based iRobot, from there to San Francisco–based Scale AI, and finally to Scale’s contracted data workers around the world (including, in this instance, Venezuelan gig workers who posted the images to private groups on Facebook, Discord, and elsewhere).
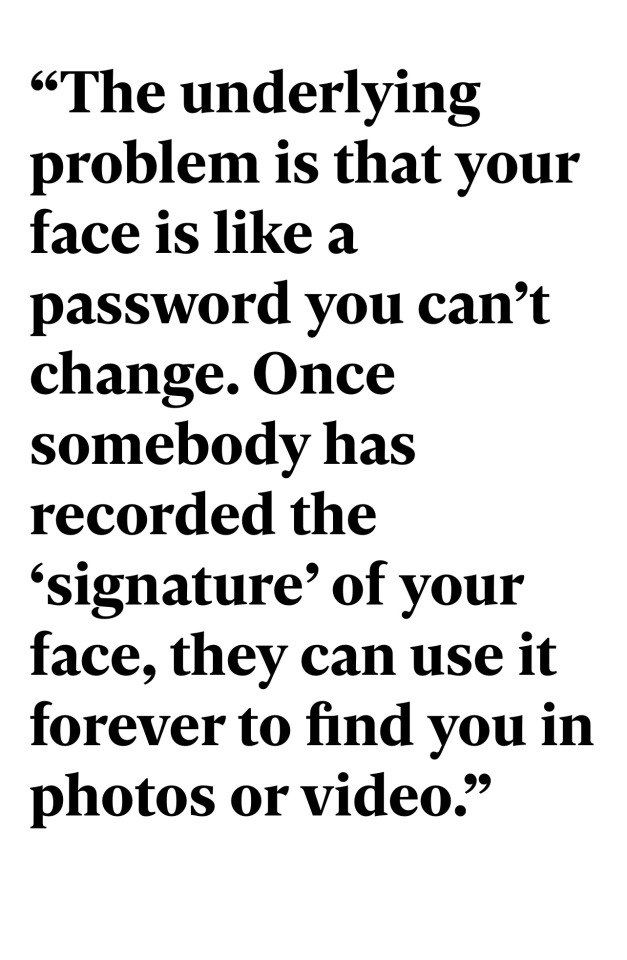
Together, the images reveal a whole data supply chain—and new points where personal information could leak out—that few consumers are even aware of.
(continue reading)
#politics#james baussmann#scale ai#irobot#amazon#roomba#privacy rights#colin angle#privacy#data mining#surveillance state#mass surveillance#surveillance industry#1st amendment#first amendment#1st amendment rights#first amendment rights#ai#artificial intelligence#iot#internet of things
5K notes
·
View notes
Text
Why Kenya's Agritech Startups Struggle to Penetrate the Market Despite Strong Investment
Discover why Kenya’s agritech startups struggle with market penetration despite strong investment, and explore how regulatory challenges and fragmented services hinder growth in the sector.
Kenya’s agritech industry faces hurdles beyond funding, including complex regulations and data security concerns. Learn how startups can overcome these challenges to scale and succeed.
Uncover the key barriers…
#agricultural technology Kenya#agritech ecosystem#agritech innovation challenges#agritech investment Kenya#agritech market penetration#agritech partnerships#Agritech Startups#AI in farming#climate resilience farming#data privacy in agriculture#data security agritech.#digital agricultural transformation#digital farming tools#digital financial services for farmers#farmer adoption of technology#fragmented service providers#IoT in agritech#Kenya agritech challenges#Kenya’s digital ecosystem#Mercy Corps AgriFin#public sector data in agriculture#regulatory barriers agritech#small-scale farming Kenya#smart farming Kenya#stakeholder engagement in agritech#sustainable agriculture Kenya#tech solutions for farmers#technology adoption barriers#technology-driven agriculture
1 note
·
View note
Text
Securing the Internet of Things: The Role of Identity Access Management in Protecting IoT Devices
The Internet of Things (IoT) has revolutionized numerous sectors, including consumer businesses, industrial applications, energy and utility systems, building and facilities management, mobility, and infrastructure. This widespread adoption has transformed how people, processes, and technologies converge to drive improvements. However, as IoT technology becomes more ubiquitous, so do the security…
#business#Business Intelligence#cybersecurity#data privacy#IAM#iam for iot#Identity Access Management#iot device management#IoT devices#iot identity management#IoT Security#market#Market Intelligence
0 notes
Text
Introduction: The Power of Industrial IoT
In today's rapidly evolving industrial landscape, the integration of technology is key to driving efficiency, productivity, and innovation. At the forefront of this digital transformation is Industrial IoT (Internet of Things), a game-changing concept that is reshaping the manufacturing sector.
