#Privacy Control Software
Explore tagged Tumblr posts
Text
truly so baffling to me to hear people complain about their electronics like my coworker was complaining that her 2017 Mac was so slow its barely functional and it’s like what do you MEAN your 8 year old Mac is dead? mine is from 2013 and runs flawlessly?? what are you doing to your $1000 machine ??? filling it with peanut butter and TikTok viruses?????
#and I’m fairly callous with mine. I’ll download anything. (although I am a tech guy so like I can think critically but#I do tend to download a bunch of random shit from like Reddit threads and forums lol) and yet my Mac is like practically mint.#his only crime is sometimes he dies at 20% and gets hot and can’t run 32bit programs (<apple’s fault)#he’s still running max graphics stardew valley with 900 mods and Minecraft mid graphics with 200 and like 30fps (<good for modded mc)#Apple truly making solid products considering every midrange windows pc I’ve used became garbage in like 4-5 years 🫥#ive spent more on my 4 windows PCs in the last 20 years than this one Mac that will probably keep trucking for another 10 years.#Like sorry im not an apple freak but considering how many devices I’ve bought used and fiddled with…… kind of incredible how Apple has#somehow managed to come out on top in the longevity/ease of use/privacy departments.#if windows didn’t force you to update and use their bloatware bullshit and not let you CONTROL THE MACHINE YOU BOUGHT id be less mad#but every time I use win 10 or 11 I want to shoot myself in the head. win1011 softwares practically feel like malware.#a day in the life of steeve#only reason I would ever have a windows device is to play sims 2. (works on Mac but no utilities which are indispensable these days).#and I’m thankful Emily has a top tier gaming laptop for me to use for sims <3#if I ever need another pc I think I’ll venture into Linux. my steam deck runs Linux and it feel so pleasant and friendly compared to win11.
8 notes
·
View notes
Text
Ensure FERPA Compliance with MeraSkool School Management Software
Ensure FERPA Compliance with MeraSkool School Management Software
Ensure FERPA Compliance with MeraSkool School Management Software
The Family Educational Rights and Privacy Act (FERPA) is a federal law that protects the privacy of student education records. For educational institutions, ensuring FERPA compliance is not just a legal obligation; it's a crucial aspect of building trust with parents and students. Choosing the right school management software can significantly simplify the process of maintaining compliance and safeguarding sensitive student data.
Understanding FERPA Compliance
FERPA grants parents and eligible students certain rights regarding their education records. These rights include:
The right to inspect and review their education records.
The right to request amendments to their education records.
The right to control the disclosure of personally identifiable information (PII) from their education records.
Non-compliance with FERPA can lead to severe penalties, including loss of federal funding. Therefore, selecting a school management system with robust security features and a commitment to data privacy is paramount.
MeraSkool: A FERPA-Compliant Solution
MeraSkool.com offers a comprehensive school management solution designed with FERPA compliance in mind. Our platform incorporates multiple layers of security to protect student data, including:
Data Encryption: MeraSkool employs advanced encryption techniques to protect student data both in transit and at rest.
Access Control: Our system uses role-based access control (RBAC), ensuring that only authorized personnel have access to sensitive information. This prevents unauthorized access and maintains data integrity.
Regular Security Audits: We conduct regular security audits and penetration testing to identify and address any potential vulnerabilities.
Data Backup and Recovery: MeraSkool provides robust data backup and recovery mechanisms to ensure data availability in case of any unforeseen circumstances. This safeguards against data loss and ensures business continuity.
Compliance Certifications: We are actively pursuing relevant compliance certifications to further demonstrate our commitment to data security and privacy. (Note: Specific certifications should be listed here if available).
AI-Powered Insights and Data Security: MeraSkool leverages AI to optimize tasks and provide insights for operational efficiency, while robust data security protocols ensure privacy and regulatory compliance. (Learn More)
Key Features for FERPA Compliance
Several features within MeraSkool directly contribute to FERPA compliance:
1. Secure Student Management:
MeraSkool's student management module (learn more) allows schools to manage student enrollment, maintain detailed profiles, track attendance, and generate grade reports securely. The system ensures only authorized personnel can access sensitive student information, maintaining confidentiality.
2. Controlled Access to Records:
Our platform provides granular control over access to student records, ensuring that only authorized individuals—parents, teachers, and administrators—can view the appropriate information. This prevents unauthorized disclosure of PII.
3. Secure Fee Management:
MeraSkool's fee management module (learn more) supports creating fee structures, generating invoices, and enabling secure online payments. This functionality maintains financial transparency while securing sensitive financial data.
4. Robust Reporting and Analytics:
MeraSkool's reporting and analytics capabilities provide valuable insights into student performance, attendance, and other key metrics. This data is accessed through secure channels, adhering to FERPA guidelines.
5. Audit Trails:
(Note: If available, mention the existence and functionality of audit trails in MeraSkool. Audit trails record all actions performed on student data, providing a valuable tool for monitoring and ensuring accountability.)
6. Powerful Printable system:
MeraSkool offers a powerful printable system (learn more) allowing for secure downloading and printing of marksheets, results, ID cards, fee receipts, and other essential documents. This functionality helps maintain accurate records while ensuring data remains secure.
Additional Benefits of MeraSkool
Beyond FERPA compliance, MeraSkool provides numerous other benefits for schools:
Exam & Assignment Management: Create, schedule, and manage exams with different question formats. (Learn More)
Timetable and Attendance Management: Automated attendance tracking and timetable creation. (Learn More)
Realtime Notification: Realtime notifications powered by WhatsApp bot. (Learn More)
World-Class Support: 24/7 support and a 7-day new feature delivery commitment. (Learn More)
Simple to Use UI & UX: Intuitive design and seamless user experience. (Learn More)
Easy Onboarding with Excel Upload: Effortless integration and seamless transition. (Learn More)
MeraSkool's Commitment to Data Privacy
MeraSkool is committed to providing a secure and compliant platform for schools. We understand the importance of protecting student data and are dedicated to continually improving our security measures to meet the evolving demands of FERPA and other relevant regulations.
Contact us today to learn more about how MeraSkool can help your school maintain FERPA compliance and streamline its operations.
Note: This information is for general guidance only and does not constitute legal advice. Consult with legal counsel to ensure your school's full compliance with FERPA.
#FERPA compliance#school management software#student privacy#data security#MeraSkool#educational software#online learning#school administration#data encryption#access control#security audits#FERPA regulations#data protection
0 notes
Text
K7 Total Security for Windows
K7 Total Security is a comprehensive cybersecurity solution developed by K7 Computing to provide multi-layer protection for personal computers. With over three decades of expertise, K7 Total Security leverages advanced technologies, such as Cerebro Scanning, to deliver robust defense against evolving malware and cybersecurity threats. Key Features of K7 Total Security 1. Real-Time Threat…
#AI-based security#best cybersecurity tools#Cerebro Scanning#cybersecurity software#K7 Total Security#malware protection#online transaction security#parental control software#privacy protection#real-time threat detection
0 notes
Text
Canada sues Google

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/12/03/clementsy/#can-tech

For a country obsessed with defining itself as "not America," Canada sure likes to copy US policies, especially the really, really terrible policies – especially the really, really, really terrible digital policies.
In Canada's defense: these terrible US policies are high priority for the US Trade Representative, who leans on Canadian lawmakers to ensure that any time America decides to collectively jump off the Empire State Building, Canadian politicians throw us all off the CN Tower. And to Canada's enduring shame, the USTR never has to look very hard to find a lickspittle who's happy to sell Canadians out.
Take anti-circumvention. In 1998, Bill Clinton signed the Digital Millennium Copyright Act, a gnarly hairball of copyright law whose Section 1201 bans reverse-engineering for any purpose. Under DMCA 1201, "access controls" for copyrighted works are elevated to sacred status, and it's a felony (punishable by a five-year prison sentence and a $500k fine) to help someone bypass these access controls.
That's pretty esoteric, even today, and in 1998, it was nearly incomprehensible, except to a small group of extremely alarmed experts who ran around trying to explain to lawmakers why they should not vote for this thing. But by the time Tony Clement and James Moore (Conservative ministers in the Harper regime) introduced a law to import America's stupidest tech idea and paste it into Canada's lawbooks in 2012, the evidence against anti-circumvention was plain for anyone to see.
Under America's anti-circumvention law, any company that added an "access control" to its products instantly felonised any modification to that product. For example, it's not illegal to refill an ink cartridge, but it is illegal to bypass the access control that gets the cartridge to recognise that it's full and start working again. It's not illegal for a Canadian software developer to sell a Canadian Iphone owner an app without cutting Apple in for a 30% of the sale, but it is illegal to mod that Iphone so that it can run apps without downloading them from the App Store first. It's not illegal for a Canadian mechanic to fix a Canadian's car, but it is illegal for that mechanic to bypass the access controls that prevent third-party mechanics from decrypting the error codes the car generates.
We told Clement and Moore about this, and they ignored us. Literally: when they consulted on their proposal in 2010, we filed 6,138 comments explaining why this was a bad idea, while only 53 parties wrote in to support it. Moore publicly announced that he was discarding the objections, on the grounds that they had come from "babyish" "radical extremists":
https://www.cbc.ca/news/science/copyright-debate-turns-ugly-1.898216
For more than a decade, we've had Clement and Moore's Made-in-America law tied to our ankles. Even when Canada copies some good ideas from the US (by passing a Right to Repair law), or even some very good ideas of its own (passing an interoperability law), Canadians can't use those new rights without risking prosecution under Clement and Moore's poisoned gift to the nation:
https://pluralistic.net/2024/11/15/radical-extremists/#sex-pest
"Not America" is a pretty thin basis for a political identity anyway. There's nothing wrong with copying America's good ideas (like Right to Repair). Indeed, when it comes to tech regulation, the US has had some bangers lately, like prosecuting US tech giants for violating competition law. Given that Canada overhauled its competition law this year, the country's well-poised to tackle America's tech giants.
