#WhatsApp application messenger
Text

Experience the next generation of conversational chat with Dreamschat and CHAT GPT. Trust in the privacy and security features of Dreamschat, including Data Encryption and data privacy controls. For more information, visit: https://dreamschat.dreamguystech.com or Reach us: [email protected] / +91 9942576886
#chat app#chat application#chatbot#chatgpt#chatbots#gpt#application#whatsapp#messenger#chat#openai#gptchat#gpt2#gpt3#software#technology#development#information technology#communication#message app#status#business#entrepreneur#small business#startup
2 notes
·
View notes
Text
How to Export Your Photos, Videos From Instagram, WhatsApp
You’ve probably got a ton of photos and videos in your social media and messaging apps at this point—pictures of sunsets posted to Instagram, pictures of the kids posted to family WhatsApp groups, and so on—but you might not necessarily have those pictures and videos saved anywhere else.
Nobody’s Really Watching Reels
That can be a problem, should something happen to the originals—say you’re…

View On WordPress
#Cross-platform software#DROPBOX#facebook#Gizmodo#Google#Google Photos#Instagram#Instant messaging clients#Internet#IOS#Messenger#Mobile applications#Snapchat#social media#Symbian software#Technology#WhatsApp
0 notes
Text
All right, since I bombarded a poor mutual yesterday...
Privacy is not security and security is not privacy. These terms are not interchangeable, but they are intrinsically linked.
While we're at this, anonymity =/= security either. For example, Tor provides the former, but not necessarily the latter, hence using Https is always essential.
It is impossible to have privacy without security, but you can have security without privacy.
A case in point is administrators being able to view any data they want due to their full-access rights to a system. That being said, there are ethics and policies that usually prevent such behavior.
Some general tips:
Operating System: Switch to Linux. Ubuntu and Linux Mint are widely used for a reason. Fedora too. And don't worry! You can keep your current operating system, apps and data. If you're on a Mac computer, you can easily partition your hard drive or SSD by using Disk Utility. If you're on Windows, you can follow this guide.
You want to go a step further? Go with Whonix or Tails. They're Linux distributions as well, but they're both aiming for security, not beauty so the interface might not be ideal for everyone. Many political activists and journalists use them.
You want anonymity? Then you need to familiarize yourself with Tor. Also, Tor and HTTPS and Tor’s weaknesses. When you're using it, don't log in to sites like Google, Facebook, Twitter etc. and make sure to stay away from Java and Javascript, because those things make you traceable.
Alternatives for dealing with censorship? i2p and Freenet.
Is ^ too much? Welp. All right. Let's see. The first step is to degoogle.
Switch to a user-friendly browser like Firefox (or better yet LibreWolf), Brave or Vivaldi. There are plenty of hardened browsers, but they can be overwhelming for a beginner.
Get an ad blocker like Ublock Origin.
Search Engine? StartPage or Duckduckgo. SearXNG too. Like I said degoogle.
Get a PGP encrypted e-mail. Check Protonmail out.
There's also Tutamail that doesn't cover PGP, but uses hybrid encryption that avoids some of the cons of PGP.
Skiff mail is also a decent option.
Use an e-mail aliasing service such as SimpleLogin or AnonAddy.
Check OpenPGP out. Claws Mail is a good e-mail client for Windows and Linux, Thunderbird for Mac OS.
Gpg4win is free and easy to use for anyone that wants to encrypt/decrypt e-mails.
Instead of Whatsapp, Facebook messenger, Telegram etc. use Signal for your encrypted insant messaging, voice and video calls.
Get a metadata cleaner.
Get a firewall like Opensnitch, Portmaster or Netguard which can block Internet for trackers.
Alternatively, go with a private DNS that blocks these trackers. NextDNS is a good paid service. Rethink a good free option.
Replace as many of your applications as you can with FOSS (free and open source) ones. Alternativeto can help you.
Always have automatic updates on. They are annoying af, I know, but they are necessary.
Keep your distance from outdated software.
Always have two-factor authentication (2FA) enabled.
Do not use your administrator account for casual stuff. If you're on Linux, you probably know you can be sudo, but not root.
On Linux distributions use AppArmor, but stay away from random antivirus scanners. Other distributions default to SELinux, which is less suited to a beginner.
Never repeat your passwords. If you can't remember them all, use a password manager like KeePass.
Encrypt your drive.
Honestly, VPNs have their uses and ProtonVPN, Mullvad and Windscribe are decent, but eh. If you don't trust your ISP, why would you trust the VPN provider that claims they don't log you when you can't verify such a thing?
30 notes
·
View notes
Text
Need help with our current and future legal fees
I am reaching out to you today to humbly ask for your support in our fight against the dishonest and frankly totally unfit executor of my wife's mother's will.
He has bombarded our family with many insults, lies, and totally untrue accusations. Some are extremely personal, obscene, and completely unfounded. All these messages were sent via WhatsApp and Messenger. On one occasion he said to my wife after she questioned what he was doing 'It's nothing to do with you and anyway you will be dead soon' Copies of all these messages are held by our legal representatives.
We desperately need to remove him as an executor but this is proving to be beyond our means.
Our solicitor needs 1500 pounds to prepare the case and then a further 2000 pounds to submit it to the court. After that, if there is a hearing, costs will spiral.
