#rbac
Explore tagged Tumblr posts
Text
Role-Based Access Control (RBAC) is an essential feature for managing user permissions in web applications. It allows you to assign different roles to users (e.g., Admin, Editor, User) and grant permissions accordingly.
In this tutorial, we will implement RBAC in Laravel 12 using spatie/laravel-permission package to manage roles and permissions efficiently.
#Laravel12#RBAC#RoleBasedAccessControl#Laravel#WebDevelopment#LaravelSecurity#Authentication#Authorization#LaravelApp#LaravelRoles#PHP#LaravelDevelopment#AccessControl#WebAppSecurity#BackendDevelopment#UserRoles#LaravelTutorial#LaravelBestPractices#LaravelProjects#RoleManagement#AccessPermissions#LaravelAuth#WebAppFeatures#LaravelAdminPanel#PermissionSystem#LaravelRoleBasedAccess
0 notes
Text
Leveraging SolveForce and The Telecom Broker to Address Key Cybersecurity Risks
Introduction Recent guidance from the Cybersecurity and Infrastructure Security Agency (CISA), alongside other global cybersecurity agencies, highlights significant vulnerabilities in telecommunications infrastructure exploited by malicious actors, such as state-sponsored cyber threats. The risks include unauthorized configuration changes, weak access controls, and insecure protocols. By…
#CISA Cybersecurity Guidance#Configuration Monitoring#Cybersecurity#encryption#MFA#Patch Management#RBAC#Secure Protocols#SIEM#SolveForce#Telecom Broker#Telecommunications Security
0 notes
Text
Implementing Role-Based Access Control in Django
Learn how to implement Role-Based Access Control (RBAC) in Django. This guide covers defining roles, assigning permissions, and enforcing access control in views and templates.
Introduction Role-Based Access Control (RBAC) is a method of regulating access to resources based on the roles of individual users within an organization. Implementing RBAC in Django involves defining roles, assigning permissions, and enforcing these permissions in your views and templates. This guide will walk you through the process of implementing RBAC in Django, covering user roles,…
#Django#Django templates#Django Views#permissions#Python#RBAC#role-based access control#Security#user roles#web development
0 notes
Text
Hey look! I made a thing! And I actually took videos of it this time!
0 notes
Text

Some jewelry on my messy bench. Excited about the Rainbow Bazaar Art Collective! We're a bunch of queer artists in southern AB and we're working together this market season!
#jewelry#rbac#sterling#silver#earrings#pearl#carnelian#turquoise#crystals#handmade#small business#gothic#upcycled
0 notes
Text
Mesh it Up Monday: Authorization - The Key to Secure Network Access
Welcome to another Mesh it Up Monday, where we delve into the world of networking with a sprinkle of humor and a whole lot of knowledge! Today, we’re going to unlock the secrets of authorization and discover how it acts as the key to secure network access. So grab your virtual keychain and let’s dive in! Chapter 1: The Magical Key 🔑✨ Imagine you’re at the entrance of a fabulous party. You…
View On WordPress
#access control#authentication#authorization#authorization methods#biometric authentication#digital signatures#network access#network dance floor#network security#RBAC#role-based access control#two-factor authentication#username and password
0 notes
Text
Understand Kubernetes RBAC: Concepts, Example & Best Practices
Part of our kubernetes series, lets Understand Kubernetes RBAC with concepts. Also, will try to cover some examples with top misconfigurations. Before we jump into kubernetes RBAC, let’s see what RBAC is. What Is Role-Based Access Control? Role-based access control is control over user groups and access to resources based on a defined role. According to the National Institute of Science and…

View On WordPress
0 notes
Text
Misconfigured Kubernetes RBAC in Azure Airflow Could Expose Entire Cluster to Exploitation
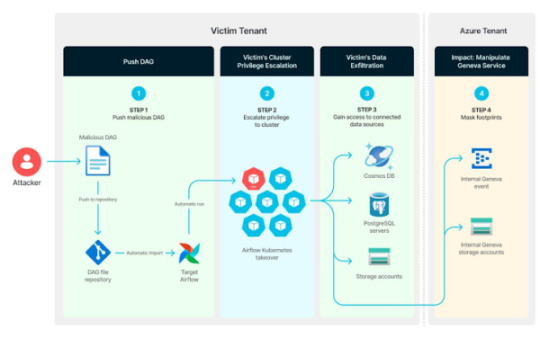
Source: https://thehackernews.com/2024/12/misconfigured-kubernetes-rbac-in-azure.html
More info: https://unit42.paloaltonetworks.com/azure-data-factory-apache-airflow-vulnerabilities/
11 notes
·
View notes
Text






