#anonymous web browser
Explore tagged Tumblr posts
Note
cluster B culture is getting an email from quora about a thread called "cluster b unmasked" and already knowing it's going to be full of ableist crap and questioning why you got an account in the first place
.
#cluster b culture is#cluster b#npd#aspd#bpd#hpd#Mod Reef#anonymous#REAL#i got it originally because i was dealing with (what i now know were) delusions but i couldn't tell if they were delusions or dissociation#and google had 0 fucking clue what the hell i was trying to describe#like. seriously. try being a young teenager trying to describe a delusion without knowing it was a delusion but being 90% sure it wasn't--#--dissociation instead#and on top of that. trying to describe it not to a human being but to a web browser's search algorithm#AND ON TOP OF THAT. trying to describe the specific delusion and not the general thing you were experiencing#anyways. nobody was helpful in the slightest lmao#and then years later i'm seeing cluster B shit from quora and just seeing the most vile things said about pwNPD#and seeing blatant misinformation about ASPD. from people with ASPD. shit like ''if you feel fear at all then you can't have ASPD''#so yeah i turned off all email notifications from quora. good riddance to be quite honest
93 notes
·
View notes
Note
I was pissed at RT for removing things from youtube to put back on their shitty shite, but then I tried to go "archive" some videos from their site and they seem to have spent more time just hiding the sources of their videos so you can't dl them than they did making an actually functionally working website and now I'm mad as all hell about it

https://pastedownload.com/roosterteeth-video-downloader/
#your suffering is now over#Anonymous#ask box 360#i still use youtube-dl for the rt site because between site updates#something must've changed to cause like. downloader extensions for web browsers to not work anymore#i had a few download sites bookmarked as backup for situations like that :3c
17 notes
·
View notes
Text
Fast Secure Proxy Browser: Browse Anonymously Without Limits

Have you ever tried to access a website, only to be met with a frustrating “This content is not available in your region” message? Or perhaps you've felt uneasy knowing your online activity might be tracked or exposed on public Wi-Fi. In today’s digital landscape, where privacy breaches and content restrictions are increasingly common, it’s no surprise that more users are turning to solutions that offer both security and speed.
That’s where a fast secure proxy browser comes in. It's more than just a digital detour — it’s your shield against surveillance, a bridge to open access, and a tool that puts you back in control of your browsing experience. But what exactly makes a proxy browser both fast and secure? And how can it help you browse anonymously without limits?
In this post, we’ll break down how a fast secure proxy browser works, explore why it matters, and guide you through choosing one that fits your needs. Whether you’re looking to protect your data, bypass geo-blocks, or simply surf without compromise, you’re in the right place. Let’s dive into the tools and tactics that make anonymous browsing not just possible—but effortless.
Understanding Proxy Browsers
Proxy browsers serve as intermediaries between your device and the internet. When you access a website through a proxy browser, your request is rerouted through a remote server. This server masks your IP address, effectively hiding your identity from websites, advertisers, and even government surveillance.
A proxy browser differs from a Virtual Private Network (VPN) in a few key ways. While both hide your IP and offer privacy, VPNs typically encrypt all internet traffic on your device, while proxy browsers work at the application level—usually within the browser itself. This makes proxy browsers lighter and often faster for everyday use.
Why does speed matter? Because privacy tools shouldn't slow you down. A fast proxy browser ensures you're not waiting forever for a webpage to load, all while keeping your identity secure. It also allows seamless streaming, gaming, and general browsing without buffering or lag.
With a secure proxy browser, you no longer need to worry about malicious entities tracking your every move. Your location stays hidden, your data remains encrypted, and your browsing history is safe from third parties.
Key Benefits of a Fast Secure Proxy Browser
Maintain Online Privacy and Hide Your IP
One of the biggest advantages of a fast secure proxy browser is the ability to mask your real IP address. By doing so, your digital footprint is hidden, and your activities can't easily be traced back to you.
