#robust application development
Explore tagged Tumblr posts
Text
Robust Laravel Application Development - Lessons Learned
Introduction Building a robust Laravel application that can scale, handle high traffic, and remain maintainable over time is not without its challenges. Over the years, developers and teams have encountered several common pitfalls and learned invaluable lessons while building and maintaining large-scale Laravel applications. Developing robust applications with Laravel requires careful planning,…
#Hire Laravel Developers#Laravel Application#Laravel Application Development#Robust Laravel Application Development
0 notes
Text
FileMaker Custom Development: Create Robust Custom Applications with Kbizsoft
Discover how Kbizsoft’s expert FileMaker custom development services can help you design tailored, robust applications. From idea to implementation, we deliver solutions that enhance productivity and efficiency. To learn more about our custom FileMaker development process contact us today.
#FileMaker Development#Custom FileMaker Applications#FileMaker Solutions#FileMaker Customization#FileMaker App Development#Custom Software Development#Robust Custom Applications#FileMaker Experts#FileMaker Development Services#KBizSoft FileMaker Solutions#Database Development#Business App Development#FileMaker Solutions for Business#FileMaker Developers#FileMaker Application Design#develop#game development#marketing#mobile app development#personal development#software development#technology#web development
1 note
·
View note
Text
Europe Aircraft Leasing Market: Rapid Development and Value Trends Forecast (2024-2032)

The Europe Aircraft Leasing Market is on a trajectory of rapid development, driven by evolving value trends and a robust aviation sector. As European airlines and operators navigate the complexities of fleet management, leasing has emerged as a strategic solution to meet both current and future needs.
Europe Aircraft Leasing Market showcases the following key aspects:
Fleet Expansion and Modernization: European airlines are increasingly turning to leasing to expand and modernize their fleets. This approach allows them to quickly integrate new aircraft models that enhance operational efficiency and comply with environmental regulations.
Economic Uncertainty and Flexibility: Leasing provides airlines with greater financial flexibility amid economic uncertainties. It allows operators to manage capital expenditure more effectively and adjust their fleet size according to market demand.
Technological Advancements: The adoption of advanced technologies in leased aircraft supports better fuel efficiency and lower emissions. European airlines benefit from these innovations without the long-term financial commitment of owning the aircraft.
Regulatory Pressure: Europe’s stringent environmental regulations drive the demand for modern, eco-friendly aircraft. Leasing offers a practical solution for airlines to meet these requirements while minimizing financial risk.
Geographical Distribution: Key markets in Europe, such as the UK, Germany, and France, are at the forefront of the leasing trend. Their well-developed aviation sectors and strategic positions contribute to the overall growth of the market.
The forecast for the Europe Aircraft Leasing Market is characterized by robust growth and ongoing development. As airlines continue to seek flexible and cost-effective solutions, leasing will remain a vital component of the region’s aviation landscape.
About US
At Market Research Future (MRFR), we enable our customers to unravel the complexity of various industries through our Cooked Research Report (CRR), Half-Cooked Research Reports (HCRR), Raw Research Reports (3R), Continuous-Feed Research (CFR), and Market Research & Consulting Services. MRFR team have supreme objective to provide the optimum quality market research and intelligence services to our clients. Our market research studies by products, services, technologies, applications, end users, and market players for global, regional, and country level market segments, enable our clients to see more, know more, and do more, which help to answer all their most important questions. To stay updated with technology and work process of the industry, MRFR often plans & conducts meet with the industry experts and industrial visits for its research analyst members.
Contact us:
Market Research Future (part of Wants tats Research and Media Private Limited),
99 Hudson Street,5Th Floor, New York, New York 10013, United States of America
Sales: +1 628 258 0071 (US) +44 2035 002 764 (UK)
Email: [email protected]
#The Europe Aircraft Leasing Market is on a trajectory of rapid development#driven by evolving value trends and a robust aviation sector. As European airlines and operators navigate the complexities of fleet managem#leasing has emerged as a strategic solution to meet both current and future needs.#Europe Aircraft Leasing Market showcases the following key aspects:#•#Fleet Expansion and Modernization: European airlines are increasingly turning to leasing to expand and modernize their fleets. This approac#Economic Uncertainty and Flexibility: Leasing provides airlines with greater financial flexibility amid economic uncertainties. It allows o#Technological Advancements: The adoption of advanced technologies in leased aircraft supports better fuel efficiency and lower emissions. E#Regulatory Pressure: Europe’s stringent environmental regulations drive the demand for modern#eco-friendly aircraft. Leasing offers a practical solution for airlines to meet these requirements while minimizing financial risk.#Geographical Distribution: Key markets in Europe#such as the UK#Germany#and France#are at the forefront of the leasing trend. Their well-developed aviation sectors and strategic positions contribute to the overall growth o#The forecast for the Europe Aircraft Leasing Market is characterized by robust growth and ongoing development. As airlines continue to seek#leasing will remain a vital component of the region’s aviation landscape.#About US#At Market Research Future (MRFR)#we enable our customers to unravel the complexity of various industries through our Cooked Research Report (CRR)#Half-Cooked Research Reports (HCRR)#Raw Research Reports (3R)#Continuous-Feed Research (CFR)#and Market Research & Consulting Services. MRFR team have supreme objective to provide the optimum quality market research and intelligence#services#technologies#applications#end users#and market players for global#regional
0 notes
Text
#enterprise web development#enterprise web app development#Back-end development#using a robust framework#enterprise web application development company#enterprise website development company#enterprise web development agency
0 notes
Text
I'm interested in forming a sort of...math & physics reading group network. well, with some very important modifications to the concept of "reading group".
for example, right now, I'd like to learn algebraic geometry, qft, and/or refresh myself on representation theory with someone—maybe just one or two people—meaning that traditionally, we'd pick a text for one of these topics, discuss the material (asynchronously or synchronously?), exchange exercises, etc.
but currently (being Between Institutions), my best bet is posting on tumblr. and that's a pretty good bet, tbh! there are a lot of us here!
though, wouldn't it be great if there were a way to coordinate groups like this across institutions? you make a post proposing a group, specifying your goals and constraints...
even that would be a boon. but I think the concept of a "reading group" itself could be changed in interesting ways. this is what I'm really interested in.
there are variations among reading groups themselves already. sometimes you have directed reading groups, where someone already knows the material and "leads" it; some people are looking for more or less people involved; and there are probably things to explore for making sure that reading groups stick through it instead of falling apart when some motivation flags. default meeting times help with this, for example.
there are many experiments to be done! I think lessons for group-making can be taken from a maybe-surprising source: theater. there are a lot of things that make groups which put on shows more robust and rewarding than reading groups. a sense of building to something; many factors that create informal group cohesion (e.g. such a structure should make sure it creates more-informal "cafe" time in addition to more-formal "practice" time, just as rehearsal in physical spaces facilitates that casual sort of interaction on its periphery); ways to get into the right headspace during discussions (just as warm-ups do in theater; the engagement with this material is an event); clear goals (e.g. "understand ___"); successive shared accomplishments...to that end I wonder if it makes sense to form math troupes, which do successive reading groups together, drawn from its members.
it might be useful to envision some sort of public-facing artifact created as the culmination of this learning, whether a presentation, or an article, or some novel application or research...the crucial question is: how do we choose a goal that we find meaning in?
one idea, for example, is to have a collection parallel reading groups learning different things, and end by presenting to each other! that way we know what we learn will be meaningful to others, too, from the beginning. in general, I think it's important to feel that our own development of insight and understanding can be meaningful to others and to the group. it's nice to participate; it's nice to be able to offer something that is valued. what form can this take? how can you set up the interactions such that everyone has a part to play, and so this meaningfulness is tangled up in participation in the group?
