#authentication bypass
Explore tagged Tumblr posts
Text

The third quality of a sannyasin is a trust in one's own organism. People trust others, the sannyasin trusts his own organism. Body, mind, soul, all are included. If he feels like loving, he flows in love. If he does not feel like loving, he says, "Sorry," but he never pretends. A non-sannyasin goes on pretending. His life is a life lived through masks. He comes home, he hugs the wife, and he does not want to hug her. He says, "I love you," and those words sound so phony because they are not coming from the heart. They are coming from Dale Carnegie. He has been reading "How to Win Friends and Influence People" and that kind of nonsense. And he is full of that nonsense, and he carries it and he practices it. His whole life becomes a false, pseudo life, a parody. And he is never satisfied, naturally; he cannot be, because satisfaction comes only out of authentic living. If you are not feeling loving, you have to say so; there is no need to pretend. If you are feeling angry, you have to say so. You have to be true to your organism, you have to trust your organism. And you will be surprised: the more you trust, the more the organism's wisdom becomes very, very clear to you. Your body has its own wisdom; it carries the wisdom of the centuries in its cells. —Osho
#Osho#authentic#authenticity#phony#anger#angry#wisdom#spirituality#consciousness#awareness#spiritual#conscious#emotion#emotions#feeling#feelings#spiritual bypassing#bypassing#somatic#somatic therapy
8 notes
·
View notes
Text
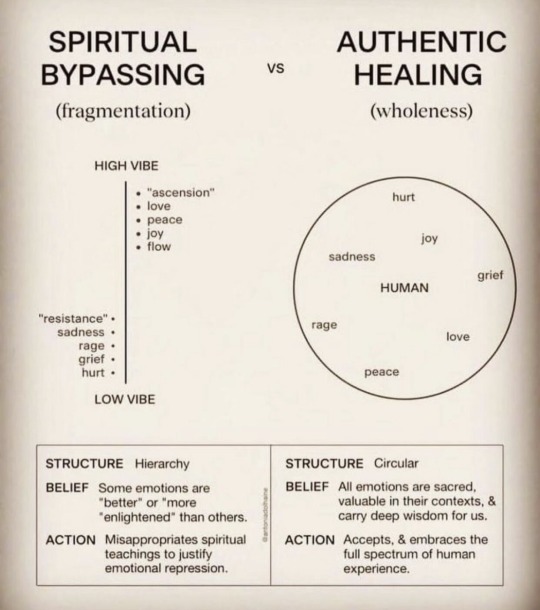
Integrity = to be “integrated” 💘
#bypass#spiritual bypass#integration#integrity#healing#wholeness#authenticity#vulnerability#judgmental#inner work#feel it to heal it#fragmented
12 notes
·
View notes
Text
they say that there's a point where you can have too much security and it impedes the usability of a system—however i'd like to commend online banking platforms for somehow simultaneously having security measures that make them incredibly inconvenient to use every day, whilst also offering fairly low actual security and being not particularly difficult to bypass if you're dedicated enough
#like none of the online banking platforms ive used have let me use an actual password?#nor do they let me set up 2fa with an authenticator app besides their own proprietary banking app#they all seem to send all verification codes by sms with the only way to authenticate otherwise is through their proprietary apps. which i#am not installing.#also perhaps this serves some purpose i dont understand but why do they frequently ask for the nth character of your pin or whatever#instead of asking for the whole pin?#like all the 'password' equivalents seem very easy to bruteforce and the sms verification can be bypassed by someone else just getting a#sim card for your number#and the fact that they never keep you logged in is annoying like i have full disk encryption on all my devices im not worried about someone#using my own device to access my bank account. i dont particularly think theres anyone trying to get into my bank account but if there were#they'd be getting in through their own device not mine... you can keep me logged in on mine...