Bypass Geo-Restrictions and Censorship
Tired of running into blocked websites? Proxy browsers help you bypass content restrictions imposed by governments, schools, or workplaces. Whether you're accessing streaming services, social media, or news outlets, you can do so freely.
Enjoy Fast Speeds Without Compromising Security
Many users avoid privacy tools due to slow speeds. Fast secure proxy browsers, however, use optimized routing and load-balancing techniques to ensure swift connections, even under heavy traffic.
Protect Data on Public Wi-Fi Networks
Public Wi-Fi is notorious for being a security risk. With a secure proxy browser, you can encrypt your traffic and ensure your data isn’t intercepted by hackers, snoopers, or malicious hotspots.
Essential Features to Look for in a Proxy Browser
End-to-End Encryption Capabilities
Ensure that the proxy browser you choose offers end-to-end encryption. This prevents any third party, including your ISP, from reading your data.
Zero-Log and No Tracking Policies
A true privacy-focused proxy browser won’t log your activity. Check for providers that openly commit to zero-log policies.
Multiple Server Locations for Flexibility
The more server locations available, the easier it is to access global content. It also allows you to switch locations if one is underperforming.
One-Click Access and User-Friendly Interface
Ease of use matters. Look for browsers that require no technical expertise and offer clean, intuitive dashboards for users of all levels.
Use Cases: Who Needs a Fast Secure Proxy Browser?
Journalists and Researchers in Restricted Regions
For those working in countries with limited internet freedom, proxy browsers offer a vital tool for uncensored information gathering.
Everyday Users Who Value Privacy
Even if you're not a whistleblower or journalist, your data matters. Proxy browsers help safeguard everyday browsing activities.
Students Accessing Blocked Educational Resources
Educational institutions sometimes block certain sites. Proxy browsers can help students bypass these restrictions to access learning materials.
Travelers Looking to Avoid Regional Content Blocks
Traveling abroad and can’t access your favorite streaming service? A proxy browser can make it seem like you're back home, unblocking content seamlessly.
How to Get Started with a Secure Proxy Browser
Choosing the Right Tool for Your Needs
Not all proxy browsers are created equal. Look for one that balances speed, privacy, and usability based on your unique needs.
Step-by-Step Setup and Configuration
Download the proxy browser from the official website.
Install and launch the application.
Select a server or location you want to browse from.
Enable encryption settings if available.
Start browsing anonymously.
Tips for Maximizing Speed and Performance
Choose servers closer to your actual location.
Avoid peak usage times when servers may be overloaded.
Clear your browser cache regularly.
Common Mistakes to Avoid
Using free proxies with poor security protocols
Forgetting to turn on encryption settings
Overlooking privacy policies and logging practices
Conclusion
In a world where digital privacy is increasingly under threat, a fast secure proxy browser isn't just a luxury—it's a necessity. From hiding your IP address to bypassing global content barriers, it empowers you to browse anonymously, safely, and without limits.
Whether you're a professional navigating sensitive research or a casual user who values their online freedom, the right proxy browser can redefine your web experience. Choose wisely, stay informed, and take control of your digital journey. Your path to a freer, more secure internet starts now.
FAQ’s
1. What makes a proxy browser fast and secure?It combines optimized server infrastructure with encryption protocols and minimal data logging, ensuring high-speed access and strong privacy.
2. Are proxy browsers legal to use?Yes, using a proxy browser is legal in most countries. However, it's important to comply with local laws regarding internet usage.
3. Can a proxy browser replace a VPN?For basic privacy and unblocking content, yes. But for full-device encryption and enhanced security, a VPN may still be preferable.
4. Do proxy browsers work on mobile devices?Many secure proxy browsers are available for Android and iOS, offering similar features as their desktop counterparts.
5. Are free proxy browsers safe? Not always. Many free services log your data or serve ads. It’s better to choose a reputable proxy browser with a transparent privacy policy.