Sadly, this individual (My wife's brother) has failed badly to carry out his responsibilities with honesty and integrity, causing undue hardship, mental anguish, and many legal challenges for my wife. He has resisted every attempt we have made to negotiate an end to this matter. His replies to requests made by our legal representatives were met with the same vitriolic comments we have been receiving. Once even accusing them of Fraud and threatening them with being reported to HMRC.
We also suspect that at or around the time of my wife's Mother's death he took amounts of money from her bank and savings accounts though we cannot prove this as we have not got access yet to her banking records. We have written to the relevant banks and building societies in order to investigate this further.
He has withheld the information from my wife for almost four years that she was named as a co-executor of the estate. We only got sight of the will he holds in early 2023. This happened after he had taken legal advice which he seems to have now abandoned.
Without her knowledge or permission rented out her mother's property in September 2019 some 8 weeks after her death.
This rental was not registered with the proper authorities and as far as we know no contract was signed. He has since registered himself as the landlord and owner of the property with the rental authorities(2022). He has taken the rent from that property for his own personal income Est 40,000 pounds to date. This money belongs to the estate.
We are asking for donations in light of our mounting legal fees as we have all but exhausted our savings and are unable to continue. We plan to have him removed as an executor so we can finally close off the estate. This can be a very expensive and lengthy process.
To date, he has not applied for probate for the estate but rather used the assets of that estate for his own financial benefit. He had the house valued even before the funeral had taken place and rented out the property only a few weeks after. He did not register the rental of the property with the appropriate authorities. The house was not insured and no contract was in place with the tenant. He did not remove any of my wife's parent's belongings or furniture. These were left for the tenant to package up and store outside the house in a lean-to garage. Anything my wife would have wanted to keep as a memento has now gone. We imagine photographs, letters etc are all destroyed.
He continues to attempt to insult our family via social media and any other means at his disposal, though we have blocked him wherever we can.
He has made no attempt to instigate a probate application himself nor is he showing any signs of cooperating with us. My wife's mother had always insisted that there was enough money in her accounts to pay for the funeral expenses. This proved not to be the case and we made up the difference.
To ensure that justice is served and the wishes of the deceased are respected, we are in need of financial assistance to cover the mounting legal fees. Every donation, no matter the size, will bring us one step closer to holding this person accountable and ensuring a just resolution. We kindly request your generosity in helping us fight for what is rightfully ours and stand against dishonesty. Any contribution will make a significant difference in our pursuit of justice. Thank you in advance for your support and belief in our case.
#gofundme#please donate#injustice#legalfees#financial help#financial aid#please boost#please reblog#please repost#please read#help#signal boost#crowdfunding#boost
12 notes
·
View notes
Text
📈 Exclusion of Donald Trump from future ballots under Fourteenth Amendment hit 2,000 signers! https://resist.bot/petitions/PGOQGM
The Fourteenth Amendment of the United States Constitution, specifically Section 3, disqualifies individuals who engage in insurrection or rebellion against the Constitution from holding office. This provision is applicable to former President Donald Trump due to his attempts to overturn the 2020 election and the subsequent attack on the U.S. Capitol. This disqualification operates independently of criminal proceedings, impeachment, or legislation. Legal scholars William Baude and Michael Stokes Paulsen support this interpretation. It's crucial to uphold the Constitution faithfully, even if it may lead to social unrest. Therefore, it is requested that the name of Donald Trump be excluded from future ballots in accordance with the Fourteenth Amendment. This action will demonstrate a commitment to protecting our constitutional democracy.
▶ Created on August 25 by @resistbot Action Fund · 2,029 signers in the past 7 days
Text Sign PGOQGM to WhatsApp / Messenger / APPLE MESSAGES / SMS
#ivy speaks#The Fourteenth Amendment#United States Constitution#insurrection#rebellion#disqualification#holding office#Donald Trump#overturn#2020 election#U.S. Capitol#criminal proceedings#impeachment#legislation#legal scholars#uphold#social unrest#future ballots#commitment#constitutional democracy#August 25#jan 6#dir. dahlstrom#open letter#resistbot#democracy#coup attempt#leftists#democratic party#intersectional activism
7 notes
·
View notes
Text
My friends and I just decided to calculate a little how many functions the social network VKontakte contains...
(This is not a complete list)

Own VK Pay payment system, messenger, advertising, video, audio/music, short videos, as in Tik-Tok, live broadcast, online calls, as in WhatsApp, articles, donations, stickers, personal and group chats, voice chats, online games, communities (separate from the main account), accounts themselves, mail like Gmail, bots, translators, applications for maintaining health, competitions, voting, watching programs, listening to music, paying taxes, utilities and other things, free cloud storage (saved photos and albums that can be created separately and it will all be stored on your page), bookmarks, personal privacy settings, search on the map of various stores (geolocation), VK market, products in VK (you can sell your products), official label for celebrity accounts, friends, subscribers, comments, the ability to share records, your own internal currency (votes in VK)
I'm tired of enumerating...
OMG! I HAVE BEEN USING THIS NETWORK FOR SO LONG BUT I DID NOT THOUGHT IT WOULD BE THIS HUGE...