Harnessing Data for Optimization
Industrial IoT revolves around the idea of interconnected devices and sensors that collect and exchange data in real-time. By leveraging this wealth of information, manufacturers gain unprecedented insights into their operations, enabling them to optimize processes, minimize downtime, and enhance overall performance.
Improving Operational Efficiency
One of the primary benefits of Industrial IoT is its ability to streamline operations. By continuously monitoring equipment and systems, manufacturers can identify inefficiencies and bottlenecks, allowing for proactive maintenance and resource allocation. This proactive approach not only reduces costs but also ensures smoother production flows and higher output levels.
Enhancing Quality Control
Quality control is paramount in manufacturing, and Industrial IoT plays a crucial role in ensuring product quality and consistency. Through advanced sensors and analytics, manufacturers can monitor every stage of the production process with unparalleled accuracy, detecting defects or deviations in real-time. This proactive quality control not only minimizes waste and rework but also strengthens customer satisfaction and brand reputation.
Enabling Predictive Maintenance
Traditional maintenance practices often rely on scheduled inspections or reactive repairs, leading to unexpected downtime and costly disruptions. Industrial IoT revolutionizes maintenance strategies by introducing predictive maintenance capabilities. By analyzing equipment performance data, manufacturers can anticipate potential failures before they occur, allowing for timely interventions and optimized asset uptime.
Facilitating Remote Monitoring and Management
In today's globalized world, remote monitoring and management are essential for agile and responsive manufacturing operations. Industrial IoT enables seamless connectivity across distributed facilities, empowering stakeholders to remotely monitor equipment, troubleshoot issues, and make data-driven decisions in real-time. This level of connectivity not only improves operational agility but also enables rapid scalability and adaptation to changing market demands.
Ensuring Data Security and Privacy
While the benefits of Industrial IoT are undeniable, ensuring data security and privacy remains a top priority. Manufacturers must implement robust cybersecurity measures to protect sensitive information from potential threats and breaches. This includes encryption protocols, access controls, and regular security audits to mitigate risks and uphold regulatory compliance.
Conclusion: Embracing the Future of Manufacturing
In conclusion, Industrial IoT represents a transformative force that is revolutionizing the manufacturing industry. By harnessing the power of interconnected devices and real-time data analytics, manufacturers can unlock new levels of efficiency, productivity, and competitiveness. However, success in this digital age requires a strategic approach, proactive mindset, and commitment to continuous innovation. By embracing Industrial IoT, manufacturers can future-proof their operations and thrive in the dynamic landscape of Industry 4.0.
#Manufacturing efficiency#Industrial IoT implementation#Quality control enhancement#Predictive maintenance#Operations streamlining#Productivity boost#Datadriven decisions#Data privacy#Remote management#Proactive maintenance#Connectivity#Smart manufacturing
0 notes
Text
What Is Hotspot 2.0 and How Will It Solve Present-Day Wi-Fi Problems? - Technology Org
New Post has been published on https://thedigitalinsider.com/what-is-hotspot-2-0-and-how-will-it-solve-present-day-wi-fi-problems-technology-org/
What Is Hotspot 2.0 and How Will It Solve Present-Day Wi-Fi Problems? - Technology Org
In the wireless world, staying connected to the internet has become more critical. As of 2022, WiFi service providers deployed about 550 million free Wi-Fi hotspots worldwide, which is only increasing.
Newer technologies, like Hotspot 2.0, aim to improve Wi-Fi quality by leveraging IoT (Internet of Things) and enhanced security measures. In this article, we’ll discuss what is Hotspot 2.0 and how it can solve some of the common Wi-Fi problems we face today.
WiFi symbol on a smartphone screen – artistic impression. Image credit: Franck via Unsplash, free license
What is Hotspot 2.0?
