#encryption devices
Explore tagged Tumblr posts
Text
Why is technology so nice until you have no internet access then it becomes the worst thing in the whole universe
#trying to transfer pictures to my ipad but im not allowed to do that because of some encryption bullshit#gott download itunes in my pc vut it cant be that easy no#i probably have to sign in then do some other shit i cant do because i dont have internet access in these devices#delete later#rambling#600 dollar paper weight
16 notes
·
View notes
Text
all day I’ve been complaining to people because I looked up the third party the place where I study uses to monitor the WiFi for ‘malicious or dangerous activity’ and it’s just plain creepy. Not as in like “I don’t like my searches being looked at but I have to tolerate it” as in “if you disconnect from the WiFi then reconnect to it it scans anything you did while disconnected at home the next time you connect, builds ‘user profiles’ with everything you look up, checks things you type offline, and can access your personal cloud storage”. And all fucking day I’ve been telling people this and they’ve gone ‘haha well I’ve got nothing to hide it can’t be that bad’ and I felt like I was going crazy. Then I got home and told my father and he just said “that sounds like a huge violation of the data protection act” and I felt so relived I wasn’t going crazy for thinking this was bad.
#like no one even seemed to fucking care? surely it’s illegal?#I’m sending them an email to try and get out of it because the website#claims that if you contact them saying you revoke consent they have to drop your device from it#but then I fear my organisation will just re-add me because I signed a contract that said they’d need to monitor#for malicious or inappropriate activity#but that was word for word all it said. I did not sign up for that#and even if I did I’m legally free to revoke that consent#but aghhhhhh why does no one even give a fuck.#like seriously#even things like WhatsApp that should be encrypted are scanned#because they have keyloggers#so the fact it’s encrypted on sending is. nothing.
8 notes
·
View notes
Text
they say that there's a point where you can have too much security and it impedes the usability of a system—however i'd like to commend online banking platforms for somehow simultaneously having security measures that make them incredibly inconvenient to use every day, whilst also offering fairly low actual security and being not particularly difficult to bypass if you're dedicated enough
#like none of the online banking platforms ive used have let me use an actual password?#nor do they let me set up 2fa with an authenticator app besides their own proprietary banking app#they all seem to send all verification codes by sms with the only way to authenticate otherwise is through their proprietary apps. which i#am not installing.#also perhaps this serves some purpose i dont understand but why do they frequently ask for the nth character of your pin or whatever#instead of asking for the whole pin?#like all the 'password' equivalents seem very easy to bruteforce and the sms verification can be bypassed by someone else just getting a#sim card for your number#and the fact that they never keep you logged in is annoying like i have full disk encryption on all my devices im not worried about someone#using my own device to access my bank account. i dont particularly think theres anyone trying to get into my bank account but if there were#they'd be getting in through their own device not mine... you can keep me logged in on mine...
6 notes
·
View notes
Text
Epilouge:


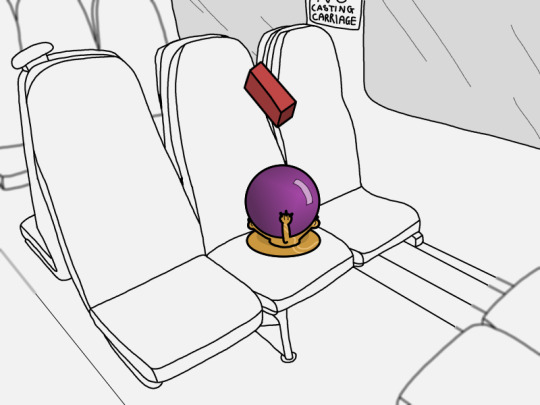
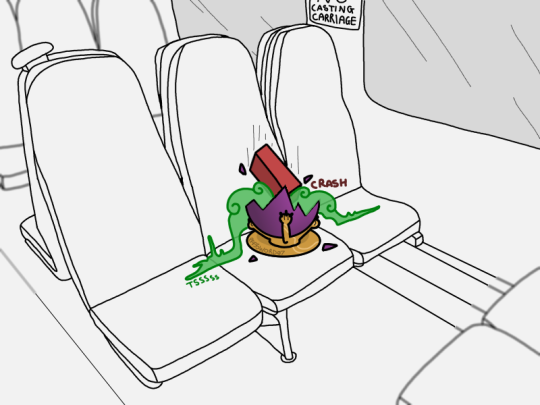


In a fantasy setting, my job would be exactly the same
