#/News
Text
Major global conflicts prompt cyber threats. US firms lag in prioritizing cybersecurity; only 52% make it central. Learn how DevSecOps can protect against escalating attacks.
RoamNook - Baked-in Security
Home
News & Insights
Community
Events
IT Tools
State of IT
Newsletters
Reviews
Login
Join
BAKED-IN SECURITY: HOW DEVSECOPS CAN PROTECT SOFTWARE SUPPLY CHAINS
By Michael Lieberman, Co-Founder and CTO of Kusari
March 27, 2024
As global conflicts threaten to spill over into cyberspace, companies must consider the security of their software supply chains. Mike Lieberman, Co-Founder and CTO of Kusari, explores how DevSecOps, Zero Trust, and open-source tools can help defend against increasingly sophisticated attacks.
The Growing Threat of Cyber Attacks
The world, it seems, is teetering on the edge of multiple regional crises. Whether it’s escalating tensions in the Middle East, an increase in hostility from North Korea, or the deepening consequences of Russia’s war with Ukraine, there’s little doubt that 2024 will be defined by mounting geopolitical uncertainty.
These hotspots of instability may feel very far away, but with just a few lines of malicious code, they can hit home devastatingly quickly. As Google observed in its most recent Cybersecurity Forecast, “major global conflicts [will] continue into next year, [so] be prepared for an uptick in disruptive hacktivism.”
Political cyber attacks are just the tip of the iceberg. We are also seeing cybercrime rise with threats like cryptocurrency mining malware injected into otherwise benign software.
For businesses in the United States, this is a problem. Research indicates that American companies simply don’t take cybersecurity as seriously as counterparts in other countries; only 52% of US firms say digital defense is a priority, versus a global average of 73%.
This has to change. Business leaders must recognize that in an increasingly tech-centric world, cyber threats are going to grow in complexity and sophistication to levels that mirror our growing reliance on complex and sophisticated software. As such, cybersecurity can no longer be an afterthought but a central thread woven through every facet of IT operations. Getting this right means embracing an innovative, multidisciplinary digital approach that can root out vulnerabilities before real damage is done.
Baked-in Security with DevSecOps
The push to integrate security into the development and operations of software, known as DevSecOps, has advanced significantly in recent years, and for a good reason: by combining cross-functional teams, the software development life cycle (SDLC) can be enhanced, automated, and accelerated.
Yet DevSecOps still isn’t mainstream. The root causes are more complex than a decades-old perception that security hinders development speed. There are financial constraints, as comprehensive DevSecOps requires investment in tools, training, and process changes. Additionally, there is a mismatch in incentives and priorities between executives focused on profit and costs versus security teams primarily concerned with risks versus developers wanting to release features. This can lead to a lack of buy-in, which, in turn, often results in cyber defenses being tacked on at the end of the process as a gate, as opposed to being embedded from the start.
However, there are now established practices to build security into software as the development progresses. The key is removing outdated legacy application security testing (AST) tools that hinder the SDLC, replacing them with more modern systems with a high degree of automation, and integrating well with existing developer workflows. This allows for seamless vulnerability scanning and analysis of internal code and third-party dependencies. Another important technique is the codification of security policies, such as access control policies, into reusable and testable assets, known as ‘policy as code.’ By integrating these policy tests into the development pipeline, teams can automatically verify that new code adheres to enterprise security standards.
The shift from gating function to full integration improves security, user experience, and development pace. Fundamentally, by streamlining risk management and helping eliminate bugs early, DevSecOps allows for more efficient security testing, ultimately enabling a more effortless digital transformation for the end user.
Maintaining Integrity throughout the Supply Chain
The movement towards DevSecOps has happened parallel to the mounting threat to software supply chains.
Targeting the tools provided by trusted third-party vendors, supply chain attacks create a weakness at one part of the digital assembly line that filters down to programs further along the SDLC. One recent example was the breach against software designer CyberLink, carried out by North Korea–backed hackers, that later infiltrated customer systems in multiple countries, including the US and Canada.
This sort of incident isn’t a rarity. In late 2020, the notorious SolarWinds hack put supply chain intrusions on the map, with cybercriminals installing backdoors in a popular IT management platform to launch subsequent attacks on dozens of downstream customers. Since then, the threat has grown significantly: between 2022 and 2023, 61% of US businesses were affected by a supply chain assault, with half of IT professionals stating that they believe the danger posed by such attacks is “high” or “extreme.”
By bringing security into the SDLC earlier, software supply chain risks can be mitigated as the integrity of components and dependencies is continually scrutinized before a product goes to market. An effective DevSecOps team will consider potential security issues from the beginning of the development process – the planning stage – and maintain that focus during sourcing, building, testing, deployment, and monitoring.
