#API And Application Protection
Explore tagged Tumblr posts
Text
ThreatX in 2023 Gartner Hype

ThreatX, a prominent API and application protection platform, has earned recognition in three categories as a Sample Vendor in the Gartner Hype Cycle reports for 2023. These reports include the Gartner Hype Cycle for Application Security 2023, the Gartner Hype Cycle for APIs 2023, and the Gartner Hype Cycle for Workload and Network Security 2023. ThreatX's presence in these reports underscores its commitment to delivering robust security tools for applications, APIs, and cloud Web Application and API Protection (WAAP) to enhance layered defense strategies and effectively counter emerging threats.
The 2023 Gartner Hype Cycle for Application Security highlights the evolving landscape of application security, characterized by intense transformation and growth. Organizations are increasingly developing their own applications using agile methodologies, relying on developers for code security rather than traditional security practitioners. This shift, coupled with new application architectures like cloud-native structures, poses challenges to established security approaches, rendering existing security controls less effective. Moreover, real-world attacks targeting applications and workloads are on the rise.
ThreatX distinguishes itself as the sole solution capable of safeguarding both APIs and applications at the edge and in real-time through risk-based, immediate blocking. What sets ThreatX apart is its ability not only to identify threats but also to thwart them in real-time. It employs risk-based blocking, which activates when an attacker's behavior surpasses a predefined threshold. Furthermore, ThreatX's Runtime API and Application Protection (RAAP) extends protection to running APIs and applications, providing organizations with a comprehensive capability to detect, track, and block threats effectively.
1 note
·
View note
Text
New Survey Finds Balancing AI’s Ease of Use with Trust is Top of Business Leaders Minds
New Post has been published on https://thedigitalinsider.com/new-survey-finds-balancing-ais-ease-of-use-with-trust-is-top-of-business-leaders-minds/
New Survey Finds Balancing AI’s Ease of Use with Trust is Top of Business Leaders Minds


A recent CIO report revealed that enterprises are investing up to $250 million in AI despite struggling to prove ROI. Business leaders are on a quest for productivity, but with new technology integration comes the need to potentially refactor existing applications, update processes, and inspire workers to learn and adapt to the modern business environment.
Nate MacLeitch, CEO of QuickBlox surveyed 136 executives to uncover the realities of AI adoption—looking at leaders’ top priorities, primary concerns, and where they seek trusted information about their prospective tools in 2025.
Are We Sacrificing Trust for Efficiency?
The survey results found ease of use and integration (72.8%) to be the top driver when selecting business AI tools. Yet, when asked about their primary concerns during the selection process, 60.3% voted privacy and security as their biggest worries. This emphasis on ease of use, however, raises questions about whether security is being adequately prioritized.
It is becoming easier for humans and machines to communicate, enabling AI users to accomplish more with greater proficiency. Businesses can automate tasks, optimize processes, and make better decisions with user-friendly analytics.
API-driven AI and microservices will allow businesses to integrate advanced AI functions into their existing systems in a modular fashion. Pair this with no-code solutions, auto-ML, and voice-controlled multimodal virtual assistants and this approach will speed up the development of custom applications without requiring extensive AI expertise.
Through continued exploration and optimization, AI is projected to add USD 4.4 trillion to the global economy. The crucial and complex part to keep in mind today is verifying that these pre-built solutions comply with regulatory and ethical AI practices. Strong encryption, tight access control, and regular checks keep data safe in these AI systems.
It’s also worth checking what ethical AI frameworks providers follow to build trust, avoid harm, and ensure AI benefits everyone. Some noted ones include, the EU AI Act, OECD AI Principles, UNESCO AI Ethics Framework, IEEE Ethically Aligned Design (EAD) Guidelines, and NIST AI Risk Management Framework.
What Do Leaders Need, and Where Do They Go To Get It?
Although data privacy concerns were leaders’ biggest worries during the AI selection phase, when asked about their integration challenges, only 20.6% ranked it as a primary issue. Instead, 41.2% of leaders stated that costs of integration were top of mind.
Interestingly, however, when asked “What additional support do you need?” the response “More affordable options” was ranked the lowest, with leaders more focused on finding training and education (56.6%), customized solutions (54.4%), and technical support (54.4%). This suggests that people aren’t just going after the cheapest options—they are looking for providers that can support them with integration and security. They would prefer to find trusted partners to guide them through proper data privacy protection methods and are willing to pay for it.
External information sources are the go-to when researching which AI applications leaders can trust. When asked to choose between social networking platforms, blogs, community platforms, and online directories as their most trusted source of information when deciding on tools, an equal majority of 54.4% said LinkedIn and X.
It is likely that these two platforms were most trusted due to the vast amount of professionals available to connect with. On LinkedIn, leaders can follow company pages, best practices, product information, and interests shared via posts, review peers’ comments, and even open conversations with other peers to gain insights from firsthand experiences. Similarly, on X, leaders can follow industry experts, analysts, and companies to stay informed about the latest developments. The platform’s fast-paced nature means if an AI tool is trending, platform members will hear about it.
Still, the potential for misinformation and biased opinions exists on any social media platform. Decision-makers must be mindful to consider a combination of online research, expert consultations, and vendor demonstrations when making AI tool purchasing decisions.
Can Leadership Evolve Fast Enough?
Limited internal expertise to manage AI was listed by 26.5% as their second biggest concern during integration, second only to integration costs. A recent IBM study on AI in the workplace found that 87% of business leaders expect at least a quarter of their workforce will need to reskill in response to generative AI and automation. While finding the right partner is a good start, what strategies can leaders use to train teams on the required information and achieve successful adoption?
Slow and steady wins the race, but aim to make every minute count. Business leaders must realize regulatory compliance and prepare their operations and workforce. This involves creating effective AI governance strategies built upon five pillars: explainability, fairness, robustness, transparency, and privacy.
It helps when everyone is on the same page—with employees who share your eagerness to adopt more efficient strategies. Start by showing them what’s in it for them. Higher profits? Less stressful workloads? Opportunities to learn and advance? It helps to have evidence to back up your statements. Be prepared to deliver some quick wins or pilot projects that solve more simple pain points. For example, in a healthcare scenario, this could be transcribing patient calls and auto-filling intake forms for doctors’ approval.
Nevertheless, you cannot predict what is on everyone’s minds, so it’s important to create spaces where teams feel comfortable sharing ideas, concerns, and feedback without fear of judgment or reprisal. This also offers the chance to discover and solve pain points you didn’t know existed. Fostering psychological safety is also crucial when adjusting to new processes. Frame failures as valuable learning experiences, not setbacks, to help encourage forward momentum.
Adopting AI in business isn’t just about efficiency gains—it’s about striking the right balance between usability, security, and trust. While companies recognize AI’s potential to reduce costs and streamline operations, they face real challenges, including integration expenses, and a growing need for AI-specific skills. Employees worry about job displacement, and leadership must proactively address these fears through transparency and upskilling initiatives. Robust AI governance is critical to navigating compliance, ethical considerations, and data protection. Ultimately, making AI work in the real world comes down to clear communication, tangible benefits, and a security-first culture that encourages experimentation.
#2025#250#access control#ADD#adoption#ai#ai act#AI adoption#AI Ethics#ai governance#AI systems#ai tools#Analytics#API#applications#approach#automation#back up#Business#business environment#CEO#cio#code#communication#Community#Companies#compliance#data#data privacy#data protection
1 note
·
View note
Text
YouTube says it will intentionally cripple the playback of its videos in third-party apps that block its ads. A Monday post in YouTube's help forum notes netizens using applications that strip out adverts while streaming YouTube videos may encounter playback issues due to buffering or error messages indicating that the content is not available. "We want to emphasize that our terms don’t allow third-party apps to turn off ads because that prevents the creator from being rewarded for viewership, and Ads on YouTube help support creators and let billions of people around the world use the streaming service," said a YouTube team member identified as Rob. "We also understand that some people prefer an entirely ad-free experience, which is why we offer YouTube Premium." This crackdown is coming at the API level, as these outside apps use this interface to access the Google-owned giant's videos. Last year, YouTube acknowledged it was running scripts to detect ad-blocking extensions in web browsers, which ended up interfering with Firefox page loads and prompted a privacy complaint to Ireland's Data Protection Commission. And several months before that, the internet video titan experimented with popup notifications warning YouTube web visitors that ad-blocking software is not allowed. A survey published last month by Ghostery, a maker of software that promotes privacy by blocking ads and tracking scripts, found that Google's efforts to crack down on ad blocking made about half of respondents (49 percent) more willing to use an ad blocker. According to the survey, the majority of Americans now use advert blockers, something recommended by the FBI when conducting internet searches.
