#Ethical-Hacking
Text
As a fire spirit, Mairon can probably forge completely naked if he wants to and now I'm thinking this might be how he baited both Melkor into becoming his sugar daddy and Celebrimbor into joining his little ring forging hobby project
#angbang#silvergifting#mairon#sauron#melkor#morgoth#celebrimbor#tyelpe#crack#silm crack#shitpost#silmarillion#mairon's fun and ethical life hacks
342 notes
·
View notes
Text

1K notes
·
View notes
Text
The Hacker's Guidebook:
Aspiring hackers! I’ve created a guide covering core cybersecurity concepts new hackers should master before tools. I break down networking, OS internals, & hacking tactics. Recognize hacking as lifelong journey—arm yourself with the basics!
Core Concepts for Budding Cybersecurity Enthusiasts
The Building Blocks of Ethical Hacking
So you want to become an ethical hacker and enter the exciting world of cybersecurity. That’s awesome! However, before you dive headfirst into firing up Kali Linux and hacking everything in sight, it’s vital to build up your foundational knowledge across several InfoSec domains. Mastering the fundamentals…

View On WordPress
#attacking tools#basics of hacking#cross site scripting#Cyber Threat Defense#cybersec#cybersecurity learning#cybersecurity professional#Ethical Hacking#fundamentals#hacking basics#hacking for beginners#hacking guide#hacking networks#hacking web#how to hack#infosec#learn hacking#learn to hack#linux#malware basics#malware for hacking#metasploit#netsec#network hacking#nmap#operating systems#Pentesting#phishing#phishing attacks#Red Team
22 notes
·
View notes
Text

THE CYBERCLOPAEDIA
This is an aspiring project aimed at accumulating knowledge from the world of cybersecurity and presenting it in a cogent way, so it is accessible to as large an audience as possible and so that everyone has a good resource to learn hacking from.
13 notes
·
View notes
Text
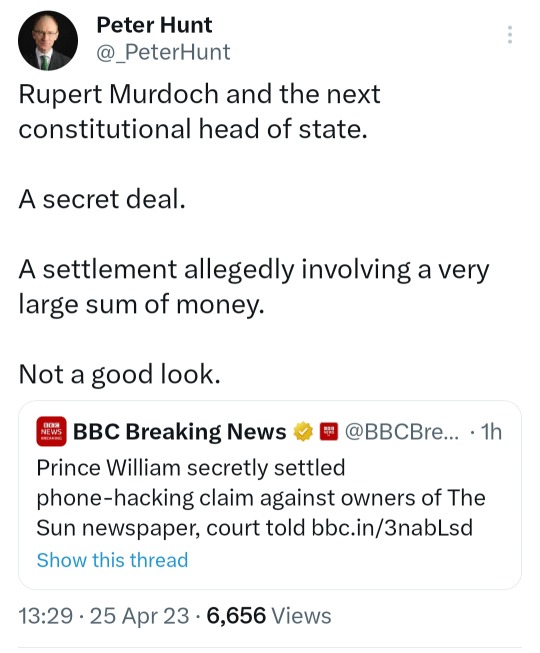

