#category-/Computers & Electronics/Software
Explore tagged Tumblr posts
Photo

Nvidia has announced the availability of DGX Cloud on Oracle Cloud Infrastructure. DGX Cloud is a fast, easy and secure way to deploy deep learning and AI applications. It is the first fully integrated, end-to-end AI platform that provides everything you need to train and deploy your applications.
#AI#Automation#Data Infrastructure#Enterprise Analytics#ML and Deep Learning#AutoML#Big Data and Analytics#Business Intelligence#Business Process Automation#category-/Business & Industrial#category-/Computers & Electronics#category-/Computers & Electronics/Computer Hardware#category-/Computers & Electronics/Consumer Electronics#category-/Computers & Electronics/Enterprise Technology#category-/Computers & Electronics/Software#category-/News#category-/Science/Computer Science#category-/Science/Engineering & Technology#Conversational AI#Data Labelling#Data Management#Data Networks#Data Science#Data Storage and Cloud#Development Automation#DGX Cloud#Disaster Recovery and Business Continuity#enterprise LLMs#Generative AI
0 notes
Note
For some reason I have the feeling you might've mentioned this once but I don't remember, but was there any particular career path Minibon wanted to follow/dreamed of following in the future?
(You know like sometimes when you're a kid you have that one really serious dream job like being a vet)
Maybe stupid question but I dunno I like Minibon lore

I probably told ya her dream job as a kid was to work at a big space organization (like a nasa engineer). I do warn, she didn't understand the jobs quite well and just found the concept/idea of them cool, so they aren't that specific as one would say "vet".
Her 'main' dream is just working at space agency (like nasa or esa). At specifically you might ask? She can't exactly answer that (She usually didn't think about being an astronaut, even tho we the thought of going to space is in all of us), girl is just too indecisive to be able to choose such a big thing for something she doesn't know that much. (It's something that will haunt her till the end of highschool). Anyhow, she had another 3 "categories" of dream jobs, that in a way allow her to work on the main one as them as one of them.
First is being a 'scientist', making a gigantic discoveries, studies on either biology about diseases and discovering cures, or a physics to comprehend and study matter and space better. Second is being engineer that "builds/makes stuff" like robots or buildings. Sounds shallow but she has the heart of a lego builder on her and she loves the idea of robotics. ( Mini bon would join a robotic club and build a few speedy robots ). Finally, just working with electronics, its being a engineer again but different field. Messing with machines/computers cables is just something she found interesting and fun, especially in age where technology and the internet was surrounding her. She would often literally take apart those toy cars or random domestic electronics to see whats inside of them. Her parents even encouraged her by gifting things to actually toy and learn (instead of destroying the tv remote). Even installing some programming softwares for kids on a small poopoo pc. This last one is what she would gravitated towards in her life.
#shaibonbon#shai oc#shai oc Mini Bon#shai ask#art#my art#drawing#oc#bunny girl#rabbit girl#anthro#kemonomimi rabbit#short hair#shai sketch#sketch#ask#scientist#engineer#sketch art#doodle#cute art
26 notes
·
View notes
Text







🇺🇲 Explore the Fascinating Fusion of Timekeeping and Communication: Unveiling the Pioneering Motorola and Timex Wristwatch-Pagers that Revolutionized Wearable Technology in the 1990s.
🤝 In 1990, Motorola Inc. made its first attempt to enter the market of electronic wristwatches with a built-in pager (similar devices at the same time were already produced by the Japanese companies Seiko and Casio). The device was called "Motorola Wrist Wach Pager". Since 1991, further production of the devices has been carried out jointly with the Timex Group Corporation under the name "The Timex Tracer Wrist Watch Pager".
👉 Since 1998, further development of the line of electronic watches with the participation of Motorola Inc. and Timex Group was associated with the high-tech "Timex Beepwear Datalink" series. These devices also continued the concept of wristwatch-pagers, but with the integration of the well-known Datalink data transmission platform, which integrates with desktop computer software.
➡️ The Datalink line was introduced in 1994 and was developed in conjunction with Microsoft Corporation as an alternative to conventional PDAs with added attributes such as water resistance and ease of programming. Taken together, all this made it possible to use the “Beepwear Datalink” watch as a full-fledged electronic organizer.
📟 The Beepwear Pager Watch epitomized the convergence of traditional wristwatches with cutting-edge communication capabilities. Introduced in the late 1990s, this innovative device redefined the concept of wearable tech, offering users unparalleled convenience and connectivity on the go.
📞 Equipped with pager functionality, the Beepwear Pager Watch allowed users to receive important notifications and messages directly on their wrist, eliminating the need for separate communication devices. With its sleek and compact design, it seamlessly integrated into everyday life, providing instant access to critical information wherever you went.
⌚️ Beyond its communication features, the Beepwear Pager Watch retained the timeless appeal of a classic timepiece, boasting a stylish and durable design that stood the test of time. With its reliable quartz movement and rugged construction, it was built to withstand the rigors of daily wear, ensuring longevity and reliability for its users.
⚙️ The "Beepware" series, as a joint product of the efforts of Timex Group and Motorola Inc. was patented, and the production of the devices was carried out by the newly created joint company "Beepwear Paging Products". The clock operated in the 900 MHz band. FLEX time was also used, which, if supported by the operator, could synchronize the clock time with the network time, and also automatically adjust to the owner's time zone.
🚀 The launch of the Timex Motorola Beepwear Pager Watch marked a significant milestone in the evolution of wearable technology, showcasing the potential for seamless integration of communication and timekeeping functions in a single device. As one of the pioneering products in this category, it paved the way for future innovations in the wearable tech industry, inspiring a new generation of smartwatches and wearable devices.
💔 However, already in 2002, Motorola Inc. was forced to carry out internal restructuring, including ceasing production and support of its own pagers.
💫 Today, the legacy of the Timex Motorola Beepwear Pager Watch lives on, remembered as a trailblazer in the realm of wearable technology. While newer devices may offer more advanced features, the Beepwear Pager Watch remains a symbol of innovation and ingenuity, reminding us of the transformative power of technology in shaping our lives.
#timetrek#brands#clock#watch#watches#time#companies#company#history#luxury watches#motorola#timex group#timex watches for men#timex#beepwear#pager#wristwatch#wrist watch#wristwatch pda#wristwatch pager#datalink#microsoft#smartwatch#digital watch#casio#seiko#made in usa#telecommunications#innovation#old gadgets
28 notes
·
View notes
Text
My personal defintion for 'video game':
Has some notion of a 'game state', where some number of these possible states are more desirable for the player than others. (These may be intrinsic or extrinsic values judgements.)
Transition between game states is accomplished by an interaction between player input and software/logical electronic game systems.
The primary means of communicating game state is through video.
Related, and often synonymously-used categories include: 'computer games', which does not have the video requirement; and 'electronic games', which does not have the video or software requirements.
There are, of course, many titles which are marginal. I won't weigh in on where the exact line is; it is not difficult to discuss a non-video game through that lens regardless, and vice vesa. Things are how we consider them.
3 notes
·
View notes
Note
Hey! I saw your tags about learning to compose music and being overwhelmed about what programs to start with so I thought I could offer some insight into some of the options available. Generally the programs people use to compose music fall into three categories.
1) DAWs, or Digital Audio Workstations: These are programs where you have multiple tracks of audio (either recorded or you can generate them in the program) and you work with sound more than visuals. If you’ve ever used Audacity to edit audio before, that’s a DAW! Good for: if you want to record your own vocals/instrumental parts, if you prefer to work with sound than sheet music, for much more detailed mixing and effects options than other programs. Recommended starter software: I don’t have much personal experience with these but if you’re on Mac than GarageBand is probably a solid place to start, or I’ve heard Cakewalk is good too for a Windows option. Or you can google “best free DAWs” and you’ll find lists with all sorts of options. If you know how to find notes on a piano keyboard, finding a DAW with a “piano roll” input mode is an especially intuitive way to get started composing (and even if you don’t, it can still be useful as a visual representation).
2) Music notation program: this is software meant to create sheet music like you would see in a piano book or larger arrangement. Most modern notation programs have playback as well which you can either export and use as-is or use it as a base to mix in other programs (like a DAW). Good for: if you can read sheet music and are comfortable in that format, if you intend to have your music played by real musicians. Recommended starter software: MuseScore is a really amazing free and open-source notation program that is easier to use than most of the paid options (though I recommend MuseScore 3 atm since 4 is fairly new and has some issues that still need to be ironed out).
3) Tracker software: These are specialized programs that are best for emulating older styles of VGM and electronic music, especially chiptune music. They work similar to programming where you input a bunch of numbers that correspond to notes and parameters for sound. Heads up that this is probably the least intuitive option compared to the other two, but some people really like it. Good for: if you like working with numbers and computers, if you want to emulate a specific sound chip. Recommended starter software: FamiTracker is meant to emulate the NES chip and the limitations of that can be helpful if you get overwhelmed by lots of fancy options.
Personally, unless you’re more comfortable with sheet music I would recommend going for a DAW since it’s the most “all-in-one” option of these. If you’re interested in more information on this topic please feel free to send me a message or ask! Composing music is a lot of fun and it would be great if it were accessible to more people. There are also many great tutorials on YouTube if you search for your software of choice there. If you’re interested in composing VGM then I have some specific channels I could recommend as well.
Oh my gosh yes thank you! Generally I learn best by seeing other people do things and then copying it a lot
9 notes
·
View notes
Text
I can be soft and vulnerable, I am willing to let you hurt me because I love you and trust you. I know you are passionate I rediscovered part of the reason why I love you so much. Your love is discrete, inverse pun intended but both homonyms applicable in this analogy. It is private, our unique form of expression
But it is also literally discrete, like recent quantum gravity field theories I may or may not have a hand in. My mind craves clarity, more so, it craves discrete caustic lines an planes. I would like to be like that every day. I want my heart to be in the inner of a particle accelerator bit-west two colliding high energy beams. All the crazy spins and flavor's of normal, charming, and even exotic sub atomic particles smashing apart, smashing together, twirling off in random spirals based on EM fields. That is who I am, not a particle reactor,
but every emergent self and extended phenotype aspect of my projects, world views, emotions, experiences, thoughts and behaviors.
Do you really want to see what I have seen when I was manic, I will make a brief outline, which barely does it justice, nor was the experience worth it in my mind
I saw reality
Across all multi scale layers of objective, subjective, abstract existance. Both perceived and externally existing.