Download NewPipe, it's what I use on Android
276 notes
·
View notes
Note
"we should boycott the use of this capital good, seeing as how it's being monopolized."
"but if it were socialist we wouldn't have to boycott it. it's not inherently evil."
[nothing happens]
capital is not a good, it is a social relation to the means of production.
capital cannot be boycotted, only consumer goods can.
boycotts (against consumer goods) are executed in an organized, targeted fashion with specific goals. otherwise it's not a boycott, it's just a consumer choice.
needless to say there exists no organized boycott campaign on AI art. even if it did, it would not be very useful because AI companies make money by licensing their API to other companies and end users are not a primary source of direct revenue for them.
there exists no monopoly on art or AI art -- not only can you use many different image generation services but you can download stable diffusion right now and make your own. you can also still Draw. there exists no monopoly here on anything
where there has been (effective, organized action) against the use of AI technology to immiserate workers (not the technology itself, only specific applications by employers) in the form of industrial action (e.g. the AI elements of the WGA and SAG-AFTRA strike demands, which were to be clear not the primary causes of those strikes) it has, shockingly, worked, and far more than "nothing" has happened, & it was good and awesome and should happen more
i'm not telling anyone not to take effective industrial action to secure labour protections from new technologies obvsies.
ceterum censeo IP law esse delendam
320 notes
·
View notes
Text
How Can Legacy Application Support Align with Your Long-Term Business Goals?
Many businesses still rely on legacy applications to run core operations. These systems, although built on older technology, are deeply integrated with workflows, historical data, and critical business logic. Replacing them entirely can be expensive and disruptive. Instead, with the right support strategy, these applications can continue to serve long-term business goals effectively.

1. Ensure Business Continuity
Continuous service delivery is one of the key business objectives of any enterprise. Maintenance of old applications guarantees business continuity, which minimizes chances of business interruption in case of software malfunctions or compatibility errors. These applications can be made to work reliably with modern support strategies such as performance monitoring, frequent patching, system optimization, despite changes in the rest of the system changes in the rest of the systems. This prevents the lost revenue and downtime of unplanned outages.
2. Control IT Costs
A straight replacement of the legacy systems is a capital intensive process. By having support structures, organizations are in a position to prolong the life of such applications and ensure an optimal IT expenditure. The cost saved can be diverted into innovation or into technologies that interact with the customers. An effective support strategy manages the total cost of ownership (TCO), without sacrificing performance or compliance.
3. Stay Compliant and Secure
The observance of industry regulations is not negotiable. Unsupported legacy application usually fall out of compliance with standards changes. This is handled by dedicated legacy application support which incorporates security updates, compliances patching and audit trails maintenance. This minimizes the risks of regulatory fines and reputational loss as well as governance and risk management objectives.
4. Connect with Modern Tools
Legacy support doesn’t mean working in isolation. With the right approach, these systems can connect to cloud platforms, APIs, and data tools. This enables real-time reporting, improved collaboration, and more informed decision-making—without requiring full system replacements.
5. Protect Business Knowledge
The legacy systems often contain years of institutional knowledge built into workflows, decision trees, and data architecture. They should not be abandoned early because vital operational insights may be lost. Maintaining these systems enables enterprises to keep that knowledge and transform it into documentation or reusable code aligned with ongoing digital transformation initiatives.
6. Support Scalable Growth
Well-supported legacy systems can still grow with your business. With performance tuning and capacity planning, they can handle increased demand and user loads. This keeps growth on track without significant disruption to IT systems.
7. Increase Flexibility and Control
Maintaining legacy application—either in-house or through trusted partners—gives businesses more control over their IT roadmap. It avoids being locked into aggressive vendor timelines and allows change to happen on your terms.
Legacy applications don’t have to be a roadblock. With the right support model, they become a stable foundation that supports long-term goals. From cost control and compliance to performance and integration, supported legacy systems can deliver measurable value. Specialized Legacy Application Maintenance Services are provided by service vendors such as Suma Soft, TCS, Infosys, Capgemini, and HCLTech, to enable businesses to get the best out of their current systems, as they prepare to transform in the future. Choosing the appropriate partner will maintain these systems functioning, developing and integrated with wider business strategies.
#BusinessContinuity#DigitalTransformation#ITStrategy#EnterpriseIT#BusinessOptimization#TechLeadership#ScalableSolutions#SmartITInvestments
3 notes
·
View notes
Text
Web to Mobile: Building Seamless Apps with .NET"
.NET is a effective, flexible, and open-supply developer platform created with the aid of Microsoft. It enables the creation of a huge range of applications—from computing device to cellular, net, cloud, gaming, and IoT. Over the years, .NET has evolved substantially and has become one of the maximum extensively used frameworks inside the software improvement enterprise.
Dot Net Programming Language

A Brief History of .NET
The .NET Framework become first delivered through Microsoft in the early 2000s. The original cause turned into to offer a steady item-oriented programming surroundings regardless of whether code became stored and finished locally, remotely, or via the internet.
Over time, Microsoft developed .NET right into a cross-platform, open-supply framework. In 2016, Microsoft launched .NET Core, a modular, high-performance, cross-platform implementation of .NET. In 2020, the company unified all its .NET technologies beneath one umbrella with the discharge of .NET five, and later persisted with .NET 6, .NET 7, and past.
Today, the unified platform is actually called .NET, and it allows builders to build apps for Windows, macOS, Linux, iOS, Android, and greater using a single codebase.
Key Features of .NET
1. Cross-Platform Development
One of the maximum tremendous features of present day .NET (publish .NET Core) is its ability to run on a couple of platforms. Developers can construct and deploy apps on Windows, Linux, and macOS with out enhancing their codebases.
2. Multiple Language Support
.NET supports numerous programming languages, together with:
C# – the maximum extensively used language in .NET development
F# – a purposeful-first programming language
Visual Basic – an smooth-to-analyze language, regularly used in legacy programs
This multilingual capability allows developers to pick out the nice language for their precise use cases.
3. Extensive Library and Framework Support
.NET offers a comprehensive base magnificence library (BCL) and framework libraries that aid the whole lot from record studying/writing to XML manipulation, statistics get entry to, cryptography, and extra.
Four. ASP.NET for Web Development
ASP.NET is a part of the .NET platform specially designed for net improvement. ASP.NET Core, the cross-platform model, permits builders to build scalable internet APIs, dynamic web sites, and actual-time packages the usage of technology like SignalR.
5. Rich Development Environment
.NET integrates seamlessly with Visual Studio, one of the most function-wealthy integrated development environments (IDEs) available. Visual Studio offers capabilities together with IntelliSense, debugging tools, challenge templates, and code refactoring.
6. Performance and Scalability
.NET is thought for high performance and scalability, especially with its guide for asynchronous programming using async/wait for and its Just-In-Time (JIT) compilation.
7. Secure and Reliable
.NET presents sturdy safety features, including code get entry to security, role-based protection, and cryptography training. It also handles reminiscence management thru rubbish series, minimizing reminiscence leaks.
Common Applications Built with .NET
1. Web Applications
With ASP.NET Core, builders can create cutting-edge, scalable internet programs and RESTful APIs. Razor Pages and Blazor are technology within ASP.NET Core that help server-facet and purchaser-facet rendering.
2. Desktop Applications
Using Windows Forms or Windows Presentation Foundation (WPF), builders can build conventional computing device applications. .NET MAUI (Multi-platform App UI) now extends this functionality to move-platform computer and cellular programs.