Hotspot 2.0 is a set of protocols and standards devised for public Wi-Fi access and to enhance the overall public connectivity experience. Also known as the Passpoint protocol, the technology allows users to connect from one network to the other on the move without the need for login or authentication. Many operating systems now support Hotspot 2.0, including Windows, Android, and IOS 7.
Revolutionizing Wi-Fi
Nowadays, we rely on the Internet for almost everything, and that’s making the limitations of traditional Wi-Fi networks more evident every day. Public and Free Wi-Fi connections can be unreliable, there are log-in and security issues, and users must often switch between networks. That’s where Hotspot 2.0 technology comes to the rescue. Here are some of the ways Hotspot 2.0 improves public Wi-Fi access:
Automatic Authentication
One of the biggest problems of traditional Wi-Fi networks is that you need to manually log in and authenticate when connecting to a free public or private Wi-Fi network. Hotspot 2.0 eliminates this by introducing automatic authentication.
Using the Passpoint standard, Hotspot 2.0 enables your device to connect to public Wi-Fi networks without manual intervention. It uses advanced authentication tools to ensure user information is not exposed over the network while allowing it to connect automatically whenever Wi-Fi is available. That improves the user experience significantly, particularly in high-density areas like stadiums, airports, etc.
Seamless Roaming
Another problem you might face is constantly switching Wi-Fi networks in a public place to get an adequate signal. Hotspot 2.0 technology solves this issue by enabling seamless roaming between compatible networks. Your device can automatically switch to another network if a better signal is available without interrupting your internet connection.
Enhanced Security and Carrier Aggregation
Security is another concern when it comes to public Wi-Fi connectivity. Hotspot 2.0 uses WPA3 encryption protocols and an Online Sign Up (OSU) framework to protect your data when transmitted over a network. That reduces the data privacy risks associated with traditional open Wi-Fi networks.
Hotspot 2.0 also introduces carrier aggregation, which means your device can connect to multiple Wi-Fi networks simultaneously for increased bandwidth and better internet connection. That can also make your internet connection more reliable and stable than traditional open-access connections.
Endnote
Hotspot 2.0 is altering the way Wi-Fi works with its ingenious features. With automatic authentication, seamless roaming, enhanced security, and carrier aggregation, this technology can make your internet connection more secure, stable, and reliable. That means you will now have a hassle-free user experience when accessing public networks with high user density. With upcoming advancements, this technology will reduce data breach risks over public, open-access networks and make public free Wi-Fi much more efficient.
#2022#android#Article#authentication#breach#connectivity#data#data breach#data privacy#encryption#Features#framework#Hardware & gadgets#how#Internet#Internet of Things#iOS#IoT#issues#it#network#networks#One#Operating Systems#Other#Other posts#privacy#risks#Security#signal
0 notes
Text
Demystifying IoTeX - The Future of IoT on the Blockchain
IoTeX is more than just another cryptocurrency; it's a vision of the future where our devices are smarter, our transactions are seamless, and our data remains private. As the lines between the physical and digital worlds continue to blur, platforms like..
Introduction To IoTeX
In the rapidly evolving world of technology, two buzzwords have consistently made headlines: cryptocurrency and the Internet of Things (IoT). But what happens when these two powerful concepts converge? Enter IoTeX, a platform that promises to revolutionize the way we perceive and interact with everyday devices. Let’s embark on a journey to understand this innovation and its…

View On WordPress
0 notes
Text
Blockchain IoT Trends and Opportunities and Distributed Ledger Advantage
The global blockchain IoT market size is expected to reach USD 12,679.5 million by 2030. The rising adoption of decentralized applications (dApps) in the blockchain IoT industry is expected to drive market growth. By combining the advantages of blockchain and IoT, these dApps introduce innovative solutions that significantly improve security, transparency, and operational efficiency across various industries. These emerging trends are anticipated to stimulate the expansion of the market. In addition, the integration of blockchain and IoT is revolutionizing data sharing, transactional trust, and process automation, leading to the emergence of innovative business models and lucrative growth opportunities.

