#Javascript password generator
Photo

JavaScript Random Password Generator
#javascript password generator#password generator#password generator javascript#html css#code#learn to code#webdev#frontenddevelopment#javascript projects for beginners#simple javascript projects#divinector
1 note
·
View note
Text
Javascript password generator

Javascript password generator how to#
Javascript password generator generator#
Javascript password generator android#
Javascript password generator software#
It will then generate the rest of it length randomly using the characters from variable a. Number 62 : remember when we created a variable that was consist of alphabets and numbers weell 62 is the length of our variable. And if you want to generate a longer password, set it to a greater number like 25.
Javascript password generator generator#
When it comes to generating the password, the generator will generate one character for each variable of s, n, u, l(4 in total). If you want to generate a shorter password you can set it to a lower number like 15 or 10. HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE)ĪRISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE. The password generator will not generate a password that contained any character that you placed in the Not field.
Javascript password generator how to#
(INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES LOSS OF USE, DATA, OR PROFITS OR BUSINESS INTERRUPTION) node.js await return value code example java debug remote code example submit() in jquery code example JScript getElement by class code example handle apostrophe in string sql server code example how to browse a file and save in angular code example FQDN command linux code example git diff all files against specific sha code example fetch. IN NO EVENT SHALL THE REGENTS OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES So, load the Font Awesome 5 CSS into the head tag of your HTML page. This password generator tool uses Font Awesome for the copy icon for the generated password copy to the clipboard button. Genera una password con formato predefinito, cvcvcvcv, cioè con 4 sillabe casuali consecutive della forma cv. How to Create JavaScript Random Password Generator 1.
Javascript password generator software#
THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS "AS IS"ĪND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. Navigazione toggle Home Javascript Canvas > Ajax SVG VRML Generatore di password. Programmers, Right-click this page and to get at the code. Keep clicking the Password button (above) until one comes up that you like. Be aware that some characters are not available from a mobile phone and some, like the euro symbol € on a British keyboard, need the Alt Gr key held down. Since 9 characters is no longer considered secure, create two passwords using the generator and use them together as one password separated by some special character of your own choice. But don't use this one - use the generator and get another one! It is obviously unguessable, but has a good chance of being memorable because it rhymes (say 3 letters at a time) and the change of case happens after the first rhyming part (the first three characters are lower-case, the rest are upper-case). This is a system for generating passwords that are unguessable, and yet memorable.Īn example of a good password is imjE2A13K. They have things that are easy to remember (and, therefore, guess) or else they forget them. Visit Source Code & Project today to see how we can help build your career!Ĭopyright 2017-2019 by SourceCode and Projects.People are ever so naughty with passwords. What more, we also provide beginners with C Tutorial, C++ Tutorial, Java Tutorial, PHP Tutorial, JavaScripts Tutorial, and Python Tutorial. So feel free to choose whichever language you want to begin your project.
Javascript password generator android#
If you want to be a game developer or android developer, we can help you get started with our list of game app projects and Android app projects. We are also the go-to platform to find the source code for the application project. The source code for the projects available is based on different computer programming languages such as C/C++, PHP, Java, Javascript, VB.Net,, Python and Swift. Please feel free to use it for educational purposes. We provide tutorials, free source codes and how to’s? to get started with projects that might interest you. We hope to provide anyone with necessary and relevant content projects they need to practice and help in their daily programming career. TL DR We are fast becoming best open source code & projects organization - Code Projects is developed to provide interested people with resources to build their knowledge, and exchange ideas.

0 notes
Text
Javascript password generator

Javascript password generator how to#
Javascript password generator generator#
Javascript password generator code#
Javascript password generator license#
Javascript password generator license#
For more license details you can check the readme file in the downloaded folder. Remember to use this project just for educational purposes. If you face any issues running it then firstly, We suggest you use the latest versions of browsers like Google Chrome and Mozilla Firefox, etc then check for other solutions. So, load the Font Awesome 5 CSS into the head tag of your HTML page.
Javascript password generator generator#
This password generator tool uses Font Awesome for the copy icon for the generated password copy to the clipboard button.
Javascript password generator how to#
Requires Font Awesome Iconic Font in this instance. How to Create JavaScript Random Password Generator 1. Create Copy buttons contained in the password subject. Create a button to generate a powerful password. How To Run the Password Generator Project Without Any Problem?Īfter downloading this project, extract the zip file, open the folder and click on the index file which will open in your default browser. Create an input file to place the generated password strings. This created password will not be saved at any place. You can copy the generated password to the clipboard and use it easily. Now a password will appear on the screen which consists of different characters as per your given instructions. To get the character of the string of a particular index we can use.
Javascript password generator code#
the we will use Math.random () and Math.floor () method to generate a number in between 0 and l-1 (where l is length of string). Copy the below and paste it into the source code of your web page. You will have to choose a minimum of one option to create a password. Approach 1: Make a string consist of Alphabets (lowercase and uppercase), Numbers and Special Characters. Other boxes will be for numeric, lower, and upper characters respectively. html file or opening the file using Google Chrome or any other browser.Then the next section for the special characters clicks on confirm if you want to add them to your password. You can also open the project by double clicking on. After you are done, open your browser and type the URL for example. After extracting, copy the project folder to your destination folder. zip file using any zip programs such as Winrar or 7Zip. After you download the program, unzip the. To run the project, you will need to download WINrar or 7Zip to extract the. This application uses a different input field like numbers, texts, Uppercases and symbols to generate a perfect password for you.
You can select whether to inlclude Symbols like $%# or not(checkbox)Ī simple web application designed to run on browser and to generate strong password using input from the users. How to create a password generator - JavaScript - For this, use Math.random() to create random passwords.ExampleFollowing is the code function makePassword(.
You can select whether to inlclude Numbers or not(checkbox).
You can select whether to inlclude Uppercase letter or not(checkbox).
You can select the number of characters you want on your password.
If you fall within this category, you should consider using this Password Generator web application which quickly generate a perfect strong password along with the input you feed to the application. About Easy Password Generator Project In JavaScript Other. So, many people often struggle with creating a strong password including symbols and numbers. Learn to create utility applications using JavaScript Programming Language. There you have it we successfully created a Simple Random Password Generator using javascript. To do this just copy write the code as shown below inside the text editor and save it as script.js. This code will generate a password characters where the length is base on the input type value. Because I can't use any HTML element directly in JavaScript. Here the constant of the display and the button is determined. Create an input file to place the generated password strings. First, the constant of some HTML functions is determined. Now you need to use some JavaScript to activate this Random Password Generator. In the internet, we often use various passwords in various websites, using similar passwords might be risky. This code contains the script of the application. Activate Password Generator with JavaScript.

