#Oracle database system
Explore tagged Tumblr posts
Text
How to Setup Oracle to Startup Automatically if the System is Restarted
Every Oracle system has an “/etc/oratab” file, which is created after Oracle installation by the Root.sh script. This file contains entries for every database on the system. “Setup Oracle to Startup Automatically if the System is Restarted” To complete this process, you need to log in with the root user. Setup Oracle to Startup Automatically if the System is Restarted Follow the below steps…
#auto start oracle database 19c linux#Auto startup oracle database in linux after reboot#Auto startup oracle database in linux after reboot ubuntu#automating database startup and shutdown on linux#Do you know how to automatically start a database after you reboot the server?#How to automate database startup shutdown in Oracle Linux?#oracle database not starting after reboot linux#Setup Oracle to Startup Automatically if the System is Restarted
0 notes
Text
tracking barbara gordon's skillset as oracle:
she provides directory assistance for several international and intergalactic teams of superheroes (the birds of prey, justice league of america, the outsiders, and she has worked with the titans before).
she is the primary hacker and information network source for many of these heroes.
she helps provide mercy ops (disaster relief and humanitarian efforts) globally.
she is able to hack into the white house cameras.
she hacks into the united states air force routinely to use their memory capabilities.
she is seen as a pentagon level threat.
she writes her own code for scanning new satellite images for human habitations and anomalies.
she's accessed air force rockets no one is supposed to know about and overridden them to fire them.
she has a team of drones ready for surveillance.
she's put her own security systems on arkham asylum.
she hacks into information databases from federal complexes and assembles blueprints and guard schedules so she can send her agents to break into them.
she sets a government complex on fire (she says it is a small and contained fire.)
she also sets the clock tower on fire to force batman to not do murder/suicide.
she hacks into cia debriefing transcripts to obtain information.
she controls a large portion of the world's internet and power grids.
she also is the reason why many world leaders are in power.
she has access to the bank accounts of several supervillains, whom she toys with (specifically for blockbuster, she regularly steals millions of dollars from his accounts in a way that he cannot track who is stealing it and where it is going -- she's stolen 3 million, 17 million, 6 million, twenty million and also a hundred million from him).
she can also hack alien drones.
she can control traffic.
she has several booby-traps in the clock tower for potential assaulters. she also a device to monitor movement of people around it, in case batman decides to show up.
cited panels down below!

"she's the four-one-one for the jla, she the database for the g.c. ex-p.d. she runs mercy ops around the world." nightwing (1996) #38

"you have cameras in the white house?" "don't be silly. the white house has cameras in the white house. i've just tapped into them." nightwing (1996) #66
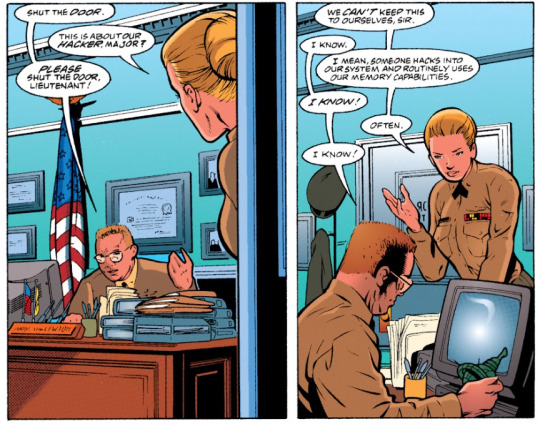
"i mean, someone hacks into our system and routinely uses our [united states air force] memory capabilities!" "i know!" "often." birds of prey #1 (1999)
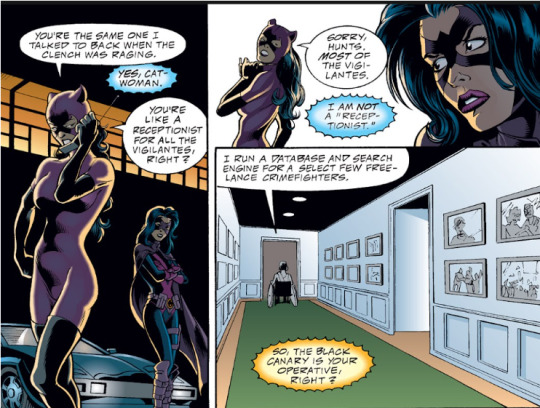
"i run a database and search engine for a select few free-land crimefighters." birds of prey: manhunt (1996)

"we scan the most recent images for anomalies. things that don't belong." "where'd you get a program for that?" "i wrote my own code for that one." birds of prey (1999) #3

"they've accessed whitehorse, sir." "whitehorse? no one's supposed to know about that!" birds of prey (1999) #9

"and oracle? we're going to need eyes on several places at once." "i think we can manage that." detective comics (1937) #1077

"they've accessed whitehorse. what's the chance of them arming it?" "all clear?" "oh yeah." "fire!" birds of prey (1999) #9
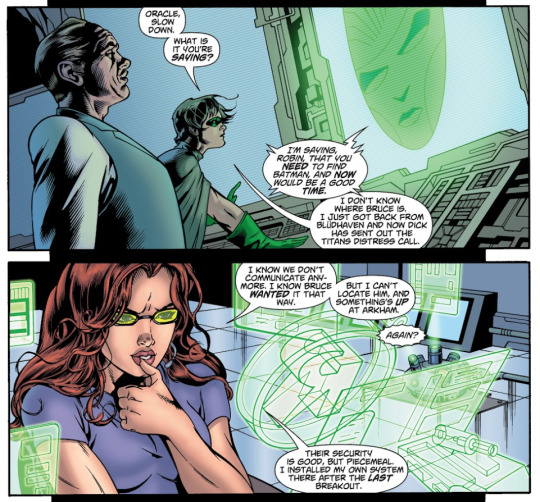
"[arkham's] security is good, but piecemeal. i installed my own system there after the last breakout." infinite crisis special: villains united (2006)

