#python program challenges
Explore tagged Tumblr posts
Text
18.03.2024
Today was a decently normal Monday. My teachers informed me today that I might be getting an essay I completed a while ago and getting my science test results back soon.
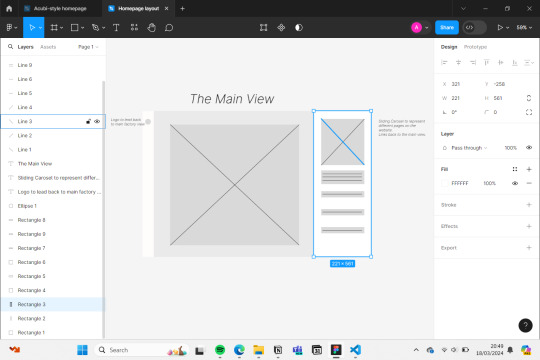
After school, I tried to start the home page of the website I'm currently building Project.Spider and I would like to say that thanks to the help of Bing AI, ChatGPT and Visual Studio Code, I could finish one part.

🎧- Shut up my mom's calling - Hotel Ugly
🌲- 3hrs
#aesthetic#studying#books#bookish#bookworm#book community#booknerd#currently reading#bookstagram#student life#coding#python#programming#engineering#developer#html#html css#css#figma#figmadesign#figma to html#studyblr community#productivity#productivity challenge#productivityboost#study#study motivation#study notes#study tips#study with me
8 notes
·
View notes
Text
Introduction: As a high school student in the 21st century, there's no denying the importance of computer science in today's world. Whether you're a seasoned programmer or just dipping your toes into the world of coding, the power of computer science is undeniable. In this blog, I'll share my journey as a 12th-grader venturing into the fascinating realms of C, C++, and Python, and how this journey has not only improved my computer science profile but also shaped my outlook on technology and problem-solving.
Chapter 1: The Foundations - Learning C
Learning C:
C, often referred to as the "mother of all programming languages," is where my journey began. Its simplicity and efficiency make it an excellent choice for beginners. As a high school student with limited programming experience, I decided to start with the basics.
Challenges and Triumphs:
Learning C came with its fair share of challenges, but it was incredibly rewarding. I tackled problems like understanding pointers and memory management, and I quickly realized that the core concepts of C would lay a strong foundation for my future endeavors in computer science.
Chapter 2: Building on the Basics - C++
Transition to C++:
With C under my belt, I transitioned to C++. C++ builds upon the concepts of C while introducing the object-oriented programming paradigm. It was a natural progression, and I found myself enjoying the flexibility and power it offered.
Projects and Applications:
I started working on small projects and applications in C++. From simple text-based games to data structures and algorithms implementations, C++ opened up a world of possibilities. It was during this phase that I began to see how the knowledge of programming languages could translate into tangible solutions.
Chapter 3: Python - The Versatile Language
Exploring Python:
Python is often praised for its simplicity and readability. As I delved into Python, I realized why it's a favorite among developers for a wide range of applications, from web development to machine learning.
Python in Real-Life Projects:
Python allowed me to take on real-life projects with ease. I built web applications using frameworks like Flask and Django, and I even dabbled in data analysis and machine learning. The versatility of Python broadened my horizons and showed me the real-world applications of computer science.
Chapter 4: A Glimpse into the Future
Continual Learning:
As I prepare to graduate high school and venture into higher education, my journey with C, C++, and Python has instilled in me the importance of continual learning. The field of computer science is dynamic, and staying up-to-date with the latest technologies and trends is crucial.
Networking and Collaboration:
I've also come to appreciate the significance of networking and collaboration in the computer science community. Joining online forums, participating in coding challenges, and collaborating on open-source projects have enriched my learning experience.
Conclusion: Embracing the World of Computer Science
My journey as a 12th-grader exploring C, C++, and Python has been an enlightening experience. These languages have not only improved my computer science profile but have also given me a broader perspective on problem-solving and technology. As I step into the future, I'm excited to see where this journey will take me, and I'm ready to embrace the ever-evolving world of computer science.
If you're a fellow student or someone curious about programming, I encourage you to take the plunge and start your own journey. With determination and a willingness to learn, the world of computer science is yours to explore and conquer.
#Computer Science#Programming Languages#Learning Journey#C Programming#C++ Programming#Python Programming#Coding Tips#Programming Projects#Programming Tutorials#Problem-Solving#High School Education#Student Life#Personal Growth#Programming Challenges#Technology Trends#Future in Computer Science#Community Engagement#Open Source#Programming Communities#Technology and Society
4 notes
·
View notes
Text



Post #56: Amazon, Kindle Challenge at the end of the year from October 1, 2024 until December 31, 2024.
#amazon kindle#kindle#kindle challenge#reading#ebooks#kindle ebooks#challenge#computer books#programming#computing#teaching#education#educate yourself#learning#lenovo computer#samsung computer#xiaomi computer#programmieren#coding#studying#python#small basic#small visual basic#scratch#turtle programming#coding for kids
1 note
·
View note
Text
DAY :1

Work of the day
Today, we kick off the 30-day Python training program. We will be following various exercises provided previously.
Step 1: Install the chosen IDE (VS Code), which we will use.
Step 2: Install the Python extension for the IDE.
Step 3: Download Python version 3.9.6 for running codes within the IDE.
Step 4: After completing each exercise, I will provide screenshots as proof of completion.
EXERCISE:
Write a Python program to print "Hello, World!"
Write a Python program to find the sum of two numbers.
Write a Python function to check if a number is even or odd.