Which is exactly what's happening! Canada's Competition Bureau just filed a lawsuit against Google over its ad-tech monopoly, which isn't merely a big old Privacy Chernobyl, but is also a massively fraudulent enterprise that rips off both advertisers and publishers:
https://www.reuters.com/technology/canadas-antitrust-watchdog-sues-google-alleging-anti-competitive-conduct-2024-11-28/
The ad-tech industry scoops up about 51 cents out of every dollar (in the pre-digital advertising world the net take by ad agencies was more like 15%). Fucking up Google's ad-tech rip off is a much better way to Canada's press paid than the link tax the country instituted in 2023:
https://www.eff.org/deeplinks/2023/05/save-news-we-must-ban-surveillance-advertising
After all, what tech steals from the news isn't content (helping people find the news and giving them a forum to discuss it is good) – tech steals news's money. Ad-tech is a giant ripoff. So is the app tax – the 30% Canadian newspapers have to kick up to the Google and Apple crime families every time a subscriber renews their subscriptions in an app. Using Canadian law to force tech to stop stealing the press's money is a way better policy than forcing tech to profit-share with the news. For tech to profit-share with the news, it has to be profitable, meaning that a profit-sharing press benefits from tech's most rapacious and extractive conduct, and rather than serving as watchdogs, they're at risk of being cheerleaders.
Smashing tech power is a better policy than forcing tech to share its stolen loot with newspapers. For one thing, it gets government out of the business of deciding what is and isn't a legit news entity. Maybe you're OK with Trudeau making that call (though I'm not), but how will you feel when PM Polievre decides that Great Replacement-pushing, conspiracy-addled far right rags should receive a subsidy?
Taking on Google is a slam-dunk, not least because the US DoJ just got through prosecuting the exact same case, meaning that Canadian competition enforcers can do some good copying of their American counterparts – like, copying the exhibits, confidential memos, and successful arguments the DoJ brought before the court:
https://www.justice.gov/opa/pr/justice-department-sues-google-monopolizing-digital-advertising-technologies
Indeed, this already a winning formula! Because Big Tech commits the same crimes in every jurisdiction, trustbusters are doing a brisk business by copying each others' cases. The UK Digital Markets Unit released a big, deep market study into Apple's app market monopoly, which the EU Commission used as a roadmap to bring a successful case. Then, competition enforcers in Japan and South Korea recycled the exhibits and arguments from the EU's case to bring their own successful prosecutions:
https://pluralistic.net/2024/04/10/an-injury-to-one/#is-an-injury-to-all
Canada copying the DoJ's ad-tech case is a genius move – it's the kind of south-of-the-border import that Canadians need. Though, of course, it's a long shot that the Trump regime will produce much more worth copying. Instead, Trump has vowed to slap a 25% tariff on Canadian goods as of January 20.
Which is bad news for Canada's export sector, but it definitely means that Canada no longer has to worry about keeping the US Trade Rep happy. Repealing Clement and Moore's Bill C-11 should be Parliament's first order of business. Tariff or no tariff, Canadian tech entrepreneurs could easily export software-based repair diagnostic tools, Iphone jailbreaking tooks, alternative firmware for tractors and medical implants, and alternative app stores for games consoles, phones and tablets. So long as they can accept a US payment, they can sell to US customers. This is a much bigger opportunity than, say, selling cheap medicine to Americans trying to escape Big Pharma's predation.
What's more, there's no reason this couldn't be policy under Polievre and the Tories. After all, they're supposed to be the party of "respect for private property." What could be more respectful of private property than letting the owners of computers, phones, cars, tractors, printers, medical implants, smart speakers and anything else with a microchip decide for themselves how they want to it work? What could be more respectful of copyright than arranging things so that Canadian copyright holders – like a games studio or an app company – can sell their copyrighted works to Canadian buyers, without forcing the data and the payment to make a round trip through Silicon Valley and come back 30% lighter?
Canadian politicians have bound the Canadian public and Canadian industry to onerous and expensive obligations under treaties like the USMCA (AKA NAFTA2), on promise of tariff-free access to American markets. With that access gone, why on Earth would we continue to voluntarily hobble ourselves?
#pluralistic#link tax#big tech#corruption#canpoli#cdnpoli#monopolies#ad-tech#publishing#canada#competition bureau#usmca#nafta#anticircumvention#r2r#right to repair#interoperability
273 notes
·
View notes
Text

He should be arrested for violating our privacy. He was not vetted by congress and has no security clearance.
Contact your state’s attorney general and request help.
Can we ask the ACLU to file a class action suit? Who’s with me?
“Let’s get into the details. Musk’s staffers have been caught plugging external hard drives into federal agency systems and reportedly locking others out of private rooms to perform—who knows what actions. This behavior violates key cybersecurity laws under FISMA and NIST guidelines, which are designed to protect sensitive federal information. Here’s why this is a serious problem.
Federal systems are strictly regulated, allowing only approved devices to connect. Unauthorized external drives can introduce viruses, ransomware, or other harmful software that may compromise entire networks and disrupt essential operations. This puts system stability and continuity of services at risk, endangering critical infrastructure.
These devices could also be used to steal or damage critical information, including personal data for millions of Americans—such as Social Security recipients and taxpayers. Unauthorized access creates significant vulnerabilities, exposing sensitive data to the risk of cyberattacks. Such attacks could cripple vital services and compromise the privacy and safety of millions of people.
Additionally, federal agencies have strict access controls to prevent unauthorized data manipulation or theft. When unauthorized devices are connected, these protections are bypassed, allowing unauthorized users to potentially alter or extract sensitive data. This undermines system integrity and opens the door to both internal and external threats.
External drives also often lack essential security features, such as encryption and antivirus scanning, making them vulnerable to cybercriminal exploitation. These security gaps further increase the risk of data breaches and system compromise, which can have far-reaching consequences.
Federal systems handle trillions of dollars in payments and manage personal data for millions of U.S. citizens. By bypassing cybersecurity laws and protocols, Musk’s staffers are putting these systems—and the public—at serious risk. This activity is illegal, reckless, and unacceptable. Immediate oversight and intervention are necessary to stop these violations!” ~ A N P S
225 notes
·
View notes
Text
One thing I noticed talking about Linux and free software is that a lot of people seem afraid of learning things about technology. I constantly read things like "I hate windows, but switching to linux would mean learning a new OS, and you have to be some super-smart programmer-hacker to do that." Or even: "Switching to firefox would mean switching browsers and I don't know how"
And that is precisely the attitude tech companies like Microsoft and Apple try to instill in their users in order to control them. They create these simple and “friendly” user interfaces for their products, but these hide information. From their OS being pre-installed to their settings apps, they keep people from learning things about how their computer works, and letting the companies make the decisions for their users.
I think people are underestimating themselves and overestimating how hard it is to learn new things are. It is like Windows/Macos have taught them some kind of technological learned helplessness. Not knowing how computers work and being afraid to learn how is how companies like Microsoft controls you, and justifies that control.
For example, people hate the forced and automatic system updates on Windows. And Microsoft justifies it as necessary because some people don’t know that their computer needs security updates and therefore don’t update, so they have to force the updates on them. That’s definitely true, and Microsoft’s tech support people is definitely very aware of that but it is a operating system that presumes that the user is incompetent and therefore shouldn’t control their own computer. And of course Microsoft abuses that power to force privacy-invading features on their users. Windows updates are also badly designed in comparison, no Linux distro I’ve used required the update program to hijack the entire computer, preventing the user from doing other things, but Windows does.
This is the dark side of “user-friendly” design. By requiring zero knowledge and zero responsibility for the user, they also take control away from the user. User-friendly graphical user interfaces (GUI) can also hide the inner workings of a system in comparison to the command line, which enables more precise control of your computer and give you more knowledge about what it is doing.
Even GUIs are not all made equal in regards to this, as the comparison between the Windows Control panel and their newer Settings app demonstrates. As I complained about before, Windows have hidden away the powerful, but complex Control Panel in favor of the slicker-looking but simplified and less powerful Settings app for over a decade now.
Of course this is a sliding scale, and there is a sensible middle-ground between using the command line for everything and user-friendly design masking taking control away from the end user.
There are Linux distros like Linux Mint and MX Linux who have created their own GUI apps for tasks that would otherwise use the command line, without taking control away from the user. This is mainly because they are open source non-profit community-driven distros, instead of being proprietary OSes made by profit-driven megacorps.
Still, giving that control to the user presumes some knowledge and responsibility on part of the user. To return to the update example, by default both Mint and MX will search and notify you of available updates, but you will have to take the decision to download and install them. Automatic updates are available in both cases, but it’s opt-in, you have to enable that option yourself. And that approach presumes that you know that you should update your system to plug security holes, something not all people do. It gives you control because it presumes you have knowledge and can take responsibility for those decisions.
All this also applies to the underlying fact that practically all pre-built computers nowadays have an operating system pre-installed. Few people install an OS themselves nowadays, instead they use whatever came with the computer. It’s usually either Windows or MacOS for desktops/laptops, and Android/IOS for smartphones (which are also a type of computer).
Now all this is very convenient and user-friendly, since it means you don’t have to learn how to install your own operating system. The OEM takes care of that for you. But again, this is a convenience that takes choice away from you. If you don’t learn how to install your own OS, you are stuck with whatever that is on the computer you bought. It’s probably precisely this step that scares people away from Linux, few people have installed even Windows, and installing your own OS seems impossibly scary. But again, learning is the only way to take back control. If you learn how to install an OS off an USB stick, you now have choices in what OS to use. (Sidenote: the hard part IMO is not the actual install process, but fiddling with the BIOS so it will actually boot from the distro on the USB stick. This old comic strip illustrates this very well).
That’s how life is in general, not just computers. Having control over your life means making decisions based on your own judgment. And to make sensible, rational decisions, you have to learn things, acquire knowledge.
The only other alternative is letting others take those decisions for you. You don’t have to learn anything, but you have no control. And in the tech world, that means big corporations like Microsoft, Google and Apple will make those decisions, and they are motivated by their own profits, not your well-being.
Computers have only become more and more capable and more important in our lives, and that can enable wonderful things. But it also means more power to the tech companies, more power over our lives. And the only way to resist that is to learn about computers, to enable us to make our own decisions about how we use technology.
