#Difference between System Software and Application Software
Explore tagged Tumblr posts
Text
Embedded Systems Course For Beginners
Embedded systems have permeated nearly every aspect of modern technology. From the smartphones we use to the cars we drive, embedded systems are responsible for powering many of the devices we rely on daily. If you're looking to gain an understanding of embedded course in Bangalore and how to work with them, you might want to consider taking a beginner's course at the Indian Institute of Embedded Systems (IIES).

Introduction
Embedded systems are integrated computer systems designed to perform specific tasks without human intervention. They are widely used in industries such as automotive, healthcare, home automation, and more, and are becoming increasingly popular as the Internet of Things (IoT) continues to grow. A beginner's course at IIES is an excellent way to get started with embedded systems and learn about the fundamental concepts, tools, and techniques used in the industry.
Why Take a Beginner's Course on Embedded Systems?
Taking a beginner's course on embedded systems has several benefits, including:
Understanding the Fundamentals
A beginner's course at IIES can help you understand the foundational concepts of embedded systems, including hardware and software components, communication protocols, and programming languages commonly used in the industry.
Developing Practical Skills
The course is designed to provide a hands-on approach to learning, allowing you to work with real-world hardware and software platforms, including the Arduino and Raspberry Pi. This practical experience will give you the confidence and skills you need to build embedded systems on your own.
Career Opportunities
As the use of embedded systems continues to grow, so does the demand for professionals in the field. Completing a beginner's course at IIES can open the door to a wide range of career opportunities, including embedded system engineer, IoT developer, and more.
Course Curriculum
The beginner's course offered at IIES covers a comprehensive range of topics, including:
Introduction to Embedded Systems
This section provides a comprehensive overview of embedded systems. It covers the basics of hardware and software components, communication protocols, and programming languages.
Microcontrollers and Microprocessors
Learn about the various microcontrollers and microprocessors used in the industry, including AVR, ARM, and PIC microcontrollers.
Programming Languages
Gain an understanding of the programming languages used in embedded systems development, including C and Python in embedded system.
Real-time Operating Systems
This section covers the basics of real-time operating systems, including scheduling algorithms, task management, and inter-task communication.
Hardware Interfacing and Peripheral Control
Learn how to interface with various hardware components, such as sensors, motors, and displays, and control them using programming languages and microcontrollers.
Projects and Workshops
The course offers several practical workshops and projects that allow students to work with real-world projects and gain hands-on experience.
Indian Institute of Embedded Systems (IIES)
IIES is one of the most reputed institutes for embedded systems training in India. The institute offers a wide range of certificate and diploma programs in embedded systems, including the beginner's course mentioned above.
Expert Trainers
IIES has a team of experienced trainers who are experts in their field. They provide practical training sessions, enabling students to gain skills that are relevant to industry standards.
Industry Partnerships
Keeping up with the current industry trends is essential to gaining expertise in a field; IIES has partnered with various companies such as Altair, Tiempo Labs, and many more reputed firms. This collaboration helps to keep the students updated about industry trends and expectations.
Advanced Facilities
IIES has cutting-edge infrastructure and world-class facilities, providing students with access to the latest hardware and software technologies and practical hands-on learning experiences.
Course Duration and Cost
The beginner's course offered by IIES is of 3 months' duration and offers flexible batch timings. The fee structure is reasonable and affordable, making it accessible to anyone interested in learning about embedded systems.
Conclusion
A beginner's course on embedded systems offered by IIES can be an excellent way to learn about this fascinating field. The program provides a comprehensive overview of embedded system concepts, tools, and techniques while also offering practical hands-on learning experiences. Completing the course can be a great career opportunity in a field where the demand for professionals continues to grow. And with IIES's expert trainers and state-of-the-art facilities, you can be confident that you're learning from the best. So, enroll today and start your journey into the exciting world of embedded systems!
#embedded systems applications#embedded engineering#Embedded Engineers#embedded software engineer#difference between c and embedded c#embedded systems projects#Embedded Systems Jobs#Embedded Developer#Embedded System Developers#embedded systems internship#advantages of embedded system#robotics and embedded systems
0 notes
Text
The Science of Discovering the Past: Geophysical Archaeology

By Glab310 - Own work, CC BY 4.0, https://commons.wikimedia.org/w/index.php?curid=113524155
While much of archaeology involves unearthing artifacts, knowing where to find those sites requires research at the surface, as does mapping the site. Geophysical surveys help archaeologists know where to focus their efforts and help them avoid fruitless digs where no artifacts or remaining structures lie below the surface as well as avoiding the destruction of sites that are culturally sensitive, such as cemeteries.

By see above - http://www.archaeophysics.com/3030/index.htmlTransferred from en.wikipedia by SreeBot, Public Domain, https://commons.wikimedia.org/w/index.php?curid=17210746
There are many methods used to map below the surface, some of which can be done with little training while others meld multiple methods for a more complete map of what's under the surface. Those techniques that are more specialized were adapted from those used to explore for minerals. Mineral surveys seek to know what is deep beneath the surface and archaeological sites are relatively near the surface. These surveys also are focused on larger structures that would take a long time to unearth.

Source: https://sha.org/the-montpelier-minelab-experiment/2012/03/
Various methods of performing geophysical surveys and reveal different information. Metal detectors can be used to find caches of metal, but they don't give detailed information of what is below the surface. They can be used to discover new places to focus studies on. They work by inducing eddy currents, or a looping current between the detector and the metal in the ground, which causes a change in how the current flows in the machine, resulting in a signal being reported to the user, either through sound or visual output. Many locations have regulations or laws that dictate how metal detectors can be used and the ownership of those items found.

Public Domain, https://commons.wikimedia.org/w/index.php?curid=109641426
A more precise form of the this falls into two types: Electrical resistance meters and electromagnetic conductivity. Electrical resistance meters work by inserting probes into the soil through which electrical currents are passed and the resistance of the ground around them is detected, revealing the structures beneath as things like stone have different resistance than the soil around them. Electromagnetic conductivity is similar to metal detection in that a magnetic field is created by an electric field of a known frequency while detectors pick up the change. These detectors and currents are stronger than those of metal detectors with a related increase in size of the detector.

By Archaeo-Physics LLC - http://www.archaeophysics.com, Public Domain, https://commons.wikimedia.org/w/index.php?curid=36404337
Ground-penetrating radar uses electromagnetic pulses to detect what is under the surface in a way similar to how radar works in other applications. The pulses are reflected off items under the surface and recorded by the detector. It's possible to discover how things are layered beneath the surface because of the differences in reflections.