6 notes
·
View notes
Text
well it happened to me, someone stole my tickets from my Ticketmaster account
I’m so annoyed. The concert is today, I already called Ticketmaster and they said they would call me back. If they don’t call me back in an hour I’m calling them again bc wtf
#change ya passwords change ya emails#tickets are literally getting transferred straight out of people’s accounts#and somehow they are bypassing the two factor authentication bc I didn’t even get an email that my ticket got transferred#I can only think they had my email credentials too
2 notes
·
View notes
Text
Effortless Guest Room Ideas Featuring Mogul Interior Carved Doors
Transforming an ordinary space into a functional and stylish guest room doesn’t require a major renovation. With a little creativity and the right design elements, you can create a welcoming retreat for visitors in no time. One versatile and unexpected tool for this transformation is the carved door. These stunning pieces of art can be repurposed in a variety of ways to bring both beauty and…
#Antique barn doors#Antique French barn door#Antique pantry door#antique rustic armoires#Antique sliding door#Authentic interior exterior door#Bedroom room#Buy custom door#Bypass Barndoors#carved door#carved door panel#closet door#Curved top door#Custom build interior exterior door#Custom built solid wood Door#Custom carved door#Custom size doors#Hand carved authentic doors#Hand carved door#Handcrafted antique French Door#Handcrafted doors#home office doors#indian carved door#Library door#Mandala carved door#Pantry door#Reclaimed wood carved door#Reclaimed wood door wall panel#rustic accent cabinet#rustic armoire
0 notes
Text
Cybercriminals are abusing Google’s infrastructure, creating emails that appear to come from Google in order to persuade people into handing over their Google account credentials. This attack, first flagged by Nick Johnson, the lead developer of the Ethereum Name Service (ENS), a blockchain equivalent of the popular internet naming convention known as the Domain Name System (DNS). Nick received a very official looking security alert about a subpoena allegedly issued to Google by law enforcement to information contained in Nick’s Google account. A URL in the email pointed Nick to a sites.google.com page that looked like an exact copy of the official Google support portal.
As a computer savvy person, Nick spotted that the official site should have been hosted on accounts.google.com and not sites.google.com. The difference is that anyone with a Google account can create a website on sites.google.com. And that is exactly what the cybercriminals did. Attackers increasingly use Google Sites to host phishing pages because the domain appears trustworthy to most users and can bypass many security filters. One of those filters is DKIM (DomainKeys Identified Mail), an email authentication protocol that allows the sending server to attach a digital signature to an email. If the target clicked either “Upload additional documents” or “View case”, they were redirected to an exact copy of the Google sign-in page designed to steal their login credentials. Your Google credentials are coveted prey, because they give access to core Google services like Gmail, Google Drive, Google Photos, Google Calendar, Google Contacts, Google Maps, Google Play, and YouTube, but also any third-party apps and services you have chosen to log in with your Google account. The signs to recognize this scam are the pages hosted at sites.google.com which should have been support.google.com and accounts.google.com and the sender address in the email header. Although it was signed by accounts.google.com, it was emailed by another address. If a person had all these accounts compromised in one go, this could easily lead to identity theft.
How to avoid scams like this
Don’t follow links in unsolicited emails or on unexpected websites.
Carefully look at the email headers when you receive an unexpected mail.
Verify the legitimacy of such emails through another, independent method.
Don’t use your Google account (or Facebook for that matter) to log in at other sites and services. Instead create an account on the service itself.
Technical details Analyzing the URL used in the attack on Nick, (https://sites.google.com[/]u/17918456/d/1W4M_jFajsC8YKeRJn6tt_b1Ja9Puh6_v/edit) where /u/17918456/ is a user or account identifier and /d/1W4M_jFajsC8YKeRJn6tt_b1Ja9Puh6_v/ identifies the exact page, the /edit part stands out like a sore thumb. DKIM-signed messages keep the signature during replays as long as the body remains unchanged. So if a malicious actor gets access to a previously legitimate DKIM-signed email, they can resend that exact message at any time, and it will still pass authentication. So, what the cybercriminals did was: Set up a Gmail account starting with me@ so the visible email would look as if it was addressed to “me.” Register an OAuth app and set the app name to match the phishing link Grant the OAuth app access to their Google account which triggers a legitimate security warning from [email protected] This alert has a valid DKIM signature, with the content of the phishing email embedded in the body as the app name. Forward the message untouched which keeps the DKIM signature valid. Creating the application containing the entire text of the phishing message for its name, and preparing the landing page and fake login site may seem a lot of work. But once the criminals have completed the initial work, the procedure is easy enough to repeat once a page gets reported, which is not easy on sites.google.com. Nick submitted a bug report to Google about this. Google originally closed the report as ‘Working as Intended,’ but later Google got back to him and said it had reconsidered the matter and it will fix the OAuth bug.