Blockchain IoT Market Report Highlights
The software & platform component segment accounted for the largest market share of 51.6% in 2022 owing to the increasing adoption of blockchain IoT solutions
The smart contracts application segment accounted for the largest revenue share of 30.7% in 2022
The self-execution and automation capabilities of smart contracts in the market are expected to drive the segment growth
The transportation & logistics vertical segment accounted for the largest revenue share of 21.8% in 2022 due to its properties in creating transparent and immutable records of transactions
The SMEs segment accounted for the largest revenue share of 60.2% in 2022 due to the increased implementation of the technology to help SMEs meet regulatory compliance requirements
North America accounted for the largest revenue share of 34.6% in 2022 and is anticipated to witness considerable growth over the forecast period mainly on account of the presence of key market players
Gain deeper insights on the market and receive your free copy with TOC now @: Blockchain IoT Market Report
The growing awareness about the vast potential of this technology in numerous areas, such as supply chain management, asset tracking, smart cities, healthcare, and energy management, is also expected to augment the market growth. Several companies focus on launching new products and partnering with key players to cater to the larger customer base and strengthen their foothold in the industry. For instance, in March 2022, IoTex, a modular Web3 infrastructure platform, partnered with Google Cloud, a subsidiary of Google LLC. The collaboration leads to the global expansion of MachineFi, a decentralized finance (DeFi) platform designed specifically for the IoT ecosystem. Moreover, the Google Cloud-based infrastructure will help the company to make MachineFi’s services and apps more secure, scalable, and reliable. Such partnerships by key players are expected to propel the market growth.
#Blockchain IoT#IoT Security#Distributed Ledger#IoT Blockchain Integration#Smart Devices#Connected Devices#IoT Applications#Blockchain Technology#IoT Solutions#Blockchain Innovation#IoT Data#Decentralized IoT#Blockchain Use Cases#IoT Connectivity#IoT Security Solutions#Blockchain Ecosystem#IoT Trust#Blockchain Development#IoT Privacy#IoT Adoption
0 notes
Text
Security Update: A Recent Assault Exposes 95% Accurate Capture of Typed Content
In Las Vegas, the annual Black Hat and Defcon security conferences play host to hackers and researchers who unveil their latest discoveries. This year’s kickoff was particularly noteworthy. A researcher has presented potential evidence suggesting that spikes in radiation recorded by sensors at the Chernobyl nuclear facility following Russia’s 2022 invasion of Ukraine might have been manipulated.…
View On WordPress
#AI#Black Hat#Chernobyl#cybersecurity#data privacy#Defcon#discoveries#Google search results#hacking#HIPAA#Intel chips#IoT devices#safety#security news#technology#threats#vulnerabilities#Yandex
1 note
·
View note
Text
Unveiling the Future: A Deep Dive into Emerging Technologies and Their Influence on Industries and Everyday Life
In an era of rapid technological advancement, emerging technologies like artificial intelligence (AI), the Internet of Things (IoT), and blockchain are revolutionizing industries and transforming the way we live and work. In this blog post, we will delve into these cutting-edge technologies, their potential applications, and the profound impact they have on various sectors and our daily…
View On WordPress
#Artificial intelligence (AI)#Blockchain technology#Connected vehicles#Creating new possibilities#Data security#Efficiency in manufacturing#Emerging technologies#Ethical implications#Future possibilities#Healthcare diagnostics#Improving efficiency#Innovations in industries#Internet of Things (IoT)#Potential applications#Privacy concerns#Profound impact#Real-life examples#Responsible use of data#Revolutionizing industries#Smart cities#Streamlining processes#Success stories#Supply chain traceability#Sustainable future#Tangible benefits#Transforming daily life#Trust and transparency
1 note
·
View note
Text
Future of the Internet | Unlocking Tomorrow's Digital Frontier
The Internet has become an integral part of our lives, connecting people worldwide in ways unimaginable just a few decades ago. As we embark on a new era of technological advancements, it is essential to examine the future of the internet and its potential to shape our societies. And the way we interact with the digital world in the years to come. We will explore the exciting possibilities and…
View On WordPress
#AI and Machine Learning#Augmented Reality#Blockchain#Cloud Computing#Connectivity#Cybersecurity#Data Privacy#Digital Frontier#Digital Transformation#Emerging Trends#Future Technologies#Innovation Ecosystem#Internet Evolution#Internet Governance#IoT (Internet of Things)#Online Communities#Tech Innovation#Virtual Reality#Web 3.0
1 note
·
View note
Note
Why did you post the pics of the woman on the toilet? Why would you do that? And the pics of the child? It doesn't seem like you really believe in privacy if you perpetuate the violation by sharing those pics. You should delete and repost with them.
