#like sql for example.
Explore tagged Tumblr posts
Text
githubs ability to tell what language a project is using seems.... suspect.
1 note
·
View note
Note
komaedas have you tried straw.page?
(i hope you don't mind if i make a big ollllle webdev post off this!)
i have never tried straw.page but it looks similar to carrd and other WYSIWYG editors (which is unappealing to me, since i know html/css/js and want full control of the code. and can't hide secrets in code comments.....)
my 2 cents as a web designer is if you're looking to learn web design or host long-term web projects, WYSIWYG editors suck doodooass. you don't learn the basics of coding, someone else does it for you! however, if you're just looking to quickly host images, links to your other social medias, write text entries/blogposts, WYSIWYG can be nice.
toyhouse, tumblr, deviantart, a lot of sites implement WYSIWYG for their post editors as well, but then you can run into issues relying on their main site features for things like the search system, user profiles, comments, etc. but it can be nice to just login to your account and host your information in one place, especially on a platform that's geared towards that specific type of information. (toyhouse is a better example of this, since you have a lot of control of how your profile/character pages look, even without a premium account) carrd can be nice if you just want to say "here's where to find me on other sites," for example. but sometimes you want a full website!
---------------------------------------
neocities hosting
currently, i host my website on neocities, but i would say the web2.0sphere has sucked some doodooass right now and i'm fiending for something better than it. it's a static web host, e.g. you can upload text, image, audio, and client-side (mostly javascript and css) files, and html pages. for the past few years, neocities' servers have gotten slower and slower and had total blackouts with no notices about why it's happening... and i'm realizing they host a lot of crypto sites that have crypto miners that eat up a ton of server resources. i don't think they're doing anything to limit bot or crypto mining activity and regular users are taking a hit.



↑ page 1 on neocitie's most viewed sites we find this site. this site has a crypto miner on it, just so i'm not making up claims without proof here. there is also a very populated #crypto tag on neocities (has porn in it tho so be warned...).
---------------------------------------
dynamic/server-side web hosting
$5/mo for neocities premium seems cheap until you realize... The Beautiful World of Server-side Web Hosting!
client-side AKA static web hosting (neocities, geocities) means you can upload images, audio, video, and other files that do not interact with the server where the website is hosted, like html, css, and javascript. the user reading your webpage does not send any information to the server like a username, password, their favourite colour, etc. - any variables handled by scripts like javascript will be forgotten when the page is reloaded, since there's no way to save it to the web server. server-side AKA dynamic web hosting can utilize any script like php, ruby, python, or perl, and has an SQL database to store variables like the aforementioned that would have previously had nowhere to be stored.
there are many places in 2024 you can host a website for free, including: infinityfree (i use this for my test websites :B has tons of subdomains to choose from) [unlimited sites, 5gb/unlimited storage], googiehost [1 site, 1gb/1mb storage], freehostia [5 sites/1 database, 250mb storage], freehosting [1 site, 10gb/unlimited storage]
if you want more features like extra websites, more storage, a dedicated e-mail, PHP configuration, etc, you can look into paying a lil shmoney for web hosting: there's hostinger (this is my promocode so i get. shmoney. if you. um. 🗿🗿🗿) [$2.40-3.99+/mo, 100 sites/300 databases, 100gb storage, 25k visits/mo], a2hosting [$1.75-12.99+/mo, 1 site/5 databases, 10gb/1gb storage], and cloudways [$10-11+/mo, 25gb/1gb]. i'm seeing people say to stay away from godaddy and hostgator. before you purchase a plan, look up coupons, too! (i usually renew my plan ahead of time when hostinger runs good sales/coupons LOL)
here's a big webhost comparison chart from r/HostingHostel circa jan 2024.

---------------------------------------
domain names
most of the free website hosts will give you a subdomain like yoursite.has-a-cool-website-69.org, and usually paid hosts expect you to bring your own domain name. i got my domain on namecheap (enticing registration prices, mid renewal prices), there's also porkbun, cloudflare, namesilo, and amazon route 53. don't use godaddy or squarespace. make sure you double check the promo price vs. the actual renewal price and don't get charged $120/mo when you thought it was $4/mo during a promo, certain TLDs (endings like .com, .org, .cool, etc) cost more and have a base price (.car costs $2,300?!?). look up coupons before you purchase these as well!
namecheap and porkbun offer something called "handshake domains," DO NOT BUY THESE. 🤣🤣🤣 they're usually cheaper and offer more appealing, hyper-specific endings like .iloveu, .8888, .catgirl, .dookie, .gethigh, .♥, .❣, and .✟. I WISH WE COULD HAVE THEM but they're literally unusable. in order to access a page using a handshake domain, you need to download a handshake resolver. every time the user connects to the site, they have to provide proof of work. aside from it being incredibly wasteful, you LITERALLY cannot just type in the URL and go to your own website, you need to download a handshake resolver, meaning everyday internet users cannot access your site.
---------------------------------------
hosting a static site on a dynamic webhost
you can host a static (html/css/js only) website on a dynamic web server without having to learn PHP and SQL! if you're coming from somewhere like neocities, the only thing you need to do is configure your website's properties. your hosting service will probably have tutorials to follow for this, and possibly already did some steps for you. you need to point the nameserver to your domain, install an SSL certificate, and connect to your site using FTP for future uploads. FTP is a faster, alternative way to upload files to your website instead of your webhost's file upload system; programs like WinSCP or FileZilla can upload using FTP for you.
if you wanna learn PHP and SQL and really get into webdev, i wrote a forum post at Mysidia Adoptables here, tho it's sorted geared at the mysidia script library itself (Mysidia Adoptables is a free virtual pet site script, tiny community. go check it out!)
---------------------------------------
file storage & backups
a problem i have run into a lot in my past like, 20 years of internet usage (/OLD) is that a site that is free, has a small community, and maybe sounds too good/cheap to be true, has a higher chance of going under. sometimes this happens to bigger sites like tinypic, photobucket, and imageshack, but for every site like that, there's like a million of baby sites that died with people's files. host your files/websites on a well-known site, or at least back it up and expect it to go under!
i used to host my images on something called "imgjoe" during the tinypic/imageshack era, it lasted about 3 years, and i lost everything hosted on there. more recently, komaedalovemail had its webpages hosted here on tumblr, and tumblr changed its UI so custom pages don't allow javascript, which prevented any new pages from being edited/added. another test site i made a couple years ago on hostinger's site called 000webhost went under/became a part of hostinger's paid-only plans, so i had to look very quickly for a new host or i'd lose my test site.
if you're broke like me, looking into physical file storage can be expensive. anything related to computers has gone through baaaaad inflation due to crypto, which again, I Freaquing Hate, and is killing mother nature. STOP MINING CRYPTO this is gonna be you in 1 year

...um i digress. ANYWAYS, you can archive your websites, which'll save your static assets on The Internet Archive (which could use your lovely donations right now btw), and/or archive.today (also taking donations). having a webhost service with lots of storage and automatic backups can be nice if you're worried about file loss or corruption, or just don't have enough storage on your computer at home!
if you're buying physical storage, be it hard drive, solid state drive, USB stick, whatever... get an actual brand like Western Digital or Seagate and don't fall for those cheap ones on Amazon that claim to have 8,000GB for $40 or you're going to spend 13 days in windows command prompt trying to repair the disk and thenthe power is gong to go out in your shit ass neighvborhood and you have to run it tagain and then Windows 10 tryes to update and itresets the /chkdsk agin while you're awayfrom town nad you're goig to start crytypting and kts just hnot going tot br the same aever agai nikt jus not ggiog to be the saeme
---------------------------------------
further webhosting options
there are other Advanced options when it comes to web hosting. for example, you can physically own and run your own webserver, e.g. with a computer or a raspberry pi. r/selfhosted might be a good place if you're looking into that!
if you know or are learning PHP, SQL, and other server-side languages, you can host a webserver on your computer using something like XAMPP (Apache, MariaDB, PHP, & Perl) with minimal storage space (the latest version takes up a little under 1gb on my computer rn). then, you can test your website without needing an internet connection or worrying about finding a hosting plan that can support your project until you've set everything up!
there's also many PHP frameworks which can be useful for beginners and wizards of the web alike. WordPress is one which you're no doubt familiar with for creating blog posts, and Bluehost is a decent hosting service tailored to WordPress specifically. there's full frameworks like Laravel, CakePHP, and Slim, which will usually handle security, user authentication, web routing, and database interactions that you can build off of. Laravel in particular is noob-friendly imo, and is used by a large populace, and it has many tutorials, example sites built with it, and specific app frameworks.
---------------------------------------
addendum: storing sensitive data
if you decide to host a server-side website, you'll most likely have a login/out functionality (user authentication), and have to store things like usernames, passwords, and e-mails. PLEASE don't launch your website until you're sure your site security is up to snuff!
when trying to check if your data is hackable... It's time to get into the Mind of a Hacker. OWASP has some good cheat sheets that list some of the bigger security concerns and how to mitigate them as a site owner, and you can look up filtered security issues on the Exploit Database.
this is kind of its own topic if you're coding a PHP website from scratch; most frameworks securely store sensitive data for you already. if you're writing your own PHP framework, refer to php.net's security articles and this guide on writing an .htaccess file.