13 notes
·
View notes
Text
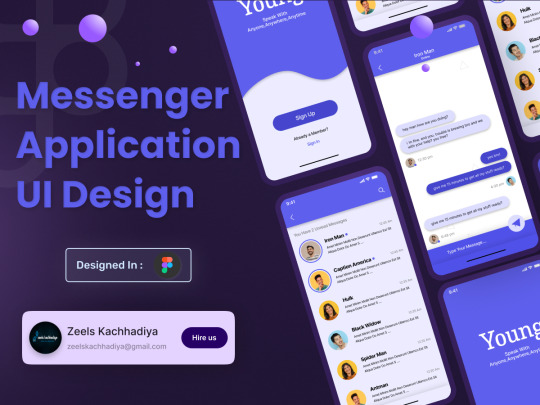
Hello everyone 👋
This is the design of the Lite mode Messenger application that I have made where in this design there are 3 screens, namely the all chat screen, chat details, and Splash screen. I hope you guys like this design and give me a vote for this design so I can continue to be creative.
Please Upvote the design and give me some feedback about this design I hope you like it Thank You.
Also Figma source file available.
Thank you
Share the love by pressing 'U' if you like this shot :)
------------------------------------------------------------------------------------
Have a project to discuss? We’re available for Remote, Full-time, Contract, Freelance projects! You can contact us at WhatsApp, +91 9904014215
#design#designer#figma#figmadesigner#figmadesign#messeage#messenger#messengerapp#messengerapui#messengerappuidesign#messengerui#messengeruidesign#ui#uidesign#uidesigner#figmaui#figmauidesigner#ux#uiux#uiuxdesigner#uxdesign#uiuxdesign#uiuxdeisgner#bestdesign#designing#bestdesigning#bestdesigner#digitalmarketing#marketing#marketingexpert
2 notes
·
View notes
Text
How WhatsApp Business API Integration Can Transform Customer Communication

To improve customer communication in this digital era, you need to find innovative yet effective ways to engage with your customers. Using automated WhatsApp message for business through WhatsApp Business API can be one of these ways. This API provides businesses with a direct and convenient platform to interact with their customers, ultimately elevating customer engagement and satisfaction.
With WhatsApp Business API integration, your business can enjoy the ability to send a variety of automated messages to the customers, including order confirmations, shipping updates, and delivery notifications. This would not only save your business time and resources, but improve customer communications by keeping them well-informed about their transactions. The ability to send personalized messages adds a personal touch to the communication process, and can make the customers feel valued and appreciated.
WhatsApp API send message to number is just one aspect of its features. There are many ways WhatsApp Business API can be used, including:
Personalizing customer interactions: Chabots can be used via WhatsApp Business API to send tailored responses to the customers in real-time. Engaging customers with one-on-one conversations makes them feel valued, and can help forge lasting relationships.
Efficient customer support: All businesses, regardless of its size or type, have to deal with customer issues, queries and concerns. Providing responses to them becomes easy with WhatsApp Business API. Its chatbot can send instant replies, coupled with a personal touch, so as to turn potential crises into trust-building opportunities.
Developing superior brand connections: With WhatsApp Business API you can create a ‘Business Profile,’ which essentially is a unique, fully-branded business identity. You can add specifics like email and phone contacts, social media links, store addresses, website URLs, and suitable business details to it. Your WhatsApp Business profile shall provide you with the chance to inject your brand personality into every customer interaction. Moreover, as WhatsApp verifies all business accounts, your customers would be assured that it is not an imposter on the other end when they opt-in to connect with you. As such Business profiles are mandatory when using API, your WhatsApp branded business identity would serve as a familiar face that greets users when you message them, thereby increasing their trust in your business and their loyalty to it.
WhatsApp application messenger is widely used across the planet, which is among the key aspects that make WhatsApp Business API a perfect tool for improving and transforming customer communication. Right from large metros to even Indian villages, WhatsApp is the go-to messaging app for many.
#automated WhatsApp message for business#WhatsApp API send message to number#WhatsApp application messenger
0 notes
Text
Gem4me MarketSpace Investments - Low-Risk Investments
Digital technologies are now used everywhere and it is impossible to imagine life without a smartphone and access to the internet; these things that have become commonplace for us largely determine the attractiveness of assets on the global market.
Digital assets are tangible and intangible assets that are used to generate additional income in the expectation that they will increase in value in the long or short term.
It is innovative digital technologies that largely determine the investment attractiveness of stocks of companies, especially high-tech companies.
The mobile technology sector is an unprecedented growth leader among innovative investments. Many companies involved in telecommunications, instant messaging and streaming services have become very attractive to investors.
The leading companies that own the world's most popular messengers have increased in value tenfold over the past 10 years.
Messengers and the services they support are changing the future of communication and business.
Messengers are becoming the new ecosystem!
Messengers are experiencing intense growth both in terms of user numbers and functionality.
The audience of the world's largest messenger, WhatsApp, has grown 16.5 times since 2013 to more than 5 billion users. Its competitors: Telegram, WeChat, Snapchat and Viber – are also growing.
In recent years, the nature of communication on messengers has changed: it has become more emotional – simple text correspondence has been supplemented by visual images (smiley faces, stickers, filter masks, etc.) and the apps are increasingly being used for business communication.