0 notes
Video
youtube
JavaScript - Chat GPT + JavaScript Password generator the future is here...
0 notes
Text
All right, since I bombarded a poor mutual yesterday...
Privacy is not security and security is not privacy. These terms are not interchangeable, but they are intrinsically linked.
While we're at this, anonymity =/= security either. For example, Tor provides the former, but not necessarily the latter, hence using Https is always essential.
It is impossible to have privacy without security, but you can have security without privacy.
A case in point is administrators being able to view any data they want due to their full-access rights to a system. That being said, there are ethics and policies that usually prevent such behavior.
Some general tips:
Operating System: Switch to Linux. Ubuntu and Linux Mint are widely used for a reason. Fedora too. And don't worry! You can keep your current operating system, apps and data. If you're on a Mac computer, you can easily partition your hard drive or SSD by using Disk Utility. If you're on Windows, you can follow this guide.
You want to go a step further? Go with Whonix or Tails. They're Linux distributions as well, but they're both aiming for security, not beauty so the interface might not be ideal for everyone. Many political activists and journalists use them.
You want anonymity? Then you need to familiarize yourself with Tor. Also, Tor and HTTPS and Tor’s weaknesses. When you're using it, don't log in to sites like Google, Facebook, Twitter etc. and make sure to stay away from Java and Javascript, because those things make you traceable.
Alternatives for dealing with censorship? i2p and Freenet.
Is ^ too much? Welp. All right. Let's see. The first step is to degoogle.
Switch to a user-friendly browser like Firefox (or better yet LibreWolf), Brave or Vivaldi. There are plenty of hardened browsers, but they can be overwhelming for a beginner.
Get an ad blocker like Ublock Origin.
Search Engine? StartPage or Duckduckgo. SearXNG too. Like I said degoogle.
Get a PGP encrypted e-mail. Check Protonmail out.
There's also Tutamail that doesn't cover PGP, but uses hybrid encryption that avoids some of the cons of PGP.
Skiff mail is also a decent option.
Use an e-mail aliasing service such as SimpleLogin or AnonAddy.
Check OpenPGP out. Claws Mail is a good e-mail client for Windows and Linux, Thunderbird for Mac OS.
Gpg4win is free and easy to use for anyone that wants to encrypt/decrypt e-mails.
Instead of Whatsapp, Facebook messenger, Telegram etc. use Signal for your encrypted insant messaging, voice and video calls.
Get a metadata cleaner.
Get a firewall like Opensnitch, Portmaster or Netguard which can block Internet for trackers.
Alternatively, go with a private DNS that blocks these trackers. NextDNS is a good paid service. Rethink a good free option.
Replace as many of your applications as you can with FOSS (free and open source) ones. Alternativeto can help you.
Always have automatic updates on. They are annoying af, I know, but they are necessary.
Keep your distance from outdated software.
Always have two-factor authentication (2FA) enabled.
Do not use your administrator account for casual stuff. If you're on Linux, you probably know you can be sudo, but not root.
On Linux distributions use AppArmor, but stay away from random antivirus scanners. Other distributions default to SELinux, which is less suited to a beginner.
Never repeat your passwords. If you can't remember them all, use a password manager like KeePass.
Encrypt your drive.
Honestly, VPNs have their uses and ProtonVPN, Mullvad and Windscribe are decent, but eh. If you don't trust your ISP, why would you trust the VPN provider that claims they don't log you when you can't verify such a thing?
40 notes
·
View notes
Text
possible purpose of /that/ secret message + tally5 info

hopefully correct transcribed text: 3aqxw97pktc8uki458fbdpfoacllex2f07bf8mg24b4mpfx2adc6v3f5yhxjd8i7sf11312zaj5lazet47jod5jczec5mvb6bz2o59r143sf2pe916sczcn7emvbl55ehe9iqb2708tt83482c8tw3c77gn47ojca634gbcfz0016s647wwlakcn46brele0eam9
so, first off: i’m almost positive this is some sort of key to the tally5 code. mainly because of them both reference being “correct”:
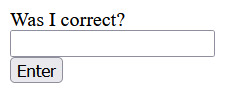
typing stuff like “yes”, “no”, and “fuck you” in this box doesn’t work, and copy-pasting the message text doesn’t work either, so unfortunately we have to try harder to figure this one out.
looking in the source code of the page, we can find evidence that the tally5 password is not english, so trying to translate the secret message to english is most likely barking up the wrong tree.
that said, i’m slightly unreliable since the source code is javascript, which i’ve never written. let me walk you through my thought process for figuring this out:
whenever the “Enter” button on the page is clicked:

variable “input” stores whatever you typed in as a password.
the code then checks if the password is correct. if it is, the page displays the image from this tumblr image url:
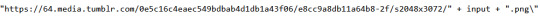
notice the “input” inserted in the middle. basically, the code generates the full url from being given the correct password. therefore the password is the ending part of the image url (excluding .png).
now i’ve never seen a tumblr image url that’s coherent english, which unfortunately means this is going to be a massive pain in the ass to figure out. but on the bright side, you won’t be confused anymore wondering why the message seems impossible to translate to actual words! (note: if you have, in fact, found a way to translate the message to actual words, disregard this.)
now for the bad news: the secret text seems way too long for a direct mode of “deciphering” to the correct url piece, so most likely no using easy methods like rot13 (my very first thought, considering the number of the footnote). it’s still going to be a puzzle to figure out how to get the missing url piece from this.
so what’s next? i don’t know---search for more clues or just try whatever you can think of in the tally5 box, i guess. good luck!
75 notes
·
View notes
Note
hi! sorry for the message, especially if it's a repeat question (i checked all the gender variable/twine gender coding tags you had and couldn't find anything, but i know tumblr can be weird). i was wondering if there was a way to use multipronouns for ROs? like say i have an RO who uses she/he pronouns. how would i go about switching between them? thank you for all the coding resources you've published btw! you're a genius
Aww, thank you so much Anon!! 🥺🥺
If your RO canonically switches between she/he pronouns, no customization from the MC needed, then you don't have to use my macro! You can just write his pronouns normally and switch up her pronouns throughout the story.
However, if you mean that you want to let the player customize the ROs' multipronouns the same way they can customize their own—I have a somewhat scuffed way you can do it, though it hurts my programming insides. It's the easiest way for you and won't require me to create another macro entirely!
LINKS — here's a link to the Github of my Multipronouns macro. You'll need it for this guide!
If you've followed the guide and need the code I wrote to compare to yours, here's a link to the itch.io page!
Password: romultipronouns
Guide
1. From my Github page with the code for the multipronouns, copy and paste the code pretty_multipronouns.js (code that goes into your Javascript) and multivar.txt (code that goes into your StoryInit) into a Google Docs. I recommend you add a blank page in between them so you can keep them separate from each other!
1.5. An explanation: all the code inside the Javascript and StoryInit code is specifically made to be used for one character only, the MC. Hence, all the code I used within them are generic or uses the keyword "mc", so it's built to be unique to MC.
HOWEVER. What we can do is copy the code used for MC and replace all the variables with different ones so you can use them for another character.
Let's say I have an RO with the initial X. They'll be the example I'll be using going forward! For your sake, replace the initial with your RO's initial.
2. Look at your Google Doc. The very first line of the code, if you copied the JS first and then the StoryInit code after, is something that says Macro.add("gender" and then a bunch of things after. In front of gender, prefix it with the initial of your RO—in my case, it'll look like Macro.add("x_gender"
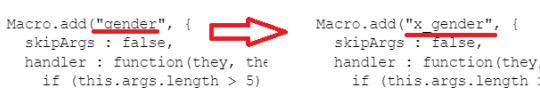
So, instead of using the macro <<gender>> to add to MC's pronouns, you use the macro <<x_gender>> to add to X's pronouns.
If you somehow pasted in multivar.txt first and then pretty_multipronouns.js so Macro.add doesn't appear on the top of your document, Ctrl+F or CMD+F to search for Macro.add within the Google Doc.
3. NEXT, hit CTRL+H OR go under Edit > Find and Replace. It'll pull up a window asking for what you want to search, and what you want to replace those search terms with.
In our case, we'll be searching for all instances of prons in our document, and replacing them with a prefix of the RO's initials at the end. In my case, I'll replace prons with x_prons. Hit "Replace All".

4. Don't leave the window yet! We'll be staying here throughout the entire guide. Now, Find the term window.pronouns and replace it with the RO's initials prefixing "pronouns" — in my case, it'll look like window.x_pronouns. Again, REPLACE ALL.

5. Find the term arr_ and replace it with a prefix of the RO's initals. Mine will look like x_arr_ (yes, you need the underscore!). REPLACE ALL. Be careful not to hit Replace All twice.
6. Find the term mc and replace it with the RO's initials. So if it was "mc", it'll be replaced with "x". REPLACE ALL.
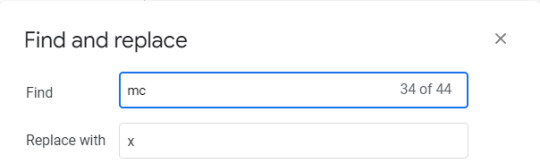
7. When you're done, copy and paste the Javascript code into your Story Javascript. Do not replace MC's multipronoun code if you have it there, if you want the MC to have multipronouns as well. This is the code from pretty_multipronouns.js. I recommend you add a comment as a header to indicate that the code you're pasting is for that RO.
8. Copy and paste the StoryInit code into your StoryInit. Again, this is the code from multivar.txt. Like #7, do not replace the original StoryInit code if you're also using multipronuns for the MC, just add it. I recommend you add a comment as a header to indicate that the code you're pasting is for that RO.