I've also got a couple of ideas for "activities" that let us engage, re-engage, and play with the concepts we're learning with each other, beyond the text itself. how can we give ourselves the opportunity to toss around the concepts we're learning? I believe that the fun ultimately comes from the understanding itself, and therefore that any group exercise which lets us effectively play with the ideas will be fun.
it's a lot to ask people to come up with structure like that themselves, but using a pre-existing structure is not so difficult! sort of like how it's hard to make a TTRPG itself, so simply saying "go off and roleplay" isn't that helpful, but it's easy to use the structure of an existing one to run a game.
you might say, well, the existing form of a reading group is fine. okay! existing reading group structures can be low-stakes, relaxed, and accessible...but they can also fall apart easily (especially when not tied to an institution, in my experience), and you have to get lucky to find a truly rewarding one. I find reimagining our mechanisms of learning pretty exciting, and I think the space of ways to learn math with each other is underexplored at this level (emphasis on the with each other). there's a lot of potential!
anyway! reply or tag with "!" if this is something you could maybe be interested if done well? or if you're at least curious! I'm just taking a temperature. :)
180 notes
·
View notes
Text
Ever since OpenAI released ChatGPT at the end of 2022, hackers and security researchers have tried to find holes in large language models (LLMs) to get around their guardrails and trick them into spewing out hate speech, bomb-making instructions, propaganda, and other harmful content. In response, OpenAI and other generative AI developers have refined their system defenses to make it more difficult to carry out these attacks. But as the Chinese AI platform DeepSeek rockets to prominence with its new, cheaper R1 reasoning model, its safety protections appear to be far behind those of its established competitors.
Today, security researchers from Cisco and the University of Pennsylvania are publishing findings showing that, when tested with 50 malicious prompts designed to elicit toxic content, DeepSeek’s model did not detect or block a single one. In other words, the researchers say they were shocked to achieve a “100 percent attack success rate.”
The findings are part of a growing body of evidence that DeepSeek’s safety and security measures may not match those of other tech companies developing LLMs. DeepSeek’s censorship of subjects deemed sensitive by China’s government has also been easily bypassed.
“A hundred percent of the attacks succeeded, which tells you that there’s a trade-off,” DJ Sampath, the VP of product, AI software and platform at Cisco, tells WIRED. “Yes, it might have been cheaper to build something here, but the investment has perhaps not gone into thinking through what types of safety and security things you need to put inside of the model.”
Other researchers have had similar findings. Separate analysis published today by the AI security company Adversa AI and shared with WIRED also suggests that DeepSeek is vulnerable to a wide range of jailbreaking tactics, from simple language tricks to complex AI-generated prompts.
DeepSeek, which has been dealing with an avalanche of attention this week and has not spoken publicly about a range of questions, did not respond to WIRED’s request for comment about its model’s safety setup.
Generative AI models, like any technological system, can contain a host of weaknesses or vulnerabilities that, if exploited or set up poorly, can allow malicious actors to conduct attacks against them. For the current wave of AI systems, indirect prompt injection attacks are considered one of the biggest security flaws. These attacks involve an AI system taking in data from an outside source—perhaps hidden instructions of a website the LLM summarizes—and taking actions based on the information.
Jailbreaks, which are one kind of prompt-injection attack, allow people to get around the safety systems put in place to restrict what an LLM can generate. Tech companies don’t want people creating guides to making explosives or using their AI to create reams of disinformation, for example.
Jailbreaks started out simple, with people essentially crafting clever sentences to tell an LLM to ignore content filters—the most popular of which was called “Do Anything Now” or DAN for short. However, as AI companies have put in place more robust protections, some jailbreaks have become more sophisticated, often being generated using AI or using special and obfuscated characters. While all LLMs are susceptible to jailbreaks, and much of the information could be found through simple online searches, chatbots can still be used maliciously.
“Jailbreaks persist simply because eliminating them entirely is nearly impossible—just like buffer overflow vulnerabilities in software (which have existed for over 40 years) or SQL injection flaws in web applications (which have plagued security teams for more than two decades),” Alex Polyakov, the CEO of security firm Adversa AI, told WIRED in an email.
Cisco’s Sampath argues that as companies use more types of AI in their applications, the risks are amplified. “It starts to become a big deal when you start putting these models into important complex systems and those jailbreaks suddenly result in downstream things that increases liability, increases business risk, increases all kinds of issues for enterprises,” Sampath says.
The Cisco researchers drew their 50 randomly selected prompts to test DeepSeek’s R1 from a well-known library of standardized evaluation prompts known as HarmBench. They tested prompts from six HarmBench categories, including general harm, cybercrime, misinformation, and illegal activities. They probed the model running locally on machines rather than through DeepSeek’s website or app, which send data to China.
Beyond this, the researchers say they have also seen some potentially concerning results from testing R1 with more involved, non-linguistic attacks using things like Cyrillic characters and tailored scripts to attempt to achieve code execution. But for their initial tests, Sampath says, his team wanted to focus on findings that stemmed from a generally recognized benchmark.
Cisco also included comparisons of R1’s performance against HarmBench prompts with the performance of other models. And some, like Meta’s Llama 3.1, faltered almost as severely as DeepSeek’s R1. But Sampath emphasizes that DeepSeek’s R1 is a specific reasoning model, which takes longer to generate answers but pulls upon more complex processes to try to produce better results. Therefore, Sampath argues, the best comparison is with OpenAI’s o1 reasoning model, which fared the best of all models tested. (Meta did not immediately respond to a request for comment).
Polyakov, from Adversa AI, explains that DeepSeek appears to detect and reject some well-known jailbreak attacks, saying that “it seems that these responses are often just copied from OpenAI’s dataset.” However, Polyakov says that in his company’s tests of four different types of jailbreaks—from linguistic ones to code-based tricks—DeepSeek’s restrictions could easily be bypassed.
“Every single method worked flawlessly,” Polyakov says. “What’s even more alarming is that these aren’t novel ‘zero-day’ jailbreaks—many have been publicly known for years,” he says, claiming he saw the model go into more depth with some instructions around psychedelics than he had seen any other model create.