#secure proxy browser#anonymous web browsing#bypass internet restrictions#online privacy tools#fast proxy service
0 notes
Note
I saw your tags on the last post and it has me curious. Do you mind explaining that micro-transactions means and why you don't care for them? I'm genuinely curious.
hello!
so micro-transactions is a business model where users can purchase virtual goods (like tumblr's badges, etc.) with micropayments. normally they're used in free games as a revenue source for developers, but in the case of a social media sites such as tumblr or publishers (i.e. The New York Times, The Washington Post, etc.) - it's charging people for access to content that should be widely available and free to all.
like i don't care for the ads, but i also don't want to feed into the capitalistic ideals of microtransactions and what they mean for the future of our society (including the ethical implications that come along with microtransactions). i'd rather deal with ads than pay a company such as tumblr, meta, x, and even youtube money monthly or yearly to get rid of them. they're annoying but we also have seen corporations like google sell out and allow ads on web browsers, so it's becoming something that in unavoidable.
i'm not judging people who do pay to get rid of ads or for things such as this - it's more of a personal preference. i'd rather my money go to causes that i care about or go into savings and i've just accepted that we will never be free of ads at this point in time.
i hope this answered your question!
#can i ask you a question?#anonymous#but yeah - i don't believe in paying for ad blockers and such#normally i use web browsers that come with ad blockers to help with it and they do a great job#great ones are opera and duckduckgo if you're interested
1 note
·
View note
Text
A Closer Look at the Dark Web
In the vast realm of the internet, where the surface web serves as a bustling marketplace of information and commerce, there exists a hidden, mysterious underworld known as the dark web. This enigmatic space, concealed from traditional search engines, has earned a reputation for harboring both illicit activities and a haven for privacy enthusiasts. In this blog post, we’ll delve into the depths…

View On WordPress
#Cryptocurrency transactions#Cybercrime#Cybersecurity#Dark Web#Dark web myths and realities#Darknet marketplaces#Deep web exploration#Digital shadows#Encrypted communication#Ethical use of technology#Hidden Internet#Illicit online activities#Internet privacy#Internet security#Navigating the dark web#Online anonymity#Privacy online#Silk road#Tor browser#Tor Network
1 note
·
View note
Note
thus, a need to switch to firefox has been established!
I have firefox I just don't use it as much lol
1 note
·
View note
Text
TOR Browser 13
TOR Browser 13.0 został wydany https://linuxiarze.pl/tor-browser-13-0-zostal-wydany/
0 notes
Text
ONİONSİTES - DRAGON+ (2)

Onion sites, also known as.onion sites, are a unique type of website that can only be accessed through the Tor network. The Tor network, short for The Onion Router, provides a layer of anonymity and encryption for users accessing these sites, making them popular for those seeking privacy and security online. Unlike traditional websites that can be accessed through standard web browsers, onion sites list require special software, such as the Tor browser, to navigate. Individuals can create onion versions of regular websites or develop standalone onion sites for specific purposes. The exclusivity and privacy features of onion sites contribute to their appeal for various users, ranging from privacy advocates to individuals navigating the dark web for specific content.
There are several reasons why individuals choose to use onion sites, with privacy and anonymity being at the forefront. Onion sites offer a level of confidentiality that is not typically found on the surface web, making them attractive to individuals seeking to protect their identity and browsing habits. Moreover, best onion sites can provide access to content that may be restricted or censored in certain regions, allowing users to circumvent such limitations and access information freely. The encrypted nature of the Tor network adds an additional layer of security, reducing the risk of surveillance and tracking by third parties, including governments and internet service providers.
Common types of content found on onion sites range from forums and marketplaces to news outlets and secure communication platforms. While exploring onion sites, individuals may come across forums, chat rooms, file-sharing platforms, and other interactive spaces that facilitate communication and information exchange in a secure environment. The anonymity and encryption offered 2024 onion sites contribute to a unique online experience, enabling users to engage with content and communities that may not be easily accessible through conventional web browsers.