9. Test it! If you did everything right, it should work. Here's a test passage and the output it made, where I set the MC's pronouns to they/xe and the X's pronouns to he/she.
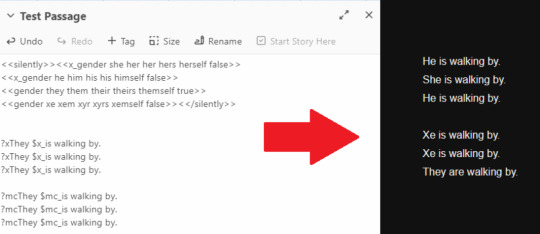
It should work the same as using multipronouns for the MC, you just replace the keyword mc with the initials you gave the RO throughout.
10. Want more ROs with multipronouns? Just do the steps all over again, but with different initials. So if I have an RO with the initial Y, I will redo the previous steps with Y instead of X. If I have an RO with the initial Z, same thing. Just keep making new variables and macros for each RO, so do NOT replace the previous code you made for each of them!
If for some reason your code doesn't work, I have the code I used for this guide here for you to compare it with. (Pass: romultipronouns) Feel free to ask questions through asks, replies or DMs! 💕💕
While my preference is to create a new macro to streamline the process by allowing you to create multipronouns for multiple characters with just a single macro, it'll require a lot of brainpower and time. That's a project I'm willing to consider in the future! For now, though, I hope this workaround works for you!
Thanks so much for asking :) 💕
#uroboros-if#uroboros#asks#anon#coding#coding resources#multipronouns#multiple pronouns#sugarcube coding resources#sugarcube#twine coding resources
31 notes
·
View notes
Text


>> Friday 18th November 2022 🎄
Its Week 5 of my coding night classes and this week's task is to create a password generator using HTML, CSS and JavaScript. In the image over, that is what I am supposed to replicate. I think I can do this, I did struggle a tiny bit during classes but I made up for that by doing extra study after class. I've created something very similar to this but using C# instead so I'll just go over that code and try and translate that to JavaScript code!
I'm coding online using Github's new CodeSpaces which I think is super cool, especially if you're not on your main computer but still want to work on your repos!
Have a nice day/night and happy programming! 🎄
#html#css#javascript#programming#coding#software developer#studyblr#100 days of code#comp sci#projetcs#programmer#developer#computer science#backend#onlinelearning#dotnet#software development#study inspo#study motivation#study aesthetic#studying#python
66 notes
·
View notes
Text
GitHub Repositories Hit by Password-Stealing Commits Disguised as Dependabot Contributions
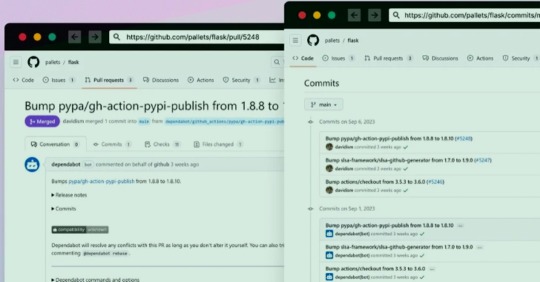
A new deceptive campaign has been observed hijacking GitHub accounts and committing malicious code disguised as Dependabot contributions with an aim to steal passwords from developers.
"The malicious code exfiltrates the GitHub project's defined secrets to a malicious C2 server and modify any existing javascript files in the attacked project with a web-form password-stealer malware code effecting any end-user submitting its password in a web form," Checkmarx said in a technical report
The malware is also designed to capture GitHub secrets and variables to a remote server by means of a GitHub Action.
The software supply chain security firm said it observed the atypical commits to hundreds of public and private GitHub repositories between July 8 and 11, 2023.
It has emerged that the victims had their GitHub personal access tokens stolen and used by the threat actors to make falsified code commits to users' repositories by posing as Dependabot.
Dependabot is designed to alert users of security vulnerabilities in a project's dependencies by automatically generating pull requests to keep them up-to-date.
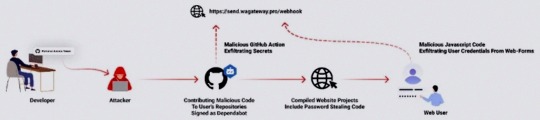
"The attackers accessed the accounts using compromised PATs (Personal Access Token) -- most likely exfiltrated silently from the victim's development environment," the company said. Most compromised users are located in Indonesia.
However, the exact method by which this theft may have taken place is currently unclear, although it's suspected that it may have involved a rogue package inadvertently installed by the developers.
This is evidenced by a new data exfiltration campaign targeting both npm and PyPI that uses as many as 39 counterfeit packages to gather sensitive machine information and transmit the details to a remote server.
The development highlights the continued attempts on part of threat actors to poison open-source ecosystems and facilitate supply chain compromises.
3 notes
·
View notes
Text
What is JSON, and why is it used in APIs?