902 notes
·
View notes
Text
Season 4 launches June 11

This is our biggest season yet - more sit-down interviews, on-site recording at game nights and conventions, Jake and Reilly playing games together, custom music, and some big experiments. Our guests continue to be ridiculously thoughtful and interesting. Reilly is hard at work editing out Jake's incoherent tangents and Jake is hard at work tracking down all the games our guests mention offhand so that we can link to them in the show notes.
Our show is entirely produced, owned, and operated by the two of us. We've kept the show independent so that we can ensure our guest's privacy, our guests can speak openly about sex and drugs and piracy and other corporate-unfriendly topics, and we can have control over the advertisements. If you're enjoying Campaign Spotlight, and you want to support us as we keep paying the production bills and putting in the hours to make this show for all of you.
Subscribe and leave a review
Our show is a lot of unscripted audio-only long-form conversations, which is not optimized for virality. We'd like more people to keep finding the show, because that's how we find out about cool new campaigns and find more guests for subsequent seasons. Help feed the various algorithms by liking, subscribing, leaving a review, or whatever the options look like on whatever platform you're using.
Tell a friend about the show
If you've already done all of that, tell another human in your life about Campaign Spotlight! We're pretty much everywhere you find podcasts, including Spotify, Apple Podcasts, and YouTube - or even straight from the RSS feed. (If your friend is listening to podcasts on a platform that doesn't have Campaign Spotlight, let us know, because Jake needs to fix that.)
Call in and tell us about your character
Why not support Campaign Spotlight by actually coming on the podcast yourself? We've set up a hotline (724 320 2020) where you can call in and tell us about your cool character (or even about your campaign!) and we'll feature it on the show. If calling in and leaving voicemail seems daunting, you can send it to [email protected] instead.
Subscribe to our Patreon
If you're in a position to help pay for our hosting expenses, the con day passes, and all the software Reilly uses to make the show sound great, the best way to do that is supporting us on Patreon. It's $3 a month, and having that recurring financial support is invaluable in letting us plan out the show. We also have a Ko-Fi which does pretty much the same thing.
Advertise on the show
Have you published your own game? Are you a professional GM looking for clients? Do you have some other cool creative project you want people to know about? Advertise it on Campaign Spotlight! Our rates are reasonable, our audience is great, and your support will absolutely help us keep the lights on around here. Send us an email at [email protected] for more information.
If you have any questions about any of this, feel free to DM us or email us at [email protected] or send us an ask. Thanks so much for listening to the show. This project has become a huge part of our lives and it's sincerely such a joy to share it with all of you.
65 notes
·
View notes
Text
alt text under cut
Alt National Park Service·
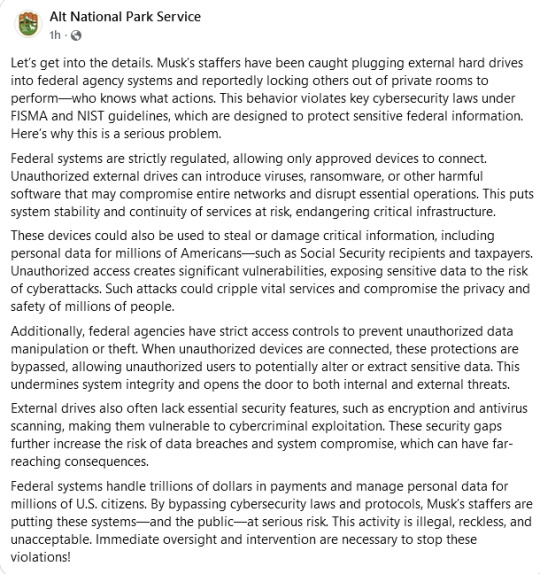
Let’s get into the details. Musk’s staffers have been caught plugging external hard drives into federal agency systems and reportedly locking others out of private rooms to perform—who knows what actions. This behavior violates key cybersecurity laws under FISMA and NIST guidelines, which are designed to protect sensitive federal information. Here’s why this is a serious problem.
Federal systems are strictly regulated, allowing only approved devices to connect. Unauthorized external drives can introduce viruses, ransomware, or other harmful software that may compromise entire networks and disrupt essential operations. This puts system stability and continuity of services at risk, endangering critical infrastructure.
These devices could also be used to steal or damage critical information, including personal data for millions of Americans—such as Social Security recipients and taxpayers. Unauthorized access creates significant vulnerabilities, exposing sensitive data to the risk of cyberattacks. Such attacks could cripple vital services and compromise the privacy and safety of millions of people.
Additionally, federal agencies have strict access controls to prevent unauthorized data manipulation or theft. When unauthorized devices are connected, these protections are bypassed, allowing unauthorized users to potentially alter or extract sensitive data. This undermines system integrity and opens the door to both internal and external threats.
External drives also often lack essential security features, such as encryption and antivirus scanning, making them vulnerable to cybercriminal exploitation. These security gaps further increase the risk of data breaches and system compromise, which can have far-reaching consequences.
Federal systems handle trillions of dollars in payments and manage personal data for millions of U.S. citizens. By bypassing cybersecurity laws and protocols, Musk’s staffers are putting these systems—and the public—at serious risk. This activity is illegal, reckless, and unacceptable. Immediate oversight and intervention are necessary to stop these violations!
64 notes
·
View notes
Text
Your Phone isn't Evil
There is way way too much focus on devices when it comes to tech wellness.
I get why. For non-technically trained people, doing anything beyond using a device in the most stock way can be intimidating - and companies pay a lot of money to make you think it's bad to do so.
But consuming more ultimately redirects our efforts away from the people who create and profit off of these issues, encourages wasteful conspicuous consumption, and adds yet another paywall to mental and physical well being.
I really think that a lot of the people buying dumbphones and flip phones in an attempt to use theirs less would be better served by simply making privacy a central tenet of how they manage their phones and stop using streaming in favor of local files which fosters better curation.
If you want to help your community, one of the things we need most now are people willing to watch tutorials and figure out how to do things like install custom OS on phones, jailbreak ereaders, make copies of DVDs and Blurays, setting up home servers, and switching a laptop to a Linux OS. These things aren't that difficult objectively but they are more time consuming than some people in our communities can manage right now.
And while we have some folks who've been carrying the torch for a long time, we need more people reviewing and recommending DRM-free books, music you can actually buy and own from places like Bandcamp, and talking about what FOSS (free and open source software) they love using.
You cannot downgrade your way to better relationship with tech alone. You also don't have to at all if you don't want to. The shifts we need are in user control. We don't get their by just picking up other devices we don't control.
38 notes
·
View notes
Text
Okay so hi I'm not super in any of your fandoms (watcher + try guys + dropout, hello welcome) but I'm a software developer and BOTH try guys and watcher announcing a custom streaming platform so close together had me suspicious.
So with just one, I'd assume that maybe they scraped together the money and resources to hire enough devs to make a well-designed secure platform (you want security for your login info and payment info). But two? Seems a bit odd.
So I actually looked a bit closer, at their privacy policies:
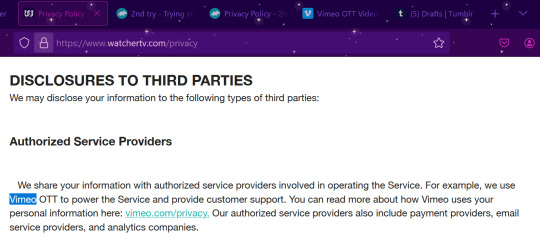
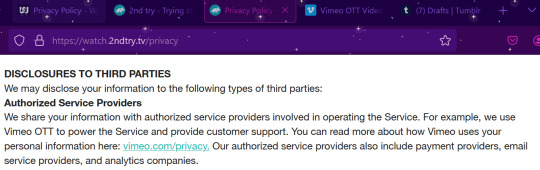
So it looks like Vimeo has decided to up their game and partner with existing yt content creation outlets to make streaming platforms.
Wait, what about Dropout? Dropout uses it too!
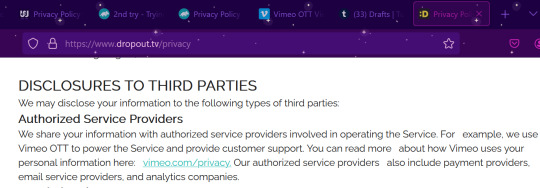
What does this mean, exactly?
Well, it means that Vimeo is providing a base software that gets customized for use by the companies (watcher, 2nd try). It means that Vimeo has a hand in your data associated with these platforms (account info, payment info, watch info, etc...). Is that a bad thing? Idk yet. Read through the streaming platform's privacy policy and Vimeo's privacy policy and make your own decision about what you feel comfortable sharing. But realistically the only additional info collected compared to your average youtube use is the financial info, and that seems to go through another third party (4th party?) (like Stripe or something like that. very common, most of your financial transactions online use things like that). It also likely means that Vimeo is taking some kind of cut of the profits made from these subscriptions (and lets be real, in this day and age, they're not just demanding a flat fee. It's likely some percentage of your subscription cost). The companies switching over (watcher and 2nd try) are making the gamble that the money made on subscriptions after cost taken is more than their adsense from yt, which isn't a wild idea considering how much we know yt loves demonetizing videos and paying their creators poorly.
It also means that Vimeo seems to be on some sort of marketing push, and that more of your favorite channels may swap over to streaming services in the near future.
Vimeo???? Yes, vimeo, that bootleg youtube that's been around for like as long as I can remember being on the internet. I guess they finally found a way to usurp yt's market control and good for them ig. Maybe this will be the thing that finally forces yt to fix their creator relationships? time will tell Why are you posting this in my favorite media company's tag?? I wanted fanart! Sorry to intrude, I just think this is neat and would love to hear opinions from other people on this knowledge.
186 notes
·
View notes
Text
EXPERIMENTAL - Konig Fic Part 2
Summary: Konig helps Researcher!Reader with a new technology they’ve been developing.
Part one: X
AO3 Link: X
Warnings: Flirting, Sexual Content, NSFW, Reader x Konig, talk of standard war stuff, Reader is a bit of a pervert. Non-con Voyeurism. Reader has anxious thoughts/low-self esteem-ish? No use of y/n, abduction, bondage, blood and injury.
Word Count: 7.2k
Reader gender/sex is incomprehensible cause I do it for the girls, the gays, and the theys
NSFW under the cut
It probably didn’t mean anything, right?