#in my irl job to “brick” a device is to send a signal to it so as soon as it's turned on the hard drive encrypts itself#making the device useless and unusable#it's a security measure to ensure that if someone finds the device they can't access sensitive company data#yeah sure they can wipe the device and reinstall an OS and use it then#but IMPORTANTLY the company data is gone#we'll claim back the cost of the lost device from insurance#in a fantasy setting the solution to lost devices is more elegant#myart
38K notes
·
View notes
Text
Oh _lovely_. Everyone go turn this off:
Enhanced Visual Search in Photos allows you to search for photos using landmarks or points of interest. Your device privately matches places in your photos to a global index Apple maintains on our servers. We apply homomorphic encryption and differential privacy, and use an OHTTP relay that hides [your] IP address. This prevents Apple from learning about the information in your photos. You can turn off Enhanced Visual Search at any time on your iOS or iPadOS device by going to Settings > Apps > Photos. On Mac, open Photos and go to Settings > General.
24K notes
·
View notes
Text
Another approach is to use Git. No, seriously, I know it's like a programmer thing, but it works for all text files and can technically work for xml based files like Word also.
If you're not confident on using a command prompt, check out Github Desktop. Contrary to the name you don't have to put repositories it makes online (and if you do they don't have to be public).
Git is helpful because all those versions of files don't remain visible in one folder, you always just see the most recent version. Past versions exist in the commit history, and you can. Roll back to specific versions, branch off from them, all that good stuff.
REMEMBER: WHEN YOU'RE WORKING ON A PIECE OF WRITING, NEVER DELETE ANYTHING
Ok, so you have a big paper due in July. You make a folder for the project called "Big Paper." You get to work, and save a file titled "PaperTopic.doc" in that folder.
You go back to your draft the next day. DO NOT simply open "PaperTopic.doc" and start editing/adding/revising. You are going to make a folder titled "Paper Versions." You are going to make a copy of "PaperTopic.doc." You are going to move it into the "Paper Versions" Folder.
Then you are going to go back to the original "PaperTopic.doc," and rename it "PaperTopic 5.14.24.doc." And you're going to repeat this EVERY DAY that you work on this project. Soon the "Paper Versions" will look like this:
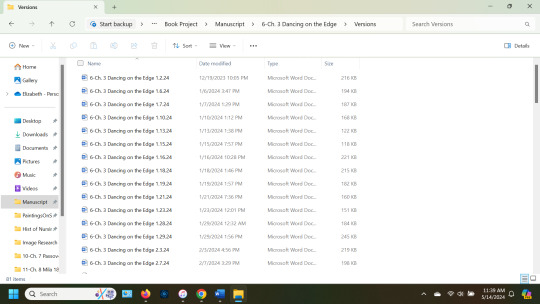
I post about this every 6 months or so, and I will continue to do so; because one day, it WILL save your ass. You're welcome.
Also, back it up to an external hard drive at least once a week.
#writing#writers#creative writing#also please please make backups!!!#they dont have to be in a cloud service#but if you want the peace of mind of cloud stuff without them spying on you consider putting your backups on cloud platforms in password#protected zip files. those are encrypted so Google or whoever wont be able to peek at them#i personally use a free tier Oracle Cloud server as my “house fire” level backup but ik thats not practical for most#remember that backups living on the same device arent really backups at all#since your whole hard drive could fail#and a bad power surge could take out all the drives in your computer#stay safe yall!
2K notes
·
View notes
Text
Revolutionizing Home Security: SwitchBot's Door Lock with Passcode
In the ever-evolving world of smart home technology, SwitchBot has emerged as a trailblazer, offering innovative solutions that seamlessly blend convenience and security. One of their standout products is the Door Lock with Passcode, a game-changer in the realm of home access control.