11K notes
·
View notes
Text
Sign-in options for Windows: Ditch Password for Enhanced Security
Since I will be publishing a guide on how to setup the revamped Windows Hello available for the Windows 11 Insider Preview Build 27754 (Canary Channel). I will focus on Windows Hello sign-in options which is a more personal and secure way to sign in to your Windows device. Instead of using a password, with Windows Hello you can sign in using facial recognition, fingerprint, or security key or a…
#bypass Windows Hello#Facial Recognition#Fingerprint Authentication#fingerprint authentication bypass#Linux#MacOS#Passwords#PIN#PIN Authentication#Security Key Authentication#Sign-in options in Windows#Windows#Windows 10#Windows 11#Windows Hello#Windows Hello Biometric Database#Windows Hello exploit#Windows Hello Face#Windows Hello for Business#Windows Server#Windows Server 2012#Windows Server 2016#Windows Server 2019
0 notes
Text
Hey everyone it seems there a malicious individual trying to hack the sims cc community again and fill it with malware you need to stay vigilant as a creator and a downloader so
i have some tips for both to stay safe while downloading:
1- sims cc file extension is always .Package never download anything that is .exe
2- do not auto unpack zip files and rar files into your mods folder directly, open each zip or rar individually check the file extensions and drag them to your mods folder one by one
3- the only mods that have a .ts4script extension are ones that affect gameplay or how the game works, understand that if you are downloading cas or bb items you shouldn't have a .ts4script file
4- if you are downloading gameplay mods that do have .ts4script make sure that A) the creator hasn't announced on their pages that its infected B) you are downloading from a link provided by the creator of the mods themselves not something off of google or a link you got sent and make sure dates of upload match dated of announcements
5- if the mod or cc creator has retired and hasn't posted for a while LOOK AT THE DATES OF THE UPLOAD if it has been "updated recently" after the creator has left the community its most likely re-uploaded by a hacker and infected
6- download mod gaurd by Twisted mexi and keep it updated and keep your windows defender or malware detector Program up to date and always running do not disable it
7- make sure everything you download comes from a direct link from the cc creator, in this day and age do not trust link shortners, adfly, linkverse, etc get the universal bypass extension and ublock extension to stay safe but genuinely NEVER CLICK ON THOSE no matter how much the creator reassures you its safe it. is. NOT.
8- this is more of a general saftey precaution but, create a system restore point weekly before you run the game with new mods that way if anything happens you could have a chance to restore your windows to an earlier date before you downloaded anything.
9- BACK UP YOUR SHIT im serious right now either weekly or monthly put your files somewhere safe like a usb a storage card a hard drive even an online cloud if you dont have any of the previous.
10- files you should back up are your media from games and media everything else, any mods, games saves, work files, passwords, saved bookmarks, any documents txt files word files pdfs, links you saved, brushes or actions for Photoshop if you have any, any digital bills or certificates if you have any, and keep a physical list of all programs you have installed and where you installed them from
11- turn on any 2 factor authentication and security measures for any account you have
12- google and firefox have the option to check your paswords and emails against any data leaks USE THIS FEATURE and change any leaked passwords
13- regularly check your logged in sessions to make sure all the logged in devices or computers are yours and log out any that aren't and any old devices or unused sessions do this for every website and app you have an account on if available
14- change your passwords often. I know this is a hassle i know its hard to come up with new passwords but changing your passwords every few months will help you against anything mention previously that wasn't detected.
