#Cyber Safety
Explore tagged Tumblr posts
Text
I don't know how accurate their information about Facebook messenger is, but Instagram (Facebook owned) had a college kid arrested for PRIVATE messages over a joke...
youtube
#Youtube#tiktok#facebook#meta#Instagram#invasion of privacy#facebook messenger#terms of service#cybersecurity#cyber security#cyber safety#tiktok ban
20 notes
·
View notes
Text
youtube
A 16-year-old boy from Pimpri-Chinchwad in Maharashtra died after jumping from the 14th floor of his building, according to the police. They suspect he was addicted to online games, which may have led him to take this tragic step. The boy left a note called "Log out note," along with a strategy map of a multiplayer combat game. The police found several sketches and maps in his notebook. However, they haven't been able to access his laptop because they don't know the password. The police plan to get help from cyber experts to find out which online game he was playing.
#general knowledge in tamil#gk on board#gkonboard#general knowledge#pothu arivu#kalanjiyam#behind earth#unsigned#tamil pokkisham#madan gowri#mr gk#online safety#mental health#digital addiction#parenting advice#cyber safety#teen behavior#online gaming impact#harmful websites#digital content control#family support#cyber investigation#parental monitoring#arya#online gaming addiction#pune#Pimpri-Chinchwad#Log out note#Youtube
5 notes
·
View notes
Text
A lot of paywalls don't work without Javascript, too! So if you ever come across one that doesn't work with this, try getting a plugin that can pause Javascript on sites.