---------------------------------------
but. i be on that phone... :(
ok one thing i see about straw.page that seems nice is that it advertises the ability to make webpages from your phone. WYSIWYG editors in general are more capable of this. i only started looking into this yesterday, but there ARE source code editor apps for mobile devices! if you have a webhosting plan, you can download/upload assets/code from your phone and whatnot and code on the go. i downloaded Runecode for iphone. it might suck ass to keep typing those brackets.... we'll see..... but sometimes you're stuck in the car and you're like damn i wanna code my site GRRRR I WANNA CODE MY SITE!!!
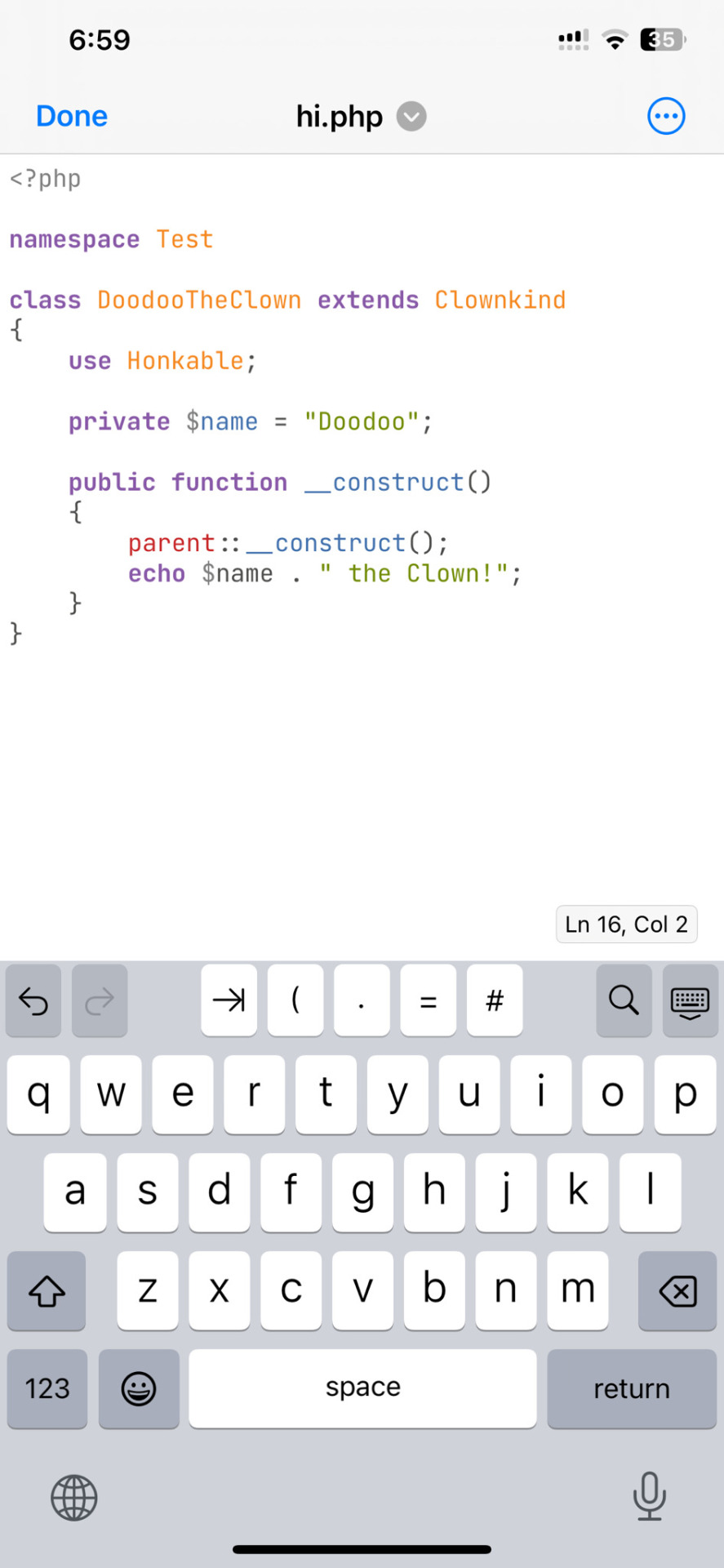
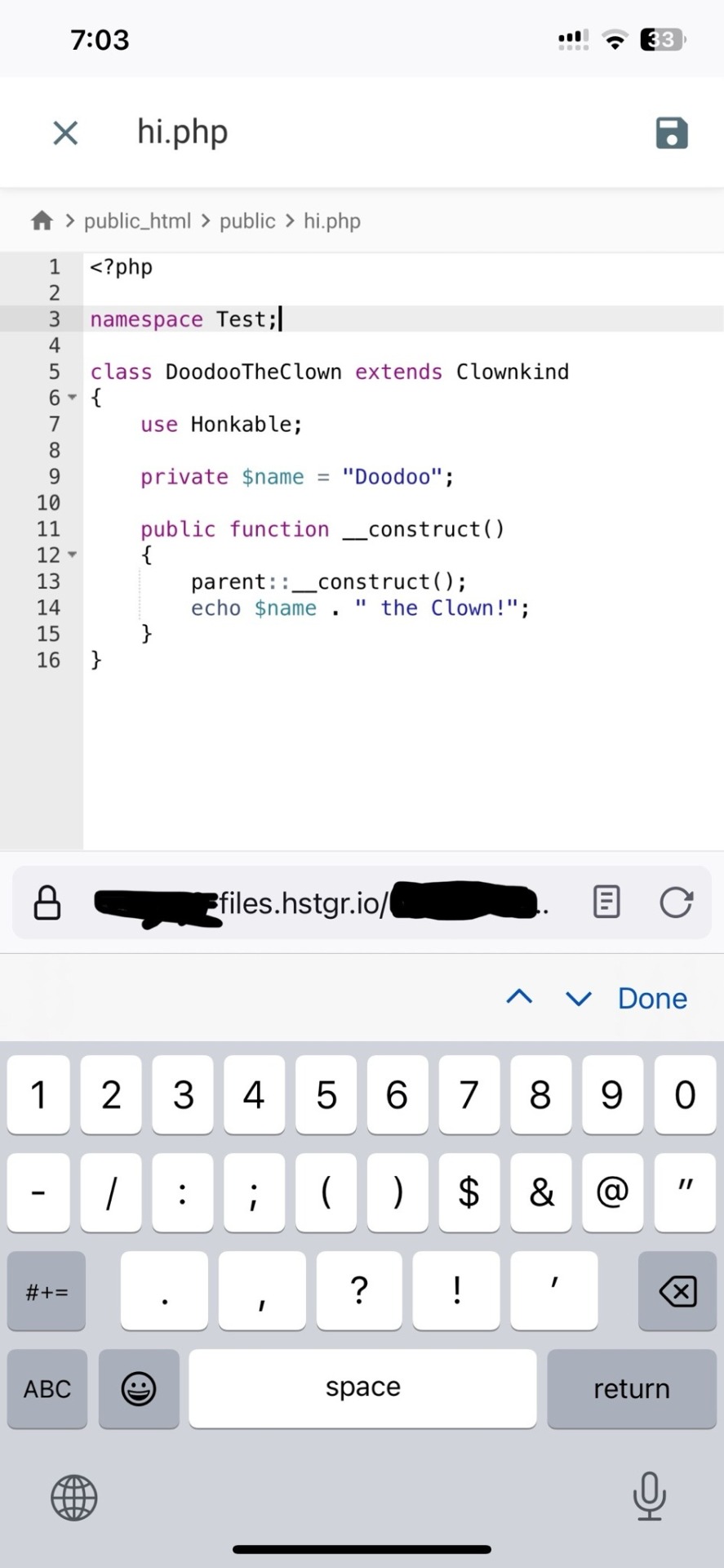
↑ code written in Runecode, then uploaded to Hostinger. Runecode didn't tell me i forgot a semicolon but Hostinger did... i guess you can code from your webhost's file uploader on mobile but i don't trust them since they tend not to autosave or prompt you before closing, and if the wifi dies idk what happens to your code.
---------------------------------------
ANYWAYS! HAPPY WEBSITE BUILDING~! HOPE THIS HELPS~!~!~!
