#Computer access control
Explore tagged Tumblr posts
Text
Twitter Blue Tests Verification With Government ID and Selfie
X (the social media site formerly known as Twitter) is in the process of launching a new identity verification feature that could prove controversial. The feature, which is currently only offered to/forced on premium “Blue” subscribers, asks users to fork over a selfie and a picture of a government issued ID to verify that they are who they say they are. Mr. Tweet Fumbles Super Bowl Tweet The…

View On WordPress
#Biometrics#Computer access control#Elon Musk#Facial recognition system#Gizmodo#Google#ID.me#Identity document#Identity management#Identity verification service#Internet#Internet privacy#Microsoft#Musk#Nima Owji#PAYPAL#Surveillance#Technology#twitter#Uber#Verification
0 notes
Text
also more codelyokoposting but I really really dig XANA as a villain. It's not a person with a complex background that led them down the path of evil, it's not a morally grey character you sympathize with but condemn. It's a powerful AI capable of controlling almost anything in the real world. It doesn't have a face or a body, we only know it for its symbol and for the monsters it controls in the virtual world. It's willing not just to kill people through various methods (poisoning, drowning, car crash, fucking space lasers too?) but also Earth as a whole (it tried to blow up a NUCLEAR PLANT and crash two trains with toxic chemicals in them). And we don't even know why it does this, at least not for now. It may not even have a particular reason, just some sort of virus or malware in the form of an AI that seeks nothing but destruction without any goals in mind. This "pure evil" characteristic doesn't come off as childish, like in some children cartoons, it's just kind of scary to think that such an incomprehensible and destructive force exists, almost feels like a natural disaster
#m#code lyoko#that said i wish the rules of what xana can and cant do were a bit more established#like not to be a cinemasins but why doesn't it just hack the factory's elevator to stop the group from entering the room#what's stopping it from attacking the real world non stop#i think it would have been great to have an episode where they go like 'hey xana needs to rest after every attack and also we've put -#some measures to always have access to the computer room just in case it tries to block the entrance or the elevator'#idk something a la death note where you know what they can and cant do with the death note#and as always i wish the action was done better because sometimes it's like. girl you can do that very easily#specially in the virtual world. sometimes there'll be one enemy standing still and no one does nothing and then they get killed and like ?#i'd feel more threatened by xana if the monsters also seemed more threatening#and if its attacks were more grounded in reality? like that one episode where it controls yumi's samurai armor. literally what#the earthquake was also very 'oh it can do that i guess'#i like it when it's stuff like the trains almost crashing with each other#the technologic stuff i think works best. especially because it's something not everyone knows how to fight against
128 notes
·
View notes
Text
When I was a kid/teenager I was only allowed 10 to 15 minutes of internet every few days to weeks so when I got my time I would download as many tumblr screenshots as possible, edit out cussing in ms paint, and print them into a huge booklet and I would read them when I was bored like the newspaper
#I also would write out deviantart post captions and tags in notes ahead of time and copy paste them so I could post as much art as I#could before my dad turned off the internet#because it wasn’t like I was told to stop#he turned the internet off on my computer and I didn’t have a phone until I was nearly 18#I figured out I could go on Google on my DS so I would look at fanart on Google images#strict parents#controlling parents#in the bright side I’m 21 now and very good at accessing electronics#cal lore drop
30 notes
·
View notes
Text
Ya think "Flower Journey" would get into controversy within the game world since the wasps are depicted as villains?
I spent too long playing this stupid flappy bird clone and I am forming stupid headcanons surrounding it.
You can probably make the same argument about the enemies in Mite Knight but they're more or less depicted as "mystical creatures".
Don't take this too seriously. I just thought it would be funny to have Flappy Bird be canceled.
#Yeah the wasps are the villains but they were mind controlled and Hoaxe is a fake wasp#they're in that era where tech is getting more prevalent at least outside of termite kingdom and so those games are the first of their kind#idk the timeline for technology evolution is funky like there's a big ol computer who can emote#I think the better way of thinking it is that its more accessible#hooray world building#vio.txt#bug fables#rambles
38 notes
·
View notes
Text
The gauge in front of Corrin refused to move down, the needle slowly climbing higher and higher. She groaned and let her forehead bonk against the display before climbing back down in front of the exposed wires that Trip had been walking her through.