Dropping this here for anyone who may not already know about it. paywallreader.com
65K notes
·
View notes
Text
Travel Safety Tips 2025: Navigate New Risks & Global Rules
Introduction: Why Travel Safety in 2025 Requires Extra Planning In 2025, global travel is rebounding strongly, but the landscape is far more complex. From new border regulations and digital surveillance to ongoing health threats and geopolitical tensions, understanding how to travel safely is essential. This guide covers the most important travel safety tips in 2025, equipping you to navigate…
#2025 travel regulations#border control updates#cyber safety#digital nomads#emergency travel kits#flight disruptions#health requirements travel#international travel alerts#political risk travel#smart travel tips#solo travel tips#travel insurance#travel safety
0 notes
Text
How to Develop a Personal Data Security Plan
In 2025, your data is more valuable than gold—and sadly, just as many people want to steal it. Whether you’re a freelancer, remote worker, business owner, or regular online user, having a personal data security plan is no longer optional—it’s essential. This guide will show you, step by step, how to take control of your digital privacy and protect yourself from identity theft, hacking, and online…
0 notes
Text
I was in the Tumblr activity page, and opened a mutual's comment to a yesterdays cat video reblog, and got a message from Avast, something like: the connection to a site yadayda was prevented, something something you are susceptible to fake sites and phishing. And I got it a second time after howering over that mutual. I only had tumblr and google tools open in the tabs.
When I checked the current safety status from Avast, there should be no harm done to my laptop, but still be alert yall.
1 note
·
View note
Text
As a person who's job title is Cyber Security Analyst, I'll tell you now, some of this stuff is actually normal for a lot of sites, some of this stuff is useless information which doesn't even make sense to need to collect...BUT a large chunk of this data is what I spend my time preventing cyber criminals from obtaining.
Not to mention ensuring organisations and subsidiaries don't store or store in a way that meets privacy and data security standards.
If a social media site is collecting a large portion of this I beg you do not download it. Especially don't download it onto work devices, you run a huge risk for data breaches, which yes we don't care about corporations but the people affected usually are not the corporations but normal people.
hey so maybe switching to threads, infamously managed by one of the worst data scraping companies of all time, isnt the play guys
heres just PART of what they're trying to track when you download the app:
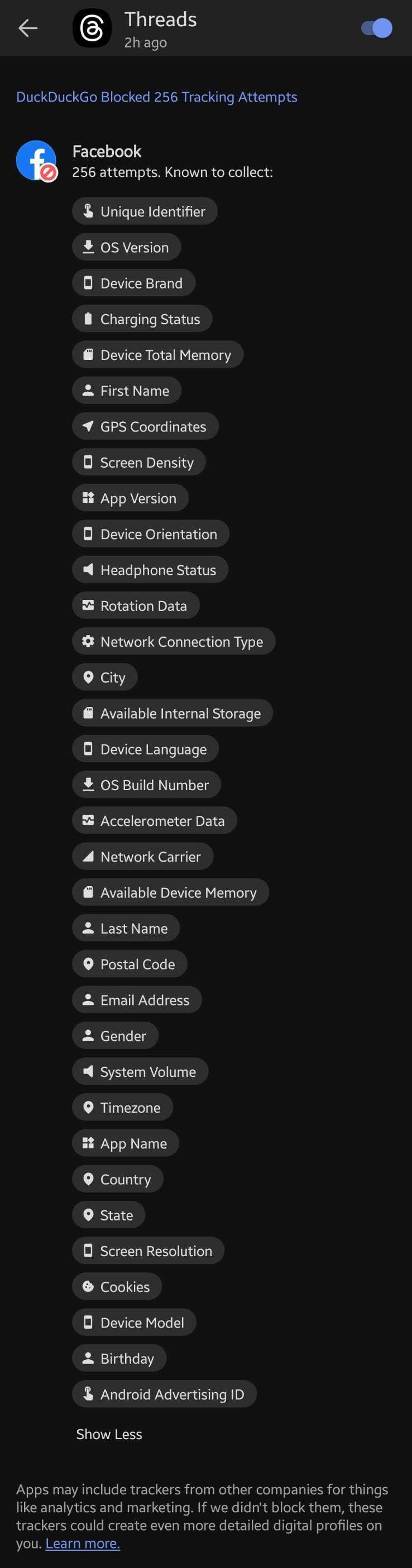
to list what they attempt to track:
unique identifier
os version
device brand
charging status
device total memory
first name
gps coordinates
screen density
app version
device orientation
headphone status
rotation data
network connection type
city
available internal storage
device language
os build number
accelerometer data
network carrier
available device memory
last name
postal code
email address
gender
system volume
timezone
app name
country
state
screen resolution
cookies
device model
birthday
android advertising id
please for the love of God, dont download threads.
47K notes
·
View notes
Text
Best Practices for Securing Your Collaborative Projects
As remote work and full-online business models become the norm, working with platforms like HackMD is becoming an increasingly popular way to carry out projects. However, with the power of digital collaboration comes the responsibility of security, and we must ensure that we protect data and project integrity when working online. Regardless of your work type, security should be a priority in the…
#collaboration safety#collaborative projects#cyber safety#Data Protection#digital security#online security#project management#project security#secure collaboration#secure sharing#team project protection#teamwork security
0 notes
Text
In today’s digital age, integrating cyber safety into early childhood education is essential for safeguarding our children. At UTCAO Child Care Center, we recognize the importance of fostering a secure environment for our young learners. Early childhood education in Vauxhall, New Jersey, not only focuses on nurturing academic and social growth but also on teaching children how to navigate the online world safely. By equipping them with the right knowledge and skills, we help protect their well-being as they grow and explore.
0 notes
Text
If Your PIN is on This List, Change It Immediately! - Tips how to Create a Strong PIN
Have you ever thought about how difficult it is for thieves to guess your card’s PIN? If you haven’t, recent research sheds light on the most common combinations that could make your PIN much easier to guess. Conducted by Nick Barry from Data Genetics, this study reveals that the most frequently used PIN in the world remains “1234.” However, there are other popular combinations that you might not…
#card&039;s pin#Change Your PIN#Crack The Code#Cyber Safety#Cyber security Awareness#Data Genetics#Data Protection#Digital Safety#Financial Security#Guess Again#Hack Proof Your Life#Hackers#Identity Theft#Password Panic#Password Safety#PINs Of Shame#PINSecurity#Protect Your Data#Protect Your Money#Safe Not Sorry#Secure Your Accounts#Secure Your Digits#Secure Your Wealth#Stay Safe Online
0 notes
Text
#parenting#internet safety#online safety#cyberbullying#child safety#digital parenting#online gaming#internet grooming#protecting children#family safety#child development#online security#digital literacy#cyber safety#parental controls#online behavior#internet education#digital citizenship#online privacy#parenting tips
1 note
·
View note
Text
Beyond Change Healthcare
The continued onslaught of cybersecurity attacks which if anything are only getting worse have impacted the healthcare system in dramatic fashion with the payment network brought down by the attack on Change Healthcare. Healthcare under Cyber Attack I keep hoping that we all get better at combatting these attempts to breach our data and that overall vigilance rises as we become more wary of…