How common is your name, really? He probably was just thinking about his girlfriend or wife at home who just happens to share the same name as you, the same wife he didn’t happen to mention during your introductions - even if it would have been a really good icebreaker.
Yeah, that’s it.
It couldn’t have been about you.
Could it?
Your thoughts are spiraling now, not giving yourself the room to dissect one detail before your brain throws another at you. You still haven’t moved, wide eyes watching warm light reflect on his skin as he basks in post-orgasm bliss.
He’s still for a while, and you’re wondering if the finish had tired him out enough to lull him into a nap.
After a few minutes of watching the rise and fall of his chest, you decide the show was over and closed out of the software. There was some part of you, some part you’d hoped wouldn’t ever come to light, that decided to keep his feed connected.
You’ve crossed so many lines already. In for a penny, in for a pound, right?
You feel like you’ve ruined whatever chance you’ve had with him, violating his privacy like this. This was a man that wasn’t even comfortable showing his face, how did you think he was going to feel knowing a stranger has not only seen him fully naked but watched him jerk his cock to completion?
He doesn’t have to know. No one has to know. It’ll be our little secret and we’ll just pretend it never happened.
Yeah, you acted real casual today when you hadn’t done a horrible, awful, perverted thing. I’m sure you’ll act real casual the next time you have to look him in the eyes.
Shut up! Shut up! Shut up!
You rest your head on your keyboard not-so-gently, accidentally booting up an ancient mail software that was sure to kick your laptop’s fans into overdrive. An audible groan leaves your mouth.
Who knew non-consensual voyeurism would leave such a horrific feeling of guilt in the pit of your stomach?
That and the arousal that sits right underneath. Your underwear now had a wet stain from watching the show, unconsciously rubbing your thighs together as you had.
There was no way you were going to be able to focus on work now. You had been planning on staying late, but there’s no way you can analyze today’s data. Review his feed. Replay your conversations. Hear his breathing…
No, you just can’t do it right now. It’s too much.
You do a quick round of the lab, performing a sloppy iteration of your closing procedures, pack up your things, and head out for the day.
Before you do, you decide you might as well round out the horrific deed by doing one last terrible thing.
You pair your personal cell phone to the software and send yourself the erotic recording of Konig.
You’ll start fresh tomorrow, you decide.
————————————————————-
You most certainly did not start fresh tomorrow.
The next few days are a vicious cycle.
Go to work. Review Konig’s simulation footage. Fantasize. Feel guilty. Review raw data. Think about Konig touching himself. Feel aroused. Feel guilty. Rewrite codes. Go home. Watch erotic recording. Feel aroused. Get off.
Feel guilty.
Feel guilty.
Feel guilty.
You can’t help it. You’re out of control, an addict desperate to get their fix, ashamed of their actions but lacking the willpower to quit.
How are you supposed to stop thinking about him when all day at work you’re watching him fight his way through the shoot house, strong hands gripping his gun, and hearing to that laugh?
How can you go home and ignore the recording of him finishing while moaning your name?
You must have replayed it a thousand times. He moaned it like he was begging you, pleading with you. Such a powerful man choking on your name. Even after a full week had passed, it still had the power to excite you in ways you haven’t felt in ages.
Your next meeting with Konig was scheduled for today and if you had to judge solely by the feeling in your gut, you would’ve guessed you had eaten rocks for breakfast. Your brain tells you to flee and fast but your body is promised to these four walls. Your leg bounces as you pick at the fingers that beg for something to do besides type code.
You wanted to call it off. Tell Konig you weren’t feeling well and you’d try again next week. Or maybe hit the bricks entirely. Just walk out of the building and never look back. Forget about everything.
You’re reconsidering your career choices as a steady knock on the lab’s swinging door rips you from your thoughts.
Your wince before you look up, quickly plastering what you hope is a convincing smile on your face.
He catches your eyes through the glass and you notice them crinkle, unable to place an emotion to it. You’d been dreading this moment all week. Even going so far as to avoid looking at his live feed after the incident, just in case you weren’t able to feign the natural responses of hearing his recounts for the ‘first’ time. That in addition to the intrapersonal understanding that you couldn’t handle carrying anymore guilt-rocks in your stomach.
Looking him in the eyes was as hard as you imagined it to be. He pushes open the door and steps in, standing hesitantly near the entrance like he did last week. You notice he has a notepad in one hand, and it looks so comically small compared to his size. Like a giant holding a sticky note. In the other he holds your earpiece in an open palm, as if hesitant to wrap his fingers around it.
It doesn’t help that the first word that left his mouth as he entered the lab was your name. Flashbacks to his sweaty body, shuddering in pleasure as he came all over his rippling muscles grab your attention.
He had followed it up with something, but you had been too distracted to catch it. You close your eyes, touching your hand to your forehead.
You were not doing a very good job hiding your fluster.
“I’m so sorry- what’d you say?” You give a small laugh, partly to ease the tension in your chest and partly at the situation itself. It’s not funny, you know that. It’s terrible. So terribly ridiculous that you can’t help but laugh at yourself for getting yourself into this mess. Your hand follows through the rest of your hair in an effort to soothe yourself before falling back down at your side.
“Good to see you.” He repeats, tilting his head, taking just a few careful steps closer to you. His eyes dart to the side briefly before returning to you, “Is everything okay?”
You give another weak laugh, “Yeah, sorry. Just still in the zone.” You gesture vaguely at scattered papers and devices on the table. You don’t give him a chance to pry further, “How was it?”
He takes a moment to eye you carefully, and you are sure he’s about to call your bluff before he responds, “Remarkable.”
You swallow, breaking eye contact with him again. It’s always been hard for you to accept a compliment. You're hoping he doesn’t notice the warmth creeping up your cheeks, but you know you have absolutely no right to such a request after what you’ve done.
He clears his throat before he continues, “I promised you I would have feedback. It wasn’t easy.” He holds his notepad up briefly as he steps up to the table to carefully set it down along with your earpiece. You can see from across the table he’s got a few scribbled sentences spaced out on the notepad. You take note of his sloppy handwriting from across the table, before realizing he didn’t write in English.
He looks down at his notes and you’re thankful you have something to stare at that’s not Konig’s eyes or intimidating frame. You’re trying hard not to think about the body filling out his gear. You’ve grown so accustomed to seeing him naked that it’s almost strange to see him with his uniform on.
You can tell he takes a deep breath before continuing and you wonder briefly if he’s nervous about sharing his feedback, worried he will hurt your feelings. “You mentioned before that it scans objects?” The end of his sentence lifts, almost like he’s asking you a question, “I think it would be good to make sure that the user is always made aware of landmines. I’m positive it will save lives.”
“Yes, absolutely. That’s a great idea.” You nod as you jot his ideas down on your laptop, a reminder to update your code.
You’re happy to be talking shop. Even happier to be talking about defensive designs instead of offensive ones.
The way he rubs his bicep with his opposing hand triggers a realization. You finally look at his eyes, his still staring down at his notes, and watch him for a moment.
The idea didn’t come from thin air.
You wonder what he saw, what traumatic memories are being replayed behind the downcast eyes to inspire such an idea.
You feel an ache in your chest for him, the desire to alienate his discomfort but unequipped to do so. Instead you look at him, your eyes swollen with sympathy and the corner of your mouth pinched in a frown.
He takes a moment before looking back up at you. He notices your warped expression but misinterprets it, “Am I overstepping?”
Your voice is low and you press a hand to your heart, “No, Konig, not at all. This is very helpful.” You’re not sure what else to say to him. What do you say to a man haunted by the violence he’s witnessed?
The only thing you can do is make sure it doesn’t happen again.
You’re not working for the government anymore, you decided. You’re going to work for Konig. To tailor your device with the purpose to save and protect him.
So you stick to the topic at hand. “Any other ideas?” You ask, voice still soft with empathy as you glance down at the notes written in German.
“Uh,” He clears his throat again and touches the back of his neck over his hood, the fabric pulling a bit on the front, “Sometimes when we’re in the heat of things, I can’t always get to my remote.” He gestured to the band on his wrist. “Do you think it would be possible to have voice command?”
Your brain’s mulling over the possibility. You’re surprised you haven’t thought of it yet. You could eliminate the remote entirely, you’re sure your supervisor will be elated with the big savings on material costs. The earpiece already has a microphone for the comm, it wouldn’t be hard for you to configure it to an additional feature.
“Absolutely, voice control. That’s clever.” Your brain is already running with alternatives to the wrist remote as you type his ideas, “Do you go on a lot of missions that require stealth?” It’s easier to make eye contact with him when you’re discussing work. He nods, and you continue, “In addition to voice command, I could also add hand controls, able to identify and respond to the signal you give it - totally silent.” You tap your fingers on the table twice, “The only draw I can think of is having to memorize control signals.”
He thinks it over for a moment and shifts in his spot, “That’s even better.”
“I think it’ll be best to have both.” Your keyboard clicks under your fingers as you enter the ideas coming to you faster than you can get them down.
This is great. I’m not even thinking about-
Stop it.
“These are great, Konig, really. Anything else?”
Your encouragement makes him look away. You follow his stare as it darts to the side and then down to his notes. He places one hand on the table next to the notepad as he leans his weight onto it.
You briefly picture yourself between him and the table, his arm pinning you in as he towers over you, hunched to watch you like you’re his prey, chests so close they’re almost touching.
You quickly push the thought to the side, moving your attention back to your laptop. The only way to survive this meeting is to repress.
Repress your memories of what he looks like with his cock in his hand, arching his hips into the thrusts. Repress the sound of his moans and your name echoing clearly in your brain. Repress the guilt from the breach of privacy to the highest degree.
Please, just until we get through this.
You close your eyes and take a breath to collect yourself while he’s not looking.
He’s got other things written on the notepad, you’re sure. Unless the two ideas he’d already pitched managed to take up the whole page. “No.”
Your brows furrow, the question leaving your mouth without thought, “You’re sure?”
He pauses. You can tell he’s sitting on a thought, but you don’t know what.
“It’s okay. Like I said, it’s just a prototype. You won’t hurt my feelings.”
He straightens his posture before he speaks, “No. That was all I could think of.” He swallows, “If you feel I didn’t make good on my promise, I can fix it.”