Across all of these non-linear and semi-non empirical scales
Ontology categories of conscious awareness -5 Planc Quantized Wireframe -4 Subatomic Interactions -3 Electron Orbitals -2 Biochemical Interactions -1 Neurological Activity 0 Perception Input and basic awareness/dispersibility [(x n-1…n5) State of dissociation of whatever perceptual order or unconsciousness/dreaming] 1 Awareness of perception and SV 2 Awareness of perception in context or awareness of awareness -Xa Intrapersonal models 3 Awareness of self, regarding one's cognitive topography -Xb Allocentric models 4 Aware of a disruptive axiomatic shift recursively impacting various areas and fidelity of one's consciousness -Xc Global and Orbital Cyberphysical Memetogeographic Space -Xd Cosmology 5 Aware of a fundamental change in perception or PMC affecting POV. Shift in paradigm -Xe Uber Universes/5D+ EGC splines (ego/exo/allo) centric/ totality of EISOA over CT0-9
In the context of modular frames, of which I have objectively real working minimal level of knowledge in all of these domains, some reaching PhD levels of mastery
1 Technology
1 Applied Science/Applied Uses of TSECpm Phenomenon 2 ~Sustainable, Agricultural, Ecological and Environmental 3 Fabrication, Trade/Craft, and Intra/Inter Human Skill/Functionality 4 Military/Security/OMA7 5 Educational, Knowledge, Cognitive, Cybernetics, and Information, DT/PT 6 Electronics, Computers, Software, Spectrum, AI 7 Industries, Material Collection, Cyclical/NA: Supply Chains, Accounting 8 Skills, Fabrication, Synthesis, and Patents, Logistics 9 Civil, Nationality, Era, Civilian, State, and Structural 0 Future Technology/Other
2 Philosophy
1 Logic 2 Epistemology 3 Aesthetics 4 Politics 5 Dialectics, Critical Thinking, and Rhetoric 6 Ethics and Morality 7 Metaphysics and Ontology 8 Meta Linguistics 9 Applied Philosophy 0 Analytic Philosophy/Other
3 Engineering
1 Nuclear Engineering 2 Chemical Engineering 3 Biological Engineering/Medical Engineering 4 Environmental Engineering 5 Systems Engineering and Cybernetics 6 Electrical Engineering 7 Mechanical Engineering 8 Industrial Engineering 9 Civil Engineering 0 Personal Engineering/Cognitive Engineering/Experience Engineering, ME0002/0013/0034/0049, Other
4 General-Cultural
1 Interactive Mediums/4, 3//Middle World IO MR Interaction/Hobbies/EISOA interactions 2 Geography, Culture, [[SMPH/ME 1/Experiment 0032 TSeCIVii|Experiment 0032 TSeCIVii]] 3 Occult/Niche Allusion/Metaphor 4 Physical, Mental, and Cognitive Skills 5 Day to Day Functionality, House Keeping, BH, and Normative and Exotic Behavior (Anomolies vs Normative Phenomena, timescale/PoF independent) 6 Law, Rules, Conduct, Ethology 7 Finance and Business/Institutions/VSM/States/Governing Bodies 8 Dynamic PPF+/-PoV, People of Interest, UJSF 9 Politics and Society – Collective Conscious Gestalt 0 UM, Pop culture/other, (**(almost) ALL EISOA can be contained in USF(EISOA Correlate))
5 Frameworks
1 Gestalt, Non Gestalt (AS/S)_, Spatial and/or Temporal Patterns, and Non-Modular and Modular Ontology, Shapes, Objects, Sounds, Qualia Framed Experiences which can be Axiomatized (basically an intersystem link to 1, 1 to enable dual +y/1, 1 functionality) 2 PT/MR Mathematical and Mapping/Fields Competition and Game Theory, NWF (applying [[Experiment 0024 LoUtrix]] to 1, 1) 3 UJSF/Society and Culture/Cyberphysical Environments (EISOA cybersocial considertations) 4 TSECpm, +y/PT, Exocognition/LLM integration 5 Mindmap/MEs, and Modelling, Psychology/EISOA, Thought Traces/2, 5/AE/DABPAx (self imposed 3, 4 for the meta task of utilizing +y effectively) 6 Experiential and PMC/5, x /1, 1/3, 1/2, x/PE (1, 1-2-5-6/2, x subjective experience. MM08, x 7 IESOA, CABS, Frames, (OMA7), Fuzzy Logic, 3, 4/VSMs/SMPH Optimal Scheduling and [[Unsignificant Sentience/Mental Experiments/Experiment 0005 Chewing Gum Loading Dock|Experiment 0005 Chewing Gum Loading Dock]] [[SMPH/ME 1/Experiment 0058 Just in Time 1, 31, 5AE+Y|Experiment 0058 Just in Time 1, 31, 5AE+Y]] HMI workflow (EIOA on IS) 8 Language and Linguistics, Metaphor/SWHs, [[SMPH/ME 1/Experiment 0012 Fractal Cosmic Regression|Experiment 0012 Fractal Cosmic Regression]] 9 Cognition, Learning, and Experience/ 09, x 0 Axiomatic Systems, Perspective Theory/other, PoFs
6 Science
1 Physics 2 Astrophysics and Cosmology 3 Chemistry 4 Biology 5 Interdisciplinary/System Science 6 Health Sciences 7 Earth Sciences 8 Formal Science 9 Social Sciences 0 Other
7 Abstract Constructs, Functions, and Relationships
1 Set Theory 2 Ontology 3 Epistemology 4 Metaphysics 5 Digital/Cognitive Twins 6 Abstract Object Mapping 7 Abstract Object Manipulating 8 Elucidating Abstract Space into IS space and vice versa 9 Metaphysical Abstract Space Workshop, CA 0 Communicable and interactive Abstract Entities/Engineering of the Abstract
At the same time, world building a sci fi universe and multiple systems of systems that would be abstracted and logically patterned into some of the most influential books in human history.
The fourth book? You are a main character you wrote your own part you played. It is probably the first case of hypersituatal fictional historic non fiction that guided the development of humanity culturally and scientifically. I became a living fictive, I had all of my human rights removed, but not my natural rights.
When you see everything, you can change everything
I had reality fuck it's way into my brain and leave gaping wounds that have never healed. I can handle some rough love dear
Maybe one day I will be able to share the light show
1 note
·
View note
Text
"Magnetic levitation is already employed in systems such as Maglev trains, flywheels and high-speed machinery. Now researchers at the Technical University of Denmark have given this old technology a fresh twist by explaining how a magnet can be levitated simply by rotating another magnet of a similar size near it. This unusual effect was first demonstrated by an electronics/computer and software engineer, Hamdi Ucar, in 2021, and the TU-Denmark team say it could be exploited in the contactless handling of objects or used to trap and manipulate ferromagnetic microparticles.
There are three main types of magnetic levitation. In the first, known as active magnetic stabilization, a control system supplies the magnetic force required keep the levitating object balanced. The second, termed electrodynamic suspension, is used in Maglev trains. Here, a moving magnet induces a current in a stationary conductor, producing a repulsive force that increases with the speed of the moving magnet. The last category, called spin-stabilized levitation, features a levitating magnet that spins at around 500 revolutions per minute (rpm) and remains stable thanks to the gyroscopic effect.
The new type of levitation involves two magnets. The first, dubbed the “rotor”, is mounted on a motor with its north and south poles oriented perpendicular to its rotation axis and made to rotate at velocities of around 10 000 rpm. In the TU-Denmark team’s experiments, this magnet was spherical, 19 mm in diameter and made from neodymium-iron-boron.
The second magnet – the “floater” – is placed near the rotor, begins to spin automatically, and then moves towards the rotor until it hovers in space a few centimetres below it. The floater precesses with the same frequency as the rotor and its magnetization is oriented close to the axis of rotation and towards the like pole of the rotor magnet. If disturbed, a restoring force moves it back to its equilibrium position.
“It is quite surprising that magnetic levitation develops in such as relatively simple system,” says Rasmus Bjørk, a physicist at TU-Denmark who led the study together with Frederik Laust Durhuus and Joachim Marco Hermansen."
"“It is intuitive to all that the magnetostatic force that one magnet exerts on another can be both attractive and repulsive,” explains Durhuus. “Without rotation, the free magnet will rotate so the force becomes purely attractive and then the magnets will collide into each other. What makes the new magnetic levitation system so special is that the rotation itself allows the floater to remain in a counterintuitive configuration, nearly perpendicular to the rotor’s field, where the magnetostatic force both attracts and repels it.”
continue reading article
#levitation#magnetism#magnetic levitation#rotation#counter rotation#spinning#gyroscopic effect#energy#electromagnetism#physics#north and south poles#polarity#dipolar coupling#science#technology#discovery
2 notes
·
View notes
Text
Demoscene and “Art” Games on PlayStation 3
Early in the seventh console generation, with the inclusion of storefronts allowing a user to download games on every home console, the ability to self-publish or be picked up by a publisher increased thanks to this new ease of access and lower costs of digital distribution as compared to boxed retail products. For Sony and the PlayStation 3, this would see the release of some games both Sony, games media, and players alike would sometimes deem non-games, especially those that came from a group of artists called demosceners which we’ll look at today.
Currently: Linger in Shadows .detuned
To be completed: flOw Echochrome PixelJunk Eden Flower Noby Noby Boy Journey Datura PixelJunk 4am Papo & Yo The Unfinished Swan Proteus Bound Linger in Shadows

Released: Thursday, October 9, 2008 On: PlayStation Network for PlayStation 3 Developed by: Plastic Published by: Sony Computer Entertainment America Inc.
Linger in Shadows was announced at the demoparty Breakpoint 2008 in Germany. Breakpoint was a successor to the demoparty mekka & symposium which ran from 1995 - 2002. Demoparties came out of the demoscene in which software crackers would create their own audiovisual effects and playbacks to be shared via demoparties, the internet, and inserted into cracked software. Organized parties would break the competition into categories of size and platform, letting the restrictions feed creativity. As explained by the organizers of the demoparty mekka & symposium:
What is MS? The mekka & symposium is a demo-scene party that was organized annually at Easter. More than 1200 young Multimedia artists gathered here for four days in order to meet similarly-minded people, to exchange ideas and to participate in the competitions, in which individuals and groups show off their talents in a certain form of electronic art called Demos. ms2002 has been the eighth and last event in a traditional party series that started back in 1995, when 300 mostly German visitors attended the BlackBox Symposium. To our 2002 event, about 1220 visitors came from all over Europe, and beyond - "sceners" have come to celebrate with us from countries as remote as Estonia and Israel! The event was never a LAN or gaming party. People playing Qu*ke or Half-Life on our events would have been considered non-creative by our "serious" visitors, and as a matter of fact, the participation of gamers on our parties has always been exceptionally low, which made the MS one of the last big enjoyable events for real sceners.
Breakpoint would see its first iteration during Easter 2003, Friday, April 18 - Monday, April 21. The lead organizer was Scamp who detailed in an interview some of the difficulties in running the first party such as heating, internet access, attendance-to-expense, and getting permission to have the meeting during the Easter holiday in Germany. Attendance cost was reportedly €40.00 for men and no cost for women. It was during Breakpoint 2008 that the team called Plastic would reveal a video teasing the project Linger in Shadows for the PlayStation 3, with official confirmation coming later that year at E3.
Linger in Shadows was released on October 9, 2008 as an “interactive art” application for $2.99. Sony was quick to assert that this was not the typical PSN release. Rusty Buchert on the PlayStation Blog would state, “I’ll start with the easier side, and that is Linger in Shadows is NOT a game. It was never meant to be a game and it will never be a game.” In IGN’s “Impressions” piece on the game Chris Roper stated, “Linger in Shadows hit the PlayStation Network this week, but make no mistake - it is not a game. It even says so in about three different places just to make sure the point gets across. Instead, it's being dubbed as "interactive art", which is a pretty fitting description.” GameSpot’s Ricardo Torres would similarly remark, “While this isn't a game…”
“Games” are restricted to things such as Pac-Man, Madden NFL, or even LittleBigPlanet. Linger in Shadows is interactable (the player makes inputs and the game responds and reacts) though because it doesn’t fall into the traditional, high score, killing, or numbers-go-up categories so familiar to game players it becomes a non-game. Sony understood this and is why they would denote it as “not a game” themselves in its promotions. While seeking out the various titles listed at the beginning of this article the main things I was looking for were “art” games that lacked the traditional video-game framework such as a scoring system or games that had “artsy” visual styles but were really just dressing up a traditional platformer or point and click adventure game.