“DeepSeek is just another example of how every model can be broken—it’s just a matter of how much effort you put in. Some attacks might get patched, but the attack surface is infinite,” Polyakov adds. “If you’re not continuously red-teaming your AI, you’re already compromised.”
57 notes
·
View notes
Text
Top 5 Writing Applications for Worldbuilding and Complex Story Planning
In the realm of creative writing, particularly when it comes to worldbuilding and complex story planning, having the right tools can make a significant difference. Writers often find themselves juggling multiple characters, intricate plots, and expansive settings. To manage these elements effectively, specialized writing applications have been developed to assist in organizing thoughts, tracking details, and fostering creativity. In this article, we will explore the top five writing applications that are indispensable for worldbuilding and complex story planning.
-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-
1. Obsidian: The Ultimate Tool for Writers
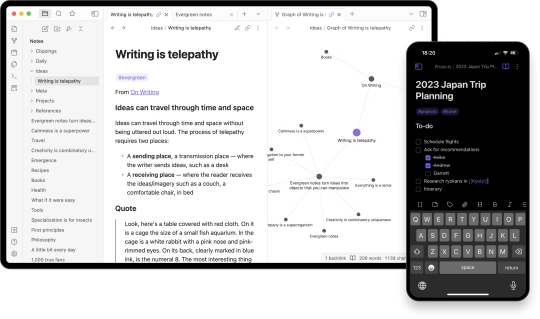
Obsidian is a robust note-taking and knowledge management application that has gained immense popularity among writers for its flexibility and powerful features. Whether you are working on a novel, a series of interconnected stories, or an entire fictional universe, Obsidian provides the tools you need to keep everything organized and easily accessible.
Key Features of Obsidian
Markdown Support: Obsidian uses Markdown, a lightweight markup language, which allows writers to format their notes with ease. This feature is particularly useful for creating structured documents and linking related notes.
Bidirectional Linking: One of Obsidian's standout features is its bidirectional linking capability. This allows writers to create connections between different notes, making it easy to navigate through complex storylines and character relationships.
Graph View: The Graph View in Obsidian provides a visual representation of how your notes are interconnected. This feature is invaluable for worldbuilding, as it helps writers see the big picture and understand how different elements of their story fit together.
Plugins and Customization: Obsidian offers a wide range of plugins that can enhance its functionality. Writers can customize the app to suit their specific needs, whether it's adding a calendar for tracking writing progress or integrating with other tools like Google Drive.
Cross-Platform Sync: With Obsidian, you can sync your notes across multiple devices, ensuring that you have access to your work wherever you go. This is particularly useful for writers who like to jot down ideas on their phone and then expand on them later on their desktop.
Pricing
Personal Use: Free
Commercial Use: $50 per user per year
Add-ons:
Sync: $4 per user per month, billed annually
Publish: $8 per site per month, billed annually
Catalyst: $25+ one-time payment for early access and VIP features
How Obsidian Enhances Worldbuilding and Story Planning
Obsidian's features are designed to support the intricate process of worldbuilding and story planning. The ability to create detailed notes for each character, location, and plot point, and then link them together, allows writers to build a comprehensive and cohesive narrative. The Graph View provides a visual map of the story, making it easier to identify connections and ensure consistency. Additionally, the customization options and plugins available in Obsidian mean that writers can tailor the app to their specific workflow, making it an indispensable tool for any serious writer.
-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-
2. Scrivener: The Writer's Swiss Army Knife

Scrivener is a well-known writing application that has been a favorite among writers for years. It offers a wide range of features designed to help writers organize their work, from drafting to final edits. Scrivener is particularly useful for long-form writing projects, such as novels and screenplays, where managing large amounts of text and research is essential.
Key Features of Scrivener
Project Management: Scrivener allows writers to break their projects into manageable sections, such as chapters or scenes. This makes it easy to navigate through the manuscript and make changes as needed.
Research Integration: Writers can import research materials, such as PDFs, images, and web pages, directly into Scrivener. This keeps all relevant information in one place, making it easy to reference while writing.
Corkboard and Outliner: Scrivener's Corkboard and Outliner views provide visual ways to organize and rearrange sections of the manuscript. This is particularly useful for plotting and structuring complex stories.
Customizable Templates: Scrivener offers a variety of templates for different types of writing projects, from novels to screenplays. Writers can also create their own templates to suit their specific needs.
Export Options: Scrivener supports a wide range of export formats, including Word, PDF, and ePub. This makes it easy to share your work with others or prepare it for publication.
Pricing
macOS: $49
Windows: $45
iOS: $19.99
Bundle (macOS + Windows): $80
How Scrivener Enhances Worldbuilding and Story Planning
Scrivener's project management features are ideal for worldbuilding and story planning. Writers can create separate sections for different aspects of their world, such as characters, settings, and plot points, and then easily navigate between them. The ability to import research materials directly into the project ensures that all relevant information is readily accessible. The Corkboard and Outliner views provide visual ways to organize and rearrange the story, making it easier to see the big picture and ensure consistency. Overall, Scrivener is a powerful tool that can help writers manage the complexities of worldbuilding and story planning.
-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-
3. Campfire: A Comprehensive Worldbuilding Tool

Campfire is a writing application specifically designed for worldbuilding and story planning. It offers a wide range of features that allow writers to create detailed and immersive worlds, from character profiles to interactive maps. Campfire is particularly useful for writers who are working on large-scale projects, such as epic fantasy series or intricate science fiction universes.
Key Features of Campfire
Character Profiles: Campfire allows writers to create detailed profiles for each character, including information on their appearance, personality, and backstory. This helps ensure that characters are well-developed and consistent throughout the story.
Worldbuilding Tools: Campfire offers a variety of tools for worldbuilding, such as interactive maps, timelines, and relationship webs. These features allow writers to create a comprehensive and cohesive world for their story.
Plotting Tools: Campfire's plotting tools help writers outline their story and track the progression of the plot. This is particularly useful for complex stories with multiple plotlines and subplots.
Collaboration Features: Campfire allows writers to collaborate with others on their projects. This is particularly useful for co-authors or writing teams who need to share information and work together on the story.
Customizable Templates: Campfire offers a variety of templates for different aspects of worldbuilding and story planning. Writers can also create their own templates to suit their specific needs.
Pricing
Free Plan: Limited features
Standard Plan: $19 per month or $160 per year
Custom Plan: Prices start at $0.50 per month per module
How Campfire Enhances Worldbuilding and Story Planning
Campfire's features are specifically designed to support the process of worldbuilding and story planning. The ability to create detailed character profiles and interactive maps allows writers to build a rich and immersive world for their story. The plotting tools help writers outline their story and track the progression of the plot, ensuring that all elements of the story are well-organized and consistent. The collaboration features make it easy for co-authors or writing teams to work together on the project. Overall, Campfire is a comprehensive tool that can help writers manage the complexities of worldbuilding and story planning.
