#Modern Cryptography
Explore tagged Tumblr posts
Text
Cryptology: The Science of Secrets
Cryptology, the study of codes and ciphers, has captivated me for years. It combines elements of mathematics, linguistics, and computer science, serving as a crucial part of secure communication in our increasingly digital world.
From ancient times, when messages were hidden through simple substitution ciphers, to modern encryption methods used to protect sensitive information, cryptology plays a vital role in safeguarding privacy and security.
As we delve into cryptology, we uncover the challenges of decoding messages, the history of famous codes, and the impact of cryptography on national security. It’s an intriguing field that highlights the importance of communication and the lengths we go to protect our secrets.
#Cryptology#Codes and Ciphers#Secure Communication#Cryptography#Mathematics and Language#Information Security#Codebreaking#History of Cryptology#Digital Privacy#Encrypted Messages#Modern Cryptography#Data Protection#Secret Codes#Linguistic Analysis#Cybersecurity#Historical Codes#Cryptographic Techniques#National Security#Code Theory#Intelligence Operations#today on tumblr#new blog
1 note
·
View note
Text
youtube
#contemporarymusic#conceptualart#graphic score#drawing#pictorial music#contemporary art#contemporary music#noise music#dadaism#dada#noise#pictograms#music#notation#graphic notation#composition#composing#cryptogram#cryptography#sound art#prepared instrument#avantgarde#electroacoustic music#electroacoustic#experimental music#contemporary#modern music#musique concrete#Youtube
4 notes
·
View notes
Text
funny things to do with a quantum computer:
* typosquat onion sites
* mitm a bank to replace people's balances with output from `fortune`
* forge signed emails from linus torvalds asking people if their refrigerators are running
* push forged commits that cause commit hash collisions in important git repos (what will happen? no one knows)
* sign ports of chromium os for all of the proprietary devices with locked down bootloaders, so people can technically install third-party operating systems, but only the worst one
0 notes
Text
Quantum Mechanics in Modern Technology: The Science Explained
Introduction
Welcome to TechtoIO! Today, we explore the intriguing world of quantum mechanics and its profound impact on modern technology. Quantum mechanics, once a purely theoretical field, is now driving innovations that are transforming industries. But what exactly is quantum mechanics, and how is it applied in today’s tech? Let’s break down the science behind this fascinating topic. Read to continue
#CategoriesScience Explained#Tagschallenges in quantum technology#entanglement in quantum mechanics#future of quantum mechanics#lasers and quantum mechanics#LEDs and quantum mechanics#modern technology#MRI and quantum mechanics#photovoltaics and quantum mechanics#quantum computing#quantum cryptography#quantum mechanics#quantum sensors#quantum teleportation#science of quantum mechanics#semiconductors and quantum mechanics#superposition in quantum mechanics#transistors and quantum mechanics#uncertainty principle#wave-particle duality#Technology#Science#business tech#Adobe cloud#Trends#Nvidia Drive#Analysis#Tech news#Science updates#Digital advancements
1 note
·
View note
Text

Robert Ormerod Preusser
Cryptography
1959
#robert ormerod preusser#preusser#robert preusser#modern art#american art#abstract#abstract painting#abstract art#texas artist#abstraction#cryptography
0 notes
Text
the reason wizards aren't into cryptography and shit anymore is because of tiktok & cocomelon. embedding your mystery teachings in a 5,000 word substack article renders it as inaccessible to the modern reader as an alchemical rebus written backwards and upside-down in aramaic. you only get into trouble if you can argue your heresies in under 240 characters, in which case they're probably not even worth persecuting in the first place.
732 notes
·
View notes
Text
Bad Batch modern AU where the brothers take Omega to a fanily fun center for her 13th birthday
Crosshair is playing laser tag sniping kids from a hideout perch
Wrecker and Tech are in an escape room where Tech spends 10 minutes solving a complicated cryptography sequence and Wrecker gets impatient and rips the whole puzzle off the wall
Echo and Hunter are in the pizza party room getting their nails painted by a bunch of preteen girls
#TBB#the bad batch#Star Wars#tbb crosshair#tbb hunter#tbb tech#tbb wrecker#tbb echo#tbb omega#sw tbb
90 notes
·
View notes
Text
TIMOTHY SNYDER
APR 19
READ IN APP
Thirty years ago today, I was driving a moving van across the country, from the west coast to the east. The hold was packed well; the ride was wobbly, and I kept the heavy vehicle between the lines, mile after mile. Driving carefully, I was surprised to be stopped by state troopers. When I rolled down the window to face some polite questioning, I didn’t know that Timothy McVeigh had bombed the Murrah Federal Building in Oklahoma City, killing 168 people and injuring 684 more.
In the days that followed, the horror was treated for what it was: an attack by a racist, right-wing anti-government terrorist. I worry now that, thirty years on, a similar attack is very likely, and would have a different outcome. I don't want us to be more frightened than we should be. But I do want us to be ready, so that a moment of predictable shock does not become a lifetime of avoidable subjugation.
As I will try to show, the present government invites a terror attack. Most of the people directing the relevant agencies are incompetent; the next few layers down have been purged in culture wars; much the remaining personnel have resigned, been fired, or are demoralized; resources have been diverted away from terror prevention; Americans has been distracted by fiction and chaos; and potential attackers have been encouraged.
And so we have to think — now — about what would follow such an attack. Musk, Trump, Vance, and the rest would try to exploit the moment to undo remaining American freedoms. Let me cite Lesson 18 of On Tyranny.
18. Be calm when the unthinkable arrives. Modern tyranny is terror management. When the terrorist attack comes, remember that authoritarians exploit such events in order to consolidate power. The sudden disaster that requires the end of checks and balances, the dissolution of opposition parties, the suspension of freedom of expression, the right to a fair trial, and so on, is the oldest trick in the Hitlerian book. Do not fall for it.
In just three months, the Trump people have made the unthinkable much more likely. They have created the conditions for terrorism, and thus for terror management. This is true at several levels.
Most obviously, they have debilitated the services that detect terrorist threats and prevent attacks: the Central Intelligence Agency (CIA), the Federal Bureau of Investigation (FBI), the Department of Homeland Security (DHS), and the National Security Agency (NSA). The CIA is a foreign intelligence service. The FBI is the federal police force. The NSA, which specializes in cryptography and foreign signals intelligence, is part of the Department of Defense. Homeland Security is a cabinet-level department that amalgamates a number of functions from immigration control through disaster relief and anti-terrorism.