With the SwitchBot Door Lock, you can bid farewell to the hassle of traditional keys and embrace the future of keyless entry. This cutting-edge device allows you to unlock your door with a simple passcode, eliminating the risk of lost or misplaced keys. Its sleek design and user-friendly interface ensure a seamless integration into any modern home décor.
But the true brilliance of the SwitchBot Door Lock lies in its advanced security features. Powered by state-of-the-art encryption technology, your passcode remains impenetrable, safeguarding your home from unwanted intrusions. Additionally, the lock offers customizable access settings, enabling you to grant temporary or permanent access to trusted individuals, such as family members or service providers.
Seamless integration with other smart home devices is another hallmark of the SwitchBot Door Lock. Through the intuitive SwitchBot app, you can effortlessly control and monitor your lock from anywhere. Receive real-time notifications when someone enters or exits your home, and rest assured knowing that your property is secure.
Experience the ultimate convenience and peace of mind with the SwitchBot Door Lock with Passcode. Embrace the future of home security and unlock a world of possibilities with this innovative solution from SwitchBot.
#home security#smart home technology#SwitchBot#Door Lock#passcode#keyless entry#encryption technology#customizable access#smart home devices#real-time notifications#convenience#innovation
0 notes
Text
Understanding the Difference Between 4G and 5G Networks
As our reliance on mobile connectivity grows, so does the need for faster, more efficient networks. Understanding the difference between 4G and 5G networks is crucial as 5G technology becomes more widely available, promising to revolutionise how we interact with the digital world. From browsing the web to powering autonomous vehicles and smart cities, 5G is set to offer significant advancements…
#4G#5G#5G applications#5G benefits#5G rollout#5G security#AI#AR#automation#autonomous vehicles#bandwidth#cell towers#cloud#Connected Devices#connectivity#cyber threats#data transfer#digital#download speed#emerging tech#encryption#firewalls#Healthcare#infrastructure#innovation#IoT#IT leaders#latency#low latency#Mobile
0 notes
Text
A gadget writer's minor equivalent of nuclear waste
What happens when privacy anxiety meets hardware meltdowns meets procrastination meets what might be a slight hoarding habit.
My home office always needs cleaning, but there’s one part of it that stays especially resistant to tidying up–the small collection of old and inoperative hardware that might have my data in a condition that might be accessible. I think of these probably-defunct devices as my own rough equivalent of nuclear waste, but instead of radioactive isotopes they may hold old personal data that I don’t…

View On WordPress
#device encryption#encryption#erase device#factory reset#half-life#HP Spectre x360#Pixel 1#Pixel 5a#reset device#Schrödinger#secure delete#VeraCrypt#wipe device
0 notes
Text
How to Disable device encryption
How to Disable device encryption
How to Disable device encryption Encryption is a powerful tool for protecting data on your Windows devices. However, there are times when you might need to disable it. Let’s walk through the process of disabling device encryption in Windows 10/11 and understand the difference between Device Encryption and BitLocker Drive Encryption. Kindly see, How to Change BitLocker Password in Windows and how…

View On WordPress
#Automatic Device Encryption#Bitlocker#BitLocker Drive Encryption Architecture#Device encryption#Windows#Windows 10#Windows 11#Windows Server 2016#Windows Server 2019#Windows Server 2022
0 notes
Text
🌐 Mac users, find out why ExpressVPN is the best choice for you! Here are 3 easy reasons why you need it for streaming, security, and privacy. 🚀 Visit https://vpnrecords.com/ for the full guide. Follow us for more tech insights and exclusive offers!
#vpn#virtual private network#express vpn#online privacy#encryption#cybersecurity#streaming#browsing#restricted section#online threats#macos#apple tv app#macintosh#apple devices#apple macos
0 notes
Text
Iranian state television on Tuesday afternoon urged people to remove WhatsApp from their smartphones, alleging without specific evidence that the messaging app gathered user information to send to Israel. In a statement, WhatsApp said it was “concerned these false reports will be an excuse for our services to be blocked at a time when people need them the most.” WhatsApp uses end-to-end encryption, meaning a service provider in the middle can’t read a message.