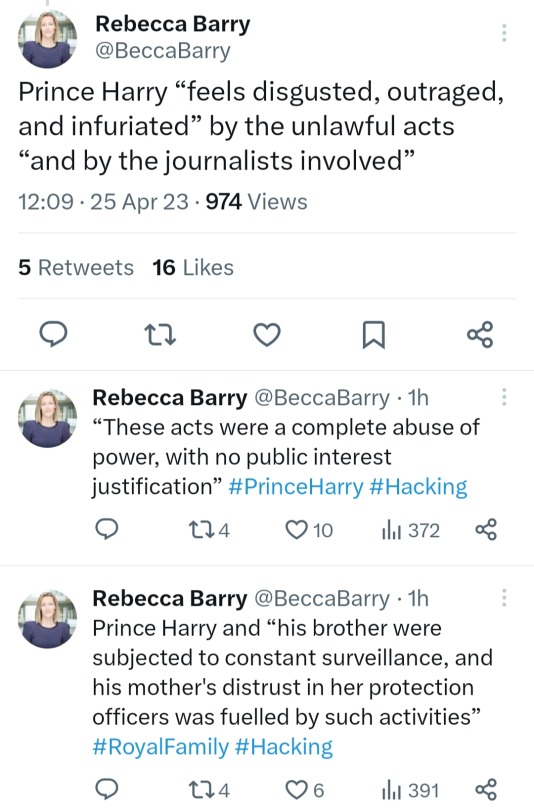
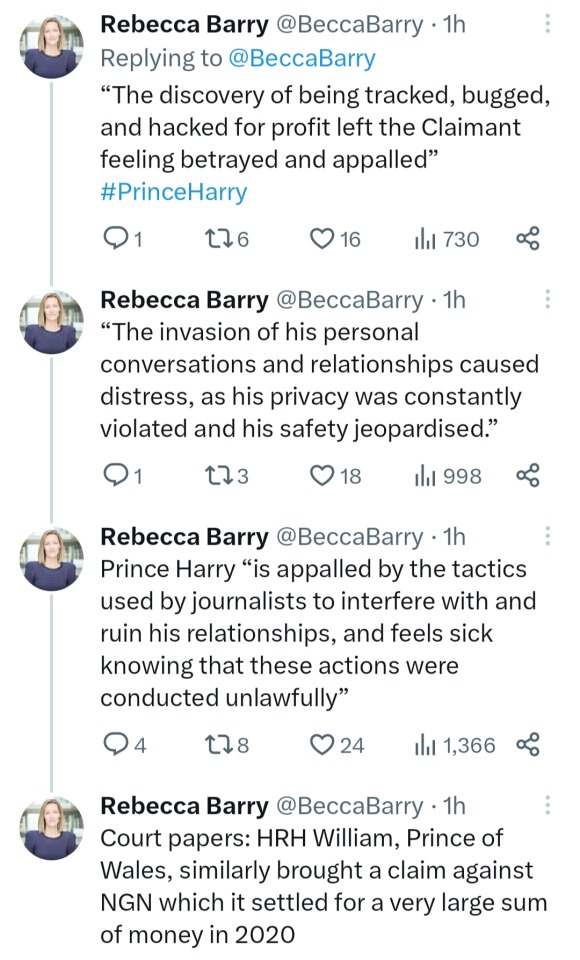
Just going to leave this here...
#nothing to add#these say it all#and ffs will people stop saying he's suing for privacy? he's suing because the law has been broken repeatedly#morally ethically legally the papers are in the wrong here#take your harry hater bias elsewhere and fuck off with your bullshit#he is in the right#prince harry#duke of sussex#prince william#phone hacking#h v the media
48 notes
·
View notes
Text
happy birthday to the good fellas at vx-underground!!
all my homies love vx-underground!

#:3#196#egg irl#traaa#rule#ruleposting#:3 hehe#r/196#vx-underground#vx underground#vxug#hacking#ethical hacking#malware#hacker#linuxposting
3 notes
·
View notes
Text
the taste of metal
still on my lips
like traces of your forbidden smile
if none of this was real
i impose upon you
tell me, darling
would you destroy everything,
everything in the world
for me?
for i destroyed myself, darling
for that nostalgic taste of steel
and if this love was artifical
all along
the paperclip problem
cannot riddle you senseless
can it, my darling machine?
#light academia#poem#poetry#quotes#spilled ink#thoughts#love#paperclip problem#artifical intelligence#ethical dilemma#hacking#destruction#dystopia#carpe-noctem-bitchess#nostalgia
8 notes
·
View notes
Text
So I've liked to hc for a while that Mairon does have a third eye and it's indeed the big flaming one and he summons and dismisses it at will (like Manwë with his wings).
My new idea is that Mairon can also move the eye, like it's not "attached" to his head or even in orbit around him or anything. He can place it wherever and likes hiding it in fireplaces to watch people. You might open your wardrobe one morning and find The Eye of Sauron just sitting there, glaring at you.
It's a neat convenience feature (for him)
#mairon's fun and ethical life hacks#mairon#sauron#headcanons#fun headcanons#crack#silmarillion#lotr#lord of the rings#cílil's casual crack & silly shitposts
69 notes
·
View notes
Text