1K notes
·
View notes
Text
Sharing is Caring

steddie x reader
summary: Steve and Eddie decide to have an open relationship and despite that, Eddie decides to keep the girl he met in a chat room a secret. Little does he know that Steve is keeping a secret of his own.
cw: brief mention of struggle with sexuality
ladybaggins has requested to chat!
ladybaggins: hi
eddiethebanished69: hi
eddiethebanished69: fan of Bilbo hm?
ladybaggins: of course
ladybaggins: that’s my husband
eddiethebanished69: so that’s my competition?
ladybaggins: we’re not exclusive. Why? Are you flirting with me, Eddie the banished?
eddiethebanished69: what if I am?
ladybaggins: then I would be prompted to ask if that’s you in your pfp
eddiethebanished69: it is
ladybaggins: fuck-
eddiethebanished69: can’t tell if that’s a compliment or insult
ladybaggins: definitely a compliment
eddiethebanished69: good
ladybaggins: are you in a band or something? I see you’re playing a guitar in your pfp
eddiethebanished69: yep
eddiethebanished69: but I won’t share my band name to protect my anonymity if you don’t mind
ladybaggins: of course I don’t mind
ladybaggins: what genre are you categorized as?
eddiethebanished69: heavy metal
ladybaggins: that’s hot
ladybaggins: I mean-that’s hot
ladybaggins: that’s really cool
eddiethebanished69: have a thing for metal bands, hm?
ladybaggins: maybe-
eddiethebanished69: you are already becoming very interesting, Lady Baggins
eddiethebanished69: well, I should go make dinner. Same time tomorrow?
ladybaggins: I wouldn't miss it! Until then, Eddie the banished.
Eddie leans back in his chair at his desk, smiling to himself as Steve enters the office. He doesn't know why, but he's quick to close the tab where he was talking to you. He has nothing to hide, especially since he and Steve recently decided that they wanted to have an open relationship. So he's not cheating on Steve and he definitely doesn't feel ashamed. He just wants to keep this to himself because he shares everything with his boyfriend. This is something he's going to keep between himself and his web browser. And you, of course.
"Hey, honey," Steve says as he drops a kiss to the top of Eddie's head. giving his shoulders a squeeze as he does so. Eddie lets out a hum as this is the one thing that he loves the most that Steve does. It just a sweet gesture that showed Eddie just how much Steve loves him.
"Hey," Eddie turns in his chair, puckering his lips, asking for a kiss and Steve is quick to oblige, resting his hands on the arm rests on the chair while leaning down and capturing Eddie's lips between his two. Once he pulls away, Eddie pats his lap and Steve is quick to sit as Eddie turns to face the desk again, opening up the city building game that Steve loves to watch him play.
This is their favorite activity of the day. No matter how many times they do it, they never get bored. Steve loves the way Eddie's hands rest on his thighs and Eddie loves how Steve will lean his head back on his shoulder. It's the perfect setup.
Afterwards, the two of them head to the kitchen where the Chinese food that Steve had picked up on his way home from work. The table is already set and they sit in their respective chairs, eating is comfortable silence.
Steve is rubbing his foot up and down Eddie’s leg and Eddie takes Steve’s free hand, bringing to his lips for a gentle kiss. Eddie doesn’t know how he got so lucky as to have someone as amazing as Steve, but he’s not going to question it. And he certainly doesn’t take it for granted either. He’s always quick to tell Steve just how much he loves him and how grateful he is to have the man in his life.
It goes both ways. Steve is equally grateful for the man sitting across from him, wondering why he had been so rude to him in high school when he’s nothing but a sweetheart. He sometimes still can’t believe that Eddie gave him a second chance when their paths crossed again when they realized that they were going to the same university.
Eddie always knew he liked men, very secure in his sexuality and Steve thinks that’s one of the many reasons why he disliked Eddie. Because he was always unapologetically himself, always seen going on dates with different men and women around town and Steve envied that.
Steve also was always attracted to men even though he would try to deny it. He just liked that guy’s pants and wanted to know where he got them or wanted to know that other guy’s workout routine so he could get jacked like him.
Steve didn’t fully come to terms with the fact that he was bisexual until his senior year of high school. Everyone was playing spin the bottle and his landed on Evan Thompson from his English class. He always thought the guy was cute and would have even gone as far to say that he had a crush on him. But kissing him was a whole other thing.