15- and as a cc creator check your cc and the accounts you host cc on and its uplaod and update dates make sure nothing has been changed without your permission :(
16- generally try not to get swept up in the "i must get it" fever you do not need to "shop" for mods weekly or monthly you do not need to download everything by that one creator you do not need to download new cc everytime you want to make a sim, im guilty of this so i know how hard it is to resist but take a breath and think "do i want this or do i need it" before downloading.
These are prevention methods i cant claim they are 100% will prevent any hacking but its better to be safe than sorry and these do keep you safe so
Brought to you by someone who has had their laptop ruined and data leaked from downloading cc once upon a time
3K notes
·
View notes
Text
A sexy, skinny defeat device for your HP ink cartridge
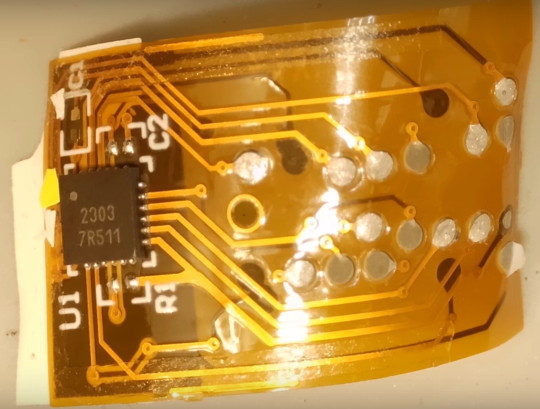
Animals keep evolving into crabs; it's a process called "carcinisation" and it's pretty weird. Crabs just turn out to be extremely evolutionarily fit for our current environment:
https://www.scientificamerican.com/article/why-do-animals-keep-evolving-into-crabs/
By the same token, all kinds of business keep evolving into something like a printer company. It turns out that in this enshittified, poorly regulated, rentier-friendly world, the parasitic, inkjet business model is extremely adaptive. Printerinisation is everywhere.
All that stuff you hate about your car? Trapping you into using their mechanics, spying on you, planned obsolescence? All lifted from the inkjet printer business model:
https://pluralistic.net/2023/07/24/rent-to-pwn/#kitt-is-a-demon
That GE fridge that won't make ice or dispense water unless you spend $50 for a proprietary charcoal filter instead of using a $10 generic? Pure printerism:
https://pluralistic.net/2020/06/12/digital-feudalism/#filtergate
The software update to your Sonos speakers that makes them half as useful and takes away your right to play your stored music, forcing you to buy streaming music subscriptions? Straight out of the HP playbook:
https://www.wired.com/story/sonos-admits-its-recent-app-update-was-a-colossal-mistake/
But as printerinized as all these gadgets are, none can quite attain the level of high enshittification that the OG inkjet bastards attain on a daily basis. In the world championships of effortlessly authentic fuckery, no one can lay a glove on the sociopathic monsters of HP.
For example: when HP wanted to soften us all up for a new world of "subscription ink" (where you have to pre-pay every month for a certain number of pages' worth of printing, which your printer enforces by spying on you and ratting you out to HP over the internet), they offered a "lifetime subscription" plan. With this "lifetime" plan, you paid just once and your HP printer would print out 15 pages a month for so long as you owned your printer, with HP shipping you new ink every time you ran low.
Well, eventually, HP got bored of not making you pay rent on your own fucking printer, so they just turned that plan off. Yeah, it was a lifetime plan, but the "lifetime" in question was the lifetime of HP's patience for not fucking you over, and that patience has the longevity of a mayfly:
https://pluralistic.net/2020/11/06/horrible-products/#inkwars
It would take many pages to list all of HP's sins here. This is a company that ships printers with half-full ink cartridges and charges more than the printer cost to buy a replacement set. The company that won't let you print a black-and-white page if you're out of yellow ink. The company that won't let you scan or send a fax if you're out of any of your ink.