Overall guidance over the intelligence agencies is exercised by Tulsi Gabbard, who is known as an apologist for the now-overthrown Assad regime in Syria and the Putin regime in Russia. The director of the FBI is Kash Patel, an author of children's books that promote conspiracy theories, and a recipient of payments from sources linked to Russia. Patel plans to run the agency from Las Vegas, where he resides in the home of a Republican megadonor. The deputy director of the FBI is Dan Bongino, a right-wing entertainer who has called the FBI "irredeemable corrupt" and indulged in conspiracy theories about its special agents. He now draws FBI special agents away from their usual duties to serve as a personal bodyguard. The director of Homeland Security is Kristi Noem, who lacks relevant expertise.
Noem has distinguished herself by posing in front of a cell full of prisoners in El Salvador. Homeland Security is focused on spectacular abductions at the expense of its other missions. Its programs to prevent terrorism have been defunded, and it is no longer keeping up its database on domestic terrorism. As one insider put it: “The vibe is: How to use DHS to go after migrants, immigrants. That is the vibe, that is the only vibe, there is no other vibe. It’s wild — it’s as if the rest of the department doesn’t exist.” The obsession with migrants means that local law enforcement, all across the country, is being in effect federalized in the service of an objective that is essentially irrelevant to core missions. That, too, makes life easier for aspiring terrorists.
The National Security Agency sits within the Department of Defense, which is run by Pete Hegseth, a right-wing entertainer and culture warrior. He has fired people who were qualified, and is unable to keep even his own people at work — he just lost four staffers in one day. The “meltdown” at the top of the Pentagon bodes ill.
The leadership of the NSA itself was recently changed, under bizarre and troubling circumstances. After a meeting with conspiracy theorist Laura Loomer, Trump fired the NSA director, General Timothy Haugh. Wendy Noble, the deputy director, was also fired. This decapitation was part of a larger set of firings initiated by Loomer. It takes place during an ongoing purge of military leaders and national security officials. From the perspective of potential attackers, the culture wars mean vulnerability.
Meanwhile, other Department of Defense agencies that are central to the twenty-first century security of the United States, such as the Defense Digital Service, are destroyed by Elon Musk’s DOGE. It is worth contemplating the reaction of a former Pentagon official: “They’re not really using AI, they’re not really driving efficiency. What they’re doing is smashing everything.” In general, the penetration of the federal government by DOGE has weakened its functions, and likely made critical data available to adversaries who wish to hurt Americans.
The rank and file of the critical institutions are subjected to administrative hostility and chaos. The names of active CIA officers have been sent on open emails to the White House, and in a Signal chat in which a reporter was included. CIA employees have been urged to take early retirement. CIA officers involved in any way in diversity recruitment have been fired (a judge has blocked this, for the time being).
FBI special agents have been exposed to similar indignities. Top FBI officials have been pressured to resign and have done so. Musk-Trump is pursuingFBI special agents who were involved in prosecutions of people who stormed the Capitol on January 6th 2021. Patel proposes that special agents be trained by a company that promotes commercial fights that is based in Las Vegas. Sending FBI special agents to Nevada to simulate Fight Club for Patel’s personal delectation is not going to keep Americans safe.
The Musk-Trump people run national security, intelligence, and law enforcement like a television show. The entire operation of forcible rendition of migrants to a Salvadoran concentration camp was based upon lies. It is not just that Kilmar Abgrego Garcia was mistakenly apprehended. The entire thing was made for television. Its point was the creation of the fascist videos. But this is a media strategy, meant to frighten Americans. And a media strategy does not stop actual terrorists. It summons them.
Terrorism is a real risk in the real world. The constant use of the word to denote unreal threats creates unreality. And unreality inside ket institutions degrades capability. Security agencies that have been trained to follow political instructions about imaginary threats do not investigate actual threats. Fiction is dangerous. Treating the administration’s abduction of a legal permanent resident as a heroic defense against terror is not only mendacious and unconstitutional but also dangerous.
Moreover, Musk-Trump make the United States look vulnerable. Americans under the spell of Trump’s or Musk’s charisma might imagine that strength is being projected. Not so. To prospective terrorists we look erratic and weak. Even apparently unrelated policies — such as enabling foreign disinformation, gutting environmental protection, undoing weather forecasting, ending food inspections, and undermining disease control — make life easier for terrorists and open avenues of attack. By taking apart the government, crashing the economy, and dividing the population, Musk and Trump invite attention of the worst sort, from people who wish to hurt Americans.
Who are such people? Three possible groups of perpetrators of a major terrorist attack in the United States are native right-wing nationalists or white supremacists (“domestic violent extremists”), Islamicists, and Russians.
Most terrorism in the United States is domestic, and most of the domestic terror comes from the far right. We have recently seen a series of white supremacist killings. Cody Balmer, who wanted to kill Pennsylvania’s (Democratic, Jewish) governor, wrote that “Biden supporters should not exist.”
It might seem counter-intuitive that the far right would carry out acts of terror under Trump, but this is already the norm, and there are good reasons to expect worse. Musk pushes the story that civil servants deserve pain. The most lethal domestic terror attack in US history, McVeigh’s bombing, was directed against federal workers. Right-wing terrorists might believe that terror is what Trump wants. The suspect in the recent Florida mass shooting “advocated for President Donald Trump's agenda and often promoted white supremacist values,” according to someone who saw him regularly. Trump has long practiced stochastic violence. His pardon of the January 6th criminals encourages terror with the promise of forgiveness. Patel promoted a recording of the January 6 criminals singing the national anthem. This coddling culture of martryrdom makes more killing more likely.
There is also another scenario. Far right movements can divide, with the more impatient angry with those they see as compromised. This is a lessonfrom the history of fascism. Some supporters of Trump will be disappointed with him. The assassination attempt on Trump was carried out by someone whose social media posts conveyed hatred of Jews and immigrants. Bongino now has to contend with fans of his show who think that the January 6th criminals should be running the FBI.

The Murrah Federal Building, Oklahoma City, 19 April 1995
And our guard has been dropped. Even at the best of times, the FBI has generally had trouble articulating the centrality of domestic right-wing terrorism. Now the risk is denied. High officials of Musk-Trump tend to sharethe views of right-wing nationalists, which makes it less likely that they will be seen as a threat. Under Patel, the FBI will deprioritize this important area of investigation. In keeping with his and Noem’s priorities, FBI agents have been assigned away from domestic terrorism. Thus far, the main "terrorist" threat seen by Trump-Musk are protestors in front of Tesla dealerships. Diverting attention to parking lots will not keep Americans safe.