"It's still building up too much pressure. I need…" The decompression won't trigger because the computer is still displaying clear levels. Despite the mocking red needle, the automatic release system isn't set up to take readings after the second valve, because usually the vents take care of it. "If you open access panel 17B you'll find, um, part of a protein resequencer panel."
If the heat from the engine block wasn't already sticking her bangs to her forehead, Corrin would have started sweating. It was made worse with only the comms connecting them, Corrin unable to do anything but wait, imagining Trip prying the panel free. "Hey, Commander, it's nothing to worry about but you should know it's a little--"
"bonkers fucking yonkers" | from @entriprises
His voice was muffled through the level between them, but she could just make it out overlapping with the comm. She really had meant to get the panel switched out, but she hadn't had time to set up an order last time they were docked. And if the fix had stayed operational, well…
"I had to patch it in as a relay after the Conatarri system… if you patch a second signal through it'll start a loop and force a fail state. It's one of the safety protocols to stop duplicate signals from overwhelming the synthesizer at the mess hall, but it should interrupt the pressure readings and force it to vent as an error response…" She's rambling. She knows she's rambling, but she's nervous and she hasn't been prepared for Commander Trip Tucker of all people to have to dig into her work. The work she was so proud of this morning suddenly felt inexperienced and inefficient when imagining it through the eyes of another. She wasn't sure if the ticking clock or the chewing out she was going to get later made her more nervous.
#corrin — these things are your becoming#c — threads#c — verse: enterprise nx-01#c — bonds: trip tucker#entriprises#TEEHEE 🧍🤸🧍#at some point a food synth got replaced and she said oup this circuit board is mine dont mind me#nobody worry that a computer piece from a glorified vending machine is used to control complex pressure balances for the ship#it is also definitely NOT the only thing janky and repurposed just in that access panel alone
6 notes
·
View notes
Text
every day i have the temptation to make a multi for only house lannister
#out of character › rambling again.#having access to my original j.oannas blogs is so bad for my self control. i do nooot have time between my three blogs#i do not need another a.soiaf blog. and yet -#anyw good morning i am gonna go walk because it is windy and mayhap go to the cinema because burrowing in a dark#room sounds good for my nerves with my computer#but gonna work on drafts later. i have a number i want to reach every day while i don't have my pc to continue bg3
2 notes
·
View notes
Text
I hate you two step verification I hate you two step verification I hate you two step verification I hate you two step verification I hate you two step verification I hate you two step verification I hate you two step verification I hate you two step verification I hate you two step verification I hate you two step verification I hate you two step verification I hate you two step verification I hate you two step verification I hate you two step verification I hate you two step verification I hate you two step verification I hate you two step verification I hate you two step verification I hate you two step verification I hate you two step verification
#me genuinely tweaking when i can’t access my computer#no but fr#IM SO SORRY I CHANGED PHONE NUMBER MICROSOFT#CLEARLY I AM TRYING TO STEAL MY OWN FUCKING IDENTITY#CLEARLY I KNEW MY OWN OLD PHONE NUMBER PASSWORD AND ALTERNATE EMAIL ACCOUNT ONLY TO STEAL MY IDENTITY#LIKE WTF JUST LET ME ACCESS MY OWN GODDAMN ACCOUNT HOLD SHIT WHY IS IT SO DIFFICULT FOR NO REASON#fuck u microsoft#AND WHY DOES MY STUPID GODDAMN OUTLOOK CONTROL WHETHER OR NOT I HAVE ACCESS TO MY C O M P U T E R THATS SO STUPID WTF#microsoft#computer#technology
2 notes
·
View notes
Text
every day the urge to cnc a metal core for a normal plastic beyblade and smoke a bunch of kids grows stronger
Beyblade heavyweight division
#I have access to a cnc#i must use self control#Also#its come to my attention that cnc means something different on tumblr#I am referring to Computer numerical control#Although technically i suppose the actions that are happening to the metal in a CNC machine#are pretty similar to actions taken in the other kind of cnc#these tags have devolved#im gonna quit while im ahead
70K notes
·
View notes
Text
I don't know I'm not done talking about it. It's insane that I can't just uninstall Edge or Copilot. That websites require my phone number to sign up. That people share their contacts to find their friends on social media.