2K notes
·
View notes
Text
INTERVIEW: @nyancrimew on online privacy and operational security
Our interview series about practical tactics to keep yourself and your community safe from the rising tide of fascism continues this week as Josh talks with maia arson crimew (it/she), a hacktivist and past guest on the show. Topics include:
The mechanics of how corporations and governments identify and track you across virtual and real-world spaces
Common ways that your devices give away information without your knowledge and how to disable those features
What encryption is and why it matters, especially when it comes to law enforcement
Tools that you can use to anonymize your usage online
3K notes
·
View notes
Text
Recall is designed to use local AI models to screenshot everything you see or do on your computer and then give you the ability to search and retrieve anything in seconds. There’s even an explorable timeline you can scroll through. Everything in Recall is designed to remain local and private on-device, so no data is used to train Microsoft’s AI models. Despite Microsoft’s promises of a secure and encrypted Recall experience, cybersecurity expert Kevin Beaumont has found that the AI-powered feature has some potential security flaws. Beaumont, who briefly worked at Microsoft in 2020, has been testing out Recall over the past week and discovered that the feature stores data in a database in plain text.
Holy cats, this is way worse than we were told.
Microsoft said that Recall stored its zillions of screenshots in an encrypted database hidden in a system folder. Turns out, they're using SQLite, a free (public domain) database to store unencrypted plain text in the user's home folder. Which is definitely NOT secure.
Further, Microsoft refers to Recall as an optional experience. But it's turned on by default, and turning it off is a chore. They buried it in a control panel setting.
They say certain URLs and websites can be blacklisted from Recall, but only if you're using Microsoft's Edge browser! But don't worry: DRM protected films & music will never get recorded. Ho ho ho.
This whole debacle feels like an Onion article but it's not.
Luckily(?) Recall is currently only available on Windows 11, but I fully expect Microsoft to try and shove this terrible thing onto unsuspecting Win10 users via Update.
Stay tuned...
3K notes
·
View notes
Note
Reading your post about safe anonymous leaking and nodding along and then going "well fuck I hope I can remember this later because if I ever consider it this is a bit incriminating to save in any way, huh"
The more people who use Tor, the less incriminating it is to use Tor.
The more you use things like Tor, the less weird it is for you to use signal and encrypted email services.
The more you use things like Tor and signal and encrypted email, the less weird it is for you to turn off the location on your devices and leave your phone at home when you go out.
It's suspicious as hell if you make a signal account the week before documents get leaked from your workplace. But it's not suspicious to have a signal account.
It's suspicious if you try to delete your google maps history the week after a protest. It's not suspicious if you don't have a google maps history because you don't use google maps.
All of which is to say: I don't think it's incriminating to check in on that post or bookmark it or start doing the things that it recommends because people should be doing the things on that post anyway. We should be using Tor casually. You should have a half dozen or so proton accounts just for convenience's sake. You should have signal, you should have your location turned off on your devices. You should be doing those things because they are good things to do, but doing those things also sets up an environment in which certain behaviors are less likely to be incriminating, or are less likely to be effective correlative evidence.
But also it has probably been a while since we talked about security nihilism around here; the deal is we live in a surviellance state and all of us are burned in some way. You sent an anon ask, but unless you sent it logged out and through an anonymizing tool, someone knows the originating IP address. If you sent it logged in, you may as well bookmark the post because you have already "contacted a security activist" in a way that can be subpoenaed (anon is only anon to the recipient! it is not anonymous to tumblr and courts can demand their records! that is why I said in the post that nobody who wanted to do any kind of leaking should say anything to me off or on anon!)
But also, consider your source: I have a bookmarks folder called "anarchist resources" that I had to remove from the toolbar because clients kept commenting on it during work calls. There is no way I'm beating the allegations.
But! Nihilism! If they want to charge you bad enough they won't need evidence to make it stick! So you might as well bookmark the post and install signal anyway. At least you can see if you can reduce your chances of getting caught!