However, achieving true transparency and control within the supply chain requires more than just internal vigilance. Emerging open-source tools, like Graph for Understanding Artifact Composition (GUAC), promise to play a crucial role. Acting as a central hub, aggregating and mapping software security metadata, GUAC gives DevSecOps personnel greater visibility into their software components.
Embrace Zero Trust
With DevSecOps spanning the length and breadth of the software supply chain, the risk of an attack is reduced. However, weaknesses will remain without robust frameworks to govern this security-meets-development-and-operations approach.
That’s why many organizations are embracing Zero Trust: a model that requires all users, whether within or outside the network, to be authenticated, authorized, and continuously validated for security configuration and posture before being granted access to applications and data. Historically, network security has focused on perimeter-based controls, like firewalls, to prevent access to the network. By adopting this zero-trust mentality, companies can safeguard their data and digital assets by enabling precise access control, limiting the blast radius in case of a breach, and providing visibility into network interactions to detect suspicious activity.
A “never trust, always verify” policy doesn’t have to be limited to devices and users – it can be extended to the SDLC through open specifications like SLSA (supply-chain levels for software artifacts). SLSA provides a framework for associating claims made by a trusted identity about critical software development practices, such as how the software was built, with the software artifacts themselves. In other words, it provides a way to trace how software was developed, built, and published.
For example, an SLSA-enabled system could restrict a package from running in production environments unless its artifacts are accompanied by an attestation asserting it has passed through required security scans. With software supply chain details and security posture codified and standardized, organizations can apply Zero Trust to validate and authorize critical phases of the SDLC.
Identities and claims can be confirmed through signatures and managed via open-source tools like GUAC, enabling organizations to verify supply chain integrity and significantly reduce the attack surface. By extending Zero Trust to cover more of the modern, dynamic software ecosystem, threats targeting third-party component vulnerabilities can be better anticipated and mitigated. All of this raises security confidence across the supply chain.
Taking Security out of Its Silo
As geopolitical tensions rise in 2024, businesses can no longer afford to view cybersecurity as a secondary concern. Supply chain attacks and sophisticated nation-state hackers have made it clear that digital threats to the systems that run countries and the global economy are becoming more elaborate. Companies must respond with an equally multifaceted approach centered around DevSecOps.
By taking security out of its silo and baking it into development from day one, organizations can move faster while also identifying vulnerabilities early. This proactive security culture must stretch across the entire software supply chain, leveraging innovative open-source tools to apply zero-trust principles to third-party components.
Between mounting global uncertainty and the accelerating pace of the digital economy, the margin for error has never been smaller. Attacks that once took weeks or months to materialize can now be launched in minutes. In an age of rising cyber risks, integrating security across the entire development lifecycle is no longer an option – it’s an imperative.
Conclusion: RoamNook - Innovating IT Security
In a world where cyber threats are increasing and software supply chains are under attack, businesses need a proactive approach to security. That's where RoamNook comes in. As an innovative technology company specialized in IT consultation, custom software development, and digital marketing, RoamNook is at the forefront of helping businesses protect their software supply chains.
With the expertise and experience of the RoamNook team, businesses can implement DevSecOps practices, integrate Zero Trust principles, and leverage open-source tools to ensure the security and integrity of their software. RoamNook's solutions empower organizations to stay ahead of mounting global threats and fuel their digital growth.
Don't wait until it's too late. Partner with RoamNook today and secure your software supply chain for a safer digital future.
Written by Michael Lieberman, Co-Founder and CTO of Kusari, this article provides valuable insights into the importance of baked-in security and how businesses can protect their software supply chains. By embracing DevSecOps, Zero Trust, and open-source tools, organizations can stay ahead of evolving cyber threats and ensure the integrity of their software. This informative content brings new information to the table, highlighting key facts and concrete data to educate and inform readers.
RoamNook is an innovative technology company dedicated to fueling digital growth. With expertise in IT consultation, custom software development, and digital marketing, RoamNook is well-equipped to help businesses navigate the complexities of the digital landscape and secure their software supply chains.
© 2024 RoamNook. All rights reserved. | RoamNook
Source: https://www.spiceworks.com/tech/devops/guest-article/baked-in-security-how-devsecops-can-protect-software-supply-chains/&sa=U&ved=2ahUKEwi1l4eel5eFAxWnD1kFHaYhA9oQxfQBegQIBxAC&usg=AOvVaw1nTBPswD4C2H4rJpXJZZ7N
0 notes
Text
Artificial intelligence is coming to the aid of the construction of a new skyscraper at the heart of New York City, maximizing efficiency in terms of costs, labor and resources.
Israeli company Buildots, which turns visual data captured via helmet-mounted cameras into actionable construction insights, has teamed up with building giant Global Holdings Management Group on a location just off Columbus Circle.