See you afterwards with the screenshots🫡 :
1 note
·
View note
Text
Essentials You Need to Become a Web Developer
HTML, CSS, and JavaScript Mastery
Text Editor/Integrated Development Environment (IDE): Popular choices include Visual Studio Code, Sublime Text.
Version Control/Git: Platforms like GitHub, GitLab, and Bitbucket allow you to track changes, collaborate with others, and contribute to open-source projects.
Responsive Web Design Skills: Learn CSS frameworks like Bootstrap or Flexbox and master media queries
Understanding of Web Browsers: Familiarize yourself with browser developer tools for debugging and testing your code.
Front-End Frameworks: for example : React, Angular, or Vue.js are powerful tools for building dynamic and interactive web applications.
Back-End Development Skills: Understanding server-side programming languages (e.g., Node.js, Python, Ruby , php) and databases (e.g., MySQL, MongoDB)
Web Hosting and Deployment Knowledge: Platforms like Heroku, Vercel , Netlify, or AWS can help simplify this process.
Basic DevOps and CI/CD Understanding
Soft Skills and Problem-Solving: Effective communication, teamwork, and problem-solving skills
Confidence in Yourself: Confidence is a powerful asset. Believe in your abilities, and don't be afraid to take on challenging projects. The more you trust yourself, the more you'll be able to tackle complex coding tasks and overcome obstacles with determination.
#code#codeblr#css#html#javascript#java development company#python#studyblr#progblr#programming#comp sci#web design#web developers#web development#website design#webdev#website#tech#html css#learn to code
2K notes
·
View notes
Text



Day 1 [24th March, Monday]
Collab Challenge with @a-fox-studies @winryrockbellwannabe @nanthegirl @larstudy 30 Days of Productivity! 💛 axy’s study time: 6h 39min 💚 aj’s study time: 3h 💜 nan’s study time: 3h ❤ lar’s study time: 8h 45min ✨ 💙 iris’s study time: 2h 41min
it's finally here!!! I'm so excited for this challenge :D :D
most of my hours are classes now that my 2nd semester has started!! I'm also including routine times and driving because well its motivating me to do the former and I'm pretty proud of the latter lol
I woke up late today. as in, I was awake but I was also reading a fic instead of studying for the two hours I was awake before I absolutely had to get ready for uni or I'd be late
my first class of the day was a 2 hour math lab, which was really chill, where we do python programs associated with math. I finished like 5 but I ran out of time before I could round it off to an even 6. T_T
I didn't want to leave because the room was air conditioned and it was like 40 degree celsius out there lol. then it was a chemistry lecture about modern batteries which was cool, followed by another math class where my prof. gave us homework last second and I didn't understand but I'll figure it out tomorrow hopefully
python theory and electrical engineering were tiring lectures because my ass ate a lot for lunch and also for electrical we were doing concepts I already been knew from like highschool. that's where the shitty doodle of the hand is from its the Fleming Left Hand Rule also I promise my notes look better than that T_T
on the way home got this ruler with a protractor thing that rolls for one of my subjects! I had shit to do after classes but I read another really long fic lol. it is what it is
📃 words read:📃 3,28,748 words [3 fics]
🎶 music: 🎶 GOLDWING [Billie Eilish]
👟 step count: 👟 4309/6000 steps
#axythings#studyblr#studyinspo#university studyblr#studyspo#study motivation#30 days of productivity#collab challenge
37 notes
·
View notes
Text
March 5, 2025 • Wednesday
--- 30 days of productivity • COLLAB CHALLENGE WITH @studaxy • Day 26/30 ---
💛 Axy's productive time: 1h 32min
💙 Iris's study time: 2h
Today I did an activity because I was bored. My textbook said that implementing the "finding GCD of numbers by prime factorization method" into a program is hard, and I went "are you challenging me?"
So yeah I spent the day doing that and turns out it was pretty hard lol XD but! I ended up succeeding!
Also, I learned about the Counter module in python, which creates a dictionary of items — the keys being the elements of an iterable passed to it, and the values being the number of occurrences of the key in the iterable. So that was fun :3

14 notes
·
View notes
Text
[Wings of Fire] Headcanon for every dragon character (a-b)
Hello! I started this thing a while ago where I created a headcanon for every Wings of Fire dragon. Right now, I'm just starting the J's, so I decided that I wanted to share some of them. Today I'm going to share my headcanons for characters with names that start with A and B.
As
Abalone - was a childhood friend of Gill; the two had a relationship with each other before Gill married Coral, but there were still always feelings between them which Gill felt guilty over. He eventually married Pearl (the member of the SeaWing council) and their son is Barracuda.
Addax - before the war, he owned a cattle farm where he lived with his family, he was a lot more friendly back then; after he got his family back, they returned to the farm where they live to this day. Arid is his daughter, but after she left for JMA, he had more dragonets.
Admiral - after TFoH, Admiral traveled the continent trying to recover from the conditioning of the flamesilk caverns. He eventually settled down in the LeafSilk Kingdom where he used his flamesilk to help the tribe.
Agave - Agave thought she had a crush on Palm when they were dragonets, but always had to hide it because Plam loved Smolder. Later, she learned that she didn't have feelings for Palm, confusing her care for Palm as a friend for romantic feelings. She would tell Palm to break up with Smolder as every solution to a problem in their relationship.
Alba - Alba loves hunting and used to work in her parents' animal skin shop before she was sent to JMA, making her a master of creating woven articles. At JMA, she taught other dragons how to use animal skin and even started a club for the activity. She and Changbai started dating after meeting at JMA.