3. Mobile Applications
Through Xamarin (now incorporated into .NET MAUI), developers can create native mobile applications for Android and iOS the usage of C#.
4. Cloud-Based Applications
.NET is nicely-acceptable for cloud development, in particular with Microsoft Azure. Developers can build cloud-local apps, serverless capabilities, and containerized microservices the usage of Docker and Kubernetes.
5. IoT Applications
.NET helps Internet of Things (IoT) development, allowing builders to construct applications that engage with sensors and gadgets.
6. Games
With the Unity sport engine, which helps C#, developers can use .NET languages to create 2D, three-D, AR, and VR games.
Components of .NET
1. .NET SDK
The Software Development Kit includes everything had to build and run .NET packages: compilers, libraries, and command-line tools.
2. CLR (Common Language Runtime)
It handles reminiscence control, exception managing, and rubbish collection.
Three. BCL (Base Class Library)
The BCL offers center functionalities including collections, record I/O, records kinds, and extra.
4. NuGet
NuGet is the package manager for .NET. It lets in builders to install, manage, and share libraries without problems.
Modern .NET Versions
.NET five (2020): Unified the .NET platform (Core + Framework)
.NET 7 (2022): Further overall performance enhancements and more desirable APIs
.NET 8 (2023): Continued attention on cloud-native, cellular, and web improvement
Advantages of Using .NET
Cross-platform assist – construct as soon as, run everywhere
Large developer network – widespread sources, libraries, and frameworks
Robust tooling – especially with Visual Studio and JetBrains Rider
Active improvement – backed by using Microsoft and open-source community
Challenges and Considerations
Learning curve – particularly for beginners due to its giant atmosphere
Legacy framework – older .NET Framework tasks aren't like minded with .NET Core or more recent variations without migration
Platform differences – sure APIs or libraries might also behave in a different way throughout operating systems
Getting Started with .NET
To begin growing with .NET:
Install the .NET SDK from the legitimate .NET internet site.
Create a new project: Use the dotnet new command or Visual Studio templates.
Write code: Develop your logic the usage of C#, F#, or VB.NET.
#btech students#bca students#online programming courses#offline institute programming courses#regular colleges university#Dot Net Programming Language
2 notes
·
View notes
Text
Symfony Clickjacking Prevention Guide
Clickjacking is a deceptive technique where attackers trick users into clicking on hidden elements, potentially leading to unauthorized actions. As a Symfony developer, it's crucial to implement measures to prevent such vulnerabilities.

🔍 Understanding Clickjacking
Clickjacking involves embedding a transparent iframe over a legitimate webpage, deceiving users into interacting with hidden content. This can lead to unauthorized actions, such as changing account settings or initiating transactions.
🛠️ Implementing X-Frame-Options in Symfony
The X-Frame-Options HTTP header is a primary defense against clickjacking. It controls whether a browser should be allowed to render a page in a <frame>, <iframe>, <embed>, or <object> tag.
Method 1: Using an Event Subscriber
Create an event subscriber to add the X-Frame-Options header to all responses:
// src/EventSubscriber/ClickjackingProtectionSubscriber.php namespace App\EventSubscriber; use Symfony\Component\EventDispatcher\EventSubscriberInterface; use Symfony\Component\HttpKernel\Event\ResponseEvent; use Symfony\Component\HttpKernel\KernelEvents; class ClickjackingProtectionSubscriber implements EventSubscriberInterface { public static function getSubscribedEvents() { return [ KernelEvents::RESPONSE => 'onKernelResponse', ]; } public function onKernelResponse(ResponseEvent $event) { $response = $event->getResponse(); $response->headers->set('X-Frame-Options', 'DENY'); } }
This approach ensures that all responses include the X-Frame-Options header, preventing the page from being embedded in frames or iframes.
Method 2: Using NelmioSecurityBundle
The NelmioSecurityBundle provides additional security features for Symfony applications, including clickjacking protection.
Install the bundle:
composer require nelmio/security-bundle
Configure the bundle in config/packages/nelmio_security.yaml:
nelmio_security: clickjacking: paths: '^/.*': DENY
This configuration adds the X-Frame-Options: DENY header to all responses, preventing the site from being embedded in frames or iframes.
🧪 Testing Your Application
To ensure your application is protected against clickjacking, use our Website Vulnerability Scanner. This tool scans your website for common vulnerabilities, including missing or misconfigured X-Frame-Options headers.

Screenshot of the free tools webpage where you can access security assessment tools.
After scanning for a Website Security check, you'll receive a detailed report highlighting any security issues:

An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
🔒 Enhancing Security with Content Security Policy (CSP)
While X-Frame-Options is effective, modern browsers support the more flexible Content-Security-Policy (CSP) header, which provides granular control over framing.
Add the following header to your responses:
$response->headers->set('Content-Security-Policy', "frame-ancestors 'none';");
This directive prevents any domain from embedding your content, offering robust protection against clickjacking.
🧰 Additional Security Measures
CSRF Protection: Ensure that all forms include CSRF tokens to prevent cross-site request forgery attacks.
Regular Updates: Keep Symfony and all dependencies up to date to patch known vulnerabilities.
Security Audits: Conduct regular security audits to identify and address potential vulnerabilities.
📢 Explore More on Our Blog
For more insights into securing your Symfony applications, visit our Pentest Testing Blog. We cover a range of topics, including:
Preventing clickjacking in Laravel
Securing API endpoints
Mitigating SQL injection attacks
🛡️ Our Web Application Penetration Testing Services
Looking for a comprehensive security assessment? Our Web Application Penetration Testing Services offer:
Manual Testing: In-depth analysis by security experts.
Affordable Pricing: Services starting at $25/hr.
Detailed Reports: Actionable insights with remediation steps.
Contact us today for a free consultation and enhance your application's security posture.
3 notes
·
View notes
Text
Best Payment Gateway In India– Quick Pay

In today's digital era, businesses of all sizes need a reliable, secure, and efficient payment gateway to process online transactions. Whether you're running an e-commerce store, a subscription-based service, or a brick-and-mortar shop expanding to digital payments, choosing the right payment gateway can significantly impact your success. Among the many options available, Quick Pay has emerged as one of the best payment gateways in the industry.
This article explores the features, benefits, security measures, and why Quick Pay is the preferred choice for businesses worldwide.
What is Quick Pay?
Quick Pay is a cutting-edge payment gateway solution that facilitates seamless online transactions between merchants and customers. It offers a secure and user-friendly interface, allowing businesses to accept payments via credit cards, debit cards, mobile wallets, and bank transfers. Quick Pay supports multiple currencies and integrates with various e-commerce platforms, making it a versatile choice for businesses operating locally and globally.
Key Features of Quick Pay
1. Multi-Channel Payment Support
One of the standout features of Quick Pay is its ability to support multiple payment channels, including:
Credit and debit card processing (Visa, Mastercard, American Express, etc.)
Mobile wallets (Apple Pay, Google Pay, PayPal, etc.)
Bank transfers and direct debit
QR code payments
Buy Now, Pay Later (BNPL) services
This flexibility ensures that businesses can cater to customers' diverse payment preferences, thereby enhancing the checkout experience and improving sales conversion rates.
2. Seamless Integration
Quick Pay offers seamless integration with major e-commerce platforms like Shopify, WooCommerce, Magento, and BigCommerce. Additionally, it provides APIs and plugins that allow businesses to customize payment processing according to their specific needs. Developers can easily integrate Quick Pay into their websites and mobile applications without extensive coding knowledge.
3. High-Level Security & Fraud Prevention
Security is a top priority for any payment gateway, and Quick Pay excels in this area with:
PCI DSS compliance (Payment Card Industry Data Security Standard)
Advanced encryption technology to protect sensitive data
AI-driven fraud detection and prevention mechanisms
3D Secure authentication for an extra layer of security
By implementing these security measures, Quick Pay minimizes fraudulent transactions and enhances customer trust.
4. Fast and Reliable Transactions
Speed and reliability are crucial in online payments. Quick Pay ensures that transactions are processed swiftly with minimal downtime. It supports instant payment processing, reducing wait times for merchants and customers alike. Businesses can also benefit from automated settlement features that streamline fund transfers to their bank accounts.