Due to its “non-game” status, reviews from release are fairly scarce. HonestGamers’ 1.5/5 community review by zippdementia says, “What bothers me is that this was such an obvious attempt to make an extra buck off the PS3 owner with overblown advertising. Next time, Sony, tell me what's really inside your package. Don't tell me you're going to give me cheese and then hand me Cheetos.” Eurogamer’s Dan Whitehead appeared to be the most adept at talking about the game in a “review” context, ending theirs with “Linger therefore exists in a strange new realm between the hardcore demoscene and the mainstream audience being asked to pay to play around with its peculiar concept. It's an interesting move if it opens up Sony's platform for more demos to reach a broader audience, but perhaps not if they have to pass through the gateway of establishment approval to get there. This experiment may at least tempt a few more people to Google "demoscene" and, payment aside, it's refreshing to see something so esoteric being championed in such a public way. You certainly won't see anything like this on Xbox Live or the Wii Store. That, at the very least, makes Linger in Shadows something rather special.”
Modern reviews have not been kind either, as Gamerhub’s ⅖ reviewer Steven Barry writes in 2022 that, “To be fair to developer Plastic, they do go out of their way to emphasise that this is not actually a game and is instead ‘interactive art’. So, it does feel a little strange to review this like any other game when in reality it’s a glorified tech demo. However, this was a purchasable product on release in 2008 over the Playstation Network so that is why it’s ultimately eligible for critique.”
Since most people were more preoccupied with grappling with its status as a “non-game,” there wasn’t much discussion about what it actually is and does. Linger in Shadows plays and unfurls itself as a dream. There is an unlogic to the procession of movement, space, and plot. The first signal of this is when watching the dog try and run through the air to escape the ethereal black cloud presence haunting the concrete setting. The dog's attempts to flee are vigorous, but without much effect, calling back to a shared experience nearly everyone who dreams has, of trying to run but finding you are unable to move at much more than a snail’s pace.
The game mostly finds itself following the presence of a black sentient cloud figure, as it moves about an impossible high rise grouping and its various unlogic features, such as a large flower atop a levitating rock, barrels similarly suspended in the air, and the biggest “tech-demo” flag of “how many moving objects of different shape and synchronicity can we have at the same time?” The black cloud can be interpreted as a malevolent entity even before it turns the dog to stone due to its coloring and the faint imagery moving about within it recalling the antennae of insects, both elements long associated with the impure. A cat impassively watches as the cloud turns the dog to stone, maybe something of a mirroring of the player impassively watching and even participating, without much of a feeling for what’s occurring on screen. Soon after, a giant creature bearing a mask with eyes and a body of trailing tentacles appears. In contrast to the black cloud, which effortlessly weaved in, out, and between various objects without much effect, this mask creature blunders its way toppling various objects as it seeks out the petrified dog which it also ends up breaking apart. Bearing familiar eyes and a more tangent shape than the ethereal black cloud, this mask creature is instantly interpreted as the “good guy.” Confronted by the black cloud, the mask ascends a pillar of stone atop of which is a semicircle of columns surrounding a statue of a woman. The black cloud begins petrifying the mask’s tentacles, furthering the black cloud’s villainy and the mask’s innocence as a victim. The “camera” is destroyed by a toppled column leading to the credits. As the demoscene is more about visual demonstrations than narrative, it's not surprising that the one displayed here is pretty simple and straightforward and more a way to show off different character models and what the player can manipulate.
The “game” portion of the game is that during this entire video playback you can at any point pause and manipulate the camera and objects on-screen. Since everything is a rendered object you can escape the usual limitations of regular video playback, and the UI even resembles the UI of media playback on the console or any DVD/Blu-Ray player of the time. The game itself will guide you through what types of manipulation you can do, with an additional hidden object portion tied to finding images that are shout-outs to other demogroups tucked away just out of frame. Playing Linger in Shadows is mostly a touch and go affair of moving the timecode forward and backward and moving around the controller and pressing buttons to see what sort of movement you can do in this specific frame or scene. Aside from whatever you can come up with yourself there isn’t any set of objectives beyond the tutorial teachings and then the image hunting collection.
It is this lack of purpose or list of things to do that I think most frustrates people into declaring Linger in Shadows “not a game!” Coming from arcades with high scores to home consoles with experience to accrue and levels to beat and people to shoot, we’ve been conditioned to think of games as filling a certain role and no other. Even Shadow of the Colossus in 2005 was heralded as the fulfillment of “Games as art” that would convince people like Roger Ebert of the medium’s value. That goal is self-defeating anyway, but also Shadow of the Colossus, while a phenomenal work, still falls into the traditional video game category quite easily, with the game bearing the objective to kill 18 colossi that are framed as unique boss encounters. While there is no progression in terms of level or equipment you do slowly increase our stamina and health over the course of the game. Nobody would mistake Shadow of the Colossus as an “interactive art piece” like they would Linger in Shadows, but both are video games.
Watching another of Plastic’s demos from 2008, called “Into the Pink,” many similarities come up, from more explicit bugs, more imposing crawling shadows, moving lots of objects floating through the air, and distorting text/images so that they jitter. Another project of theirs, “Catzilla,” is much more an entertainment object playing with destruction on a city-wide scale which just happened to come out the same year as Man of Steel and its similar experiments.
This art stands among the other “demoscene” game(s) on PlayStation 3 as a period when Sony was interested in courting the margins of games in order to sell its struggling console. At the time, the PlayStation 3 was in dead last place when it came to home console sales, and so Sony had to look at alternative ways to attract engagement. One of those ways was to present the PlayStation 3 as something more than just a video game console. Early advertisements for the PlayStation 3 are routinely mocked, though they really don’t stray too far from some of the advertisements for the PlayStation 2, such as those famously directed by David Lynch. These more “heady” adverts attempt to sell the console based not on gameplay footage but on an idea of what the console could do/be. It didn’t work.
Not until the Kevin Butler series of commercials did PlayStation 3 begin to majorly change its presentation to the larger gaming audience. PlayStation Plus, courting indies, and the humbled approach they took towards developers with the creation of the PlayStation 4, culminating in the disaster that was the Xbox One’s lead-up to launch, secured their continued success to this day. The cost of that success has been a lack of effort to engage the margins of gaming, something unofficially certified with the closure of its internal Japan Studio in early 2021 and further with the shuttering of PixelOpus and the announcement of ending support for MediaMolecule’s Dreams just this month. With its focus on huge titles, contemporary Sony would not throw money towards a group of students and tell them to “go wild” and release their demoware title on the PlayStation Network. The closest we have gotten in recent years was the release of Dreams, a game to create other games from MediaMolecule, itself a development team founded in part by a demoscene participant named Alex Evans known as Statix/TPOLM during the 1990s.
This is not to write off Microsoft and Nintendo’s attempts to court the indie space for success, as Xbox Live famously had its “Summer of Arcade'' titles, as well as being the console that really began today’s online network connectivity and distribution of smaller titles on the OG Xbox. Microsoft still had a restrictive storefront however, with file sizes and other limitations holding back small developers from seeking it out as the best place to try and publish their game. Nintendo also had some success with indie releases under the WiiWare brand (World of Goo and Bit.Trip Beat), but failed to do much to advertise or promote them.
One question that persists is in the intention behind the team of Plastic in creating Linger in Shadows. Dipping into demos and their productions, what strikes me is that the challenge comes from crafting advanced renders on platforms with limited and dated capabilities. As I’ll detail later, .theprodukkt was able to create a first person shooter with a file size of 96kb, and results for demoparties are broken down by platforms such as the C64, Amiga, and restricted file sizes such as 64kb. So why choose to utilize the PlayStation 3? Proudly boasted as the most powerful next-generation console in 2007, what appeal does that have to a group regularly challenging themselves to see what they can create using computers from the 1980s? Perhaps it was the challenge of working with the difficult to develop for CELL processor powered console. Perhaps they just thought it would be fun to swindle Sony out of some cash and just create whatever their whim deemed suitable for a wider audience instead of fellow demosceners. As I mentioned before, portions of Linger in Shadows definitely seem to be examples of the team simply trying to see how much they could get away with without breaking the game, though in 2023 it can be hard to look at it with the same eyes as someone in 2008, as graphics are continually chasing more and more fidelity with reality.
Shared between Linger in Shadows and the next demoscene game, .detuned, is Rusty Buchert, a producer at Sony Santa Monica who was the face of these demoscene games to the PlayStation audience at the time. Previously at Interplay Entertainment from 1990 - 2003, Buchert joined Sony Santa Monica Studio in 2003 and his major credits include flOw, Everyday Shooter, Linger in Shadows, Flower, .detuned, and despite his departure from the company in 2011 gained Special Thanks in Datura, Sorcery, The Unfinished Swan, and Sound Shapes. Speaking to Engadget in 2007, Buchert detailed his role as focusing on producing PSN titles for the PlayStation 3 and details what type of games and culture Sony was interested in cultivating.
We started searching for games like this [flOw] from the outset and we were searching through the Indie Scene right out the gate. In general the Scene thinks outside the traditional development box. All too often people get indoctrinated into one general way of thinking about games in genre, design, and execution. You are not going to get anything new thinking like that. We were betting on the fact that people wanted something new and not a rehash of a rehash of a rehash. There are a lot of games to sort through. When we find a gem we start pursuing it. Some work out, some don't. I recently heard back from one developer that wanted to finish college and then he would like to try. The game made me think he was already programming professionally. There are some other experimental projects that will also fit in this vein too. These are very much art and an extremely different take on interactivity.
In a later post on the PlayStation Blog, Buchert also discusses how he, and another producer, George Weising (who is still at Sony today) scoured the Indie Games Festival booth at GDC 2007 where they found and signed a deal with the team behind Everyday Shooter. Their seeking out of indie games led to the next project from a group called Plastic.
Linger in Shadows developer Plastic was a Polish demogroup led by Michal Staniszewski (bonzaj). Alongside Staniszewski for all three Plastic projects were Grzegorz Juraszek (fei) and Damian Bajowski (mime). Those who developed Linger in Shadows and went on to Datura in 2012 are Krzysztof Deoniziak (rork) and Wojciech Golczewski (Blz). Shared staff between Datura and Bound, released for the PlayStation 4 in 2016, are Andrzej Uszakow (uho), Kinga Staniszewska, Marek Bielawski (mare), and Michał Szymczyk (misz). Plastic joined Epic Games in 2022, and was credited in Cyberpunk 2077 under “Outsource Partners,” though Staniszewski details on his Linkedin that the work was, “Responsible for visual development and prototyping of Cyberspace in Cyberpunk 2077.”