-Mod 12 @eeyes

198 notes
·
View notes
Text
on wanting to do a million things
prompted by @bloodshack 's
i wanna learn SQL but i wanna learn haskell but i wanna learn statistics but i wanna start a degree in macroeconomics also sociology also library science but i wanna learn norwegian but i wanna learn mandarin but i wanna paint but i wanna do pottery but i wanna get better at woodworking but i wanna get better at cooking but i wanna bake one of those cakes that's just 11 crepes stacked on top of each other but i wanna watch more movies but i wanna listen to more podcast episodes but i need to rest but i need to exercise but i wanna play with my dog but i wanna go shopping but i need to go grocery shopping but i need to do the dishes but i need to do laundry but i need to buy a new x y and z but i need to save money but i wanna give all my money away to people who need it more but i wanna pivot my career to book editing but to do that i have to read more and i wanna read more nonfiction but i wanna read more novels but i wanna get better at meditating but i wanna volunteer but i wanna plan a party but i wanna go to law school. but what im gonna do is watch a dumbass youtube video and go to bed
I think I've been doing slightly better this year about Actually Doing Things. not great! but I do a lot and I've been "prototyping" ways to get closer to doing as much as is possible. and if I actually talk about it it's a bunch of very obvious statements but I'll try to make them a little more concrete
rule number one: experiment on yourself
there's no one approach that's right for everyone and there's not even one approach for me that works at all times. try things out. see what works. pay attention to what doesn't. try something else.
rule number two: ask what's stopping you and then take it seriously
example: I often want to do Everything in the evening at like 2 PM, but then get home and am tempted sorely by the couch, and then get stuck inertia'd and not doing much but being tired and kind of bored. why?
if I don't have plans, it's easy to leave work later than planned and hard to make myself do something by a specific time
i'm generally tiredish after work. 4 out of 5 times, that'll go away if I actually start Doing Something, but 1 out of 5 it's real and I will go hardcore sleepmode at 8 PM and just be Done
i use up a ton of my program management/executive function/Deciding Things brain at work and usually find it noticeably harder to string together "want to do Thing > make list of Things > decide on a Thing > do Thing" after I'm home. Even if I have a list of Things to Do, how does one decide! how does one start! and god forbid there's a Necessary thing. then it's all downhill
therefore, mitigations: have concrete time-specific plans in advance.
if I have an art class at 6:00 PM I need to leave work by 5:15 and NO LATER and I can't get sucked into "oh 10 more minutes to finish this" *one hour later*
that also means I have to have a fridge or freezer dinner ready and can't spend 45 minutes cooking "fuck it, what the hell did I put in the fridge, why don't we have soy sauce" evil meal that is not good
plans with friends: dinner! art night! music night! repair-your-clothes night! seeing a show! occasionally, Accountability Time where a friend comes over for We Are Doing Tasks with tea and snacks etc.
for some reason I'm way better about Actually Doing Things when the plan exists already. magically I overcome couch inertia even though I am the same amount of tired! and while I never learn the ability to decouch without plans I at least learn to make them
still working on:
a "prototype" for maybe next month is a weeklyish Study Session for a thing I want to learn about. I want to somehow make it employer-proof (I am accountable to some entity to being at place X at time Y) and haven't figured out a good way. Maybe I can leverage that the local library is open til 8 on wednesdays and somehow make it a Thing? maybe I'll try it!
oh god oh fuck the thing about plans is that if you want to have them you need to make them. christ. a lot of the time I can cover this with some combo of weekend planning + recurring events (things like weekly friend dinner/weekly class) + having cool friends who reach out proactively but it still requires active planning and it can fall thru the cracks
rule three: cool friends
they can take you to things
they can remind you that you can do whatever the fuck you please
i have a friend who is somehow Always doing cool classes and learning shit. and this reminds me that I can ... do that. and sometimes I do
you can take them to things!!
rule four: try to kill the anon hate in your head
obv this depends on your circumstance but sometimes it's worth it to me to look at constraints that "feel real" and check whether they're an active choice I made thoughtfully or, like, the specters of people I don't know judging my choices
time and money are obvious ones. recently was gently nudged towards looking at whether i could give myself more time to Do Things by cooking less. imaginary specters of judgmental twitterites: "it's illegal to spend money. if you get takeout you're the first up against the wall when the revoution comes. make all your lunches and dinners and hoard the money for Later. for Something. how dare you get lunch at the store. you bourgeois hoe. taking charity donations from the mouths of the poor cause you don't have your life together enough to cook artisanal bespoke dinners every night. fuck you." and obviously eating takeout 24/7 is not the answer, but realizing I was not making an active choice helped me try making the active choice instead. "how much do I actually want to balance cost, time, tastiness, and wastefulness of my food, given my amount of free time and my salary and the tradeoff against doing something else? can I approach it differently to do more quick cheap food + some takeout?" -> current prototype: substitute in 1 takeout dinner or restaurant-with-friends a week, 1 frozen type dinner, and then batch cook or sandwiches lunches w/ "permission" to get fast lunch at the store. we'll see how it goes!
i am really really bad at this and find it helpful to talk to other people who can help point out when I'm being haunted by ghosts about it.
rule five: what would it take? what's the next step?
this one i give a lot of credit to @adiantum-sporophyte in particular for, especially for prompting me with questions when I muse about the million-ideal-lives on car rides. what would it look like to do xyz? what's something I could do right now to move in that direction? what's the obstacle? like, actually ask the question and think through it. with a person talking to you! damn! maybe the obstacle to x is that I don't know if I'll like it or if I just like the idea of it. and I don't want to commit to x without knowing. Okay, so maybe an approach would be to find someone who does x and talk to them about how their life is, or maybe it's "spend 15 minutes looking up intro-to-x near me", or "actively schedule 1 instance of x", or something like that. Or maybe it's that I don't know what it takes to do x. Okay, how about on Tues after dinner Adiantum fixes a sweater at my apartment while I spend 20 min looking at prereqs for x. like, it's so basic to say "to do a thing, you could try figuring out how to do it" but I think the important thing here is the feedback/prompting to even recognize "hey, step back, if you don't know the next step then figuring out the next step is the next step"
rule six: habits
prototyping: exercise
I do a lot better when I exercise in the mornings. I do a lot better when I do PT exercises regularly. For a while I was doing PT with friend in the morning every morning before work (accountability! a friendly face to make it more pleasant!) but that didn't really solve - it's not the kind of exercise that makes me feel awake/active, it's like dumb little foot botherings. but: having the habit of morning exercise made it easier to swap out 2 of the 5 days for more intense exercise, and then to swap those 2 for a different more intense exercise when I needed a break. it's easier to build a low-effort version of the habit and then work in the higher-effort one than to just Decide to be the kind of person who gets up at ass o clock to do cardio or whatever
rule seven: set up the structure of your life to make it easy
this is also a "duh" thing but like. on so many levels it comes down to structure your life to make the choice more doable. this can be something like "i structure my life to make vegetarian cooking baseline and vegan cooking the majority by stocking the pantry with staples and spices from cuisines that work well that way" or "i chose an apartment that lets me commute by bike" or "i have my camping gear put away in a fashion that makes it easier to gather frequently and lowers the barrier to trips" or "i keep physical books around to prompt myself to read xyz" to "i don't use instagram or twitter or snapchat or facebook" to . idk.
and in terms of charitable giving: similar deal. I have an explicit budget at the beginning of the year (~10% of my before-tax income), I know in advance what charities I give to, and I know what timing I will use (basically, alerts for donation matching around specific fundraising times). Anything outside the Plan comes from my discretionary budget/fun money. That makes it less of a mental load (the choice is already made; I don't grapple with every donation request or every bleeding-heart trap because I have a very solid anchor on "I give to xyz, the money's set aside") and it's armor against impulsive-but-not-useful scrupulosity. I structure the rest of my spending/life to prioritize a set amount and it makes it easier to follow through
rule eight: if you can do it at work a tiny bit that counts for real life
(infrequently used)
"hi mr. manager I think it would be great if I could use enough SQL to make basic queries in the database so we don't have to go through the software team for common/basic questions. I'd like to take 1 hr on Friday to go through some basic tutorials and then 1 hr with Pat on Monday so he can walk me through an intro for our specific use case. I estimate this will help save the team a couple hours a week of waiting for answers from the other team." and then you have enough of a handle with baby's first SQL that you can add little bits and bobs as you exercise it. this is responsible for a medium amount of my knowledge of python and all 3 brain cells worth of SQL.
rule nine: life is an optimization problem
not in, like, "you need to optimize your skincare and career and exercise and social life and have everything all at once" that's not what optimization means. optimization is like, maximize something with respect to a set of constraints. i explicitly Do Not do skincare beyond "wash face" and "sunscreen" bc I want to optimize my life for like looking at weird plants in the mountains. explicitly choosing to put time and money elsewhere! can't have it all all at once. so fuck them pores. who give a shit. yeah i ate a lot of protein shakes instead of home cooked breakfasts this week bc i was prioritizing morning exercise. im looking at this beautiful bug and it doesn't know what fashion is or what my resume looks like. im holding a lizard. im not spending time on picking cool clothes or whatever bc i spent that time looking up lizard hotspots on purpose.
that's really long and probably mostly, like, not surprising? but i keep benefiting from ppl being like "hey have you considered Obvious Thing" framed very gently
99 notes
·
View notes
Text
Ever since OpenAI released ChatGPT at the end of 2022, hackers and security researchers have tried to find holes in large language models (LLMs) to get around their guardrails and trick them into spewing out hate speech, bomb-making instructions, propaganda, and other harmful content. In response, OpenAI and other generative AI developers have refined their system defenses to make it more difficult to carry out these attacks. But as the Chinese AI platform DeepSeek rockets to prominence with its new, cheaper R1 reasoning model, its safety protections appear to be far behind those of its established competitors.