5. Competitive Pricing & Transparent Fees
Unlike many payment gateways that have hidden charges, Quick Pay provides transparent pricing models. It offers:
No setup fees
Low transaction fees with volume-based discounts
No hidden maintenance or withdrawal charges
Custom pricing plans for high-volume merchants
This cost-effective approach makes Quick Pay a preferred choice for startups and large enterprises alike.
6. Recurring Payments & Subscription Billing
For businesses offering subscription-based services, Quick Pay provides a robust recurring payment system. It automates billing cycles, reducing manual efforts while ensuring timely payments. Customers can set up autopay, making it convenient for them and improving customer retention rates for businesses.
7. Multi-Currency & Global Payment Support
In an increasingly globalized economy, accepting international payments is vital. Quick Pay supports transactions in multiple currencies and offers dynamic currency conversion. This allows businesses to cater to international customers without dealing with complex exchange rate issues.
Benefits of Using Quick Pay
1. Enhanced Customer Experience
Quick Pay ensures a smooth checkout experience by providing multiple payment options and a user-friendly interface. Faster payment processing reduces cart abandonment and boosts customer satisfaction.
2. Improved Business Efficiency
With automated invoicing, seamless integration, and real-time transaction tracking, businesses can streamline their payment operations, saving time and resources.
3. Higher Security & Reduced Fraud Risk
With its state-of-the-art security measures, Quick Pay minimizes risks associated with fraud and data breaches. This enhances business credibility and customer trust.
4. Increased Sales & Revenue
Supporting multiple payment options and international transactions helps businesses tap into a broader customer base, leading to higher sales and revenue growth.
How to Set Up Quick Pay for Your Business?
Setting up Quick Pay is a straightforward process:
Sign Up – Visit the Quick Pay website and create an account.
Verify Business Details – Submit the required business documents for verification.
Integrate Quick Pay – Use APIs, plugins, or custom scripts to integrate Quick Pay into your website or app.
Configure Payment Options – Select the preferred payment methods you want to offer customers.
Go Live – Once approved, start accepting payments seamlessly.
Why Quick Pay Stands Out Among Competitors
While several payment gateways exist, Quick Pay differentiates itself with:
Superior security measures compared to standard gateways.
Faster payouts than many competitors, ensuring businesses receive funds quicker.
Customer-friendly interface making it easier for both merchants and users.
Scalability, accommodating businesses from small startups to large enterprises.
Conclusion
Quick Pay is undoubtedly one of the best payment gateway in India available today. Its blend of security, efficiency, affordability, and ease of use makes it an ideal choice for businesses across various industries. Whether you run an e-commerce store, a SaaS business, or a global enterprise, Quick Pay ensures smooth, secure, and hassle-free payment processing.
By choosing Quick Pay, businesses can enhance customer experience, reduce fraud risks, and boost revenue. With seamless integration, multi-currency support, and advanced features, Quick Pay is the go-to payment gateway for modern businesses looking for a reliable and future-proof payment solution.
Are you ready to streamline your payments and take your business to the next level? Sign up for Quick Pay today!
2 notes
·
View notes
Text
Revolutionizing DeFi Development: How STON.fi API & SDK Simplify Token Swaps

The decentralized finance (DeFi) landscape is evolving rapidly, and developers are constantly seeking efficient ways to integrate token swap functionalities into their platforms. However, building seamless and optimized swap mechanisms from scratch can be complex, time-consuming, and risky.
This is where STON.fi API & SDK come into play. They provide developers with a ready-to-use, optimized solution that simplifies the process of enabling fast, secure, and cost-effective swaps.
In this article, we’ll take an in-depth look at why developers need efficient swap solutions, how the STON.fi API & SDK work, and how they can be integrated into various DeFi applications.
Why Developers Need a Robust Swap Integration
One of the core functions of any DeFi application is token swapping—the ability to exchange one cryptocurrency for another instantly and at the best possible rate.
But integrating swaps manually is not a straightforward task. Developers face several challenges:
Complex Smart Contract Logic – Handling liquidity pools, slippage, and price calculations requires expertise and rigorous testing.
Security Vulnerabilities – Improperly coded swaps can expose user funds to attacks.
Performance Issues – Slow execution or high gas fees can frustrate users and hurt adoption.
A poorly integrated swap feature can turn users away from a DeFi application, affecting engagement and liquidity. That’s why an efficient, battle-tested API and SDK can make a significant difference.
STON.fi API & SDK: What Makes Them a Game-Changer?
STON.fi has built an optimized API and SDK designed to handle the complexities of token swaps while giving developers an easy-to-use toolkit. Here’s why they stand out:
1. Seamless Swap Execution
Instead of manually routing transactions through liquidity pools, the STON.fi API automates the process, ensuring users always get the best swap rates.
2. Developer-Friendly SDK
For those who prefer working with structured development tools, the STON.fi SDK comes with pre-built functions that remove the need for extensive custom coding. Whether you’re integrating swaps into a mobile wallet, trading platform, or decentralized app, the SDK simplifies the process.
3. High-Speed Performance & Low Costs
STON.fi’s infrastructure is optimized for fast transaction execution, reducing delays and minimizing slippage. Users benefit from lower costs, while developers get a plug-and-play solution that ensures a smooth experience.
4. Secure & Scalable
Security is a major concern in DeFi, and STON.fi’s API is built with strong security measures, protecting transactions from vulnerabilities and ensuring reliability even under heavy traffic.
Practical Use Cases for Developers
1. Building Decentralized Exchanges (DEXs)
STON.fi API enables developers to integrate swap functionalities directly into their DEX platforms without having to build custom liquidity management solutions.
2. Enhancing Web3 Wallets
Crypto wallets can integrate STON.fi’s swap functionality, allowing users to exchange tokens without leaving the wallet interface.
3. Automating Trading Strategies
The API can be used to build automated trading bots that execute swaps based on real-time market conditions, improving efficiency for traders.
4. Scaling DeFi Platforms
For DeFi applications handling high transaction volumes, STON.fi API ensures fast and cost-effective execution, improving user retention.
Why Developers Should Consider STON.fi API & SDK
For developers aiming to create efficient, user-friendly, and scalable DeFi applications, STON.fi offers a robust solution that eliminates the complexities of manual integrations.
Saves Development Time – Reduces the need for custom swap coding.
Improves Security – Pre-tested smart contracts minimize vulnerabilities.
Enhances User Experience – Faster swaps create a smoother, more reliable platform.
Optimizes Performance – Low latency and cost-efficient execution ensure better outcomes.
Whether you’re working on a new DeFi project or improving an existing platform, STON.fi’s API & SDK provide a solid foundation to enhance functionality and scalability.
By leveraging STON.fi’s tools, developers can focus on building innovative features, rather than getting caught up in the technical challenges of token swaps.