Musk-Trump are also generating scenarios for Islamicist terror. A motivation for Islamicist terrorists is contention over territory in the Middle East. The Trump administration advocates the ethnic cleansing of the entire (surviving) population of Gaza. The US armed forces are also firing ordnance into Yemen with the announced goal of "annihilating" the Houthis who hold power. In a Signal group chat, top national security officials rejoiced (with emojis) over a strike in which a building collapsed. It seems unclear that Musk-Trump will have accounted for the related terrorism risk.
Russia is now a risk in a way that it was not before. It has special units that carry out acts of destruction abroad, such as assassinations and sabotage. In the last three years, these operations have accelerated inside Europe, and include blowing up military sites. Russia also pays people inside other countries to carry out acts of terror and sabotage. Russia has been carrying out cyber attacks inside the United States for years.
Before Musk-Trump, the United States had been fastidious about including Russia as a possible source of foreign terror. Now Russia is presented as an ally and Putin as a friend; intelligence and defense work designed to monitor Russian sabotage inside the United States have been scaled back, as has tracking of Russian war crimes in Ukraine and public reporting on Russia. Gabbard, the director of national intelligence, rationalizes Russian aggression. Patel, the FBI director, owes his career to the claim that people who (truthfully) speak of Russian operations inside the United States are carrying out a hoax. Trump’s nominee for US district attorney for Washington, DC, is a media star in Russia.
This is all beyond the wildest dreams of the Kremlin. The Putinism on display in the federal government creates an atmosphere in which a Russian operation inside the United States would be much easier.
It is not hard to see what Russia would gain from a false-flag terror attack on American territory. Moscow would be seeking to weaken the United States, and by generating a response from Musk-Trump that suits Russia. Having Trump blame his enemies for what was in fact a Russian attack is in the interest of the Russian Federation.
Other actors than these three are also possible. I fear, though, that whether I am right or wrong about the specific source, there can be no doubt that we are far more vulnerable than we were three months ago. And any major attack, regardless of origin, would lead to the same kind terror management. The people in the White House have no governing skills, but they do have entertainment skills. They will seek to transform themselves from the villains of the story to the heroes, and in the process bring down the republic. Please indulge me if I ask you to consider Lesson 18 again.
18. Be calm when the unthinkable arrives. Modern tyranny is terror management. When the terrorist attack comes, remember that authoritarians exploit such events in order to consolidate power. The sudden disaster that requires the end of checks and balances, the dissolution of opposition parties, the suspension of freedom of expression, the right to a fair trial, and so on, is the oldest trick in the Hitlerian book.��Do not fall for it.
20 lessons, read by John Lithgow
That lesson arises from two notorious twentieth-century examples: the Reichstag Fire in Germany in 1933, which Hitler used to declare a state of emergency, and the Kirov assassination in the Soviet Union in 1934, which Stalin used as an excuse to expand terror. In both cases, it is the reactionthat we remember, rather than the event itself.
I wish that terrorist attacks were a moment when government could be trusted. But the temptation, for any government, is to take the shock and to divert it in a convenient direction. And the temptation, for us, is to imagine that our leaders will rise to the occasion. After 9/11, I listened to President Bush address the nation, sitting in my pickup, on the driveway outside a friend’s house. Though my own politics were very different, I remember the pull inside me, the wish to believe that he would do the right thing. I didn’t let myself believe anything of the sort, but I remember the feeling: and it is that tug that we cannot let get the best of us.
Our present government would be the last to resist the temptation to exploit terror. Musk-Trump would, I fear, make little if any attempt to apprehend the responsible people, especially if they are Americans or Russians. They might blame the Democratic Party, or Americans they hate for other reasons, or the opposition generally, or Canadians or Ukrainians or other Europeans. They will likely try to put an end to the American republic.
This is the critical moment when we must prevent ourselves from going along.
I do not relish describing this chain of events. But the only way to cut the chain it is to see the links. And when we can imagine that we ourselves have the power to cut the links, as we do, we can also imagine ourselves more free.
History teaches us how terrorist attacks are exploited. Our advantage is that we know this history, and so react sensibly. Do not give the present regime the benefit of the doubt after it allows a terrorist attack to take place on American soil. Be skeptical about its account of who is to blame. Insist that Musk-Trump take responsibility. And understand that freedom is the first condition of security. A terrorist attack is no reason to concede anything to this regime. On the contrary: such a failure by Musk-Trump would be one more reason, and a very powerful one, to resist it.
Throughout history, and around the world right now, government indifference and incompetence that leads to civilians deaths has been seen as a reason for protest.
The night before I was stopped by the police, I had been driving that truck through water. It was a time of high rain in the central United States. Highways were flooded.
In the pre-revolutionary France of the eighteenth century, decadent rulers said “après nous, le déluge” — “after us, the flood.” We care not at all about the consequences of our actions; we are here to profit so long as we can. This is the attitude of Musk, Trump, and the rest. They are in it for themselves, provoking disasters for the rest of us along the way.
A few days before that drive began, I finished my doctoral dissertation, about revolutions, based on research in post-communist Poland. One of my supervisors was the the British historian Timothy Garton Ash. Considering the task of Poland’s new democratic government, he reversed the formula of French royalty, writing: “après le deluge, nous.”
After the flood, we remain. The disaster brought by the decadent is part of the story. But it is not the conclusion. It is what we do next that matters.
22 notes
·
View notes
Text
Tales Of Crystals
Hey in the early 90s Hasbro put out a tabletop roleplaying larp for tween girls called Tales Of The Crystals, and there's a lot going on here, so I want to talk about it.
First, I want to give credit to @riseupcomus on twitter for doing a thread on it first. Riseup's thread is linked at the bottom, right after hasbro's pdf of Tales Of Crystals.
Now, what is Tales Of Crystals? Well, it's a journaling game. And it's an indie TTRPG. And it's a larp kit. And it's an audio game. And it's a cryptography kit.
It comes with its own map, rulebook, a cassette tape with multiple scenarios, a non-dice-based resolution system, four player roles, and a ruleset that's split up so that each of the four players is in charge of a different part.
If feels like a high concept, big swing indie title from 2024, but it's got thirty years worth of jump on the modern scene.
The basic premise is that the players are crystal bearers in the court of a fantasy kingdom, and there's an evil nation in the goblin swamp next door, and they have to guard the nation against treachery and ensorcellment and whatnot. It's not super duper fresh, but with how many things the game is juggling it's extremely reasonable that the plot's a little plain.
Each player's crystal comes with a power, and the powers are asymmetrical. The Leader gets the Crystal Of Shimmering Ice, which lets you oneshot enemies (nonlethally, by freezing them for a minute.) The Protector gets the Crystal Of True Sight, and can see through all lies and enchantments and mind control enemies for a minute (tbh this one is just better). There's a healing crystal and an invisibility crystal as well---and interestingly the invisibility crystal is given to the role responsible for journaling everybody's adventures. The game recognizes that at least one player of a fantasy larp for tween girls in the 90s is probably going to be a wallflower writer, and deliberately enshrines that role.