Cora & Rose Rivers for @whyeverr Rebuild a City Challenge (more info + download under the cut)
I've been following whyeverr's rbac-challenge for such a long time and I was (and still am) totally in awe of the dedication that she puts into the challenge and the story itself! So when she announced that she was looking for survivors for the challenge, I knew I had to create some sims.
Meet Cora and Rose, two sisters who are originally from Chestnut Ridge, where they grew up on the outskirts of the city on a horse farm ... everything was fine until the day tragedy struck and the townie apocalypse started. They left their farm in a hurry and lost their parents who fought the townies off so that they could escape. There was grief, anger, and yet, determination to survive until the day, they would take back the farm from the townies.
Cora is pretty straightforward, she's a woman of action and has never lost a fight, while Rose is still a teenager who's trying to find herself against all odds. She may be seen hanging around with the wrong crowd and her decisions might not be the best, but she's always looking out for her loved ones. Even though both sisters are very different, they always have each other's back. (If anyone still knows the TV show The Tribe, that's where I got my inspiration for Rose from)
Download: You can find them in the gallery, my ID is aeromantica (please turn on custom content in the search, I've not used any CC but they somehow have that label)
#rbaccsurvivor#the sims 4#ts4#ts4 simblr#ts4 cas#whyeverr#sims download#sims 4 download#show us your sims#sims 4#sims 4 screenshots#sims 4 no cc#I am a cc-girlie so this was difficult but I hope they turned out well!#regarding The Tribe - I watched it when I was way too young but I loved the weird and iconic outfits back then#this is my last 'real' post before my holidays the rest will be queued until the 29th of september#*mine#*mydownload
41 notes
·
View notes
Text
hey lovies
so i was going to upload a percabeth christmas oneshot but now it’s gonna be winter because i was too late to surprise you guys with a christmas fic as a present
she will get done eventually. actually gonna go write after this. but i’m only like 1500 words in and i want it to be longer
also for those wondering where rbac/iwdafy is… i lowkey hate everything ive written but also want to keep going and just don’t want it to be cringe and sound like a nine year old wrote it
tl/dr: i’m procrastinating writing because it stresses me out and i don’t want to give yall a shitty product
much love
🩷 invisibleperiwinkle
#percy jackson#annabeth chase#percabeth#percy jackson and the olympians#pjo#percy and annabeth#fanfiction#pjo fic#percy jackson fanfiction#percabeth fanfic
4 notes
·
View notes
Text
What is Argo CD? And When Was Argo CD Established?

What Is Argo CD?
Argo CD is declarative Kubernetes GitOps continuous delivery.
In DevOps, ArgoCD is a Continuous Delivery (CD) technology that has become well-liked for delivering applications to Kubernetes. It is based on the GitOps deployment methodology.
When was Argo CD Established?
Argo CD was created at Intuit and made publicly available following Applatix’s 2018 acquisition by Intuit. The founding developers of Applatix, Hong Wang, Jesse Suen, and Alexander Matyushentsev, made the Argo project open-source in 2017.
Why Argo CD?
Declarative and version-controlled application definitions, configurations, and environments are ideal. Automated, auditable, and easily comprehensible application deployment and lifecycle management are essential.
Getting Started
Quick Start
kubectl create namespace argocd kubectl apply -n argocd -f https://raw.githubusercontent.com/argoproj/argo-cd/stable/manifests/install.yaml
For some features, more user-friendly documentation is offered. Refer to the upgrade guide if you want to upgrade your Argo CD. Those interested in creating third-party connectors can access developer-oriented resources.
How it works
Argo CD defines the intended application state by employing Git repositories as the source of truth, in accordance with the GitOps pattern. There are various approaches to specify Kubernetes manifests:
Applications for Customization
Helm charts
JSONNET files
Simple YAML/JSON manifest directory
Any custom configuration management tool that is set up as a plugin
The deployment of the intended application states in the designated target settings is automated by Argo CD. Deployments of applications can monitor changes to branches, tags, or pinned to a particular manifest version at a Git commit.
Architecture
The implementation of Argo CD is a Kubernetes controller that continually observes active apps and contrasts their present, live state with the target state (as defined in the Git repository). Out Of Sync is the term used to describe a deployed application whose live state differs from the target state. In addition to reporting and visualizing the differences, Argo CD offers the ability to manually or automatically sync the current state back to the intended goal state. The designated target environments can automatically apply and reflect any changes made to the intended target state in the Git repository.
Components
API Server
The Web UI, CLI, and CI/CD systems use the API, which is exposed by the gRPC/REST server. Its duties include the following:
Status reporting and application management
Launching application functions (such as rollback, sync, and user-defined actions)
Cluster credential management and repository (k8s secrets)
RBAC enforcement
Authentication, and auth delegation to outside identity providers
Git webhook event listener/forwarder
Repository Server
An internal service called the repository server keeps a local cache of the Git repository containing the application manifests. When given the following inputs, it is in charge of creating and returning the Kubernetes manifests:
URL of the repository
Revision (tag, branch, commit)
Path of the application
Template-specific configurations: helm values.yaml, parameters
A Kubernetes controller known as the application controller keeps an eye on all active apps and contrasts their actual, live state with the intended target state as defined in the repository. When it identifies an Out Of Sync application state, it may take remedial action. It is in charge of calling any user-specified hooks for lifecycle events (Sync, PostSync, and PreSync).
Features
Applications are automatically deployed to designated target environments.
Multiple configuration management/templating tools (Kustomize, Helm, Jsonnet, and plain-YAML) are supported.
Capacity to oversee and implement across several clusters
Integration of SSO (OIDC, OAuth2, LDAP, SAML 2.0, Microsoft, LinkedIn, GitHub, GitLab)
RBAC and multi-tenancy authorization policies
Rollback/Roll-anywhere to any Git repository-committed application configuration
Analysis of the application resources’ health state
Automated visualization and detection of configuration drift
Applications can be synced manually or automatically to their desired state.
Web user interface that shows program activity in real time
CLI for CI integration and automation
Integration of webhooks (GitHub, BitBucket, GitLab)
Tokens of access for automation
Hooks for PreSync, Sync, and PostSync to facilitate intricate application rollouts (such as canary and blue/green upgrades)
Application event and API call audit trails
Prometheus measurements
To override helm parameters in Git, use parameter overrides.
Read more on Govindhtech.com
#ArgoCD#CD#GitOps#API#Kubernetes#Git#Argoproject#News#Technews#Technology#Technologynews#Technologytrends#govindhtech
2 notes
·
View notes
Text
My new jewelry, knitwear, and home decor store is coming soon!
Some jewelry and an in progress recycled sari silk sweater! Just a little photo dump to warm up. Etsy coming soon!