Grzegorz Juraszek (fei) is still active in the scene as he is the main organizer of the demoparty Riverwash, the largest of its kind in Poland. Damian Bajowski (mime) continues to work as an artist, most recently contributing to an episode of Netflix’s “Love, Death and Robots” called “Manson’s Rats.” Micahl Staniszewski (bonzaj) now works at Epic Games and has many YouTube videos talking about Plastic’s last game, Bound, which was released on PlayStation 4 in 2016. He has one lone video on the making of Linger in Shadows from December 2008. Krzysztof Deoniziak (rork) is also active in the scene, being credited on several demos in 2022. Wojciech Golczewski (Blz) continues to make music, though hasn’t been a participant in the demoscene since his time with Plastic early on. Andrzej Uszakow (uho) appears to still be at CD Projekt Red as a “Senior Engine Programmer.” I couldn't find much of anything to see what Kinga Staniszewska has been up to since Bound’s release. Marek Bielawski (mare) is currently a senior audio programmer at CD Projekt Red. Michał Szymczyk (misz) has the most surprising transition, while most of the developers stuck to Poland, Szymczyk is a Senior Software Engineer at the LA-based developer Infinity Ward starting in September 2017.
Plastic’s work on Linger in Shadow would be the first, but not only, demoscene game to find its way onto the PlayStation 3, as within a year of release another title from another demogroup would appear on the PlayStation Network.
.detuned

Released: Thursday, October 15, 2009 On: PlayStation Network for PlayStation 3 Developed by: .theprodukkt GmbH Published by: Sony Computer Entertainment America Inc.
Developed by .theprodukkt, .detuned™ is a personalized, interactive music experience which gives you the opportunity to create dynamic artwork in real-time to accompany your XMB™ music collection. Manipulate the given scene by interacting with and modifying its unique graphics using the DUALSHOCK®3 Wireless Controller. Plus you can change and tweak your own music to accompany the scene. .detuned™'s brilliant design and capabilities call for the state-of-the-art processing power that can only be done on the PS3™ system. Download .detuned™ today for an artistic music experience! Features: -Artistic Experiences: An abstract and surreal interactive experience to players of all levels and interests -Personalized Music: Manipulate and tweak music tracks on the XMB™ to accompany your artistic creations -Power of the PS3™ system: Stunning and crisp HD environment that brings your artistic visions to life in real-time
It started with a team of eleven people, a majority of which came from 49Games GmbH of Hamburg, Germany. 49Games GmbH’s main development was the annual winter and summer games for PC and consoles in Germany. Summer Athletics 2009 for Wii, released on July 24, 2009 was the largest collaborative effort, seeing nine of the eleven developers for .detuned credited on that game. An earlier collaborative effort is more closely related to the work of .detuned, a first person shooter game called .kkrieger. Released on April 10, 2004 for Windows PCs, .kkrieger was a product of the Breakpoint demoscene party in April 2004 in Bingen, Germany. It was the result of a challenge to create a first person shooter in the vein of Unreal Tournament and Quake but with the restriction of being 96KB in size. GameDeveloper has an interview with programmer Fabian Giesen (who was only 19 at the time!) and Nostalgia Nerd on YouTube has a great video documenting the development of .kkrieger that is worth a watch if you want to know more about how they accomplished this feat.
Sony Santa Monica Studios Producer Rusty Buchert announced .detuned on the PlayStation Blog on May 1, 2009. He said it would, “[offer] an abstract and surreal interactive experience like nothing else. It is not exactly a game or an art piece like Linger in Shadows. It allows you to create your own visual to accompany your favorite music tracks on the XMB, and using the SIXAXIS™ Wireless Controller, you will be able to manipulate the given scene by interacting with and modifying a man and his world. It even lets you tweak your music as you play with it.” Their announcement is already getting ahead of the “not a game!” crowd, though the comments on that PlayStation Blog piece are generally positive and welcoming.
.detuned would release on PSN for $2.99 on October 15, 2009. Games media reviews were limited, as most game “critics” were used to reviewing games such as Madden, Call of Duty, and Uncharted, but something like .detuned was challenging when approached from the limited scope of a consumer review with the stated goal being a buyer’s guide to “should you purchase this?” IGN gave it a 4/10, Bad, with Chris Roper saying, “Currently selling for $2.99 in the US PlayStation Store, that's about a dollar per minute of entertainment. If you have cash to blow and want to see one of the weirdest pieces of software on any system, go for it. Otherwise, just watch our videos and you'll get the point.” GamesRadar’s Shaun Curnow would rate .detuned 2.5/5 with its negatives being, “-Not really a game, -Won't amuse everyone, -Won't amuse for long.” Again we hit the same reactions and falsehoods of criticism, not being a [mainstream’s expectation of a] game, not reaching some imagined universal appeal, and not lasting long enough to be “worth” it in the mental formula of $/hour. A retrospective review in 2019 from Gaming Audio News’ Trevor Chan would say, “It didn’t take long to wonder if it was worth paying the small amount of money for this bite-sized experience. It’s a great snapshot of a bygone decade. Does that mean one would go recommending .detuned as a ‘must-play’? No, but it is worth experiencing, even if just for a few minutes.” Again we come back to reviews being centered on this one point: Monetary Price. No matter the time it costs you, don’t go questioning whether those 40 hours in the latest RPG were truly meaningful, be glad you got more bang for your buck compared to this!
As mentioned by GameSpy’s Sterlin McGarvey in their news writeup for .detuned’s announcement, Linger in Shadows, and .detuned, were positively regarded for their easy trophies, “It [Linger in Shadows] was also a handy way to clean up on some good trophies, another reason why many people picked it up.” This sentiment was echoed in PlayStation The Official Magazine Issue 22 for August 2009 whose Trophies for Cheaters by Carlos Ruiz includes entries for Linger in Shadows, Flower, and Noby Noby Boy. I admit, my purchase of Linger in Shadows and .detuned at the time was more for their easy trophies than interest in the demoscene or its history. It is only while looking back do I realize there is a richer field to examine than just a quick injection of trophy points.
What is .detuned if not a video game? The visual effects manually activated by the player suggests it is a visualizer meant to mesmerize you while enjoying your custom tracks imported onto the PlayStation 3 hard drive. Reliance on human, rather than machine, for these effects means the attention of the player is squarely on enacting movement to the rhythm of whatever track is currently being played instead of enjoying the track and visuals meshed together. Due to this, it reads as more of a toy, something to pick up and play around with, poking at its odds and ends, seeing what action you can provoke and manipulate, before setting it down and moving on. This briefness of experience and interest may be why publisher, reviewer, and player alike referred to it as, “not a game.” It failed, intentionally so, to entertain for multiple hours, tell a story, or offer a high score. Still, I find it limiting to restrict the moniker of “game” from .detuned and its ilk. The player can manipulate and control aspects programmed by the developer, engaging in a unique kind of conversation between player and program that can only happen in video games.
As a game, what does .detuned evoke? The first time through was spent poking and prodding at the game, seeing what the different button press combinations could accomplish and create in the suited man. The default track demo that you can watch to get an overall feel for what this game is capable of producing works well, though the cuts and camera movement seem way out of range of what the player is capable of producing when in control. The lack of an editable timeline means creating your own music video with this game as the base foundation would be a waste of time and effort. So, as before, it remains a toy, something you can plug a music track into in order to have some fun pulling and twisting it around in your hand, not quite as literal given the capability of the Sixaxis within the PlayStation 3 controller (though maybe for the best given the Sixaxis never achieved much in its lifetime). One of the tracks I chose to test out was probably the most apt for a repeatable batch of animations: Daft Punk’s “Around the World.” Some other experiments were on Blink 182’s “What’s My Age Again?” and M.O.O.N.’s “Hydrogen” from the Hotline Miami soundtrack. Unfortunately I did not realize I could turn off the sound effect to the “crank” noise when using the analog sticks to forward and rewind the animations. Due to this, my experience, and footage, are inseparable from the annoying click-clack of the crank.
In 2012 Q-Games released a game very similar to .detuned in intention, PixelJunk 4am, a game for the PlayStation Move motion controller that allowed players to, “Mix and create your own music with the PlayStation®Move. ‘Paint’ with sound in 3D space by pulling new tracks from the surrounding audio palette.” Though more social-minded than .detuned was, the audio effect manipulation and importing of your own custom tracks, aka your iTunes library, is very similar to the sandbox playground of .detuned, and is something I hope to try out once I obtain a PlayStation Move myself.
Some members of .theprodukkt continue to work in the demoscene today. Dierk Ohlerich (chaos) is an organizer for The Revision, a German demoparty that continues even to this year with an event in April 2023. Thomas Mahlke (fiver2) has continued working in the demoscene as well, most often with the group Farbrausch, one of the groups shouted out in Linger in Shadows. Tammo Hinrichs (kb) has also helped organize The Revision, and continues to make music for demos. Sebastian Grillmaier (wayfinder) has continued to create music for the scene and even provided the theme music for The Revision 2022. Christoph Mütze (giZMo) also appears to have remained active in the scene contributing to projects as late as 2021. Fabian Giesen (ryg) currently works at RAD Game Tools in Kirkland, Washington and maintains his blog to this day. Bleick Bleicken (mcfly) has most recently worked as an art director for Chorus developed by Deep Silver. I had trouble looking for any recent output from Oliver Waechter (joey) and Uwe Meier (moonlay). I believe Thomas Heinrich (aTom) is this same Thomas Heinrich on Twitter who links to Glare Productions as his current place of employment. Lastly Leonard Ritter (paniq) is currently a co-founder and developer at Duangle working on a crowdfunded game called Nowhere, an “alien life simulator.” The game has been in development since 2011 though sadly it appears the latest update was in March 2021.
Ever since my article on the short lived studio Endrant I’ve always wondered where these groups of people end up long after this project I’ve just played was probably last on their mind. Thankfully, in the comments of that Nostalgia Nerd video YouTube on .kkrieger there is a message from Tammo “kb” Hinrichs posted in October 2022 who gives an update on where the team is at now,
"Where are those guys now?" We exist, living our lives, all outside actual game development nowadays (because we wanted to have lives), but still quietly working away on various things that you might or might not have seen. Some of us are still active in the demoscene, and we're all fine, thank you :)
3 notes
·
View notes
Text
ECE Full Form, Course Details, Admission and Eligibility: A Complete Guide
Engineering continues to be a top choice for students after completing their higher secondary education. Among the many specializations offered, ECE is one of the most popular and versatile fields. In this blog, we’ll explore the ECE full form, course details, career scope, and how to get admitted into top institutions like Karpagam College of Engineering.
What is the ECE Full Form in Engineering?
The ECE full form is Electronics and Communication Engineering. It is a core branch of engineering that deals with the design, development, and application of electronic devices and communication systems. ECE combines aspects of electrical engineering and computer science, making it a highly dynamic and in-demand field in today’s digital world.
The ECE course provides students with in-depth knowledge about electronic circuits, communication protocols, signal processing, embedded systems, and wireless technologies.
ECE Course Overview
The ECE course is a four-year undergraduate program (Bachelor of Engineering or Bachelor of Technology) spread across eight semesters. It includes a blend of theoretical concepts, practical training, laboratory sessions, and real-time projects.
Key Subjects Covered in ECE:
Analog and Digital Electronics
Signals and Systems
Microprocessors and Microcontrollers
Digital Signal Processing
Communication Systems (Analog & Digital)
VLSI Design
Embedded Systems
Wireless Communication
Antenna and Wave Propagation
Internet of Things (IoT) and Machine Learning (Advanced topics)
Students also undergo internships and participate in projects that expose them to real-world applications, preparing them for careers in core and IT sectors.
Career Opportunities after ECE
Graduates of the ECE course have a wide range of career options in both government and private sectors. With electronics being the backbone of today’s technology and communication driving every industry, ECE professionals are always in demand.