“No, no!” You say with urgency, a hand shaking in his direction, “Those ideas you gave me were perfect. I just wanted to make sure you weren’t holding back on me.” A weak laugh escapes you. “I can’t stress how helpful this has been. I’m glad we’re doing this.”
Konig looks at you, those intimidating eyes staring at you from across the table. You wish you could see his face, hoping it would give some insight on what was going through his head. Even if you could you don’t think you’d be able to maintain eye contact.
He knows.
No, he doesn’t, shut up.
“I’ll keep thinking.” He says definitively, like he’s trying to right a wrong.
“You’ve only had it for a week,” you reassure, “Besides, you’ve given me plenty to work with.” You force a smile at him, not even caring how it’s coming off because you’re just hoping not to choke on the tension suffocating the room. You wonder if he feels it too, or if it’s all in your head.
He nods, and you look to your laptop in a futile attempt to thwart the dread suddenly pooling in your stomach. You’re reminded of what you’ve done when he crosses his arms, and your eyes are drawn to the same bicep on the arm that he used to pleasure himself. You’re picturing how it looks under his uniform, comparing it to your filthy reference. Your heart quickens and you can’t help but take in his build, even from across the long lab table. You feel extra small sitting on your stool while he stands, arms still crossed, staring.
The air between you two is definitely weird. Him getting off to probably-not-you and you watching but him not knowing that you know will certainly fill the room with a tension unlike any other.
These drawn-out silences are smothering you, not knowing what goes on being his hood.
He looks disappointed in you.
He knows.
“How can I help you in the meantime?”
You can’t help but breathe a small sigh of relief. You were planning on taking him back out to shoot house, running a few more simulations, and having him give feedback on a few more overlays.
You scrap that plan, looking forward to expanding on his ideas while your synapses are still firing.
“Well, here’s my thoughts so far. Landmine identification, the coding for that will be easy. The device already has the scanning capability for obscured objects. All I have to do is enable the specific object for full-time recognition. The hard part will be testing. I’ll have to meet with weapons development to develop prop landmines for simulation.”
You glance at the notes on your laptop, “Voice control - easy. Mic’s already installed and all I would have to do is add speech-to-text recognition, repurpose the wrist control coding, and then…testing.” Your hand finds the side of your face as you think it over, “Well, I may need to sample voice lines from you and a couple of your friends…” You loosely gesture with the same hand as you continue, “But there may be workarounds to that. Put a pin in that.” You’re on a roll now, “Now the hand controls - that might be more complicated. I’m thinking I’ll have to start fresh with the hardware.” You look up, “Then again… it already has the scanning capacity. I could probably just teach the current model with software alone. But the coding will take some time to figure out.”
Your eyes find him again. He’s staring and as per usual you can’t decipher it.
“Y’know,” you continue with a smile, “You could help me come up with hand signals?”
He nods.
He doesn’t give you much to work with, does he?
“I’ll need references of your hands. To teach the AI, is that okay?”
He looks down in a way that makes you feel so, so ashamed. If he is hesitant about recordings of just his gloved hands, how would he feel if he found out about what you did? About the video living on your phone?
After a moment he looks back up at you, “I’ll do it.” His voice is stern as usual, always treating everything with importance, with determination.
You give him another shaky smile, “Might be awhile. Wanna sit?”
He pulls up a stool to his end of the table and you instruct him to put his earpiece on as you return to your software on the laptop, trying not to trigger the memory of the last time you watched his feed. You pretend to resync your devices, glad he can’t see your screen. A wave of shame washes over you.
You’re both collaborating for some time, you offering a prompt and him stiffly coming up with a corresponding hand command. You supervise his feed, having him tilt his hands so the AI has references from multiple angles.
The rest of the meeting is professional and you manage to steady your obsessive thoughts as best you can. It’s hard to observe his hands and not think about the video, about what you watched those same hands do.
About how those hands would feel mapping all of the curves of your body.
How they would feel gripping onto your hips as you rode him.
How they would feel sneaking up your thighs, teasing you.
Somehow, you make it.
Once you decide you’ve covered enough references, Konig heads out, and you hope to continue staving off your thoughts by wasting no time on incorporating his ideas into your design. You’re hoping to have a least one rough draft done before next week’s meeting, so you plan on hunkering down and forfeit your Friday night to work overtime.
—————————————————————-
It’s late in the evening, you can tell by how your eyes are burning, strained from staring at your bright screen. You don’t bother to check the actual time. It would just bum you out. Spending your Friday night working. Not that you would have been doing anything partially exciting if you hadn’t. You probably would have just spent your evening analyzing footage anyway, just of a more perverted genre.
When you finally call it quits, the base is barren. Everyone’s gone home or retired to their quarters by now. It’s quiet after the base door shuts behind you, automatic locks clicking into place.
You’re feeling better after today’s meeting with Konig. Somewhere in the previous week you’d convinced yourself that he knew, that at any moment he was going to report you, and at any moment security would bust in the lab to escort you out.
Seeing him again, even though you couldn’t always figure out what he was thinking, reassured you that he hadn’t somehow telepathically figured out your terrible deed. You don’t think he would have bothered to keep helping you, or even be able to look at you without disgust if he did know.
The meeting also re-sparked your feelings of arousal and excitement. The knot in your lower abdomen made its presence known again. So much more desirable than the spiraling guilt. You’ve come to lean into the highs, enjoying it while you can, knowing soon you’ll be feeling nauseous at the thought of yourself.
You don’t know how much longer you can take the rollercoaster. This week has been exhausting. You can’t believe you’ve allowed this man to root himself into your life, seeping into every facet.
Career, personal, sexual, and - well, you’re still in denial about the romantic feelings - but it’s incredibly impressive how this man was capable of fucking your entire life up for the small price of a couple of hours and a few exchanged words.
When you finally get to the privacy of your home, you let out an audible groan. Loud enough to carry but quiet enough to not disturb the neighbors. You just needed to let something out, it was getting frustrating.
You didn’t want to think anymore, you didn’t want to think!
“Long day at work?”
You freeze, and the sound of heavy footsteps fill your ears. Two armed soldiers with fully equipped gear stride from the depth of your home, meeting you at the entrance.
The sight of them alone is enough to intimidate you. You instinctively back against the locked door, your trunk obscuring a hand moving towards the doorknob.
“Tsk, tsk. I wouldn’t do that if I were you.”The taller of the two soldiers wears a black balaclava with a skull stitched in, his unimpressed stare drilling into you. You hear a click, and your wide eyes lock on to the gun in his hands, pointing right at your core.
You slowly release the doorknob, raising your shaking hands so they could see your palms.
“That’s good babe,” The other soldier speaks, but you’re too busy staring down the barrel of the gun to worry about it.
“I have to admit I’m a little upset with you,” Skull-face, as you appropriately nicknamed him, speaks as his eyes bore into you, “You kept us waiting a long time.”
He’s got some sort of thick accent laced into his grave voice, they both do, actually, but you’re too busy trying not to piss your pants to be able to place the region of origin.
A lump forms in your throat and you don’t think you‘ve taken a breath since you heard the unfamiliar voice in your home.
It’s violating. Them being here. Where you go after a long day of work to relax. Where you eat, sleep, shower, and just be.
How dare they defile and taint your safe place, where you hide away and pretend the exhausting world around you doesn’t exist?
You’re stuck, unsure of your next move and paralyzed with fear.
“We think you have something we want.”
You’re not sure what they mean, but you nod in compliance anyway. Not much you can say no to against two heavily armed men. You finally break your gaze away from the gun and take turns making frightful eye contact with them. You speak after a failed attempt of swallowing your fear, voice soft and broken, “Take it.”
They exchange a knowing glance with each other, the man with his face exposed bears an irritatingly smug grin.
Skull-face approaches you threateningly, sending fear down your spine and making your skin crawl as you push yourself further into the door. He leaves no room for pleas as he flips his gun around, the stock coming down on your forehead with enough force to knock you out cold.
————————————————————-
Your splitting headache was the first thing you registered when you came to. You can’t seem to concentrate, the fog in your brain so extreme your thoughts are incoherent. You let out a meek whimper as you attempt to open your eyes, the lights in the room stunning you and intensifying the throbbing pain in your skull. You wince, closing your eyes again to block it out.
A few moments pass - and the next thing you notice is the dryness in your mouth, unable to manage a swallow from the dehydration.
Water.
The only intelligible thought you’ve had after registering your discomfort, the instinctual desire stronger than the dizzy haze clouding your brain.
You lift your head, trying to move but your weakened muscles fail you.
Your muscles are weak, yes, but what’s really keeping you in place are the restraints.
You wince again, eyes scrunched to block out the brutal light as you tug to confirm you’re secured. Your wrists were bound behind you, your shoulders overextending around the back of the chair you were planted on. Your ankles bound to either leg of the chair. There’s another restraint wrapping under your arms and around the back of the chair, keeping your upper half upright. There’s a rashy burn underneath the coarse ropes that dug into your skin as your unconscious body leaned into it.
You let out another whimper from the back of your coarse throat. While you weren’t alert, every instinct within you notified you of the danger you were in.
Gotta move.
You try to squint one eye, but it still doesn’t save you from the flash intensity of your headache. Your eyes are stinging on top of it and you realize you’re partially blinded, vision blurred and doubled, stained red with your own blood.
You grit your teach, determined to figure out where you are. You try to concentrate your vision but to no avail.
Even so, you can tell you’re not at home, and you’re not on base.
Once you make your discovery, one that expended what little willpower you had, your eyes clench back shut, desperate to alleviate the migraine.
A secondary location, you thought to yourself through the pain, I’m fucked.
You can’t hear anything, the ringing in your ears deafening you.
You let out one more defeated whine before resting your chin on your chest, pinching your eyes closed.
You have no idea how long you drift in and out of consciousness for. During the brief moments you come to, you’re so disoriented you can’t make sense of your thoughts, and that coupled with the debilitating pain in your head is unnerving enough to make you cry tears of pure confusion.
It’s your neck snapping back to follow the hair yanking on your scalp that jolts you awake, and try to open your eyes to find the threat but they’re still not working as they should. Underneath the debilitating ringing, you can hear the sound of muffled male voices, unable to make out what they’re saying.