I wouldn't use an adblocker if ads were just banners on the side funding a website I enjoy using and want to support. Ads pop up invasively and fill my whole screen, I misclick and get warped away to another page just for trying to read an article or get a recipe.
Every app shouldn't be like every other app. Instagram didn't need reels and a shop. TikTok doesn't need a store. Instagram doesn't need to be connected to Facebook. I don't want my apps to do everything, I want a hub for a specific thing, and I'll go to that place accordingly.
I love discord, but so much information gets lost to it. I don't want to join to view things. I want to lurk on forums. I want to be a user who can log in and join a conversation by replying to a thread, even if that conversation was two days ago. I know discord has threads, it's not the same. I don't want to have to verify my account with a phone number. I understand safety and digital concerns, but I'm concerned about information like that with leaks everywhere, even with password managers.
I shouldn't have to pay subscriptions to use services and get locked out of old versions. My old disk copy of photoshop should work. I should want to upgrade eventually because I like photoshop and supporting the business. Adobe is a whole other can of worms here.
Streaming is so splintered across everything. Shows release so fast. Things don't get physical releases. I can't stream a movie I own digitally to friends because the share-screen blocks it, even though I own two digital copies, even though I own a physical copy.
I have an iPod, and I had to install a third party OS to easily put my music on it without having to tangle with iTunes. Spotify bricked hardware I purchased because they were unwillingly to upkeep it. They don't pay their artists. iTunes isn't even iTunes anymore and Apple struggles to upkeep it.
My TV shows me ads on the home screen. My dad lost access to eBook he purchased because they were digital and got revoked by the company distributing them. Hitman 1-3 only runs online most of the time. Flash died and is staying alive because people love it and made efforts to keep it up.
I have to click "not now" and can't click "no". I don't just get emails, they want to text me to purchase things online too. My windows start search bar searches online, not just my computer. Everything is blindly called an app now. Everything wants me to upload to the cloud. These are good tools! But why am I forced to use them! Why am I not allowed to own or control them?
No more!!!!! I love my iPod with so much storage and FLAC files. I love having all my fics on my harddrive. I love having USBs and backups. I love running scripts to gut suck stuff out of my Windows computer I don't want that spies on me. I love having forums. I love sending letters. I love neocities and webpages and webrings. I will not be scanning QR codes. Please hand me a physical menu. If I didn't need a smartphone for work I'd get a "dumb" phone so fast. I want things to have buttons. I want to use a mouse. I want replaceable batteries. I want the right to repair. I grew up online and I won't forget how it was!
68K notes
·
View notes
Text
simon changed the default settings to print to the upstairs printer (why????) AND he made it so if i change it to the new printer/photocopier, the default is two-sided.
he's onto me. he's aware of how much paper i'm printing and is trying to control me.
#no i don't like him#he's out of control#he thinks the rent is too high (above market rate apparently) and wants to work toward being officeless and everyone working from home#that's so easy for him to say as he caravans around Australia remotely accessing any computer he wishes#sigh#i hate him#without the paper then what do i file????????#my whole job is filing#with no paper then what do i move from one side of the desk to the other????????#think it through Simon!!!!!!!!#he's mad about not getting a seat in the senate with the fusion party#his new project is fixing Sophia's accounting firm#once he's done that then he'll run for the state election against Nick Staikos#people will definitely vote for him if he was able to fix Sophia('s business)!!!!!!!!!!!!!!!#he'll convince everyone what a waste of paper Nick's crosswords are#booooooo#i'm not even bentleigh electorating any more#i don't know what electorate i'm in for the state election#is it next year???#okay i'm just molevern district#oh man michael o'brien i swear he keeps putting things in my letterbox#well him and jeremy cameron obviously#that's still a funny joke i don't care it's funny
0 notes
Text

It’s a good thing that the Inspector is so skilled in so many things that they can simply open a panel to gain access to the station’s computer system and hack it to determine what’s going on in the control booth.