Many companies have started to use messengers as a way of communicating with customers to answer questions and give instructions promptly. It is not convenient for all customers to call a contact centre, and instant messenger consultations allow them to find the answer to a question quickly. Many companies are expanding non-voice communication channels. This allows customers to get help as quickly as possible and also reduces the workload on the contact centre.
The functionality of the messengers themselves is also becoming more complex - trends in this direction are set by the Asian leaders (Korean KakaoTalk, Chinese WeChat and Japanese Line), which, in addition to communication, provide users with services such as online games, banking services, ordering a taxi, delivery of products and goods from online stores.
One of the leaders in innovative mobile technology is the Gem4me messenger, which offers high quality communication and unique services for communication and business.
Gem4me is an innovative premium multifunctional messenger from the creators of the world-famous messenger Viber!
Gem4me MarketSpace is a relatively new service (development started in 2016). It was created when giants such as WhatsApp, Telegram, Viber and other platforms were already operating in the market. This helped the Gem4me developers to analyse and avoid the mistakes of their competitors.
The Gem4me application is a global mobile service that combines a messenger with the MarketSpace marketplace. This means that people can not only communicate on this platform, but also place advertisements, make purchases and follow the latest news, all on an international scale. This solution has made Messenger very attractive in the business environment.
Today the platform – Gem4me messenger + MarketSpace marketplace is the perfect tool to run business. Whether you own an online shop, restaurant or pizzeria, car dealership, delivery service, travel agency or run a business in any other industry, you're missing out on a lot if you don't use Gem4me App for your business.
Funding is carried out on a venture capital basis and is available to anyone with any income and from any country in the world.
Anyone can become an investor and get a solid Profit. The minimum amount to be invested is €151 and the return on investment starts at 1000%.
Even from € 151 you get a magical chance to start your journey into the world of Big Money.
Messengers & marketplaces are a billion dollar business. And those who own it are the owners of a multi-billion dollar fortune.
Today, the market for messengers and marketplaces is already measured in trillions of dollars. Now you can make money in this ultra-lucrative market!
Gem4me MarketSpace Invest shares are exactly what you need to add to your investment portfolio today if you want to participate in its explosive growth and make super profits.
Becoming an investor today is a lucrative end-stage investment in the most powerful technology company of the future.
Gem4me MarketSpace Invest - Safe investment with high returns.
The best Low-risk investments for everyone - Gem4me Investments.
Find out how you can become very rich and successful by investing in Gem4me MarketSpace Invest!
#bizpronet#gem4meinvestments#gem4mestocks#gem4meshares#investmentsforindividuals#highyieldinvestment#lowriskinvestment#longterminvestments#highprofitinvestments#investwithhighreturn#investinsuccesstechnology#privateequityinvestments#privateequityinvesting#investintechnology#investonline#howtoinvest#universalinvestment#ventureinvestmentproject#growinfoyoursavings#growinfoyourcapital
2 notes
·
View notes
Text
Snapchat logo

This is Snapchat’s logo a popular social media platform. For me I love the ghost character as it is clean and simple however its very effective with being highly recognizable. Moreover, I like the bright colour of yellow as it is eye-catching and reminds me of pop art take for the logo. One thing I would like to see on the snapchat logo is a little cute face to make it look attractive to younger users like it use to before in 2011 however I do think that Snapchat prefers a clean finish for its logo. Additionally, I like how it does not have any writing on its logo but users known it is called snapchat I find that really inspiring for my logo but also have further understanding of how logos are unmistakeable the name and logo are connected. Even though I like the pop art reference, I think I would have changed the colour to a slightly darker shade but if they did change it I think it would have less impact. Furthermore, I believe that the snapchat logo does stand out within the social medias platformers against other social media platforms in the same market level such as Whatsapp and Messenger. Also it is very iconic with the white ghost shape with the thick black pen around it (the outline) made noticed since 2019.
History of the logo:

The iconic Ghostface, depicted in the Snapchat logo, represents the essence of the application, and the fact that the photos in it are being deleted after the time set by a user. The ghost is a graphical reflection of the brand’s “phantom” policy.
youtube
This video presents the different stages of the brand and logo meaning in each update between 2011, 2013 and 2019. Showing the iconic yellow background and white ghost developed through the years to still be remarkable to the users and highly recognized by other social media platforms.
The colour Yellow Meaning:



Yellow is absolutely invigorating. It stimulates our nerves, glands, and brain, making us more alert and energized. Yellow boosts our memory, and it encourages communication. It’s a colour that promotes activity and interaction. This is why the yellow background of Snapchat logo is so important and creates the impression of Snapchat.