You gave up.
You were wounded & trapped, and in nature that meant a death sentence. You were in no shape to properly defend yourself. Couldn’t see, couldn’t hear, couldn’t move, couldn’t think.
You were as done as the toast made from your own designs.
After wincing, your eyes screwed shut, you go limp and give in to the man physically controlling you like a sadistic puppeteer.
The muffled voices are louder, you still can’t make out their words but you can tell they’re having some sort of argument. They’re yelling at each other, and your scalp becomes collateral as the one tightens his grip on your hair to match his escalated volume
He’s right in your ear now and it’s not helping with the headache.
Just hurry it up, You manage through the haze, just hurry it up and put me out of my misery.
He throws your head forward to the position it was in before, slumped over as much as the ropes would allow with your chin pointed to the ground. The force rattles your skull in a way that makes you see a searing white behind your eyelids. What little water you had left in you was escaping through your swollen eyes lids and down tear-stained cheeks.
Just kill me, please.
——————————————————-
When you come to again, you’re no longer sitting. You’re flat on your back. Your neck secured so your head is in line with your spine. Your headache takes the front stage but the pain has noticeably subsided. You try to open your eyes again, but the lights above you are still excruciating.
You let out a low moan and shut your eyes again.
Your ears still ring, but a good portion of your hearing has returned to you. You hear your name, followed by, “are you awake?”
You grunt in response, unable to form sentences.
“Can you open your eyes for me?”
You wince, trying to shake your head but unable. Instead, you grunt again before parting your lips. You tried to say, “Lights,” but your voice is so hoarse it comes out broken and cracked.
“What is it?”
You try and clear your throat, putting all your power into your strained voice, “Lights.”
They understand, and while you still can’t hear the flick of the switch, you can tell from behind your eyelids they’ve been shut off.
You try to mutter a “Thank you,” but give up a quarter of the way through.
You slowly open your eyes, still burning but blood wiped away from them. Your vision is still blurry, but no longer doubled.
“Do you remember what happened?”
You try to shake your head, but can’t. So you force a weak, “No.”
“Do you know where you are?”
“No.”
“Do you know what today’s date is?”
You just grunt, closing your eyes again. You didn’t know the answer but you were too fed up with the questions to respond.
“Can you see?”
You grunt again.
“Okay, how ‘bout this? Can you wiggle your fingers for me?”
You try to lift your arm in the direction of the voice but your action is cut short, your arm jerked still by a restraint on your wrist. You open and close your fingers slowly at the maximum range the restraint will allow.
“How ‘bout your toes?”
Your toes move slightly, your calves aching at even such a mild movement.
“Good, thank you. How’s the hearing?”
Kill me or leave me alone, you think.
You eventually freeze the owner of voice out, finally leaving you alone to rest.
The next few days are a miserable, confusing blur. Somewhere along the way you’re informed you’re in medical, being treated for your extreme concussion. No skull fracture, thankfully, but they suspect the bruising is severe if it was enough to knock you unconscious.
The concussion had scrambled you good, and you were not nearly as sharp as you usually are.
It took you a whole five days, not that you could keep track of the passing time, before you realized that you were not at medical on your base.
You were in medical, restrained to a hospital bed-
in enemy care.
————————————————————
There was nothing you could do. Restrained to your bed, sedated with painkillers when they thought you were becoming too active.
“To help you rest.” They told you, but you couldn't trust a word that came out of their mouths.
Medics are supposed to be neutral, bound to an ethical code to heal the injured, enemy or not. That didn’t stop some medics from harboring grudges after years of patching up their own soldier’s brutal wounds of war.
The next time the medicine wears off for a long amount of time, with no medics in sight, you conveniently get visitors, the soldiers that had visited you in your home.
The events had been beaten out of you, but the traumatic event had seeped somewhere deeper into your psyche, and you knew deep down you were in trouble at the mere sight of them.
Skull-face especially, you don’t know how or why, but your intuition tells you he’s responsible for this. “Ready to answer some questions? Or do you need me to put you back to sleep?”
You can tell by the sharp edge in his voice he doesn’t mean the painkillers.
“Maybe I’d be able to answer your questions if you hadn’t given me brain damage.” Your patience is running thin, and an ember ignites a flame inside you, “Who knows what information you knocked out of me.” You stare directly into his eyes, brows furrowed, the tone of your voice inviting trouble in.
He already took everything away from you. At this point you don’t care if he puts you under. You’re begging him too. Every time you wake up you just want to go back to sleep. You don’t want to deal with it, any of it.
Skull-face makes a move to advance but the maskless soldier stops him by putting an arm out, laying it firmly across his to hold him back.
You don’t flinch, eyes now staring down the soldier with a stubbled jaw and a mohawk that ended in a widow's peak. It’s a haircut you find highly unusual for a soldier.
Your face doesn’t crack, but you squint at the pair, “What do you even want to know? I don’t even work on the field, I have no information.”
Skull-face looks down at you, “Oh, we know.” That stupid accent and that stupid mask. If you weren’t restrained you think you would have launched at him, risking it all to get a few good scratches in with your fingernails. He reaches into his pocket and your eyes widen and your brows retract at what he pulls out.
Not a weapon, no.
It’s your design, the AI-powered earpiece, and your wrist remote.
Skull-face notices the realization that sets across your face, “Awh, looks like your memory is working fine after all.”
The flame inside you laps at your skin, your features flushing with anger. A lot at Skull-face, for being such a cocky prick, but mostly at yourself.
You did this yourself. You figured your day of reckoning would come eventually. That karma would bite you in the ass, and those who are affected by your designs will stand by and laugh at your demise.
You should have just stuck with redesigning kitchen appliances.
“Why don’t you show us what you’ve been cooking up, huh? We know you’ve been busy.”
The pair share another knowing glance, Mohawk snickering at your expense.
“How did you get that?” You ask through gritted teeth, knowing there’s no way they could have gotten into the highly secured base.
“What is it?” Skull-face asks.
“It’s an intercom.” You grit, the ache in your head pulsing. You miss the painkillers.
“Don’t lie.”
“I’m not.”
Mohawk steps in, “It’s okay, we all get embarrassed about our porn.”
You furrow your brows at him.
What the hell was he talking about?
Skull-face elbows him in the side, but it doesn’t keep his partner from smiling, “What is it?” He asks again.
“It’s an intercom.”
He’s getting sick of this game and he goes to step to you again but Mohawk cuts him short. “Ghost!” He says firmly.
Ghost, that was Skull-faces name. Or call sign, at least. You hated him, but you’d wished the other soldier would just let him at you. You didn’t care anymore.
Mohawk looks at you, “Look, there’s only so much I can do,” gesturing to Ghost, “Can’t we all just get along for a little bit, yeah?”
“How about you get along with deez nuts.” You laugh at your dumb joke, a laugh influenced by the daze of concussion and painkillers. You’re in hysteria, the laugh spills out and doesn’t let up. A release of built-up stress and frustration and anger that seeped out uncontrollably. Cackling at yourself for ending up in this situation. Only you would be capable of such hijinks. The laugh leaves you out of breath and with eyes full of tears. You don’t even care how it exacerbates the headache, or how you’re coming off as insane. It feels too good to let out the pent-up emotions, one way or another.
Your elation is cut short with a squeak as a gloved hand cuts harshly into your trachea. Ghost squeezes, roughly lifting you by the neck before shoving you back down on the hospital bed, his grip tighter than before. His voice is low and filled with caution, “I am getting sick of you.”
If you could breathe enough to talk, you’d tell him the feeling’s mutual. Instead you gag and sputter, which he takes as a sign that you are still getting air, and forces more of his weight onto your neck.
Your hands fail to defend yourself, the restraints holding you from fighting back. You’re getting close to blacking out, your laugh having already knock most of the wind out of you, but Mohawk pulls Ghost off of you, his hands firm on Ghost’s shoulders, “Stop! Stop.”
You involuntarily gasp, desperate for air, trying not to choke on your own spit. For a moment all you can hear is the blood rushing in your ears, flowing desperately to replace what Ghost restricted.
“Come on, last try.” He warns, and you can tell in your voice he means it.
You eye him carefully, still heaving for air. When you collect yourself, you speak, “I’ll show you.” You say, voice weak and breathy. You try to hold out your hand, but get stopped by the restraints.
Mohawk glances at Ghost, but Ghost keeps his stern eyes trained on you. He stays still for a moment, studying you with his arms crossed.
You roll your eyes, your chest still huffing as you reclaim your air, “Don’t trust me? Fine. I’ll walk you through it. Put the fucking bracelet on.”
He stares for another moment before taking the device from Mohawk. Must of handed it off so he could strangle you better.
He puts it on his wrist.
“Now tap the top.”
He follows your instructions, the wrist remote’s projection displaying above his wrist.
“Go ahead and open your settings.” You guide him through it, activating a few select overlays. “You got it. Now put the earpiece on.”
Ghost hesitates, looking over to his companion before he slowly reaches up underneath his balaclava, attaching the earpiece.
“Yep, and while you’re in there, go ahead and hit the button on the base.”
You watch as your design activates, displaying the transparent overlay over his eyes. He’s taken aback, unnerved by the unidentified design being so close to his vulnerable eyes.
“Ta-da!” You say sarcastically, showing off the full range of the restraints as you offer weak jazz hands. “So I’ve given you some information. Maybe you can give me a little information, yeah?”
He doesn’t say anything as he removes his hand from his mask.
“Where am I?” You ask.
“You know where you are.”
“How’d you find me?”
“We tracked your cell phone.”
You squint, “Why were you tracking my phone?” It doesn’t make any sense, there’s no way they would have been able to pin your cell phone information back to base. You don’t use it for work and there’s no way you had connected to the private Wi-Fi. It’s apples and oranges, you think.
Mohawk steps in front of Ghost and holds out his phone in your direction. It takes a moment for the image to come into view, your vision still impaired. When your eyes adjust, the screen shows you something that makes your blood turn cold.
It’s the video of Konig jerking off.
“Okay! Okay.” You wave your hands, “Just put that away, I get it.”
When you connected your phone to your software to transfer the recording of Konig, it briefly connected to your laptop.