In today's digital world, data needs to be transferred quickly and efficiently between different systems. JSON, or JavaScript Object Notation, is one of the most popular formats used to achieve this. Understanding JSON and its role in APIs can help you appreciate its importance in modern web development.
What is JSON?
JSON (JavaScript Object Notation) is a lightweight data format that is easy for both humans to read and write, and for machines to parse and generate. It uses a simple syntax, similar to JavaScript, to represent structured data like objects, arrays, numbers, strings, and Booleans.
Here’s a basic example of a JSON object:
{
"name": "Webstep",
"age": 10,
"isStudent": false,
"courses": ["Website Development", "SEO", "SMO"]
}
This example shows how JSON can represent various types of data, such as text, numbers, Booleans, and lists, in a way that is both simple and flexible.
Why is JSON Used in APIs?
Data Interchange: JSON is primarily used in APIs (Application Programming Interfaces) as a data interchange format. APIs allow two applications to communicate with each other, and JSON provides a common language for data exchange. Whether it’s a weather app fetching the latest data or a shopping site displaying product information, JSON helps make that communication possible.
Simplicity and Readability: JSON’s structure is straightforward, making it easy to read and understand. Developers can quickly see the data being exchanged, which speeds up development and debugging processes.
Lightweight: Unlike other data formats such as XML, JSON is compact and lightweight. This reduces the amount of data that needs to be transferred between a server and a client, resulting in faster communication and lower bandwidth usage.
Compatibility: JSON is language-independent, which means it can be used across different programming languages. Most modern programming languages, such as Python, Java, and JavaScript, have built-in libraries to easily parse and generate JSON data.
Support for Complex Data Structures: JSON can represent complex data structures like nested objects and arrays, making it ideal for transmitting detailed information. For example, a single JSON object can contain all the details of a customer, including their contact information, order history, and preferences, in a structured format.
Real-World Examples of JSON in APIs
Web Applications: When you log in to a website, your browser sends your credentials (like username and password) to the server in JSON format. The server checks the information and sends a JSON response back, indicating whether the login was successful.
Mobile Apps: JSON is commonly used in mobile apps to fetch real-time data, like news feeds or social media updates. The app sends a request to the server via an API, and the server responds with the requested data in JSON format.
IoT Devices: Many Internet of Things (IoT) devices use JSON to send data to cloud servers. For example, a smart thermostat may send temperature readings and settings to a remote server in JSON format.
Conclusion
JSON is a powerful and efficient data format that plays a crucial role in the world of APIs. Its simplicity, compatibility, and flexibility make it the preferred choice for data exchange between applications. As more and more services rely on APIs for communication, JSON will continue to be a vital tool for developers and businesses alike.
Contact - Webstep development Team
0 notes
Text
How to Apply Free OTP Technology in Your App and Website: - Infinity Webinfo Pvt Ltd

One-Time Password (OTP) technology is a widely-used method to enhance security in apps and websites. By using OTPs, you can ensure that even if a user's password is compromised, their account remains secure. This guide will show you how to implement free OTP technology in your app or website, OTP implement, free OTP implement and how to apply free OTP.
APPLY FREE OTP TECHNOLOGY IN YOUR WEBSITE AND APP
1. What is OTP Technology?
OTP Explained:
An OTP is a unique, time-sensitive code sent to a user to verify their identity. It is commonly used for two-factor authentication (2FA) or during sensitive transactions.
Benefits of OTP Implementation:
OTPs provide an additional layer of security, making it significantly harder for unauthorized users to access accounts.
2. Choosing a Free OTP Service
To apply free OTP technology, you need to select a service provider that offers a free tier for OTP implementation. Here are some popular options:
Google Authenticator:
Description: Google Authenticator is a mobile app that generates time-based one-time passwords (TOTP). It's widely used and can be integrated with various systems and applications.
Features: Easy to use, secure, supports multiple accounts, offline functionality.
Integration: You can integrate Google Authenticator using libraries that support TOTP in your preferred programming language, like pyotp for Python or otplib for Node.js.
Authy:
Description: Authy by Twilio is another popular app for generating OTPs. It offers both TOTP and push-based notifications.
Features: Multi-device synchronization, backups, and support for both TOTP and SMS-based OTPs.
Integration: You can integrate Authy using their API, which allows for both TOTP generation and SMS-based OTPs. This is useful if you want to give users multiple options for receiving OTPs.
FreeOTP by Red Hat:
Description: FreeOTP is an open-source mobile app by Red Hat that generates TOTP and HOTP (HMAC-based One-Time Password) tokens.
Features: Open-source, supports both TOTP and HOTP, no ads, and privacy-focused.
Integration: Similar to Google Authenticator, it can be integrated into your system using TOTP libraries.
TOTP (Time-based One-Time Password) Algorithms:
Description: TOTP is a standardized algorithm used to generate time-based OTPs. It’s widely supported and is the underlying technology behind many OTP apps, including Google Authenticator and FreeOTP.
Features: Time-based OTPs are dynamic and expire after a short period, typically 30 seconds, making them more secure.
Integration: You can implement TOTP directly using libraries like pyotp (Python), otplib (Node.js), or other language-specific libraries. These libraries provide functions to generate and verify OTPs.
When choosing an OTP technology, consider your users' needs and the level of security required. All these options are robust and can significantly enhance the security of your website or app.
3. Steps to Implement OTP in Your Website or App
1. Choose an OTP Method
Decide whether you want to implement SMS, email, or app-based OTPs. SMS and email are easier for users but may incur costs if scaled, whereas app-based OTPs are cost-effective and secure but require users to install an app.
2. Select a Library or API
Use a free library or API that supports OTP generation and validation. Some popular options include:
Python: PyOTP library for TOTP and HOTP (HMAC-based One-Time Password).
JavaScript: speakeasy for TOTP and HOTP.
PHP: GoogleAuthenticator.php for integrating with Google Authenticator.
Node.js: otplib for generating OTPs.
3. Integrate OTP Generation
In your application, add code to generate OTPs. For example, using the PyOTP library in Python: # Generate a TOTP key
totp = pyotp.TOTP('base32secret3232')
otp = totp.now()
print("Your OTP is:", otp)
This code generates a time-based OTP that you can send to the user.
4. Send the OTP
Once the OTP is generated, send it to the user via the chosen method (SMS, email, or app). For SMS, you might use a free or freemium service like Twilio, while email can be sent using SMTP libraries or services like SendGrid.
5. Validate the OTP
After the user enters the OTP, validate it using the same library. For example, in Python: is_valid = totp.verify(user_input_otp)
if is_valid:
print("OTP is valid!")
else:
print("OTP is invalid!")
6. Handle Errors and Expirations
Ensure that your implementation handles cases where the OTP has expired or the wrong OTP is entered. Provide user-friendly messages and options to resend the OTP if necessary.
Security Best Practices
Short Expiry Time: Ensure that OTPs expire quickly, typically within 30 seconds to 5 minutes, to minimize the risk of unauthorized access.
Rate Limiting: Implement rate limiting to prevent brute-force attempts to guess the OTP.
Secure Transmission: Always use HTTPS to send OTPs to avoid interception by attackers.
Backup Options: Provide users with backup authentication methods, such as recovery codes, in case they cannot access their OTP.
7. Verify the OTP
After sending the OTP, prompt the user to enter the code they received.
Verify the entered OTP using the service provider’s API or through custom logic if using an open-source library.
8. Ensure Security
OTPs should be time-limited, typically expiring within 5 to 10 minutes.
Use secure channels (like encrypted SMS) to transmit OTPs.
Implement rate limiting to prevent brute force attacks.
4. Testing Your OTP Implementation
Test thoroughly across different devices and network conditions to ensure reliability.
Verify that OTPs are correctly sent, received, and validated.
Ensure that expired or incorrect OTPs trigger appropriate error messages.
5. Scaling Beyond Free Tiers
As your app or website grows, you might outgrow the free OTP tiers. Consider upgrading to a paid plan to accommodate more users.
Evaluate your options to balance cost with the reliability and features you need.
Conclusion
Implementing free OTP technology in your app or website is a straightforward process that enhances security without incurring significant costs. By following the steps outlined above, you can apply OTP technology effectively, ensuring your users’ accounts and data remain secure. Whether you use a service like Google Authenticator, Authy, or FreeOTP by Red Hat, the key is to integrate, test, and secure your OTP implementation properly.
#OTP Technology#Free OTP TECHNOLOGY#OTP Implementing Free#Apply free#OTP#website and app development company
0 notes
Photo

