#misconfiguration
Explore tagged Tumblr posts
Text

Kevin Malone
0 notes
Text
There is no "trans gene". If there is, we should not base any diagnosis off of it.
“this animal was born biologically nonbinary 🥰” just say intersex. we’re talking about sex and not gender. the animal is intersex. its not a dirty word
#trans reddit likes the idea of a 'trans brain' that is misconfigured during embryonic development#this implies that dysphoria is necessarily the result of an intersex condition#which is batshit insane and also invalidating
18K notes
·
View notes
Text
The Skills Power Duo: Threat Intelligence and Reverse Engineering
New Post has been published on https://thedigitalinsider.com/the-skills-power-duo-threat-intelligence-and-reverse-engineering/
The Skills Power Duo: Threat Intelligence and Reverse Engineering
The 2024 Summer Olympics may have garnered as much cybersecurity related media focus as the games themselves. Every two years, threat actors from a slew of countries seek notoriety by attempting to or succeeding in breaching one of the world’s largest sporting events, giving cybersecurity teams all they can handle to mitigate potential threats.
Although no incidents disrupted the 300-plus medal competitions across dozens of sporting events held in Paris, authorities in France reported more than 140 cyberattacks occurred during this year’s summer games. From late July through the closing ceremonies on August 11, France’s national cybersecurity agency ANSSI recorded 119 reports of “low-impact security events” and 22 additional incidents in which malicious actors successfully targeted information systems. According to ANSSI, the attacks focused mostly on government agencies as well as sports, transportation, and telecoms infrastructure.
From the Olympics to financial institutions to all sectors of most industries, organizations need their workforces to possess the best cybersecurity skills possible. A recent survey of IT professionals conducted by Pluralsight revealed that the top two skills needed to dismantle the most dangerous emerging security threats are threat intelligence and reverse engineering.
Organizations that arm themselves with a workforce that brings this one-two punch to cybersecurity are better equipped to defend themselves from malicious actors. When threat analysis, reporting, and response (threat intelligence) is combined with uncovering how malicious software works and identifying vulnerabilities (reverse engineering), the results play a significant role to help future-proof a business’s defense systems.
Taking Action Against Innovative, Novel Cyber Threats
Using threat intelligence and reverse engineering in tandem can optimize cyber risk mitigation programs and fortify cybersecurity defenses. Professionals trained in threat intelligence and reverse engineering are more likely than those lacking these skills to develop updates and implement patches to avert risk quickly and effectively.
Threat intelligence helps drive early detection and improved response to threats by analyzing patterns and indicators of compromise as well as giving security teams more effective incident response plans to quickly mitigate threats. Reverse engineering drives better understanding of malware by analyzing its structure and methods of operation as well as developing mechanisms for detecting its characteristics. Even when faced with innovative, novel cyber threats, teams who possess these skills will be ready to take immediate action.
Incidents such as the BlackCat ransomware attack, the Poly Network hack, and several high-profile breaches in the healthcare sector reflect ongoing trends in cyber threats and the importance of instituting robust cybersecurity measures across all industries.
Companies that fall behind in their efforts to upskill and train their IT teams against cyber threats will become increasingly more susceptible to opportunistic attackers. In 2023, Pluralsight found that surveyed IT professionals know they’ll need to learn AI skills to secure their careers as 96% say staying up to date with AI skills is the best way to ensure their job security.
As such, organizations need to reduce the cyber workforce skills gap by training their employees in the latest tech trends to give them the expertise they need to proactively guard against attacks. According to a report from the Sloan School of Managementat the Massachusetts Institute of Technology, cloud misconfigurations, increasingly sophisticated ransomware, and vendor exploitation hacks are contributing to rising cyberattacks.
The Threat Landscape Continues to Grow
As organizations seek to fill traditional positions or create new cybersecurity roles to defend themselves, the threat landscape continues to grow. According to the Biden administration’s director of National Intelligence, the number of ransomware attacks worldwide grew by as much as 74% in 2023. In testimony to Congress earlier this year, Avril Haines said U.S. entities were the most heavily targeted last year with attacks in sectors like healthcare doubling between 2022 and 2023.
The current and future cybersecurity landscape will be characterized by a range of threats and factors that include the role of skills development in protecting against cyberattacks, from day-to-day business operations to high profile events like the Olympics, large-scale public gatherings, and political elections.
In the United States, cybersecurity issues related to the 2024 presidential election have already come into focus after a trove of confidential information was hacked from Donald Trump’s campaign operations. Although the handful of news outlets that received the information from an anonymous source chose not to publish any of it, the damage had already been done, orchestrated by a hacker who identified themselves only as “Robert.”