By Cargyrak - Own work, CC BY-SA 4.0, https://commons.wikimedia.org/w/index.php?curid=48685015
Lidar is an optical technique that uses light, usually lasers, to map the land. It has the ability to penetrate foliage, such as forest canopies, and allows features beneath the surface to be distinguished. This also allows features that are too large to be distinguished from the ground to be mapped. Lidar has the additional benefit of being easily integrated into Geographical Information Systems, integrated computer hardware and software systems that are used to analyze and visualize geographic data.
24 notes
·
View notes
Text
What is the kernel of an operating system ?
You can think of the kernel as the core component of an operating system, just like the CPU is the core component of a computer. The kernel of an operating system, such as the Linux kernel, is responsible for managing system resources ( such as the CPU, memory, and devices ) . The kernel of an operating system is not a physical entity that can be seen. It is a computer program that resides in memory.
Key points to understand the relationship between the kernel and the OS:
The kernel acts as the intermediary between the hardware and the software layers of the system. It provides a layer of abstraction that allows software applications to interact with the hardware without needing to understand the low-level details of the hardware
The kernel controls and manages system resources such as the CPU, memory, devices, and file systems. It ensures that these resources are allocated and utilized efficiently by different processes and applications running on the system.
The kernel handles tasks like process scheduling, memory management, device drivers, file system access, and handling interrupts from hardware devices.
The kernel can be extended through the use of loadable kernel modules (LKM). LKMs allow for the addition of new functionality or device drivers without modifying the kernel itself.
#linux#arch linux#ubuntu#debian#code#codeblr#css#html#javascript#java development company#python#studyblr#progblr#programming#comp sci#web design#web developers#web development#website design#webdev#website#tech#html css#learn to code#Youtube
225 notes
·
View notes
Text
On February 10, employees at the Department of Housing and Urban Development (HUD) received an email asking them to list every contract at the bureau and note whether or not it was “critical” to the agency, as well as whether it contained any DEI components. This email was signed by Scott Langmack, who identified himself as a senior adviser to the so-called Department of Government Efficiency (DOGE). Langmack, according to his LinkedIn, already has another job: He’s the chief operating officer of Kukun, a property technology company that is, according to its website, “on a long-term mission to aggregate the hardest to find data.”
As is the case with other DOGE operatives—Tom Krause, for example, is performing the duties of the fiscal assistant secretary at the Treasury while holding down a day job as a software CEO at a company with millions in contracts with the Treasury—this could potentially create a conflict of interest, especially given a specific aspect of his role: According to sources and government documents reviewed by WIRED, Langmack has application-level access to some of the most critical and sensitive systems inside HUD, one of which contains records mapping billions of dollars in expenditures.
Another DOGE operative WIRED has identified is Michael Mirski, who works for TCC Management, a Michigan-based company that owns and operates mobile home parks across the US, and graduated from the Wharton School in 2014. (In a story he wrote for the school’s website, he asserted that the most important thing he learned there was to “Develop the infrastructure to collect data.”) According to the documents, he has write privileges on—meaning he can input overall changes to—a system that controls who has access to HUD systems.
Between them, records reviewed by WIRED show, the DOGE operatives have access to five different HUD systems. According to a HUD source with direct knowledge, this gives the DOGE operatives access to vast troves of data. These range from the individual identities of every single federal public housing voucher holder in the US, along with their financial information, to information on the hospitals, nursing homes, multifamily housing, and senior living facilities that HUD helps finance, as well as data on everything from homelessness rates to environmental and health hazards to federally insured mortgages.
Put together, experts and HUD sources say, all of this could give someone with access unique insight into the US real estate market.
Kukun did not respond to requests for comment about whether Langmack is drawing a salary while working at HUD or how long he will be with the department. A woman who answered the phone at TCC Management headquarters in Michigan but did not identify herself said Mirksi was "on leave until July." In response to a request for comment about Langmack’s access to systems, HUD spokesperson Kasey Lovett said, “DOGE and HUD are working as a team; to insinuate anything else is false. To further illustrate this unified mission, the secretary established a HUD DOGE taskforce.” In response to specific questions about Mirski’s access to systems and background and qualifications, she said, “We have not—and will not—comment on individual personnel. We are focused on serving the American people and working as one team.”
The property technology, or proptech, market covers a wide range of companies offering products and services meant to, for example, automate tenant-landlord interactions, or expedite the home purchasing process. Kukun focuses on helping homeowners and real estate investors assess the return on investment they’d get from renovating their properties and on predictive analytics that model where property values will rise in the future.
Doing this kind of estimation requires the use of what’s called an automated valuation model (AVM), a machine-learning model that predicts the prices or rents of certain properties. In April 2024, Kukun was one of eight companies selected to receive support from REACH, an accelerator run by the venture capital arm of the National Association of Realtors (NAR). Last year NAR agreed to a settlement with Missouri homebuyers, who alleged that realtor fees and certain listing requirements were anticompetitive.
“If you can better predict than others how a certain neighborhood will develop, you can invest in that market,” says Fabian Braesemann, a researcher at the Oxford Internet Institute. Doing so requires data, access to which can make any machine-learning model more accurate and more monetizable. This is the crux of the potential conflict of interest: While it is unclear how Langmack and Mirski are using or interpreting it in their roles at HUD, what is clear is that they have access to a wide range of sensitive data.
According to employees at HUD who spoke to WIRED on the condition of anonymity, there is currently a six-person DOGE team operating within the department. Four members are HUD employees whose tenures predate the current administration and have been assigned to the group; the others are Mirski and Langmack. The records reviewed by WIRED show that Mirski has been given read and write access to three different HUD systems, as well as read-only access to two more, while Langmack has been given read and write access to two of HUD’s core systems.
A positive, from one source’s perspective, is the fact that the DOGE operatives have been given application-level access to the systems, rather than direct access to the databases themselves. In theory, this means that they can only interact with the data through user interfaces, rather than having direct access to the server, which could allow them to execute queries directly on the database or make unrestricted or irreparable changes. However, this source still sees dangers inherent in granting this level of access.
“There are probably a dozen-plus ways that [application-level] read/write access to WASS or LOCCS could be translated into the entire databases being exfiltrated,” they said. There is no specific reason to think that DOGE operatives have inappropriately moved data—but even the possibility cuts against standard security protocols that HUD sources say are typically in place.
LOCCS, or Line of Credit Control System, is the first system to which both DOGE operatives within HUD, according to the records reviewed by WIRED, have both read and write access. Essentially HUD’s banking system, LOCCS “handles disbursement and cash management for the majority of HUD grant programs,” according to a user guide. Billions of dollars flow through the system every year, funding everything from public housing to disaster relief—such as rebuilding from the recent LA wildfires—to food security programs and rent payments.
The current balance in the LOCCS system, according to a record reviewed by WIRED, is over $100 billion—money Congress has approved for HUD projects but which has yet to be drawn down. Much of this money has been earmarked to cover disaster assistance and community development work, a source at the agency says.
Normally, those who have access to LOCCS require additional processing and approvals to access the system, and most only have “read” access, department employees say.
“Read/write is used for executing contracts and grants on the LOCCS side,” says one person. “It normally has strict banking procedures around doing anything with funds. For instance, you usually need at least two people to approve any decisions—same as you would with bank tellers in a physical bank.”
The second system to which documents indicate both DOGE operatives at HUD have both read and write access is the HUD Central Accounting and Program System (HUDCAPS), an “integrated management system for Section 8 programs under the jurisdiction of the Office of Public and Indian Housing,” according to HUD. (Section 8 is a federal program administered through local housing agencies that provides rental assistance, in the form of vouchers, to millions of lower-income families.) This system was a precursor to LOCCS and is currently being phased out, but it is still being used to process the payment of housing vouchers and contains huge amounts of personal information.
There are currently 2.3 million families in receipt of housing vouchers in the US, according to HUD’s own data, but the HUDCAPS database contains information on significantly more individuals because historical data is retained, says a source familiar with the system. People applying for HUD programs like housing vouchers have to submit sensitive personal information, including medical records and personal narratives.
“People entrust these stories to HUD,” the source says. “It’s not data in these systems, it’s operational trust.”