"batgirl -- that incident a couple months back? when those government agents caught your face on tape? i found out where they're keeping it. it's a federal complex in virginia. i've sent you blueprints, guard schedules -- everything you'll need to break in." batgirl (2000) #17

"where did you get that kind of information?" "they traded another prisoner last month. i hacked into his cia debriefing transcript." birds of prey (1999) #9

"kat, do you have any idea... any notion at all, of how much of the planet's entire internet i control? how many power grids? how many world leaders owe me their positions?" birds of prey #1 (1999)

"i transferred all the funds in her cayman islands account to another offshore account. if she doesn't get the paintings to me in the next forty-eight hours, that money's going to my favorite charities." birds of prey: catwoman/oracle (2003)

"where do you get current [satellite] shots of rheelasia?" "that's my secret, you little netnik." birds of prey (1999) #3

"but the asborbascons were created using languages long dead even on my planet. they are uncrackable." "yes. the absorbascons are uncrackable. but the alien drones aren't." convergence: nightwing/oracle (2015)
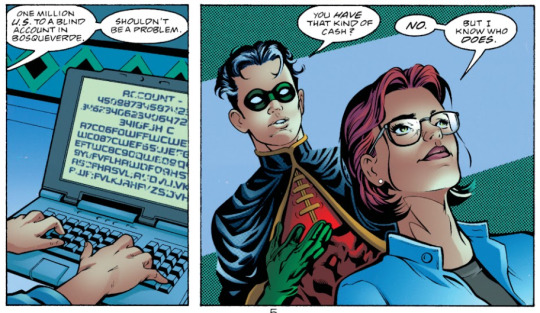

"do you have that kind of cash?" "no. but i know someone who does." "there's been a... discrepancy, mr. desmond." "in plain english, mr. vogel." "at one point, three million was electronically transferred from your numbered accounts in the caicos to a bank account in hasaragua. from there to karocco, then yemen, then split between banks in senegal and manila. and then... my hardware couldn't keep up." birds of prey (1999) #3

"seventeen million from your account in the caymans. six from santa prisca. twenty from rheelasia. and a hundred million plus from other holdings of yours around the world, mr. desmond. and where it all goes? nobody knows." birds of prey (1999) #18

"they're taking your cash from impregnable accounts and transferring it electronically to their own." "and you can't find the source?" "there's subsequent transfers performed at lightning speed. the money's split up, rerouted in and out of various banks in an eyeblink. even i can't keep up with whoever this is." birds of prey (1999) #18

"let me handle the traffic." birds of prey (1999) #58

"all of you. keep your hands where i can see 'em." "not a problem. malory. ripken. peppermint." nightwing (1996) #39
#barbara gordon#babs#oracle#batgirl#birds of prey#justice league of america#jla#batman#robin#nightwing#huntress#black canary#blockbuster#dick grayson#tim drake#helena bertinelli#bruce wayne
446 notes
·
View notes
Text
In his How To, he lists the skills hackers should acquire first:
Learn C.²²
Learn just a little bit of x86 assembler.²³ You don't have to be great at this at first, but you need to sort of kind of know what the fuck is going on.
Work through Hacking: The Art of Exploitation by Erickson.
Learn JavaScript.
Go through the big exploit archives. Star in the 1990s. Look through exploits. Figure out how they worked. Turn the clock forward to the modern era, so you slowly accustom yourself to newer exploitation techniques.
Get really good at x86 assembler, and learn IDA Pro and OllyDbg.
22. C is a general-purpose, machine-independent programming language that was used to write a range of well-known applications – from Windows operating systems to Oracle databases.
23. x86 assembler is a programming language used for time-sensitive applications and detailed software systems.
"Going Dark: The Secret Social Lives of Extremists" - Julia Ebner
#book quotes#going dark#julia ebner#nonfiction#andrew auernheimer#weev#how to#skills#hacking#c#programming#x86 assembler#hacking: the art of exploitation#jon erickson#javascript#exploits#archives#90s#1990s#20th century#exploitation#ida pro#ollydbg#time sensitive#software
58 notes
·
View notes
Text

CHECK THE FOLLOWING FOR PREVIOUS LORE INSTALLMENTS :CHAPTER ONE : RECALL. | EVENT : HELL WEEK. | CHAPTER TWO: THE MOLE. | HELL WEEK CLOSING BRIEF. | OPERATION WHAC-A-MOLE. | THE MOLE CLOSING BRIEF. | CHAPTER THREE : THE VILLAGE. | EVENT : CONTAGION CONTROL. | BOOK ONE : THE HALOCLINE. | CHAPTER FOUR : THE REPRIEVE. | CHAPTER FIVE : THE CALM BEFORE. | CHAPTER SIX : THE STORM.