To stay ahead of opportunistic bad actors, it’s more important now than ever before for organizations to build out a workforce that possesses the most sought-out cybersecurity skills like threat intelligence and reverse engineering. In today’s competitive labor market, this entails not only recruiting and hiring the best talent available but also fostering a culture of continuous learning across the business to ensure that skills gaps are identified and workforces remain as equipped as possible on thwarting cyberattacks.
This includes proficiency in knowing how GenAI can be properly leveraged for threat detection and as a response tool against emerging attacks. Amidst the evolving AI landscape, its adoption by malicious actors, and ongoing cybersecurity skills gaps in the technology workforce, Pluralsight has found that over 80% of surveyed IT professionals are concerned about AI-powered threats.
By mounting a cyber defense using AI tools, organizations can bolster their strengths in threat detection and prevention, incident response, vulnerability management, user authentication, fraud detection, and threat forecasting. As such, AI can enhance cybersecurity by delivering advanced tools for detecting and responding to threats, automating routine tasks, and improving the overall efficiency of security operations.
According to a report from IBM, in 2023 the average cost savings for organizations that used security AI and automation extensively for cybersecurity and breach prevention was $2.22 million compared to companies that did not do so. The report also found that the average cost of a data breach globally is $4.8 million, which represents a 10% increase over the prior year and is, to date, the highest total per breach cost ever. The findings also revealed that one out of every three breaches involved shadow data, showing that the proliferation of data is making it harder to secure it all.
Defending Digital Assets and Ensuring the Safety and Reliability of Systems
By upskilling the workforce and implementing the right technologies and practices, organizations can safeguard their digital assets and ensure the confidentiality and integrity of their data and networks. The multi-faceted discipline of cybersecurity is critical to ensure the safe and reliable operation of technology systems. When armed with the right skills and consistently practicing how to react to simulated cyberattacks, businesses can create the best defense possible against an increasingly active threat landscape.
#2022#2023#2024#Administration#ai#ai skills#ai tools#AI-powered#Analysis#arm#assets#attackers#authentication#automation#biden#BlackCat#breach#Business#Careers#Cloud#cloud misconfigurations#Companies#Competitions#compromise#continuous#cost savings#cyber#cyber risk#Cyber Threats#Cyberattacks
0 notes
Text
Fixing Magento 2 Internal Server Error on Localhost | Apache Server Configuration
Sometime when we installed magento 2 in localhost. When trying to run frontend and Backend then we get the this issue Internal Server Error, that means apache server not configured properly, Then we need to configured apache 2 server configuration. It will come when using XAMPP for windows, MAMP for Macos. So we need to set apache 2 configuration in localhost. Internal Server ErrorThe server…
#Internal Server Error in magento 2?#Magento 2 after installation getting this error?#magento 2 internal server error#Please contact the server administrator#The server encountered an internal error or misconfiguration
0 notes
Text
FanFiction.net is not gone.
Right now it's a victim of DNS (Domain Name Service) spoofing. This means that a malicious party is trying to steal traffic from FFn by purchasing a very similar domain.
Correction:
The new "fake" site that people are seeing still belongs to FanFiction.net—they just misconfigured their servers and are not redirecting traffic from the bare fanfiction.net to the main site at www.fanfiction.net. There is likely no malicious agent. Didn't mean to scare anyone! Just wanted to let people know the site wasn't deleted!
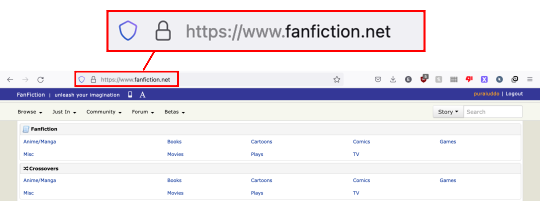
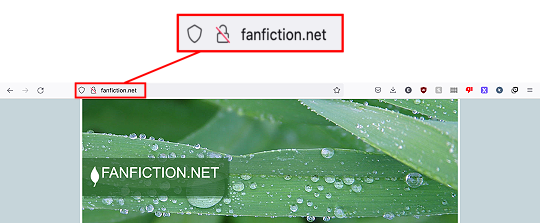
So if you want to read fanfiction and not see leaves, you have have to type out "www.fanfiction.net".
Please share so people stop panicking.
#i was not expecting this to become ANYWHERE near as popular as this is#sorry for the misinformation concerning why the website wasn't working#just wanted to get the point across the ffn isn't dead#fanfiction#ffn#fanfiction.net#fanfiction dot net#fanfictionnet#ff net#purs post#psa
49K notes
·
View notes
Text
Servers & Misconfigurations
A server is a system of hardware and software suited to respond to requests across a network of computers to provide network service. When you suddenly notice that your server is down and can no longer connect to the internet, or website pages load slowly, there are many things that can be causing server problems. An internal server error is an error on the web server you’re trying to access.