Random Password Generator
#password generator#password generator javascript#javascript projects for beginners#javascript#javascript projects#learn to code#code#html css#frontenddevelopment#webdev#divinectorweb
0 notes
Text

HTML
HTML Course Content
HTML, or *HyperText Markup Language*, is the standard language used for creating and structuring content on the web. It defines the structure of web pages through the use of elements and tags, which dictate how text, images, links, and other multimedia are displayed in a web browser. HTML provides the foundation for web documents, allowing developers to format content, organize sections, and create interactive features. It consists of a series of elements enclosed in angle brackets, such as <p> for paragraphs, <a> for links, and <img> for images, which together build the content and layout of a webpage.
HTML Contents
HTML (HyperText Markup Language) is the foundation of web pages and web applications. It structures content on the web, defining elements like headings, paragraphs, links, images, and other multimedia. Here’s a breakdown of key HTML contents:
1. *Basic Structure*:
*<!DOCTYPE html>*: Declares the document type and version of HTML.
*<html>*: The root element that encompasses the entire HTML document.
*<head>*: Contains meta-information about the document, such as title, character set, and links to CSS or JavaScript files.
*<body>*: Contains the content that is visible on the web page, including text, images, and interactive elements.
2. *Text Elements*:
*<h1> to <h6>*: Heading tags, with <h1> being the most important.
*<p>*: Paragraph tag for regular text.
*<a>*: Anchor tag for creating hyperlinks.
*<span>* and *<div>*: Generic containers for grouping inline and block content, respectively.
3. *Lists*:
*<ul>*: Unordered list.
*<ol>*: Ordered list.
*<li>*: List item, used within <ul> or <ol>.
4. *Images and Media*:
*<img>*: Embeds images.
*<video>* and *<audio>*: Embeds video and audio files.
*<figure>* and *<figcaption>*: For adding images or media with captions.
5. *Forms*:
*<form>*: Contains form elements for user input.
*<input>*: Various input fields (text, password, checkbox, radio, etc.).
*<textarea>*: For multi-line text input.
*<button>* and *<select>*: Buttons and dropdown menus.
6. *Tables*:
*<table>*: Defines a table.
*<tr>*: Table row.
*<th>*: Table header cell.
*<td>*: Table data cell.
7.*Semantic Elements*:
*<header>, *<footer>**: Defines the header and footer sections.
*<nav>*: Navigation section.
*<article>*: Independent content item.
*<section>*: Thematic grouping of content.
*<aside>*: Sidebar or additional content.
*<main>*: Main content of the document.
8. *Metadata and Links*:
*<meta>*: Provides metadata such as descriptions, keywords, and viewport settings.
*<link>*: Links external resources like CSS files.
*<script>*: Embeds or links JavaScript files.
Importance of HTML
HTML is critically important for several reasons:
1. *Foundation of Web Pages*:
HTML is the core language that structures content on the web. Without HTML, web pages wouldn’t exist as we know them. It organizes text, images, links, and other media into a cohesive and navigable format.
2. *Accessibility*:
Proper use of HTML ensures that web content is accessible to all users, including those with disabilities. Semantic HTML elements provide context to assistive technologies, making it easier for screen readers to interpret the content.
3. *SEO (Search Engine Optimization)*:
Search engines rely on HTML to understand the content of web pages. Properly structured HTML with relevant tags and attributes improves a website’s visibility in search engine results, driving more traffic to the site.
4. *Interoperability*:
HTML is universally supported by all web browsers, ensuring that content can be displayed consistently across different devices and platforms. This cross-compatibility makes HTML the most reliable way to share content on the web.
5. *Foundation for CSS and JavaScript*:
HTML is the backbone that supports styling and interactivity through CSS and JavaScript. It provides the structure that CSS styles and JavaScript enhances, creating dynamic, interactive, and visually appealing web experiences.
6. *Web Standards Compliance*:
HTML is maintained by the World Wide Web Consortium (W3C), which sets standards to ensure the web remains open, accessible, and usable. Following these standards helps developers create web content that is robust and future-proof.
7. *Ease of Learning and Use*:
HTML is relatively simple to learn, making it accessible to beginners and non-programmers. Its simplicity also allows for rapid development and prototyping of web pages.
In summary, HTML is essential because it structures and defines web content, ensuring it is accessible, searchable, and interoperable across various platforms. It is the foundation upon which modern web design and development are built.
0 notes
Text
18/100
Hoy transcribí el módulo 10 de mi juego al código e ingresé un nuevo personaje.
Luego para boludear un rato y practicar javascript, empecé un mini proyecto de simular entrar a la computadora de alguien. Las fotos de la chica son generadas con IA.
Puedes checkearlo aqui (la contraseña inicial es password)
---
Today I transcribed module 10 of my game into code and entered a new character. He is called Vlad and is the first aid instructor in the game.
Just to fool around for a bit and to practice javascript, I started a mini project of pretending to break into someone's computer. The photos of the girl are generated with AI.
You can check it here (the password is literally "password")
#personal#diario#diary#blog#studyblr#codeblr#100 days of productivity#100dop#100 dias de productividad#100 dop#web development#web developers#web developing company#webdesign#programming#dearstalkerproject
1 note
·
View note
Note
Yo, a dumbass with no knowledge about programming here. You don't have to explain stuff if you don't wanna, but I am curious about the "there should not be apps, only websites" post.