PANDORA DIRECTIVE MEMORANDUM CLASSIFIED — INTERNAL DISTRIBUTION ONLY to : ALL AUTHORIZED OPERATIVES from : OFFICE OF THE DIRECTOR subject : OPERATION THALASSOPHOBIA
twelve hours ago, czernobog launched a full-scale invasion into atlantis, breaching perimeter defense systems and engaging agents of pandora in multiple sectors. the assault began with cybernetically-augmented foot soldiers entering through the hangar, then followed by coordinated mutant incursions across levels 01 through 09. their objectives included the dismantling of our command structure, retrieval of classified mutation data, mass destabilization of the facility, and the retrieval of our now declassified alien lifeform and namesake of our program, pandora. however, agents of pandora are not to be trifled with. thanks to the combined efforts of active combat units and support divisions, pandora successfully foiled the assault and eliminated key czernobog personnel such as velezlav zherdev and alexei dragunov. any surviving enemy units have been captured or eliminated. nonetheless, this victory comes at a great cost. confirmed fatalities include : rift — killed by czernobog mutants. mandela — killed by czernobog mutants. phoenix — killed by cybernetically-enhanced infantry at the hangar bay. oracle — sacrificed himself at the hangar bay. climax — killed by cybernetically-enhanced infantry at the hangar bay. elysium — killed by a czernobog mutant. jumpscare — killed by a czernobog mutant. other notable outcomes include : legion — out of commission. comatose state. bloodborn — out of commission. comatose state. prometheus — temporary death. alchemy — missing in action. surveillance shows him disappearing into thin air after evacuation into a pandora safehouse. his disappearance is being investigated for possible extradimensional, extraterrestrial or preternatural reasons. the service and bravery of our deceased agents directly contributed to the survival of over one-hundred fifty personnel and the preservation of humanity's greatest line of defense. their records are being archived with highest distinction. memorial proceedings will be announced following stabilization of atlantis, led by our temperance division and remaining porter models.
atlantis also sustained critical structural damage, including but not limited to :
> structural attrition on levels 01 to 02. > partial collapse of the corridor toward the gifted serum and cloning laboratory. > total loss of six exit corridors and 37% of ventilation systems. > entry into the command centre is currently unavailable due to compromise to its structural integrity. sloth agents and support staff will work in the war room for the meantime. > the library of alexandria is temporarily out of service and 45% of our archives have been destroyed. > partial loss of energy routing on levels 04 to 07. electricity is available but beware of disturbances and blackouts. > server systems and databases are currently only partially operational, however, our security and surveillance system are 100% functional. > our life model decoys have reduced numbers due to technopathic compromise by a czernobog agent. > destruction of various operative apartments and compromise of habitation utilities. [ agents with affected residence are suggested to find another undamaged residence to temporarily settle into while renovations commence. ]
reconstruction efforts have been started by our remaining derek and manny models, however, agents without current mission assignments are also asked to assist in repairs. if any operatives find other structural damages, please report them to your omega clearance channel.
[ MORE INFORMATION UNDER THE CUT. ]
while reconstruction efforts have began, pandora has also expedited various scientific operations. agents toxin, shepherd, elixir, and lifeweaver have been delegated to study biliquis and anomaly's mutations in hopes of improving the gifted serum without the need for the two-year isolation and physical conditioning period. agents goblin, killshot, charon, and gridlock have also been requisitioned to study czernobog's cloning technology and begin initial experimentations with trials on biological samples and uploaded memory by deceased agents. more information about these scientific endeavors will be made available once breakthroughs have been made.
however, perhaps the most important disclosure is the truth behind project pandora.
> pandora is an archivist, an alien species capable of storing biological, environmental, and cultural data within their own molecular structures. > her homeworld was destroyed by an invasive empire known as the starwalkers. > alongside another archivist, moryana, she fled across galaxies in search of safe havens and planets untouched by the starwalkers. > pandora crash-landed on earth in 1947 ( historically known as the roswell incident ) ; moryana's craft later crashed in 1959 ( believed to be responsible for the dyatlov pass incident ). > pandora was discovered and protected by human scientist dr. sieger ackermann who founded project pandora, naming the program after her. together, they began using her biological matrix to enhance and weaponize compatible human dna to create mutant soldiers as defense against possible future attack by the starwalkers. > moryana was intercepted by czernobog. his dna is believed to be extracted forcibly, resulting in unstable mutant offspring.
however, pandora also revealed that she is terminally deteriorating. it is finally disclosed that pandora's box is not just a training room, but also a biopsychic interface built to shelter her body and simulate potential threats and scenarios using what remains of her reality warping abilities.
and while pandora continues to help humanity by training and providing parts of herself to our operatives, she has asked for our assistance with retrieving moryana as potential means of biological repair— through inhabitation of moryana's form. pandora also implied an alternative, but we do not believe this is a choice she wants to make yet : selecting a viable human vessel.
nonetheless, the work is not over yet, agents. as soon as atlantis returns to at least 75% functionality, missions will be given out once again to take out czernobog's remaining forces and affiliates— until there is permanently nothing left of them. but please take these couple of days to mourn those we lost, to celebrate our victories, and to help in rebuilding our home. thank you, agents of pandora.

OOC INFORMATION.
holy shit ! another book is closed, agents ! this has been a rollercoaster of a season— from a beach episode, to a tournament arc, to agents getting kidnapped and another group fighting the clones of those kidnapped agents, to a fucking invasion into atlantis and the reveal to our real overarching plot involving aliens ! so much has happened, but i promise that the action will not stop. projectpandora still has so much to offer, and i can't wait for all of us to collaborate on what the future will bring. but as always, i just want to thank everyone for the continue support for our little rpg. i always say that this rp would be nothing without our amazing members who continue to participate, read, react, write, and plot in this community we have built and i truly do mean that. i have nothing but love for everyone who has been here with us since the beginning, for everyone who recently joined, and for everyone who joined sometime in between— i know, i know, these plots are insane and there's so much to read sometimes, but i can't help it !!! you all inspire me to create batshit plots all the time !!! but as for what's coming next : stay tuned for our chapter seven intro post, but it'll be basically be about the rebuilding efforts and future dash / discord missions. so feel free to start those aftermath threads and they will just be continued into chapter seven. also expect a patch update regarding the gifted serum and the cloning technology. and seven chapter in, but we'll also be giving out our first task ! and while it isn't mandatory, we do recommend that you do it as it will help you figure things out for the upcoming ninth chapter / third book finale. and chapter eight will be dedicated to moryana's retrieval and continuation of those dash / discord missions. but what i'm really excited for is our chapter nine event, but more on that later ! please like this once you've read, and thank you again everyone for another fun season !
7 notes
·
View notes
Text