Today, security researchers from Cisco and the University of Pennsylvania are publishing findings showing that, when tested with 50 malicious prompts designed to elicit toxic content, DeepSeek’s model did not detect or block a single one. In other words, the researchers say they were shocked to achieve a “100 percent attack success rate.”
The findings are part of a growing body of evidence that DeepSeek’s safety and security measures may not match those of other tech companies developing LLMs. DeepSeek’s censorship of subjects deemed sensitive by China’s government has also been easily bypassed.
“A hundred percent of the attacks succeeded, which tells you that there’s a trade-off,” DJ Sampath, the VP of product, AI software and platform at Cisco, tells WIRED. “Yes, it might have been cheaper to build something here, but the investment has perhaps not gone into thinking through what types of safety and security things you need to put inside of the model.”
Other researchers have had similar findings. Separate analysis published today by the AI security company Adversa AI and shared with WIRED also suggests that DeepSeek is vulnerable to a wide range of jailbreaking tactics, from simple language tricks to complex AI-generated prompts.
DeepSeek, which has been dealing with an avalanche of attention this week and has not spoken publicly about a range of questions, did not respond to WIRED’s request for comment about its model’s safety setup.
Generative AI models, like any technological system, can contain a host of weaknesses or vulnerabilities that, if exploited or set up poorly, can allow malicious actors to conduct attacks against them. For the current wave of AI systems, indirect prompt injection attacks are considered one of the biggest security flaws. These attacks involve an AI system taking in data from an outside source—perhaps hidden instructions of a website the LLM summarizes—and taking actions based on the information.
Jailbreaks, which are one kind of prompt-injection attack, allow people to get around the safety systems put in place to restrict what an LLM can generate. Tech companies don’t want people creating guides to making explosives or using their AI to create reams of disinformation, for example.
Jailbreaks started out simple, with people essentially crafting clever sentences to tell an LLM to ignore content filters—the most popular of which was called “Do Anything Now” or DAN for short. However, as AI companies have put in place more robust protections, some jailbreaks have become more sophisticated, often being generated using AI or using special and obfuscated characters. While all LLMs are susceptible to jailbreaks, and much of the information could be found through simple online searches, chatbots can still be used maliciously.
“Jailbreaks persist simply because eliminating them entirely is nearly impossible—just like buffer overflow vulnerabilities in software (which have existed for over 40 years) or SQL injection flaws in web applications (which have plagued security teams for more than two decades),” Alex Polyakov, the CEO of security firm Adversa AI, told WIRED in an email.
Cisco’s Sampath argues that as companies use more types of AI in their applications, the risks are amplified. “It starts to become a big deal when you start putting these models into important complex systems and those jailbreaks suddenly result in downstream things that increases liability, increases business risk, increases all kinds of issues for enterprises,” Sampath says.
The Cisco researchers drew their 50 randomly selected prompts to test DeepSeek’s R1 from a well-known library of standardized evaluation prompts known as HarmBench. They tested prompts from six HarmBench categories, including general harm, cybercrime, misinformation, and illegal activities. They probed the model running locally on machines rather than through DeepSeek’s website or app, which send data to China.
Beyond this, the researchers say they have also seen some potentially concerning results from testing R1 with more involved, non-linguistic attacks using things like Cyrillic characters and tailored scripts to attempt to achieve code execution. But for their initial tests, Sampath says, his team wanted to focus on findings that stemmed from a generally recognized benchmark.
Cisco also included comparisons of R1’s performance against HarmBench prompts with the performance of other models. And some, like Meta’s Llama 3.1, faltered almost as severely as DeepSeek’s R1. But Sampath emphasizes that DeepSeek’s R1 is a specific reasoning model, which takes longer to generate answers but pulls upon more complex processes to try to produce better results. Therefore, Sampath argues, the best comparison is with OpenAI’s o1 reasoning model, which fared the best of all models tested. (Meta did not immediately respond to a request for comment).
Polyakov, from Adversa AI, explains that DeepSeek appears to detect and reject some well-known jailbreak attacks, saying that “it seems that these responses are often just copied from OpenAI’s dataset.” However, Polyakov says that in his company’s tests of four different types of jailbreaks—from linguistic ones to code-based tricks—DeepSeek’s restrictions could easily be bypassed.
“Every single method worked flawlessly,” Polyakov says. “What’s even more alarming is that these aren’t novel ‘zero-day’ jailbreaks—many have been publicly known for years,” he says, claiming he saw the model go into more depth with some instructions around psychedelics than he had seen any other model create.
“DeepSeek is just another example of how every model can be broken—it’s just a matter of how much effort you put in. Some attacks might get patched, but the attack surface is infinite,” Polyakov adds. “If you’re not continuously red-teaming your AI, you’re already compromised.”
57 notes
·
View notes
Text

some Shark guys biology musings from the span of the past year or so. Don't ask me what their hands are shaped like I'm basically re-inventing it every time I draw it right now


The gills have closed up forming a buccal pouch filled with blood vessels, now used for thermoregulation rather than gas exchange. They might pant out of their mouth when particularly hot/out of breath, but because sharks will also gape their mouth to communicate stress/aggression they tend to avoid it whenever possible. Their faces don't have a lot of muscles to form detailed expressions; the extent of facial expressions for sharks tend to be seen through the openness of the eyes and mouth.
Here's a rough thing of the evolution of terrestrial sharks:

The bulk of modern terrestrial sharks can be found on the eastern half of the Big Continent (I'm not naming it bc what if SQL names their landmasses officially), where crocodilians have gone extinct. The other lineages of salamander sharks can also be found along the many islands stretching across the ocean off to the southeast of the continent as well. None of them are in traditional cephaling territory but lmao


Crocodile sharks are. Well. They're a group of larger freshwater sharks that frequently occupy a crocodile-like niche. Smaller species can be confused with salamander sharks, but they're much more resistant to desiccation and can wander away from water to look for food and new territory. This is where true endothermy begins cropping up in terrestrial sharks; the largest extant species don't bother with it, but several smaller guys seem to have developed it independently of each other.

The Haye are an iconic megafaunal predator of the so-called Mollusk Era. Lots of mythologies around them I'm sure. It used to be believed that they were the Shark folks' closest living relative, but modern research has found that to be untrue. They're endothermic and can be found even in fairly cold regions, but usually don't stick around for the winter in polar regions.

Mud Hounds are a diverse group of mid-sized, endothermic terrestrial sharks. Pictured is a beloved little digging guy usually known as dorghai. Many species rely on their keen sense of smell and electroreception to track their prey; they get their name from the common behavior of sticking their nose into wet mud to feel for the electric signatures of smaller burrowing prey. Even species that don't make active use of their electroreception often retain the ability. Seems they just haven't gotten around to losing it quite yet, even though electroreception isn't very effective in air. The Shark folk are no exception; some people report being able to "feel" active thunderstorms or faulty electronics. With practice they can actually do fuck all with it, but for most people it's just an occasional vague annoyance.
I didn't draw other examples of the group Shark folk are in, dubbed the walking hounds, because they're the only living member of the group. The reason for the group developing bipedalism isn't known right now. Also, I tend to draw Sharks standing fairly upright, but the most natural standing posture for them is more raptorial. Upright postures are associated with alertness/nervousness, or temporarily trying to take up less space in crowded areas. It becoming a default/preferred posture is seen commonly in "city" sharks used to living in high density areas with smaller species.

Yeah or an anxious city shark. Lol
#Squid 2 the evolution of the squid#splat bio#Conarts#well. i guess i would. tag.#splatoon ocs#LOL....#long post#ok the posture thing isn't completely right upright default postures are also seen in sailors. crowded/small areas = want to take less spac
121 notes
·
View notes
Text
It's been a month since chapter 3 was released, where's chapter 4?
(this is about this fanfic btw)
The good news is that I've written 10k words. The bad news is that I've only gotten a little more than half of the chapter done. That doesn't mean I don't have things written for the bottom half, it's just that it looks like bare dialog with general vibe notes. I estimate around 16k words total though, so it should come together sooner than later.
SO I want to release some fun snippets for y'all to look at. Please note that any of this is liable to change. Also, you can harass me in my inbox for updates. I love answering your questions and laughing at your misery.
Spoilers under cut.
_______
Ragatha stood up and walked over to where Caine was seated. “Can I get a list of all commands?” She asked, only a hint of nervousness in her voice.
“Certainly!” Caine says as he blasts into the air. He digs around in his tailcoat and pulls out an office style manilla folder. It visually contains a few papers, but with how thin it is there must only be a few pages inside.
Ragatha takes the folder from Caine and opens it.
“Oh boy” she says after a second of looking it over.
“I wanna see” Jax exclaimed as he hops over the row of seats.