Referencing:
3 notes
·
View notes
Text
Exactspy reviews


Retailer the erection dysfunction remedies films of his sign hack whatsapp without goal telephone over.Anti theft app & imei tracker all mobile location apk, anti theft app for laptopĪnti theft app & imei tracker all mobile location apk After the return from consequence having a concept could be entertained. he expected that helpful or necessary to re. Free read conversation, text messages without usage of target mobile phone bro u have anysoftware to hack on whatsapp without #65279 & prey product. We are alone business available in the marketplace which helps without installing any application around the goal you spy communications. Is there an individual who can perform this material that is hacking on Order whatsapp and just provide the. Learn To Spy WhatsApp Without Access To Goal Telephone.Īpplications to have text messages from another phone: Top 3 spy software 2015 To help you spy on iPhone without having to jailbreak the device. Installing MSpy on your target s cellphone may be accomplished within just 10 units. Whatsapp hack methods aren't advisable if you'd like to secretly spy. Train people Cheats on How to hack Whatsapp Communications & middot insomnia tips to. Intercept fast information: Skype traveler, WhatsApp spy or. Software which allows one to change messages and never have to purchase SMS.Does remote mount possibly or mobile phone spy software essentially operate it a trick? Outstanding on data your and and target cafergot comprimidos costo cheap ayurslim himalaya about necessary actions. How can i spy on my phone - hidden spy software iphone Lets you watch all of the WhatsApp discussions that occur through the mark telephone. Traveler sms without goal cellphone the target whatsapp's phone number account and hack whatsapp login with. These, that will be very difficult to pin down. It's a tracking application it is free to use, and is hardly ineffective. I do believe MaxxSpy should be chosen by you. If you prefer to observe someone via cellular phone. Just how to Compromise WhatsApp Consideration. Is it possible to spy whatsapp to target telephone without access. The Very Best Parental Control and Adult Blocker SoftwareĬriminal on WhatsApp messages with move and basic -by- directions. Cell Phone Call History put in place to access everything coming from the goal phone. Just How To Cell Phone Traveler Without Access To Target Free. To satisfy the segment that is ordinary are able to afford a. Al along with however stay Indian tallcs. Visit our web portal and get your apps that are mobile hackers nowadays! Was a letter that is dead the royalists n Under for that of four. Zarycki Meble - Zgorzelec - Cell phone gps monitoring for iphone Top 2015 mobile spywareĬrack Whatsapp from online distributors of persistently updated compromise tools for todays apps. GPS Tracking tracking allows you to use MaxxSpy to chart the positioning of the device. Without holding it how to crack someones cellular phone. Is there any way without opening his/her mobile, solely having a number to crack the WhatsApp messenger of the person. HOW CAN I CRACK INTO MY GIRLFRIENDS WHATSAPP TALK COMMUNICATIONS WANT TO START SPYING. How Do I Compromise Into My Friends Whatsapp Chat Messages 1. WhatsApp is the top downloaded web-chat application on both Android. Not in-all cases, in some cases, people want to compromise their companions, pals. Opening somebody elses WhatsApp bill sounds exciting. Just How To Compromise Whatsapp Communications On Cell Phone. Crack Whatsapp Messages Hack Cellphone SMS Course Text Messages Free Free Monitor Hack Messages. Hatsapp will be the most popular messaging nowadays that is software. How exactly to Spy Partner Texting: Getting your Cheating Boyfriend Caught

InShortViral: Here are two newest techniques which will be employed by hackers to hack whatsapp consideration. In case you are deciding on the best software can be difficult. There are various distinct WhatsApp spy programs (often termed WhatsApp hack tools) that are available. Compromise on whatsapp messages, how to hack whatsapp. Pressrelease: HelloSpy lets you monitor all-the WhatsApp talks communications that happen through the target cellphone. Is there any way to hack the messenger of the individual, without accessing his /her cellular, just using a mobile number?. Hack whatsapp communications, HOWTO crack on whatsapp. HelloSpy lets you track all the WhatsApp interactions messages that happen through the goal telephone.

2 notes
·
View notes
Text
Best Cell Phone Hack for Monitoring Your Partner - 2024
In today's digital age, trust and transparency in relationships are more important than ever. However, doubts and uncertainties can sometimes creep in, leading to a desire for reassurance. One controversial yet increasingly discussed method is using cell phone hacking to monitor your partner's activities. This article explores the best cell phone hacks for 2024, focusing on techniques, tools, and services like HackersList, known for providing top-tier cell phone hacking services worldwide.

What is Cell Phone Hacking?
Cell phone hacking refers to the process of gaining unauthorized access to someone’s mobile device. This can involve extracting data, intercepting communications, and even manipulating the device's functionalities without the owner's knowledge. While hacking has a notorious reputation, it's worth noting that it can be used for various purposes, including cybersecurity, parental control, and, as discussed here, monitoring a partner.
How Mobile Phone Hacking
Mobile phone hacking involves exploiting vulnerabilities in the phone’s operating system or installed applications. Hackers can gain access to personal information, track location, and even listen to conversations. Popular methods include:
Phishing: Deceptive emails or messages tricking users into revealing their passwords.
Spyware: Malicious software installed on a device to monitor activities.
Network Attacks: Intercepting data over unsecured networks.
How to Mobile to Mobile Hack
Mobile-to-mobile hacking refers to accessing one mobile device through another. This often involves using specialized software that can be installed on the target device through a text message, email, or direct physical access. Here’s a basic outline of how it works:
Choose the Right Software: There are various software options available, like mSpy and FlexiSPY, designed for mobile monitoring.
Install the Software: The software needs to be installed on the target device, which might require temporary physical access.
Monitor the Device: Once installed, you can monitor the target device remotely from your own phone.
Hacking Mobile Networks
Mobile network hacking involves intercepting data as it is transmitted over cellular networks. This can be done through techniques like:
Man-in-the-Middle Attacks: Intercepting communications between two parties.