Albatross - before Lagoon became queen, Albatross and Lagoon's mother, Queen Monsoon, was very careful with Albatross's magic and he rarely ever had to use it. This made it especially difficult when Lagoon became queen and demanded that Albatross use it for her.
Allknowing - Allknowing and Vigilance were friends as dragonets, Allknowing being the younger of the two. Vigilance was aware that Allknowing wasn't the strongest seer in the kingdom, but was biased as Allknowing was her friend, which was why she got to be Vigilance's personal seer until Clearsight's power was discovered. Quickdeath was Allknowing's son, which made her hate Darkstalker and Clearsight even more after Darkstalker killed him.
Anaconda - Anaconda inherited the throne from her aunt, Queen Jaguar, in a royal challenge, as her mother, Queen Dieteri, got the throne from their mother but was channeled by her sister. Anaconda had a close relationship with her mother and viewed the challenges as more of revenge for taking the throne, as she was never the more ambitious dragonet of her and her sister. She didn't let Python see it, but she was fond of her sister and let her take military charge and do what she would like to make her happy.
Anemone - Anemone felt relieved when animus magic disappeared and found an interest in pottery. She enjoyed actually using her claws to make something beautiful rather than making something beautiful at the expense of her soul.
Anhinga - Anhinga loved reading and established a program to collect ancient MudWing literature that would be stored in the MudWing palace library, fittingly named the Anhinga Library.
Aphid - Aphid would be one of the HiveWings to settle in the LeafSilk Kingdom as his father was horrified when he saw his baby dragonet being used like a puppet by Queen Wasp. He is the younger brother of Carabid who also lives in the LeafSilk Kingdom.
Arctic - Arctic was the oldest of his siblings, all of them being male and none of them being able to inherit the throne. Because of this, Diamond was very serious about Arctic specifically getting married and having dragonets so that she could have direct heirs and also continue the animus lineage. After moving to the Night Kingdom and having trouble with his marriage, Arctic began to figure out he was bi and experimented with male NightWings behind Hope's back which she found out about, but it was one of the things the two were more cautious about, so Whiteout and Darkstalker never learned about it.
Argus - Argus is a SilkWing servant of one of the kinder HiveWings which is why he can sometimes appear to be lazy to the Chrysalis, as he was in love with his boss. He didn't tell this to the other members because he was afraid it would make him look bad since their relationship had an imbalance of power. After TFoH, Argus's boss remained in the Hive Kingdom while he moved to the LeafSilk Kingdom to get away, knowing he should spend some time away from HiveWings. He is the older brother of Cinnabar and the grandson of Daniad.
Arid - Arid is grumpy and blunt due to spending time in the stronghold around dragons influenced by Burn. She isn’t the biggest fan of other tribes but JMA has helped her to open up
Armadillo - Armadillo was raised in the Scorpion Den by their father, Adder, a powerful business dragon in the den. Eventually, Armadillo met Thorn and when Thorn became queen, they and their father moved to the SandWing stronghold. Armadillo becomes Blaze's partner.
Ash - Ash is not a LeafWing, but actually a SilkWings, as the book she is in was written during a time when the LeafWings and SilkWings lived peacefully together.
Asha - Asha was in love with Dune and the two had a relationship with each other before Asha's death. Dune always mourned for her and it was one of the reasons why he was often sad and upset.
Atala - in the LeafSilk Kingdom, Atala becomes a member of the SilkWing assembly and marries her LeafWing partners, being one of the first SilkWing-LeafWing couples post-Tree Wars.
Auklet - Auklet has pink accents like Anemone did. Auklet will become the next queen of the SeaWings (many, many years into the future) after Coral dies of a SeaWing plague.
Avalanche - Avalanche meets Secretkeeper while the Talons of Peace go to the Rainforest Kingdom for a meeting and the two become partners.
Bs
Barracuda - Barracuda is skittish and longer/skinnier than most SeaWings. He and Newt are in a relationship.
Battlewinner - Battlewinner is the sister of Morrowseer, Quickstrike, and an unnamed male NightWing. Before her injury, she was ambitious and some of the kinder, less loyal NightWings were afraid that she would try to take over multiple tribes. The frostbreath injury she got was not from an IceWing in a battle, that is only a cover story. Battlewinner actually had fallen in love with an IceWing, but to protect her tribe, she attacked Battlewinner, making her resentful of the IceWings, even more so than before.
Bayou - when the MudWing Succession Crisis happened, Bayoun ran away to the Sand Kingdom where she befriended Jerboa III. The two remained friends until Bayou's death from old age.
Belladonna - Belladonna and Hemlock did not want to marry each other initially, and Belladonna tried to protest to her mother, Linden, but ultimately the two decided that it would be better for their tribe if they married, even if they did not love each other. The two see each other as close friends and partners in crime, but not lovers.
Beryl - Beryl is a SeaWing Scarlet knew from her reign as queen who was incredibly rich from an unknown source and had certain powers that scared the SkyWing queen. She is deathly afraid of Beryl which is why she never mentioned her to anybody before.
Bigtail - Bigtail is larger than most dragons which he is self-conscious about. This was made worse when Pike yelled at him in the prey center.
Blaze - Blaze enjoys dressing up other dragons, not just herself, and loves matching outfits with her friends.
Blister - Blister was a keen scholar, and despite her cunningness, she loved history and protecting scrolls. Before her mother's death, she organized the SandWing stronghold library herself. She is also passionate about theater and if she did not have the pressure of taking the throne and fighting in the war, she would have become an actor. She is a major scrollworm, similar to Starflight.