That server has become misconfigured via a developed corruption that prevents it from responding properly to what you’re asking it to do.
0 notes
Text

the universe doesn't want me to play Baldur's Gate
1 note
·
View note
Text
Automake is a curse.
Basic compilers like gcc are your sigil magic. Simple, takes a little knowledge to get working, but they're where the actual magic happens. make is a spell -- a formula that combines those sigils in a way more people can cast because they don't need an understanding of what likes beneath. The writer of the spell needs to understand, but not the users. CMake is a piece of magical machinery with interchangeable parts so that the wielder can fine-tune it for their needs. It's more advanced than make, which is often good but can be a double-edged sword. Installation wizards are just that -- wizards -- and package managers are the wizards who can cast the combination of spells that you need for what you've asked for.
Automake is asking an eldritch horror to cast your spell for you. If you'd taken the time to learn it yourself then it would've been fine. But instead of summoning a creature to do your bidding you've turned your arm into a lobster. Technicially it is a creature, and it will do your bidding, but you're starting to realize this was all more hassle than it's actually worth.
#runic ramblings#whyyyy do people use automake for their code when they clearly don't understand it#Had to automake something yesterday and it was a NIGHTMARE figuring out what was actually missing#'just enter make' Makefile.am is misconfigured and you don't even know it! Because it's so variable between OSes that you have no reason to
0 notes
Text
Unlock the potential of your website with our curated list of the top WordPress themes for 2023. This comprehensive guide showcases the latest themes that offer stunning design, cutting-edge features, and the flexibility to create a website that truly stands out. Whether you're building a blog, portfolio, e-commerce site, or a business website, these themes are handpicked to help you make a powerful online impression.
#Wordpress SEO Mistakes#WordPress SEO mistakes to avoid#Common SEO mistakes in WordPress#WordPress SEO errors#WordPress SEO pitfalls#SEO blunders on WordPress#Beginner WordPress SEO mistakes#WordPress on-page SEO mistakes#WordPress off-page SEO mistakes#WordPress SEO plugin errors#WordPress SEO misconfigurations
0 notes
Note
Can you explain a bit more about the "no art is good" thing? It sounds like an interesting idea.
the point of art is to make something that nature can't make. for whatever purpose it might serve, whether it's to send a message or just because you want to see something that didnt exist before you made it-- creating "art" is creating a pattern or a shape or an idea or a sound that the universe didn't form naturally on its own. one that can't exist on its own purely because it makes sense for it to, because it doesn't. you could listen to field recordings of the churning of a dead universe for 50 trillion years, and i bet you still wouldn't hear anything that sounds like "crank that" by soulja boy.
art by definition is the misconfiguration of the natural world to suit the vanity of man, and is no different from something like a tumor.
luckily! i don't give a shit, so i still love art.
610 notes
·
View notes
Note

"misconfiguration" bffr. oh you MISCONFIGURED a whole-ass fake sale. is the default ALSO putting things on sale? is the default in the room with us right now? who is falling for this
☁️
8 notes
·
View notes
Text
Misconfigured Kubernetes RBAC in Azure Airflow Could Expose Entire Cluster to Exploitation
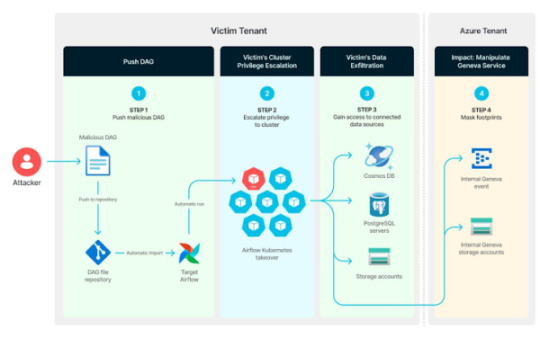
Source: https://thehackernews.com/2024/12/misconfigured-kubernetes-rbac-in-azure.html
More info: https://unit42.paloaltonetworks.com/azure-data-factory-apache-airflow-vulnerabilities/
11 notes
·
View notes
Note
Hey I think something is up with the Aurora website. I can’t seem to read any pages beyond 1.22.54. And if I use the archive button to view a page after that, if I hit the “next” button it jumps right back there.
Weirdly I'm seeing a similar problem, but it's happening inconsistently - at one point the back arrow jumped me all the way to the first page, but then worked correctly a minute later. The latest page at one point displayed a forward arrow that took me back to 1.22.54, but is no longer doing that on my end.
Since it's happening inconsistently and is difficult to reproduce, I'm inclined to think it's some kind of backend database issue rather than a misconfiguration I can fix. I've never seen this kind of problem before. Hopefully it's a weird one-off.