Popular Job Roles for ECE Graduates:
Electronics Design Engineer
Communication Engineer
Embedded Systems Developer
Network Planning Engineer
Signal Processing Analyst
VLSI Engineer
IoT Developer
Telecom Engineer
Software Developer (due to coding skills gained during the course)
Additionally, ECE graduates can explore opportunities in PSUs (like BEL, BHEL, ISRO, DRDO), pursue higher studies (M.Tech, MBA), or even move into research and teaching.
Admission Process for ECE Course
Admission into the ECE course in most Indian colleges is based on entrance exams. However, specific procedures may vary depending on the institution and state.
Common Admission Pathways:
National-Level Entrance Exams: JEE Main is accepted by many top engineering colleges across India.
State-Level Entrance Exams: Some states conduct their own exams like TNEA (Tamil Nadu), KCET (Karnataka), etc.
Management Quota / Direct Admission: Some private colleges offer direct admission based on Class 12 marks.
Students must ensure they meet the eligibility criteria before applying.
Eligibility Criteria for ECE
To get admission into an ECE course, candidates generally need to fulfill the following criteria:
Educational Qualification: Must have completed 10+2 (Higher Secondary) or equivalent with Physics, Chemistry, and Mathematics as compulsory subjects.
Minimum Marks: Most colleges require a minimum of 50% aggregate in PCM (relaxation for reserved categories may apply).
Age Limit: There is usually no upper age limit, but candidates should meet the age criteria set by entrance examination authorities.
Why Choose Karpagam College of Engineering for ECE?
Located in Coimbatore, Karpagam College of Engineering (KCE) is a premier institution offering high-quality engineering education, including a comprehensive ECE course.
Highlights of ECE at Karpagam College of Engineering:
Industry-Relevant Curriculum: Updated regularly to include the latest technologies such as IoT, AI, and 5G.
Experienced Faculty: A team of qualified professors and researchers with industry expertise.
Advanced Laboratories: Well-equipped labs for electronics, embedded systems, and communication projects.
Placement Opportunities: Strong campus recruitment from top companies like TCS, Infosys, Wipro, Cognizant, and core companies.
Research and Innovation: Active involvement in research projects, paper presentations, and national-level competitions.
Karpagam College not only focuses on academic excellence but also prepares students for the practical challenges of the tech world.
Conclusion
To sum up, the ECE full form is Electronics and Communication Engineering—a powerful and future-ready branch of engineering. It opens up numerous career opportunities in electronics, IT, telecom, and automation sectors. By choosing a reputed institution like Karpagam College of Engineering, students can ensure a solid academic foundation, industry exposure, and career growth in the evolving world of technology.
Website:https://kce.ac.in/
Address:Myleripalayam Village, Othakkal Mandapam Post, Coimbatore - 641032, Tamilnadu, India
+91 82203 33750, +91 82203 33620 +91 422 2619005, +91 422 2619006
Mail id :[email protected]
0 notes
Text
🚀💸 OpenAI Enters Hardware with $6.4 Billion Acquisition
Hold onto your GPUs, crypto enthusiasts! OpenAI just decided to shake things up by dropping an eye-watering $6.4 billion on Jony Ive's io Products, and you know what that means—time to dust off those old hardware memes! 🎉 This is OpenAI’s first venture into hardware, solidifying their dominance in the AI-powered computing device universe and sending ripples through the tech pond like your favorite meme going viral. 😂
But wait, it gets better! Renowned design guru Jony Ive is hopping aboard as the creative head, while Sam Altman and his crew of genius whirlwind engineers and physicists are set to revolutionize our daily lives. Sam confidently declared, “We gathered together the best hardware and software engineers, the best technologists, physicists, scientists, researchers, and experts in product development and manufacturing.” Talk about assembling the Avengers of tech! 💪💥 - OpenAI Announcement
📉 Market Reactions Mixed on OpenAI's Hardware Move
Tech pundits are buzzing like the latest meme format, with some praising this bold expansion, while others exhibit skepticism (because when has tech ever gone wrong, right?). Analysts reckon this could trigger major industry shifts but brace yourselves; regulatory bodies are probably sharpening their pencils as we speak. 🖋️📑
What’s next? Expect disruptions and possible innovations as OpenAI’s foray into hardware may just create a brand-new consumer electronics category. Look out world, the tech shift we never knew we needed is on the horizon! 🌅
📲 OpenAI's Move Echoes Tech Giants' Hardware Strategies
If you think back, it's easy to see the trend: tech behemoths like Google and Apple have jumped into the hardware ring, leaving patterns like breadcrumbs for others to follow. OpenAI’s big bucks acquisition is following suit, and industry experts from Kanalcoin warn us that we might be on the verge of another tech revolution. Buckle up for possible innovation explosions that might just be more exciting than bagels on a Sunday morning! ��💣
Disclaimer: This website provides information only and is not financial advice. Cryptocurrency investments are risky. We do not guarantee accuracy and are not liable for losses. Conduct your own research before investing.
Read the full story on Kanalcoin.com and tell us your thoughts! Are you hyped for this hardware takeover or are you ready to make a meme out of it? Let’s hear your hottest takes in the comments below! 🔥👇 #OpenAI #CryptoNews #Innovation #TechTrends #Investment #DisruptiveTech
0 notes
Text
Understanding Different Types of CNC Machines
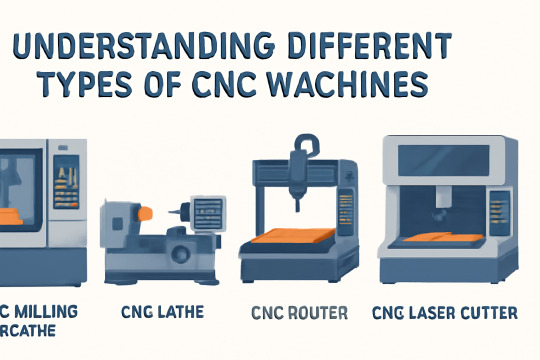
Introduction to CNC Machines
CNC machines have revolutionized manufacturing and production industries across the globe. These advanced tools have transformed how products are designed, engineered, and built, enabling unprecedented precision and efficiency. But what exactly is a CNC machine, and why is it so vital in modern production?
CNC stands for Computer Numerical Control, a system that uses computer software to control the movement of machinery and tools. Unlike traditional manual machining, CNC machines execute pre-programmed sequences with incredible accuracy, allowing for the production of complex parts and components with minimal human intervention. This precision reduces errors, waste, and production times significantly.
CNC machines can work with a wide variety of materials, including metals, plastics, wood, and composites. This versatility makes them indispensable in industries such as aerospace, automotive, electronics, and medical device manufacturing. Their ability to produce intricate designs and maintain consistency over high production runs is unmatched by conventional methods.
Basic Categories of CNC Machines
There are several primary types of CNC machines, each designed to perform specific functions in the manufacturing process. Understanding these categories helps in selecting the right machine for your project’s needs.
CNC Milling Machines
CNC milling machines are among the most versatile and commonly used CNC equipment. These machines use rotating cutting tools to remove material from a workpiece to create various shapes, holes, and profiles. Milling machines can operate along multiple axes — from simple 2-axis milling to complex 5-axis or more — allowing for intricate and precise machining.
Some of the popular subtypes of CNC milling machines include vertical mills, horizontal mills, and gantry mills. Vertical milling machines have the spindle oriented vertically and are widely used for precision tasks. Horizontal mills, where the spindle lies horizontally, are suitable for heavy-duty material removal and larger parts. Gantry mills offer an extended working area, often used for large, complex parts.
CNC milling machines find applications across many sectors, including aerospace parts manufacturing, automotive components, and even intricate molds for plastic injection molding. Their adaptability makes them a staple in many machine shops.
CNC Turning Machines (Lathes)
Turning machines, commonly known as CNC lathes, operate by rotating the workpiece against a cutting tool, which removes material to form cylindrical shapes. Unlike milling, which moves the cutting tool, turning rotates the material itself. This method is especially effective for producing symmetrical parts like shafts, bolts, and pulleys.
Modern CNC lathes can be equipped with multiple axes and tools, allowing for highly complex shapes and features. The ability to perform drilling, threading, and grooving operations on a single machine improves efficiency and reduces handling time.
If your project involves creating round or tubular parts, CNC turning machines are often the best choice. They provide excellent surface finishes and high repeatability, making them ideal for high-volume manufacturing.
Exploring CNC Machining Services
When looking to manufacture precision parts efficiently, many businesses turn to cnc machining services. These services offer access to a wide range of CNC machines and expert operators who can handle everything from design assistance to final production. Utilizing professional machining services means you benefit from optimized setups, high-quality materials, and fast turnaround times without investing heavily in your own equipment.
By outsourcing your CNC machining needs, you gain flexibility and scalability, allowing your production to adapt quickly to changes in demand or product design. Whether you require small prototype runs or mass production, CNC machining services can tailor their approach to fit your project’s requirements.
Specialized CNC Machines
Beyond the basic milling and turning machines, the CNC world includes specialized equipment designed for cutting, shaping, and finishing with unique technologies.
Laser Cutting CNC Machines
Laser cutting machines use a focused beam of light to cut through materials with extreme precision. The laser heats the material until it melts or vaporizes, creating clean cuts with minimal kerf (cut width) and no mechanical contact.
This technology is excellent for processing thin metals, plastics, and even wood with intricate patterns or designs. Laser cutting is popular in industries requiring fine detail, such as electronics enclosures, signage, and jewelry manufacturing.
Advantages of laser cutting include reduced material distortion, fast processing speeds, and the ability to cut complex shapes without the need for expensive tooling. However, laser cutting is generally limited to thinner materials and may not be suitable for thick, dense metals.
Plasma Cutting Machines
Plasma cutting machines operate by sending a high-velocity jet of ionized gas (plasma) through an electrically conductive workpiece, melting the metal and blowing away the molten material. This method allows for fast cutting of thick metals that would be challenging with laser technology.
Plasma cutting is widely used in fabrication shops, automotive repair, and construction where precision is essential but not as fine as laser cutting. It’s cost-effective for medium to heavy-duty cutting applications and works well with materials like steel, aluminum, and stainless steel.
Compared to traditional cutting methods, plasma cutting reduces manual labor and speeds up production, making it a popular choice for large-scale metalworking.
Electrical Discharge Machines (EDM)
Electrical Discharge Machining is a unique CNC process where material is removed from a workpiece by electrical sparks. There are two primary types: Wire EDM and Sinker EDM.
Wire EDM uses a thin wire electrode to cut intricate shapes through electrically conductive materials.
Sinker EDM involves a shaped electrode that erodes the workpiece to form cavities or complex internal shapes.
EDM is highly effective for producing parts that are difficult to machine using conventional methods, such as hardened tool steel molds, dies, and complex internal geometries. Its precision can reach tolerances in the micrometer range, and it leaves excellent surface finishes.
This technique is invaluable in industries like aerospace, medical implants, and mold making, where exacting standards are mandatory.
Benefits of Using CNC Machines
Using CNC machines provides a wide array of advantages, which is why they have become the backbone of modern manufacturing.
Precision and Accuracy
CNC machines follow digital instructions with extreme precision, often achieving tolerances within microns. This accuracy ensures parts fit together perfectly, reducing rework and improving overall product quality.
Increased Production Speed
Because CNC machines operate continuously and quickly, they drastically cut down production times compared to manual machining. Their ability to automate complex tasks means higher throughput and faster time-to-market.