They make you "recalibrate" your printer or "clean your heads" by forcing you to print sheets of ink-dense paper. They also refuse to let you use your ink cartridges after they "expire."
HP raised the price of ink to over $10,000 per gallon, then went to war against third-party ink cartridge makers, cartridge remanufacturers, and cartridge refillers. They added "security chips" to their cartridges whose job was to watch the ink levels in your cartridge and, when they dip below a certain level (long before the cartridge is actually empty), declare the cartridge to be dry and permanently out of use.
Even if you refill that cartridge, it will still declare itself to be empty to your printer, which will therefore refuse to print.
Third party ink companies have options here. One thing they could do is reverse-engineer the security chip, and make compatible ones that say, "Actually, I'm full." The problem with this is that laws like Section 1201 of the Digital Millennium Copyright Act (DMCA) potentially makes this into a felony punishable by a five-year prison sentence and a $500k fine, for a first offense.
DMCA 1201 bans bypassing "an effective means of access control" to a copyrighted work. So if HP writes a copyrighted "I'm empty" program for its security chip and then adds some kind of access restriction to prevent you from dumping and reverse-engineering that program, you can end up a felon, thanks to the DMCA.
Another countermove is to harvest security chips out of dead cartridges that have been sent overseas as e-waste (one consequence of HP's $10,000/gallon ink racket is that it generates mountains of immortal, toxic e-waste that mostly ends up poisoning poor countries in the global south). These can be integrated into new cartridges, or remanufactured ones.
In practice, ink companies do all of this and more, and total normie HP printer owners go to extremely improbable lengths to find third party ink cartridges and figure out how to use them. It turns out that even people who find technology tinkering intimidating or confusing or dull can be motivated to learn and practice a lot of esoteric tech stuff as an alternative to paying $10,000/gallon for colored water.
HP has lots of countermoves for this. One truly unhinged piece of fuckery is to ask Customs and Border Patrol to block third-party ink cartridges with genuine HP security chips that have been pried loose from e-waste shipments. HP claims that these are "counterfeits" (because they were removed and re-used without permission), even though they came out of real HP cartridges, and CBP takes them at their word, seizing shipments.
Even sleazier: HP pushes out fake security updates to its printers. You get a message telling you there's an urgent security update, you click OK, and your printer shows you a downloading/installing progress bar and reboots itself. As far as you can tell, nothing has changed. But these aren't "security" updates, they're updates that block third-party ink, and HP has designed them not to kick in for several months. That way, HP owners who get tricked into installing this downgrade don't raise hell online and warn everyone else until they've installed it too, and it's too late:
https://www.eff.org/deeplinks/2020/11/ink-stained-wretches-battle-soul-digital-freedom-taking-place-inside-your-printer
This is the infectious pathogen business model: one reason covid spread so quickly was that people were infectious before they developed symptoms. That meant that the virus could spread before the spreader knew they had it. By adding a long fuse to its logic bomb, HP greatly increases the spread of its malware.
But life finds a way. $10,000/gallon ink is an irresistible target for tinkerers, security researchers and competitors. Necessity may be the mother of invention, but the true parent of jaw-dropping ingenuity is callous, sadistic greed. That's why America's army of prisoners are the source of so many of the most beautiful and exciting forms of innovation seen today:
https://pluralistic.net/2021/06/09/king-rat/#mother-of-invention
Despite harsh legal penalties and the vast resources of HP, third-party ink continues to thrive, and every time HP figures out how to block one technique, three even cooler ones pop up.
Last week, Jay Summet published a video tearing down a third-party ink cartridge compatible with an HP 61XL:
https://www.youtube.com/watch?v=h0ya184uaTE
The third-party cartridge has what appears to be a genuine HP security chip, but it is overlaid with a paper-thin, flexible, adhesive-backed circuit board that is skinny enough that the cartridge still fits in an HP printer.
This flexible circuit board has its own little microchip. Summet theorizes that it is designed to pass the "are you a real HP cartridge" challenge pass to the security chip, but to block the followup "are you empty or full?" message. When the printer issues that challenge, the "man in the middle" chip answers, "Oh, I'm definitely full."