WASS, or the Web Access Security Subsystem, is the third system to which DOGE has both read and write access, though only Mirski has access to this system according to documents reviewed by WIRED. It’s used to grant permissions to other HUD systems. “Most of the functionality in WASS consists of looking up information stored in various tables to tell the security subsystem who you are, where you can go, and what you can do when you get there,” a user manual says.
“WASS is an application for provisioning rights to most if not all other HUD systems,” says a HUD source familiar with the systems who is shocked by Mirski’s level of access, because normally HUD employees don’t have read access, let alone write access. “WASS is the system for setting permissions for all of the other systems.”
In addition to these three systems, documents show that Mirski has read-only access to two others. One, the Integrated Disbursement and Information System (IDIS), is a nationwide database that tracks all HUD programs underway across the country. (“IDIS has confidential data about hidden locations of domestic violence shelters,” a HUD source says, “so even read access in there is horrible.”) The other is the Financial Assessment of Public Housing (FASS-PH), a database designed to “measure the financial condition of public housing agencies and assess their ability to provide safe and decent housing,” according to HUD’s website.
All of this is significant because, in addition to the potential for privacy violations, knowing what is in the records, or even having access to them, presents a serious potential conflict of interest.
“There are often bids to contract any development projects,” says Erin McElroy, an assistant professor at the University of Washington. “I can imagine having insider information definitely benefiting the private market, or those who will move back into the private market,” she alleges.
HUD has an oversight role in the mobile home space, the area on which TCC Management, which appears to have recently wiped its website, focuses. "It’s been a growing area of HUD’s work and focus over the past few decades," says one source there; this includes setting building standards, inspecting factories, and taking in complaints. This presents another potential conflict of interest.
Braesemann says it’s not just the insider access to information and data that could be a potential problem, but that people coming from the private sector may not understand the point of HUD programs. Something like Section 8 housing, he notes, could be perceived as not working in alignment with market forces—“Because there might be higher real estate value, these people should be displaced and go somewhere else”—even though its purpose is specifically to buffer against the market.
Like other government agencies, HUD is facing mass purges of its workforce. NPR has reported that 84 percent of the staff of the Office of Community Planning and Development, which supports homeless people, faces termination, while the president of a union representing HUD workers has estimated that up to half the workforce could be cut The chapter on housing policy in Project 2025—the right-wing playbook to remake the federal government that the Trump administration appears to be following—outlines plans to massively scale back HUD programs like public housing, housing assistance vouchers, and first-time home buyer assistance.
16 notes
·
View notes
Text
Duplicate Frame Deletion: A Likely Unnecessary Tutorial
So… you updated to MacOS Sonoma, and–while it is amazing in many regards for photoshop things–it is a dang bummer and mood killer if you use MPV. However, after slamming my head into a wall trying to change the code on my own, I realized there is a much, much simpler solution to this.
In this tutorial, I will be showing you all how to delete duplicate frames from your gifs, with two options:
duplicate finder
within photoshop
Under the cut because pictures are a visual learner’s best friend!
A quick note:
MPV is odd with this. I’ve not had to do this on 4k capping, but have had to on anything under that. I don’t know the full reasoning, but it mostly looks to be something with the way it is reading frame rate. I know it’s in the code, but could not pinpoint it myself, and these were the only tricks that worked. If you find a better solution, please let me know! It has been rough, otherwise.
Step 1: Cap in MPV as normal
Now, this may be obvious, but make your caps in MPV. For a full tutorial on this, I highly recommend this one by kylos. The only difference between our software and their suggestion is going to be using the newest version of MPV (.0.36 at the time of this), and not the older. This is because there is an issue with MacOS Sonoma and older versions of MPV that prevent it from opening for… Some reason.
Step 2: Make sure you have your caps
I recommend moving your caps to whatever folder you like for your own ease of use. My biggest rec is to have it in its own folder, with no older folders within the folder. Not really a requirement, but in my mind, it makes the process faster (only true depending on number of files in other folders). You should have something like this (I am doing a scene from TWOT, as it’s one I’ve tested this method on a few times in several instances):
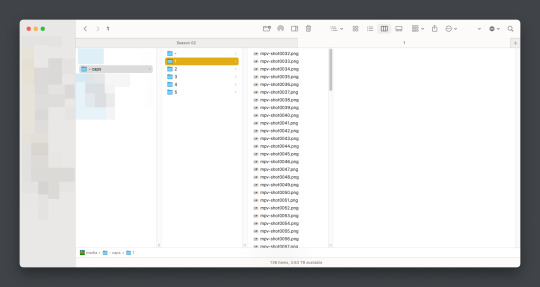
Once there, it’s time for the line split. I recommend option 1 the most (it’s faster, IMO), but again, this is a two option thing.
Option 1: Duplicate File Finder
So, duplicate finders are what they sound like. They are pieces of software that can be used to scan your device (or specific sections of said device), for duplicate files. It does not matter the title of the file, if the system reads it as a copy, it will find it.
There are a number of varieties for this, paid and free. I will not lie, the one I use is a paid version, because I had a huge issue with duplicate files taking up space when I moved to a new device. This also helps a lot with cloud file keeping, in my opinion. But that is beside the point.
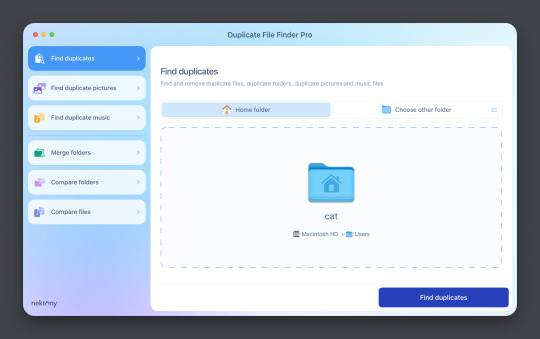
This is Duplicate File Finder Pro, which I got for other reasons, but has been very useful since this became an issue. The free version is sufficient for removing duplicate files found in folders, and that is why I still suggest it. You only need to get the pro if you have other intentions.
Now, onto the next step…
Step 3: Drag and drop the folder
With our folder full of caps, we simply drag and drop it into the application to begin.
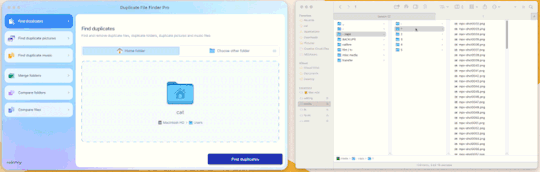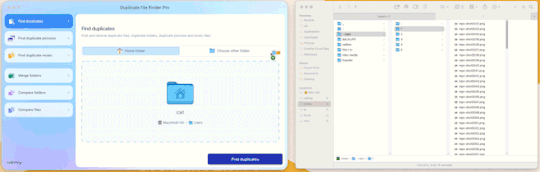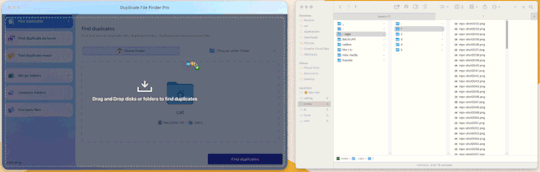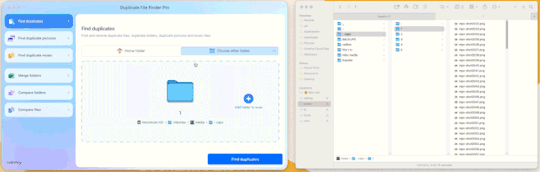
Step 4: Click “Find duplicates” and watch the pretty graph roll.
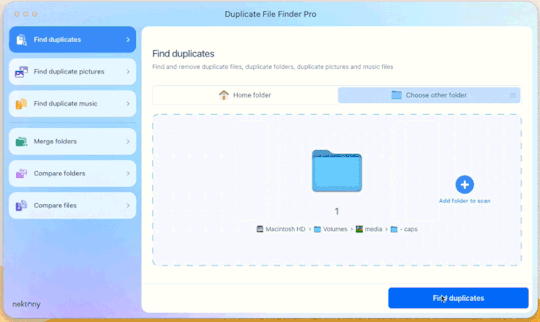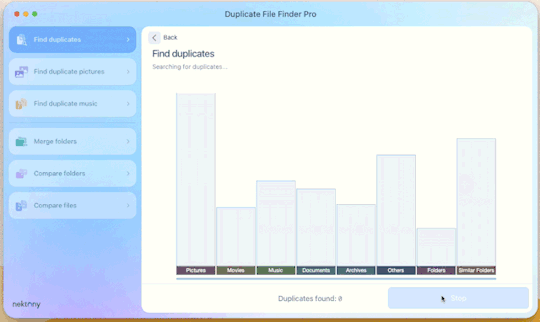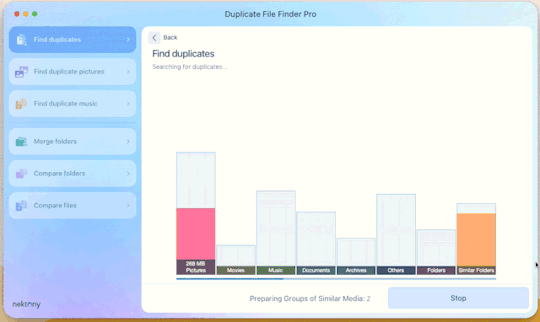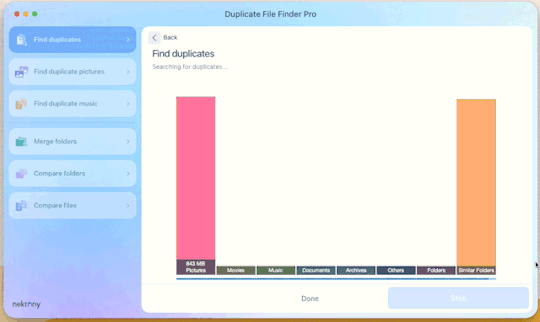
Step 5: Select the duplicate images
You can see here it found the duplicates.
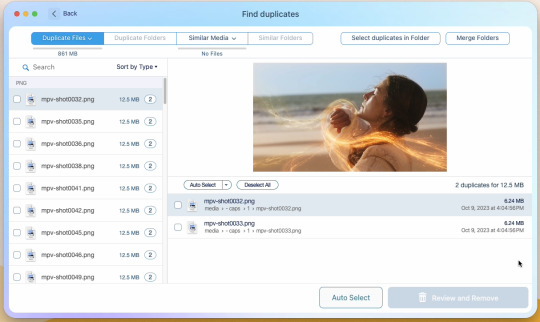
Now, I could go through by hand and click them, but… that’s a lot of time I don’t want to waste. I let it auto select them instead (you can tweak the settings for auto-select, but this is not that tutorial).
Step 6: Select review & remove, complete!
Wham bam! You’re completely set and good to go. Gif as normal~ (all final results at bottom)
Now, of course, maybe you don’t want a duplicate remover. Understandable, so what then? Well…
Option 2: Photoshop & the Changing Frame rate
So, this one is a little more technical. I suggest basic giffing and Photoshop knowledge before attempting.
Step 3: Import folder as you normally would
I believe this works as it would for import video, but I don’t want to say that and be wrong. But load your files in and you’ll be here:
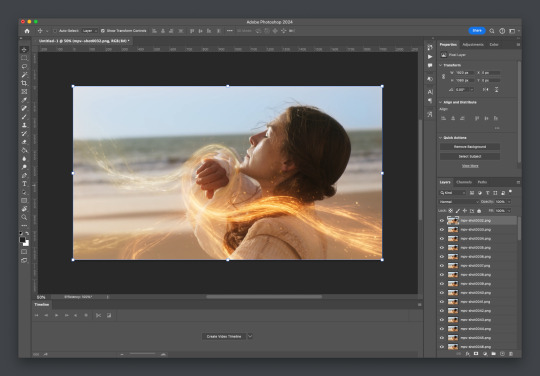
Now create video timeline, make frames from layers, yada yada (kylos’ guide is very good with this if you need help, it’s the same that was linked at the beginning of this). You’ll now be here:
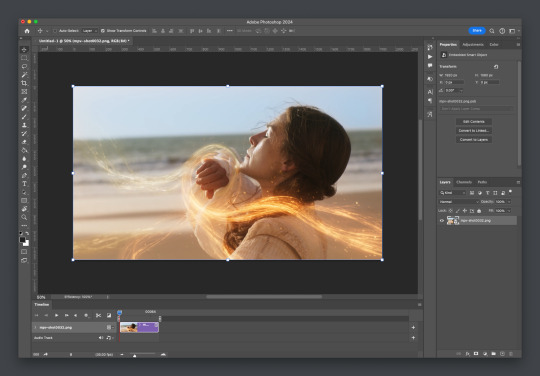
And the actual part of the tutorial you all came here for...
Step 4: Change the frame rate
So, in the bottom, next to the mountains for zooming in on the timeline, you’ll see it reads “30.00 fps.” We need to change this to 60. How? Easy! Click the three lines circled here:
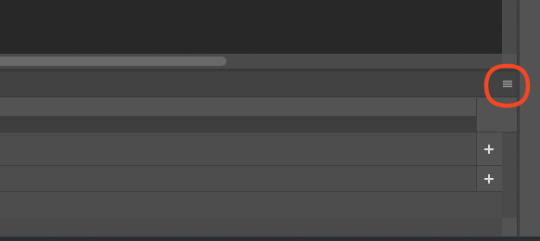
Then click “Set Timeline Frame Rate…”
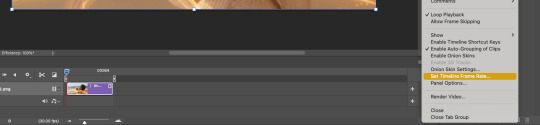
A little box will pop up, change the 30 to 15 (dropdown or typing, it works the same) and click “OK.”
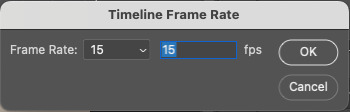
Your timeline will now be cut in half for length. That’s OKAY. DO NOT PANIC.
(Optional) Step 5: Double Checking
Click play on your gif, and you’ll notice it is no longer duplicate framed! To verify, let’s convert back to frames, just to see…
And it did, success! So make the rest of your gif as normal.
Your final results for the gif will be the following, with the gifs all labeled on what option was taken (or not). These were cropped for uploading and sharpened because of how I am. No coloring applied.
If anything was confusing, please don't hesitate to reach out! I'm happy to help in any way I can on this. My ask is always open. Happy Giffing!
#*tutorial#*ps#photoshop#resources#tutorial#alielook#singinprincess#sophiedevreaux#tuserabbie#tuserheidi#userace#userairi#useraish#userbarrow#userdorksinlove#userhella#userkayjay#userkraina#usermadita#usernik#userrobin#usershale#usersmia#usersray#usertj
175 notes
·
View notes
Note
Is there really a difference between software engineering, computer science and programming? i feel like calling myself a soon to be engineer is too extreme and not even correct
for someone who is only learning javascript off of YouTube after learning html and css. like idk computer science like that I actually find it hard
Hiya 💗
Yes there is a difference between each one, though they all fall under the same field of Computer Science.
💻 Software Engineer
Software engineering is building real-world software, like apps and websites.
It's about making sure the software is reliable and efficient.
Software engineers take ideas and turn them into working programs.
This is normally learnt through higher education like University.
💻 Computer Science
Computer science is about understanding the core ideas behind computers and algorithms.
It's like learning the rules of the game but not necessarily playing it.
Computer scientists solve complex problems using theory.
💻 Programming
Programming is writing instructions for a computer in a language it understands. I made a post about it here about the difference between programming and coding: LINK
It's literally how you create apps, games, and websites.
As a programmer, you make the computer do what you want it to do.
In summary, computer science is the theoretical foundation of computing, software engineering is the practical application of that knowledge to build software systems, and programming is the hands-on skill of writing code to create software!
Now you mentioned you only know JavaScript, HTML and CSS, it would make you just a programmer!
Hope this helps! 🤗💗