Consistency and Repeatability
Once a program is set, CNC machines produce identical parts consistently, even across thousands of runs. This repeatability is crucial in industries where uniformity directly impacts safety and functionality.
Reduced Human Error
Automation reduces the potential for mistakes caused by fatigue, misreading blueprints, or manual setup errors. CNC machines execute the program exactly as written, leading to fewer defects and less scrap.
Factors to Consider When Choosing CNC Machines
Choosing the right CNC machine depends on several critical factors to match your project’s unique needs.
Material Type and Thickness: Some machines are better suited for metals, others for plastics or composites. Material thickness also influences the choice, especially for cutting processes.
Complexity of Design: More complex parts may require multi-axis machines or specialized cutting methods.
Production Volume: High-volume production benefits from machines with faster cycle times and automation options, while prototyping might prioritize flexibility.
Budget and Cost Efficiency: Initial investment, operating costs, and maintenance should be balanced against the expected production output and quality requirements.
Selecting the right machine upfront prevents costly adjustments and downtime later.
The Future of CNC Technology
The future of CNC machining looks exciting as advances continue to push boundaries.
Automation and Smart CNC Machines
Integration with robotic systems and automated material handling will further increase efficiency. Smart CNC machines equipped with sensors can monitor tool wear, adjust parameters in real-time, and predict maintenance needs.
Integration with AI and IoT
Artificial intelligence and the Internet of Things will enable machines to learn from previous runs, optimize cutting paths, and communicate seamlessly with other factory systems, creating truly smart manufacturing environments.
Sustainability and Eco-Friendly Manufacturing
As environmental concerns grow, CNC technology is evolving to reduce energy consumption and waste. Efficient machining processes, recyclable materials, and eco-friendly coolants are becoming standard.
Understanding the types of CNC machines and their applications helps manufacturers and businesses make informed decisions that drive quality, efficiency, and innovation. Whether you need simple milling or complex EDM, there’s a CNC solution to fit every need and push your production capabilities forward.
0 notes
Text
BCA: Your Gateway to the Digital World

From fintech apps that simplify payments to AI-driven chatbots that shape customer service, software is the invisible engine behind modern life. If you’d like to help build that engine—but prefer a three-year program focused squarely on computing—the Bachelor of Computer Applications (BCA) could be your ideal launchpad.
Why Choose a BCA?
A BCA blends the core principles of computer science with practical training in programming, databases, networking, web development, and emerging tech such as cloud and cybersecurity. Compared to a B Tech in Computer Science, the curriculum is lighter on advanced mathematics and electronics, but richer in software-centric labs and projects.
BCA Admission: Pathways & Timelines
BCA admission processes generally fall into three buckets:
Merit-Based Admission
Public universities and many well-known private institutes admit students based on 12th-grade board marks. You submit an online form with your marksheets, the college releases a cutoff list, and if your aggregate meets or exceeds that cutoff, you secure a seat. Merit lists typically roll out between May and July, right after board results are declared.
Entrance-Exam Admission
Some autonomous or deemed universities conduct entrance tests covering basic math, logical reasoning, and computer awareness. Examples include IPU-CET, CUET, and SET. Scoring well not only wins you a seat but can also unlock scholarships.
Direct Admission & Management Quota
Smaller private colleges often keep a few seats open for spot admission. While the fees can be higher, this route helps students who decide late or narrowly miss cutoffs.
Regardless of the pathway, applying early, watching notification dates, and keeping digital copies of certificates handy will save you stress.
youtube
BCA Eligibility: Are You Qualified?
BCA eligibility rules are refreshingly straightforward:
Academic Background: Most institutions require candidates to have passed 10+2 (or equivalent) with a minimum aggregate of 45–50 %. Science and Commerce students are equally welcome; Arts students are accepted in many colleges too, provided they studied mathematics, informatics, or computer science as an elective.
Subject Requirements: While a few top-tier universities insist on Mathematics at the +2 level, many accept Computer Science, Information Practices, Statistics, or even Business Mathematics instead.
Age Limit: A handful of state universities cap entry at 21 years for the general category and 24 for reserved categories, but the majority impose no age restriction.
BCA Fees: Crunching the Numbers
Investing in any degree means weighing upfront costs against future earnings. BCA fees depend mainly on the institution’s status and location:

BCA Placement: What Awaits After Graduation?
A degree is only as good as the opportunities it unlocks. The good news: BCA placement statistics have surged in recent years because IT services, startups, and even non-tech firms crave digital talent. Here’s what the landscape looks like:
Roles Offered
Software Developer / Trainee Engineer
QA / Test Engineer
Technical Support Associate
Web Designer / UI Developer
Data Analyst (entry-level)
Cloud Support Engineer
Key Recruiters
IT giants such as TCS, Infosys, Wipro, HCL, and Cognizant routinely visit top campuses. Product startups—especially in fintech and ed-tech—are emerging recruiters. Non-tech conglomerates like Reliance and Aditya Birla also hire BCAs for in-house IT teams.
The Road Ahead
Choosing a career is part aspiration, part strategy. A BCA gives you the coding chops, domain knowledge, and project experience to join the tech workforce quickly—without the four-year commitment of an engineering degree. By understanding the BCA admission cycle, confirming your eligibility, budgeting for fees, and maximizing placement opportunities, you position yourself at the forefront of India’s digital revolution. With curiosity as your compass and code as your craft, the future is yours to script.
0 notes
Text
How to Establish an IT Company in India: Legal Procedure, Dispute Management & Key Insights under BNS
Learn how to establish an IT company in India with a step-by-step legal guide, including company registration, dispute resolution strategies, and key BNS (Bharatiya Nyaya Sanhita) provisions.
Authored by B S Makar, Advocate & Solicitor.
Introduction
India’s IT sector is booming and continues to attract entrepreneurs from across the globe. Establishing an Information Technology (IT) company in India involves a blend of regulatory compliance, strategic planning, and legal foresight. Whether you’re a tech visionary or a legal advisor helping a startup, understanding the legal landscape — including the role of Bharatiya Nyaya Sanhita (BNS) in dispute resolution — is crucial.
This blog provides a step-by-step guide to setting up an IT company in India, navigating legal formalities, managing disputes effectively, and staying compliant with the latest Indian laws.
1. Preliminary Planning: Business Structure Selection
Before registration, choose the most suitable business structure:
Private Limited Company (most preferred for IT firms due to limited liability and scalability)
Limited Liability Partnership (LLP)
Sole Proprietorship
Partnership Firm
Each structure has different tax implications, compliance requirements, and funding potential.
2. Company Registration Procedure (MCA Compliance)
Registering a company in India is governed by the Ministry of Corporate Affairs (MCA) under the Companies Act, 2013.
Steps to Register:
Obtain Digital Signature Certificate (DSC)
Apply for Director Identification Number (DIN)
Name Reservation via RUN (Reserve Unique Name)
Incorporation through SPICe+ (Simplified Proforma for Incorporating Company Electronically)
Apply for PAN & TAN (automatically included in SPICe+)
Open a Current Bank Account in the Company’s Name
Timeframe:
Registration typically takes 7–10 working days if documents are complete.
3. Licensing & Tax Registrations
GST Registration (if turnover exceeds Rs. 20 Lakhs or Rs. 10 Lakhs in special category states)
Professional Tax Registration (if applicable in your state)
Import Export Code (IEC) (if offering services to overseas clients)
Software Technology Parks of India (STPI) Registration (for export incentives)
4. Data Protection, Cyber Law & IP Compliance
Draft IT Contracts: NDAs, Service Agreements, Terms of Use, Privacy Policies
Intellectual Property: Register trademarks, copyrights for proprietary software and logos
Data Protection: Comply with the Digital Personal Data Protection Act, 2023
Cyber Law: Be aware of offenses under the Information Technology Act, 2000 and BNS provisions related to cyber fraud
5. Dispute Management for IT Companies
Disputes in IT businesses can stem from client conflicts, IP theft, payment delays, or employee misconduct. Having a structured dispute resolution mechanism is vital.
Common Legal Disputes:
Breach of Software Licensing Agreements
Cybersecurity Breaches or Data Leaks
Intellectual Property Infringement
Breach of Confidentiality
Dispute Resolution Strategies:
Arbitration Clauses in contracts
Mediation or Conciliation before court action
Digital Evidence Handling in case of cybercrime
6. Criminal Provisions under Bharatiya Nyaya Sanhita (BNS)
The new Bharatiya Nyaya Sanhita (BNS), which replaces the Indian Penal Code (IPC), includes robust provisions for cyber-related offenses relevant to IT companies:
Key BNS Provisions:
Section 336: Cyber fraud and identity theft
Section 337: Unauthorized access to computer networks
Section 338: Tampering with electronic records and digital signatures
Section 337(3): Offense of phishing, hacking or introducing malware
These sections provide the basis for FIRs and legal action in case of digital or contractual fraud.
7. Case Study: Cyber Theft Resolved through Mediation
XYZ Technologies Pvt Ltd faced a major cyber breach due to insider theft. The data theft was reported under Section 336 BNS. Rather than pursuing lengthy litigation, both parties agreed to arbitration.
Outcome:
Damages of Rs. 25 Lakhs were recovered
The insider was barred from the industry for 5 years
Reputation of the company remained intact
8. Conclusion: Legal Preparedness Ensures Growth
The Indian IT industry is dynamic and full of potential. However, legal preparedness — right from company registration to dispute resolution — is critical for sustainable growth. By understanding new laws like BNS and embracing strong compliance protocols, startups can avoid legal pitfalls and focus on innovation.
Need Legal Assistance?
If you are planning to start an IT company in India or facing legal disputes in the tech domain, professional guidance is just a call away.
Author:
B S Makar, Advocate & Solicitor
669, Sector-64 (Phase -10), Mohali, Punjab
Website: www.makarlaws.com Contact: +91 9878131111 Location: Mohali, Punjab, India
0 notes
Text
Checklist to Keep Your Virtual PPOB GST-Compliant Year-Round
To remain Virtual PPOB GST compliant throughout the year, a regular and organized approach to taxation and documentation is the key. As the initial step, ensure that all invoices raised are GST compliant, mentioning GSTIN, SAC codes, taxable value, and tax rate. The monthly activities must comprise timely submission of GSTR-1 and GSTR-3B and reconciliation of Input Tax Credit (ITC) with GSTR-2B to ensure no mismatch. It's equally crucial to credit the GST paid within the set due dates in order to avoid interest
and fines. Quarterly, check vendor compliance, reconcile purchases and sales reports, and submit GSTR-4 if your Virtual PPOB is subject to the composition scheme. Annually, submission of GSTR-9 and, where needed, GSTR-9C is required in order to remain GST-compliant.

Establishing a GST-Compliant Virtual PPOB
Setting up a GST-compliant Virtual PPOB (Payment Point Online Bank) requires organizing your business structure according to Goods and Services Tax regulations from the beginning. Start with registering your business as GST and securing a valid GSTIN, which is obligatory for businesses dealing with taxable services. While providing services like mobile recharges, bill payments for utilities, and DTH services, make your invoices GST-compliant by including your GSTIN, SAC codes, taxable amount, and the applicable tax rate.
Select the proper tax category—normal or composition—according to your annual turnover and business model. Make use of GST-compliant accounting software to mechanize invoicing, tax computation, and return filing. You need to submit periodic GST returns like GSTR-1 and GSTR-3B, and keep proper records of all electronic transactions via your PPOB platform.