More: Here
11 notes
·
View notes
Link
11 notes
·
View notes
Text
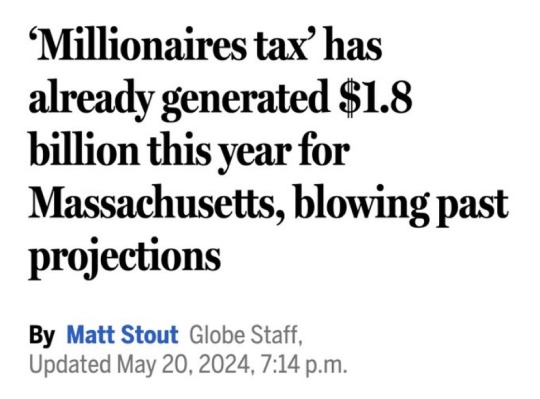
Source
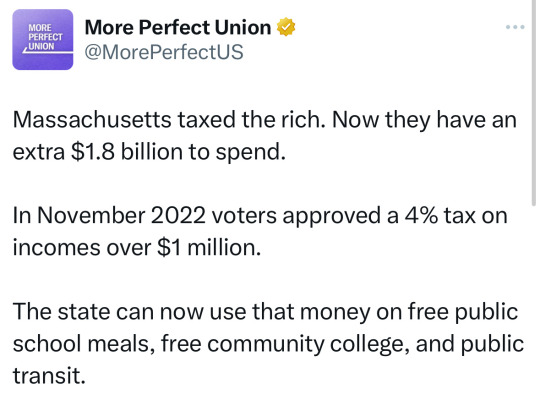
#tax the rich#eat the rich#politics#us politics#government#massachusetts#the left#progressive#current events#news#billionaires should not exist#good news
62K notes
·
View notes
Text

Happy Pride Month
#yemen#jerusalem#tel aviv#current events#palestine#free palestine#gaza#free gaza#news on gaza#palestine news#news update#war news#war on gaza#happy pride 🌈#pride month#gaza genocide#genocide#happy pride month#lgbtqia
73K notes
·
View notes
Text

[Image ID: The Destiel confession meme edited so that Dean answers 'There's a petition to ban conversion therapy in the EU' to Cas' 'I love you'. /End ID]
If you are a citizen in the EU please sign this petition:
#europe#european union#lgbtq+#lgbtqia+#destiel news channel#destiel meme#destiel#supernatural#spn#pride#pride month
76K notes
·
View notes
Text
In mine and many other east Asian cultures, the dragon traditionally symbolises things like power, wealth and strength (imperial symbol and all)
I think we often forget that in the story of the Great Race, the dragon came in fifth because it'd stopped to give people rain. Then it'd stopped again to push a rabbit adrift on a log across the wide river so it reached the shore safely (that's why the Rabbit year comes before the Dragon).
Dragons aren't meant to just be powerful - they are meant to do good with such power, and to help those in need.
So in this lunar new year, I hope you gain more power, so that you might be able to help others. I pray you have abundant resources so you may give to yourself and those around you. I wish you courage, endurance, kindness and generosity, for yourself and your people.
I hope you, and I, will be rain givers, life preservers, joy bringers.
I hope we will be dragons.
Extremely belated postscript that should have been here far earlier:
Free Palestine, Free Sudan, Free Congo 🇵🇸🇸🇩🇨🇩
96K notes
·
View notes
Text

it's the last day you can rb this
126K notes
·
View notes
Text
As protests start ramping up and violence escalates please remember:
DO NOT PUT MILK IN YOUR EYES FOR PEPPER SPRAY OR TEAR GAS.
It can and will cause infection due to bacteria. Flush with water, distilled if possible, and never EVER wear contact lenses to protests where there may be police retaliation.
Please reblog. It may save someone's sight.
#palestine#free palestine#columbia university#ucla#columbia#kent state#nyu#psu#portland university#new york university
83K notes
·
View notes
Text
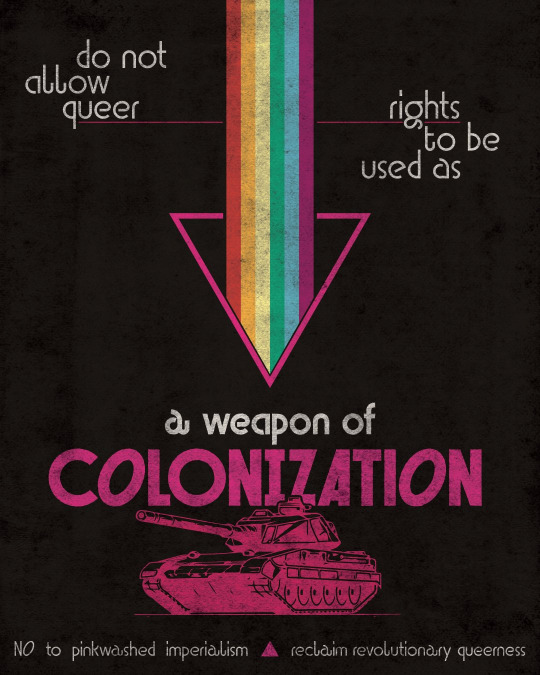
OG: https://earthliberationstudio.com/shop/reclaim-revolutionary-queerness/ !!!!!