⤷ ○ ♡ my shop ○ my twt ○ my youtube ○ pinned post ○ blog's navigation ♡ ○
#my asks#resources#codeblr#coding#progblr#programming#studying#studyblr#learn to code#comp sci#tech#programmer
130 notes
·
View notes
Text
Weirdly Motivated to Write



Well, I did say that I have a new keyboard—to correct my posture and not look like a pretzel while I work remotely. Small victories, right?
Now, let’s talk about motivation. Because for some reason, I am absolutely buzzing with it today. Is it because of my keyboard? Most likely. Is that weird? Probably. But hey, I never claimed to be normal.
See, besides being a full-time student, I also have a job. And that job? Writing. Creating. Capturing life in words, pictures, and fleeting moments of inspiration. Filming, writing, photography—these are the things that make me absolutely happy. And honestly? Life is just too beautiful not to share.
There’s something about having the right tools that makes everything feel different. You could give me the exact same blank document yesterday, and I wouldn’t have been nearly as eager to write as I am today. But now? With my new keyboard? I feel like I could churn out a whole novel, rewrite history, or at the very least, write an unnecessarily long blog post about why I feel like writing.
Maybe it’s the clickity-clackity. (Yes, that’s a technical term.) There’s just something deeply satisfying about hearing each keystroke, like a tiny round of applause with every word I type. It’s hypnotizing. Encouraging. Addictive, even. Without it, I don’t think I’d be half as motivated to write.
And that brings me to a very important question:
Could this mean my iPad will replace my laptop?
Ha! Not a chance. Never. Not in a million years.
As much as I love this setup, there are things my iPad just cannot do. And honestly, those things make a huge difference in my daily workflow. Don’t get me wrong—iPads are fantastic. They’re lightweight, portable, and perfect for quick notes, reading, or sketching. But when it comes to serious work? My Windows laptop remains irreplaceable.