Tales Of Crystals has a solid core loop, with a deck of cards for prompts and a cassette tape for scenarios and a little circle with YES and NO marked on it that you can scatter your gems onto to get oracle answers to questions during play. It also has a LOT of gimmicks.
There's a tube of powder you can sprinkle on things to disenchant them. There's a mirror you need to read script that's been written backwards. There's three cryptographic cyphers at the back of the book. There's a box specifically for confining the evil Spider Crystal (after you've sprinkled it with powder to neutralize it.) This is a game of dozens of components, and it's a miracle the design is so tight that they all loop together so well.
Now, I don't have sales data (riseup might,) but I suspect maybe this thing didn't sell amazingly. It requires you to set up six or so distinct locations around your yard, pretty much needs a group of exactly four friends to play it, requires you to give clue elements to your parents---you'd have to be cool with it, your friends would have to be cool with it, your parents would have to be cool with it, and you'd have to have a big suburban yard in order to get a proper intended game experience. That said, its larp design is really stable, its gameplay is carefully thought out, and it includes a section at the start to encourage you to play safely and a section at the end to talk about your game together, journal your experiences, and to clean up the game components as a group when you're done.
This is good tech! And it even specifically recommends having a snack and relaxing afterward.
Tales Of Crystals doesn't use terms like bleed and session zero, but it's a good ways ahead of the curve on larp and ttrpg safety.
I didn't find the designer's name (they're listed as uncredit on BoardGameGeek, not mentioned in the PDF, and missing from the wiki page,) but they knocked this one out of the park. There's stuff in here that modern indie ttrpg designers could learn from---myself very much included.
So if you like ttrpgs, 90s magic, and stuff like Tamora Pierce and Sailor Moon, give riseup's original thread a look, and definitely check out the PDF link.
I'm thrilled this thing exists, and I hope more designers get to look at it.
#ttrpg#ttrpg homebrew#ttrpgs#ttrpg design#indie ttrpgs#rpg#indie ttrpg#tabletop#dnd#rpgs#tales of crystals#larp
120 notes
·
View notes
Text
Rebecca Roque’s “Till Human Voices Wake Us”

I'm touring my new, nationally bestselling novel The Bezzle! Catch me in TOMORROW (Apr 17) in CHICAGO, then Torino (Apr 21) Marin County (Apr 27), Winnipeg (May 2), Calgary (May 3), Vancouver (May 4), and beyond!

"Till Human Voices Wake Us" is Rebecca Roque's debut novel: it's a superb teen thriller, intricately plotted and brilliantly executed, packed with imaginative technological turns that amp up the tension and suspense:
https://www.blackstonepublishing.com/till-human-voices-wake-us-gn3a.html#541=2790108
Modern technology presents a serious problem for a thriller writer. Once characters can call or text one another, a whole portfolio of suspense-building gimmicks – like the high-speed race across town – just stop working. For years, thriller writers contrived implausible – but narratively convenient – ways to go on using these tropes. Think of the shopworn "damn, my phone is out of battery/range just when I need it the most":
https://www.youtube.com/watch?v=XIZVcRccCx0
When that fails, often writers just lean into the "idiot plot" – a plot that only works because the characters are acting like idiots:
https://en.wikipedia.org/wiki/Idiot_plot
But even as technology was sawing a hole in the suspense writer's bag of tricks, shrewd suspense writers were cooking up a whole new menu of clever ways to build suspense in ways that turn on the limitations and capabilities of technology. One pioneer of this was Iain M Banks (RIP), whose 2003 novel Dead Air was jammed with wildly ingenious ways to use cellphones to raise the stakes and heighten the tension:
https://web.archive.org/web/20030302073539/http://www.wired.com/wired/archive/11.03/play.html?pg=8
This is "techno-realism" at its best. It's my favorite mode of storytelling, the thing I lean into with my Little Brother and Martin Hench books – stories that treat the things that technology can and can't do as features, not bugs. Rather than having the hacker "crack the mainframe's cryptography in 20 minutes when everyone swears it can't be done in less than 25," the techno-realist introduces something gnarlier, like a supply-chain attack that inserts a back-door, or a hardware keylogger, or a Remote Access Trojan.
Back to Roque's debut novel: it's a teen murder mystery told in the most technorealist way. Cia's best friend Alice has been trying to find her missing boyfriend for months, and in her investigation, she's discovered their small town's dark secret – a string of disappearances, deaths and fires that are the hidden backdrop to the town's out-of-control addiction problem.
Alice has something to tell Cia, something about the fire that orphaned her and cost her one leg when she was only five years old, but Cia refuses to hear it. Instead, they have a blazing fight, and part ways. It's the last time Cia and Alice ever see each other: that night, Alice kills herself.
Or does she? Cia is convinced that Alice has been murdered, and that her murder is connected to the drug- and death-epidemic that's ravaging their town. As Cia and her friends seek to discover the town's secret – and the identity of Alice's killer – we're dragged into an intense, gripping murder mystery/conspiracy story that is full of surprises and reversals, each more fiendishly clever than the last.
But as good as the storytelling, the characterization and the mystery are, Roque's clever technological gambits are even better. This book is a master-class in how a murder mystery can work in the age of social media and ubiquitous mobile devices. It's the first volume in a trilogy and it ends on a hell of a cliff-hanger, too.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/04/16/dead-air/#technorealism
80 notes
·
View notes
Text
On Accepting Victories Where They Come
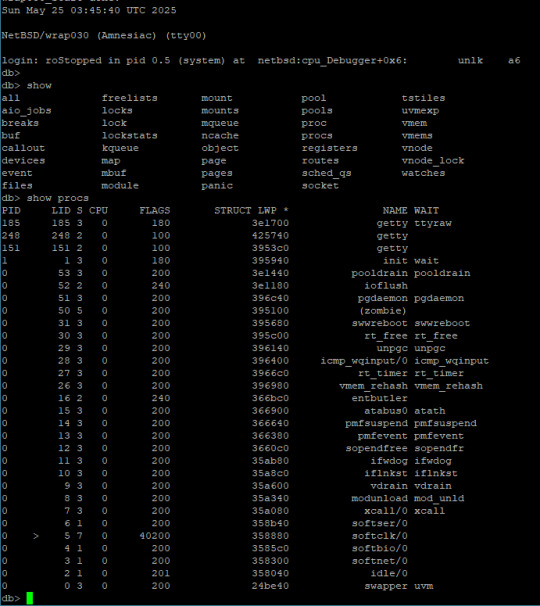
At the end of my last post on getting NetBSD running on my 68030 homebrew computer, I had a (mostly) working root shell prompt in single-user mode.