Base internet has state-of-the-art firewalls and encryptions to prevent surveillance, hack-in, key logs.
Cell phones do not.
So they’ve been tracking you all week, and who knows what kind of information they were able to pull from your software? From your laptop, containing dozens of government secrets?
No, you think, they wouldn’t be going through the trouble of keeping me alive if they had the information on my laptop.
“What’s the matter? Embarrassed that gettin’ your rocks off caused a security breach in confidential information regarding warfare development?” Mohawk mocks.
Well, yes you were, now that he mentions it. You’re actually very worried your perverted little stunt will somehow end up forever immortalized in history books.
In the moment, though, your main concern was making sure that Konig wouldn’t find out, as you had started transmitting the device’s feed to him as soon as Ghost turned the earpiece on.
Part Three
#könig cod#könig mw2#konig x you#konig x reader#call of duty#fic#smut#konig fic#modern warefare ii#konig#konig call of duty#könig call of duty#könig#konig modern warfare#konig mw2#experimental#x reader#uhohwriting
664 notes
·
View notes
Text
Ensure FERPA Compliance with MeraSkool School Management Software
Ensure FERPA Compliance with MeraSkool School Management Software
Ensure FERPA Compliance with MeraSkool School Management Software
The Family Educational Rights and Privacy Act (FERPA) is a federal law that protects the privacy of student education records. For educational institutions, ensuring FERPA compliance is not just a legal obligation; it's a crucial aspect of building trust with parents and students. Choosing the right school management software can significantly simplify the process of maintaining compliance and safeguarding sensitive student data.
Understanding FERPA Compliance
FERPA grants parents and eligible students certain rights regarding their education records. These rights include:
The right to inspect and review their education records.
The right to request amendments to their education records.
The right to control the disclosure of personally identifiable information (PII) from their education records.
Non-compliance with FERPA can lead to severe penalties, including loss of federal funding. Therefore, selecting a school management system with robust security features and a commitment to data privacy is paramount.
MeraSkool: A FERPA-Compliant Solution
MeraSkool.com offers a comprehensive school management solution designed with FERPA compliance in mind. Our platform incorporates multiple layers of security to protect student data, including:
Data Encryption: MeraSkool employs advanced encryption techniques to protect student data both in transit and at rest.
Access Control: Our system uses role-based access control (RBAC), ensuring that only authorized personnel have access to sensitive information. This prevents unauthorized access and maintains data integrity.
Regular Security Audits: We conduct regular security audits and penetration testing to identify and address any potential vulnerabilities.
Data Backup and Recovery: MeraSkool provides robust data backup and recovery mechanisms to ensure data availability in case of any unforeseen circumstances. This safeguards against data loss and ensures business continuity.
Compliance Certifications: We are actively pursuing relevant compliance certifications to further demonstrate our commitment to data security and privacy. (Note: Specific certifications should be listed here if available).
AI-Powered Insights and Data Security: MeraSkool leverages AI to optimize tasks and provide insights for operational efficiency, while robust data security protocols ensure privacy and regulatory compliance. (Learn More)
Key Features for FERPA Compliance
Several features within MeraSkool directly contribute to FERPA compliance:
1. Secure Student Management:
MeraSkool's student management module (learn more) allows schools to manage student enrollment, maintain detailed profiles, track attendance, and generate grade reports securely. The system ensures only authorized personnel can access sensitive student information, maintaining confidentiality.
2. Controlled Access to Records:
Our platform provides granular control over access to student records, ensuring that only authorized individuals—parents, teachers, and administrators—can view the appropriate information. This prevents unauthorized disclosure of PII.
3. Secure Fee Management:
MeraSkool's fee management module (learn more) supports creating fee structures, generating invoices, and enabling secure online payments. This functionality maintains financial transparency while securing sensitive financial data.
4. Robust Reporting and Analytics:
MeraSkool's reporting and analytics capabilities provide valuable insights into student performance, attendance, and other key metrics. This data is accessed through secure channels, adhering to FERPA guidelines.
5. Audit Trails:
(Note: If available, mention the existence and functionality of audit trails in MeraSkool. Audit trails record all actions performed on student data, providing a valuable tool for monitoring and ensuring accountability.)
6. Powerful Printable system:
MeraSkool offers a powerful printable system (learn more) allowing for secure downloading and printing of marksheets, results, ID cards, fee receipts, and other essential documents. This functionality helps maintain accurate records while ensuring data remains secure.
Additional Benefits of MeraSkool
Beyond FERPA compliance, MeraSkool provides numerous other benefits for schools:
Exam & Assignment Management: Create, schedule, and manage exams with different question formats. (Learn More)
Timetable and Attendance Management: Automated attendance tracking and timetable creation. (Learn More)
Realtime Notification: Realtime notifications powered by WhatsApp bot. (Learn More)
World-Class Support: 24/7 support and a 7-day new feature delivery commitment. (Learn More)
Simple to Use UI & UX: Intuitive design and seamless user experience. (Learn More)
Easy Onboarding with Excel Upload: Effortless integration and seamless transition. (Learn More)
MeraSkool's Commitment to Data Privacy
MeraSkool is committed to providing a secure and compliant platform for schools. We understand the importance of protecting student data and are dedicated to continually improving our security measures to meet the evolving demands of FERPA and other relevant regulations.
Contact us today to learn more about how MeraSkool can help your school maintain FERPA compliance and streamline its operations.
Note: This information is for general guidance only and does not constitute legal advice. Consult with legal counsel to ensure your school's full compliance with FERPA.
#FERPA compliance#school management software#student privacy#data security#MeraSkool#educational software#online learning#school administration#data encryption#access control#security audits#FERPA regulations#data protection
0 notes
Text

Let’s get into the details. Musk’s staffers have been caught plugging external hard drives into federal agency systems and reportedly locking others out of private rooms to perform—who knows what actions. This behavior violates key cybersecurity laws under FISMA and NIST guidelines, which are designed to protect sensitive federal information. Here’s why this is a serious problem.
Federal systems are strictly regulated, allowing only approved devices to connect. Unauthorized external drives can introduce viruses, ransomware, or other harmful software that may compromise entire networks and disrupt essential operations. This puts system stability and continuity of services at risk, endangering critical infrastructure.
These devices could also be used to steal or damage critical information, including personal data for millions of Americans—such as Social Security recipients and taxpayers. Unauthorized access creates significant vulnerabilities, exposing sensitive data to the risk of cyberattacks. Such attacks could cripple vital services and compromise the privacy and safety of millions of people.
Additionally, federal agencies have strict access controls to prevent unauthorized data manipulation or theft. When unauthorized devices are connected, these protections are bypassed, allowing unauthorized users to potentially alter or extract sensitive data. This undermines system integrity and opens the door to both internal and external threats.
External drives also often lack essential security features, such as encryption and antivirus scanning, making them vulnerable to cybercriminal exploitation. These security gaps further increase the risk of data breaches and system compromise, which can have far-reaching consequences.
Federal systems handle trillions of dollars in payments and manage personal data for millions of U.S. citizens. By bypassing cybersecurity laws and protocols, Musk’s staffers are putting these systems—and the public—at serious risk. This activity is illegal, reckless, and unacceptable. Immediate oversight and intervention are necessary to stop these violations!
42 notes
·
View notes
Text
Following a White House edict effectively banning federal employees from disclosing their personal pronouns in email signatures, sources within multiple federal agencies say pronouns are now being systemically blocked across multiple email clients and other software.
WIRED confirmed various automated efforts with employees at the United States Agency for International Development (USAID), the Environmental Protection Agency (EPA), the General Services Administration (GSA), the US Department of Agriculture, and the Centers for Disease Control and Prevention (CDC).
The employees spoke to WIRED on condition of anonymity, citing fears of retaliation.
Multiple agency directors sent emails over the weekend telling staff that, due to President Donald Trump’s executive order, their offices would be removing the pronoun capability from Office 365. Employees were told they’d also need to remove pronouns from their email signatures in order to comply with the directive.
A staffer at USAID says the formal deactivation of their ability to list pronouns occurred last week, in response to executive orders defining sexes issued by President Trump on his first day in office. A GSA staffer says pronouns were wiped from employees’ email signatures after hours on Friday and were also no longer visible in Slack, the workplace messaging app. At the CDC, there used to be a section for employees to share their pronouns on their Teams profiles, another workplace app. That field no longer exists.
Reached for comment, the White House transferred WIRED to OPM communications director McLaurine Pinover, who pointed to January 29 memorandum ordering agencies to disable all features “that prompt users for their pronouns.”
The ban on personal pronouns follows sweeping efforts by the White House to eliminate programs that encourage diversity and social justice within the federal government, as well as other references to “diversity, equity, and inclusion” in federal employees’ discourse.
In a striking example of the policy in action, an image surfaced last week of a wall being painted over at the Federal Bureau of Investigation's Quantico, Virginia, academy due to it listing "diversity" among the bureau's core values. (According to an email from the FBI’s Office of Integrity and Compliance obtained by Mother Jones, the bureau no longer counts "diversity" among its core values.)
The Trump administration began a radical campaign last week aimed at inducing members of the federal workforce to leave their jobs ahead of threatened reductions. The effort is spearheaded by Elon Musk, leader of the so-called Department of Government Efficiency (DOGE), a task force that has effectively seized control of several federal agencies and sensitive government systems with apparent clearance from the White House.
WIRED reported last week that Musk’s outfit had effectively taken over the Office of Personnel Management, the US government’s human resources department. In this and other efforts, it is employing inexperienced young engineers whose ages range from 19 to 24—many of whom, public records show, are former interns or have been affiliated with Musk-aligned companies.
OPM emailed federal workers on January 28 with a “deferred resignation offer,” sparking widespread confusion among federal workers. (DOGE’s own new HR chief was unable to answer basic questions about the offer in a contentious staff meeting last week, WIRED reported.) In an email to staff Sunday evening, OPM clarified whether the deferred resignation program complied with existing privacy laws. “Yes,” read the answer. “The deferred resignation program uses only basic contact information about federal employees, like name and government address, along with short, voluntary email responses. The information is stored on government systems. To the extent that the Privacy Act applies, all information relevant to the program is covered by existing OPM System Records Notices.”