Why My Windows Laptop Wins Every Time
Multitasking Like a Pro iPads have some multitasking capabilities, but let's be real—nothing beats having multiple windows open, side by side, without limitations. On my laptop, I can have a research paper in one window, my notes in another, a video playing on the side, and Spotify running in the background. Try doing that on an iPad without constantly swiping between apps. It’s just not the same.
File Management That Actually Makes Sense The Windows file system is superior. Hands down. Drag-and-drop functionality, proper file explorer, external drive support—it’s just easier. iPads, on the other hand, have a clunky file system that often makes me want to scream into the void. Copying files? Moving them? Finding them again? It takes way longer than it should.
Software Compatibility & Heavy-Duty Programs This one’s a dealbreaker. There are so many professional-grade applications that just don’t run on iPads. Things like:
Adobe Premiere Pro for serious video editing (iPad versions are limited)
Photoshop & Illustrator (yes, they have mobile versions, but they’re nowhere near as powerful)
Microsoft Excel with Macros (because let's be honest, the iPad version is lacking)
Programming software & full IDEs (if I ever decide to code, my iPad will just sit there, useless)
Mouse & Keyboard Freedom Yes, iPads can connect to a mouse and keyboard, but do they truly function like a laptop? Nope. There are still weird limitations. Right-clicking? Custom shortcuts? The precision of a real trackpad or external mouse? Windows just does it better. Period.
Downloading Anything Without Jumping Through Hoops iPads don’t let you download everything you want, especially if it’s outside the App Store. Need a program that isn’t on Apple’s list of approved software? Too bad. Meanwhile, on Windows? I can download whatever I want, whenever I want, however I want. No restrictions.
Serious Writing & Formatting Writing on an iPad is fine for quick drafts, but when it comes to formatting long documents, citations, and exporting files in different formats? My laptop is my best friend. Whether it's proper PDF editing, running reference managers like Zotero, or managing multiple Word documents with complex layouts, iPads just don’t cut it.
Gaming & Emulation Okay, maybe not work-related, but still important! iPads have mobile games, sure. But do they run full-fledged PC games? Nope. Can I use them for game modding? Nope. Can I play older games with emulators? Again, nope. My Windows laptop, on the other hand? Unlimited possibilities.
The Verdict?
As much as I love the convenience of my iPad + keyboard combo, it will never replace my laptop. Ever. My laptop is where the real magic happens—the deep work, the serious projects, the things that actually require a proper computer.
But will I still use my iPad for writing on the go? Absolutely. Because nothing beats the clickity-clackity joy of my new keyboard. And if that keeps me weirdly motivated to write, then hey—I’ll take it.
So if you ever see me typing away somewhere, looking ridiculously focused, just know—it’s not me. It’s the keyboard.
#book#books#bookstore#new books#book review#booklr#books and reading#bookworm#book quotes#book blog#old books#bookblr#books & libraries#read#reading#reader#currently reading#long reads#library#literature#classic literature#english literature#book lover#english#classic#classics#bookshelf#bookshelves#productivity#ipad
10 notes
·
View notes
Text
'This city is like a parody of the sorts of novels I used to read when I was younger' - The Literalisation of Cyberpunk's Digital Unreality
youtube
i've been rewatching Psycho Pass with the gf recently and something really jumped out at me during Makishima and Choe's conversation in episode 15, just before they set out to Nona Tower. Makishima compares Psycho Pass' vision of Japan to the works of a few different 20th century SFF authors, Gibson, Orwell, and Dick, eventually concluding that it most closely resembles a Philip K. Dick novel. obviously part of this is just the show wearing its influences on its sleeve, but what fascinates me about this interaction is the specific wording of "this city is like a parody of the sorts of novels i used to read when i was younger". intentional or not, i think something about that line gets at a quiet, fundamental shift that's happened in cyberpunk media since its inception, as a direct result of the genre's impact on the world.
reading old cyberpunk fiction, one thing that becomes clear is that a world mediated through a layer of digital unreality was often used as a shorthand for the layer of psychic unreality imposed on society by capitalism. the classical example of this is of course The Matrix, but it's just as often employed less as total-immersion VR and more as just, a world where digital technology runs through every part of our lives. i think this is especially noticeable in Gibson's stuff, particularly The Winter Market (in which the protaganist's tentative connection with another sputters and dies as her personality gradually leaves the real world and is uploaded into cyberspace) and Dogfight (in which a man with nothing becomes so obsessed with the cheap high of digital success that he destroys everyone around him). so much early cyberpunk is about being blind to the people around you because you can't tell what's real and what's software anymore. the software follows laws and logic disconnected from reality, and yet you have to immerse yourself in it to survive, even if you know it's wrong. splitting your attention between the real world and the digital exerts a mental strain that often causes characters to snap.
silicone valley tech geniuses saw this devastatingly effective metaphor for the dehumanisation and alienation of capitalism (as evidenced by their constant, pathetic invoking of classic sci-fi and cyberpunk that they've read in their public personas) and instead of recognising it for what it was, rushed to make that metaphor literal because, read superficially, those stories present a digital world as the aesthetic of "the future". this is why tech bros are constantly creating the Torment Nexus from hit novel Don't Create The Torment Nexus. they can't understand that the Torment Nexus, or whatever other nightmarish hypothetical technology, could ever mean something beyond its literal application in-fiction, that it might have been saying something about its contemporary social context, and so don't realise that they're creating systems that, as a direct result of their inspiration, are doomed from first principles to reinforce the worst excesses of capitalism. i say this not to excuse these freaks, but merely to highlight the systemic incentives that lead them to do all the evil shit they do.
while the metaverse might seem the logical culmination of this mindset, i think ai art is the true final form of this kind of intellectual rot. the desire to unroot art from reality entirely, to drag it with them into the sea of software so that it's all just datapoints and averages, is something that i think a lot of people find so immediately and viscerally disgusting because on some level they recognise that this is an impulse founded entirely in the logic of the software, the ideology, not reality. the people dickriding this tech don't get that something can be within a piece of art beyond aesthetics, that a dystopian world fully mitigated by digital interactions can be anything other than a cool aesthetic for the future, that people love art because through it you feel some measure of the artist's touch and understand something about how they see the world.
and yet, for now, it seems that these people have won. they've mostly imposed a literal simulacrum of a metaphorical manifestation of psychic torment and misery on those of us living in the imperial core. the corporate internet is the unreal layer of digital reality made real, systems that mediate a staggering volume of communication between people within the core, even between people who know each other irl. and it extends beyond even this, to the computerised logic of late-stage capitalism, where untold suffering is inflicted on workers through layoffs and wage cuts to make lines go up, because a line going up is recognised as "good" within the system, and must be pursued at all costs. making the line go up is worth trashing the health of the economies and businesses which the line is nominally supposed to represent the health of. this logic is pervasive, and endemic to the chaotic decline we're currently living through.
this is where i circle back around to Psycho Pass. in 2013, at the time of the show's release, the internet was rapidly becoming an unavoidable part of daily life, a process which has only sped up since then. cyberpunk media has been caught in a grimly ironic position where its metaphorical concerns have been literalised; the world it commentates on has become, as Makishima put it, a parody, built off of wonky, incomplete misunderstandings of 20th century sci fi and cyberpunk in particular. Psycho Pass even responds to this idea in some ways, especially through its use of holograms; the very first scene in the show, that iconic flash-forward to episode 16, takes care to show the camera swooping through a building that is entirely holographic, while the show focuses on the dead, insubstantial aspects of the holo-interiors of buildings (shoutout to the gf for clocking that one). Makishima, who to be clear is a character whose flaws i could talk about for days, is nevertheless compelling when he talks about craving a book's "familiar smell of pulp and glue", the unique way in which a physical book "stimulates your senses", even if it technically has all the same words as an ebook. the fictional, digital representation of the psychic insubstantiality and contradiction of capitalist ideology has begun to seep out and infect the material world. this trend has even continued in the show's wake; for a show released a decade before LLMs were rebranded into "AI", the revelation of how the Sybil System actually works seems eerily prescient, right down to the deliberate obfuscation of the obviously biased human training data behind a rhetorical shield of passionless, objective artificial intelligence, something that at the time of release was almost certainly instead intended to be a commentary on the bogus claims of impartiality made by the criminal justice system.
there's something uniquely bleak about this process, especially as it intertwines with the unrelenting war that has been waged on academia and the humanities in particular over the past few decades. STEM is good and valuable, but the way it's rhetorically deployed by policymakers and elites as a bludgeon against the humanities is probably at least somewhat related to a generation of those elites' kids watching The Matrix and deciding that the biggest thematic takeaway is that they should become silicone valley investors and make that technology real.
with all of that being said, while it's often been observed that one of the greatest strengths of capitalism is its ability to hollow out and then incorporate criticisms that are levelled against it, in this case, i think there's a world where the results of that process end up being self-defeating. after all, part of the reason digital unreality was such a compelling concept thematically was that it laid bare the contradictions and tensions of capitalism in an extremely obvious and easy to understand way. making that into a real thing that millions and millions of people have to use every single day has, i think, already started to cause major problems, for example as politicians here in the UK slip completely into the digital layer of unreality, captured by a war over the ideological affections of a small minority of extremists on social media (TERFs, Nazis, pro-Israeli cheerleaders, 15 minute city conspiracy theorists, opinion columnists, etc), the disconnect from reality leaves an incredibly obvious vacuum that allows the increasingly poor, sick, and repressed general population to see exactly the ways that this system works against their interests. anecdotally, i do believe there is a palpable sense of exhaustion even from normies with the way that technology has been used to make everything shittier, and the strain that causes is becoming ever more visible to the naked eye.
12 notes
·
View notes
Text
What does Automation Testing software do?
Automation Testing Services