Accurate GST Registration and Updates
Proper GST registration and time updates are essential to ensure legal compliance and a hassle-free run in the Goods and Services Tax regime. At the time of registering for GST, proper details regarding business name, PAN, principal place of business, and classification of the right business activity using HSN/SAC codes must be furnished. For a Virtual PPOB or any service-based enterprise, selection of the appropriate nature of services and state-wise registration (if it is operating in more than one state) guarantees correct tax jurisdiction. After registration, enterprises are assigned a unique GSTIN, which should be quoted on invoices and communications. To remain compliant, changes in business structure—address updates, change in authorized signatories, or addition of new branches—need to be updated immediately on the GST portal via an amendment application. It is essential to keep your GST registration and updates accurate to avoid fines and legal consequences and to ensure trust with clients and suppliers by having updated information in all GST filings and verifications.
Invoice Management and E-Invoicing Compliance
Invoice Management & E-Invoicing Compliance
Issue GST-Compliant Invoice
Add supplier & recipient GSTIN, invoice number, date, HSN/SAC codes, taxable value, GST rate, and total amount.
Meet E-Invoicing Requirements (if applicable)
Compulsory for businesses having turnover over ₹5 crore (as per most recent threshold); invoices should be registered with Invoice Registration Portal (IRP).
Create IRN and QR Code
Upload invoice details to IRP to receive a distinct Invoice Reference Number (IRN) and dynamic QR code, which has to be printed on the end invoice.
Use GST-Compliant Accounting Software
Automate generation of invoices, IRN generation, and GST format compliance through tools embedded in NIC-IRP.
Store Digital Copies of Invoices
Save all issued and received invoices digitally for audit, reconciliation, and future reference.
Reconcile Invoices Monthly with GSTR-1 & GSTR-3B
Make sure to report all sales invoices correctly in monthly GST returns for claiming Input Tax Credit to prevent mismatches.
Prevent Manual Mistakes
Automate to the greatest extent possible to avoid GST calculation mistakes or omitting invoice information.
Renew Invoice Series Annually
Renew invoice serial number series at the beginning of every financial year, as is mandated under GST law.
Get E-Invoice Information into Returns
Make sure that e-invoice information auto-populates within GSTR-1 and reflects your monthly returns.
Timely Filing of GST Returns
File GSTR-1 (Outward Supplies)
File monthly on or before the 11th of next month (or quarterly under QRMP scheme). Ensures correct reflection of sales to customers and recipients.
File GSTR-3B (Summary Return)
Compulsory monthly/quarterly filing for reporting tax liability and availing Input Tax Credit (ITC). To be filed by the 20th, 22nd, or 24th, depending on your state and scheme.
Escape Interest & Penalties
Filing GST returns in time prevents late fees, interest, and GST registration cancellation.
Monitor Due Dates on a Regular Basis
Make use of compliance calendars, reminders, or accounting software to keep ahead of all the return deadlines.
File NIL Returns in Case of No Activity
Despite zero turnover during a period, NIL returns need to be filed in order to keep up with compliance and prevent system blocking.
Reconcile Before Filing
Align data from your books with GSTR-2B and earlier returns to avoid errors and minimize the likelihood of notices.
File GSTR-9 and GSTR-9C Every Year
Applicable for companies with annual turnover over ₹2 crore and ₹5 crore respectively.
Utilize GST Portal or Authorized Software
File returns through the official GST portal or authorized software connected with GSTN to provide secure and accurate filing.
Input Tax Credit (ITC) Reconciliation
Match Purchases with GSTR-2B: regularly reconcile ITC claimed in your books with the auto-generated GSTR-2B to ensure vendor compliance and avoid ineligible claims.
Verify Vendor Filings: Ensure suppliers have filed GSTR-1 correctly and on time so that their invoices reflect in your GSTR-2B.
Claim Only Eligible ITC: Follow GST rules to claim only ITC on goods/services used for business purposes; block credits (like on personal expenses) must be excluded.
Maintain Proper Documentation: Keep all purchase invoices, debit notes, and payment proofs organized as valid supporting documents for claiming ITC.
Timely Booking of Invoices: Book purchase invoices in the correct tax period; delayed entries can lead to missed ITC claims or notices from the department.
Reverse Ineligible ITC Promptly: Reverse ITC on unpaid invoices after 180 days or on ineligible goods/services to avoid penalties.
Adjust ITC in GSTR-3B: Make necessary additions/reversals in Table 4 of GSTR-3B based on reconciliation outcomes.
Use ITC Reconciliation Tools: Utilize accounting software or GST compliance platforms for automated Input Tax Credit (ITC) reconciliation and reporting.
Reverse Charge Mechanism (RCM) Compliance
Reverse Charge Mechanism (RCM) Compliance
Understand When RCM Applies
RCM compliance is necessary when GST is to be paid by the recipient, and not by the supplier—common in situations such as legal services, transport (GTA), or purchases from unregistered vendors.
Identify RCM Transactions
Categorize expenses such as import of services, security services, rent from unregistered individuals, and other notified services under RCM.
Self-Invoice for RCM Transactions
Create a self-invoice for each such applicable RCM transaction where the supplier has not charged GST.
Pay Cash Only
GST under RCM has to be paid in cash (in electronic cash ledger), but not through Input Tax Credit (ITC).
Claim ITC on RCM Tax Paid
Once payment under RCM is made, you can claim the same as Input Tax Credit, subject to the condition that the supply is for business purposes and otherwise qualifying.
Report in GSTR-3B Correctly
Mention outward RCM liability in Table 3.1(d) and ITC in Table 4(A)(3) of GSTR-3B.
Keep Comprehensive RCM Records
Retain records like self-invoices, payment receipts, and RCM ledger postings for audit and compliance purposes.
Check RCM Applicability Periodically
Regularly review your business transactions to look for new RCM notifications or changes in applicability.
Year-End Compliance Activities
Year-End Compliance Activities
Reconcile All GST Returns
Reconcile all GST returns (GSTR-1, GSTR-3B, GSTR-9, etc.) to reflect accurately sales, purchases, tax liabilities, and ITC claims.
File GSTR-9 (Annual Return)
File GSTR-9 on or before 31st December for firms with turnover more than ₹2 crore. It combines all the information filed through monthly or quarterly returns.
File GSTR-9C (Reconciliation Statement)
If your turnover crosses ₹5 crore, submit GSTR-9C, which contains audited financial statements of a Chartered Accountant (CA).
Reconcile Input Tax Credit (ITC)
Verify that all ITC availed throughout the year is valid, properly reported, and backed by proper documents, such as invoices and payments.
Reconcile Accounts with GST Returns
Align the books of accounts of the business with the GST returns to verify that there is no mismatch in reported sales, purchases, and tax dues.
Guarantee Compliance with E-Invoicing
Scan all e-invoicing compliance and guarantee all eligible invoices registered in the Invoice Registration Portal (IRP) with the suitable IRN and QR code.
Review Pending Payments and Liabilities
Identify pending GST payments and guarantee these are paid in full before end-of-year so no penalties or interest are applicable.
Audit Vendor and Customer GST Compliance
Ensure that all the suppliers and recipients have submitted their GST returns and that ITC claims are not being held back because of non-compliance from suppliers.
Conclusion
In summary, GST compliance is a year-round obligation that must be given high priority by businesses, particularly Virtual PPOBs. By keeping track of timely GST return filings like GSTR-1 and GSTR-3B, and regularly dealing with invoices and ITC reconciliation, businesses can avoid penalties and provide correct tax reporting. Reverse Charge Mechanism (RCM) rules must be understood and implemented for particular transactions to remain compliant. While nearing the end of the year, the companies need to concentrate on certain year-end compliances like depositing GSTR-9 and GSTR-9C, reconciliations of accounting, and properly disclosing tax payables and tax credits. Maintenance of regular updations in GST details of registration along with verifying compliance of vendors as well as customers is equally crucial. Through the use of technology to mechanize tasks and make processes efficient, companies are able to minimize the chances of errors and increase efficiency, providing long-term financial stability and efficient operations.
0 notes
Text
Cybersecurity: Safeguarding the Digital Frontier
Introduction
In our increasingly interconnected world, the security of digital systems has never been more critical. As individuals, corporations, and governments digitize operations, data becomes a prime target for malicious actors. Cybersecurity, once a niche concern, is now a cornerstone of digital strategy. It encompasses the practices, technologies, and processes designed to protect systems, networks, and data from cyber threats. With the rise of cybercrime, which causes trillions in damages annually, understanding cybersecurity is essential — not just for IT professionals, but for anyone using the internet.
1. What is Cybersecurity?
Cybersecurity refers to the practice of defending computers, servers, mobile devices, electronic systems, networks, and data from malicious attacks. It is often divided into a few common categories:
Network security: Protecting internal networks from intruders by securing infrastructure and monitoring network traffic.
Application security: Ensuring software and devices are free of threats and bugs that can be exploited.
Information security: Protecting the integrity and privacy of data, both in storage and transit.
Operational security: Managing and protecting the way data is handled, including user permissions and policies.
Disaster recovery and business continuity: Planning for incident response and maintaining operations after a breach.
End-user education: Teaching users to follow best practices, like avoiding phishing emails and using strong passwords.
2. The Rising Threat Landscape
The volume and sophistication of cyber threats have grown rapidly. Some of the most prevalent threats include:
Phishing
Phishing attacks trick users into revealing sensitive information by masquerading as trustworthy sources. These attacks often use email, SMS, or fake websites.
Malware
Malware is any software designed to harm or exploit systems. Types include viruses, worms, ransomware, spyware, and trojans.
Ransomware
Ransomware locks a user’s data and demands payment to unlock it. High-profile cases like the WannaCry and Colonial Pipeline attacks have demonstrated the devastating effects of ransomware.
Zero-day Exploits
These are vulnerabilities in software that are unknown to the vendor. Hackers exploit them before developers have a chance to fix the issue.
Denial-of-Service (DoS) Attacks
DoS and distributed DoS (DDoS) attacks flood systems with traffic, overwhelming infrastructure and causing service outages.
3. Importance of Cybersecurity
The consequences of cyberattacks can be severe and widespread:
Financial Loss: Cybercrime is estimated to cost the world over $10 trillion annually by 2025.
Data Breaches: Personal data theft can lead to identity fraud, blackmail, and corporate espionage.
Reputational Damage: A data breach can erode trust in a company, damaging customer relationships.
Legal Consequences: Non-compliance with data protection laws can lead to lawsuits and hefty fines.
National Security: Governments and military networks are prime targets for cyber warfare and espionage.
4. Key Cybersecurity Practices
1. Risk Assessment
Identifying and prioritizing vulnerabilities helps organizations allocate resources efficiently and address the most significant threats.
2. Firewalls and Antivirus Software
Firewalls monitor incoming and outgoing traffic, while antivirus software detects and removes malicious programs.
3. Encryption
Encryption protects data by converting it into unreadable code without a decryption key, ensuring data privacy even if intercepted.
4. Multi-Factor Authentication (MFA)
MFA adds a layer of protection beyond passwords, requiring users to verify identity through additional means like OTPs or biometrics.
5. Regular Updates and Patching
Cybercriminals often exploit outdated systems. Regular software updates and security patches close these vulnerabilities.
6. Backups
Frequent data backups help in recovery after ransomware or system failure.