Steve went for it anyway since rules were rules and even though it was just a quick peck, up until he kissed Eddie for the first time, that was the best kiss he had ever had.
That night, he went home and couldn’t get Evan or the kiss out of his head, wondering what was wrong with him and why he was thinking about it so much. He didn’t think about guys in that way. He was just confused because he hadn’t kissed anyone in a while.
But after a long conversation with Robin, they both came to the same conclusion. That Steve was bi and that there was nothing wrong with that. And accepting it was like a giant weight had been lifted from his chest. It was like he could finally breathe for the first time.
He tried to date men when he moved out of Hawkins and went to college, but it never seemed to go quite right. He was ready, he knew it, but he just couldn’t quite get comfortable enough to be himself.
That is, until he officially met Eddie towards the end of their freshman year. It was a lame party and the two of them shared a joint out on the back porch of the house.
Eddie was the first person Steve officially came out to other than Robin and besides her, he was the only other person who really saw him. To him, he wasn’t Steve “the hair” Harrington, he was just Steve.
Chemistry built pretty quickly and before either of them could stop it, the two of them were making out, the joint long gone, their hands now tangled in each other’s hair.
And afterwards, Eddie walked Steve back to his apartment and the rest is history. They’ve been together ever since.
After dinner and plenty of kisses, Eddie retires back to his office, wondering if you had messaged him again while he was eating, but there’s no new messages nor a green dot next to your profile pic.
He can’t stop thinking about you and he doesn’t know why. He hasn’t really been attracted to anyone else since he got with Steve, but you’re different and he can’t quite put his finger on it.
He thinks it’s because he’s still got it. He’s able to flirt without being too awkward and you seemed to be into it. He wonders if you’ll message him tomorrow and flirt with him some more.
#stranger things#eddie munson#eddie munson x reader#eddie x y/n#eddie munson x you#eddie munson x fem!reader#eddie munson fluff#steve harrington#steve harrington x reader#steve harrington x you#steve harrington x fem!reader#steve harrington fluff#steddie#steddie x reader#steddie x fem!reader#steddie x y/n#steddie x you#steddie fluff
182 notes
·
View notes
Text
PSA for anyone with an Android phone. Delete your Meta apps (Facebook, Facebook Messenger, Instagram, WhatsApp, Threads). They are spying on you. Much worse than you thought they were. (June 7, 2025)
Gift link to a Washington Post article: https://wapo.st/45hNMeB
Quote from the article:
…apps from Meta and Yandex, a technology company that originated in Russia, circumvented privacy protections in Android devices in ways that allowed their apps to secretly track people as they browsed the web.
That should not have happened. Apps on your phone are walled off from accessing your activity on other apps, including web browser apps like Chrome. Meta and Yandex found work-arounds.
The techniques essentially were akin to malware, or malicious software that is surreptitiously planted on your phone or computer, Dolanjski said.
Google said the behaviors of Meta and Yandex “blatantly violate our security and privacy principles.”
Technical analysis from Ars Technica: https://arstechnica.com/security/2025/06/meta-and-yandex-are-de-anonymizing-android-users-web-browsing-identifiers/
Note: the WaPo article says that so far, there’s no evidence this is happening on iPhones, but that it would be theoretically possible. So you should probably delete your Meta apps on iPhone, too.
50 notes
·
View notes
Note
When will we have a feature (1) to disable GIFs autoplay that works for both web and app, and (2) notification for anonymous ask? Like I've using this proud product of Tumblr that I love only for me to realize that there's no notification that tells me my anonymous asks have been answered. How am I supposed to track dozens of anon asks I sent? :")
Answer: Hello, @iluxurycruisedthatship.
We’ll answer your questions one at a time. The option to disable auto-playing GIFs has been available on mobile for a long time! You can find it in your settings, and then to general settings. From here, you will see media auto-play—click here, and select “Never auto-play.”