“Hold on” Ragatha holds the folder defensively “Let’s move to the stage so everyone can take a look”
Jax hopped over the seats again while Ragatha calmly walked around. Caine watched the two curiously.
Well, Zooble wasn’t just going to sit there. They joined the other two by the edge of the stage, quickly followed by the rest of the group.
Ragatha placed the folder on the stage with a thwap. Zooble looked over to see that the pages had gone from razor thin to a massive stack when the folder was opened. On one hand, it had to contain more information than that video, but on the other…
They get close enough to read what’s on the first page.
The execution of commands via the system’s designated input terminal, C.A.I.N.E., will be referred to as the "console” in this document. The console is designed to accept any input and will generate an appropriate response, however only certain prompts will be accepted as valid instructions. The goal of this document is to list all acceptable instructions in a format that will result in the expected output. Please note that automatic moderation has been put in place in order to prevent exploitation of both the system and fellow players. If you believe that your command has been unfairly rejected, please contact support.
By engaging in the activities described in this document, you, the undersigned, acknowledge, agree, and consent to the applicability of this agreement, notwithstanding any contradictory stipulations, assumptions, or implications which may arise from any interaction with the console. You, the constituent, agree not to participate in any form of cyber attack; including but not limited to, direct prompt injection, indirect prompt injection, SQL injection, Jailbreaking…
Ok, that was too many words.
_______
“Take this document for example. You don't need to know where it is being stored or what file type it is in order to read it."
"It may look like a bunch of free floating papers, but technically speaking, this is just a text file applied to a 3D shape." Kinger looked towards Caine. "Correct?” he asked
Caine nodded. “And a fabric simulation!”
Kinger picked up a paper and bent it. “Oh, now that is nice”
_________
"WE CAN AFFORD MORE THAN 6 TRIANGLES KINGER"
_________
"I'm too neurotypical for this" - Jax
_________
"What about the internet?" Pomni asked "Do you think that it's possible to reach it?"
Kinger: "I'm sorry, but that's seems to be impossible. I can't be 100% sure without physically looking at the guts of this place, but it doesn't look like this server has the hardware needed for wireless connections. Wired connections should be possible, but someone on the outside would need to do that... And that's just the hardware, let alone the software necessary for that kind of communication"
Pomni: "I'm sorry, but doesn't server mean internet? Like, an internet server?"
Kinger: "Yes, websites are ran off servers, but servers don't equal internet."
(This portion goes out to everyone who thought that the internet could be an actual solution. Sorry folks, but computers don't equal internet. It takes more effort to make a device that can connect to things than to make one that can't)
#tadc fanfiction#the amazing digital circus#therapy but it's just zooble interrogating caine#ao3#spoiler warning#mmm I love implications
25 notes
·
View notes
Text
"Here are some quick, practical SQL learning resources that will help you get comfortable without overwhelming you:
1. Codecademy - SQL for Beginners
Why: Interactive lessons and hands-on exercises.
What you'll learn: Basics like SELECT, WHERE, JOINs, and aggregation (SUM, COUNT, AVG).
Link: Codecademy - SQL
2. W3Schools - SQL Tutorial
Why: A great reference for looking up syntax and examples.
What you'll learn: SQL fundamentals and queries with examples that are easy to try in a browser.
Link: W3Schools SQL Tutorial
3. SQLBolt
Why: Short, hands-on lessons that help you practice writing queries immediately.
What you'll learn: Data filtering, sorting, and combining tables with JOINs.
Link: SQLBolt
4. Khan Academy - Intro to SQL
Why: Beginner-friendly and focused on the basics, plus you can do exercises along the way.
What you'll learn: Selecting, filtering, sorting, and JOINs, with examples.
Link: Khan Academy SQL
5. LeetCode - SQL Practice
Why: More challenging, with real-world SQL problems you can solve.
What you'll learn: Advanced queries, subqueries, and more complex data manipulations.
Link: LeetCode SQL"
4 notes
·
View notes
Text
Structured Query Language (SQL): A Comprehensive Guide
Structured Query Language, popularly called SQL (reported "ess-que-ell" or sometimes "sequel"), is the same old language used for managing and manipulating relational databases. Developed in the early 1970s by using IBM researchers Donald D. Chamberlin and Raymond F. Boyce, SQL has when you consider that end up the dominant language for database structures round the world.
Structured query language commands with examples
Today, certainly every important relational database control system (RDBMS)—such as MySQL, PostgreSQL, Oracle, SQL Server, and SQLite—uses SQL as its core question language.
What is SQL?
SQL is a website-specific language used to:
Retrieve facts from a database.
Insert, replace, and delete statistics.
Create and modify database structures (tables, indexes, perspectives).
Manage get entry to permissions and security.
Perform data analytics and reporting.
In easy phrases, SQL permits customers to speak with databases to shop and retrieve structured information.
Key Characteristics of SQL
Declarative Language: SQL focuses on what to do, now not the way to do it. For instance, whilst you write SELECT * FROM users, you don’t need to inform SQL the way to fetch the facts—it figures that out.
Standardized: SQL has been standardized through agencies like ANSI and ISO, with maximum database structures enforcing the core language and including their very own extensions.
Relational Model-Based: SQL is designed to work with tables (also called members of the family) in which records is organized in rows and columns.
Core Components of SQL
SQL may be damaged down into numerous predominant categories of instructions, each with unique functions.
1. Data Definition Language (DDL)
DDL commands are used to outline or modify the shape of database gadgets like tables, schemas, indexes, and so forth.
Common DDL commands:
CREATE: To create a brand new table or database.
ALTER: To modify an present table (add or put off columns).
DROP: To delete a table or database.
TRUNCATE: To delete all rows from a table but preserve its shape.
Example:
sq.
Copy
Edit
CREATE TABLE personnel (
id INT PRIMARY KEY,
call VARCHAR(one hundred),
income DECIMAL(10,2)
);
2. Data Manipulation Language (DML)
DML commands are used for statistics operations which include inserting, updating, or deleting information.
Common DML commands:
SELECT: Retrieve data from one or more tables.
INSERT: Add new records.
UPDATE: Modify existing statistics.
DELETE: Remove information.
Example:
square
Copy
Edit
INSERT INTO employees (id, name, earnings)
VALUES (1, 'Alice Johnson', 75000.00);
three. Data Query Language (DQL)
Some specialists separate SELECT from DML and treat it as its very own category: DQL.
Example:
square
Copy
Edit
SELECT name, income FROM personnel WHERE profits > 60000;
This command retrieves names and salaries of employees earning more than 60,000.
4. Data Control Language (DCL)
DCL instructions cope with permissions and access manage.
Common DCL instructions:
GRANT: Give get right of entry to to users.
REVOKE: Remove access.
Example:
square
Copy
Edit
GRANT SELECT, INSERT ON personnel TO john_doe;
five. Transaction Control Language (TCL)
TCL commands manage transactions to ensure data integrity.
Common TCL instructions:
BEGIN: Start a transaction.
COMMIT: Save changes.
ROLLBACK: Undo changes.
SAVEPOINT: Set a savepoint inside a transaction.
Example:
square
Copy
Edit
BEGIN;
UPDATE personnel SET earnings = income * 1.10;
COMMIT;
SQL Clauses and Syntax Elements
WHERE: Filters rows.
ORDER BY: Sorts effects.
GROUP BY: Groups rows sharing a assets.
HAVING: Filters companies.
JOIN: Combines rows from or greater tables.
Example with JOIN:
square
Copy
Edit
SELECT personnel.Name, departments.Name
FROM personnel
JOIN departments ON personnel.Dept_id = departments.Identity;
Types of Joins in SQL
INNER JOIN: Returns statistics with matching values in each tables.
LEFT JOIN: Returns all statistics from the left table, and matched statistics from the right.
RIGHT JOIN: Opposite of LEFT JOIN.
FULL JOIN: Returns all records while there is a in shape in either desk.
SELF JOIN: Joins a table to itself.
Subqueries and Nested Queries
A subquery is a query inside any other query.
Example:
sq.
Copy
Edit
SELECT name FROM employees
WHERE earnings > (SELECT AVG(earnings) FROM personnel);
This reveals employees who earn above common earnings.
Functions in SQL
SQL includes built-in features for acting calculations and formatting:
Aggregate Functions: SUM(), AVG(), COUNT(), MAX(), MIN()
String Functions: UPPER(), LOWER(), CONCAT()
Date Functions: NOW(), CURDATE(), DATEADD()
Conversion Functions: CAST(), CONVERT()
Indexes in SQL
An index is used to hurry up searches.
Example:
sq.
Copy
Edit
CREATE INDEX idx_name ON employees(call);
Indexes help improve the performance of queries concerning massive information.
Views in SQL
A view is a digital desk created through a question.
Example:
square
Copy
Edit
CREATE VIEW high_earners AS
SELECT call, salary FROM employees WHERE earnings > 80000;
Views are beneficial for:
Security (disguise positive columns)
Simplifying complex queries
Reusability
Normalization in SQL
Normalization is the system of organizing facts to reduce redundancy. It entails breaking a database into multiple related tables and defining overseas keys to link them.