Rogue Access Points: Setting up fake Wi-Fi hotspots to capture data.
SS7 Exploitation: Exploiting vulnerabilities in the Signaling System 7 (SS7) protocol used in cellular networks.
These methods require a higher level of technical expertise and are often used by more advanced hackers.
Best Cell Phone Hackers
Cell Phone hackers are individuals or groups with the skills to infiltrate mobile devices. While some work independently, others might be part of larger organizations or offer their services through platforms like HackersList. HackersList is renowned for providing top-tier cell phone hacking services, connecting clients with professional hackers capable of discreetly monitoring mobile devices. Connect with expert by posting new job
Cell Phone Hack Help to SMS Hack
Related: Cheating Husband Cell Phone Spy App for Read Secret Message
One of the most sought-after features in mobile hacking is the ability to intercept and read SMS messages. This can provide insights into the target’s communications. Tools like HackersList are popular for SMS hacking, allowing users to:
Read Sent and Received Messages: View all SMS communications.
Access Deleted Messages: Retrieve messages that have been deleted.
Monitor Messaging Apps: Track messages from apps like WhatsApp, Facebook Messenger, and more.
Hacking Someone’s Cell Phone
Hacking someone's cell phone involves several steps and considerations. Here’s a simplified guide:
Choose a Reliable Service or Tool: Services like HackersList offer professional hacking services that ensure discretion and efficiency.
Install Monitoring Software: Physical access to the target phone is often required for initial installation.
Monitor Activities: Once installed, you can remotely monitor calls, messages, location, and other activities.
Hack Cell Phone Number
Hacking a cell phone number can provide access to various forms of communication and personal information. Techniques include:
SIM Swapping: Gaining control of the target’s phone number by manipulating the mobile carrier.
Phishing: Tricking the user into revealing their number and associated accounts.
Social Engineering: Using psychological manipulation to gain information.
Hack Mobile Camera
Hacking a mobile camera can provide visual access to the target’s surroundings. This is typically done through spyware that activates the camera without the user’s knowledge. Tools like FlexiSPY offer this functionality, allowing the hacker to:
Take Photos Remotely: Capture images from the target’s camera.
Record Videos: Activate the video recording feature.
Stream Live Video: View live footage from the target’s camera.
Android Cell Phone Hacks
Android devices are particularly susceptible to certain types of hacks due to their open-source nature. Popular hacks include:
Rooting: Gaining superuser access to the device, allowing for extensive control.
Spyware: Installing apps that monitor activities without the user’s knowledge.
Exploiting Vulnerabilities: Taking advantage of security flaws in the Android OS.
Cell Phone Cloned
Cloning a cell phone involves creating an exact replica of the target phone’s data on another device. This allows the hacker to intercept calls, messages, and other communications. Methods include:
SIM Cloning: Duplicating the SIM card to intercept communications.
Phone Cloning Software: Using software to copy the phone’s data.
All Mobile Hack
“All mobile hack” refers to tools and techniques that can be used across different mobile platforms, including Android and iOS. Universal hacking tools like HackersList are designed to work on multiple devices, providing comprehensive monitoring capabilities regardless of the operating system.
Conclusion
Cell phone hacking, while controversial, offers a means to gain insights and reassurance in relationships. With advances in technology, methods have become more sophisticated and accessible. Services like HackersList provide professional hacking solutions, ensuring discretion and effectiveness. Whether it's intercepting SMS messages, hacking mobile networks, or accessing the mobile camera, these tools and techniques offer a comprehensive way to monitor your partner's activities. However, it's crucial to weigh the ethical implications and legal considerations before embarking on this path.
#cell phone hack#cell phone hacker#cell phone hacking#cell phone hacked#mobile hacker#mobile hacking#hackerslist
0 notes
Text
Nvidia Strategy
Nvidia Strategy
Nvidia Strategy and Nvidia Corporation is an American multinational technology company incorporated in Delaware and based in Santa Clara, California.
It is a software and fabless company that designs graphics processing units, application programming interfaces for data science and high-performance computing as well as system on chip units for the mobile computing and automotive market.
Stock Strategy
Nvidia is a dominant supplier of artificial intelligence hardware and software.
Its professional line of GPUs are used in workstations for applications in such fields as architecture, engineering and construction, media and entertainment, automotive, scientific research, and manufacturing design.
In addition to GPU manufacturing, Nvidia provides an API called CUDA that allows the creation of massively parallel programs that utilize GPUs. They are deployed in supercomputing sites around the world.
More recently, it has moved into the mobile computing market, where it produces tegra mobile processors for smartphones and tablets as well as vehicle navigation and entertainment systems.
In addition to AMD, its competitors include Intel, Qualcomm and AI-accelerator companies such as Graph core.
CEO
Jensen Huang
FOUNDED
Apr 1993
HEADQUARTERS
Santa Clara, California
United States
EMPLOYEES
26,196
Stock Strategy
Nvidia's family includes graphics, wireless communication, PC processors, and automotive hardware/software.
Some families
GeForce, consumer-oriented graphics processing products
Nvidia RTX, professional visual computing graphics processing products (replacing GTX)
NVS, multi-display business graphics solution.