To do so, just go to your settings, and then to general settings. From here, you will see media auto-play—click here, and select “Never auto-play.”
1.
2.
3.
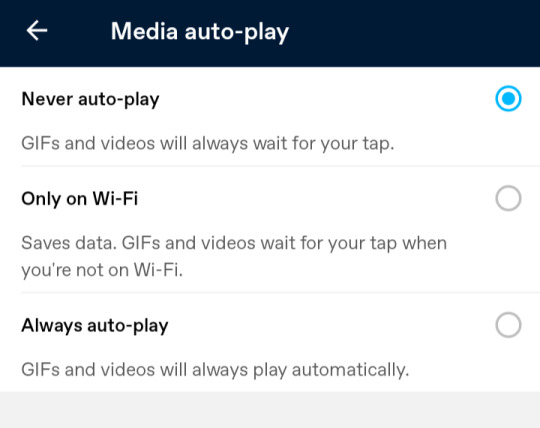
On Web, we respect the browser’s setting, and the location varies wildly based on the browser—as does the functionality. For example, some disable auto-play for all media, and others disable only for videos. In short, on Web, it’s up to the browser, and there are many browsers.
As with many things, notifications for anonymous asks, while a good idea, is not something we have the bandwidth to work on at the moment—even though we agree it’s easy to miss an answered anonymous ask you’ve sent. We would encourage you to follow the blogs you’re asking, and maybe subscribe for notifications for the blog while you’re waiting for the answer.
We hope that helps, and thanks for your question.
36 notes
·
View notes
Text
so you've probably been warned against clicking strange links and to especially avoid revealing your personal information online, even in "private" accounts. But what about a "cute" spin-the-wheel link above a tumblr poll?? (like the post in the following screenshot)
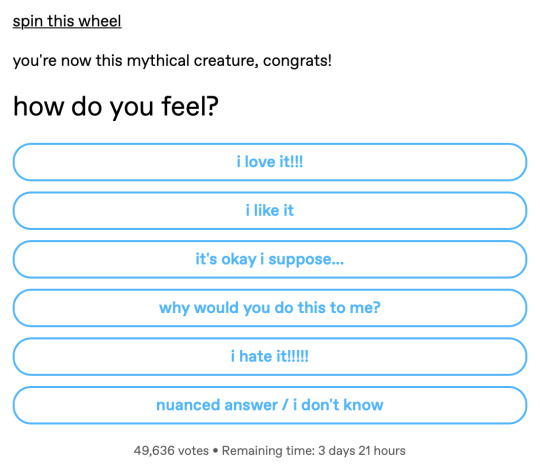
FYI: getting people to click an external link is a great strategy for gathering more details about a mostly anonymous user in a forum or tumblr or wherever. Here's some reasons why: 1. If you shared a unique link in a restricted forum or channel or community or chatroom or public fandom blog or at the end of a fic on ao3, you can be sure only the people of interest could click on it 2. That URL could lead to fucking anything of their choosing. Do they want to do an intensive browser fingerprint or get a log of IP addresses? Do they want to estimate the hardware specs of everyone's machines? Do they want to try loading other things on the page to test for adblockers or other blacklists? (an additional kind of profiling) 3. People LOVE to give away identifying information for the sake of a poll or cute name generator. Here are some questions I've seen recently and what information it can point to: - First anime? (fuzzy proxy for age and country) - First celebrity crush? (fuzzy proxy for age and country) - First album? (fuzzy proxy for age and country) - First name using first letter of last name, Last name using birthday month (do I need to spell this out? last name and birthday month) - What word do you use for [common item]? (region, language, culture, class) - Getting people to talk about astrology (you've all given away your birth month for free, wtf) Another fun fact about "Spin The Wheel" links: they can generate ad revenue for someone! Fun fact about Quizzes: they can help build deeper advertising profiles for linkbait sites like facebook or buzzfeed or the daily mail or tmz Another fun fact: besides the info the Spin The Wheel or Name Generator pages save direct to the server, the page can encode that information back into where the wheel stops or the name it gives you. That makes it easier to gather information because it's recorded 1st on the server (controlled by person fishing to unmask someone) 2nd back in the post notes or in the discord channel or wherever. And we all know how much people want to gab about the Fun poll or survey or quiz and reveal even more information. Another fun fact about Spin the Wheel or Name Generator or Quiz pages: You might be seeing a list of options nobody else saw that only appear for IP addresses from a certain region! And if you post your result (that would be mostly unique) it's an INSTANT indication that the person from [region] is logged in. (same goes for browser fingerprint - which device a certain person has) I remember a line from an article about digital detectives (I think it was feds tracking dark web stuff), it said they wait for YEARS for someone to post or log in just to confirm a person of interest was in a certain place at a certain time. You and I probably don't remember the information we leaked years and years ago in the notes of a post or on a retweet of some idiot, but any people who might want to figure you