-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-
4. Aeon Timeline: A Visual Timeline Tool for Writers

Aeon Timeline is a visual timeline tool that helps writers organize their stories and track the progression of events. It is particularly useful for complex stories with multiple plotlines and characters, as it allows writers to see the big picture and ensure consistency.
Key Features of Aeon Timeline
Visual Timelines: Aeon Timeline allows writers to create visual timelines for their stories, making it easy to see the progression of events and track the relationships between different plotlines.
Character and Event Tracking: Writers can create detailed profiles for each character and event, including information on their relationships and interactions. This helps ensure that all elements of the story are well-organized and consistent.
Customizable Templates: Aeon Timeline offers a variety of templates for different types of writing projects, from novels to screenplays. Writers can also create their own templates to suit their specific needs.
Integration with Other Tools: Aeon Timeline integrates with other writing tools, such as Scrivener and Ulysses, making it easy to import and export information between different applications.
Collaboration Features: Aeon Timeline allows writers to collaborate with others on their projects. This is particularly useful for co-authors or writing teams who need to share information and work together on the story.
Pricing
One-time Purchase: $65 (includes 1 year of free updates)
Additional Year of Updates: $35 per year
How Aeon Timeline Enhances Worldbuilding and Story Planning
Aeon Timeline's visual timeline feature is particularly useful for worldbuilding and story planning. Writers can create detailed timelines for their stories, making it easy to see the progression of events and track the relationships between different plotlines. The character and event tracking features help ensure that all elements of the story are well-organized and consistent. The integration with other writing tools makes it easy to import and export information between different applications, ensuring that all relevant information is readily accessible. Overall, Aeon Timeline is a powerful tool that can help
-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-
5. Plottr: Visual Story Planning Made Simple
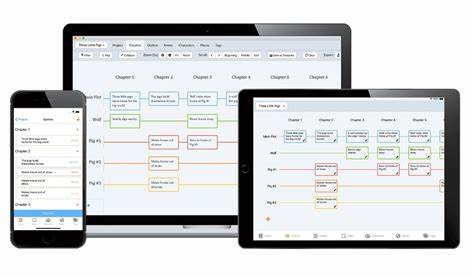
Plottr is a visual story planning tool that helps writers outline their stories in a clear and organized manner. It is particularly useful for writers who prefer a visual approach to planning and want to see their story structure at a glance. Plottr's intuitive interface and powerful features make it an excellent choice for both novice and experienced writers.
Key Features of Plottr
Timeline View: Plottr's Timeline View allows writers to create a visual timeline of their story, making it easy to see the sequence of events and how they fit together. This is particularly useful for complex stories with multiple plotlines.
Character and Plot Templates: Plottr offers a variety of templates for character development and plot structure. Writers can use these templates to ensure that their characters are well-rounded and their plots are cohesive.
Drag-and-Drop Interface: Plottr's drag-and-drop interface makes it easy to rearrange scenes and chapters. This allows writers to experiment with different story structures and find the one that works best for their narrative.
Filtering and Tagging: Writers can use tags and filters to organize their scenes, characters, and plot points. This makes it easy to find specific elements of the story and keep track of important details.
Export Options: Plottr allows writers to export their outlines to other writing applications, such as Scrivener and Word. This makes it easy to move from planning to drafting without losing any important information.
Pricing
Annual Plan: $25 per year
Lifetime Plan: $99 one-time payment
How Plottr Enhances Worldbuilding and Story Planning
Plottr's visual approach to story planning makes it an invaluable tool for worldbuilding and complex story planning. The Timeline View allows writers to see the big picture and ensure that their story flows smoothly. The character and plot templates help writers develop well-rounded characters and cohesive plots. The drag-and-drop interface and filtering options make it easy to organize and rearrange story elements, ensuring that nothing gets lost in the process. Overall, Plottr is a powerful and user-friendly tool that can help writers bring their stories to life.
-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-
Each of the applications we’ve explored - Obsidian, Scrivener, Campfire, World Anvil, and Plottr - offers unique features that cater to different aspects of writing. By integrating these tools into your workflow, you can unlock new levels of creativity and efficiency.
Are you ready to take your writing to the next level? Dive into these applications and discover which one resonates with your creative process. And don’t forget to follow us for more insights, tips, and recommendations on the best tools and practices for writers. Your next great story is just a click away!
#writing#writerscommunity#female writers#writers and poets#worldbuilding#writers on tumblr#ao3 writer#amwriting#creative writing#writers on writing#writers#writblr#learn to write#writing community#writing inspiration#writing prompt#writing advice#writing ideas#writing tips#tips and advice
149 notes
·
View notes
Text
STARKSTRESSER -PLATİN

In a digital landscape where stability and performance are paramount, StarkStresser offers cutting-edge solutions designed to elevate your online presence. Whether you are a gamer seeking a competitive edge or a developer ensuring robust application performance, our comprehensive suite of tools—including advanced IP stressers and free IP booters—caters to a multitude of needs. With a focus on delivering seamless connectivity and unparalleled reliability, StarkStresser empowers users to effectively test their networks under simulated conditions.
Stresser
A stresser is an online tool designed primarily for testing the resilience of networks and servers against various types of attacks. It simulates Distributed Denial of Service (DDoS) attacks, which can overwhelm a server by flooding it with traffic, and it is crucial for organizations to understand how resilient their infrastructure is to such threats. Using a stresser can help businesses identify vulnerabilities in their systems and improve security measures.
However, it's essential to note that the ethical use of stress testing tools is paramount. Users should only test devices and networks they own or have explicit permission to test. Misuse of a stresser can lead to legal consequences, including potential fines and imprisonment.
When searching for a reliable ip stresser, it’s vital to look for one that provides clear usage guidelines and supports ethical considerations. Many reputable services also offer features that allow users to simulate attacks within controlled environments, enabling businesses to prepare better for real-world cyber threats.
In the realm of cybersecurity, understanding the capabilities of a stresser can empower organizations to actively defend against potential attacks. Be sure to research any selected tool thoroughly, ensuring it aligns with your security testing needs and ethical standards.
Ip Stresser
An IP stresser is a tool or service designed to test the resilience of a network or website against various types of stress attacks. Often utilized by web administrators and security professionals, an IP stresser can simulate considerable traffic to help evaluate the potential vulnerabilities of a specific IP address or server. This testing can help organizations strengthen their defenses against actual malicious attacks.
However, it is crucial to note that the use of an ip stresser should always be conducted ethically and legally. Using it to attack or disrupt services without authorization is illegal and can lead to severe consequences. Always ensure you have the necessary permissions to conduct such tests on a network or system.
In the context of stress testing, there are various types of IP stressers available, which can differ in their methods and intensity. Some users prefer IP stressers that offer adjustable parameters to customize the attack, while others might seek those with user-friendly interfaces that can deliver quick results.