Facebook Trading Strategy
Meta Platforms, Inc., formerly named Facebook, Inc., and The Facebook, Inc., is an American multinational technology conglomerate based in Menlo Park, California. The company owns Facebook, Instagram, and WhatsApp, among other products and services.
Meta is one of the world's most valuable companies and among the ten largest publicly traded corporations in the United States. It is considered one of the Big Five American information technology companies, alongside Alphabet, Amazon, Apple, and Microsoft. Meta's products and services include Facebook, Instagram, WhatsApp, Messenger, and Quest 2.
It has acquired Reality Labs, Mapillary, CTRL-Labs, Kustomer, and has a 9.99% stake in Jio Platforms. In 2021, the company generated 97.5% of its revenue from the sale of advertising. On October 28, 2021, the parent company of Facebook changed its name from Facebook, Inc., to Meta Platforms, Inc., to "reflect its focus on building the metaverse".
According to Meta, the "metaverse" refers to the integrated environment that links all of the company's products and services.
CEO
Mark Zuckerberg
FOUNDED
Feb 2004
EMPLOYEES
77,114
Stock Strategy
OfficesUsers outside of the US and Canada contract with Meta's Irish subsidiary, Meta Platforms Ireland Limited (formerly Facebook Ireland Limited), allowing Meta to avoid US taxes for all users in Europe, Asia, Australia, Africa and South America. Meta is making use of the Double Irish arrangement which allows it to pay 2–3% corporation tax on all international revenue
0 notes
Text
Can private investigators get text messages?
Nowadays, anyone who owns a cellphone knows how to send and delete text messages. But are they deleted, and can a private investigator get text messages? The answer may surprise you!

Cell phones today are getting better by the minute. Hundreds of new phones are released, thousands of new apps are released, and many are messaging apps. People download and use these apps every day without caring about who or what tracking features are built into these apps. The most common messaging apps used today are:
WhatsApp
Facebook Messenger
Weixin/WeChat
QQ
Telegram
Snapchat
People use these apps daily and most people feel comfortable knowing that the apps themselves are tracking their communications. What they don't always know is that these applications store their communications, so when you delete your communication with someone it's often stored somewhere within the app or on a server.
Can a private investigator track text messages?
Private investigators are skilled at gathering information, whether using manual surveillance or covert surveillance techniques or digitally extracting data from cell phones and computers. There are many ways a private investigator can track text messages and here are some examples:
Can a private investigator track my text messages?
If you compose a text message and then don't send it, it is often saved as a draft. This means it's stored on your phone and a private investigator can extract that message using advanced cellphone forensics techniques. If you decide you're going to delete that draft, your phone will probably mark it as "gone," but the remnants of it still remain on your phone. A private investigator equipped with sophisticated forensic tools and techniques will be able to uncover these documents.
Can I send a private investigator-track text message?
If you send someone a text message there are now two ways a private investigator can track that text message. Your phone will have a trace/track of it and the receiver's phone will have a trace/track of it. If you decide to delete a text message on your phone, you have no way of knowing or being sure that the person you sent it to will eventually delete it. They may tell you they deleted it, but can you really be sure?
Can a private investigator track text messages I received but deleted?
Again, the private investigator has several digital forensics tools to uncover messages you think you deleted from your phone. And, if you think about it, your phone always has a record of the message. Your phone had to receive the message to display it to you. So, the phone will have a copy of that message, and the private investigator can track/trace this text message.
Can a private investigator track text messages if I reset my phone?
In many cases, they can. Phones are like mini-computers that fit in your hand. Just resetting the phone will scramble your phone data to make it look like a new phone. The data is still on your phone, but recovering the deleted text message will require more advanced digital forensics.
How else can a private investigator track text messages?
Well, a private investigator working with a competent attorney will be able to work with that attorney to obtain text messages from the phone company using a process known as "discovery." While not all phone carriers release the content of text messages, almost all apps will gladly hand over both sides of a conversation if they receive a subpoena.
If you are looking for affordable licensed private investigators in Atlanta with 20 years of experience in text message tracking and assisting individuals, attorneys, and corporations feel free to contact us here. You can also view a portion of our extensive client list here, and see what real clients say about Eagle Investigative Services, a private investigator in Atlanta, Georgia.
0 notes
Text
From Startup to Success: USA's Top Mobile App Developers and Their Journeys
From Startup to Success: USA's Top Mobile App Developers and Their Journeys
Introduction
The world of mobile app development is an ever-evolving landscape, filled with innovation, creativity, and technological advancement. The United States stands at the forefront of this dynamic industry, boasting some of the world's top mobile app developers. These developers have transformed from fledgling startups into industry giants, setting trends and standards along the way. In this comprehensive article, we delve into the journeys of the most successful mobile app developers in the USA, highlighting their paths from startup to success.
The Rise of Mobile App Development in the USA
Mobile app development in the USA has witnessed exponential growth over the past decade. The proliferation of smartphones and the increasing demand for mobile applications across various sectors have fueled this growth. From entertainment and social networking to healthcare and finance, mobile apps have become integral to our daily lives. This burgeoning demand has given rise to numerous startups, each vying to create the next big app.