371 notes
·
View notes
Text
Curie would love the followers of the apocalypse girlie needs to find a way to contact them immediately.
#she is trying so hard doing what folkowers doesnin west but just by herself alone in east coast#she would love sharing her 200 years of archived knowledge in her brain#also when she is synth followers would like to do some research (completely ethical amd with her consent)#like how they try to hack mr house to learn how he lives that long they would use synth biology knowledge to improve human lifes#curie herself would love it#she would also love learning about new knowledge like post war history or species that doesn't exist in east like nightkin etc.#geym#fallout 4#curie
4 notes
·
View notes
Text
Building Your Own Cyberdeck:
What do you do when you have extra time between a job and your next? How about building your own Cyberdeck? Check this article out for tips on building your own!
The Ultimate Hacker Project
For aspiring cybersecurity professionals, cyberpunk enthusiasts, hardware hackers, and circuit benders, one of the best hands-on projects you can take on is building your own cyberdeck. Despite overwhelming schedules full of training programs, full time work weeks, sometimes limited funds, and the endless possibilities of hardware combinations, many fans of the…

View On WordPress
#Cyber#Cyber Security#cyberdeck#cyberpunk#Cybersecurity Specialist#Ethical Hacking#hack#hacker#infosec#IT#IT professional#mobile#mobile computer#Pentesting#programming#project
20 notes
·
View notes
Text

#mdshirajumbillahsiam#succession#the mandalorian#donald trump#margot robbie#taylor swift#ethical hacker#Red Team#cyber security specialist#hacking your mind#hackers
2 notes
·
View notes
Text
Unmasking the Invisible: Ethical Hackers and the Art of Vulnerability Hunting