Bloodworm - Bloodworm wanted to take the throne from Wasp for a long time during Wasp's rule and would secretly practice her fighting. If Wasp hadn't been removed from her position earlier, Bloodworm would have developed a plan to kill Wasp and take the throne. Bloodworm killed Wasp after the two were put in the flamesilk factory, just for her own peace of mind, making her other sisters afraid of her.
Blue - after settling in the LeafSilk Kingdom, Blue attended higher education at the first LeafSilk academy, Sapling Academy. After he graduated, he became a lawyer and would later in life become a teacher at an academy built after he had graduated called Chrysalis University.
Bombardier - Bombardier also came to live in the LeafSilk Kingdom and as an adult, apologized to Cricket for how he acted toward her. The two would become friends and Bombardier works as an accountant at Chrysalis University.
Bonecruncher - as the settlement of Renewal expanded, a council was formed and Bonecruncer was named the head of agriculture. He never formally changed his name to Greentalon, but his close friends call him that.
Boto - Boto is the younger brother of Bullfrog. He had a crush on Thrush before Thrush started dating Ostrich.
Bright - Bright was Tualang's sister and they were kidnapped together while exploring the outer parts of the RainWing village. Although it was believed that Bright died, she was only pretending, and when the NightWings threw her "corpse" into the ocean, she miraculously survived until she reached the top of the Claws of the Clouds Mountains. She is currently lost in the Sky Kingdom due to not knowing the continent.
Bromeliad - Glory eventually assigned Bromeliad to be an envoy between the Rainforest Kingdom and the lost city of night, which Bromeliad found more enjoyable than all of her previous jobs. Bromeliad looks similar to Kestrel which makes Glory feel uneasy sometimes.
Bryony - Bryony's relationship with Grayling was platonic, she eventually got into a polyamorous relationship with several other LeafWings
Bullfrog (MudWing) - Bullfrog is the nephew of Queen Moorhen and one of her most trusted advisors; after coming back from Pantala, he met Bullfrog the RainWing when the medic visited the Mud Kingdom to learn the medical properties of mud; Bullfrog, being the healer of his sibling troop, got along with the other Bullfrog and the two started dating
Bullfrog (RainWing) - Bullfrog would eventually return to the Rainforest Kingdom with the MudWing Bullfrog; to keep others from getting their names mixed up, the RainWing bullfrog went by Frog and the MudWing Bullfrog went by Bull
Bumblebee - Bumblebee saw Sundew and Cricket as her parental figures growing up, going between those two households
Burn - Burn always felt strange when visiting Scarlet in the Sky Kingdom; she had a suspicion that the SkyWing queen had a crush on her, but was too awkward to bring it up; Despite her cruel personality, Burn was extremely awkward when it came to doing anything with other dragons besides killing
Burnet - after moving to the LeafSilk Kingdom, Burnet got a leadership position in the department of housing where she ran operations to build infrastructure
Byblis - Byblis is Linden's sister's daughter, making her Belladonna's cousin; the two are best friends
22 notes
·
View notes
Text
Why Not Write Cryptography
I learned Python in high school in 2003. This was unusual at the time. We were part of a pilot project, testing new teaching materials. The official syllabus still expected us to use PASCAL. In order to satisfy the requirements, we had to learn PASCAL too, after Python. I don't know if PASCAL is still standard.
Some of the early Python programming lessons focused on cryptography. We didn't really learn anything about cryptography itself then, it was all just toy problems to demonstrate basic programming concepts like loops and recursion. Beginners can easily implement some old, outdated ciphers like Caesar, Vigenère, arbitrary 26-letter substitutions, transpositions, and so on.
The Vigenère cipher will be important. It goes like this: First, in order to work with letters, we assign numbers from 0 to 25 to the 26 letters of the alphabet, so A is 0, B is 1, C is 2 and so on. In the programs we wrote, we had to strip out all punctuation and spaces, write everything in uppercase and use the standard transliteration rules for Ä, Ö, Ü, and ß. That's just the encoding part. Now comes the encryption part. For every letter in the plain text, we add the next letter from the key, modulo 26, round robin style. The key is repeated after we get tot he end. Encrypting "HELLOWORLD" with the key "ABC" yields ["H"+"A", "E"+"B", "L"+"C", "L"+"A", "O"+"B", "W"+"C", "O"+"A", "R"+"B", "L"+"C", "D"+"A"], or "HFNLPYOLND". If this short example didn't click for you, you can look it up on Wikipedia and blame me for explaining it badly.
Then our teacher left in the middle of the school year, and a different one took over. He was unfamiliar with encryption algorithms. He took us through some of the exercises about breaking the Caesar cipher with statistics. Then he proclaimed, based on some back-of-the-envelope calculations, that a Vigenère cipher with a long enough key, with the length unknown to the attacker, is "basically uncrackable". You can't brute-force a 20-letter key, and there are no significant statistical patterns.
I told him this wasn't true. If you re-use a Vigenère key, it's like re-using a one time pad key. At the time I just had read the first chapters of Bruce Schneier's "Applied Cryptography", and some pop history books about cold war spy stuff. I knew about the problem with re-using a one-time pad. A one time pad is the same as if your Vigenère key is as long as the message, so there is no way to make any inferences from one letter of the encrypted message to another letter of the plain text. This is mathematically proven to be completely uncrackable, as long as you use the key only one time, hence the name. Re-use of one-time pads actually happened during the cold war. Spy agencies communicated through number stations and one-time pads, but at some point, the Soviets either killed some of their cryptographers in a purge, or they messed up their book-keeping, and they re-used some of their keys. The Americans could decrypt the messages.