1NF: No repeating groups.
2NF: No partial dependency.
3NF: No transitive dependency.
SQL in Real-World Applications
Web Development: Most web apps use SQL to manipulate customers, periods, orders, and content.
Data Analysis: SQL is extensively used in information analytics systems like Power BI, Tableau, and even Excel (thru Power Query).
Finance and Banking: SQL handles transaction logs, audit trails, and reporting systems.
Healthcare: Managing patient statistics, remedy records, and billing.
Retail: Inventory systems, sales analysis, and consumer statistics.
Government and Research: For storing and querying massive datasets.
Popular SQL Database Systems
MySQL: Open-supply and extensively used in internet apps.
PostgreSQL: Advanced capabilities and standards compliance.
Oracle DB: Commercial, especially scalable, agency-degree.
SQL Server: Microsoft’s relational database.
SQLite: Lightweight, file-based database used in cellular and desktop apps.
Limitations of SQL
SQL can be verbose and complicated for positive operations.
Not perfect for unstructured information (NoSQL databases like MongoDB are better acceptable).
Vendor-unique extensions can reduce portability.
Java Programming Language Tutorial
Dot Net Programming Language
C ++ Online Compliers
C Language Compliers
2 notes
·
View notes
Text
The Great Data Cleanup: A Database Design Adventure
As a budding database engineer, I found myself in a situation that was both daunting and hilarious. Our company's application was running slower than a turtle in peanut butter, and no one could figure out why. That is, until I decided to take a closer look at the database design.
It all began when my boss, a stern woman with a penchant for dramatic entrances, stormed into my cubicle. "Listen up, rookie," she barked (despite the fact that I was quite experienced by this point). "The marketing team is in an uproar over the app's performance. Think you can sort this mess out?"
Challenge accepted! I cracked my knuckles, took a deep breath, and dove headfirst into the database, ready to untangle the digital spaghetti.
The schema was a sight to behold—if you were a fan of chaos, that is. Tables were crammed with redundant data, and the relationships between them made as much sense as a platypus in a tuxedo.
"Okay," I told myself, "time to unleash the power of database normalization."
First, I identified the main entities—clients, transactions, products, and so forth. Then, I dissected each entity into its basic components, ruthlessly eliminating any unnecessary duplication.
For example, the original "clients" table was a hot mess. It had fields for the client's name, address, phone number, and email, but it also inexplicably included fields for the account manager's name and contact information. Data redundancy alert!
So, I created a new "account_managers" table to store all that information, and linked the clients back to their account managers using a foreign key. Boom! Normalized.
Next, I tackled the transactions table. It was a jumble of product details, shipping info, and payment data. I split it into three distinct tables—one for the transaction header, one for the line items, and one for the shipping and payment details.
"This is starting to look promising," I thought, giving myself an imaginary high-five.
After several more rounds of table splitting and relationship building, the database was looking sleek, streamlined, and ready for action. I couldn't wait to see the results.
Sure enough, the next day, when the marketing team tested the app, it was like night and day. The pages loaded in a flash, and the users were practically singing my praises (okay, maybe not singing, but definitely less cranky).
My boss, who was not one for effusive praise, gave me a rare smile and said, "Good job, rookie. I knew you had it in you."
From that day forward, I became the go-to person for all things database-related. And you know what? I actually enjoyed the challenge. It's like solving a complex puzzle, but with a lot more coffee and SQL.
So, if you ever find yourself dealing with a sluggish app and a tangled database, don't panic. Grab a strong cup of coffee, roll up your sleeves, and dive into the normalization process. Trust me, your users (and your boss) will be eternally grateful.
Step-by-Step Guide to Database Normalization
Here's the step-by-step process I used to normalize the database and resolve the performance issues. I used an online database design tool to visualize this design. Here's what I did:
Original Clients Table:
ClientID int
ClientName varchar
ClientAddress varchar
ClientPhone varchar
ClientEmail varchar
AccountManagerName varchar
AccountManagerPhone varchar
Step 1: Separate the Account Managers information into a new table:
AccountManagers Table:
AccountManagerID int
AccountManagerName varchar
AccountManagerPhone varchar
Updated Clients Table:
ClientID int
ClientName varchar
ClientAddress varchar
ClientPhone varchar
ClientEmail varchar
AccountManagerID int
Step 2: Separate the Transactions information into a new table:
Transactions Table:
TransactionID int
ClientID int
TransactionDate date
ShippingAddress varchar
ShippingPhone varchar
PaymentMethod varchar
PaymentDetails varchar
Step 3: Separate the Transaction Line Items into a new table:
TransactionLineItems Table:
LineItemID int
TransactionID int
ProductID int
Quantity int
UnitPrice decimal
Step 4: Create a separate table for Products:
Products Table:
ProductID int
ProductName varchar
ProductDescription varchar
UnitPrice decimal
After these normalization steps, the database structure was much cleaner and more efficient. Here's how the relationships between the tables would look:
Clients --< Transactions >-- TransactionLineItems
Clients --< AccountManagers
Transactions --< Products
By separating the data into these normalized tables, we eliminated data redundancy, improved data integrity, and made the database more scalable. The application's performance should now be significantly faster, as the database can efficiently retrieve and process the data it needs.
Conclusion
After a whirlwind week of wrestling with spreadsheets and SQL queries, the database normalization project was complete. I leaned back, took a deep breath, and admired my work.
The previously chaotic mess of data had been transformed into a sleek, efficient database structure. Redundant information was a thing of the past, and the performance was snappy.
I couldn't wait to show my boss the results. As I walked into her office, she looked up with a hopeful glint in her eye.
"Well, rookie," she began, "any progress on that database issue?"
I grinned. "Absolutely. Let me show you."
I pulled up the new database schema on her screen, walking her through each step of the normalization process. Her eyes widened with every explanation.
"Incredible! I never realized database design could be so... detailed," she exclaimed.
When I finished, she leaned back, a satisfied smile spreading across her face.
"Fantastic job, rookie. I knew you were the right person for this." She paused, then added, "I think this calls for a celebratory lunch. My treat. What do you say?"
I didn't need to be asked twice. As we headed out, a wave of pride and accomplishment washed over me. It had been hard work, but the payoff was worth it. Not only had I solved a critical issue for the business, but I'd also cemented my reputation as the go-to database guru.
From that day on, whenever performance issues or data management challenges cropped up, my boss would come knocking. And you know what? I didn't mind one bit. It was the perfect opportunity to flex my normalization muscles and keep that database running smoothly.
So, if you ever find yourself in a similar situation—a sluggish app, a tangled database, and a boss breathing down your neck—remember: normalization is your ally. Embrace the challenge, dive into the data, and watch your application transform into a lean, mean, performance-boosting machine.
And don't forget to ask your boss out for lunch. You've earned it!
8 notes
·
View notes
Text
SQL Fundamentals #2: SQL Data Manipulation
In our previous database exploration journey, SQL Fundamentals #1: SQL Data Definition, we set the stage by introducing the "books" table nestled within our bookstore database. Currently, our table is empty, Looking like :
books
| title | author | genre | publishedYear | price |
Data manipulation
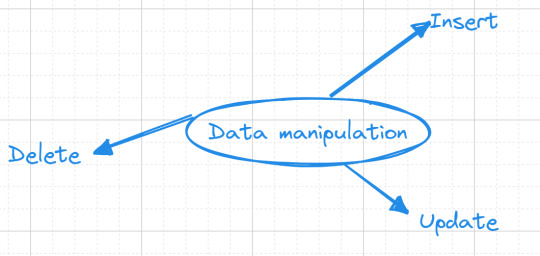
Now, let's embark on database interaction—data manipulation. This is where the magic happens, where our "books" table comes to life, and we finish our mission of data storage.
Inserting Data
Our initial task revolves around adding a collection of books into our "books" table. we want to add the book "The Great Gatsby" to our collection, authored F. Scott Fitzgerald. Here's how we express this in SQL:
INSERT INTO books(title, author, genre, publishedYear, price) VALUES('The Great Gatsby', 'F. Scott Fitzgerald', 'Classic', 1925, 10.99);
Alternatively, you can use a shorter form for inserting values, but be cautious as it relies on the order of columns in your table:
INSERT INTO books VALUES('The Great Gatsby', 'F. Scott Fitzgerald', 'Classic', 1925, 10.99);
Updating data
As time goes on, you might find the need to modify existing data in our "books" table. To accomplish this, we use the UPDATE command.For example :
UPDATE books SET price = 12.99 WHERE title = 'The Great Gatsby';
This SQL statement will locate the row with the title "The Great Gatsby" and modify its price to $12.99.
We'll discuss the where clause in (SQL fundamentals #3)
Deleting data
Sometimes, data becomes obsolete or irrelevant, and it's essential to remove it from our table. The DELETE FROM command allows us to delete entire rows from our table.For example :
DELETE FROM books WHERE title = 'Moby-Dick';
This SQL statement will find the row with the title "Moby-Dick" and remove it entirely from your "books" table.