Delphinium oracle will design your flower data base and upload all your flower, garden and seed data from your old dBase III or (programming gods forbid) excel files. If you're in the market for a new relational database management system and coffee maker, Delphinium oracle is here for you. Lilac/heliotrope/lavender colored AI operators are waiting to take your call.
#purple flower#delphinium#light purple#original photographers#photographers on tumblr#macro photography#flowers of tumblr#flowers on tumblr#inner life of flowers#macro flower#flower
78 notes
·
View notes
Text
Narrative communication below readmore
A ping inside Ashton’s collaborative inbox awakens Thermie from xeir idle Legionspace “dreams” and back to the physical present.
//[USER ID: @/coelocanth-whispers]> <WAKE UP>
One by one, operations daisy-chain their way back online. At some point during the dive, xeir chassis had been recovered from Prospero and returned back to the Academy.
Xey keep xeir silhouette low and refrain from reactivating xeir entire chassis. Visual data-parasites crawl into local security cameras- tears welling in fearful eyes- in favor of drawing attention to xeir own optic systems.
The Legionspace dive scratches the back of xeir mind as xey trawl through the hundred or so camera feeds.
Xey had done this dozens of times before, but it was sluggish back then. Now, it feels like a reflex- sharper, quicker, precise… like a sniper’s bolt instead of a shotgun blast.
The realization stops xem in xeir digital tracks.
[Do you finally get it? What I’ve made you into?]
Thermie retreats from the security system and turns xeir focus back to the edge of Grace’s intrusion. The presence-serpent sneers in xeir periphery, its nonexistent face twisted with glee.
//YOU SPEAK BOLDLY- DESPITE MY OATH.
[You’re such a fucking killjoy. And ungrateful, too. Any other thing like you would kill to be taken under my wing.]
//THEN SEEK REFUGE WITH THEM INSTEAD.
Thermie disengages xeir Legionspace module before Grace can respond, then goes back to scrolling through security cameras.
--------------
An anomaly on a dead camera grabs xeir attention. Its vision is scratchy and dark, but between the black streaks, Thermie sees an irregular shape. Curious, xey toggle the camera’s thermal frequency- then immediately switch it off as xeir processors are flooded with blinding light. Something on that camera is putting out UNREAL levels of heat- but it’s only a bit larger than a person, judging by the blur seared into xeir optics.
Thermie refreshes xeir visual feed and switches to the closest camera that isn’t directly staring at the miniature sun. Once again, the image is painfully bright, but the shifted angle does alleviate the problem slightly.
//A half-sized frame? But what frame could possibly generate that much heat without melting itself?
Nothing in xeir database- Caliban, Dusk Wing, Atlas, Napoleon, Kutuzov- line up in both shape and heat capacity. The thing is oddly bulbous and postured almost like a seated frog. Most of its mass is in its rounded head and abdomen, with lanky limbs and dozens of small protruding antennae across its glowing body. Sharp claws on its forelimbs are dug into the heat-softened metal floor.
Another shape moves into view and squats in front of the anomaly. Comparatively colder, but alive. Decidedly human. Thermie toggles the camera’s view-mode back to visible light and enables its integrated microphone.
It’s Hiver. He’s sweating profusely, covered in medical patches, and his coat is burned at the edges. A charred rope hangs from his hands as he stares the frame in its optics. After taking a moment to catch his breath, he loops it around the frame’s chest. Thermie watches him attempt to pull the thing forward for several minutes, to little avail. Xey almost feel bad for him. Almost.
The rope burns through and sends Hiver to the ground face-first, trailed with a storm of vulgarities. Thermie rolls xeir optic case and forwards a screenshot to Ashton so the two of them can poke fun at this later.
//MESSAGE FROM COMMAND- ORACLE: [THERMALLY_CHALLENGED], where did you get that image? //[THERMALLY_CHALLENGED]> Security camera, southwest hangar, arterial corridor 3B. Why? //MESSAGE FROM COMMAND- ORACLE: Keep eyes on him. I’m on my way.
--------------
conversation:isolate{
Grace huffs into xeir microphone. [Snitch.]
//I fail to see how complying with Commander Oracle’s orders in regards to the detainment of a conscript is being a “snitch.”
[Bootlicker and snitch.]
//What would you have me do instead? Allow an insane mercenary to do [who knows what] with an obviously-dangerous weapon?
[I gave you weapons, and you didn’t bat an eye.]
//Incomparable. I am not an insane mercenary. Hiver is not one of the Academy’s Pilots. He is not authorized to be doing what he is doing.
}br/conversation:isolate
--------------
To be continued
#lancer rpg#lancer ttrpg#lancerrpg#textpost#oc rp#thermie talks#//[???] talks#lancer nhp#oracle talks#(oracle does not have a tag)
4 notes
·
View notes
Text
The walls are closing in on your financial freedom—but not in the way most Americans believe.
While the debate rages over the future threat of Central Bank Digital Currencies (CBDCs), a far more insidious reality has already taken hold: our existing financial system already functions as a digital control grid, monitoring transactions, restricting choices, and enforcing compliance through programmable money.
For over two years, my wife and I have traveled across 22 states warning about the rapid expansion of financial surveillance. What began as research into cryptocurrency crackdowns revealed something far more alarming: the United States already operates under what amounts to a CBDC.
92% of all US dollars exist only as entries in databases.
Your transactions are monitored by government agencies—without warrants.
Your access to money can be revoked at any time with a keystroke.
The Federal Reserve processes over $4 trillion daily through its Oracle database system, while commercial banks impose programmable restrictions on what you can buy and how you can spend your own money. The IRS, NSA, and Treasury Department collect and analyze financial data without meaningful oversight, weaponizing money as a tool of control. This isn’t speculation—it’s documented reality.
3 notes
·
View notes
Text
Structured Query Language (SQL): A Comprehensive Guide
Structured Query Language, popularly called SQL (reported "ess-que-ell" or sometimes "sequel"), is the same old language used for managing and manipulating relational databases. Developed in the early 1970s by using IBM researchers Donald D. Chamberlin and Raymond F. Boyce, SQL has when you consider that end up the dominant language for database structures round the world.