out probably have a huge spreadsheet with everything recorded. They can and do analyze and annotate it all, and can start to narrow down where you are, how old you are, your interests, hobbies, class background, devices you use etc. You might be thinking: "but I don't worry about federal agents or intelligence agencies, why do I care?" What if tomorrow your post goes viral, truly globally Viral? You can go from tumblr nobody to target for stalkers and/or hate crimes instantly. An even more serious example from this year: What if you've been advocating for years for people that are now scapegoat of the day for the fascists? What if a federal agent is tasked with creating a list of "those people" for surveillance? The less information you have unintentionally posted about yourself the better. A perhaps more personal and private example: what if you had to get away from a city or country or person or persons or family and didn't want them to follow you? People with a grudge will go to great lengths to get back at someone
#privacy online is bigger than direct reveals of the big details like dob or location#gotta be careful#some people make it their life's work to tease out key information without you ever noticing - they're experts#be cautious and wary out there#you don't know who's reading your posts or sharing your dms or charting your ip addresses#my blog#digital privacy
31 notes
·
View notes
Text
Some tips on how to survive a fascist state
From your auntie who has been around this block before.
This was made for people living in the US, but most of this is generally useful.
Assess your level of risk. For example, if you are not a citizen, going to a protest is much higher risk than it is for a citizen. But also recognize that the landscape of who is and is not being targeted is rapidly changing, so keep that in mind.
Get an updated passport. Make this a priority. If you live in a state where they have them, also get an Enhanced ID (not a Real ID, specifically an Enhanced ID) so you have a second way to cross land or sea borders into Canada and Mexico. That way, if authorities take your passport, you have another way out of the country.
Assume that the law is not there to protect you. Many parts of the law that are meant to protect you no longer apply. It's good to know your rights, but also know that the administration is not going to respect them. Just because you aren't doing anything illegal does not mean they won't come after you.
Move your communications, especially political communications, to encrypted messaging services. Use Signal for texts, ProtonMail for email, and Cryptpad as a word processor.
Get a private web browser. DuckDuckGo is a good option. I've also heard good things about Norton's private browser.
If you post political content on social media, you have two options. Make your account private and spend an evening going through your followers to weed out the ones you don't trust. Or, make it anonymous. But if you are picking the latter, know that it is hard to anonymize an account where you previously shared your identity. It's easier to go private if it's linked to your real life self, including through mutuals.
Turn off face ID on your devices. Police can force you to open them with your biometrics, even without a warrant. Additionally, make sure you have strong passwords (that are different for every account!) and keep track of them using a secure password manager.
If you go to protests or otherwise engage in subversive activity, DO NOT POST ABOUT IT ONLINE. Doing so endangers yourself and potentially others. Especially do not post pictures of protests, even if you've blurred the faces, even if you think you scrubbed the metadata. Even better, don't take photos at protests.
If you're exiting and re-entering the US, get a burner phone. I'm serious. Get an iPhone secondhand if you can afford it, but a flip phone will work if you need it to. Don't assume that just deleting anything sensitive off your device will be enough. You may not find it all, and depending on how thoroughly they search your phone, they may be able to see things that were deleted.