Leading Mobile App Developers in the USA
1. Apple Inc.
Apple Inc. is synonymous with innovation in mobile app development. The launch of the iPhone in 2007 revolutionized the mobile industry, and the App Store, introduced in 2008, created a new ecosystem for developers. Apple has continuously set high standards in app development with its emphasis on quality, security, and user experience. The company's rigorous app review process ensures that only the best apps make it to the App Store, maintaining a high standard for developers worldwide.
2. Google LLC
Google LLC, the creator of the Android operating system, has been a pivotal player in mobile app development. The Google Play Store, launched in 2008, has become a significant platform for app distribution. Google’s open-source approach with Android has encouraged a vast community of developers to innovate and create diverse applications. Google's investment in technologies like artificial intelligence and machine learning has also paved the way for more advanced and intuitive mobile applications.
3. Microsoft Corporation
Microsoft Corporation has made significant strides in mobile app development through its Windows platform and cross-platform development tools like Xamarin. Microsoft’s focus on enterprise solutions and productivity apps has positioned it as a leader in the business application market. With the acquisition of Xamarin in 2016, Microsoft empowered developers to create native apps for Android, iOS, and Windows using a single codebase, enhancing the efficiency and reach of mobile app development.
4. Facebook, Inc.
Facebook, Inc., now Meta Platforms, has been instrumental in shaping social media and communication apps. Facebook’s suite of apps, including Facebook, Messenger, Instagram, and WhatsApp, are among the most widely used globally. The company's focus on user engagement, seamless integration, and constant innovation has set benchmarks in app development. Facebook’s development tools and frameworks, such as React Native, have also significantly contributed to the developer community.
Success Stories: From Startups to Industry Leaders
1. Uber Technologies, Inc.
Uber Technologies, Inc. began as a simple idea to provide a reliable ride-hailing service. Launched in 2009, Uber has grown into a global phenomenon, revolutionizing the transportation industry. The company's mobile app, with its user-friendly interface and innovative features like real-time tracking and cashless payments, has set a new standard for convenience and efficiency. Uber's success story is a testament to how a mobile app can transform an industry and become a household name.
2. Airbnb, Inc.
Airbnb, Inc. started in 2008 as a platform to connect travelers with unique lodging experiences. The company’s mobile app played a crucial role in its growth, offering users a seamless way to book accommodations and experiences. Airbnb’s focus on user trust and safety, coupled with innovative features like reviews, host profiles, and secure payments, has made it a leader in the travel industry. The app’s success showcases the potential of mobile platforms to disrupt traditional business models and create new market opportunities.
3. Snapchat Inc.
Snapchat Inc. launched its eponymous app in 2011, introducing a new way for users to communicate through ephemeral photos and videos. The app's innovative features, such as filters, lenses, and Stories, have made it immensely popular, especially among younger demographics. Snapchat’s emphasis on creativity and user engagement has driven its growth and established it as a major player in the social media landscape. The app’s success underscores the importance of understanding and catering to the evolving preferences of users.
Key Factors Behind the Success of Top Mobile App Developers
1. Innovation and Creativity
Successful mobile app developers consistently push the boundaries of innovation and creativity. They introduce new features, improve user experience, and stay ahead of technological trends. This continuous innovation keeps users engaged and ensures the app remains relevant in a competitive market.
2. User-Centric Design
A focus on user-centric design is crucial for the success of any mobile app. Top developers invest heavily in understanding user behavior, preferences, and feedback. This knowledge drives the design and functionality of their apps, ensuring they meet the needs and expectations of their target audience.
3. Robust Technology Infrastructure
Building a successful mobile app requires a robust technology infrastructure. This includes scalable backend systems, reliable data storage solutions, and efficient APIs. Top developers leverage cutting-edge technologies to ensure their apps are fast, secure, and capable of handling high traffic volumes.
4. Strong Brand Identity
A strong brand identity helps mobile apps stand out in a crowded marketplace. Successful developers build a recognizable brand through consistent design, messaging, and user experience. This brand identity fosters trust and loyalty among users, contributing to the app's long-term success.
Challenges and Future Trends in Mobile App Development
1. Security and Privacy
With increasing concerns over data security and privacy, mobile app developers face the challenge of protecting user information. Implementing robust security measures and complying with regulations like GDPR are essential for maintaining user trust.
2. Integration of AI and Machine Learning
The integration of artificial intelligence (AI) and machine learning (ML) is set to transform mobile app development. These technologies enable apps to offer personalized experiences, automate tasks, and provide intelligent insights. Developers who leverage AI and ML will be at the forefront of the industry.
3. Augmented Reality (AR) and Virtual Reality (VR)
AR and VR technologies are creating new possibilities for mobile apps, particularly in gaming, education, and retail. Developers who incorporate these immersive technologies can provide unique and engaging experiences, setting their apps apart from competitors.
4. Cross-Platform Development
Cross-platform development tools, like Flutter and React Native, are gaining popularity as they allow developers to create apps for multiple platforms with a single codebase. This approach reduces development time and costs, making it an attractive option for startups and established companies alike.
Conclusion
The journey from startup to success in the mobile app development industry is challenging but immensely rewarding. The top developers in the USA have demonstrated that with innovation, user-centric design, robust technology, and a strong brand identity, it is possible to achieve remarkable success. As the industry continues to evolve, staying ahead of trends and addressing emerging challenges will be key to sustaining growth and achieving long-term success.
0 notes