Well here we are a week or so later and I have ... a (mostly) working root shell prompt in single-user mode.
It turns out bringing up a modern operating system is hard.
The first problem was the default collection of init scripts. There are a ton of scripts in /etc/rc.d that are run at startup to finish bringing up the system after the kernel is loaded but before users can log in. These scripts do things like check filesystem integrity, mount disks, initialize networking, etc. Most of the scripts are not relevant to my specific hardware, but I wasn't even getting far enough along for that to matter. I was getting stuck early on in two steps in particular: filesystem checks and initializing /dev/random.
The latter issue there's not really anything I can do about. I can copy a pre-populated entropy file from an existing system, but I don't have the hardware support for random number generation. Frankly I don't need it either, if I'm not doing anything with cryptography like using TLS certificates. So remove that script.
I can check and repair the filesystem much faster on my host machine, so remove that script for now also.
And remove all of those networking-related scripts since I don't have the hardware for networking either.
…
It turns out init scripts have declared dependencies on other scripts. So removing one, especially an early important one like checking filesystem, means editing others to continue without it. It's dependency hell.
So for the sake of just getting things running, I removed everything and wrote my own. There were just a few things I really needed, like mounting the root filesystem as writeable and initializing TTYs.
It took a few tries to get it right, but my init script did eventually run without stalling. This was it, time for it to initialize the terminals and print the login prompt …
init: can't add utmpx record for 'tty01': Bad file descriptor
… That's not a login prompt. That's not a login prompt at all. What does that even mean? What on earth is utmpx?
The error message itself is printed by init. UTMPX keeps record of logged-in users, and it does so using a file, /var/run/utmpx. But is the bad file descriptor error relating to that file or to /dev/tty01?
I was stuck here for a while. I tried everything I could think of to make sure my tty devices were created properly and with the right major/minor numbers and permissions. I finally realized that I didn't get the error if the utmpx file didn't exist. So something was wrong with writing the file, possibly due to never being able to properly shut down and close out the file & filesystem any time it got created. But it's easy enough to just make sure it's deleted by the init script before getting to that point.
It's at this point where I went down a rabbit hole of trying to create a RAM disk for root just to eliminate the possibility of lingering problems with the ATA driver or similar. This proved to be a dead end because the system would only boot single-user from a RAM disk, and I also got stuck in dependency hell trying to get it to compile a RAM disk image that included the actual login binary.
After some more experimentation, I learned that if I had no extra terminals defined in /dev/ttys, then it would at least show the login prompt on the root console, but would never actually log in. Kernel debugger & SIGINFO would show that login was stuck waiting for something. If I did have multiple terminals defined, I would never see a login prompt and it would show that getty, which spawns the terminals, was sleeping, waiting for something.
And that's where I'm stuck. I have no idea what these programs are waiting on, and don't really have any way to check. I suspect it's possible they need those hardware interrupts I don't have, but since I can see activity on the UART chip select lines, I don't think that's the case.
So for now, facing a looming deadline and burnout setting in after a solid month of working on this, I've decided to accept the victory I have and admit defeat where I must. I have a computer that I built myself which can load and run a modern operating system up to the point of a root shell prompt. That is a remarkable accomplishment and I will absolutely accept that victory. There is already so much the machine is capable of just getting to that point. And going from knowing nothing about porting an OS to a new machine to having a running shell in under a month is a victory all on its own.
But, I was not able to get it fully running in multi-user mode on all of my terminals. I will happily accept that defeat in light of the major victory of getting as far as I have.
So, with VCFSW coming up very soon, I've decided to turn my attention back to my multi-user BASIC system. I have a few refinements and new features in mind that I would love to have ready by the show.
#homebrew computing#mc68030#motorola 68k#motorola 68030#debugging#vcfsw#wrap030#vcf#Retrocomputing#NetBSD#homebrew computer
18 notes
·
View notes
Text
#noise music#dadaism#dada#noise#notation#graphic notation#composition#composing#cryptogram#cryptography#sound art#prepared instrument#avantgarde#electroacoustic music#electroacoustic#experimental music#contemporary#modern music#musique concrete#oldphoto#vintagephotography#RetroPhotography#film photography#electronic music#audiovisual#visual#visualart#videocollage#double exposure#collage art
1 note
·
View note
Text
Thirty years ago today, I was driving a moving van across the country, from the west coast to the east. The hold was packed well; the ride was wobbly, and I kept the heavy vehicle between the lines, mile after mile. Driving carefully, I was surprised to be stopped by state troopers. When I rolled down the window to face some polite questioning, I didn’t know that Timothy McVeigh had bombed the Murrah Federal Building in Oklahoma City, killing 168 people and injuring 684 more.
In the days that followed, the horror was treated for what it was: an attack by a racist, right-wing anti-government terrorist. I worry now that, thirty years on, a similar attack is very likely, and would have a different outcome. I don't want us to be more frightened than we should be. But I do want us to be ready, so that a moment of predictable shock does not become a lifetime of avoidable subjugation.
As I will try to show, the present government invites a terror attack. Most of the people directing the relevant agencies are incompetent; the next few layers down have been purged in culture wars; much the remaining personnel have resigned, been fired, or are demoralized; resources have been diverted away from terror prevention; Americans has been distracted by fiction and chaos; and potential attackers have been encouraged.
And so we have to think — now — about what would follow such an attack. Musk, Trump, Vance, and the rest would try to exploit the moment to undo remaining American freedoms. Let me cite Lesson 18 of On Tyranny.
18. Be calm when the unthinkable arrives. Modern tyranny is terror management. When the terrorist attack comes, remember that authoritarians exploit such events in order to consolidate power. The sudden disaster that requires the end of checks and balances, the dissolution of opposition parties, the suspension of freedom of expression, the right to a fair trial, and so on, is the oldest trick in the Hitlerian book. Do not fall for it.
In just three months, the Trump people have made the unthinkable much more likely. They have created the conditions for terrorism, and thus for terror management. This is true at several levels.
Most obviously, they have debilitated the services that detect terrorist threats and prevent attacks: the Central Intelligence Agency (CIA), the Federal Bureau of Investigation (FBI), the Department of Homeland Security (DHS), and the National Security Agency (NSA). The CIA is a foreign intelligence service. The FBI is the federal police force. The NSA, which specializes in cryptography and foreign signals intelligence, is part of the Department of Defense. Homeland Security is a cabinet-level department that amalgamates a number of functions from immigration control through disaster relief and anti-terrorism.