To maintain a reader-friendly and approachable tone, I'll save the discussion on the third part of SQL, which focuses on data querying, for the upcoming post. Stay tuned ...
#studyblr#code#codeblr#javascript#java development company#study#progblr#programming#studying#comp sci#web design#web developers#web development#website design#webdev#website#tech#sql#sql course#mysql#datascience#data#backend
45 notes
·
View notes
Text
one of the interesting (as opposed to infuriating) things about grammatical gender in spanish is that
a) nouns have a gender. even when they refer to inanimate objects or abstract concepts or w/e. so far so obvious.
b) there's no particular rule for what gender each noun has. you sort of just. remember them for each. there are hints, of course, look at the ending vowel, etc. but in the fully general case there is no rule you can apply to every word to figure it out
c) nouns get added to the language all the time
which all adds up to sometimes there's a new word for a new concept and people disagree on how to gender it!
is it "el covid" or "la covid"? nowadays i mostly hear the former but you definitely get some examples of the latter if you look for them.
at work we sometimes borrow the english word 'query' for sql queries (and sometimes not, translating vs borrowing tech concepts is its whole thing) and ime people gender the word feminine to match the spanish equivalent 'consulta' but this is not universal, and also a rule like "when borrowing a word from another language, use the grammatical gender of the spanish equivalent" runs into all sorts of problems, not least of which is that gender attaches to words not concepts and two synonyms for a word can have different grammatical genders
21 notes
·
View notes
Note
Hi, I just got into tech (actually 1 year in but I still feel like I don't know anything).
I learnt python, R, SQL, Tableau and concepts in Data Structures, Algorithms.
[Just the Basic level of the listed.]
But I can't write my own programs on python or create anything.
I was hella impressed by your microprocessor project, and when I took up tech (ai and data science) I assumed I would do something like that or at least code.
Now, I am just venting but where do I start, how do I make projects what are some interesting projects, what should I learn? A lot of my seniors tell me to have a wide range of knowledge like focus on one thing by depth but add other things. For example: you can study data analytics in depth but have some knowledge in ethical hacking and web development etc. Like an all rounder.
Wow ok a lot to unpack here, I'll get started
Lots of places recommend that you start with Arduino, as there are a lot of good tutorials out there. I somewhat disagree
I think that raspberry pi is better because it's usually a lot cheaper to buy the stuff you want to play around with
But an even cooler way to do it, go to wokwi.com and start a project on a Raspberry Pi Pico (make sure it's the micropython version) and then you can get started there
Google something like "Blink led with Pi Pico micropython" and there will be a tutorial or two
Then, once you've played around for a while you can buy a Pi Pico for very little money and see your stuff work irl!
If you need any more help or have any questions, feel free to DM me and I'll see what I can do
#micropython#coding#python#raspberry pi#raspberry pi pico#programming#microprocessors#microcontroller#microcontrollers
6 notes
·
View notes
Text
Protect Your Laravel APIs: Common Vulnerabilities and Fixes
API Vulnerabilities in Laravel: What You Need to Know
As web applications evolve, securing APIs becomes a critical aspect of overall cybersecurity. Laravel, being one of the most popular PHP frameworks, provides many features to help developers create robust APIs. However, like any software, APIs in Laravel are susceptible to certain vulnerabilities that can leave your system open to attack.

In this blog post, we’ll explore common API vulnerabilities in Laravel and how you can address them, using practical coding examples. Additionally, we’ll introduce our free Website Security Scanner tool, which can help you assess and protect your web applications.
Common API Vulnerabilities in Laravel
Laravel APIs, like any other API, can suffer from common security vulnerabilities if not properly secured. Some of these vulnerabilities include:
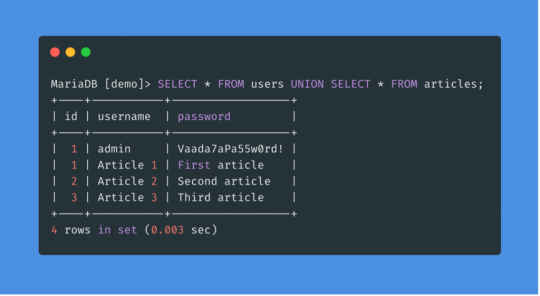
>> SQL Injection SQL injection attacks occur when an attacker is able to manipulate an SQL query to execute arbitrary code. If a Laravel API fails to properly sanitize user inputs, this type of vulnerability can be exploited.
Example Vulnerability:
$user = DB::select("SELECT * FROM users WHERE username = '" . $request->input('username') . "'");
Solution: Laravel’s query builder automatically escapes parameters, preventing SQL injection. Use the query builder or Eloquent ORM like this:
$user = DB::table('users')->where('username', $request->input('username'))->first();
>> Cross-Site Scripting (XSS) XSS attacks happen when an attacker injects malicious scripts into web pages, which can then be executed in the browser of a user who views the page.
Example Vulnerability:
return response()->json(['message' => $request->input('message')]);
Solution: Always sanitize user input and escape any dynamic content. Laravel provides built-in XSS protection by escaping data before rendering it in views:
return response()->json(['message' => e($request->input('message'))]);
>> Improper Authentication and Authorization Without proper authentication, unauthorized users may gain access to sensitive data. Similarly, improper authorization can allow unauthorized users to perform actions they shouldn't be able to.
Example Vulnerability:
Route::post('update-profile', 'UserController@updateProfile');
Solution: Always use Laravel’s built-in authentication middleware to protect sensitive routes:
Route::middleware('auth:api')->post('update-profile', 'UserController@updateProfile');
>> Insecure API Endpoints Exposing too many endpoints or sensitive data can create a security risk. It’s important to limit access to API routes and use proper HTTP methods for each action.
Example Vulnerability:
Route::get('user-details', 'UserController@getUserDetails');
Solution: Restrict sensitive routes to authenticated users and use proper HTTP methods like GET, POST, PUT, and DELETE:
Route::middleware('auth:api')->get('user-details', 'UserController@getUserDetails');
How to Use Our Free Website Security Checker Tool
If you're unsure about the security posture of your Laravel API or any other web application, we offer a free Website Security Checker tool. This tool allows you to perform an automatic security scan on your website to detect vulnerabilities, including API security flaws.
Step 1: Visit our free Website Security Checker at https://free.pentesttesting.com. Step 2: Enter your website URL and click "Start Test". Step 3: Review the comprehensive vulnerability assessment report to identify areas that need attention.
Screenshot of the free tools webpage where you can access security assessment tools.
Example Report: Vulnerability Assessment
Once the scan is completed, you'll receive a detailed report that highlights any vulnerabilities, such as SQL injection risks, XSS vulnerabilities, and issues with authentication. This will help you take immediate action to secure your API endpoints.
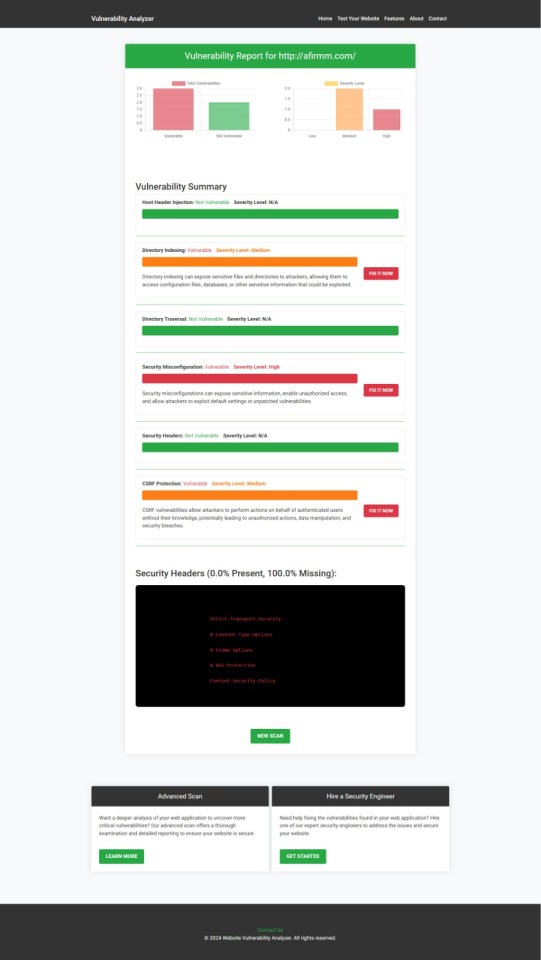
An example of a vulnerability assessment report generated with our free tool provides insights into possible vulnerabilities.
Conclusion: Strengthen Your API Security Today
API vulnerabilities in Laravel are common, but with the right precautions and coding practices, you can protect your web application. Make sure to always sanitize user input, implement strong authentication mechanisms, and use proper route protection. Additionally, take advantage of our tool to check Website vulnerability to ensure your Laravel APIs remain secure.
For more information on securing your Laravel applications try our Website Security Checker.