Unfortunately for them, Winnie is at the control station and realises that someone has gotten into the system and attempts to block the Inspector’s access.
#Inspector Spacetime#Cosmos Got Talent (episode)#New Powers As the Plot Demands (trope)#New Powers As the Plot Demands#Hollywood Hacking (trope)#Hollywood Hacking#the Inspector (character)#is so skilled in so many things#they can simply open a panel#gain access to the station's computer system#to determine what's happening#in the control room#Winnie (character)#sits at the control station#realises someone's gotten into the system#attempts to block the Inspector's access#counterhacking
0 notes
Text
Transforming Interaction: A Bold Journey into HCI & UX Innovations.
Sanjay Kumar Mohindroo Sanjay Kumar Mohindroo. skm.stayingalive.in Explore the future of Human-Computer Interaction and User Experience. Uncover trends in intuitive interfaces, gesture and voice control, and emerging brain-computer interfaces that spark discussion. #HCI #UX #IntuitiveDesign In a world where technology constantly redefines our daily routines, Human-Computer Interaction (HCI)…
#Accessibility#Adaptive Interfaces#Brain-Computer Interfaces#Ethical Design#Future Trends In UX#Gesture-Controlled Systems#HCI#Human-Computer Interaction#Innovative Interface Design#Intuitive Interfaces#Multimodal Interaction#News#Sanjay Kumar Mohindroo#Seamless Interaction#user experience#User-Centered Design#UX#Voice-Controlled Systems
0 notes
Text
guess who had to put parental controls on YouTube because someone was constantly distracted and unable to animate. On the other hand, now I'm getting distracted by tumblr.
#can i legally tag this as animation despite there being no art#do you think more parental controls is smart or will that ruin my computer#in all honesty maybe allowing myself free internet access as a whole was a bad idea#for the record im an adult and can roam the internet if I want#the question is SHOULD I#animation
0 notes
Text
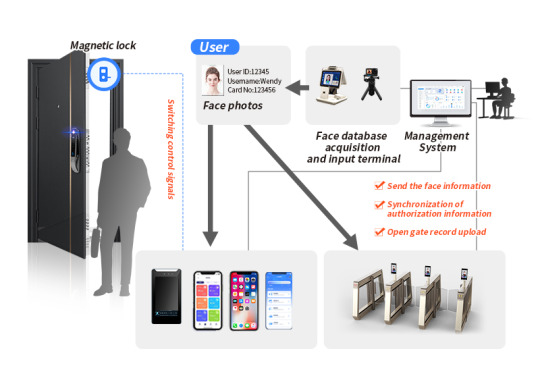
Solution of Edge Computing Access Control Screen Based on FET3568-C SoM
Edge Computing Access Screen is designed to provide an edge computing-based solution for access control systems. It can realize face recognition, data processing, fingerprint recognition and other functions, and improve the security and convenience of the access control system. In terms of application scenarios, intelligent monitoring and access control system is an important part of intelligent building security.
The application of edge computing technology can increase the monitoring effect and response speed, avoid the security risks in the process of data transmission, and protect the privacy of users. Edge computing devices can process authentication faster and improve the response speed and security of access control systems.
Hardware requirements for edge computing access control screen
(1) Processor
Select a high-performance and low-power embedded processor, the processor itself needs to come with arithmetic power to meet the needs of edge computing.
(2) Memory
Configure appropriate memory and flash for system and application data.
(3) Interface
Provide necessary interfaces between the carrier board and other devices, such as GPIO, UART, I2C, SPI, etc.
(4) Communication module
Support Wi-Fi or 4G to facilitate data transmission with the cloud platform.