Overall guidance over the intelligence agencies is exercised by Tulsi Gabbard, who is known as an apologist for the now-overthrown Assad regime in Syria and the Putin regime in Russia. The director of the FBI is Kash Patel, an author of children's books that promote conspiracy theories, and a recipient of payments from sources linked to Russia. Patel plans to run the agency from Las Vegas, where he resides in the home of a Republican megadonor. The deputy director of the FBI is Dan Bongino, a right-wing entertainer who has called the FBI "irredeemable corrupt" and indulged in conspiracy theories about its special agents. He now draws FBI special agents away from their usual duties to serve as a personal bodyguard. The director of Homeland Security is Kristi Noem, who lacks relevant expertise.
Noem has distinguished herself by posing in front of a cell full of prisoners in El Salvador. Homeland Security is focused on spectacular abductions at the expense of its other missions. Its programs to prevent terrorism have been defunded, and it is no longer keeping up its database on domestic terrorism. As one insider put it: “The vibe is: How to use DHS to go after migrants, immigrants. That is the vibe, that is the only vibe, there is no other vibe. It’s wild — it’s as if the rest of the department doesn’t exist.” The obsession with migrants means that local law enforcement, all across the country, is being in effect federalized in the service of an objective that is essentially irrelevant to core missions. That, too, makes life easier for aspiring terrorists.
The National Security Agency sits within the Department of Defense, which is run by Pete Hegseth, a right-wing entertainer and culture warrior. He has fired people who were qualified, and is unable to keep even his own people at work — he just lost four staffers in one day. The “meltdown” at the top of the Pentagon bodes ill.
The leadership of the NSA itself was recently changed, under bizarre and troubling circumstances. After a meeting with conspiracy theorist Laura Loomer, Trump fired the NSA director, General Timothy Haugh. Wendy Noble, the deputy director, was also fired. This decapitation was part of a larger set of firings initiated by Loomer. It takes place during an ongoing purge of military leaders and national security officials. From the perspective of potential attackers, the culture wars mean vulnerability.
Meanwhile, other Department of Defense agencies that are central to the twenty-first century security of the United States, such as the Defense Digital Service, are destroyed by Elon Musk’s DOGE. It is worth contemplating the reaction of a former Pentagon official: “They’re not really using AI, they’re not really driving efficiency. What they’re doing is smashing everything.” In general, the penetration of the federal government by DOGE has weakened its functions, and likely made critical data available to adversaries who wish to hurt Americans.
The rank and file of the critical institutions are subjected to administrative hostility and chaos. The names of active CIA officers have been sent on open emails to the White House, and in a Signal chat in which a reporter was included. CIA employees have been urged to take early retirement. CIA officers involved in any way in diversity recruitment have been fired (a judge has blocked this, for the time being).
FBI special agents have been exposed to similar indignities. Top FBI officials have been pressured to resign and have done so. Musk-Trump is pursuing FBI special agents who were involved in prosecutions of people who stormed the Capitol on January 6th 2021. Patel proposes that special agents be trained by a company that promotes commercial fights that is based in Las Vegas. Sending FBI special agents to Nevada to simulate Fight Club for Patel’s personal delectation is not going to keep Americans safe.
The Musk-Trump people run national security, intelligence, and law enforcement like a television show. The entire operation of forcible rendition of migrants to a Salvadoran concentration camp was based upon lies. It is not just that Kilmar Abrego Garcia was mistakenly apprehended. The entire thing was made for television. Its point was the creation of the fascist videos. But this is a media strategy, meant to frighten Americans. And a media strategy does not stop actual terrorists. It summons them.
Terrorism is a real risk in the real world. The constant use of the word to denote unreal threats creates unreality. And unreality inside ket institutions degrades capability. Security agencies that have been trained to follow political instructions about imaginary threats do not investigate actual threats. Fiction is dangerous. Treating the administration’s abduction of a legal permanent resident as a heroic defense against terror is not only mendacious and unconstitutional but also dangerous.
Moreover, Musk-Trump make the United States look vulnerable. Americans under the spell of Trump’s or Musk’s charisma might imagine that strength is being projected. Not so. To prospective terrorists we look erratic and weak. Even apparently unrelated policies — such as enabling foreign disinformation, gutting environmental protection, undoing weather forecasting, ending food inspections, and undermining disease control — make life easier for terrorists and open avenues of attack. By taking apart the government, crashing the economy, and dividing the population, Musk and Trump invite attention of the worst sort, from people who wish to hurt Americans.
Who are such people? Three possible groups of perpetrators of a major terrorist attack in the United States are native right-wing nationalists or white supremacists (“domestic violent extremists”), Islamicists, and Russians.
Most terrorism in the United States is domestic, and most of the domestic terror comes from the far right. We have recently seen a series of white supremacist killings. Cody Balmer, who wanted to kill Pennsylvania’s (Democratic, Jewish) governor, wrote that “Biden supporters should not exist.”
It might seem counter-intuitive that the far right would carry out acts of terror under Trump, but this is already the norm, and there are good reasons to expect worse. Musk pushes the story that civil servants deserve pain. The most lethal domestic terror attack in US history, McVeigh’s bombing, was directed against federal workers. Right-wing terrorists might believe that terror is what Trump wants. The suspect in the recent Florida mass shooting “advocated for President Donald Trump's agenda and often promoted white supremacist values,” according to someone who saw him regularly. Trump has long practiced stochastic violence. His pardon of the January 6th criminals encourages terror with the promise of forgiveness. Patel promoted a recording of the January 6 criminals singing the national anthem. This coddling culture of martryrdom makes more killing more likely.
There is also another scenario. Far right movements can divide, with the more impatient angry with those they see as compromised. This is a lesson from the history of fascism. Some supporters of Trump will be disappointed with him. The assassination attempt on Trump was carried out by someone whose social media posts conveyed hatred of Jews and immigrants. Bongino now has to contend with fans of his show who think that the January 6th criminals should be running the FBI.
And our guard has been dropped. Even at the best of times, the FBI has generally had trouble articulating the centrality of domestic right-wing terrorism. Now the risk is denied. High officials of Musk-Trump tend to share the views of right-wing nationalists, which makes it less likely that they will be seen as a threat. Under Patel, the FBI will deprioritize this important area of investigation. In keeping with his and Noem’s priorities, FBI agents have been assigned away from domestic terrorism. Thus far, the main "terrorist" threat seen by Trump-Musk are protestors in front of Tesla dealerships. Diverting attention to parking lots will not keep Americans safe.