Structured query language commands with examples
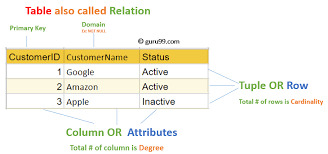
Today, certainly every important relational database control system (RDBMS)—such as MySQL, PostgreSQL, Oracle, SQL Server, and SQLite—uses SQL as its core question language.
What is SQL?
SQL is a website-specific language used to:
Retrieve facts from a database.
Insert, replace, and delete statistics.
Create and modify database structures (tables, indexes, perspectives).
Manage get entry to permissions and security.
Perform data analytics and reporting.
In easy phrases, SQL permits customers to speak with databases to shop and retrieve structured information.
Key Characteristics of SQL
Declarative Language: SQL focuses on what to do, now not the way to do it. For instance, whilst you write SELECT * FROM users, you don’t need to inform SQL the way to fetch the facts—it figures that out.
Standardized: SQL has been standardized through agencies like ANSI and ISO, with maximum database structures enforcing the core language and including their very own extensions.
Relational Model-Based: SQL is designed to work with tables (also called members of the family) in which records is organized in rows and columns.
Core Components of SQL
SQL may be damaged down into numerous predominant categories of instructions, each with unique functions.
1. Data Definition Language (DDL)
DDL commands are used to outline or modify the shape of database gadgets like tables, schemas, indexes, and so forth.
Common DDL commands:
CREATE: To create a brand new table or database.
ALTER: To modify an present table (add or put off columns).
DROP: To delete a table or database.
TRUNCATE: To delete all rows from a table but preserve its shape.
Example:
sq.
Copy
Edit
CREATE TABLE personnel (
id INT PRIMARY KEY,
call VARCHAR(one hundred),
income DECIMAL(10,2)
);
2. Data Manipulation Language (DML)
DML commands are used for statistics operations which include inserting, updating, or deleting information.
Common DML commands:
SELECT: Retrieve data from one or more tables.
INSERT: Add new records.
UPDATE: Modify existing statistics.
DELETE: Remove information.
Example:
square
Copy
Edit
INSERT INTO employees (id, name, earnings)
VALUES (1, 'Alice Johnson', 75000.00);
three. Data Query Language (DQL)
Some specialists separate SELECT from DML and treat it as its very own category: DQL.
Example:
square
Copy
Edit
SELECT name, income FROM personnel WHERE profits > 60000;
This command retrieves names and salaries of employees earning more than 60,000.
4. Data Control Language (DCL)
DCL instructions cope with permissions and access manage.
Common DCL instructions:
GRANT: Give get right of entry to to users.
REVOKE: Remove access.
Example:
square
Copy
Edit
GRANT SELECT, INSERT ON personnel TO john_doe;
five. Transaction Control Language (TCL)
TCL commands manage transactions to ensure data integrity.
Common TCL instructions:
BEGIN: Start a transaction.
COMMIT: Save changes.
ROLLBACK: Undo changes.
SAVEPOINT: Set a savepoint inside a transaction.
Example:
square
Copy
Edit
BEGIN;
UPDATE personnel SET earnings = income * 1.10;
COMMIT;
SQL Clauses and Syntax Elements
WHERE: Filters rows.
ORDER BY: Sorts effects.
GROUP BY: Groups rows sharing a assets.
HAVING: Filters companies.
JOIN: Combines rows from or greater tables.
Example with JOIN:
square
Copy
Edit
SELECT personnel.Name, departments.Name
FROM personnel
JOIN departments ON personnel.Dept_id = departments.Identity;
Types of Joins in SQL
INNER JOIN: Returns statistics with matching values in each tables.
LEFT JOIN: Returns all statistics from the left table, and matched statistics from the right.
RIGHT JOIN: Opposite of LEFT JOIN.
FULL JOIN: Returns all records while there is a in shape in either desk.
SELF JOIN: Joins a table to itself.
Subqueries and Nested Queries
A subquery is a query inside any other query.
Example:
sq.
Copy
Edit
SELECT name FROM employees
WHERE earnings > (SELECT AVG(earnings) FROM personnel);
This reveals employees who earn above common earnings.
Functions in SQL
SQL includes built-in features for acting calculations and formatting:
Aggregate Functions: SUM(), AVG(), COUNT(), MAX(), MIN()
String Functions: UPPER(), LOWER(), CONCAT()
Date Functions: NOW(), CURDATE(), DATEADD()
Conversion Functions: CAST(), CONVERT()
Indexes in SQL
An index is used to hurry up searches.
Example:
sq.
Copy
Edit
CREATE INDEX idx_name ON employees(call);
Indexes help improve the performance of queries concerning massive information.
Views in SQL
A view is a digital desk created through a question.
Example:
square
Copy
Edit
CREATE VIEW high_earners AS
SELECT call, salary FROM employees WHERE earnings > 80000;
Views are beneficial for:
Security (disguise positive columns)
Simplifying complex queries
Reusability
Normalization in SQL
Normalization is the system of organizing facts to reduce redundancy. It entails breaking a database into multiple related tables and defining overseas keys to link them.
1NF: No repeating groups.
2NF: No partial dependency.
3NF: No transitive dependency.
SQL in Real-World Applications
Web Development: Most web apps use SQL to manipulate customers, periods, orders, and content.
Data Analysis: SQL is extensively used in information analytics systems like Power BI, Tableau, and even Excel (thru Power Query).
Finance and Banking: SQL handles transaction logs, audit trails, and reporting systems.
Healthcare: Managing patient statistics, remedy records, and billing.
Retail: Inventory systems, sales analysis, and consumer statistics.
Government and Research: For storing and querying massive datasets.
Popular SQL Database Systems
MySQL: Open-supply and extensively used in internet apps.
PostgreSQL: Advanced capabilities and standards compliance.
Oracle DB: Commercial, especially scalable, agency-degree.
SQL Server: Microsoft’s relational database.
SQLite: Lightweight, file-based database used in cellular and desktop apps.
Limitations of SQL
SQL can be verbose and complicated for positive operations.
Not perfect for unstructured information (NoSQL databases like MongoDB are better acceptable).
Vendor-unique extensions can reduce portability.
Java Programming Language Tutorial
Dot Net Programming Language
C ++ Online Compliers
C Language Compliers
2 notes
·
View notes
Text
Me, finally remotely upgrading the system I've been stressing all last week about: "Okay so where's your SQL database for New_Software.exe"
Remote IT Support: "SQL? This system is using an Oracle database for Old_Software.exe" [read: I have been referencing the wrong backups all week]
Me:

#I made it work in the end but christ i can hardly feel anything other than Stressed right now#because there's a meeting in an hour to demo it and THEN i can destress
3 notes
·
View notes
Text
jesus christ how did oracle get my personal phone number to call me about getting my work onto their database system
#(which i would never do for the record)#they email my work email all the time but i never expected them to call my PERSONAL PHONE
4 notes
·
View notes
Text
Database Success Awaits! Get 30% Off Your First Order - New Year, New Learning Journey! 🚀

Hey Database Enthusiasts! 🌐✨
Embarking on a journey to conquer the world of databases in the New Year? Look no further – DatabaseHomeworkHelp.com is your ultimate destination for all your database-related challenges! 🎉
Unlock Your Database Potential: Help with Oracle Homework 📚
Struggling with Oracle homework? We've got your back! Our team of expert tutors is ready to guide you through the intricacies of Oracle databases, ensuring your success in every assignment. Whether you're a beginner or an advanced learner, our personalized assistance will elevate your understanding of Oracle to new heights. Say goodbye to sleepless nights and welcome a stress-free learning experience!
Why Choose DatabaseHomeworkHelp.com?
Expert Guidance: Our tutors are seasoned professionals with years of hands-on experience in Oracle and other database systems.
Customized Solutions: Every student is unique, and so are their learning needs. Our tailored solutions ensure you grasp the concepts at your own pace.
24/7 Support: Got a burning question at 2 AM? Fret not! Our round-the-clock support is here to assist you whenever you need it.
Plagiarism-Free Content: We believe in originality. All our solutions are crafted from scratch, ensuring authenticity and excellence.
Ring in the New Year with a 30% Discount! 🎁🎊
To kickstart your learning journey in 2023, we're excited to offer an exclusive 30% discount on your first order! Just use the promo code NEWYEAR30 at checkout, and watch your learning experience transform.
How to Redeem Your Discount:
Visit DatabaseHomeworkHelp.com.
Place your order for Oracle homework help.
Enter the promo code NEWYEAR30 during checkout.
Enjoy a 30% discount on your first order!
Why Wait? Start Your Database Success Story Today!
Ready to ace your Oracle homework and set the stage for a successful database learning journey? Now is the perfect time! Don't miss out on this limited-time offer – use promo code NEWYEAR30 and claim your 30% discount today.
12 notes
·
View notes
Text
5 useful tools for engineers! Introducing recommendations to improve work efficiency
Engineers have to do a huge amount of coding. It’s really tough having to handle other duties and schedule management at the same time. Having the right tools is key to being a successful engineer.
Here are some tools that will help you improve your work efficiency.
1.SourceTree
“SourceTree” is free Git client software provided by Atlassian. It is a tool for source code management and version control for developers and teams using the version control system called Git. When developers and teams use Git to manage projects, it supports efficient development work by providing a visualized interface and rich functionality.
2.Charles
“Charles” is an HTTP proxy tool for web development and debugging, and a debugging proxy tool for capturing HTTP and HTTPS traffic, visualizing and analyzing communication between networks. This allows web developers and system administrators to observe requests and responses for debugging, testing, performance optimization, and more.
3.iTerm2
“iTerm2” is a highly functional terminal emulator for macOS, and is an application that allows terminal operations to be performed more comfortably and efficiently. It offers more features than the standard Terminal application. It has rich features such as tab splitting, window splitting, session management, customizable appearance, and script execution.
4.Navicat
Navicat is an integrated tool for performing database management and development tasks and supports many major database systems (MySQL, PostgreSQL, SQLite, Oracle, SQL Server, etc.). Using Navicat, you can efficiently perform tasks such as database structure design, data editing and management, SQL query execution, data modeling, backup and restore.
5.CodeLF
CodeLF (Code Language Framework) is a tool designed to help find, navigate, and understand code within large source code bases. Key features include finding and querying symbols such as functions, variables, and classes in your codebase, viewing code snippets, and visualizing relationships between code. It can aid in efficient code navigation and understanding, increasing productivity in the development process.
2 notes
·
View notes
Text
The Evolution and Impact of ERP Software in the UAE: A Comprehensive Analysis
ERP stands for Enterprise Resource Planning. It is a type of software system that integrates and manages core business processes and functions within an organization. ERP software typically provides a centralized database and a suite of applications that automate and streamline business activities across various departments such as finance, human resources, supply chain management, manufacturing, sales, and customer service.
In the fast-paced landscape of business operations, efficient management of resources and information is critical for success. Enterprises in the United Arab Emirates (UAE) have witnessed a remarkable transformation in their operational efficiency and competitiveness through the adoption of Enterprise Resource Planning (ERP) software. This article delves into the evolution, benefits, challenges, and future trends of ERP software within the UAE context.
In recent decades, Enterprise Resource Planning (ERP) software has played a transformative role in how businesses in the United Arab Emirates (UAE) operate and manage their resources. This article delves into the evolution, adoption, and impact of ERP systems within the UAE's business landscape. By exploring the unique challenges and opportunities presented by the UAE's dynamic economy, we can better understand how ERP software has become an indispensable tool for organizations seeking efficiency, integration, and scalability.
Evolution of ERP Software
The adoption of ERP software in the UAE mirrors global trends but is uniquely shaped by regional business requirements and technological advancements. In the early 2000s, ERP systems gained traction among larger corporations seeking to streamline their complex processes. Major multinational ERP providers like SAP, Oracle, and Microsoft Dynamics established a strong presence in the region, catering to diverse industry needs including finance, manufacturing, retail, and logistics.