(5) Sensor
Integrate multiple sensors, such as face recognition, fingerprint recognition, and RF card reader.
Edge Computing Access Control Screen Design
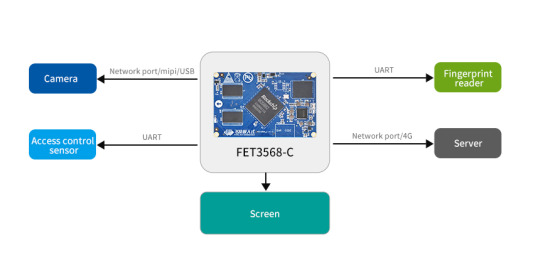
The FET3568-C SoM is recommended to be used as the hardware platform of edge computing access control screen. The system on module has a quad-core ARM Cortex-A55 processor with a main frequency of 2.0 GHz, and its own NPU has a computing power of 1TOPS, which can meet the needs of lightweight edge computing tasks.
Memory: FET3568-C SoM supports LPDDR4 and eMMC storage, and can be configured with appropriate memory and flash memory to meet the needs of the access control system.
Interface: Native GPIO, UART, I2C, SPI, Gigabit port, etc. can communicate with other lines.
Communication module: FET3568-C supports wireless communication technologies such as Wi-Fi, Bluetooth, and GPS. The appropriate communication module can be selected according to the requirements.
Sensors: FET3568-C supports multiple sensor interfaces, such as GPIO, I2C, SPI, etc., and can easily integrate multiple sensors, including face recognition, fingerprint recognition modules, etc.
Power supply module: According to the requirements of the access control system, the appropriate power supply chip can be selected to provide stable and reliable power supply for the entire carrier board.
Peripheral expansion: USB and SD card slots are convenient for secondary development and function expansion.
Originally published at www.forlinx.net.
0 notes
Text
I am begging people to use LibreOffice and personal storage devices like hard drives or USB sticks instead of relying 100% on Google Docs. LibreOffice is free and open-source, it saves files to your own computer, and it lets you save as many different file types. You can write in it, format ebooks in it, and do everything you might possibly need to do as a writer.
"Oh, but I'll lose my USB stick--" Fine, back things up in whatever cloud you use as a form of extra protection, but you should also try your absolute damnedest to also put them on some form of storage that isn't a cloud.
I know it's not accessible to everyone, but if you at all have the ability, don't rely on shit that lives on other people's computers. Especially with everything going on with AI theft and aggressive censorship of adult media. If you don't store your files on your own personal computer that you have control over, your files aren't fully yours, and they're at the whims of whoever owns the cloud.
Learn where your files are stored and how to access them. Get into the habit of backing up your files to your own personal storage. Even if you're not up for intense tech research and you don't care about how the computer actually works, please stop letting your art live in corporate clouds.
#every time I see another writer post that they only use Google Docs#part of me dies inside#original post
8K notes
·
View notes
Text
NTT Unveils Breakthrough AI Inference Chip for Real-Time 4K Video Processing at the Edge
New Post has been published on https://thedigitalinsider.com/ntt-unveils-breakthrough-ai-inference-chip-for-real-time-4k-video-processing-at-the-edge/
NTT Unveils Breakthrough AI Inference Chip for Real-Time 4K Video Processing at the Edge
In a major leap for edge AI processing, NTT Corporation has announced a groundbreaking AI inference chip that can process real-time 4K video at 30 frames per second—using less than 20 watts of power. This new large-scale integration (LSI) chip is the first in the world to achieve such high-performance AI video inferencing in power-constrained environments, making it a breakthrough for edge computing applications.
Revealed during NTT’s Upgrade 2025 summit in San Francisco, the chip is designed specifically for deployment in edge devices—hardware located physically close to the source of data, like drones, smart cameras, and sensors. Unlike traditional AI systems that rely on cloud computing for inferencing, this chip brings powerful AI capabilities directly to the edge, drastically reducing latency and eliminating the need to transmit ultra-high-definition video to centralized cloud servers for analysis.