In their writeup, Hackaday identifies the chip as "a single IC in a QFN package." This is just so clever and delightful:
https://hackaday.com/2024/09/28/man-in-the-middle-pcb-unlocks-hp-ink-cartridges/
Hackaday also notes that HP CEO Enrique J Lores recently threatened to brick any printer discovered to be using third-party ink:
https://arstechnica.com/gadgets/2024/01/hp-ceo-blocking-third-party-ink-from-printers-fights-viruses/
As William Gibson famously quipped, "the future is here, it's just not evenly distributed." As our enshittification-rich environment drives more and more companies to evolve into rent-seeking enterprises through printerinisation, HP offers us a glimpse of the horrors of the late enshittocene.
It's just as Orwell prophesied: "If you want a picture of the future, imagine a HP installing malware on your printer to force you to spend $10,000/gallon on ink – forever."

Tor Books as just published two new, free LITTLE BROTHER stories: VIGILANT, about creepy surveillance in distance education; and SPILL, about oil pipelines and indigenous landback.


If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/09/30/life-finds-a-way/#ink-stained-wretches

Image: Jay Summet https://www.youtube.com/watch?v=h0ya184uaTE
4K notes
·
View notes
Text
Apple and Some Linux Distros are Open to Bluetooth Attack
A Bluetooth authentication bypass vulnerability, tracked as CVE-2023-45866, allows attackers to connect to Apple, Android, and Linux devices and inject keystrokes to run arbitrary commands.
View On WordPress
0 notes
Text
#acebook login without 2-factor authentication#Bypassing Facebook 2FA for login#Accessing Facebook account without two-factor verification#Logging into Facebook without 2FA#How to disable two-factor authentication on Facebook login#Facebook login bypass without two-factor authentication#Steps to log in to Facebook without 2FA
0 notes
Note
i HATE it when antis join fandoms for shows that are like, explicitly proship.
The Owl Houses main message is all about being anti harasment and being authentic to yourself (THE FIRST EPISODE INCLUDED SOMEONE SHIPPING WEIRD SHIT AND TALKED ABOUT HOW THEY SHOULD BE ALLOWED TO DO THAT COME ON) and the creator is anti-censorship! but the fandom is absolutely crawling with antis
Mouthwashing depicts the same dark topics antis will tell proshippers to kill themselves over depicting and its creator is anti-harasment but the fandom is still crawling with antis!
Gravity Falls main message is , once again, about being authentic to yourself and being anti-harasment, the creator himself does not give a flying fuck about what people ship and shares the same sentiment of fiction not being reality, the creator is also anti-censorship, the show/books depict the same content that proshippers get attacked for on the daily through billford and their dynamic, but the fandom is absolutely infested with antis!
it just pisses me off so much! its like they suddenly forget all about their 'morals' the moment a piece of media gets popular! sorry if this doesn't make much sense its just really grinding my gears.
It's wild how antishippers see explicitly proship fandoms and flock to it. They very obviously aren't welcome.
Granted, they're crawling around AO3 despite it being designed to bypass censorship soooooo.
#proshippers against censorship#jackal barks#proship please interact#proshippers please interact#proship positivity#proship#proshipper safe#proshipping#proshipper#anti anti#ask#asks#pro stance
384 notes
·
View notes
Text

✦ 100 LEONS IN A YEAR ✦
(6/100) drawings of Leon S. Kennedy because I made it my personality and I’m seeing it through.
🗂️ CIVILIAN ZERO – FILE 01928-K
📁 SUBJECT: Kennedy, L.S.
CLASS: Urban Casualties Archive
CLEARANCE: [REACPRL13–] Declassified via unknown leak channel
“This ain’t my first smoke break.”
— Audio transcript, intercepted on unsecured comms (timestamp unverified)
A rare publication from the Echo Briefs Collection
This issue was never meant for distribution.
But 100 copies found their way into circulation—exactly 100. No digital trace. All physical. All real.