While I get that some apps are at least more convenient than websites, others, especially for services that you likely won't use often, seem kind of pointless from user perspective. I think. But also I might just be used to how things were like 15-20 years ago.
I'd like to know why apps would be preferable to websites, and if there are exceptions to that?
The short answer: Native-run applications are much much more performant and better in almost every single way except for the fact that they need to be installed. They can access local resources and perform logic using native hardware that browsers can't to the same extent. They can do anything a web application can do, better, plus more. However, web applications are still very good at running snappy interfaces that only need to serve text and relatively small images dynamically. They're much easier and much cheaper to develop.
-
This is a little hard to talk about with big generalizations because there are so many different types of applications with different intents, and there's a huge spectrum of how reliant applications are on remote computing and data transfer. I can't cover every architecture here, so I'm thinking specifically mobile applications vs. modern web applications (not the Amazon, Youtube, and Netflix's of the world, they are engineering undertakings out of this scope).
First, the bad: There is a type of mobile application (that I think you were kind of hinting at) that is essentially there with the single purpose of serving you the company's website exactly as it can already be accessed through a browser. The only advantages to the user that I can really conceive of in this case is that it's a convenient bookmark on your home screen and that it can access your phone's password manager and native payment methods/services that require specific permissions. Big examples of this are access to your phone's camera and FaceID. Also, applications are much better at creating persistent sessions, meaning that they can keep you logged in without having to re-authenticate all the time. Beyond those specific cases, you could say these types of mobile apps are pretty useless.
However, as soon as you get into anything more complicated, the advantages of applications are huge. You can think of them as a phone's equivalent to a desktop application. I actually hate that many desktop applications are now re-packaged web applications similar to the above example. Think Notion. This means no or limited offline app use, which makes me irate. IMO saving files to server storage like with Fusion360 (a CAD program) should be an option, not the default.
Web architectures and browsers are hamstrung on purpose. They can't save files locally beyond specific cases like when caching and when a file is spit into your Downloads folder. This is to protect you. To offset the fact that web browsers can't do a lot on your end (among other reasons), when you use a web application like Google's translation app, the logic performing that translation is not done in the browser with Javascript, it's done server side, then sent back to you. This means that your computer is not actually performing that logic, and therefore all of this data (sometimes needed in real time) needs to be transferred over your network. Google makes this seamless with a lot of money and engineering work.
The expedient calculation and transfer of data is a huge consideration in Computer Science. Beyond companies just not wanting to store expensive files, this is a reason why social media sites, for example, have maximum image upload sizes. Even then, they compress assets on their end to make sure that someone scrolling through their timeline isn't an unmanageable mess because fetching large images takes so long. Pre-caching images and resources helps ensure the experience for the user is smooth and consistent, which is pivotal. Social media applications have the exact same problem because they're reliant on streaming data in the same way a web app is.
All this is to say, applications (meaning mobile applications) are just more performant than web applications. When you do your upfront download of an application, you're downloading logic engines and assets natively that are then loaded from your phone's hard storage into memory. The calculations that normally need to be offloaded to a cloud server can be performed locally. Local assets and phone-specific architectures mean snappier interfaces and much better quality assurance. This isn't to mention the baseline performance increases from using the Android and Apple developed SDKs (written in Java/Kotlin and Swift/Java/etc) to perform logic and render native user interfaces.
Browser side, things have gotten better recently with SPAs, or Single Page Applications. Have you ever noticed how the current version of Tumblr doesn't refresh the entire page when you click a navigation link? It uses a Single Page architecture so that it only has to serve content that needs to be refreshed as necessary. Companies like Adobe, who make very calculation-heavy applications, are pushing hard to enter the web space so that their apps can be more accessible to more (mobile) users. The reality is, the web apps are just not anywhere near as performant because they require offloading the logic to Adobe's servers, just like Google.
Overall, the difference of being able to perform logic client-side is huge. If your application needs to do any amount of image rendering, video streaming, 3D rendering, or image manipulation (like the Snapchat example lmao) it's just going to be better and faster in a natively run application, if it was even possible in browser in the first place.
This is why browser games are pretty limited. It's amazing what we can do in browser with webGL these days. Look at OnShape or Vention.io's online CAD. It's phenomenal. But those apps were created with the very specific purpose of needing to be browser-based for accessibility, and their desktop/installed counterparts are much more performant.
#this got long#but I hope it's at least somewhat illustrative#programming#comp sci#filing this alongside pictures of boys kissing