1K notes
·
View notes
Text
How Canadians Can Access Google Bard: A Guide with VPN Tips
New Post has been published on https://thedigitalinsider.com/how-canadians-can-access-google-bard-a-guide-with-vpn-tips/
How Canadians Can Access Google Bard: A Guide with VPN Tips
Google Bard, one of the latest AI chatbots from Google, has gained significant attention for its ability to provide up-to-date information and answer complex queries using the latest data. Unlike its main competitor, ChatGPT, which only has data up to April 2023, Google Bard can access real-time information and summarize web content. Despite its advantages, Canadians face a roadblock: Google Bard is currently unavailable in Canada due to regulatory uncertainties. However, there is a way around this—using a VPN.
What is Google Bard?
Google Bard is an AI chatbot that was launched in early 2023, following the success of ChatGPT. This tool is designed to assist users in a wide range of tasks, from answering questions with the most recent information to summarizing web pages. Its ability to stay current with the latest data makes it particularly useful for research and other applications where up-to-date knowledge is crucial.
Why is Google Bard Unavailable in Canada?
The unavailability of Google Bard in Canada stems from “regulatory uncertainty,” although Google has not provided a detailed explanation. This is likely related to the ongoing disputes over Canada’s Online News Act, which requires tech companies like Google to compensate news outlets for content shared on their platforms. This act has already led to Facebook banning news sharing in Canada, and Google seems to have taken a cautious approach by restricting access to Bard in the country.
Can You Access Google Bard with a VPN?
Yes, Canadians can access Google Bard by using a Virtual Private Network (VPN). A VPN allows you to connect to the internet through a server located in another country, effectively bypassing the regional restrictions placed on services like Google Bard. By connecting to a server in the United States or another country where Bard is available, you can use the chatbot without any issues.
How to Choose a VPN for Accessing Google Bard
Not all VPNs are created equal, and choosing the right one is crucial for a seamless experience with Google Bard. Here are some tips:
Avoid Free VPNs: Free VPNs often come with limitations such as restricted bandwidth, slower speeds, and a smaller number of servers. They may also pose security risks, which is why it’s recommended to opt for a premium VPN service.
Speed Matters: To ensure smooth use of Google Bard, choose a VPN that offers high-speed connections. VPNs with the WireGuard protocol or its variants, like NordLynx, are known for their fast performance.
Server Availability: A VPN with thousands of servers in multiple countries will provide more options and better speeds. This is crucial for maintaining a fast and reliable connection to Google Bard.
Security Features: Look for VPNs with advanced security features like a kill switch, which prevents data leaks if the VPN connection drops, and obfuscated servers, which hide the fact that you are using a VPN. This can be particularly useful if you face stringent restrictions.
Customer Support: 24/7 customer support is a valuable feature, especially if you encounter issues or have questions while using the VPN.
Recommended VPN: NordVPN
One of the top choices for accessing Google Bard is NordVPN. It offers a range of features that make it ideal for this purpose:
Advanced Security: NordVPN uses AES-256 encryption, making your data highly secure.
Fast Connections: With over 5,000 servers in 60 countries, including options like NordLynx for faster speeds, NordVPN ensures a quick and stable connection.
Specialty Servers: NordVPN offers features like obfuscated servers and a kill switch, enhancing your security and bypassing restrictions effectively.
Threat Protection: This feature blocks malicious websites, ads, and trackers, adding an extra layer of security.
Meshnet: NordVPN’s Meshnet allows users to connect devices through encrypted private tunnels, enabling secure file sharing and collaboration.
Other recommended options include Express VPN and Surfshark. Other options are available in our list of the best VPNs for Canadian residents.
Conclusion
While Google Bard is currently unavailable in Canada due to regulatory challenges, Canadians can still access this powerful AI tool by using a reliable VPN service like NordVPN. With the right VPN, you can bypass regional restrictions, maintain your online security, and enjoy the full capabilities of Google Bard.
#000#2023#ai#AI Chatbot#AI chatbots#applications#approach#attention#bard#Canada#chatbot#chatbots#chatGPT#Collaboration#Companies#content#data#data leaks#devices#encryption#explanation#express#Facebook#Features#Full#Google#Google BARD#how#how to#Internet
0 notes