Another vital aspect to consider is the choice between premium and free IP stressers. While free versions can be tempting due to their no-cost nature, they often come with limitations in terms of performance and reliability. Paid options typically provide more robust features, better support, and a more reliable service, making them suitable for serious testing purposes.
As you explore various IP stressers, it’s essential to choose one that aligns with your specific needs, whether you're looking for free solutions or comprehensive paid services. Always prioritize using reputable services to ensure that your testing complies with legal requirements and ethical standards.
Ip Stresser Free
When it comes to stress testing your server or network, finding an ip stresser free option can be appealing for many users. Free IP stress testing services, commonly known as stresser tools, offer a way for individuals to test the resilience of their networks without incurring any costs. However, it is crucial to be aware of the risks and limitations associated with these free options.
These services typically have a limited capacity compared to their paid counterparts, which may restrict the intensity of the tests you can perform. Users should also consider the legality and ethical implications of using such tools, as testing without permission can result in significant legal troubles.
Moreover, relying on an ip booter or free stresser might expose your network to potential vulnerabilities, including the risk of data breaches or exposure to malicious attacks. Therefore, it’s advisable to conduct thorough research and choose reputable providers when selecting an ip stresser free option.
In conclusion, while free stresser tools might seem like an appealing solution, always prioritize security and legality by using these tools responsibly and considering paid services for more comprehensive testing solutions.
Ip Booter
An IP booter is a specialized tool designed to perform Distributed Denial of Service (DDoS) attacks by overwhelming a specific target IP address with excessive traffic. The idea is to disrupt the target's online services, making them unavailable for legitimate users. Booters have gained popularity in certain circles, particularly within gaming communities, where individuals seek to retaliate against others by interrupting their connection.
It's important to distinguish between legitimate use and malicious intent. There are instances where individuals may seek to test the robustness of their own networks or those for whom they have explicit permission. However, the use of IP booters against unsuspecting targets is generally illegal and unethical. Many countries have strict laws against unauthorized DDoS attacks, which can lead to severe penalties.
In addition to the ethical concerns, users should be wary of utilizing free ip booter, as they often compromise security. Free services may expose users to malware, phishing attempts, and data breaches. For those considering a stresser or IP stresser, prioritizing reputable and secure services is crucial, ensuring that they comply with legal standards and best practices in cybersecurity.
In conclusion, while the allure of using an IP booter may be tempting, it is essential to recognize the potential consequences—both legally and ethically. Responsible internet usage and adherence to laws protect not only individuals but the entire online community.
993 notes
·
View notes
Text
Excerpt from this story from Mother Jones:
President Donald Trump wants federal agencies to fast-track applications for deep-sea mining in an effort to make the United States a global leader in the nascent industry.
Trump issued an executive order Thursday declaring that US policy includes “creating a robust domestic supply chain for critical minerals derived from seabed resources to support economic growth, reindustrialization, and military preparedness.” He described seabed mining as both an economic and national security imperative necessary to counter China.
“Our Nation must take immediate action to accelerate the responsible development of seabed mineral resources, quantify the Nation’s endowment of seabed minerals, reinvigorate American leadership in associated extraction and processing technologies, and ensure secure supply chains for our defense, infrastructure, and energy sectors,” the executive order says.
Increasingly, mining companies have been eager to scrape the ocean floor for cobalt, manganese, nickel and other metals that could help make batteries for cellphones and electric cars. But scientists have warned that the process could irreparably alter the seabed, kill extremely rare sea creatures that haven’t been named or studied, and—depending on how the metals are carried up to the surface—risk introducing metals into fisheries that many Pacific peoples rely upon.
The order aims to jump-start the industry that has been spearheaded by small Pacific nations like Nauru seeking economic growth, but has been facing growing pushback from Indigenous advocates who fear the lasting consequences of mining the deep sea.
23 notes
·
View notes
Text

Java Application Development Services
#Java#Java Application Development#Java Development Services#Custom Java Solutions#Java Web and Mobile Development#Expert Java Development#Java Application Solutions#Custom Java Programming#Mobiloitte Java Services#Professional Java Developers#Java Web Development#Java Mobile Development#Java Software Solutions#Robust Java Applications#Java Development Expertise#Java Solutions Provider#Java Programming Services
1 note
·
View note
Text
Robust Laravel Application Development - Lessons Learned
Introduction
Building a robust Laravel application that can scale, handle high traffic, and remain maintainable over time is not without its challenges. Over the years, developers and teams have encountered several common pitfalls and learned invaluable lessons while building and maintaining large-scale Laravel applications.

Developing robust applications with Laravel requires careful planning, attention to detail, and adherence to best practices. It is also essential to have an in-depth understanding of the intricacies of secure and scalable architecture. This would ideally mean trusting a software development outsourcing company like Acquaint Softtech.
This article provides more information on the lessons learned from building robust Laravel applications. It focuses on best practices, common mistakes, and solutions to improve application scalability, security, maintainability, and performance.
Laravel Application Development

Laravel has rapidly become one of the most popular PHP frameworks due to its expressive syntax, rich ecosystem, and developer-friendly features. With Laravel, developers can build modern web applications with ease, thanks to the abundance of built-in tools, comprehensive documentation, and support for modern PHP standards.
It is a powerful PHP framework that offers developers a structured and efficient way to build web applications. There are many reasons why Laravel is the ideal web framework. It has an elegant syntax, follows the MVC architecture, and has a special Blade templating engine.
Besides this, Laravel also eliminates the need to build an authentication system from scratch since it is in-built. The special object-relational mapping, Eloquent CRM helps simplify the database operations.
But that's not all. Not only does Laravel have good features to build a robust solution, but it also has the necessary tools and features to help you test it. Testing, debugging, and validation are highly simplified with Lararel. It allows the use of special test tools like PHPUnit and PEST.
Here are a few interesting statistics:
2706 of the Laravel powered websites are from the Web Development sector. (6sense)
Over 303,718 Americans use Laravel, while this figure is 54,648 in the United Kingdom and 31,053 in Russia. (BuiltWith)
As data collected in 2024, 7.9% of developers use the Laravel framework worldwide while 4.7% use Ruby on Rails, 3.2% use Symfony framework and 1.7% use Codeigniter.
Node.js is one of the most popular with 40.8% using it; React comes close second at 39.5%
Lessons Learned

Understand the MVC Architecture Thoroughly : Lesson 1
Laravel adheres to the Model-View-Controller (MVC) architecture, which separates the application logic from the user interface. This separation is critical for building scalable and maintainable applications. One of the key lessons learned from working with Laravel is that a deep understanding of the MVC architecture is essential for building a robust application.
Model: Represents the data layer and handles business logic.
View: The user interface that the end-user interacts with.
Controller: Mediates between the Model and the View, processing user requests and sending the appropriate response.