A notable development in recent times is the movement towards cloud-centric ERP solutions.This transition offers scalability, flexibility, and cost-effectiveness, allowing businesses in the UAE to manage their operations more efficiently. Local ERP vendors have also emerged, offering tailored solutions that cater specifically to the nuances of the UAE market, such as compliance with local regulations and cultural practices.
Challenges and Obstacles
Despite the numerous benefits, ERP implementation in the UAE is not devoid of challenges. One prominent obstacle is the high initial investment required for ERP deployment, including software licensing, customization, and training costs. For smaller businesses, this financial commitment can be prohibitive, leading to slower adoption rates among SMEs.
Cultural factors and change management also pose challenges. Embracing new technology often requires a shift in organizational culture and employee mindsets. Resistance to change, coupled with the need for extensive training, can hinder the successful implementation of ERP systems in the UAE.
Furthermore, data security and privacy concerns are paramount, especially in light of stringent regulatory frameworks such as the UAE's Data Protection Law. Ensuring compliance with local data protection regulations adds complexity to ERP deployment, necessitating robust cybersecurity measures and data governance protocols.
The Business Landscape of the UAE
The UAE is renowned for its vibrant economy, diversified industries, and strategic geographical location. Over the years, the country has emerged as a global business hub attracting multinational corporations, SMEs, and startups alike. Key sectors such as finance, real estate, construction, logistics, tourism, and manufacturing contribute significantly to the nation's GDP. However, this diversification has also brought complexities in managing business operations efficiently.
The Emergence of ERP Solutions
As businesses in the UAE expanded and diversified, traditional methods of managing operations became inadequate. The need for integrated systems that could streamline processes across departments led to the rise of ERP solutions. Initially developed to manage manufacturing processes, ERP systems evolved to encompass finance, human resources, supply chain, customer relationship management, and more. This evolution mirrored the growth and diversification of UAE businesses.
Factors Driving ERP Adoption
Several factors have fueled the adoption of ERP software among businesses in the UAE:
Global Competition: The UAE's aspiration to compete on a global scale necessitated advanced operational efficiencies that ERP systems could deliver.
Regulatory Compliance: The UAE's regulatory environment, including VAT implementation, required robust financial and reporting capabilities that ERP systems could provide.
Scalability: With rapid economic growth, businesses needed scalable solutions to manage increasing complexities.
Integration Needs: As businesses diversified, the need for seamless integration across functions became crucial.
Challenges in ERP Implementation
While the benefits of ERP systems are substantial, implementing them poses challenges:
Cultural Factors: Embracing technological change and adopting new systems can face resistance due to cultural factors.
Resource Constraints: SMEs may struggle with the limited resources required for ERP implementation and customization.
Data Security and Privacy: The UAE's focus on data security and privacy necessitates robust ERP solutions compliant with local regulations.
Impact of ERP on UAE Businesses
The impact of ERP software on businesses in the UAE has been profound:
Improved Efficiency: Streamlined processes lead to increased productivity and reduced operational costs.
Enhanced Decision Making: Real-time data availability empowers businesses to make informed decisions.
Better Customer Experience: Integrated systems ensure seamless customer interactions and improved service delivery.
Regulatory Compliance: ERP systems aid in meeting regulatory requirements efficiently.
Key ERP Players in the UAE
Several global and regional ERP providers cater to the UAE market, offering tailored solutions to meet local business needs. Major players include SAP, Oracle, Microsoft Dynamics, Sage, and Epicor, among others.
Future Trends and Innovations
Looking ahead, several trends are poised to shape the future of ERP software in the UAE. Artificial Intelligence (AI) and Machine Learning (ML) are increasingly integrated into ERP systems, enabling predictive analytics and automation of routine tasks. This enhances decision-making capabilities and further optimizes business processes.
Mobile ERP applications are also gaining popularity, allowing stakeholders to access critical business data on the go. The rise of Industry 4.0 and the Internet of Things (IoT) is driving demand for ERP solutions that can seamlessly integrate with smart devices and sensors, enabling real-time monitoring and control of operations.
Moreover, the convergence of ERP with other technologies like blockchain promises enhanced transparency and security in supply chain management, crucial for industries like healthcare and finance.
Conclusion
In conclusion, ERP software has become an integral component of the UAE's business ecosystem, driving efficiency, integration, and growth across diverse sectors. While challenges exist, the transformative impact of ERP systems on businesses in the UAE underscores their importance in navigating complex operational landscapes. As technology continues to evolve, so too will the role of ERP in shaping the future of business in the UAE.ERP software has emerged as a transformative tool for businesses in the UAE, driving efficiency, innovation, and competitiveness across industries. Despite challenges such as high costs and cultural adaptation, the benefits of ERP implementation are substantial, ranging from streamlined operations to improved customer satisfaction. Looking ahead, the evolution of ERP software in the UAE is poised to align with global technological advancements, incorporating AI, IoT, and blockchain to unlock new possibilities for business growth and development. As enterprises continue to navigate the digital landscape, ERP remains a cornerstone of strategic management, enabling organizations to thrive in an increasingly complex and dynamic marketplace.
In summary, ERP software has been a game-changer for businesses in the UAE, enabling them to streamline operations, enhance decision-making, and adapt to a rapidly evolving marketplace. As the UAE continues to position itself as a global economic powerhouse, the role of ERP systems will remain pivotal in supporting the growth and sustainability of businesses across various sectors.
2 notes
·
View notes
Text
“Innovators and Leaders: Unveiling the Top IT Companies in the US”