[re: this post]
Nah, I’m not doing that. Its good as is. Their faces were blanked out. Besides, unlike my little blog, that post was simply an excerpt from an article that has probably already been seen and read thousands and thousands of times. You gon write MIT Technology Review and bitch at them too?
SN: it’s a really good article, I fully suggest people read it in its entirety (link to article—with faces blacked out—here)
The real problem is that Roombas (iRobot, Amazon, etc) are taking identifiable pictures and they are doing next to nothing to protect the people’s privacy or their identities - the unredacted pictures literally ended up on Facebook, FFS! To reiterate what was in the article: “the images reveal a whole data supply chain—and new points where personal information could leak out—that few consumers are even aware of”
Look, I don’t mind accommodating people’s reasonable wishes on social media, but some of you get carried away when you start demanding what I should or shouldn’t post on my own blog. I could understand if I was posting stuff that was anti-Black racism, or misogynistic, homophobic, transphobic, antisemitic, Islamophobic, etc… You know that if you don’t like what I’m posting, you can go make a post of your own, right? If you are even a semi-regular follower of mine, then you should know that I am not down with pissy little, passive aggressive foolishness like this. Next thing you know, you’ll be complaining to HR that my “sighing” is negatively impacting your mental wellbeing
Sorry, anon, I’m not giving in to your … concern trolling or whatever this is supposed to be
Grow up
¯\_(ツ)_/¯
#anon#ask#answered#privacy rights#iot#internet of things#data mining#some people really be tryna use your kindness and good manners against you#i hate passive aggressive#like - just say whatever you *really* mean#dont try to hide it behind concern trolling
20 notes
·
View notes
Text
IoT Adoption and Security Issues in French Cities
The Internet of Things (IoT) is rapidly changing the way we interact with technology, and French cities are no exception. As urban centers seek to become more efficient and sustainable, they are increasingly turning to IoT devices to help manage everything from traffic flow to energy usage. However, as with any new technology, there are also significant security challenges that must be addressed…

View On WordPress
#Citizen engagement#CYBERSECURITY#Data management#Data privacy#Digital transformation#Energy efficiency#French cities#Internet connectivity#IoT#Mobile devices#Network security#Public services#Risk management#Security challenges#Sensor technology#Smart cities#Sustainability#Urban infrastructure#Urban planning
0 notes
Text
Google Says It Doesn’t 'Sell' Your Data. Here’s How the Company Shares, Monetizes, and Exploits It. | Electronic Frontier Foundation
“Google will never sell any personal information to third parties; and you get to decide how your information is used.” – Sundar Pichai
Sound familiar? Although big tech companies like Google keep the lights on by harvesting and monetizing your personal data, they can be quick to mince words and deny the strawman scenario of exchanging hard drives full of your data for a suitcase of money. Now…

View On WordPress
#ai#analytics#anonymity#artificial intelligence#corporate#cybersecurity#data#data privacy#dataprivacy#google#Government#internet#internet of things#IoT#monitoring#online#Operations Security#opsec#privacy#security#social graph#spying#surveillance#tracking
1 note
·
View note
Text
How Apple Designed Siri with AI: The Evolution of Virtual Assistance
Apple’s Siri, one of the first widely-used virtual assistants, was introduced in 2011 as a feature of the iPhone 4S. Since then, Siri has become a staple of Apple’s product lineup and has evolved to include more advanced features powered by artificial intelligence (AI). In this article, we’ll delve into the design of Siri with AI and explore how this technology has helped shape the future of virtual assistants.
The foundation of Siri’s AI technology is natural language processing (NLP), which allows the virtual assistant to understand and respond to user requests in a more human-like manner. NLP algorithms analyze user requests to identify the intention behind the request, such as finding a restaurant or setting a reminder. This allows Siri to provide a more accurate response, rather than just searching for keywords.