3 notes
·
View notes
Text
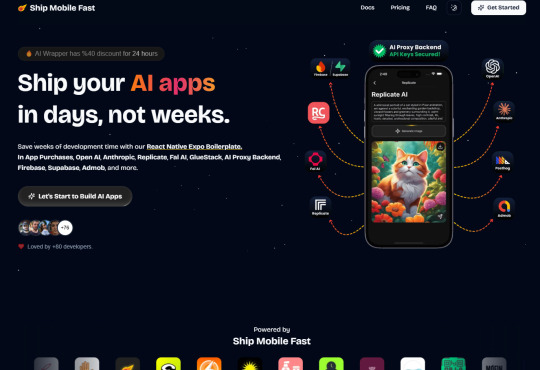
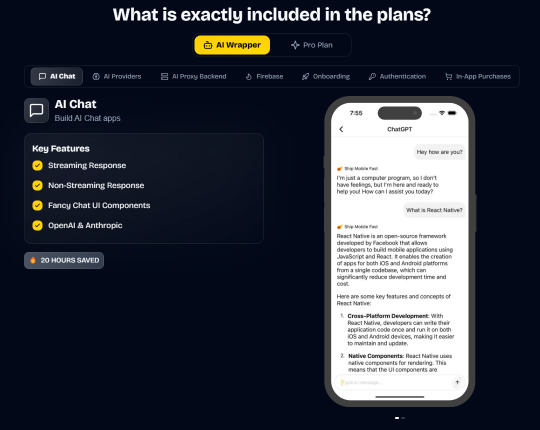
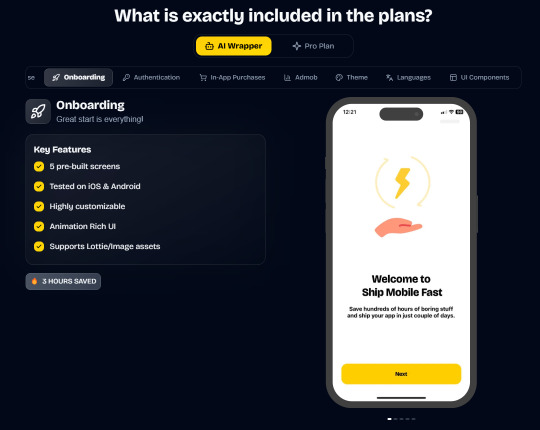
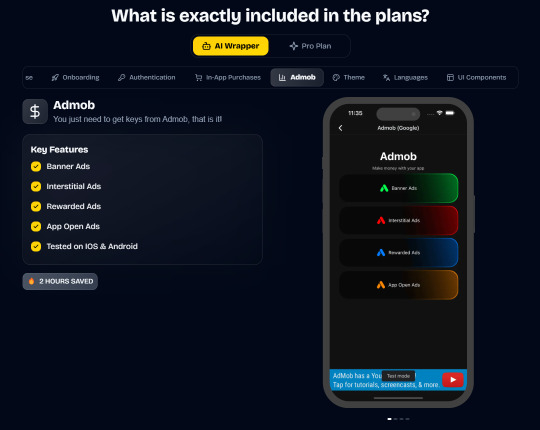
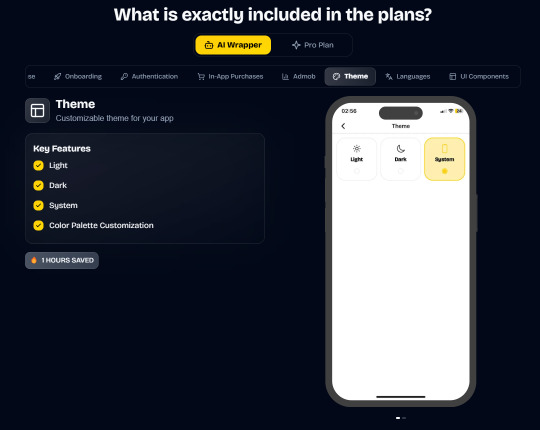
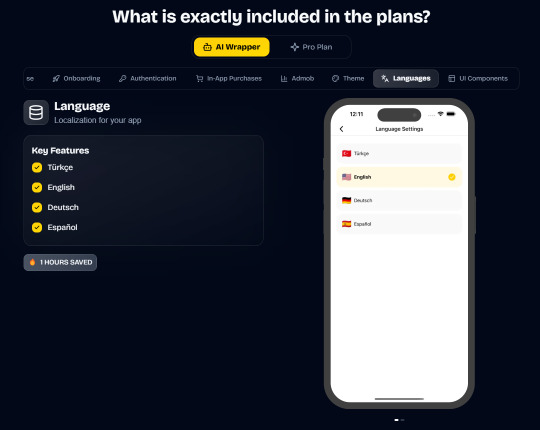
Ship Mobile Fast
Ship your AI apps in days, not weeks.
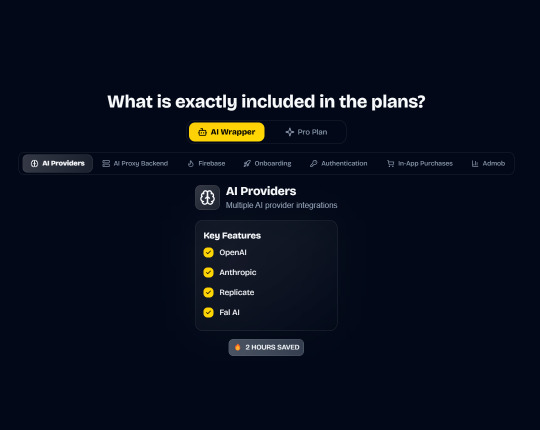
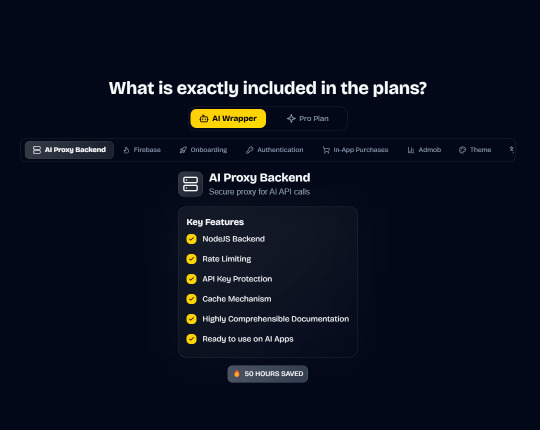
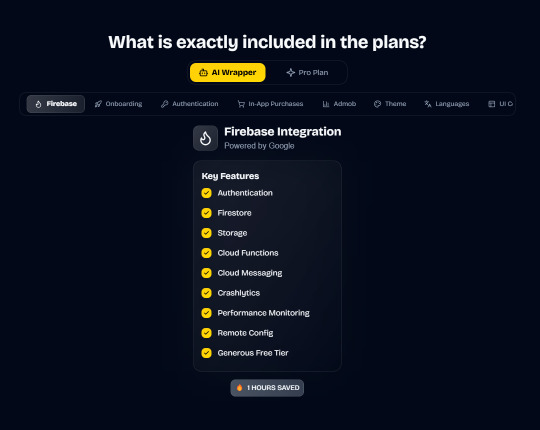
Save weeks of development time with our React Native Expo Boilerplate. In App Purchases, Open AI, Anthropic, Replicate, Fal AI, GlueStack, AI Proxy Backend, Firebase, Supabase, Admob, and more.
Ship Mobile Fast AI Wrapper is Live!🔥
For those who want to build AI applications…
Now, you can create the apps you envision in just 1-2 days.😎
Integrations with OpenAI, Anthropic, Replicate, and Fal AI. Protect your API keys from being stolen with AI Proxy Backend.