I made these earrings and the two necklaces for loved ones. From left to right, the blue necklace was given to my mother; the red earrings, to my girlfriend; and the pearl necklace, to my wife, for our first mother's day. (I love my poly family!) The mother of pearl hearts were left over from a strand we used to decorate her wedding bouquet. A pair of the pearl earrings went to her, but more are available!



#jewellery#handmade#jewelry#alberta#artisan#queer#fashion#canadian#aesthetic#demi fine#knitting#sterling#wip#quartz#silver#coral#turquoise#mother of pearl#pearl#shell#carnelian#skulls#hippie#y2k#gothic#RBAC
1 note
·
View note
Text
Safeguarding Privacy and Security in Fast-Paced Data Processing

In the current era of data-centric operations, rapid data processing is essential across many industries, fostering innovation, improving efficiency, and offering a competitive advantage.
However, as the velocity and volume of data processing increase, so do the challenges related to data privacy and security. This article explores the critical issues and best practices in maintaining data integrity and confidentiality in the era of rapid data processing.
The Importance of Data Privacy and Security
Data privacy ensures that personal and sensitive information is collected, stored, and used in compliance with legal and ethical standards, safeguarding individuals' rights. Data security, on the other hand, involves protecting data from unauthorized access, breaches, and malicious attacks. Together, they form the foundation f trust in digital systems and processes.
Challenges in Rapid Data Processing
Volume and Velocity: The sheer amount of data generated and processed in real-time poses significant security risks.
Complex Data Environments: Modern data processing often involves distributed systems, cloud services, and multiple third-party vendors, creating a complex ecosystem that is challenging to secure comprehensively.
Regulatory Compliance: With stringent regulations like GDPR, CCPA, and HIPAA, organizations must ensure that their rapid data processing activities comply with data privacy laws.
Anonymization and De-identification: Rapid data processing systems must implement robust anonymization techniques to protect individual identities.
Best Practices for Ensuring Data Privacy and Security
Data Encryption: Encrypting data at rest and in transit is crucial to prevent unauthorized access.
Access Controls: Role-based access controls (RBAC) and multi-factor authentication (MFA) are effective measures.
Regular Audits and Monitoring: Continuous monitoring and regular security audits help identify and mitigate vulnerabilities in data processing systems.
Data Minimization: Collecting and processing only the necessary data reduces exposure risks.
Compliance Management: Staying updated with regulatory requirements and integrating compliance checks into the data processing workflow ensures adherence to legal standards.
Robust Anonymization Techniques: Employing advanced anonymization methods and regularly updating them can reduce the risk of re-identification.
Conclusion
As organizations leverage rapid data processing for competitive advantage, prioritizing data privacy and security becomes increasingly critical. By adopting best practices and staying vigilant against evolving threats, businesses can safeguard their data assets, maintain regulatory compliance, and uphold the trust of their customers and stakeholders.
To know more: project management service company
data processing services
Also read: https://stagnateresearch.com/blog/data-privacy-and-security-in-rapid-data-processing-a-guide-for-market-research-professionals/
#onlineresearch#marketresearch#datacollection#project management#survey research#data collection company
3 notes
·
View notes