In today's digital age, our reliance on technology has created a vast and interconnected landscape. While this interconnectedness offers undeniable benefits, it also introduces vulnerabilities – chinks in the armor that can be exploited by malicious actors. Imagine a grand castle, its walls seemingly impenetrable. But what if there were hidden weaknesses, unseen passages known only to a select few? This is where ethical hackers, the unsung heroes of cybersecurity, come in. They are the vulnerability hunters, the digital detectives on a relentless quest to identify and expose these weaknesses before they can be used for malicious purposes.
This blog delves into the fascinating world of vulnerability hunting, exploring the role of ethical hackers in safeguarding our digital assets. We'll uncover the techniques they employ, the challenges they face, and the importance of cyber security training Mumbai for fostering a skilled workforce of ethical hackers.
The Invisible Threat: Unveiling Vulnerabilities
Imagine a digital thief attempting to break into a bank vault. They wouldn't simply smash through the front door; they'd meticulously search for weaknesses – a faulty security system, a hidden ventilation shaft. Similarly, vulnerabilities in software, hardware, and network configurations act as those hidden access points for malicious hackers. These vulnerabilities can be:
Software Bugs: Errors in the code that can be exploited to gain unauthorized access or cause unexpected behavior.
Misconfigurations: Improper settings in network devices or software applications that create security gaps.
Zero-Day Attacks: Previously unknown vulnerabilities that attackers exploit before software vendors have a chance to issue a patch.
These vulnerabilities are often invisible to the untrained eye. This is where ethical hackers, also known as white hats, step in. They act as the security guardians, wielding specialized tools and techniques to hunt for these hidden weaknesses.
The Art of the Hunt: Techniques of a Vulnerability Hunter
Ethical hackers employ a diverse arsenal of techniques in their pursuit of vulnerabilities. Here are some of the most common methods which you can learn in cyber security training mumbai :
Network Scanning: Ethical hackers use specialized tools to scan networks and identify devices, open ports, and potential security weaknesses.
Penetration Testing: This involves simulating a cyberattack to identify vulnerabilities that could be exploited by malicious actors. Ethical hackers attempt to gain unauthorized access to systems using various techniques, mimicking the methods black hats might employ.
Social Engineering Testing: This involves testing the organization's security awareness by attempting to trick employees into revealing sensitive information or clicking on malicious links.
Code Review: Ethical hackers meticulously examine the code of software applications to identify potential vulnerabilities and bugs.
These techniques require a deep understanding of cybersecurity principles, programming languages, and hacking methodologies. Cyber security training Mumbai can equip individuals with the necessary skills and knowledge to become proficient vulnerability hunters.
The Challenges of the Hunt: A Constant Cat-and-Mouse Game
The world of vulnerability hunting is a constant cat-and-mouse game. As technology evolves, so do the vulnerabilities that ethical hackers need to identify. Here are some of the key challenges they face:
The Ever-Expanding Attack Surface: With the increasing use of cloud computing, mobile devices, and the Internet of Things (IoT), the attack surface – the potential points of entry for attackers – is constantly expanding. This makes it more challenging for ethical hackers to identify all potential vulnerabilities.
Zero-Day Attacks: The constant threat of zero-day attacks, where attackers exploit previously unknown vulnerabilities, keeps ethical hackers on their toes. They need to be constantly researching and developing new methods to identify these vulnerabilities before they can be used in real-world attacks.
Staying Ahead of Black Hats: Malicious hackers are constantly innovating and developing new attack techniques. Ethical hackers need to stay up-to-date on the latest hacking trends and methodologies to ensure they can identify vulnerabilities before they are exploited.
The Value of the Hunt: Why Vulnerability Hunting Matters
Vulnerability hunting plays a critical role in safeguarding our digital infrastructure. By proactively identifying and patching vulnerabilities, ethical hackers can significantly reduce the risk of successful cyberattacks. Here are some of the key benefits of vulnerability hunting:
Reduced Risk of Cyberattacks: By identifying and patching vulnerabilities, ethical hackers make it more difficult for malicious actors to gain unauthorized access to systems and data.
Improved Security Posture: The process of vulnerability hunting helps organizations identify and address weaknesses in their overall security posture, leading to a more robust defense.
Enhanced Compliance: Many regulations require organizations to conduct regular vulnerability assessments. Ethical hacking helps organizations meet these compliance requirements.
Cyber security training Mumbai can equip individuals with the skills to become ethical hackers, contributing to a safer digital landscape. These courses can provide valuable knowledge on vulnerability hunting methodologies, penetration testing techniques, and ethical hacking best practices.
2 notes
·
View notes
Text
it continues to be funny to me in such a weird way I can't place my finger on that all the things I'm "supposed" to be boycotting are....already things I don't consume....
#like idk why this is funny to me but it is#like ppl hacking out ethical consumption over stuff and I'm just lie#oh well I didn't buy/read/watch that anyway so#easy for me I guess!
2 notes
·
View notes
Text
Hack Someone Device Wirelessly.
.
.
.
.
.
#hacking #devine #device #android #cpp #procoder#programming #java #python #wireless #blackhat #whitehat #Black #white #instagram #viral #instagood #cybercrime #cyberday #cybrtrk #cybersecurity
#binance#ethical hacking#crytptocurrency#hacking#how to hack#sextortion#hackgame#justgothacked#deleted account#facebookrecovery#accounthacked#cheating spouse#bitcoin#stolencoin
2 notes
·
View notes
Text
2 notes
·
View notes