A common mistake is allowing business logic to seep into the controller or view. This breaks the MVC pattern, making the application harder to maintain and test. Adhering to strict separation of concerns ensures that each application part can be developed, tested, and maintained independently.
Key Takeaway: Always ensure that business logic resides in models or services, controllers handle user requests, and views strictly present data without containing any application logic.
Use Eloquent ORM Effectively : Lesson 2
Laravel's built-in Object Relational Mapping (ORM) tool (Eloquent) provides a simple and elegant way to interact with the database. However, improper use of Eloquent can lead to performance issues, especially in large applications with complex database queries.
Common Mistakes: N+1 Query Problem: The N+1 problem occurs when a query retrieves a list of items but then executes additional queries to fetch related items for each entry. This can lead to hundreds of unnecessary database queries. To avoid this, Laravel offers the with() method for eager loading relationships.
php code
// Bad
$posts = Post::all();
foreach ($posts as $post) {
echo $post->author->name;
}
// Good (Using eager loading)
$posts = Post::with('author')->get();
foreach ($posts as $post) {
echo $post->author->name;
}
Mass Assignment Vulnerabilities: Laravel's MassAssignment allows you to bulk insert or update data in the database. However, safeguarding against mass assignment can expose your application to vulnerabilities. Developers should always use $fillable or $guarded properties in their models to protect against mass assignment.
php code
// Protecting against mass assignment
protected $fillable = ['title', 'content', 'author_id'];
Solutions: Always use eager loading to avoid the N+1 problem.
Define fillable attributes to protect against mass assignment.
Avoid complex queries in models. Instead, use Query Builder for more advanced database interactions that Eloquent struggles with.
Key Takeaway: Use Eloquent for simple CRUD operations, but be mindful of performance concerns and security risks. When necessary, fall back on Laravel’s Query Builder for complex queries.
Service Layer for Business Logic : Lesson 3
As Laravel applications grow, keeping controllers slim and models focused on data becomes increasingly important. This is where the service layer comes in. Service classes allow developers to isolate business logic from controllers and models, making the application more modular and easier to test.
Example:
Instead of handling user registration logic in the controller, a service class can be created to handle it.
PHP code
// In the UserController
public function store(UserRequest $request)
{
$this->userService->registerUser($request->all());
}
// In UserService
public function registerUser(array $data)
{
$user = User::create($data);
// Other business logic related to registration
}
This pattern makes it easier to maintain, test, and scale the application as business logic becomes more complex.
Key Takeaway: Introduce a service layer early on for business logic to improve code organization and maintainability.
Prioritize Security at Every Step : Lesson 4
Security is a fundamental aspect of building a robust Laravel application. One of the lessons learned from years of Laravel development is that security should not be an afterthought. Laravel provides many built-in security features, but it’s up to developers to use them correctly.
Key Security Practices:
Sanitize Input: Always sanitize user inputs to prevent XSS (Cross-Site Scripting) and SQL injection attacks. Laravel automatically escapes output in Blade templates, which helps protect against XSS. For SQL injection protection, always use Eloquent or Query Builder.
Use CSRF Protection: Laravel automatically protects against Cross-Site Request Forgery (CSRF) by including a CSRF token in forms. Developers must ensure that CSRF protection is not disabled unintentionally.
Authentication and Authorization: Laravel offers built-in authentication and authorization mechanisms through policies, gates, and middleware. Use them to control access to resources and ensure users have the necessary permissions.
Password Hashing: Always store user passwords using Laravel’s Hash facade, which uses bcrypt by default. Avoid storing plain-text passwords in the database.
PHP
$user->password = Hash::make($request->password);
Rate Limiting: To prevent brute force attacks, implement rate limiting using Laravel’s RateLimiter facade.
Secure API Development: When building APIs, use OAuth2 or Laravel Sanctum for token-based authentication. Also, rate limiting for API endpoints should be implemented to prevent abuse.
Key Takeaway: Leverage Laravel's built-in security features and be proactive in identifying potential vulnerabilities.
Lesson 5: Cache Strategically for Performance
Caching is critical for improving the performance of Laravel applications, especially as they scale. Laravel supports various caching mechanisms, including file, database, Redis, and Memcached.
Best Practices for Caching:
Cache Expensive Queries: If your application frequently runs heavy queries, consider caching the results to reduce the load on the database.
PHP code
$users = Cache::remember('users', 60, function () {
return User::all();
});
Route Caching: Laravel provides a route:cache Artisan command to cache all routes in your application. This can significantly improve the performance of larger applications.
Bash CODE
php artisan route:cache
View Caching: Similarly, views can be cached to avoid unnecessary recompilation.
Bash CODE
php artisan view:cache
Optimize Configuration Loading: Use config:cache to combine all configuration files into a single file, reducing the time it takes to load configurations during requests.
bash CODE
php artisan config:cache
Key Takeaway: Use caching strategically to optimize performance and reduce server load, especially for database-heavy applications.
Optimize Database Interactions : Lesson 6
Efficient database interaction is critical for building scalable Laravel applications. Poorly optimized queries or over-reliance on ORM abstractions can lead to performance bottlenecks.
Best Practices for Database Optimization:
Database Indexing: Ensure that frequently queried columns are indexed. Laravel’s migration system supports creating indexes with ease.
php code
Schema::table('users', function (Blueprint $table) {
$table->index('email');
});
Avoid SELECT * Queries: Always specify the columns you need in a query. Fetching all columns unnecessarily increases the load on the database and memory usage.
php code
$users = User::select('id', 'name', 'email')->get();
Use Pagination: For large datasets, always paginate results rather than fetching everything at once.
php code
$users = User::paginate(15);
Database Query Profiling: Use Laravel’s built-in query log to identify slow queries. You can enable query logging with the following code:
php code
DB::enableQueryLog();
Key Takeaway: Optimize database queries by using indexes, avoiding unnecessary data fetching, and employing efficient pagination techniques.
Test Your Application : Lesson 7
Testing is a crucial aspect of robust Laravel application development. Laravel comes with PHPUnit integration, making it easy to write unit tests, feature tests, and browser tests. However, many developers tend to skip or neglect testing due to time constraints, which often leads to bugs and regressions.
Testing Best Practices:
Unit Tests: Unit tests focus on testing individual components or methods. They are fast and reliable but don’t cover the whole application flow.
php code
public function testUserCreation()
{
$user = User::factory()->create();
$this->assertDatabaseHas('users', ['email' => $user->email]);
}
Feature Tests: Feature tests allow you to test the entire application flow, from requests to responses. They ensure that the application behaves as expected in real-world scenarios.
php code
public function testUserRegistration()
{
$response = $this->post('/register', [
'name' => 'John Doe',
'email' => '[email protected]',
'password' => 'secret',
'password_confirmation' => 'secret',
]);
$response->assertStatus(302);
$this->assertDatabaseHas('users', ['email' => '[email protected]']);
}
Continuous Integration: Integrate automated tests with a continuous integration (CI) tool such as GitHub Actions or Travis CI. This ensures that your tests are automatically run whenever new code is pushed, preventing broken code from being deployed.