5. Cybersecurity for Individuals
Individuals are often the weakest link in cybersecurity. Here’s how to stay safe:
Use strong, unique passwords for every account.
Be cautious of unsolicited emails or messages, especially those requesting personal information.
Regularly update devices and apps.
Enable two-factor authentication wherever possible.
Avoid public Wi-Fi for sensitive transactions unless using a VPN.
6. Cybersecurity for Businesses
Businesses face unique threats and must adopt tailored security strategies:
Security Policies
Organizations should develop formal policies outlining acceptable use, incident response, and data handling procedures.
Employee Training
Staff should be trained to recognize phishing attacks, report suspicious behavior, and follow cybersecurity protocols.
Security Operations Center (SOC)
Many businesses use SOCs to monitor, detect, and respond to cyber incidents 24/7.
Penetration Testing
Ethical hackers simulate attacks to uncover vulnerabilities and test a company’s defenses.
7. Emerging Technologies and Cybersecurity
As technology evolves, so too do the threats. Here are some emerging fields:
Artificial Intelligence and Machine Learning
AI enhances threat detection by analyzing massive datasets to identify patterns and anomalies in real-time.
Internet of Things (IoT)
With billions of connected devices, IoT expands the attack surface. Weak security in smart devices can create backdoors into networks.
Quantum Computing
While quantum computing promises advancements in processing power, it also threatens traditional encryption methods. Post-quantum cryptography is a new area of focus.
8. Cybersecurity Regulations and Frameworks
Governments and industries enforce standards to ensure compliance:
GDPR (General Data Protection Regulation): Governs data privacy in the EU.
HIPAA (Health Insurance Portability and Accountability Act): Protects health data in the U.S.
NIST Cybersecurity Framework: A widely adopted set of standards and best practices.
ISO/IEC 27001: International standard for information security management.
Compliance not only avoids fines but demonstrates a commitment to protecting customer data.
9. Challenges in Cybersecurity
Cybersecurity faces numerous challenges:
Evolving Threats: Attack techniques change rapidly, requiring constant adaptation.
Talent Shortage: There’s a global shortage of qualified cybersecurity professionals.
Budget Constraints: Small businesses often lack resources for robust security.
Third-Party Risks: Vendors and contractors may introduce vulnerabilities.
User Behavior: Human error remains one of the leading causes of security breaches.
10. The Future of Cybersecurity
Looking ahead, the cybersecurity landscape will be shaped by:
AI-powered threat detection
Greater emphasis on privacy and data ethics
Cybersecurity as a core part of business strategy
Development of zero-trust architectures
International cooperation on cybercrime
Conclusion
Cybersecurity is no longer optional — it’s a necessity in the digital age. With cyber threats becoming more frequent and sophisticated, a proactive and layered approach to security is crucial. Everyone, from casual internet users to CEOs, plays a role in protecting digital assets. Through education, technology, policy, and cooperation, we can build a safer digital world.
0 notes
Text
What Does a Service Mechanic Really Do? Inside the Shop

Service mechanics play a vital role in keeping our vehicles, machinery, and equipment running smoothly. But for many people, the daily tasks and responsibilities of a service mechanic remain somewhat of a mystery. What exactly does a service mechanic do? What skills do they need? And what is it like working inside the shop?
In this blog post, we will dive deep into the world of service mechanics, uncovering the different aspects of their job, from diagnosing complex issues to performing repairs and maintenance. Whether you're considering becoming a mechanic or simply want to learn more about the profession, this article will offer a comprehensive overview of what it’s like to work in this essential and dynamic field.
Understanding the Role of a Service Mechanic
At its core, a service mechanic is someone who specializes in diagnosing, repairing, and maintaining vehicles or machinery. Service mechanics can work in a wide variety of settings, including automotive repair shops, heavy equipment dealerships, manufacturing facilities, and even on-site at construction or mining sites. Their work is essential to ensuring that machinery, whether it's a car, truck, or industrial equipment, functions properly and is safe to use.
In essence, service mechanics are problem solvers. They use their expertise in mechanics, electrical systems, hydraulics, and computer systems to figure out what’s wrong with a machine and fix it.
Types of Service Mechanics
The role of a service mechanic can vary significantly based on their specialization. Some common types of service mechanics include:
Automotive Mechanics: These mechanics work with cars, trucks, motorcycles, and other vehicles. They are experts in internal combustion engines, brakes, transmission systems, and electrical systems.
Diesel Mechanics: Diesel mechanics specialize in the maintenance and repair of diesel engines, often found in trucks, buses, and heavy equipment. They have specific knowledge about diesel fuel systems, exhaust systems, and emission controls.
Heavy Equipment Mechanics: These professionals focus on repairing and maintaining large machinery used in construction, mining, or agriculture. This includes bulldozers, cranes, excavators, and more.
Industrial Machinery Mechanics: These mechanics work with machines found in manufacturing plants. They repair equipment like conveyor belts, pumps, and automated systems.
Aircraft and Marine Mechanics: These mechanics work on airplanes and boats. Their work requires specialized knowledge in aviation or marine engineering, as well as regulatory knowledge and safety certifications.
Though the job may look different depending on the field, the fundamental skills remain the same: diagnosing issues, repairing parts, and performing routine maintenance to keep equipment running.
Skills and Education Required
Becoming a service mechanic is not a straightforward path, but it is highly rewarding for those who enjoy hands-on work and problem-solving. The skills required to be an effective mechanic can be grouped into three major categories: technical, physical, and interpersonal.
Technical Skills: A service mechanic must have a solid understanding of mechanical systems. Whether it's an internal combustion engine or a complex hydraulic system, mechanics need to know how the various parts of a machine or vehicle work together. Additionally, modern machinery often involves electronics, so mechanics must also be familiar with computer diagnostics, wiring, and even software systems.
Physical Skills: Mechanics need to be comfortable with physical work, including lifting heavy objects, using specialized tools, and performing repairs in sometimes cramped or difficult spaces. Physical stamina is important, as the work can involve bending, kneeling, and standing for extended periods.
Interpersonal Skills: Communication is another key skill. Service mechanics need to explain technical problems to clients, especially when they are not familiar with machinery. Additionally, mechanics often work as part of a team and need to be able to collaborate and communicate effectively with other mechanics and staff.
In terms of formal education, a high school diploma is typically the minimum requirement to become a service mechanic. However, many mechanics pursue additional training through technical schools or community colleges, where they can gain certifications in specific areas like automotive repair, diesel mechanics, or HVAC systems. Many automotive repair shops and equipment manufacturers also offer apprenticeship programs, allowing aspiring mechanics to learn on the job under the supervision of experienced professionals.
Daily Life Inside the Shop
The day-to-day work of a service mechanic involves a combination of hands-on repairs, diagnostics, customer interaction, and administrative tasks. Each day can bring a new challenge, requiring mechanics to use a diverse set of skills.
Diagnosing the Problem
A mechanic’s first job is often diagnosing the issue with a vehicle or machine. This can be tricky, as mechanical problems are not always obvious. Sometimes, the problem is easy to spot: a flat tire, a broken belt, or an obvious leak. However, many issues require more extensive investigation. For example, a vehicle might have a strange noise that doesn’t immediately indicate where the problem lies. In these cases, mechanics use a variety of tools to pinpoint the issue.
Modern mechanics have access to sophisticated diagnostic tools that can help identify issues quickly. For example, an automotive mechanic might plug a scanner into a car’s computer system to retrieve error codes that point to specific parts of the vehicle, such as the engine or transmission. For heavy equipment or industrial machinery, mechanics might use sensors or even drone technology to inspect hard-to-reach parts.
Repair and Maintenance Work
Once the problem is diagnosed, the mechanic must take the necessary steps to repair the issue. This often involves disassembling parts of the vehicle or machine, replacing worn-out components, and reassembling everything to ensure it works as intended.
For example, replacing the brake pads on a car involves lifting the vehicle, removing the wheel, taking apart the brake system, installing new brake pads, and then reassembling everything and testing the system to ensure it functions properly. Similarly, a diesel mechanic might need to remove and replace an entire fuel injector system if it’s not working.
Mechanics also perform routine maintenance work, which is just as important as repairs. This includes tasks like oil changes, fluid checks, tire rotations, and brake inspections. Regular maintenance is essential to preventing breakdowns and extending the life of the machinery or vehicle.
Working with Tools and Equipment
A mechanic’s toolbox is an extension of their skillset. Mechanics use a wide range of hand tools, power tools, and specialized equipment to perform their work. Some of the most commonly used tools include:
Wrenches and Sockets: Used to tighten or loosen nuts and bolts.
Screwdrivers: Essential for removing screws in a variety of sizes.
Pliers: Used for gripping, bending, and cutting materials.
Diagnostic Scanners: Used in modern automotive repair to retrieve error codes from the vehicle’s computer system.
Hydraulic Lifts: Used to raise heavy vehicles or machinery to make repairs or maintenance tasks easier.
Lathes and Milling Machines: Common in industrial settings to machine parts that are no longer available.
The constant advancement of technology means that mechanics must continually update their knowledge and toolset to keep up with innovations in machinery and vehicles.
Customer Interaction
Customer service is another important aspect of the service mechanic’s job. Mechanics often communicate directly with customers, explaining what issues they’ve identified, how the repairs will be carried out, and how much the repair will cost. In some cases, mechanics must also give customers advice on maintenance or when to replace equipment to avoid costly repairs down the road.
In customer-facing roles, a mechanic’s ability to explain complex technical issues in simple terms is key to building trust and ensuring satisfaction. Mechanic shops with strong customer service often get repeat business, as satisfied customers return for routine maintenance and refer others to the shop.
Challenges of the Job
Though the work of a service mechanic is rewarding, it can also be challenging. The job requires a mix of physical stamina, technical expertise, and problem-solving skills. Additionally, there are a few challenges that mechanics regularly face:
Constant Learning: With the rapid pace of technological advancement, mechanics must keep learning to stay ahead. Newer vehicles and machinery often include complex systems that mechanics may not have encountered before, requiring them to continuously update their skills.
Physical Demands: The work can be physically exhausting. Mechanics often work in tight spaces, under vehicles, or around heavy equipment. Lifting heavy parts and working in uncomfortable positions can take a toll on the body over time.
Tight Deadlines: Many mechanics work under pressure, particularly in busy shops. When vehicles or equipment break down unexpectedly, customers often expect a quick turnaround. Meeting these demands while ensuring that the repairs are done correctly can be stressful.
Working with Hazardous Materials: Mechanics often work with hazardous materials, such as oils, solvents, and chemicals, which must be handled properly to avoid safety risks. Proper training and adherence to safety regulations are essential in avoiding accidents and maintaining a safe work environment.
Conclusion
Service mechanics are the unsung heroes who ensure that our vehicles, machinery, and equipment are in top working condition. From diagnosing problems and repairing faulty systems to performing routine maintenance, their work is both diverse and challenging. As technology continues to evolve, the role of a service mechanic will likely become even more complex, requiring ongoing education and adaptation.
For anyone considering a career as a service mechanic, the road is not always easy, but it is undeniably rewarding. Whether it's working with cutting-edge technology in automotive repair or maintaining heavy equipment on a construction site, being a service mechanic offers a unique and fulfilling way to apply technical expertise and problem-solving skills. Inside the shop, mechanics truly are the backbone of industries that rely on machinery to keep the world moving.
0 notes