Automation Testing and its software is a tool and useful resource that helps to test applications automatically without any major considerations to look into while testing. Instead of having testers manually check every feature or function, automation tools run pre-written test scripts to check if the software works as expected. These tools can simulate user actions, test various inputs, and quickly and accurately check the software's behavior.
The main goal of automation test software is to save time, reduce human error, and increase testing coverage. It is beneficial when you must run the same tests many times, like regression testing or continuous integration setups.
Key Functions of Automation Testing Software -
Automation testing software performs several tasks that help ensure software quality. It checks if the application meets business requirements, validates data processing, tests user interfaces, and monitors performance under different conditions.
These tools can work across multiple browsers, devices, and operating systems. They help catch bugs early in the development process, reducing the cost and time needed to fix them later.
Many automation tools also integrate with other systems like CI/CD pipelines, test management platforms, and reporting dashboards—making the whole testing and development process smoother.
Benefits of Using Automation Testing Software -
Automation test software helps companies speed up testing, increase accuracy, and launch products faster. It reduces the need for repetitive manual testing, freeing testers to focus on more complex tasks.
The software runs tests 24/7 if needed, offers detailed test reports, and allows quick feedback to developers. It also supports better collaboration between QA and development teams, helping improve overall product quality.
While automation helps a lot, it doesn't fully replace manual testing. QA professionals still need to plan tests, review results, and test complex scenarios that automation can't handle, as they both are essential for the process. Automation Test is best for repetitive and everyday tasks like checking login pages, payment forms, or user dashboards and analytics. It's also helpful in regression testing — where old features must be retested after certain updates or common system upgrades.
Automation Testing software is a must-have tool and essential for modern software development operations as it gives completely transparent and reliable results if opting towards it as it saves time and the efforts of checking manually. It brings speed, reliability, and efficiency to the testing process. Trusted companies like Suma Soft, IBM, Cyntexa, and Cignex offer advanced automation testing solutions that support fast delivery, better performance, and improved software quality for businesses of all sizes.
3 notes
·
View notes
Text
Here’s some positivity for systems who don’t use Simply Plural and/or PluralKit!
PluralKit and Simply Plural are both excellent tools created by and for systems, with aims to help plurals manage and organize their system, and express themselves online. However, not every system wants or is able to use these tools. These systems are still important, and aren’t any less valued members of the plural community because of the tools they use or don’t use!
If you find PluralKit or Simply Plural confusing or too challenging to learn how to use - that’s okay! It can be incredibly difficult learning how to work with a new software or application. Both PluralKit and Simply Plural are complex with lots of different features and aspects that may take quite some time to figure out. It’s okay to not use these programs due to being unable to understand them, regardless of why you’re having trouble learning about them!
If you don’t have a device that is compatible with PluralKit or Simply Plural, don’t have an email address or Discord account, or otherwise don’t have access to the tools required to run these programs - there is absolutely nothing wrong with this! If you want to use these programs, we’re so sorry that you have been unable to access them. Remember that there are no requirements to use these programs in order to be plural or a system!
If you simply don’t like these programs, have no interest in using them, or feel like they won’t be beneficial for your system - we are proud of you for understanding your system and recognizing when something popular won’t be helpful for you! Not everyone has to use or benefit from PluralKit and Simply Plural. Your validity is not connected to the tools you use to manage your system! It is perfectly fine to not like either of these tools and to avoid using them for your own comfort!
If you are a median or midcontinuum system who can’t use PluralKit or Simply Plural due to having trouble distinguishing between headmates - that is totally valid! Not everyone is going to be able to use or benefit from these programs. It makes sense that systems who are closer to singlets, are often blurry, are made up of facets, or are less separated in general may have more difficulty benefitting from these tools. There is absolutely nothing wrong with this! Your system is not any less real and your plurality isn’t any less valid simply because you have trouble using these tools.
If you can’t or don’t use PluralKit or Simply Plural for ANY reason, please know that those who do use these programs are not any better than you for choosing to use them! Each system should feel welcome to use or reject whatever tools they wish for helping, organizing, and learning about their system. You and your system are just as important and valued members of the plural community just the way you are! You don’t have to change or attempt to navigate a new program just to fit in to this community - you already belong here with or without PluralKit and Simply Plural!
We hope you and your system can take care of each other and continue to learn more about each other and grow together. Rest assured you should feel no pressure to start using tools that you’re incapable of understanding or have no interest in! The plural community should never be gatekept, and this means not excluding those who are unable or choose not to use popular tools within the community!
Remember you are loved, you are worthy of kindness and respect, and your system will always belong here! Thanks for reading, and have a great day!
(Image ID:) A pale orange userbox with a cluster of multicolored flowers for the userbox image. The border and text are both dark orange, and the text reads “all plurals can interact with this post!” (End ID.)
#multiplicity#pluralgang#plurality#actuallyplural#system positivity#plural positivity#plural pride#system pride#pluralkit#simply plural
95 notes
·
View notes
Text
Cyberchase: How to Hack the Motherboard
So, when I was writing my episode discussion post on Cyberchase Season 1 Episode 1 "Lost My Marbles", I mentioned that I might make another post about the security breach that allowed The Hacker to infect Motherboard with the virus. What did The Hacker do to set this up? How did the kids accidentally open the breach? And other questions like that. I have a bit of background in software engineering. I will try to keep things as simple as possible.
Much of this is head-canon built on top of what we see in the episode. Of course, the show plays it fast and loose with computer terminology. Don't try to hack things in real life. You will go to prison.
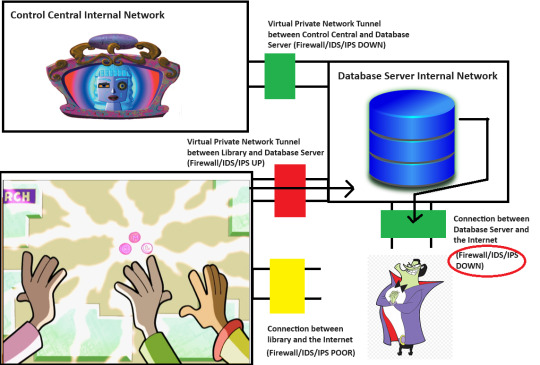
So, here's an MSPaint diagram of a tiny piece of Motherboard's setup. Keep in mind that she is the god of the Internet, and her Internet may even stretch beyond Earth into other galaxies.
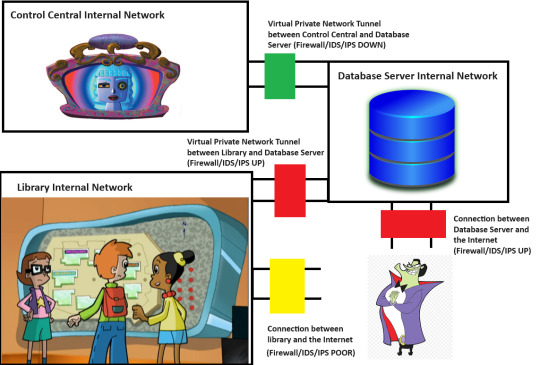
So, there are three separate network segments here. We have the library's internal network, which has the big board on it. We have Control Central's internal network, which has Motherboard on it. And then we have a Database Server internal network, which has a Database Server running on it.
The Database Server is something that I invented here. Remember that this whole diagram is head-canon. However, it's not too far-fetched to think that Motherboard must reach across Cyberspace to a separate Database Server, maybe at the Cybrary.
Now, we know that Motherboard is not directly reachable, even with her Firewall down. Otherwise, The Hacker wouldn't have needed a separate security breach to get to her. He would have just pushed the virus once she took down her firewall for maintenance.
However, Motherboard has a Virtual Private Network (VPN) tunnel to the Database Server. If The Hacker can compromise the Database Server and get his virus in there, it might be able to ride the tunnel into Control Central.
The purpose of any Firewall is to apply a set of rules to any network traffic going into or out of a network, device or application. A good Firewall configuration allows on the traffic that is needed and denies everything else. Motherboard's firewall between herself and the Database Server is currently down. The Database Server itself has connection points to the larger Internet without using a VPN tunnel. However, the Database Server's own Firewall for that access point is UP. If The Hacker tried to throw his virus at that access point, it wouldn't work.
However, there is another connection point into the Database Server. This is another VPN tunnel from the library network. Let's say that the board retrieves the data on the locations of different objects on the map and the icons for those objects by reading one of the Databases. Maybe the board also writes data to the Database to log what directions people requested.
The point here is that some traffic from the Board is authorized to pass through the Firewall on that VPN tunnel. Now, is there a way for The Hacker to get the Board to send authorized traffic over the VPN tunnel to tell the Database Server to open a breach in the Firewall for that public access point? Maybe. It is an Internet-of-Things (ioT) device. Alot of people get these devices, and then they either leave passwords set to their defaults or they forget to keep the sofware patches up to date.
There is a public access point to the Board with a poorly-configured firewall. Maybe there's a way for him to get inside. It may be possible for him to dump the virus code into the board, but there's no guarantee that it would be able to go any further, since the Firewall between the Board and the Database Server is working.
So, let's think about the Board as its own thing.

Suppose that we have two user accounts associated with the board. There is a Principle of Least Privilege that states that a given user account or system process should only be given the minimum amount of permissions required to perform its tasking. That way, if the user account or system process attempts to do something out of line with its permissions, it won't be allowed to perform the operation.
However, if you leave other unnecessary permissions open, and the user account or system process attempts to do something outside of its original intended operations, then the operation may succeed and have unintended consequences.
This also links up with the software development concept of the Minimum Viable Product. You build your software to perform only the exact tasking that it needs it perform. You don't put any additional, undocumented functions in there. Otherwise, those functions could activate and have unexpected consequences.
The board's purpose it to display the different locations. It allows for users to input two points, and it will draw a line between them to assist in navigation. We also established earlier that it reads its information from the Database and writes other information out to the Database.
However, suppose there was some undocumented functionality here. Suppose the developers had a special feature installed in the board that ran a cleanup command against the Database if you pressed three buttons in quick succession. Suppose that the cleanup command in question could be any arbitrary command. Therefore, the developers put the command into a configuration file to be read and executed by the software at runtime.
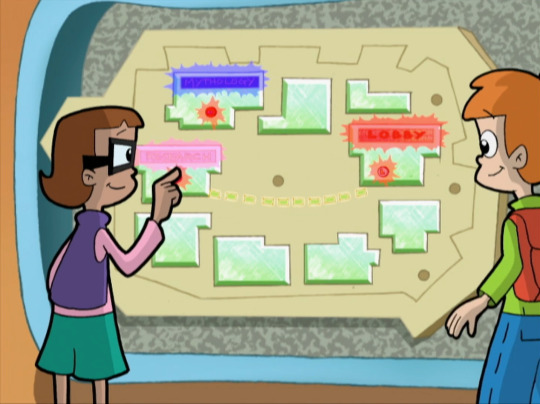
However, the developers knew that if some kids turned up and started poking the map, they could accidentally kick off the Database Cleanup command. They removed the Database Cleanup command from the configuration file. That way, if someone did poke three buttons in quick succession, the software would check the configuration file, see that there was no command defined, and then do nothing.
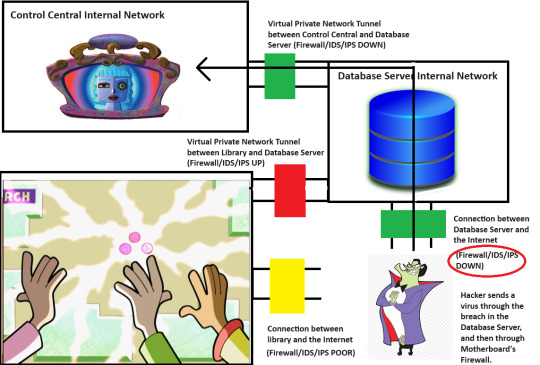
The trouble is that they left the part of the software that read the configuration file and ran the arbitrary command in place. So, if the command was somehow added back to that part of the configuration file, then there would be a command for the software to run. Then, if someone else pushed the three buttons, that command would be run. So, yeah, someone could put a command in there to write a bunch of junk into the Database until it filled up and crashed. Again, these are commands being sent to the Database from the Board. The Firewall would let them through just fine.
That's pretty bad, but that only lets them modify the Database, right? It's not like they can just tell the Database to open the Firewall on the server that it is sitting on, right?
Well, what if one of the things that the Database could do, upon request, was to open a command shell on the server and run a command. And what if, that command shell was able to run commands that impacted things on the server beyond the Database itself.
What if we called it "xp_cmdshell" and called the Database Server "Microsoft SQL Server 2000". Windows XP and Microsoft SQL Server 2000 would have been around at the time of "Lost My Marbles" after all. Those were also the key players in the real-world Heartland Payment Systems data breach of 2008, which inspired this post.
But hey, just because the Database could open a command shell on the Database Server doesn't mean that The Hacker could use it to bust the Database Server's external Firewall, right? He still needs a way to execute "xp_cmdshell". So, he needs an account with the correct permissions to tell the Database to execute "xp_cmdshell", and he needs the Database itself to have high-enough permissions to run a command via "xp_cmdshell" that can bust the Database Server's external firewall and open a path to Motherboard. Thankfully, the Database only run the "xp_cmdshell" for the top-level Database Administrator account.
This is where we get back to the Principle of Least Privilege. The Board should connect to the Database with a fairly low-power account. It only needs to read-from and write-to a few Database tables after all. Likewise, the Database itself should have been started on the Database Server by a fairly low-power account, as it only needs to handle reading and writing its own set of tables.
But then some moron decided to hook up the Board to the Database Server on the top-level Database Administrator Account. So, if the Board was configured to send an "xp_cmdshell" command, the Database would run it. Oh, and another moron decided to have the Database Server start the Database with the "root" account for that server. So, if the Board was configured to send in an "xp_cmdshell" command to nuke the external Firewall, then the Database would be able to nuke the external Firewall.