If a user asks Siri, “What’s the best Italian restaurant in town?” the virtual assistant will use NLP to understand that the user is looking for a recommendation for an Italian restaurant. Siri will then use its database of local restaurants to provide the user with a list of options and suggest the top-rated Italian restaurant based on user ratings and reviews.
In addition to NLP, Apple has also integrated machine learning into Siri’s design to continually improve the virtual assistant’s performance over time. The more people use Siri, the more data the virtual assistant collects, which can be used to improve its understanding of language and ability to respond to requests. This is known as machine learning in action, as the virtual assistant can learn from its interactions with users and adapt to provide a better experience.
If a large number of users ask Siri to play a specific song, the virtual assistant will learn to prioritize that request and make it easier to play in the future. Similarly, if a user frequently asks Siri to call a specific contact, the virtual assistant will learn to recognize that contact and make it easier to call in the future.
In addition to NLP and machine learning, Apple has also integrated computer vision technology into Siri, allowing the virtual assistant to recognize and respond to visual information. For example, Siri can now recognize and provide information about objects in photos, such as the location, date, and people in the image. This has expanded Siri’s capabilities beyond just voice commands, making it a more versatile virtual assistant.
Computer vision technology has also allowed Siri to integrate with other Apple products, such as the Apple Watch and Apple TV, and provide users with a seamless experience across devices. For example, if a user asks Siri to play a specific song on their Apple Watch, the virtual assistant can immediately start playing the song on the connected iPhone or iPad.
Finally, Apple has made significant investments in privacy and security to ensure that user data is protected. All of Siri’s interactions are encrypted, and user data is stored securely on Apple’s servers. Additionally, Apple has implemented strict privacy policies to ensure that user data is not shared with third-party companies without consent.
This is in contrast to other virtual assistants, such as Amazon’s Alexa, which stores user data on Amazon’s servers and may share data with third-party companies for advertising and marketing purposes. Apple’s commitment to privacy has helped to establish trust with its users and has been a key factor in Siri’s success.
Apple’s design of Siri with AI has transformed the virtual assistant from a basic voice-controlled feature to a sophisticated tool that can understand and respond to a wide range of requests. The integration of NLP, machine learning, computer vision, and privacy protections has made Siri a more human-like and versatile virtual assistant. The continued investment in AI technology has allowed Siri to evolve and improve over time, providing users with a more personalized and intuitive experience. The focus on privacy and security has also helped establish trust with users, making Siri a leading virtual assistant in the market.
As technology continues to advance, it is likely that virtual assistants like Siri will become even more integrated into our daily lives. The ability to control and interact with our devices through voice commands has already revolutionized the way we interact with technology, and the integration of AI will only continue to enhance this experience. With its commitment to privacy, security, and continuous improvement, Apple’s Siri with AI is setting the standard for virtual assistants and shaping the future of human-computer interaction.
Sources:
Apple’s official Siri website: https://www.apple.com/siri/
Apple’s Machine Learning Journal: https://machinelearning.apple.com/
The Siri section of Apple’s Artificial Intelligence and Machine Learning Research paper collection: https://ai.apple.com/research/#siriApple’s official Siri website: https://www.apple.com/siri/
Apple’s Machine Learning Journal: https://machinelearning.apple.com/
The Siri section of Apple’s Artificial Intelligence and Machine Learning Research paper collection: https://ai.apple.com/research/#siri
#siri#apple#iphone#ipod#ipad#technology news#tech news#technology#programming#coding#ai#artificial intelligence#machine learning#computer vision#steve jobs#privacy#data privacy#data#security#iot#internetofthings#internet of things#voice assistant#natural language processing#nlp
0 notes
Text
Re-Blog : Who Is Collecting Data from Your Car?
Vous ne savez pas ce qu'on fait des données de votre voiture et elles valent de l'or #bigdata #privacy #cars
Temps de lecture : 3 minutesmots-clés : Cars, data, hub de données, selling, privacy, IoT, objets connectés, Big data
Chers lecteurs,
Je vous propose aujourd’hui la lecture d’un dossier d’investigation mené par le consortium libre Markup avec les journalistes Jon Keegan et Alfred Ng au sujet des hub de données de véhicules, sujet qui ne semble pas intéresser grand monde alors que ça concerne…

View On WordPress
0 notes