125 notes
·
View notes
Note
Also Noir's clothes are different from regular papyrus's
He'd be wearing something more like black pants, a pullover and a jacket. His scarf would be more work out and the color would be faded.

Something like this but with a pullover and a scarf.
He'd probably be the type to smoke, from the paranoia and the itch of knowing someone exists and having proof but barely remembering them.
Maybe he'd be having contact with alphys to know how things are going in his AU while he's away.
.
And then one day she stops responding.
And suddenly, he feels like a little piece of him just got emptied. Like a part of his soul- of his code, just got removed.
He goes to the omega timeline, where he usually goes to rest.
Goes to the inn, where he usually sleeps at. Asks the old lady at the counter if she's ever had that feeling.
"oh, most people here had that feeling before. That's usually the feeling people outta their AU get when it crumbles or the code gets corrupted."
WHAAAAAT? YOU CANT JUST LEAVE THAT IN MY ASK BOX 😭😭 /j
It's aesthetically interesting that Papyrus replaced the vibrant and colorful colors he wore with more sober and dark tones, almost as if he wore the mourning of memories that never happened (at least not in that timeline). I like to think he would wear something more detective style? Abandoning the hero/royal guard style
And as you said before (or possibly @howlsofbloodhounds ), since it was Killer who did the last reset, something could have definitely gone wrong, after all, his code had been misconfigured for a long time, so why not his resets?
I think Killer's AU possibly closed itself off after a while after Noir left, as if a barrier had closed so that no one could leave or enter. Or it was deleted by Error because it was another anomaly.
Or maybe Nightmare himself did something to stop Noir from chasing after Killer once and for all, so why not destabilize him a little by destroying his refuge?
12 notes
·
View notes
Photo

I think I may have misconfigured something in my webcam setup
158 notes
·
View notes
Text
A database containing sensitive, sometimes personal information from the United Nations Trust Fund to End Violence Against Women was openly accessible on the internet, revealing more than 115,000 files related to organizations that partner with or receive funding from UN Women. The documents range from staffing information and contracts to letters and even detailed financial audits about organizations working with vulnerable communities around the world, including under repressive regimes.
Security researcher Jeremiah Fowler discovered the database, which was not password protected or otherwise access controlled, and disclosed the finding to the UN, which secured the database. Such incidents are not uncommon, and many researchers regularly find and disclose examples of exposures to help organizations correct data management mistakes. But Fowler emphasizes that this ubiquity is exactly why it is important to continue to raise awareness about the threat of such misconfigurations. The UN Women database is a prime example of a small error that could create additional risk for women, children, and LGBTQ people living in hostile situations worldwide.
“They're doing great work and helping real people on the ground, but the cybersecurity aspect is still critical,” Fowler tells WIRED. “I've found lots of data before, including from all sorts of government agencies, but these organizations are helping people who are at risk just for being who they are, where they are.”
A spokesperson for UN Women tells WIRED in a statement that the organization appreciates collaboration from cybersecurity researchers and combines any outside findings with its own telemetry and monitoring.
“As per our incident response procedure, containment measures were rapidly put in place and investigative actions are being taken,” the spokesperson said of the database Fowler discovered. “We are in the process of assessing how to communicate with the potential affected persons so that they are aware and alert as well as incorporating the lessons learned to prevent similar incidents in the future.”
The data could expose people in multiple ways. At the organizational level, some of the financial audits include bank account information, but more broadly, the disclosures provide granular detail on where each organization gets its funding and how it budgets. The information also includes breakdowns of operating costs, and details about employees that could be used to map the interconnections between civil society groups in a country or region. Such information is also ripe for abuse in scams since the UN is such a trusted organization, and the exposed data would provide details on internal operations and potentially serve as templates for malicious actors to create legitimate-looking communications that purport to come from the UN.
“You have a list of organizations and details about their staff and activities, and some of the projects I saw had budgets in the millions of dollars,” Fowler says. “If this data fell into the wrong hands or it reached the dark web, you could have scammers or an authoritarian government looking at which organizations are working where, and who they working with, to target them and even find out names of people they've been helping.”
This leads to the other crucial element of the finding: In addition to fueling scams and potentially exposing local organizations, the data could be exploited to directly target at-risk individuals with extortion attempts or even local law enforcement action.
“I saw letters from people who were victims of kidnapping, rape, abuse—people telling their stories probably believing that they will remain anonymous,” Fowler says. “There was a letter from someone who had gotten HIV who was helped out by a foundation, and they told their whole story of how their family and friends had turned on them.”
If the finding spurs infrastructure review and other detections, it could go a long way toward helping UN Women—and the sprawling ecosystem of UN organizations more broadly—to catch any other easy-to-fix errors and prevent potential data breaches.
11 notes
·
View notes