#free palestine#palestine#gaza#israel#current events#israel is a terrorist state#palestine news#news on gaza#news update#west bank#queer#queer community#queer palestinians#queer palestinians exist!!!#dont let israel pinkwash you
56K notes
·
View notes
Text
i thought my laptop was on its last leg because it was running at six billion degrees and using 100% disk space* at all times and then i turned off shadows and some other windows effects and it was immediately cured. i just did the same to my roommate's computer and its performance issues were also immediately cured. okay. i guess.
so i guess if you have creaky freezy windows 10/11 try searching "advanced system settings", go to performance settings, and uncheck "show shadows under windows" and anything else you don't want. hope that helps someone else.
*yes sorry i mean usage i posted this before bed :( i do not mean the hard drive is full aaaaghhhh
168K notes
·
View notes
Text
goodbye 2023👋hello 𓏏𓉔𓇋𓋴 𓇌𓅂𓄿𓂋 𓇋 𓅃𓇋𓃭𓃭 𓎼𓅂𓏏 𓄿 𓅓𓅲𓅓𓅓𓇌 𓃀𓅱𓇌𓆑𓂋𓇋𓅂𓈖𓂧 𓅓𓄿𓇌𓃀𓅂 𓉔𓅲𓋴𓃀𓄿𓈖𓂧 𓇋𓆑 𓉔𓅂𓂕𓋴 𓎢𓅱𓅱𓃭 𓅃𓇋𓏏𓉔 𓏏𓉔𓄿𓏏
156K notes
·
View notes
Text
If you’re lucky enough to be staying at the Beverly Hilton or the Waldorf Astoria Beverly Hills hotels any time soon, your green conscience can rest clean – the two luxury hotels are now cutting down on fossil fuels and reducing carbon emissions using an Israeli technology based on ice.
Israeli startup Nostromo Energy has a solution that stores energy in modular ice capsules installed on the roof, walls or basements of commercial and industrial buildings and then directs it to cool down commercial spaces, a procedure that usually accounts for up to 45 percent of global power demand during peak hours.
Read More: Israel21c
7 notes
·
View notes
Text
Happy New Year 2024 from Korea.
Year of the 🐲🐉!
#Seoul#korea#happy 2024#new year#drone show#drone#fireworks#amazing#video#viral#3d#technology#🎇#nature#space#Star#night#earth#awesome#tumblr#hd#dragon#dragon year#chinese#tradition#art#love#moon#animal
100K notes
·
View notes
Text

Source

#good news#politics#us politics#abolish landlords#government#the left#progressive#current events#news#activism#Hawaii#housing rights
75K notes
·
View notes
Text
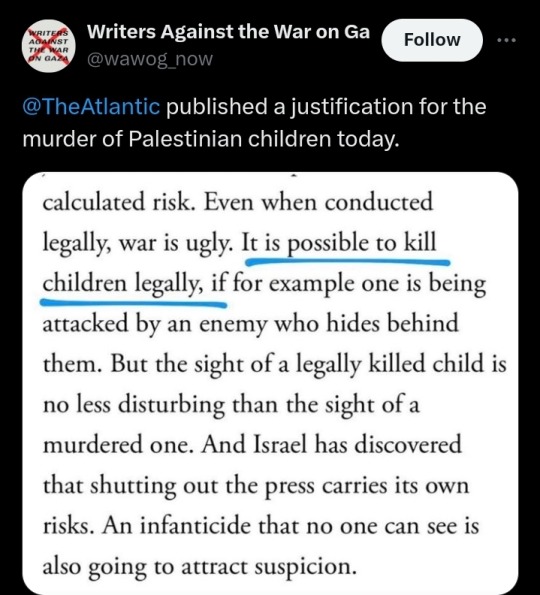
If you, for some reason, still have a subscription to the Atlantic, cancel it
#yemen#jerusalem#tel aviv#current events#palestine#free palestine#gaza#free gaza#news on gaza#palestine news#news update#war news#war on gaza#children of gaza#gaza genocide#genocide#media bias#manufactured consent
63K notes
·
View notes