Here is how: If you have message $A$ and message $B$, and you re-use the key $K$, then an attacker can take the encrypted messages $A+K$ and $B+K$, and subtract them. That creates $(A+K) - (B+K) = A - B + K - K = A - B$. If you re-use a one-time pad, the attacker can just filter the key out and calculate the difference between two plaintexts.
My teacher didn't know that. He had done a quick back-of-the-envelope calculation about the time it would take to brute-force a 20 letter key, and the likelihood of accidentally arriving at something that would resemble the distribution of letters in the German language. In his mind, a 20 letter key or longer was impossible to crack. At the time, I wouldn't have known how to calculate that probability.
When I challenged his assertion that it would be "uncrackable", he created two messages that were written in German, and pasted them into the program we had been using in class, with a randomly generated key of undisclosed length. He gave me the encrypted output.
Instead of brute-forcing keys, I decided to apply what I knew about re-using one time pads. I wrote a program that takes some of the most common German words, and added them to sections of $(A-B)$. If a word was equal to a section of $B$, then this would generate a section of $A$. Then I used a large spellchecking dictionary to see if the section of $A$ generated by guessing a section of $B$ contained any valid German words. If yes, it would print the guessed word in $B$, the section of $A$, and the corresponding section of the key. There was only a little bit of key material that was common to multiple results, but that was enough to establish how long they key was. From there, I modified my program so that I could interactively try to guess words and it would decrypt the rest of the text based on my guess. The messages were two articles from the local newspaper.
When I showed the decrypted messages to my teacher the next week, got annoyed, and accused me of cheating. Had I installed a keylogger on his machine? Had I rigged his encryption program to leak key material? Had I exploited the old Python random number generator that isn't really random enough for cryptography (but good enough for games and simulations)?
Then I explained my approach. My teacher insisted that this solution didn't count, because it relied on guessing words. It would never have worked on random numeric data. I was just lucky that the messages were written in a language I speak. I could have cheated by using a search engine to find the newspaper articles on the web.
Now the lesson you should take away from this is not that I am smart and teachers are sore losers.
Lesson one: Everybody can build an encryption scheme or security system that he himself can't defeat. That doesn't mean others can't defeat it. You can also create an secret alphabet to protect your teenage diary from your kid sister. It's not practical to use that as an encryption scheme for banking. Something that works for your diary will in all likelihood be inappropriate for online banking, never mind state secrets. You never know if a teenage diary won't be stolen by a determined thief who thinks it holds the secret to a Bitcoin wallet passphrase, or if someone is re-using his banking password in your online game.
Lesson two: When you build a security system, you often accidentally design around an "intended attack". If you build a lock to be especially pick-proof, a burglar can still kick in the door, or break a window. Or maybe a new variation of the old "slide a piece of paper under the door and push the key through" trick works. Non-security experts are especially susceptible to this. Experts in one domain are often blind to attacks/exploits that make use of a different domain. It's like the physicist who saw a magic show and thought it must be powerful magnets at work, when it was actually invisible ropes.
Lesson three: Sometimes a real world problem is a great toy problem, but the easy and didactic toy solution is a really bad real world solution. Encryption was a fun way to teach programming, not a good way to teach encryption. There are many problems like that, like 3D rendering, Chess AI, and neural networks, where the real-world solution is not just more sophisticated than the toy solution, but a completely different architecture with completely different data structures. My own interactive codebreaking program did not work like modern approaches works either.
Lesson four: Don't roll your own cryptography. Don't even implement a known encryption algorithm. Use a cryptography library. Chances are you are not Bruce Schneier or Dan J Bernstein. It's harder than you thought. Unless you are doing a toy programming project to teach programming, it's not a good idea. If you don't take this advice to heart, a teenager with something to prove, somebody much less knowledgeable but with more time on his hands, might cause you trouble.
358 notes
·
View notes
Text
Your Printer is (Probably) a Snitch
In these bewildering times you might want to put up flyers or posters around a neighborhood, or mail a strongly-worded letter to someone. You might be scared of reprisals and wish to do that sort of thing anonymously, but it turns out that governments would prefer that they be able to track you down anyway.
In the early 2010s, a few different innovations were making their way into high-end scanners and printers. One was the EURION constellation, a set of dots that you'll recognize in the constellations on Euro notes or in the distribution of the little numeral 20 speckled around the back of a twenty-dollar bill. Scanners are programmed to look for dots in exactly that pattern and refuse to scan the paper that those dots are on. Can't make a copy of it! Can't scan it in. We'll get back to that.
The other innovation are **tracking dots**. The Electronic Frontier Foundation (EFF) estimates that in 2025, basically every color laser printer on the market embeds a barely-visible forensic code on each of its printouts, which encodes information about the printer and its serial number. (Maybe more data too - I don't have all the details.) Maybe you remember Reality Winner, who leaked classified intelligence to journalists? They received high quality copies (maybe originals) of the documents that were leaked. When officials were able to examine them, they were able to combine regular IT forensics ("how many users printed documents on these dates, to printers of this make & model") and work backwards from the other end, to get a narrow list of suspects.
To defeat those signatures, you either need to use a printer that doesn't embed those features (Challenging! The EFF says basically all printers do this now) or you need to be careful to employ countermeasures like this Python tool. The tool can spray lots of nonsense codes into a PDF that make forensic extraction harder (or impossible).
What does this have to do with the EURion constellation? Well, before anyone can even start to extract little invisible yellow dots from your poster... they have to scan it into their system. And their very law-abiding scanner -- unless it's owned by an agency that fights counterfeiting like the Secret Service does -- probably doesn't have its EURion brainwashing disabled. So when they go to scan your poster or strongly-worded letter, the EURion constellation on it probably stops them from doing it.