*
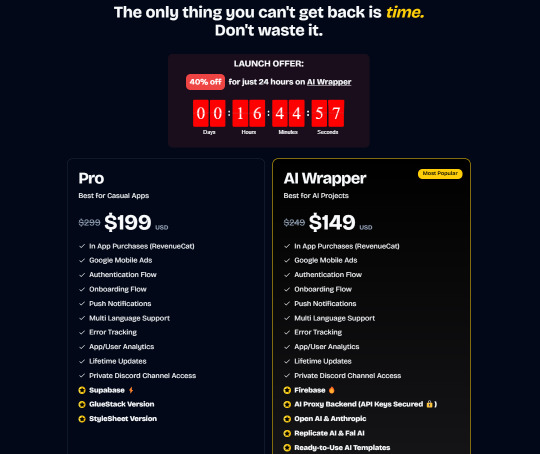
Pro (Best for Casual Apps):
In App Purchases (RevenueCat) Google Mobile Ads Authentication Flow Onboarding Flow Push Notifications Multi Language Support Error Tracking App/User Analytics Lifetime Updates Private Discord Channel Access Supabase⚡️ GlueStack Version StyleSheet Version
*
AI Wrapper (Best for AI Projects):
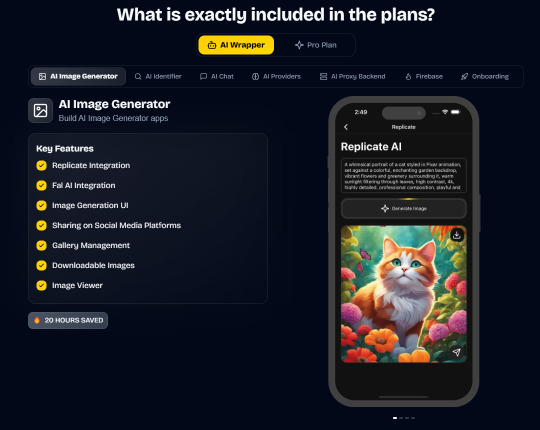
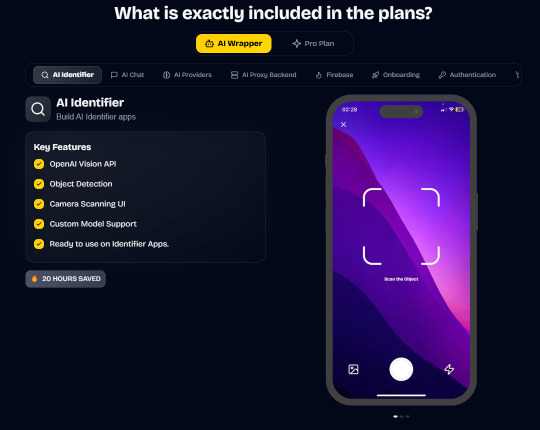
In App Purchases (RevenueCat) Google Mobile Ads Authentication Flow Onboarding Flow Push Notifications Multi Language Support Error Tracking App/User Analytics Lifetime Updates Private Discord Channel Access Firebase🔥 AI Proxy Backend (API Keys Secured🔒) Open AI & Anthropic Replicate AI & Fal AI Ready-to-Use AI Templates
*
Ship Mobile Fast: https://shipmobilefast.com/?aff=1nLNm
Telegram: ahmetmertugrul


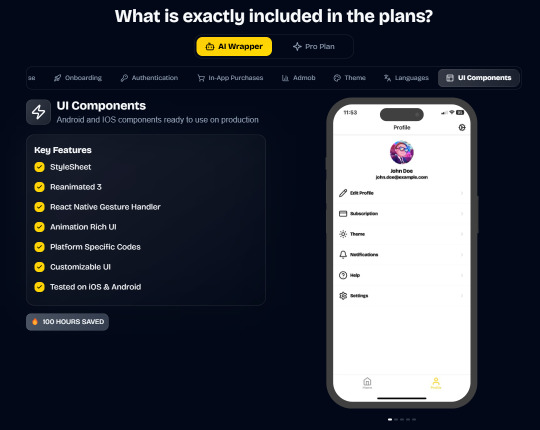
#ai#app#ship#mobile#fast#openai#claude#deepseek#proxy#api#admob#ads#firebase#supabase#falai#backend#ui#ux#replicate#revenuecat#google#expo#boilerplate#template#wrapper
2 notes
·
View notes
Text
Apple Unveils Mac OS X
Next Generation OS Features New “Aqua” User Interface
MACWORLD EXPO, SAN FRANCISCO
January 5, 2000
Reasserting its leadership in personal computer operating systems, Apple® today unveiled Mac® OS X, the next generation Macintosh® operating system. Steve Jobs demonstrated Mac OS X to an audience of over 4,000 people during his Macworld Expo keynote today, and over 100 developers have pledged their support for the new operating system, including Adobe and Microsoft. Pre-release versions of Mac OS X will be delivered to Macintosh software developers by the end of this month, and will be commercially released this summer.
“Mac OS X will delight consumers with its simplicity and amaze professionals with its power,” said Steve Jobs, Apple’s iCEO. “Apple’s innovation is leading the way in personal computer operating systems once again.”
The new technology Aqua, created by Apple, is a major advancement in personal computer user interfaces. Aqua features the “Dock” — a revolutionary new way to organize everything from applications and documents to web sites and streaming video. Aqua also features a completely new Finder which dramatically simplifies the storing, organizing and retrieving of files—and unifies these functions on the host computer and across local area networks and the Internet. Aqua offers a stunning new visual appearance, with luminous and semi-transparent elements such as buttons, scroll bars and windows, and features fluid animation to enhance the user’s experience. Aqua is a major advancement in personal computer user interfaces, from the same company that started it all in 1984 with the original Macintosh.
Aqua is made possible by Mac OS X’s new graphics system, which features all-new 2D, 3D and multimedia graphics. 2D graphics are performed by Apple’s new “Quartz” graphics system which is based on the PDF Internet standard and features on-the-fly PDF rendering, anti-aliasing and compositing—a first for any operating system. 3D graphics are based on OpenGL, the industry’s most-widely supported 3D graphics technology, and multimedia is based on the QuickTime™ industry standard for digital multimedia.
At the core of Mac OS X is Darwin, Apple’s advanced operating system kernel. Darwin is Linux-like, featuring the same Free BSD Unix support and open-source model. Darwin brings an entirely new foundation to the Mac OS, offering Mac users true memory protection for higher reliability, preemptive multitasking for smoother operation among multiple applications and fully Internet-standard TCP/IP networking. As a result, Mac OS X is the most reliable and robust Apple operating system ever.
Gentle Migration
Apple has designed Mac OS X to enable a gentle migration for its customers and developers from their current installed base of Macintosh operating systems. Mac OS X can run most of the over 13,000 existing Macintosh applications without modification. However, to take full advantage of Mac OS X’s new features, developers must “tune-up” their applications to use “Carbon”, the updated version of APIs (Application Program Interfaces) used to program Macintosh computers. Apple expects most of the popular Macintosh applications to be available in “Carbonized” versions this summer.
Developer Support
Apple today also announced that more than 100 leading developers have pledged their support for the new operating system, including Adobe, Agfa, Connectix, id, Macromedia, Metrowerks, Microsoft, Palm Computing, Quark, SPSS and Wolfram (see related supporting quote sheet).
Availability
Mac OS X will be rolled out over a 12 month period. Macintosh developers have already received two pre-releases of the software, and they will receive another pre-release later this month—the first to incorporate Aqua. Developers will receive the final “beta” pre-release this spring. Mac OS X will go on sale as a shrink-wrapped software product this summer, and will be pre-loaded as the standard operating system on all Macintosh computers beginning in early 2001. Mac OS X is designed to run on all Apple Macintosh computers using PowerPC G3 and G4 processor chips, and requires a minimum of 64 MB of memory.
4 notes
·
View notes
Text
Top 10 In- Demand Tech Jobs in 2025

Technology is growing faster than ever, and so is the need for skilled professionals in the field. From artificial intelligence to cloud computing, businesses are looking for experts who can keep up with the latest advancements. These tech jobs not only pay well but also offer great career growth and exciting challenges.
In this blog, we’ll look at the top 10 tech jobs that are in high demand today. Whether you’re starting your career or thinking of learning new skills, these jobs can help you plan a bright future in the tech world.
1. AI and Machine Learning Specialists
Artificial Intelligence (AI) and Machine Learning are changing the game by helping machines learn and improve on their own without needing step-by-step instructions. They’re being used in many areas, like chatbots, spotting fraud, and predicting trends.
Key Skills: Python, TensorFlow, PyTorch, data analysis, deep learning, and natural language processing (NLP).
Industries Hiring: Healthcare, finance, retail, and manufacturing.
Career Tip: Keep up with AI and machine learning by working on projects and getting an AI certification. Joining AI hackathons helps you learn and meet others in the field.
2. Data Scientists
Data scientists work with large sets of data to find patterns, trends, and useful insights that help businesses make smart decisions. They play a key role in everything from personalized marketing to predicting health outcomes.
Key Skills: Data visualization, statistical analysis, R, Python, SQL, and data mining.
Industries Hiring: E-commerce, telecommunications, and pharmaceuticals.
Career Tip: Work with real-world data and build a strong portfolio to showcase your skills. Earning certifications in data science tools can help you stand out.
3. Cloud Computing Engineers: These professionals create and manage cloud systems that allow businesses to store data and run apps without needing physical servers, making operations more efficient.
Key Skills: AWS, Azure, Google Cloud Platform (GCP), DevOps, and containerization (Docker, Kubernetes).
Industries Hiring: IT services, startups, and enterprises undergoing digital transformation.