There is a principle called Defense-in-Depth, where you build multiple layers of defense around your critical item. That way, if a layer fails, you may be okay. We're running out of layers.
We only have one or two layers left. We know that the Board doesn't run "xp_cmdshell" for its regular operations today. Sure it has an undocumented debug mode that allows someone to execute any command in its configuration file (including "xp_cmdshell") against the Database. But someone would need to get to that file.
The board's main account doesn't give you a filesystem to play with, as they wouldn't want kids running up, poking things, and deleting the filesystem. No, you only get the interfaces that you get. You can pick two items and see a path between them. Or you can pick three items and see the undocumented debug mode run whatever command is in the configuration file.
But what if there was some sort of maintenance account accessible through the Internet that didn't enable someone to send commands to the Database, but would enable someone to get into the filesystem and mess around with it? And what if that maintenance account was still using a weak or default password because people just don't check that for IoT devices?

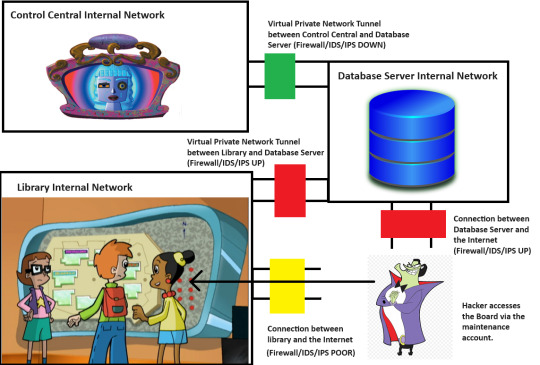
So, he's in the Board's filesystem now. That's concerning. And wouldn't you know it, yet another moron left that critical configuration file in a state where the maintenance account can make changes to it. So, of course, he found the empty configuration item for the cleanup command. Remember, this was setup to run any arbitrary command. Of course, he put in an "xp_cmdshell" command that tells the Database to nuke the external firewall on its own server.
While The Hacker was able to put the command in place, the maintenance account doesn't have the power to send commands to the Database on its own. That power is only enabled for the system account tied to the Board's user interface. So, he still has to rely on someone in the real world to push three buttons in quick succession.


Well...shit.
That's not good.

That's not good at all.


Seriously though, don't try this at home.
I suppose we can speculate on the nature of the virus. We know from Season 1 Episode 14 "Cool It" that Motherboard goes through more cryoxide than normal due to the virus. There are actual computer viruses out there that were designed to turn off heat safety warnings on CPUs and then cause them to run hotter. Some CPUs would eventually melt and ruin the computer.
The original infection destroyed the Encryptor Chip, and it is stated that only a replacement Encryptor Chip could cure the virus. The name suggests that it deals with data encryption, but perhaps it is also a virus cleanup tool. Perhaps it worked to weaken the existing virus until it was eventually overwhelmed and destroyed. Perhaps the virus exhausted most of its strength destroying the Encryptor Chip first.
In any case, curing the virus permanently would end the show.
#cyberchase#2000s#cartoon#nostalgia#pbs kids#2000s childhood#not for use in real life#you'll get busted
12 notes
·
View notes
Text
Building Your Own Operating System: A Beginner’s Guide
An operating system (OS) is an essential component of computer systems, serving as an interface between hardware and software. It manages system resources, provides services to users and applications, and ensures efficient execution of processes. Without an OS, users would have to manually manage hardware resources, making computing impractical for everyday use.

Lightweight operating system for old laptops
Functions of an Operating System
Operating systems perform several crucial functions to maintain system stability and usability. These functions include:
1. Process Management
The OS allocates resources to processes and ensures fair execution while preventing conflicts. It employs algorithms like First-Come-First-Serve (FCFS), Round Robin, and Shortest Job Next (SJN) to optimize CPU utilization and maintain system responsiveness.
2. Memory Management
The OS tracks memory usage and prevents memory leaks by implementing techniques such as paging, segmentation, and virtual memory. These mechanisms enable multitasking and improve overall system performance.
3. File System Management
It provides mechanisms for reading, writing, and deleting files while maintaining security through permissions and access control. File systems such as NTFS, FAT32, and ext4 are widely used across different operating systems.
4. Device Management
The OS provides device drivers to facilitate interaction with hardware components like printers, keyboards, and network adapters. It ensures smooth data exchange and resource allocation for input/output (I/O) operations.
5. Security and Access Control
It enforces authentication, authorization, and encryption mechanisms to protect user data and system integrity. Modern OSs incorporate features like firewalls, anti-malware tools, and secure boot processes to prevent unauthorized access and cyber threats.
6. User Interface
CLI-based systems, such as Linux terminals, provide direct access to system commands, while GUI-based systems, such as Windows and macOS, offer intuitive navigation through icons and menus.
Types of Operating Systems
Operating systems come in various forms, each designed to cater to specific computing needs. Some common types include:
1. Batch Operating System
These systems were widely used in early computing environments for tasks like payroll processing and scientific computations.
2. Multi-User Operating System
It ensures fair resource allocation and prevents conflicts between users. Examples include UNIX and Windows Server.
3. Real-Time Operating System (RTOS)
RTOS is designed for time-sensitive applications, where processing must occur within strict deadlines. It is used in embedded systems, medical devices, and industrial automation. Examples include VxWorks and FreeRTOS.
4 Mobile Operating System
Mobile OSs are tailored for smartphones and tablets, offering touchscreen interfaces and app ecosystems.
5 Distributed Operating System
Distributed OS manages multiple computers as a single system, enabling resource sharing and parallel processing. It is used in cloud computing and supercomputing environments. Examples include Google’s Fuchsia and Amoeba.
Popular Operating Systems
Several operating systems dominate the computing landscape, each catering to specific user needs and hardware platforms.
1. Microsoft Windows
It is popular among home users, businesses, and gamers. Windows 10 and 11 are the latest versions, offering improved performance, security, and compatibility.
2. macOS
macOS is Apple’s proprietary OS designed for Mac computers. It provides a seamless experience with Apple hardware and software, featuring robust security and high-end multimedia capabilities.
3. Linux
Linux is an open-source OS favored by developers, system administrators, and security professionals. It offers various distributions, including Ubuntu, Fedora, and Debian, each catering to different user preferences.
4. Android
It is based on the Linux kernel and supports a vast ecosystem of applications.
5. iOS
iOS is Apple’s mobile OS, known for its smooth performance, security, and exclusive app ecosystem. It powers iPhones and iPads, offering seamless integration with other Apple devices.
Future of Operating Systems
The future of operating systems is shaped by emerging technologies such as artificial intelligence (AI), cloud computing, and edge computing. Some key trends include:
1. AI-Driven OS Enhancements
AI-powered features, such as voice assistants and predictive automation, are becoming integral to modern OSs. AI helps optimize performance, enhance security, and personalize user experiences.
2. Cloud-Based Operating Systems
Cloud OSs enable users to access applications and data remotely. Chrome OS is an example of a cloud-centric OS that relies on internet connectivity for most functions.
3. Edge Computing Integration
With the rise of IoT devices, edge computing is gaining importance. Future OSs will focus on decentralized computing, reducing latency and improving real-time processing.
4. Increased Focus on Security
Cyber threats continue to evolve, prompting OS developers to implement advanced security measures such as zero-trust architectures, multi-factor authentication, and blockchain-based security.
3 notes
·
View notes
Text
Top B.Tech Courses in Maharashtra – CSE, AI, IT, and ECE Compared
B.Tech courses continue to attract students across India, and Maharashtra remains one of the most preferred states for higher technical education. From metro cities to emerging academic hubs like Solapur, students get access to diverse courses and skilled faculty. Among all available options, four major branches stand out: Computer Science and Engineering (CSE), Artificial Intelligence (AI), Information Technology (IT), and Electronics and Communication Engineering (ECE).
Each of these streams offers a different learning path. B.Tech in Computer Science and Engineering focuses on coding, algorithms, and system design. Students learn Python, Java, data structures, software engineering, and database systems. These skills are relevant for software companies, startups, and IT consulting.
B.Tech in Artificial Intelligence covers deep learning, neural networks, data processing, and computer vision. Students work on real-world problems using AI models. They also learn about ethical AI practices and automation systems. Companies hiring AI talent are in healthcare, retail, fintech, and manufacturing.
B.Tech in IT trains students in systems administration, networking, cloud computing, and application services. Graduates often work in system support, IT infrastructure, and data management. IT blends technical and management skills for enterprise use.
B.Tech ECE is for students who enjoy working with circuits, embedded systems, mobile communication, robotics, and signal processing. This stream is useful for telecom companies, consumer electronics, and control systems in industries.
Key Differences Between These B.Tech Programs:
CSE is programming-intensive. IT includes applications and system-level operations.
AI goes deeper into data modeling and pattern recognition.
ECE focuses more on hardware, communication, and embedded tech.
AI and CSE overlap, but AI involves more research-based learning.
How to Choose the Right B.Tech Specialization:
Ask yourself what excites you: coding, logic, data, devices, or systems.
Look for colleges with labs, project-based learning, and internship support.
Talk to seniors or alumni to understand real-life learning and placements.
Explore industry demand and long-term growth in each field.
MIT Vishwaprayag University, Solapur, offers all four B.Tech programs with updated syllabi, modern infrastructure, and practical training. Students work on live projects, participate in competitions, and build career skills through soft skills training. The university also encourages innovation and startup thinking.
Choosing the right course depends on interest and learning style. CSE and AI suit tech lovers who like coding and research. ECE is great for those who enjoy building real-world devices. IT fits students who want to blend business with technology.
Take time to explore the subjects and talk to faculty before selecting a stream. Your B.Tech journey shapes your future, so make an informed choice.
#B.Tech in Computer Science and Engineering#B.Tech in Artificial Intelligence#B.Tech in IT#B.Tech ECE#B.Tech Specialization
2 notes
·
View notes
Text
Microservices vs Monolith: Choosing the Right Architecture