—
No official response. No denial.
And the question isn’t who leaked it.
The question is—why hasn't it been buried?
—
Rumor says it’s because the subject didn’t protest. Some say he posed. Some say he sent it himself.
VOL. 05 | ISSUE 09
• Urban field sketch recovered mid-2024
• Psychological classification: Detached, noncompliant, functional
• File source “A.W.” – Clearance bypass suspected
• Cover image confirmed as authentic (via ex-agency scan signature)
—
📦 NOT FOR COMMERCIAL SALE.
Copies acquired only through handler channels, black market dealers, or “Echo briefers.”
Ask once. Don’t ask twice.
🖋️ Art recovery & visual compilation by @runim3y (me)
📎 Unauthorized. Unverified. Uncensored.
📌 This file has not been denied by any agency.
📌 No cease & desist has been issued.
📌 Which says everything.

#leon kennedy#fanart#resident evil#rebhfun#drawingleonuntilifinallygethimright#100 drawings of leon challenge
161 notes
·
View notes
Note
Phainon could stub his toe and he’d still refuse to show any reaction in front of reader, not willing to be look any less cool in front of them
That is a very funny thought because it gives me the delightful reminder that, once you have the first taste of what you assume is love, you'll want to do your utmost to appear in your best state in front of the culprit. And Phainon is no exception to this.
Especially because everyone and their grandmas can tell what is going on with him. He thinks he's doing a decent enough job maintaining his cool hero image in front of you, completely oblivious to the fact that his brain blanks enough for him to not notice how visibly flustered and happy he becomes around you. As well as the drastic shift in temperament the moment you're out of his field.
This idea would be even more fun with a reader who has a bit (or a lot, your choice) of a mischievous side and purposefully gets him in situations where his patience is tested. Oh there's these people who keep bothering you, he wouldn't be willing to bypass the consequences of smudging his reputation to give them a good beating, would he? Oh there's this rare piece of antique they're saying is being sold in the market that you really really want! But the problem is, it's so difficult to spot. If only you could just... buy everything.
Then there's a reader who's just... concerned about him. There's already so much going on inside of him and now he's trying to wave off his physical pain, too? It ends up as an actual win for Phainon this time, because you pay extra attention to him. Okay, maybe being a damsel in distress instead wouldn't be too bad.
And if you're someone who ‘doesn't really care’, pretends like you can't see right through him and his shenanigans, please take the liberty and just tell it to his face as well. You'd like him being authentic, so that it can save both of your precious time and energy, I assume. Phainon would be relived as well, even if he does feel rather salty in the beginning for his plan having failed.
#what a boyfailure#if you can't picture phainon doing this just research kevin and dr mei. trust me that guy had Simp as his middle name#phainon#phainon brainrot#phainon x reader#yandere phainon#yandere phainon x reader
228 notes
·
View notes
Text
VMware Discloses Critical VCD Appliance Authentication Bypass With No Patch
VMware has disclosed a critical authentication bypass vulnerability (CVE-2023-34060) affecting its Cloud Director appliance deployments. The flaw only affects upgraded versions of the VCD Appliance 10.5.
View On WordPress
#affecting#authentication#bypass#cloud#Critical#CVE202334060#Director#disclosed#VMware#vulnerability
0 notes
Text


Reprogramming your mind isn't "just" about affirming.A guide to creating durable and anchored assumptions for shifting and manifestation.
1) The myth of the "subconscious sponge"
Many in the shifting/manifestation community believe that the subconscious absorbs everything like a sponge.
But this is only true for young children (under 7 years old). At that age, they have almost no critical filter, which allows ideas to imprint directly on the subconscious.
-> For teens and adults? That filter is very active. It sorts, judges, and sometimes actively rejects affirmations it doesn't find credible.(It’s more or less active depending on the person and their profile that's why some people struggle more than others.)

2) But what exactly is the conscious filter?
The conscious filter (or “critical faculty”) is a mental barrier between your conscious mind (the one that doubts, analyzes, judges) and your subconscious (the one that automates).