Musk-Trump are also generating scenarios for Islamicist terror. A motivation for Islamicist terrorists is contention over territory in the Middle East. The Trump administration advocates the ethnic cleansing of the entire (surviving) population of Gaza. The US armed forces are also firing ordnance into Yemen with the announced goal of "annihilating" the Houthis who hold power. In a Signal group chat, top national security officials rejoiced (with emojis) over a strike in which a building collapsed. It seems unclear that Musk-Trump will have accounted for the related terrorism risk.
Russia is now a risk in a way that it was not before. It has special units that carry out acts of destruction abroad, such as assassinations and sabotage. In the last three years, these operations have accelerated inside Europe, and include blowing up military sites. Russia also pays people inside other countries to carry out acts of terror and sabotage. Russia has been carrying out cyber attacks inside the United States for years.
Before Musk-Trump, the United States had been fastidious about including Russia as a possible source of foreign terror. Now Russia is presented as an ally and Putin as a friend; intelligence and defense work designed to monitor Russian sabotage inside the United States have been scaled back, as has tracking of Russian war crimes in Ukraine and public reporting on Russia. Gabbard, the director of national intelligence, rationalizes Russian aggression. Patel, the FBI director, owes his career to the claim that people who (truthfully) speak of Russian operations inside the United States are carrying out a hoax. Trump’s nominee for US district attorney for Washington, DC, is a media star in Russia.
This is all beyond the wildest dreams of the Kremlin. The Putinism on display in the federal government creates an atmosphere in which a Russian operation inside the United States would be much easier.
It is not hard to see what Russia would gain from a false-flag terror attack on American territory. Moscow would be seeking to weaken the United States, and by generating a response from Musk-Trump that suits Russia. Having Trump blame his enemies for what was in fact a Russian attack is in the interest of the Russian Federation.
Other actors than these three are also possible. I fear, though, that whether I am right or wrong about the specific source, there can be no doubt that we are far more vulnerable than we were three months ago. And any major attack, regardless of origin, would lead to the same kind terror management. The people in the White House have no governing skills, but they do have entertainment skills. They will seek to transform themselves from the villains of the story to the heroes, and in the process bring down the republic. Please indulge me if I ask you to consider Lesson 18 again.
18. Be calm when the unthinkable arrives. Modern tyranny is terror management. When the terrorist attack comes, remember that authoritarians exploit such events in order to consolidate power. The sudden disaster that requires the end of checks and balances, the dissolution of opposition parties, the suspension of freedom of expression, the right to a fair trial, and so on, is the oldest trick in the Hitlerian book. Do not fall for it.
That lesson arises from two notorious twentieth-century examples: the Reichstag Fire in Germany in 1933, which Hitler used to declare a state of emergency, and the Kirov assassination in the Soviet Union in 1934, which Stalin used as an excuse to expand terror. In both cases, it is the reaction that we remember, rather than the event itself.
I wish that terrorist attacks were a moment when government could be trusted. But the temptation, for any government, is to take the shock and to divert it in a convenient direction. And the temptation, for us, is to imagine that our leaders will rise to the occasion. After 9/11, I listened to President Bush address the nation, sitting in my pickup, on the driveway outside a friend’s house. Though my own politics were very different, I remember the pull inside me, the wish to believe that he would do the right thing. I didn’t let myself believe anything of the sort, but I remember the feeling: and it is that tug that we cannot let get the best of us.
Our present government would be the last to resist the temptation to exploit terror. Musk-Trump would, I fear, make little if any attempt to apprehend the responsible people, especially if they are Americans or Russians. They might blame the Democratic Party, or Americans they hate for other reasons, or the opposition generally, or Canadians or Ukrainians or other Europeans. They will likely try to put an end to the American republic.
Right then comes is the critical moment when we must prevent ourselves from going along.
I do not relish describing this chain of events. But the only way to cut the chain it is to see the links. And when we can imagine that we ourselves have the power to cut the links, as we do, we can also imagine ourselves more free.
History teaches us how terrorist attacks are exploited. Our advantage is that we know this history, and so react sensibly. Do not give the present regime the benefit of the doubt after it allows a terrorist attack to take place on American soil. Be skeptical about its account of who is to blame. Insist that Musk-Trump take responsibility. And understand that freedom is the first condition of security. A terrorist attack is no reason to concede anything to this regime. On the contrary: such a failure by Musk-Trump would be one more reason, and a very powerful one, to resist it.
Throughout history, and around the world right now, government indifference and incompetence that leads to civilians deaths has been seen as a reason for protest.
The night before I was stopped by the police, I had been driving that truck through water. It was a time of high rain in the central United States. Highways were flooded.
In the pre-revolutionary France of the eighteenth century, decadent rulers said “après nous, le déluge” — “after us, the flood.” We care not at all about the consequences of our actions; we are here to profit so long as we can. This is the attitude of Musk, Trump, and the rest. They are in it for themselves, provoking disasters for the rest of us along the way.
A few days before that drive began, I finished my doctoral dissertation, about revolutions, based on research in post-communist Poland. One of my supervisors was the the British historian Timothy Garton Ash. Considering the task of Poland’s new democratic government, he reversed the formula of French royalty, writing: “après le deluge, nous.”
After the flood, we remain. The disaster brought by the decadent is part of the story. But it is not the conclusion. It is what we do next that matters.
14 notes
·
View notes
Note
Top 5 books?
Mexican Gothic is a great gothic horror book that cleverly interweaves colonialist and misogynist dynamics into the story. 10/10, I should go read more by this author.
Longitude is a fascinating history about the race to create an accurate and seafaring-stable clock in the 18th century. I read this at a flight instructor's recommendation and LOVED IT.
Into Thin Air is an account of the 1996 Everest disaster. It's a fascinating book about the people who are drawn to the most extreme parts of the world.
Trapped Under the Sea is about a massive infrastructure project undertaken in Boston Harbor, creating a huge tunnel that ran beneath the ocean for miles for sewage. The project was wildly mismanaged, necessitating a team of scuba divers to take on an over-land project in the dead air tunnel to complete the project, with deadly results.
The Code Book is about cryptography throughout time, starting with basic ciphers in 17th century France, all the way through to the modern era. It's written to be accessible to people who don't normally deal with math, and will give you a good idea of how secrets have been transported and conveyed throughout centuries.
#thanks for the ask!!#almost caught up with this batch of asks!#also happy to take any recommendations on disaster and/or infrastructure and/or nerd books 👀#yourlocalegotisticalqueerishere#asks
9 notes
·
View notes
Text

U.S. Air Force Awards RTX $1 Billion Contract to Upgrade F-22 Sensors
The contract follows the recent news about the tests of new advanced sensors on the F-22 Raptor, which the U.S. Air Force is planning to field quickly as part of the ongoing upgrade program.