#EURion#steganography#printers and scanners#tracking#cybersecurity#sigils#anonymity#electronic frontier foundation
12 notes
·
View notes
Text

Tools of the Trade for Learning Cybersecurity
I created this post for the Studyblr Masterpost Jam, check out the tag for more cool masterposts from folks in the studyblr community!
Cybersecurity professionals use a lot of different tools to get the job done. There are plenty of fancy and expensive tools that enterprise security teams use, but luckily there are also lots of brilliant people writing free and open-source software. In this post, I'm going to list some popular free tools that you can download right now to practice and learn with.
In my opinion, one of the most important tools you can learn how to use is a virtual machine. If you're not already familiar with Linux, this is a great way to learn. VMs are helpful for separating all your security tools from your everyday OS, isolating potentially malicious files, and just generally experimenting. You'll need to use something like VirtualBox or VMWare Workstation (Workstation Pro is now free for personal use, but they make you jump through hoops to download it).
Below is a list of some popular cybersecurity-focused Linux distributions that come with lots of tools pre-installed:
Kali is a popular distro that comes loaded with tools for penetration testing
REMnux is a distro built for malware analysis
honorable mention for FLARE-VM, which is not a VM on its own, but a set of scripts for setting up a malware analysis workstation & installing tools on a Windows VM.
SANS maintains several different distros that are used in their courses. You'll need to create an account to download them, but they're all free:
Slingshot is built for penetration testing
SIFT Workstation is a distro that comes with lots of tools for digital forensics
These distros can be kind of overwhelming if you don't know how to use most of the pre-installed software yet, so just starting with a regular Linux distribution and installing tools as you want to learn them is another good choice for learning.
Free Software
Wireshark: sniff packets and explore network protocols
Ghidra and the free version of IDA Pro are the top picks for reverse engineering
for digital forensics, check out Eric Zimmerman's tools - there are many different ones for exploring & analyzing different forensic artifacts
pwntools is a super useful Python library for solving binary exploitation CTF challenges
CyberChef is a tool that makes it easy to manipulate data - encryption & decryption, encoding & decoding, formatting, conversions… CyberChef gives you a lot to work with (and there's a web version - no installation required!).
Burp Suite is a handy tool for web security testing that has a free community edition
Metasploit is a popular penetration testing framework, check out Metasploitable if you want a target to practice with
SANS also has a list of free tools that's worth checking out.
Programming Languages
Knowing how to write code isn't a hard requirement for learning cybersecurity, but it's incredibly useful. Any programming language will do, especially since learning one will make it easy to pick up others, but these are some common ones that security folks use:
Python is quick to write, easy to learn, and since it's so popular, there are lots of helpful libraries out there.
PowerShell is useful for automating things in the Windows world. It's built on .NET, so you can practically dip into writing C# if you need a bit more power.
Go is a relatively new language, but it's popular and there are some security tools written in it.
Rust is another new-ish language that's designed for memory safety and it has a wonderful community. There's a bit of a steep learning curve, but learning Rust makes you understand how memory bugs work and I think that's neat.
If you want to get into reverse engineering or malware analysis, you'll want to have a good grasp of C and C++.
Other Tools for Cybersecurity
There are lots of things you'll need that aren't specific to cybersecurity, like:
a good system for taking notes, whether that's pen & paper or software-based. I recommend using something that lets you work in plain text or close to it.
general command line familiarity + basic knowledge of CLI text editors (nano is great, but what if you have to work with a system that only has vi?)
familiarity with git and docker will be helpful
There are countless scripts and programs out there, but the most important thing is understanding what your tools do and how they work. There is no magic "hack this system" or "solve this forensics case" button. Tools are great for speeding up the process, but you have to know what the process is. Definitely take some time to learn how to use them, but don't base your entire understanding of security on code that someone else wrote. That's how you end up as a "script kiddie", and your skills and knowledge will be limited.
Feel free to send me an ask if you have questions about any specific tool or something you found that I haven't listed. I have approximate knowledge of many things, and if I don't have an answer I can at least help point you in the right direction.
#studyblrmasterpostjam#studyblr#masterpost#cybersecurity#late post bc I was busy yesterday oops lol#also this post is nearly a thousand words#apparently I am incapable of being succinct lmao
22 notes
·
View notes
Text
instagram
Learning to code and becoming a data scientist without a background in computer science or mathematics is absolutely possible, but it will require dedication, time, and a structured approach. ✨👌🏻 🖐🏻Here’s a step-by-step guide to help you get started:
1. Start with the Basics:
- Begin by learning the fundamentals of programming. Choose a beginner-friendly programming language like Python, which is widely used in data science.
- Online platforms like Codecademy, Coursera, and Khan Academy offer interactive courses for beginners.
2. Learn Mathematics and Statistics:
- While you don’t need to be a mathematician, a solid understanding of key concepts like algebra, calculus, and statistics is crucial for data science.
- Platforms like Khan Academy and MIT OpenCourseWare provide free resources for learning math.
3. Online Courses and Tutorials:
- Enroll in online data science courses on platforms like Coursera, edX, Udacity, and DataCamp. Look for beginner-level courses that cover data analysis, visualization, and machine learning.
4. Structured Learning Paths:
- Follow structured learning paths offered by online platforms. These paths guide you through various topics in a logical sequence.
5. Practice with Real Data:
- Work on hands-on projects using real-world data. Websites like Kaggle offer datasets and competitions for practicing data analysis and machine learning.
6. Coding Exercises:
- Practice coding regularly to build your skills. Sites like LeetCode and HackerRank offer coding challenges that can help improve your programming proficiency.