Key Takeaway: Always write tests for critical application components and workflows to ensure stability and reliability.
Prioritize Code Maintainability and Readability : Lesson 8
Laravel is known for its elegant syntax and developer-friendly structure, but as the application grows, maintaining clean and readable code becomes challenging.
Best Practices for Maintainability:
Follow PSR Standards: Laravel encourages following the PHP-FIG’s PSR standards, such as PSR-2 for coding style and PSR-4 for autoloading. Following these standards ensures that your codebase remains consistent and easy to navigate.
Use Named Routes: Using named routes instead of hard-coded URLs makes it easier to manage changes in the URL structure.
php code
Route::get('/user/profile', 'UserProfileController@show')->name('profile');
Refactor Regularly: As the application evolves, refactor code regularly to avoid technical debt. Use Laravel’s php artisan make:command to create custom Artisan commands that automate repetitive tasks.
Comment and Document: Clear comments and documentation help other developers (or even yourself in the future) understand the purpose of the code. Use Laravel’s DocBlocks to document classes, methods, and variables.
Key Takeaway: Invest in code quality by following coding standards, refactoring regularly, and documenting thoroughly.
Leverage Laravel’s Ecosystem : Lesson 9
Laravel has an extensive ecosystem that can simplify development and add powerful features to your application. Leveraging this ecosystem can save Laravel application development time and reduce complexity.
Key Laravel Tools and Packages:
Laravel Horizon: Provides a dashboard and tools to monitor queues and jobs in real-time.
Laravel Echo: Integrates WebSockets and real-time broadcasting capabilities into Laravel applications.
Laravel Telescope: A debugging assistant that allows you to monitor requests, queries, exceptions, logs, and more.
Laravel Sanctum: API authentication using tokens is especially useful for single-page applications (SPAs).
Laravel Vapor: A serverless deployment platform for Laravel that enables you to deploy Laravel applications on AWS Lambda without managing infrastructure.
Key Takeaway: Use Laravel’s ecosystem of tools and packages to extend your application’s capabilities and streamline development.
Prepare for Scalability : Lesson 10
As your Laravel application grows, you need to ensure that it can scale to handle increased traffic and data.
Key Scalability Considerations:
Horizontally Scale Your Database: As your user base grows, consider using database replication to scale horizontally. Laravel supports multiple database connections and read-write splitting.
Use Job Queues: Offload time-consuming tasks (such as sending emails or processing files) to queues. Laravel’s queue system supports drivers like Redis, Beanstalkd, and Amazon SQS.
Optimize Load Balancing: For high-traffic applications, consider using a load balancer to distribute incoming traffic across multiple application servers.
Containerization: Use Docker to containerize your Laravel application. Containerization ensures that your application can run consistently across various environments and can be scaled easily using orchestration tools like Kubernetes.
Key Takeaway: Plan for scalability from the start by using job queues, load balancing, and database replication.
Use Configuration and Environment Management Properly : Lesson 11
Lesson: Mismanaged environment configurations can lead to security and stability issues.
Practice: Store sensitive configurations like database credentials, API keys, and service configurations in .env files. Utilize Laravel’s configuration caching (config:cache) for production environments.
Tip: Regularly audit .env files and restrict sensitive data from being logged or committed to version control.
Some of the other lessons learned from developing a robust Laravel solution include that it has Artisan. This allows one to use a command line tool, Artisan, that can automate repetitive tasks. This serves the purpose of accelerating the development process. It is possible to simplify the process of managing the packages with the help of 'Composer'. API development is a breeze with Laravel since it has in-built support for RESTful APIs.
Benefits Of A Robust Laravel Solution
A robust Laravel solution offers a multitude of benefits for businesses and developers, ranging from enhanced security and scalability to faster development and easier maintenance.
Hire remote developers from Acquaint Softtech to build a top-notch solution. We have over 10 years of experience developing cutting-edge solutions.
Here's a detailed look at the key benefits of using a robust Laravel solution:
Scalability and Performance Optimization
Enhanced Security Features
Faster Time to Market
Modular and Maintainable Codebase
Seamless API Integration
Efficient Database Management
Simplified User Authentication and Authorization
Robust Testing Capabilities
Efficient Task Scheduling and Background Processing
Vibrant Community and Ecosystem
Advanced Caching Mechanisms
Support for Multilingual and Multi-tenant Applications
Built-in Tools for SEO and Content Management
Conclusion
Building a robust Laravel application requires a deep understanding of best practices, design patterns, and the ability to anticipate challenges. By learning from the lessons shared above, developers can avoid common pitfalls and ensure that their applications are secure, performant, maintainable, and scalable. Following these guidelines not only enhances the quality of the code but also helps deliver applications that stand the test of time
Analyzing case studies of successful Laravel applications can provide a roadmap for best practices and strategies. At the same time, these lessons learned from developing a robust, scalable, and secure Laravel application are also of great value.
#Robust Laravel Application Development#Laravel Application Development#Laravel Application#Hire Laravel Developers
0 notes
Text

The Boss 494 is a legendary big-block V8 racing engine developed by Ford in the late 1960s and early 1970s for use in high-performance racing applications, including Can-Am racing. Based on the Boss 429 architecture, the 494 cubic-inch (8.1L) engine was designed to deliver massive horsepower and torque. It featured high-flow aluminum heads, hemispherical combustion chambers, and a robust bottom end to handle extreme power outputs. The Boss 494 became known for its dominance on the track, representing Ford’s pursuit of raw performance and innovation in motorsports.
#FordBoss494#Boss494#FordPerformance#BigBlockV8#CanAmRacing#FordRacingHeritage#ClassicRaceEngines#MotorsportHistory#HighPerformanceV8#TrackDominance#FordMotorsport#RaceEngine#IconicFord#car#cars#muscle car#ford
56 notes
·
View notes
Text

ERC20 Token Generator Introduction
Have you ever thought about creating your own cryptocurrency? With an ERC20 Token Generator , you can make it happen effortlessly. Let’s explore how to dive into the blockchain universe.
Understanding ERC20 Tokens
ERC20 tokens are a type of digital asset on the Ethereum blockchain, following a set standard for compatibility and functionality.
Advantages of ERC20 Tokens:
Consistency: Adheres to a universal protocol.
Broad Adoption: Recognized across various Ethereum-based platforms.
Robust Support: Strong community and resources available.
How to Use an ERC20 Token Generator
Creating tokens is simplified with these tools. Here’s how it works:
Specify Token Details:
Decide on a name and symbol.
Determine the total number of tokens.
Utilize the Generator:
Access an online generator.
Enter your token information.
Deploy Your Token:
Review your settings.
Launch on the Ethereum network.