Career Tip: Get certified in cloud platforms like AWS (e.g., AWS Certified Solutions Architect).
4. Cybersecurity Experts
Cybersecurity professionals protect companies from data breaches, malware, and other online threats. As remote work grows, keeping digital information safe is more crucial than ever.
Key Skills: Ethical hacking, penetration testing, risk management, and cybersecurity tools.
Industries Hiring: Banking, IT, and government agencies.
Career Tip: Stay updated on new cybersecurity threats and trends. Certifications like CEH (Certified Ethical Hacker) or CISSP (Certified Information Systems Security Professional) can help you advance in your career.
5. Full-Stack Developers
Full-stack developers are skilled programmers who can work on both the front-end (what users see) and the back-end (server and database) of web applications.
Key Skills: JavaScript, React, Node.js, HTML/CSS, and APIs.
Industries Hiring: Tech startups, e-commerce, and digital media.
Career Tip: Create a strong GitHub profile with projects that highlight your full-stack skills. Learn popular frameworks like React Native to expand into mobile app development.
6. DevOps Engineers
DevOps engineers help make software faster and more reliable by connecting development and operations teams. They streamline the process for quicker deployments.
Key Skills: CI/CD pipelines, automation tools, scripting, and system administration.
Industries Hiring: SaaS companies, cloud service providers, and enterprise IT.
Career Tip: Earn key tools like Jenkins, Ansible, and Kubernetes, and develop scripting skills in languages like Bash or Python. Earning a DevOps certification is a plus and can enhance your expertise in the field.
7. Blockchain Developers
They build secure, transparent, and unchangeable systems. Blockchain is not just for cryptocurrencies; it’s also used in tracking supply chains, managing healthcare records, and even in voting systems.
Key Skills: Solidity, Ethereum, smart contracts, cryptography, and DApp development.
Industries Hiring: Fintech, logistics, and healthcare.
Career Tip: Create and share your own blockchain projects to show your skills. Joining blockchain communities can help you learn more and connect with others in the field.
8. Robotics Engineers
Robotics engineers design, build, and program robots to do tasks faster or safer than humans. Their work is especially important in industries like manufacturing and healthcare.
Key Skills: Programming (C++, Python), robotics process automation (RPA), and mechanical engineering.
Industries Hiring: Automotive, healthcare, and logistics.
Career Tip: Stay updated on new trends like self-driving cars and AI in robotics.
9. Internet of Things (IoT) Specialists
IoT specialists work on systems that connect devices to the internet, allowing them to communicate and be controlled easily. This is crucial for creating smart cities, homes, and industries.
Key Skills: Embedded systems, wireless communication protocols, data analytics, and IoT platforms.
Industries Hiring: Consumer electronics, automotive, and smart city projects.
Career Tip: Create IoT prototypes and learn to use platforms like AWS IoT or Microsoft Azure IoT. Stay updated on 5G technology and edge computing trends.
10. Product Managers
Product managers oversee the development of products, from idea to launch, making sure they are both technically possible and meet market demands. They connect technical teams with business stakeholders.
Key Skills: Agile methodologies, market research, UX design, and project management.
Industries Hiring: Software development, e-commerce, and SaaS companies.
Career Tip: Work on improving your communication and leadership skills. Getting certifications like PMP (Project Management Professional) or CSPO (Certified Scrum Product Owner) can help you advance.
Importance of Upskilling in the Tech Industry
Stay Up-to-Date: Technology changes fast, and learning new skills helps you keep up with the latest trends and tools.
Grow in Your Career: By learning new skills, you open doors to better job opportunities and promotions.
Earn a Higher Salary: The more skills you have, the more valuable you are to employers, which can lead to higher-paying jobs.
Feel More Confident: Learning new things makes you feel more prepared and ready to take on tougher tasks.
Adapt to Changes: Technology keeps evolving, and upskilling helps you stay flexible and ready for any new changes in the industry.
Top Companies Hiring for These Roles
Global Tech Giants: Google, Microsoft, Amazon, and IBM.
Startups: Fintech, health tech, and AI-based startups are often at the forefront of innovation.
Consulting Firms: Companies like Accenture, Deloitte, and PwC increasingly seek tech talent.
In conclusion, the tech world is constantly changing, and staying updated is key to having a successful career. In 2025, jobs in fields like AI, cybersecurity, data science, and software development will be in high demand. By learning the right skills and keeping up with new trends, you can prepare yourself for these exciting roles. Whether you're just starting or looking to improve your skills, the tech industry offers many opportunities for growth and success.
#Top 10 Tech Jobs in 2025#In- Demand Tech Jobs#High paying Tech Jobs#artificial intelligence#datascience#cybersecurity
2 notes
·
View notes
Text
How-To IT
Topic: Core areas of IT
1. Hardware
• Computers (Desktops, Laptops, Workstations)
• Servers and Data Centers
• Networking Devices (Routers, Switches, Modems)
• Storage Devices (HDDs, SSDs, NAS)
• Peripheral Devices (Printers, Scanners, Monitors)
2. Software
• Operating Systems (Windows, Linux, macOS)
• Application Software (Office Suites, ERP, CRM)
• Development Software (IDEs, Code Libraries, APIs)
• Middleware (Integration Tools)
• Security Software (Antivirus, Firewalls, SIEM)
3. Networking and Telecommunications
• LAN/WAN Infrastructure
• Wireless Networking (Wi-Fi, 5G)
• VPNs (Virtual Private Networks)
• Communication Systems (VoIP, Email Servers)
• Internet Services
4. Data Management
• Databases (SQL, NoSQL)
• Data Warehousing
• Big Data Technologies (Hadoop, Spark)
• Backup and Recovery Systems
• Data Integration Tools
5. Cybersecurity
• Network Security
• Endpoint Protection
• Identity and Access Management (IAM)
• Threat Detection and Incident Response
• Encryption and Data Privacy
6. Software Development
• Front-End Development (UI/UX Design)
• Back-End Development
• DevOps and CI/CD Pipelines
• Mobile App Development
• Cloud-Native Development
7. Cloud Computing
• Infrastructure as a Service (IaaS)
• Platform as a Service (PaaS)
• Software as a Service (SaaS)
• Serverless Computing
• Cloud Storage and Management
8. IT Support and Services
• Help Desk Support
• IT Service Management (ITSM)
• System Administration
• Hardware and Software Troubleshooting
• End-User Training
9. Artificial Intelligence and Machine Learning
• AI Algorithms and Frameworks
• Natural Language Processing (NLP)
• Computer Vision
• Robotics
• Predictive Analytics
10. Business Intelligence and Analytics
• Reporting Tools (Tableau, Power BI)
• Data Visualization
• Business Analytics Platforms
• Predictive Modeling
11. Internet of Things (IoT)
• IoT Devices and Sensors
• IoT Platforms
• Edge Computing
• Smart Systems (Homes, Cities, Vehicles)
12. Enterprise Systems
• Enterprise Resource Planning (ERP)
• Customer Relationship Management (CRM)
• Human Resource Management Systems (HRMS)
• Supply Chain Management Systems
13. IT Governance and Compliance
• ITIL (Information Technology Infrastructure Library)
• COBIT (Control Objectives for Information Technologies)
• ISO/IEC Standards
• Regulatory Compliance (GDPR, HIPAA, SOX)
14. Emerging Technologies
• Blockchain
• Quantum Computing
• Augmented Reality (AR) and Virtual Reality (VR)
• 3D Printing
• Digital Twins
15. IT Project Management
• Agile, Scrum, and Kanban
• Waterfall Methodology
• Resource Allocation
• Risk Management
16. IT Infrastructure
• Data Centers
• Virtualization (VMware, Hyper-V)
• Disaster Recovery Planning
• Load Balancing
17. IT Education and Certifications
• Vendor Certifications (Microsoft, Cisco, AWS)
• Training and Development Programs
• Online Learning Platforms
18. IT Operations and Monitoring
• Performance Monitoring (APM, Network Monitoring)
• IT Asset Management
• Event and Incident Management
19. Software Testing
• Manual Testing: Human testers evaluate software by executing test cases without using automation tools.