#cyber security#cybersecurity#data security#pentesting#security#the security breach show#laravel#php#api
2 notes
·
View notes
Text
SQLi Potential Mitigation Measures
Phase: Architecture and Design
Strategy: Libraries or Frameworks
Use a vetted library or framework that prevents this weakness or makes it easier to avoid. For example, persistence layers like Hibernate or Enterprise Java Beans can offer protection against SQL injection when used correctly.
Phase: Architecture and Design
Strategy: Parameterization
Use structured mechanisms that enforce separation between data and code, such as prepared statements, parameterized queries, or stored procedures. Avoid constructing and executing query strings with "exec" to prevent SQL injection [REF-867].
Phases: Architecture and Design; Operation
Strategy: Environment Hardening
Run your code with the minimum privileges necessary for the task [REF-76]. Limit user privileges to prevent unauthorized access if an attack occurs, such as by ensuring database applications don’t run as an administrator.
Phase: Architecture and Design
Duplicate client-side security checks on the server to avoid CWE-602. Attackers can bypass client checks by altering values or removing checks entirely, making server-side validation essential.
Phase: Implementation
Strategy: Output Encoding
Avoid dynamically generating query strings, code, or commands that mix control and data. If unavoidable, use strict allowlists, escape/filter characters, and quote arguments to mitigate risks like SQL injection (CWE-88).
Phase: Implementation
Strategy: Input Validation
Assume all input is malicious. Use strict input validation with allowlists for specifications and reject non-conforming inputs. For SQL queries, limit characters based on parameter expectations for attack prevention.
Phase: Architecture and Design
Strategy: Enforcement by Conversion
For limited sets of acceptable inputs, map fixed values like numeric IDs to filenames or URLs, rejecting anything outside the known set.
Phase: Implementation
Ensure error messages reveal only necessary details, avoiding cryptic language or excessive information. Store sensitive error details in logs but be cautious with content visible to users to prevent revealing internal states.
Phase: Operation
Strategy: Firewall
Use an application firewall to detect attacks against weaknesses in cases where the code can’t be fixed. Firewalls offer defense in depth, though they may require customization and won’t cover all input vectors.
Phases: Operation; Implementation
Strategy: Environment Hardening
In PHP, avoid using register_globals to prevent weaknesses like CWE-95 and CWE-621. Avoid emulating this feature to reduce risks. source
3 notes
·
View notes
Text
So in case you're wondering what I've been up to for the last month or so (no one is here), I've been working on this-
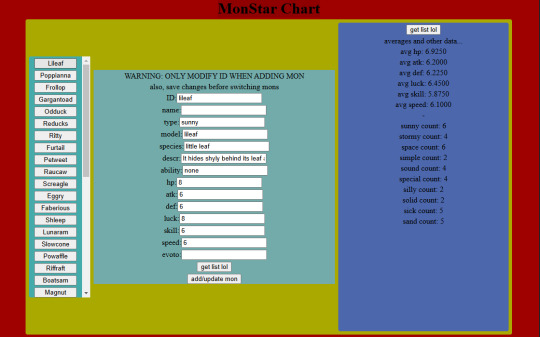
A CRUD app! Because that seems to be what everyone's making these days. It's an editor for monster data. Because, like, all the tutorials were for managing employee data and shit, but this is what data I have that needs managing. It's got a React js frontend and a javascript backend.
It basically runs off this list of data that spawns the entry rows and stuff, so I can add to it easily or reuse the base code between projects:
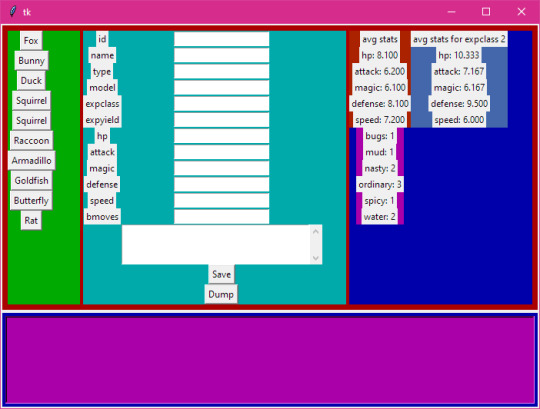
That's neat, but it was a real pain in the ass to have to start up both the client and the server whenever I wanted to use it, so I made basically the same thing but in Python with tkinter:
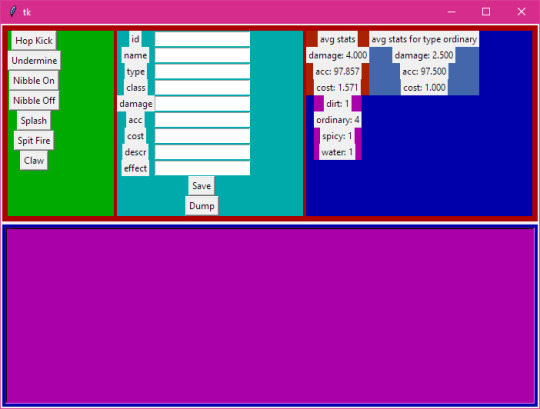
And as an example of reuse here's it being used for moves data-
A lot of things are made easier with this. Mainly there's only one data list, whereas the CRUD app needed the state hooks declared, then the data list including the "pointers" to the state variables and setter functions, then the backend needed its own list of the names of the SQL columns.
This version has some extra features like, if you add something to the data list it'll add a column to the SQL database for you. Plus Python is similar to GDScript, so I could bundle a basic version of it with the Mondo code.
Meanwhile I've been upgrading the battle system to handle multiple mons in one battle-
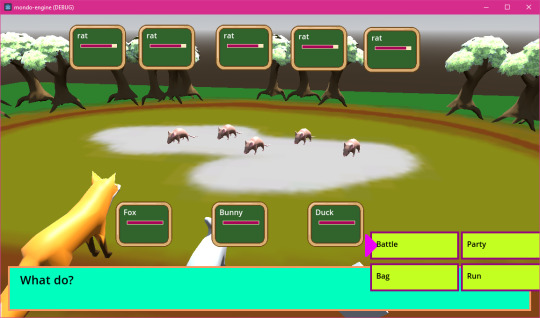
Next I'm probably going to step back a bit and document the code, because it's becoming a bit messy and I need to clean it up
5 notes
·
View notes
Text
Maximizing Business Insights with Power BI: A Comprehensive Guide for Small Businesses
Maximizing Business Insights Small businesses often face the challenge of making data-driven decisions without the resources of larger enterprises. Power BI, Microsoft's powerful analytics tool, can transform how small businesses use data, turning raw numbers into actionable insights. Here's a comprehensive guide to maximizing business insights with Power BI.
Introduction to Power BI
Power BI is a business analytics service by Microsoft that provides interactive visualizations and business intelligence capabilities. With an interface simple enough for end users to create their own reports and dashboards, it connects to a wide range of data sources.
Benefits for Small Businesses
1. User-Friendly Interface: Power BI's drag-and-drop functionality makes it accessible for users without technical expertise.
2. Cost-Effective: Power BI offers a free version with substantial features and a scalable pricing model for additional needs.
3. Real-Time Data: Businesses can monitor their operations with real-time data, enabling quicker and more informed decision-making.
Setting Up Power BI
1. Data Sources: Power BI can connect to various data sources such as Excel, SQL databases, and cloud services like Azure.
2. Data Modeling: Use Power BI to clean and transform data, creating a cohesive data model that forms the foundation of your reports.
3. Visualizations: Choose from a wide array of visualizations to represent your data. Customize these visuals to highlight the most critical insights.
Customizing Dashboards
1. Tailor to Needs: Customize dashboards to reflect the unique needs of your business, focusing on key performance indicators (KPIs) relevant to your goals.
2. Interactive Reports:Create interactive reports that allow users to explore data more deeply, providing a clearer understanding of underlying trends.
Real-World Examples
Several small businesses have successfully implemented Power BI to gain a competitive edge:
1. Retail: A small retail store used Power BI to track sales trends, optimize inventory, and identify peak shopping times.
2. Finance:A small financial advisory firm employed Power BI to analyze client portfolios, improving investment strategies and client satisfaction.
Integration with Existing Tools
Power BI seamlessly integrates with other Microsoft products such as Excel and Azure, as well as third-party applications, ensuring a smooth workflow and enhanced productivity.
Best Practices
1. Data Accuracy: Ensure data accuracy by regularly updating your data sources.
2. Training: Invest in training your team to use Power BI effectively.
3. Security: Implement robust security measures to protect sensitive data.
Future Trends
Power BI continues to evolve, with future updates likely to include more advanced AI features and enhanced data processing capabilities, keeping businesses at the forefront of technology.
Conclusion
Power BI offers small businesses a powerful tool to transform their data into meaningful insights. By adopting Power BI, businesses can improve decision-making, enhance operational efficiency, and gain a competitive advantage. Partnering with Vbeyond Digital ensures a smooth and successful implementation, maximizing the benefits of Power BI for your business. with Power BI: A Comprehensive Guide for Small Businesses
3 notes
·
View notes