Multiple agency sources told WIRED last week that several of Musk's lieutenants had been granted access to key computer systems controlled by the GSA, an independent agency tasked by Congress with overseeing federal buildings and providing equipment, supplies, and IT support across the government.
31 notes
·
View notes
Text
CDA 230 bans Facebook from blocking interoperable tools

I'm touring my new, nationally bestselling novel The Bezzle! Catch me TONIGHT (May 2) in WINNIPEG, then TOMORROW (May 3) in CALGARY, then SATURDAY (May 4) in VANCOUVER, then onto Tartu, Estonia, and beyond!

Section 230 of the Communications Decency Act is the most widely misunderstood technology law in the world, which is wild, given that it's only 26 words long!
https://www.techdirt.com/2020/06/23/hello-youve-been-referred-here-because-youre-wrong-about-section-230-communications-decency-act/
CDA 230 isn't a gift to big tech. It's literally the only reason that tech companies don't censor on anything we write that might offend some litigious creep. Without CDA 230, there'd be no #MeToo. Hell, without CDA 230, just hosting a private message board where two friends get into serious beef could expose to you an avalanche of legal liability.
CDA 230 is the only part of a much broader, wildly unconstitutional law that survived a 1996 Supreme Court challenge. We don't spend a lot of time talking about all those other parts of the CDA, but there's actually some really cool stuff left in the bill that no one's really paid attention to:
https://www.aclu.org/legal-document/supreme-court-decision-striking-down-cda
One of those little-regarded sections of CDA 230 is part (c)(2)(b), which broadly immunizes anyone who makes a tool that helps internet users block content they don't want to see.
Enter the Knight First Amendment Institute at Columbia University and their client, Ethan Zuckerman, an internet pioneer turned academic at U Mass Amherst. Knight has filed a lawsuit on Zuckerman's behalf, seeking assurance that Zuckerman (and others) can use browser automation tools to block, unfollow, and otherwise modify the feeds Facebook delivers to its users:
https://knightcolumbia.org/documents/gu63ujqj8o
If Zuckerman is successful, he will set a precedent that allows toolsmiths to provide internet users with a wide variety of automation tools that customize the information they see online. That's something that Facebook bitterly opposes.
Facebook has a long history of attacking startups and individual developers who release tools that let users customize their feed. They shut down Friendly Browser, a third-party Facebook client that blocked trackers and customized your feed:
https://www.eff.org/deeplinks/2020/11/once-again-facebook-using-privacy-sword-kill-independent-innovation
Then in in 2021, Facebook's lawyers terrorized a software developer named Louis Barclay in retaliation for a tool called "Unfollow Everything," that autopiloted your browser to click through all the laborious steps needed to unfollow all the accounts you were subscribed to, and permanently banned Unfollow Everywhere's developer, Louis Barclay:
https://slate.com/technology/2021/10/facebook-unfollow-everything-cease-desist.html
Now, Zuckerman is developing "Unfollow Everything 2.0," an even richer version of Barclay's tool.
This rich record of legal bullying gives Zuckerman and his lawyers at Knight something important: "standing" – the right to bring a case. They argue that a browser automation tool that helps you control your feeds is covered by CDA(c)(2)(b), and that Facebook can't legally threaten the developer of such a tool with liability for violating the Computer Fraud and Abuse Act, the Digital Millennium Copyright Act, or the other legal weapons it wields against this kind of "adversarial interoperability."
Writing for Wired, Knight First Amendment Institute at Columbia University speaks to a variety of experts – including my EFF colleague Sophia Cope – who broadly endorse the very clever legal tactic Zuckerman and Knight are bringing to the court.
I'm very excited about this myself. "Adversarial interop" – modding a product or service without permission from its maker – is hugely important to disenshittifying the internet and forestalling future attempts to reenshittify it. From third-party ink cartridges to compatible replacement parts for mobile devices to alternative clients and firmware to ad- and tracker-blockers, adversarial interop is how internet users defend themselves against unilateral changes to services and products they rely on:
https://www.eff.org/deeplinks/2019/10/adversarial-interoperability
Now, all that said, a court victory here won't necessarily mean that Facebook can't block interoperability tools. Facebook still has the unilateral right to terminate its users' accounts. They could kick off Zuckerman. They could kick off his lawyers from the Knight Institute. They could permanently ban any user who uses Unfollow Everything 2.0.
Obviously, that kind of nuclear option could prove very unpopular for a company that is the very definition of "too big to care." But Unfollow Everything 2.0 and the lawsuit don't exist in a vacuum. The fight against Big Tech has a lot of tactical diversity: EU regulations, antitrust investigations, state laws, tinkerers and toolsmiths like Zuckerman, and impact litigation lawyers coming up with cool legal theories.
Together, they represent a multi-front war on the very idea that four billion people should have their digital lives controlled by an unaccountable billionaire man-child whose major technological achievement was making a website where he and his creepy friends could nonconsensually rate the fuckability of their fellow Harvard undergrads.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/05/02/kaiju-v-kaiju/#cda-230-c-2-b

Image: D-Kuru (modified): https://commons.wikimedia.org/wiki/File:MSI_Bravo_17_(0017FK-007)-USB-C_port_large_PNr%C2%B00761.jpg
Minette Lontsie (modified): https://commons.wikimedia.org/wiki/File:Facebook_Headquarters.jpg
CC BY-SA 4.0: https://creativecommons.org/licenses/by-sa/4.0/deed.en
#pluralistic#ethan zuckerman#cda 230#interoperability#content moderation#composable moderation#unfollow everything#meta#facebook#knight first amendment initiative#u mass amherst#cfaa
246 notes
·
View notes
Note
oooo okay omg imagine lyla knows miguel likes you. he won’t admit it but he does. and she purposely downloads this ‘love meter software. and whenever miguel talks to you at hq, the meter goes like “warning: you have reached maximum love limit, love overflowing” and red lights start flashing and everybody starts panicking 😭😭😭
OMG this reminds of “operation: true love” on webtoon 🤭🤭!!
lyla is known to be silly and eccentric at times always knowing how to rile miguel up or use things she knows about him against him just for the fun of it. we know that lyla likes to take pictures of miguel with filters + recording him at his most embarrassing moments.
lyla is smart, obviously an AI, who you would think wouldn’t have a personality or feeling emotions but she does. she has a mind of her own. miguel had confided in her that he had a crush on you. “oh my god! no way miguel~ who knew you were capable of such feelings!” she said snickering while she had secretly recorded their conversation maybe to one day show you proof that miguel had also liked you back. lyla is the confidant of the both of you. she knows you like him but miguel doesn’t know that you like him back. so she had devised this plan in hopes miguel and you got the memo.
she had installed a software called “love meter” secretly behind miguel’s back. one day she wanted to do a test run on the software as you were present, chatting up with miguel in the control room. miles, gwen,pavitr, hobie, and margo were messing around in the background while letting you and miguel talk.
“warning: you have reached maximum love limit, love overflowing” it appeared on all the screens of the control room, which indicated miguel’s heart beat was rising by just being near you. the little love meter was at 100. the alarm then resounded throughout the HQ, as red flashing lights flickered throughout the entire multi-sectioned building.
everyone’s heads quickly turned towards miguel and you. miguel was about to speak but was soon got off by the gang’s comments and laughter. you couldn’t help but stare at miguel feeling your cheeks heat up feeling a tad bit shy. you were genuinely shocked by the turn of evidentes.
“i knew he had a crush on y/n!” gwen laughed while pointing a finger at miguel. hobie would definitely chime in as well, “who knew the big boss man is whipped for you,” directing his voice at you. miles and margo, laughed, literally everyone did while pav went up to miguel and you saying he had sensed the romantic tension from a mile away.
“LYLA! what did you do!?” miguel said embarrassed while he was BEET RED. he was really flustered. he was caught red handed and he wasn’t sure if you were about to reject him on the spot or not.
“sorry pal! i didn’t know it would do that…” lyla nervously giggled while she glanced at you then at miguel. you couldn’t help but laugh at the whole situation because of the way the other spider people came bustling in the control room thinking it was a problem. of course, it wasn’t it was just very hilarious to you that you found out that miguel has a crush on you TOO.
“guys-um, it isn’t an emergency—just go back to whatever you were doing.” he said as he stumbled over his words and told everyone to leave. he wasn’t necessarily mad but he was more so embarrassed. everyone was dismissed even your favorite teenagers had all
left but they respected your privacy. miguel would shake his head as he ran his hands through his hair directly his attention to you but not being able to hold eye contact. quickly, lyla vanished into thin air but she could still hear everything.
“i’m sorry about what lyla did.” he came close to you as he placed an apologetic hand on your shoulder with a gentle touch. you could tell he was blushing. you could tell he was into you in the way his eyes would casually go to you lips then to your eyes. he did it a couple times.
“it’s fine miguel,” you inches closer to him closing the distance between the two of you, “i wanted to tell you that i also like you too!” you giggled while you made it your effort to maintain eye contact with him. you were a very shy person but you weren’t one to stumble on your words. miguel was dumbfounded but at the same time very relief that you liked him back too.
“you like me too??” he gently stroked your cheek, “you like someone like me?” you heart aches a bit whenever he would put himself down like that as if he felt he was incapable of being loved. you gently placed a hand on top of the hand he was caressing your cheek with as you leaned into his touch.
“miguel, of course. you’re capable of being cared for, thought of, and loved.” you embraced him as you wrapped your arms around his waist. he was stunned a bit not knowing what to do since he hasn’t hugged someone in such a long time. but slowly and carefully he wrapped his arms around your upper shoulders as he placed his chin on top of your head. with one hand he carded your hair lovingly, “i promise to be the best man i can be for you, if you allow me to.”
“yes of course.” everyone in the HQ was so happy for you and they were also happy that miguel’s behavior improved drastically for the better, all thanks to you.
#spiderman atsv#miguel o'hara#spider man: across the spider verse#miguel o’hara x reader#miguel spiderman#spider person#spidersona#atsv x reader#miguel o’hara x y/n#ao3 works#miguel o’hara fanfiction#miguel x reader#atsv miguel#atsv#spiderman 2099#spider woman#atsv headcanons#🌱 lin writes
478 notes
·
View notes