It is influenced by:
- Your past experiences
- Your stress level
- Your vigilance level
- Your neurodivergence (e.g., autism, ADHD, anxiety)
- Your self-criticism or inner dialogue
-> Repeating “power affirmations” can sometimes strengthen this filter instead of weakening it,especially if your conscious mind doesn’t believe them.
3) Does spirituality deserve a meritocracy?
Many shifting discourses say: “If you really want it, you’ll shift / manifest.”
That’s false and dangerously guilt-inducing.
-> We all have different cognitive profiles. Some absorb faster, others have a noisy mind.
It’s not a lack of effort/assumption/persistance,you just need a different path.
-> Letting go doesn’t mean being perfect or emotionless. Sometimes, sadness or calm is more suitable for shifting than anxious euphoria.

An article about meritocracy
4)How to deactivate the conscounes filter
Here are techniques that work better than repeating affirmations:
- Hypnagogic state (between waking and sleep): your filter is weakened → perfect moment to anchor ideas.
- Visualization + real emotion: authentic emotion = filter bypass.+ Light hypnotic induction: breathing, progressive relaxation, or guided self-hypnosis.
- Metaphors / stories: the critical mind lets its guard down.
- Whisper instead of saying it out loud: the subconscious responds more to intimacy than insistence.
- Don’t force an idea, but gently infuse it.
- Listen to subliminals in a relaxed state.
5)Assuming ≠ Being positive
Assuming a reality is not about forcing toxic smiles.
To “assume” something means to internally inhabit it as a truth. And that doesn't always come with joy.
Example:
You can assume you're safe while feeling a peaceful sadness.
You can assume you’ll shift even if you’re in a neutral, melancholic, or tired state.
The key emotion is inner acceptance, not blind positivity.

6)Consciousness,ego, subconscious: who does what?
Conscious → Analyzes, plans, judges
Ego → Wants to control, resists change
Subconscious → Automates, believes emotionally repeated messages
When you want to manifest or shift, you need to calm the conscious and the ego so the subconscious can accept.
And if you're experiencing mental overload?
Your whole system goes into resistance mode, no matter how many affirmations you repeat.
7)One size doesn't fit all
The biggest problem in spirituality or manifestation: trying to apply one-size-fits-all methods.
Most advice might help some profiles but not everyone.
-> A neurodivergent person, a traumatized person, a child, or a stressed adult: they will never manifest in the same way.
-> Customize your approaches:
If you're very critical → use metaphors, hypnosis, play.
If you're sensory → use physical sensations in visualization.
If you're hyperactive or inconsistent → find short scripts or routines, not rigid ones.


8) Tips for manifesting / shifting sustainably
Favor mental softness over intense effort.
- Use calm or deep emotion, not necessarily joyful.
- Introduce roles: "If I were already in my desired reality / with my manifestation, how would I act?"
- Use the pre-sleep state to infuse your mind.
Be subtle, not robotic: one sincere affirmation > 1000 mechanical ones.
(Even if that can work for some profiles)
9) Summary: true power is adaptation
You aren't broken
-> Your brain is not broken.
-> You are not lacking in “positive vibrations”.
You just need a bridge between you and your subconscious, and that bridge isn’t always built with “affirmations + persistence”.
It can be built with:
- Acceptance
- Gentleness
- Hypnosis
- Rest
- Authentic emotions
- Meditation
My favorite alpha waves for manifestation.
And others.
(Translated from my TikTok post)
#dr self#desired reality#shiftinconsciousness#shifting help#self concept#reality shifting community#shifting methods#shifting#fulfillment#reality shifting#shifting reality#shifters#kpop shifting#spirituality#law of assumption#manifestabundance#anti shifters dni#scripting#manifestation#shifting motivation#shifting stories#black shifters#reality shifter#manifestação#law of attraction#marvel shifting#shiftblr#shifting advice#shifting antis dni#shifting blog
92 notes
·
View notes