Parth Satam
F-22 new sensors contract
An F-22 Raptor takes off from Nellis Air Force Base, Nevada, June 30, 2022. (U.S. Air Force photo by Senior Airman Zachary Rufus)
Amid the acute need for 5th generation fighters in modern combat scenarios against peer adversaries, the U.S. Air Force is looking to upgrade its F-22 Raptor with a series of sensors to make it more survivable and relevant. The service announced on Aug. 29, 2024, the award of a $1 billion contract to RTX‘s Raytheon for new sensors that are categorized as “Group B hardware”, together with spares and support equipment.
“Work will be performed in McKinney, Texas, and is expected to be completed by May 8, 2029,” said the DoD contracts statement. The Aviationist had recently reported that the Air Force was testing new sensors on the F-22 to extend its service life, which would also be applied to the NGAD (Next Generation Air Dominance) family of systems.
That report also quoted Brig. Gen. Jason D. Voorheis, the Program Executive Officer for Fighter and Advanced Aircraft, who said they were hoping to field these sensors faster. The Raptor team had conducted six flight tests to demonstrate the advanced sensors.
“The F-22 team is working really hard on executing a modernization roadmap to field advanced sensors, connectivity, weapons, and other capabilities. We’re executing that successfully, and that will lead to […] a rapid fielding in the near future.” This would be done through a Middle Tier Acquisition (MTA) program.
Some of the sensors included in the contract could be the stealthy pods seen on the F-22. Air and Space Forces earlier quoted officials who confirmed that the pods host IRST (Infrared Search and Track) sensors. The development of a new IRST sensor for the Raptor was also confirmed by the service’s 2025 budget request, which however did not mention the sensor being podded.
This work is part of an F-22 improvement campaign that calls for $7.8 billion in investments before 2030, which includes $3.1 billion for research and development and $4.7 billion in procurement.

An F-22 Raptor with the Air Combat Command F-22 Raptor Demonstration Team performs a flyover and air demonstration at the U.S. Air Force Academy in Colorado Springs, Colo., Aug 13, 2024. (U.S Air Force Photo by Trevor Cokley)
F-22’s future in the U.S. Air Force
The development is also in contrast with previously reported USAF plans to retire the older F-22 airframes, for which it had sought approval from the Congress. These F-22s are 32 Block 20 units from a total fleet of 186. At the same time, the service aims to upgrade the remaining 154 with new cryptography, an expanded open architecture, new weapons and an advanced threat warning receiver, beside the IRST.
However, the service now appears to be reconsidering that plan, after Voorheis was quoted in the ASF report: “From an F-22 sunsetting perspective, I don’t have a date for you.” “What I can tell you is that we are hyper-focused on modernization to sustain that air superiority combat capability for a highly contested environment for as long as necessary,” he added.
IMAGE 3: A U.S. Air Force F-22 Raptor assigned to the 3rd Wing takes off above Joint Base Elmendorf-Richardson, Alaska, Jun. 17, 2024. (Image credit: USAF/Senior Airman Julia Lebens)
The U.S. Air Force describes the Raptor as a combination of stealth, supercruise, maneuverability, and integrated avionics, designed to project air dominance, rapidly and at great distance. Initially introduced as an air-superiority-only asset, the F-22 later started performing both air-to-air and air-to-ground missions.
The F-35 is largely a strike fighter and an airborne sensor-fusion and data-processing capable command post in its tactical orientation. But the Raptor is a pure air dominance interceptor. Although costly to upgrade and maintain, it nevertheless can play an important role in degrading adversary air power through either long-range BVR (Beyond Visual Range) and dogfights.
Moreover, having F-22s also increases the number of LO (Low Observable) aircraft in the inventory, at least until more F-35s are available, especially the TR-3 (Technology Refresh-3) Block 4 upgraded variants.
In 2021 too, then Air Force chief General Charles Q. Brown Jr. revealed his “4+1” fighter plan, suggesting the F-22 to be replaced by the NGAD while retaining the F-35, F-15E and EX, and the F-16. The “plus 1” was the A-10, but in March 2023, Brown said the A-10s were being retired faster than expected and the entire fleet would possibly be divested by 2030.
Meanwhile the NGAD’s future itself is uncertain after U.S.A.F have noted its technical complexity and financial implications. The F-22 thus seems to be back in the running.
On Jul. 10, 2024, Air Combat Command chief Gen. Kenneth Wilsbach said during a Mitchell Institute event that the service has no official plan to retire its F-22 Raptors. “Right now, there’s…frankly isn’t an F-22 replacement and the F-22 is a fantastic aircraft,” said Wilsbach. “I’m in favor of keeping the Block 20s. They give us a lot of training value, and even if we had to in an emergency use the Block 20s in a combat situation, they’re very capable.”
F-22 Indonesia

U.S. Air Force F-22 Raptors assigned to the 27th Expeditionary Fighter Squadron, conduct Dynamic Force Employment operations at I Gusti Ngurah Rai Air Force Base, Indonesia, on Aug. 6, 2024. (U.S. Air Force photo by Senior Airman Mitchell Corley)
Other known F-22 upgrades
Other upgrades mentioned in the 2025 budget request are a Mode 5 Identification Friend or Foe (IFF), Link 16, a Multifunction Information Distribution System Joint Tactical Radio System (MIDS JTRS), a new Operational Fight Program, advanced radar Electronic Protection and an Embedded GPS/Inertial Navigation System (INS) Modernization (EGI-M).
Voorheis also mentioned the GRACE (Government Reference Architecture Compute Environment) software that would allow “non-traditional F-22 software” to be installed on the aircraft and provide “additional processing and pilot interfaces.”
A new helmet is also being tested, as part of the Next Generation Fixed Wing Helmet program to replace the current 40-year-old HGU-55P headgear. The new helmet would also allow the introduction of helmet-mounted devices which provide essential flight and weapon aiming information through line of sight imagery, easing the workload of the pilots.
About Parth Satam
Parth Satam's career spans a decade and a half between two dailies and two defense publications. He believes war, as a human activity, has causes and results that go far beyond which missile and jet flies the fastest. He therefore loves analyzing military affairs at their intersection with foreign policy, economics, technology, society and history. The body of his work spans the entire breadth from defense aerospace, tactics, military doctrine and theory, personnel issues, West Asian, Eurasian affairs, the energy sector and Space.
@Theaviationist.com
15 notes
·
View notes