View On WordPress
#cyber attacks#cyber awareness#cyber defense#cyber hygiene#cyber resilience#cyber safety#cyber threats#CyberCrime#Cybersecurity#cybersecurity awareness#cybersecurity best practices#cybersecurity challenges#cybersecurity culture#cybersecurity education#cybersecurity measures#cybersecurity news#cybersecurity protocols#cybersecurity resources#cybersecurity risks#cybersecurity solutions#cybersecurity strategy#cybersecurity tips#cybersecurity training#cybersecurity trends#data breach#data encryption#data protection#data security#Digital Health#Healthcare
0 notes
Text
A Parent's Guide to Navigating the Digital Landscape
On Shannon’s show, we have Clayton Cranford joining us. Clayton is a Sergeant in a Southern California law enforcement agency and the founder of Total Safety Solutions LLC. Renowned as one of the nation’s leading law enforcement educators, he specializes in social media awareness, child safety, and behavioral threat assessments. Clayton is also the acclaimed author of “Parenting in the…

View On WordPress
#Child Safety#Clayton Cranford#cyber safety#Holistic Internet#Law Enforcement#screen time#Shannon Zeeman#Social Media.
0 notes
Text
A Parent's Guide to Navigating the Digital Landscape
On Shannon’s show, we have Clayton Cranford joining us. Clayton is a Sergeant in a Southern California law enforcement agency and the founder of Total Safety Solutions LLC. Renowned as one of the nation’s leading law enforcement educators, he specializes in social media awareness, child safety, and behavioral threat assessments. Clayton is also the acclaimed author of “Parenting in the…

View On WordPress
#Child Safety#Clayton Cranford#cyber safety#Holistic Internet#Law Enforcement#screen time#Shannon Zeeman#Social Media.
0 notes
Text
on another note, this is horrifying. Did not realize this was a thing.
quote:
“Even if you don’t enroll in Face ID, the TrueDepth camera* intelligently activates to support Attention Aware features. With Attention Aware features, iPhone can check whether you’re paying attention to your device and automatically take action. For example,
When you’re looking at your device, your display will not dim until you stop looking at your device.
If you're looking at your device, it will lower the volume sound of your alerts.”
0 notes
Text
Revealed: Can You Really See Who Viewed Your WhatsApp Profile Photo?

Hey there, WhatsApp enthusiasts! 🌟 Have you ever found yourself wondering whether it's possible to track who's been sneaking a peek at your WhatsApp profile picture? 🤔 We're here to tackle this burning question and shed some light on the truth behind this popular WhatsApp myth.
First and foremost, let's address the elephant in the room: Can you really see who viewed your WhatsApp profile photo? It's time to uncover the reality and put an end to the speculation once and for all. While many third-party apps claim to offer this functionality, it's crucial to understand the risks associated with such services. Our comprehensive analysis will delve into the technicalities, highlighting the potential privacy implications and security concerns linked to these deceptive services.
We've meticulously tested various methods, including the notorious 'Who Viewed My WhatsApp Profile' apps, to provide you with an insightful overview of their functionality and potential hazards. Our findings emphasize the significance of safeguarding your privacy and data in today's digital landscape.
Join us on this illuminating journey as we decipher the truth behind the 'Who Viewed My WhatsApp Profile' phenomenon and provide you with practical tips on maintaining a secure and private WhatsApp experience. 💡
To learn more about the reality of this intriguing topic, head over to our comprehensive blog post here: Who Looked at My WhatsApp Profile Photo.
#WhatsApp#privacy#social media#messaging app#online security#digital privacy#data protection#WhatsApp privacy settings#online privacy#WhatsApp profile#privacy concerns#technology#internet privacy#personal data#social networking#data security#cyber safety
0 notes