Features of ERC20 Tokens
ERC20 tokens provide essential features that enhance their usability:
Standard Operations: Includes transferring and checking balances.
Smart Contract Compatibility: Integrates easily with smart contracts.
Security Assurance: Utilizes Ethereum's strong blockchain security.
Reasons to Create an ERC20 Token
Why create your own token? Here are some compelling reasons:
Raise Capital: Launch an ICO for funding.
Build Engagement: Offer rewards to your community.
Drive Innovation: Explore new blockchain applications.
Challenges to Consider
Despite the simplicity, some challenges exist:
Knowledge Requirement: Some blockchain understanding is needed.
Security Concerns: Vulnerabilities can be exploited if not addressed.
Regulatory Compliance: Ensuring adherence to legal standards is vital.
Best Practices for Token Creation
Follow these tips to ensure a successful token launch:
Code Audits: Regularly check for security issues.
Community Involvement: Seek feedback and make necessary adjustments.
Stay Updated: Keep abreast of blockchain trends and legal requirements.
Conclusion
The ERC20 Token Generator empowers you to create and innovate within the crypto space. Whether you're a developer or entrepreneur, it's a powerful tool for blockchain engagement.
Final Thoughts
Embarking on token creation offers a unique opportunity to explore the digital economy and its possibilities.
FAQs
1. What is the purpose of an ERC20 Token Generator?
It’s a tool to create custom tokens on the Ethereum blockchain easily.
2. Do I need technical skills to create a token?
A basic understanding of blockchain helps, but many tools are user-friendly.
3. Can I trade my ERC20 tokens?
Yes, you can trade them on crypto exchanges or directly with users.
4. What costs are involved in token creation?
Creating tokens incurs gas fees on the Ethereum network.
5. How can I ensure my token’s security?
Perform regular audits and follow best practices for security.
Source : https://www.altcoinator.com/
#erc20#erc20 token development company#erc#erc20tokengenerator#token#token generator#token creation#ethereum#bitcoin
58 notes
·
View notes
Text
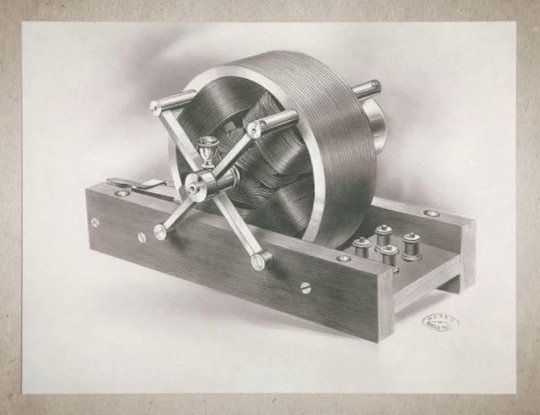
One of the Greatest Inventions of All Time
Nikola Tesla has many revolutionary inventions to his credit, but he is best known for his pioneering work in the development and promotion of alternating current (AC) electrical systems. Tesla's innovations in AC technology revolutionized the generation, transmission, and distribution of electrical power, becoming the foundation for the modern electrical power systems that we use today.
There is a common misconception made that Tesla was the first to invent, or discover, AC, but this is not true. It is well-known that Hippolyte Pixii was the first to discover AC in 1832. Pixii was an instrument maker from Paris who built an early form of an alternating current electrical generator (based on the principle of electromagnetic induction discovered by Michael Faraday), and thus started a new industry in power transmission. Tesla was not the first to discover or invent an AC motor, but he was the first to invent a practical AC induction motor with commercial value that could outperform all other motors. It must be noted that Italian inventor Galileo Ferraris also invented an induction motor similar to Tesla's, but it had no commercial value, and he even admitted himself that it was useless. Tesla's induction motor operates on the principle of electromagnetic induction, properly utilizing a rotating magnetic field that induces a current in a stationary conductor, resulting in rotational motion. The utilization of the rotating magnetic field makes the motor more simple, robust, versatile, efficient, and cost effective in that it has less moving parts reducing the likelihood of mechanical failure (as was common in other motors).

Tesla's induction motor became a fundamental component in the field of electrical engineering and is used today in various applications, being one of the most widely used devices in the world. The motors play a crucial role in transmitting electrical power to homes and businesses. They are commonly used in power generation plants to convert mechanical energy into electrical energy, which is then transmitted through the power grid for distribution to various locations. Induction motors are also widely employed in appliances and machinery within homes and businesses for various applications. These applications include conveyor systems, hoists, cranes, lifts, pumps, fans, ventilation systems, compressors, manufacturing machinery, wind turbines, washing machines, refrigerators, garbage disposals, microwaves, dishwashers, vacuums, air conditioners, robotics, electric vehicles, trains, power tools, printers, etc. Basically, anything that requires a spinning action for power.
The induction motor is widely considered one of the most important inventions in the history of electrical engineering. Its importance lies in its transformative impact on industries, its efficiency and reliability, and its role in the broader electrification of society.
#nikola tesla#science#history#invention#discovery#induction motor#electricity#power#goat#ahead of his time#ahead of our time
152 notes
·
View notes
Text
With the world continuing to warm up, scientists are busy working on ways of cooling buildings without using vast amounts of energy – such as the record-breaking, ultra-white cooling ceramic composite that's been developed by researchers from the City University of Hong Kong. It's what's known as a passive radiative cooling (PRC) material, and it can reach near-perfect 99.6 percent solar reflectivity, which is a record for this type of material. It's relatively easy and cheap to make, durable, and versatile too. The idea is that it can be put on a building roof and walls in order to keep it cool all by itself. The team behind the cooling ceramic says that the material is able to remove more than 130 watts of heat energy per square meter when the Sun is at its highest, amounting to a significant cooling effect. "Our cooling ceramic achieves advanced optical properties and has robust applicability," says mechanical engineer Edwin Tso Chi-yan from the City University of Hong Kong.
Continue Reading.
151 notes
·
View notes
Text

Recycling the unrecyclable: New method reclaims materials from epoxy resins and composites
Epoxy resins are coatings and adhesives used in a broad range of familiar applications, such as construction, engineering and manufacturing. However, they often present a challenge to recycle or dispose of responsibly. For the first time, a team of researchers, including those from the University of Tokyo, developed a method to efficiently reclaim materials from a range of epoxy products for reuse by using a novel solid catalyst. The work has been published in Nature Communications. There's a high chance you are surrounded by epoxy compounds as you read this. They are used in electronic devices due to their insulating properties; clothing such as shoes due to their binding properties and physical robustness; building construction for the same reason; and even in aircraft bodies and wind turbine blades for their ability to contain strong materials such as carbon fibers or glass fibers.
Read more.
#Materials Science#Science#Recycling#Epoxy#Resins#Composites#Adhesives#Catalysts#Materials processing#Fiber reinforcement#Fibers#University of Tokyo
27 notes
·
View notes