Edge Computing vs. Cloud Computing: Why It Matters
In traditional cloud computing, data from devices like drones or cameras is sent to remote data centers—often located hundreds or thousands of miles away—where it’s processed and analyzed. While this approach offers virtually unlimited compute power, it introduces delays due to data transmission, which is problematic for real-time applications like autonomous navigation, security monitoring, and live decision-making.
By contrast, edge computing processes data locally, on or near the device itself. This reduces latency, preserves bandwidth, and enables real-time insights even in environments with limited or intermittent internet connectivity. It also enhances privacy and data security by minimizing the need to transmit sensitive data over public networks.
NTT’s new AI chip fully embraces this edge-first philosophy—delivering real-time 4K video analysis directly within the device, without relying on the cloud.
A New Era for Real-Time AI on Drones and Devices
With this chip installed, a drone can detect people or objects from up to 150 meters (492 feet)—the legal altitude limit for drones in Japan. That’s a dramatic improvement over traditional real-time AI systems, which are generally limited to a 30-meter range due to lower resolution or processing speed.
This advancement enables a host of new use cases, including:
Infrastructure inspections in hard-to-reach places
Disaster response in areas with limited connectivity
Agricultural monitoring across wide fields
Security and surveillance without constant cloud uplinks
All of this is achieved with a chip that consumes less than 20 watts—dramatically lower than the hundreds of watts required by GPU-powered AI servers, which are impractical for mobile or battery-powered systems.
Inside the Chip: NTT’s Proprietary AI Inference Engine
The LSI’s performance hinges on NTT’s custom-built AI inference engine, which ensures high-speed, accurate results while minimizing power use. Key innovations include:
Interframe correlation: By comparing sequential video frames, the chip reduces redundant calculations, improving efficiency.
Dynamic bit-precision control: This technique adjusts the numerical precision required on the fly, using fewer bits for simpler tasks, conserving energy without compromising accuracy.
Native YOLOv3 execution: The chip supports direct execution of You Only Look Once v3, one of the fastest real-time object detection algorithms in machine learning.
These combined features allow the chip to deliver robust AI performance in environments previously considered too power- or bandwidth-limited for advanced inferencing.
Path to Commercialization and the IOWN Vision
NTT plans to commercialize the chip within fiscal year 2025 through its operating company, NTT Innovative Devices Corporation.
Researchers are already exploring its integration into the Innovative Optical and Wireless Network (IOWN)—NTT’s next-generation infrastructure vision aimed at overhauling the digital backbone of modern society. Within IOWN’s Data-Centric Infrastructure (DCI), the chip would take advantage of the All-Photonics Network for ultra-low latency, high-speed communication, complementing the local processing power it brings to edge devices.
NTT is also collaborating with NTT DATA, Inc. to combine the chip’s capabilities with its Attribute-Based Encryption (ABE) technology, which enables secure, fine-grained access control over sensitive data. Together, these technologies will support AI applications that require both speed and security—such as in healthcare, smart cities, and autonomous systems.
A Legacy of Innovation and a Vision for the Future
This AI inference chip is the latest demonstration of NTT’s mission to empower a sustainable, intelligent society through deep technological innovation. As a global leader with over $92 billion in revenue, 330,000 employees, and $3.6 billion in annual R&D, NTT serves more than 75% of Fortune Global 100 companies and millions of consumers across 190 countries.
Whether it’s drones flying beyond the visual line of sight, cameras detecting events in real-time without cloud dependency, or securing data flows with attribute-based encryption, NTT’s new chip sets the stage for the next frontier in AI at the edge—where intelligence meets immediacy.
#000#2025#4K#access control#ai#ai at the edge#AI chip#ai inference#AI performance#AI systems#AI video#Algorithms#amp#Analysis#applications#approach#Artificial Intelligence#autonomous#autonomous systems#battery#battery-powered#billion#Cameras#chip#cities#Cloud#cloud computing#communication#Companies#computing
1 note
·
View note