7. Learn Data Manipulation and Analysis Libraries:
- Familiarize yourself with Python libraries like NumPy, pandas, and Matplotlib for data manipulation, analysis, and visualization.
For more follow me on instagram.
#studyblr#100 days of productivity#stem academia#women in stem#study space#study motivation#dark academia#classic academia#academic validation#academia#academics#dark acadamia aesthetic#grey academia#light academia#romantic academia#chaotic academia#post grad life#grad student#graduate school#grad school#gradblr#stemblog#stem#stemblr#stem student#engineering college#engineering student#engineering#student life#study
7 notes
·
View notes
Photo

From George's turn as Pirate Bob on Rutland Weekend Television. 1975. (More from that appearance here, and the backstory here.)
“I felt like I’d known them [Monty Python] all for years, because I’d watched all the programs and had had them on videotape. So it only took ten minutes before we were the best of friends.” - George Harrison, Rolling Stone, April 19, 1979 “Even when we first met I felt like I’d known him forever. Not the Beatle George, he never seemed like that to me, nor the bearded garden gnome George, but the man, the real man with the deep, dark eyes and the crooked grin and the loud laugh. [...] I never knew a man like him. It was as if we fell in love. His attention, his concern, his loving friendship was so strong and powerful that it encompassed your entire life. You felt comfortable and secure. We would stay up all night and talk for hours about our lives, about the hurts and pains, about the groups we had been in and the trying emotional strains and problems that being in such groups entails. He was always full of spiritual comfort, counsel, and advice. He saw everything from the cosmic point of view. Our deaths were natural and unavoidable, and he viewed everything from that perspective, even then in the mid-seventies. He had come off a tour of America, where things had been unpleasant for him. The ‘Dark Hoarse Tour,’ he called it. His pseudonym — for hotels, security (and guitar picks) — had been Jack Lumber. (He was always a raving certified Python fanatic as, of course, I had always been a raving certified Beatle fan.) Drugs and brandy had ruined his voice on that tour, and I think he had set out to challenge and defy the expectations of his North American audiences, presenting Ravi Shankar and the Indian music first and then doing jokey versions of various of his songs. The good news was that he met Olivia, the love of his life, and retired to Friar Park, where he felt safe and from where he would rarely emerge. Here he would discover the other great love of his, gardening, which became a living example of his concern to create beauty on the planet wherever he could. […] [H]e won my heart and I fell in love with him and am filled with that love to this day.” - Eric Idle, The Greedy Bastard Diary (x)
#George Harrison#Eric Idle#Olivia Harrison#Monty Python#quote#quotes about George#quotes by George#George and Eric Idle#1975#1970s#1980s#1990s#2000s#fits queue like a glove
114 notes
·
View notes
Text
Hacktivism: Digital Rebellion for a New Age 🌐💥
In an era where our lives are intertwined with the digital landscape, the concept of hacktivism has become more than just a buzzword. It’s the fusion of hacking and activism—where people use their coding and cyber skills to disrupt power structures, challenge injustice, and amplify voices that often go unheard. It's a rebellion born from the belief that access to information, privacy, and freedom are rights, not privileges. But how did this digital resistance movement come to be, and how can you get involved? Let’s dive into it. 💻⚡️
What Exactly Is Hacktivism? 🤖✨
At its core, hacktivism is activism with a digital twist. It’s about using technology and hacking tools to advance social, political, and environmental causes. The most common methods include:
DDoS Attacks (Distributed Denial of Service): Overloading a target’s website with too much traffic, essentially crashing it, to temporarily shut down an online service.
Website Defacement: Replacing a website’s homepage with a political message, often exposing corruption or unethical practices.
Data Leaks: Exposing hidden documents or sensitive information that reveal corporate or governmental wrongdoing.
Bypassing Censorship: Circumventing firewalls or government restrictions to make sure information reaches the people it needs to.
The idea is simple: when a government or corporation controls the narrative or hides the truth, hacktivists take it into their own hands to expose it. 🌍💡
Why Is Hacktivism Important? 🔥
In a world dominated by corporations and powerful governments, hacktivism represents a form of resistance that’s accessible. It’s about leveling the playing field, giving people—especially those who lack resources—an avenue to protest, to expose corruption, and to disrupt systems that perpetuate inequality. The digital world is where much of our lives now happen, and hacktivism uses the very systems that oppress us to fight back.
Think about WikiLeaks leaking documents that exposed global surveillance and the activities of intelligence agencies. Or how Anonymous has played a pivotal role in advocating for free speech, standing up against internet censorship, and exposing corrupt governments and corporations. These are the digital warriors fighting for a cause, using nothing but code and their knowledge of the web.
Hacktivism is a direct response to modern issues like surveillance, censorship, and misinformation. It's a way to shift power back to the people, to give voice to the voiceless, and to challenge oppressive systems that don’t always play by the rules.
The Ethical Dilemma 🤔💭
Let’s be real: hacktivism doesn’t come without its ethical dilemmas. While the intentions are often noble, the methods used—hacking into private systems, defacing websites, leaking sensitive info—can sometimes lead to unintended consequences. The line between activism and cybercrime is thin, and depending on where you live, you might face serious legal repercussions for participating in hacktivist activities.
It’s important to consider the ethics behind the actions. Are you defending the free flow of information? Or are you inadvertently causing harm to innocent bystanders? Are the people you’re exposing truly deserving of scrutiny, or are you just participating in chaos for the sake of it?
So if you’re thinking of getting involved, it’s crucial to ask yourself: What am I fighting for? And is the harm done justified by the greater good?