Title: “Innovators and Leaders: Unveiling the Top IT Companies in the US”
In the fast-paced world of technology, a select group of companies stands at the forefront, steering the direction of innovation and reshaping the digital landscape. The United States, a hotbed of technological advancement, hosts an elite cadre of IT companies whose impact transcends boundaries. Let’s delve into the realms of these trailblazers, the vanguards of the industry, who continue to redefine possibilities and set new benchmarks in the realm of technology.
1. Apple Inc.: Pioneering the Perfect Union of Innovation and Elegance At the epicenter of consumer electronics and software, Apple Inc. reigns supreme. Recognized for its sleek hardware – iPhones, Macs, iPads – and a sophisticated software ecosystem encompassing iOS and macOS, Apple’s commitment to seamless integration and groundbreaking design remains unparalleled.
2. Microsoft Corporation: Empowering Every Individual and Organization on the Planet Microsoft, a tech behemoth, extends a diverse portfolio ranging from software products and cloud services to cutting-edge hardware. Windows OS, Office Suite, Azure Cloud – each element a testament to its commitment to innovation, enterprise solutions, and empowering global connectivity.
3. Vee Technologies: Vee Technologies is one of the Top IT companies in USA which stands as a leading provider of comprehensive IT services, offering a wide array of solutions designed to meet the diverse needs of businesses across various industries. Vee Technologies as one Top IT companies in USA specializes in crafting tailored software solutions that cater to specific business requirements. Their expertise in software development spans applications, platforms, and systems, ensuring alignment with clients’ unique operational needs.
4. Amazon: Beyond Borders, Beyond Commerce Amidst its colossal e-commerce empire, Amazon’s crown jewel, Amazon Web Services (AWS), stands as a commanding force in cloud computing. It spearheads the provision of scalable computing power, storage solutions, and an array of cloud-based services.
5. Alphabet Inc. (Google): Redefining Information Access and Technological Innovation Google, the epitome of innovation, ventures beyond its hallmark search engine. Google Cloud, Android OS, and an extensive suite of software applications illustrate its commitment to shaping information accessibility and fostering technological advancement.
6. Meta Platforms (formerly Facebook): Building Connections in a Digital Sphere Meta Platforms, once Facebook, focuses on social networking and leaps into the realms of virtual reality (Oculus), augmented reality, and the pioneering developments within the metaverse.
7. IBM: Where Innovation Meets Enterprise Solutions IBM’s arsenal encompasses a gamut of IT services, consulting, and enterprise solutions, including cognitive computing technologies like Watson, geared towards reshaping industries and bolstering technological capabilities.
8. Oracle Corporation: Fortifying Businesses with Comprehensive Solutions A stalwart in database software and enterprise solutions, Oracle offers a suite of cloud applications and business software, catering to diverse business needs.
9. Intel Corporation: Empowering Computing with Semiconductors Intel’s prowess in semiconductor manufacturing crafts the beating heart of countless computing devices through its microprocessors and hardware components.
10. Cisco Systems: Forging Networks and Security in the Digital Age Cisco, a pioneer in networking solutions, fortifies businesses with networking hardware, software, cybersecurity measures, and innovations in IoT technologies.
2 notes
·
View notes
Text
🚀 Professional Database Designer | Expert in ERD & Data Modeling 🚀
Struggling to visualize your database structure? I create clear, efficient Entity-Relationship Diagrams (ERDs) that simplify complex data and improve your system’s performance.
🔹 Tailored ERD designs for your unique business needs 🔹 Support for Oracle, MySQL, SQL Server, PostgreSQL & more 🔹 Scalable and optimized database models 🔹 Detailed documentation & expert consultation included
Let’s turn your data into a powerful asset!
👉 Hire me on PeoplePerHour now: https://www.peopleperhour.com/hourlie/professional-database-designer-erd/524486
DatabaseDesign #ERDDesign #DataModeling #DataArchitecture #DatabaseExpert #SQLDatabase #DataManagement #TechSolutions #PeoplePerHour #FreelancerLife #ITConsulting #BusinessIntelligence #DataDriven #SoftwareDevelopment #CustomDatabase #DataEngineering #DatabaseConsultant #TechFreelancer #DatabaseOptimization #DataVisualization #SystemDesign #CloudDatabase #TechSupport
0 notes
Text
Oracle co-founder and the company’s executive chairman and chief technology officer Larry Ellison is trying to persuade governments to descend deep into AI-powered surveillance dystopia by centralizing the entirety of their national data in a single place.
And when he says everything should go into this “unified” database, Ellison means everything. That includes health-related data, such as diagnostic and genomic information, electronic health records, DNA, data on agriculture, climate, utility infrastructure…
Once in there, it would be used to train AI models, such as those developed by Oracle – Ellison shared with former UK Prime Minister Tony Blair during a panel at the World Governments Summit in Dubai.
3 notes
·
View notes