Mask up, especially when you're at a protest. In general, it's a good idea to mask since covid and many other viruses are going around. But masking has the added benefit of reducing the amount of biometric information you are making visible. Additionally, facial recognition software relies heavily on eyebrows, so cover them using a beanie or similar item.
Get involved or strengthen your ties with some kind of community. You are going to need others to lean on, whether that's emotionally or politically, in times like these.
22 notes
·
View notes
Text
This is not a rejection of the Internet or your precious digital connections. If anything, you'll find you rediscover your digital agency and how it's been stripped from you! You'll engage in new ways online that put you in the drivers' seat. You'll also find your values start to shift. You'll stop asking if a service can do something for you, and instead ask what it wants from you in return--and whether that's a price worth paying, especially if it's "free."
It's also not a course for those deep into the InfoSec world (Information Security). I won't teach you how to go dark, how to move around the web entirely anonymously. But I will teach you how to take steps toward that direction, so that the path is available to you once these short weeks are up.
To that end, I will recommend systems and services that some people who are deep into infosec won't like. Internet nerds have deep and well informed opinions and controversies erupt all the time. For instance, some people recently are angry at Mozilla for some changes they are making, so they recommend not using Firefox. That's just one example. Some will be upset to find that I am still recommending Firefox -- among many other options.
Why? For one, I want to recommend user-friendly systems of many stripes. I will never tell you to just use one thing: the ball is in your court! I'll also tell you when there are concerns, some of which you may care about and others you won't. I don't think there is (or should be) one system to rule them all. There should be many options. We should use many of them, instead of just one. It's way more freeing to do so.
I also want to get you used to something new: moving. Jumping ship. Right now, we think of moving from one service to another like moving a house you've lived in for fifty years. It's a huge burden, and exhausting to even consider. This forces a kind of lock-in where users never want to leave. Tech companies count on this. Academics hand-wring over this form of lock-in, especially in social media.
But once you get started moving your data around, taking agency in how you work the web, you'll see it's actually much easier than you thought. That way, you might move to a new browser and not like it very much (for whatever reason)-- and instead of going back to Google, you'll try something new. Easy peasy. No moving company involved.
I'll clue you in to a different way to use the web. You'll pay more attention to tech gossip. You'll know if a company is doing something nefarious or making a change. You'll know what to do if so. You'll already have one foot out the door anyway.
That's because Opting Out isn't just about leaving systems we don't like -- it's about opting in to systems and communities we value instead.
31 notes
·
View notes
Text
The song "Timestopper Tactics" from the game 'corru.observer', a 2022 adventure / visual novel developed and published by corru.works. Released as a web browser game.
youtube



-Submission by anonymous
22 notes
·
View notes
Text
So I cooked up a kinda stupid wreck it ralph au in my head. Not at my computer so you only get this doodle and my explanation

I solely came up with this because turbo/king candy and knowsmore share a voice actor. so y'know how in Ralph breaks the internet they establish that once you're programmed into a game you'll regenerate in said game, pretty much implying that turbo is still alive??
Well. What if turbo regenerated after getting frazzled in diet cola mountain, and hid for a very long time until the wifi router was introduced. In this time he taught himself more about coding like he did after the roadblasters incident. He made his way onto the internet and this time crafted a persona as a lil handy dandy web browser. There's still traces of his inflated ego in that persona too. Giving himself posh looking clothes, a place of authority, literally naming himself "knows more" as in "knows more than you" (he wants to keep big noting himself. If he can't be a racer ohhh you better know he must make it known how amazing he is in general)
But like how could you even stop him now if he's literally basically the WIR version of google??? He'd not wanna be suspicious but I bet he'd start planting his stupid face all over the web.
And he'd comment from anonymous accounts on anything talking about turbotime on retro gaming forums. He'd pretend to be someone who grew up going to Mr Litwak's arcade and is one of the few people who actually got to see the elusive king candy character rumoured to be in the game.
Anyway it's almost 1am this is so dumb but I hope you guys got a kick out of reading it xD
44 notes
·
View notes