Content: When developing software systems, architecture is one of the first and most impactful decisions. Two primary models dominate: monolithic applications and microservices architectures.
Monoliths consolidate all functions into a single unit, making them easier to build initially. However, they often become cumbersome as the codebase grows, making deployments riskier and updates slower.
Microservices, on the other hand, break applications into independent services that communicate over APIs. Each service is loosely coupled, allowing teams to work independently, use different tech stacks, and scale specific components without overhauling the entire system.
However, microservices come with their own challenges: higher complexity, the need for service orchestration, and potential for network latency.
Choosing between monolith and microservices depends largely on your team's size, project complexity, and long-term goals. Companies uses tools like Software Development assist in evaluating your needs to design the most appropriate architecture, balancing scalability with simplicity.
Ultimately, it’s not about trends—it’s about choosing what fits your project’s current and future states.
Before jumping into microservices, ensure your team masters clean modular design within a monolith first—it’ll make the transition smoother if/when you need it.
3 notes
·
View notes
Text
Infrastructure for Teamwork, a.k.a. Version Control
Working together on a game is quite difficult. How do you make sure everyone is on the same page?
You could send zips with assets and code between people, but that is slow, cumbersome, and very error-prone.
This is why Source Control software was invented. With Source Control, you can store the project files on a server, and everyone who wants to work on the project files, can download the project from the server. Once they're done with their changes, they send them back to the server. Then the other people can get those changes from the server again.
There are many different Source Control softwares. Probably the best-known one is git. (Source Control, Version Control, Revision Control all mean essentially the same thing.) Git is very good for working on projects that are all just plain-text code. However, it kind of falls flat when it needs to deal with binary assets, like textures, models, and sounds. Unreal Engine Scenes and Blueprints are also binary files. So if you don't use C++, but only Blueprints, basically your entire project is binary files.
This is why I went looking for a different Version Control Software that can handle this better. At my internship, I used Subversion, which is said to work better with binary assets, but in my experience then, it still wasn't exactly great. Though that might also have been due to the fact that they barely used any of its fancier features there.
Unreal Engine itself recommends using Perforce Helix Core. (Perforce is the company, Helix Core is the VCS, but the term "Perforce" is usually used to refer to the VCS itself, due to historical reasons. Source) So I looked into it, and indeed, it seemed very suitable!
So we requested a computer from the XR Lab to use as server for this project, and I installed the Helix Core Server on it.


It was surprisingly easy to install!
I then downloaded the Helix Core Client application on my laptop, and connected to the server. The setup there took a while, because there was a lot to learn. But in the end, I did it!
Sadly, Perforce is not free, so we are forced to use the free version, which is limited to a maximum of five users. We are with ten people, so we had to choose a few "representatives" who would actually put the things everyone made into the project. We requested an educational licence from Saxion, but got told to wait. Now that the project is over, we still don't have it. We also requested an educational licence from Perforce itself, directly, but we have still not got a response. But we made do with the limitations we got.
I wrote a guide for my teammates on how to set up a workspace for the project with Perforce, and improved it multiple times based on user testing and feedback. (I sat next to my teammates while they were following the guide and tried my best to now say anything; to let the guide speak for itself. I would then take note of what went wrong and improved that section of the guide for the next user test.)
Over the months of this project, we all used P4V and Perforce to work together on the project. Due to Perforce's locking system, we never had any merge conflicts! Most of the team actually really enjoyed working with Perforce. Personally, I do miss git, but I acknowledge that for an Unreal Engine project, Perforce is a lot better. And I also found it pretty nice to work with. The documentation was pretty good, and they have a lot of tutorials, guide, and demonstration videos, which have been very helpful during the setup. It's very useful to be able to follow along every single click.
3 notes
·
View notes
Text
Weirdly Motivated to Write



Well, I did say that I have a new keyboard—to correct my posture and not look like a pretzel while I work remotely. Small victories, right?
Now, let’s talk about motivation. Because for some reason, I am absolutely buzzing with it today. Is it because of my keyboard? Most likely. Is that weird? Probably. But hey, I never claimed to be normal.
See, besides being a full-time student, I also have a job. And that job? Writing. Creating. Capturing life in words, pictures, and fleeting moments of inspiration. Filming, writing, photography—these are the things that make me absolutely happy. And honestly? Life is just too beautiful not to share.
There’s something about having the right tools that makes everything feel different. You could give me the exact same blank document yesterday, and I wouldn’t have been nearly as eager to write as I am today. But now? With my new keyboard? I feel like I could churn out a whole novel, rewrite history, or at the very least, write an unnecessarily long blog post about why I feel like writing.
Maybe it’s the clickity-clackity. (Yes, that’s a technical term.) There’s just something deeply satisfying about hearing each keystroke, like a tiny round of applause with every word I type. It’s hypnotizing. Encouraging. Addictive, even. Without it, I don’t think I’d be half as motivated to write.
And that brings me to a very important question:
Could this mean my iPad will replace my laptop?
Ha! Not a chance. Never. Not in a million years.
As much as I love this setup, there are things my iPad just cannot do. And honestly, those things make a huge difference in my daily workflow. Don’t get me wrong—iPads are fantastic. They’re lightweight, portable, and perfect for quick notes, reading, or sketching. But when it comes to serious work? My Windows laptop remains irreplaceable.



Why My Windows Laptop Wins Every Time
Multitasking Like a Pro iPads have some multitasking capabilities, but let's be real—nothing beats having multiple windows open, side by side, without limitations. On my laptop, I can have a research paper in one window, my notes in another, a video playing on the side, and Spotify running in the background. Try doing that on an iPad without constantly swiping between apps. It’s just not the same.
File Management That Actually Makes Sense The Windows file system is superior. Hands down. Drag-and-drop functionality, proper file explorer, external drive support—it’s just easier. iPads, on the other hand, have a clunky file system that often makes me want to scream into the void. Copying files? Moving them? Finding them again? It takes way longer than it should.
Software Compatibility & Heavy-Duty Programs This one’s a dealbreaker. There are so many professional-grade applications that just don’t run on iPads. Things like:
Adobe Premiere Pro for serious video editing (iPad versions are limited)
Photoshop & Illustrator (yes, they have mobile versions, but they’re nowhere near as powerful)
Microsoft Excel with Macros (because let's be honest, the iPad version is lacking)
Programming software & full IDEs (if I ever decide to code, my iPad will just sit there, useless)
Mouse & Keyboard Freedom Yes, iPads can connect to a mouse and keyboard, but do they truly function like a laptop? Nope. There are still weird limitations. Right-clicking? Custom shortcuts? The precision of a real trackpad or external mouse? Windows just does it better. Period.
Downloading Anything Without Jumping Through Hoops iPads don’t let you download everything you want, especially if it’s outside the App Store. Need a program that isn’t on Apple’s list of approved software? Too bad. Meanwhile, on Windows? I can download whatever I want, whenever I want, however I want. No restrictions.
Serious Writing & Formatting Writing on an iPad is fine for quick drafts, but when it comes to formatting long documents, citations, and exporting files in different formats? My laptop is my best friend. Whether it's proper PDF editing, running reference managers like Zotero, or managing multiple Word documents with complex layouts, iPads just don’t cut it.
Gaming & Emulation Okay, maybe not work-related, but still important! iPads have mobile games, sure. But do they run full-fledged PC games? Nope. Can I use them for game modding? Nope. Can I play older games with emulators? Again, nope. My Windows laptop, on the other hand? Unlimited possibilities.
The Verdict?
As much as I love the convenience of my iPad + keyboard combo, it will never replace my laptop. Ever. My laptop is where the real magic happens—the deep work, the serious projects, the things that actually require a proper computer.
But will I still use my iPad for writing on the go? Absolutely. Because nothing beats the clickity-clackity joy of my new keyboard. And if that keeps me weirdly motivated to write, then hey—I’ll take it.
So if you ever see me typing away somewhere, looking ridiculously focused, just know—it’s not me. It’s the keyboard.
#book#books#bookstore#new books#book review#booklr#books and reading#bookworm#book quotes#book blog#old books#bookblr#books & libraries#read#reading#reader#currently reading#long reads#library#literature#classic literature#english literature#book lover#english#classic#classics#bookshelf#bookshelves#productivity#ipad
3 notes
·
View notes