How to Get Started 💻💡
So, you’re interested in getting involved? Here’s a starting point to help you use your tech skills for good:
Learn the Basics of Hacking 🔐: Before diving into the world of hacktivism, you'll need to understand the tools of the trade. Start with the basics: programming languages like Python, HTML, and JavaScript are good foundational skills. Learn how networks work and how to exploit vulnerabilities in websites and servers. There are plenty of free online resources like Codecademy, Hack This Site, and OverTheWire to help you get started.
Understand the Ethical Implications ⚖️: Hacktivism is, above all, about fighting for justice and transparency. But it’s crucial to think through your actions. What’s the bigger picture? What are you trying to achieve? Keep up with the latest issues surrounding privacy, data rights, and digital freedom. Some online groups like The Electronic Frontier Foundation (EFF) provide great resources on the ethics of hacking and digital activism.
Join Communities 🕸️: Being part of a like-minded group can give you support and insight. Online communities, like those on Reddit, Discord, or specific forums like 4chan (if you're cautious of the chaos), can help you learn more about hacktivism. Anonymous has also had an iconic role in digital activism and can be a place where people learn to organize for change.
Stay Informed 🌐: To be effective as a hacktivist, you need to be in the know. Follow independent news sources, activist blogs, and websites that report on global surveillance, corporate corruption, and governmental abuse of power. Hacktivism often reacts to injustices that would otherwise go unnoticed—being informed helps you take action when necessary.
Respect the Digital Space 🌱: While hacktivism can be used to disrupt, it’s important to respect the privacy and safety of ordinary people. Try to avoid unnecessary damage to private citizens, and focus on the systems that need disrupting. The internet is a tool that should be used to liberate, not to destroy without purpose.
Never Forget the Human Side ❤️: As with all activism, the heart of hacktivism is about making a difference in real people’s lives. Whether it's freeing information that has been hidden, protecting human rights, or challenging unjust power structures—always remember that at the end of the code, there are humans behind the cause.
Final Thoughts 💬
Hacktivism is a powerful, transformative form of resistance. It’s not always about flashy headlines or viral attacks—often, it’s the quiet work of exposing truths and giving people a voice in a world that tries to keep them silent. It’s messy, it’s complex, and it’s not for everyone. But if you’re interested in hacking for a purpose greater than yourself, learning the craft with the intention to fight for a better, more just world is something that can actually make a difference.
Remember: With great code comes great responsibility. ✊🌐💻
#Hacktivism#DigitalRevolution#TechForGood#Activism#CodeForJustice#ChangeTheSystem#Anarchism#Revolution
8 notes
·
View notes
Text



Day 2 [25th March, Tuesday]
Collab Challenge with @a-fox-studies @winryrockbellwannabe @nanthegirl @larstudy 30 Days of Productivity! 💛 axy’s study time: 6 hours 💚 aj’s study time: 4 hours 💜 nan’s study time: 4 hours ❤ lar’s study time: 10 hours ✨ 💙 iris’s study time: 2 hours 53 minutes
I have this awful habit of forgetting to take off what little make-up I wear - - winged eyeliner. only - as armor because of my social anxiety so I woke up looking like a racoon today 👍
I got a little bit of work done before uni - a rarity in my routines I tell you - mostly some problems in math and some writing work in CAED. speaking of, CAED lab was fun because lines are fun and computers are fun and when you put em together you get fun squared :D
my math and chem lectures felt like it dragged on and on however, but I really should’ve appreciated how chill my life was before lunch happened because I unearthed drama in my friend group that went on for months without me knowing so that was fun. its okay though because, besides some oscar-worthy acting and awkwardness, I live my life as unbothered as I can and ultimately, it is what it is
the python lecture after lunch was fun because we dissected a couple of programs to execute tomorrow in lab which I’m looking forward to and then I skipped the last two hours because I was too tired and also fasting T_T
📃 words read:📃 203,894 words [2 fics]
🎶 music: 🎶 Already Over [Sabrina Carpenter]
👟 step count: 👟 7197/6000 steps
#axythings#studyblr#studyinspo#30 days of productivity#collab challenge#university studyblr#studyspo#university life#study motivation
20 notes
·
View notes
Text
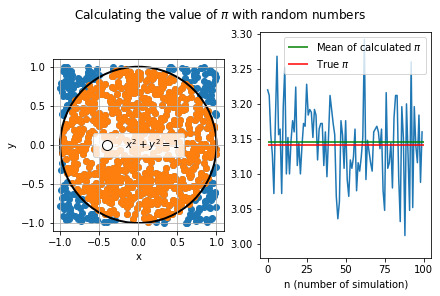
Heyyyy ✨✨✨✨
This is a very simple way to calculate the value of pi. It's based on the ratio between the area of a unit circle and the area of the square that encloses it; this is equal to pi/4, so it's easy to derive the value of pi.
Translated into code, all you need to do is generate enough random numbers and count how many "fall" inside the circle: the ratio of these to the total number of points generated will tend towards pi/4 as more points are generated!
In the figure on the left, you can see graphically what I mentioned above, while on the right, you can see how close you can get to the true value of pi with a few simulations in which I generated a few thousand random numbers each time. However, despite the proximity to the true value, the value I managed to calculate was accurate only up to the second decimal place… This method remains a rather naive one!
I challenge you to try to recreate it; it's very simple! I did it in Python, but you can use any programming language ;)
#studyblr#physics student#university#physics studyblr#physics#study life#python#coding#3.14#stem student#stemblog#stem academia#women in stem#stem#study inspiration
44 notes
·
View notes