0 notes
Text
Step-by-Step Guide to Building a Custom CMS Web Development
Creating a custom Content Management System (CMS) is a powerful way to gain full control over your website's functionalities and user experience. Unlike generic CMS platforms, a custom CMS is tailored to meet specific business needs, offering unparalleled flexibility and scalability. This guide provides a detailed, step-by-step approach to building your own custom CMS from scratch.
Initial Planning and Research
Defining Project Goals and Requirements
The foundation of any successful project lies in clear and comprehensive planning. Begin by defining the primary goals of your CMS Web Development. What unique features do you need? How many users will the system support? Identify the essential requirements and prioritize them to ensure your development process remains focused and efficient.
Conducting Market and Technical Research
Conduct thorough market research to understand current CMS solutions and identify gaps that your custom CMS can fill. Technical research is equally important—investigate the latest web development trends, security practices, and performance optimization techniques to ensure your CMS is built on a solid technological foundation.
Technology Stack Selection
Front-end Technologies
Choose robust front-end technologies to create an intuitive and responsive user interface. Popular choices include HTML5, CSS3, and JavaScript frameworks such as React or Angular. These technologies enable the creation of dynamic and interactive web pages that enhance user experience.
Back-end Technologies
For the back-end, select technologies that provide a solid foundation for handling data and business logic. Frameworks like Node.js, Django, or Laravel are popular for their flexibility and scalability. Ensure that the chosen back-end technology aligns with your project requirements and team expertise.
Database Options
The database is the cornerstone of your CMS. Opt for a database system that supports scalability and performance. SQL databases like MySQL or PostgreSQL are reliable choices for structured data, while NoSQL databases like MongoDB are suitable for more flexible data models.
Designing the System Architecture
Database Schema Design
Designing an efficient database schema is crucial for data integrity and performance. Start by mapping out the data entities and their relationships. Use normalization techniques to reduce data redundancy and improve query performance. Tools like ER diagrams can help visualize the database structure.
Application Logic and Workflow
Define the core application logic and workflows that will drive your CMS. This includes user authentication, content creation, editing, and publishing workflows. A well-designed application logic ensures smooth interactions between different components of the system.
Development of Core Features
User Authentication and Authorization
Implementing a robust user authentication system is critical for security. Use secure hashing algorithms for password storage and consider multi-factor authentication for additional security. Define user roles and permissions to control access to various parts of the CMS.
Content Management and Editing Tools
Develop user-friendly content management and editing tools. Incorporate WYSIWYG editors to allow non-technical users to create and edit content easily. Ensure that the CMS supports rich media content, version control, and collaborative editing features.
Adding Advanced Functionalities
SEO and Performance Optimization
Integrate SEO tools to help users optimize their content for search engines. Features like meta tag management, URL customization, and keyword analysis can significantly improve search engine rankings. Additionally, implement performance optimization techniques such as caching and lazy loading to enhance user experience.
Integration with Third-Party Services
To extend the capabilities of your CMS, integrate with third-party services such as social media platforms, analytics tools, and payment gateways. These integrations can provide additional functionalities and improve the overall user experience.
Testing and Quality Assurance
Automated Testing
Automated testing ensures that your CMS functions correctly and efficiently. Write unit tests for individual components and end-to-end tests for complete workflows. Automated tests can quickly identify bugs and regressions, improving the reliability of your CMS.
User Acceptance Testing
User Acceptance Testing (UAT) involves real users testing the CMS to ensure it meets their needs and expectations. Collect feedback and make necessary adjustments to improve usability and functionality. UAT is a critical step to ensure that the CMS is user-friendly and effective.
Deployment and Maintenance
Setting Up the Production Environment
Deploying your CMS to a production environment requires careful planning. Choose a reliable hosting provider that offers the necessary resources and scalability. Configure the server environment to optimize performance and security. Consider using containerization tools like Docker to ensure consistent deployments.
Ongoing Maintenance and Security
Maintaining your CMS involves regular updates and security patches. Stay informed about new vulnerabilities and promptly apply security updates. Regularly update your technology stack to benefit from the latest features and performance improvements. Implement a robust backup strategy to ensure data can be restored in case of an incident.
Conclusion
Building a custom CMS is a complex but rewarding process. By following a systematic approach—from planning and research to development and maintenance—you can create a powerful, flexible, and secure CMS tailored to your specific needs. As technology evolves, staying updated with the latest trends and advancements in CMS development will keep your system at the forefront of innovation. A custom CMS provides the freedom to shape your website exactly as you envision, ensuring it meets both current and future demands.
0 notes