• Automated Testing: Use of testing tools (e.g., Selenium, JUnit) to run automated scripts and check software behavior.
• Functional Testing: Validating that the software performs its intended functions.
• Non-Functional Testing: Assessing non-functional aspects such as performance, usability, and security.
• Unit Testing: Testing individual components or units of code for correctness.
• Integration Testing: Ensuring that different modules or systems work together as expected.
• System Testing: Verifying the complete software system’s behavior against requirements.
• Acceptance Testing: Conducting tests to confirm that the software meets business requirements (including UAT - User Acceptance Testing).
• Regression Testing: Ensuring that new changes or features do not negatively affect existing functionalities.
• Performance Testing: Testing software performance under various conditions (load, stress, scalability).
• Security Testing: Identifying vulnerabilities and assessing the software’s ability to protect data.
• Compatibility Testing: Ensuring the software works on different operating systems, browsers, or devices.
• Continuous Testing: Integrating testing into the development lifecycle to provide quick feedback and minimize bugs.
• Test Automation Frameworks: Tools and structures used to automate testing processes (e.g., TestNG, Appium).
19. VoIP (Voice over IP)
VoIP Protocols & Standards
• SIP (Session Initiation Protocol)
• H.323
• RTP (Real-Time Transport Protocol)
• MGCP (Media Gateway Control Protocol)
VoIP Hardware
• IP Phones (Desk Phones, Mobile Clients)
• VoIP Gateways
• Analog Telephone Adapters (ATAs)
• VoIP Servers
• Network Switches/ Routers for VoIP
VoIP Software
• Softphones (e.g., Zoiper, X-Lite)
• PBX (Private Branch Exchange) Systems
• VoIP Management Software
• Call Center Solutions (e.g., Asterisk, 3CX)
VoIP Network Infrastructure
• Quality of Service (QoS) Configuration
• VPNs (Virtual Private Networks) for VoIP
• VoIP Traffic Shaping & Bandwidth Management
• Firewall and Security Configurations for VoIP
• Network Monitoring & Optimization Tools
VoIP Security
• Encryption (SRTP, TLS)
• Authentication and Authorization
• Firewall & Intrusion Detection Systems
• VoIP Fraud DetectionVoIP Providers
• Hosted VoIP Services (e.g., RingCentral, Vonage)
• SIP Trunking Providers
• PBX Hosting & Managed Services
VoIP Quality and Testing
• Call Quality Monitoring
• Latency, Jitter, and Packet Loss Testing
• VoIP Performance Metrics and Reporting Tools
• User Acceptance Testing (UAT) for VoIP Systems
Integration with Other Systems
• CRM Integration (e.g., Salesforce with VoIP)
• Unified Communications (UC) Solutions
• Contact Center Integration
• Email, Chat, and Video Communication Integration
2 notes
·
View notes
Text
What Are the Costs Associated with Fintech Software Development?

The fintech industry is experiencing exponential growth, driven by advancements in technology and increasing demand for innovative financial solutions. As organizations look to capitalize on this trend, understanding the costs associated with fintech software development becomes crucial. Developing robust and secure applications, especially for fintech payment solutions, requires significant investment in technology, expertise, and compliance measures. This article breaks down the key cost factors involved in fintech software development and how businesses can navigate these expenses effectively.
1. Development Team and Expertise
The development team is one of the most significant cost drivers in fintech software development. Hiring skilled professionals, such as software engineers, UI/UX designers, quality assurance specialists, and project managers, requires a substantial budget. The costs can vary depending on the team’s location, expertise, and experience level. For example:
In-house teams: Employing full-time staff provides better control but comes with recurring costs such as salaries, benefits, and training.
Outsourcing: Hiring external agencies or freelancers can reduce costs, especially if the development team is located in regions with lower labor costs.
2. Technology Stack
The choice of technology stack plays a significant role in the overall development cost. Building secure and scalable fintech payment solutions requires advanced tools, frameworks, and programming languages. Costs include:
Licenses and subscriptions: Some technologies require paid licenses or annual subscriptions.
Infrastructure: Cloud services, databases, and servers are essential for hosting and managing fintech applications.
Integration tools: APIs for payment processing, identity verification, and other functionalities often come with usage fees.
3. Security and Compliance
The fintech industry is heavily regulated, requiring adherence to strict security standards and legal compliance. Implementing these measures adds to the development cost but is essential to avoid potential fines and reputational damage. Key considerations include:
Data encryption: Robust encryption protocols like AES-256 to protect sensitive data.
Compliance certifications: Obtaining certifications such as PCI DSS, GDPR, and ISO/IEC 27001 can be costly but are mandatory for operating in many regions.
Security audits: Regular penetration testing and vulnerability assessments are necessary to ensure application security.
4. Customization and Features
The complexity of the application directly impacts the cost. Basic fintech solutions may have limited functionality, while advanced applications require more extensive development efforts. Common features that add to the cost include:
User authentication: Multi-factor authentication (MFA) and biometric verification.
Real-time processing: Handling high volumes of transactions with minimal latency.
Analytics and reporting: Providing users with detailed financial insights and dashboards.
Blockchain integration: Leveraging blockchain for enhanced security and transparency.
5. User Experience (UX) and Design
A seamless and intuitive user interface is critical for customer retention in the fintech industry. Investing in high-quality UI/UX design ensures that users can navigate the platform effortlessly. Costs in this category include:
Prototyping and wireframing.
Usability testing.
Responsive design for compatibility across devices.
6. Maintenance and Updates
Fintech applications require ongoing maintenance to remain secure and functional. Post-launch costs include:
Bug fixes and updates: Addressing issues and releasing new features.
Server costs: Maintaining and scaling infrastructure to accommodate user growth.
Monitoring tools: Real-time monitoring systems to track performance and security.
7. Marketing and Customer Acquisition
Once the fintech solution is developed, promoting it to the target audience incurs additional costs. Marketing strategies such as digital advertising, influencer partnerships, and content marketing require significant investment. Moreover, onboarding users and providing customer support also contribute to the total cost.
8. Geographic Factors
The cost of fintech software development varies significantly based on geographic factors. Development in North America and Western Europe tends to be more expensive compared to regions like Eastern Europe, South Asia, or Latin America. Businesses must weigh the trade-offs between cost savings and access to high-quality talent.
9. Partnering with Technology Providers
Collaborating with established technology providers can reduce development costs while ensuring top-notch quality. For instance, Xettle Technologies offers comprehensive fintech solutions, including secure APIs and compliance-ready tools, enabling businesses to streamline development processes and minimize risks. Partnering with such providers can save time and resources while enhancing the application's reliability.
Cost Estimates
While costs vary depending on the project's complexity, here are rough estimates:
Basic applications: $50,000 to $100,000.
Moderately complex solutions: $100,000 to $250,000.
Highly advanced platforms: $250,000 and above.
These figures include development, security measures, and initial marketing efforts but may rise with added features or broader scope.
Conclusion
Understanding the costs associated with fintech software development is vital for effective budgeting and project planning. From assembling a skilled team to ensuring compliance and security, each component contributes to the total investment. By leveraging advanced tools and partnering with experienced providers like Xettle Technologies, businesses can optimize costs while delivering high-quality fintech payment solutions. The investment, though significant, lays the foundation for long-term success in the competitive fintech industry.
2 notes
·
View notes
Text

Neuro Review - What Is It?
“Revolutionize Your Workflow with the Power of Neuro!”
In the rapidly evolving world of artificial intelligence, staying ahead is a game-changer. Enter Neuro, the world’s first universal AI app that gives you one-click access to all major AI models—without paying for multiple subscriptions!
Imagine creating an entire business ecosystem in minutes. With Neuro, you can build websites using Claude AI, write content with ChatGPT, craft logos with Leonardo AI, design landing pages using Canva AI, and even promote your services with Microsoft Copilot—all from a single, intuitive dashboard.
Neuro isn’t just a convenience; it’s a transformation tool. This software promises to enhance your results across various AI platforms, making them 19x more effective. Whether you’re looking to automate tasks, create high-quality assets, or launch profitable businesses, Neuro eliminates the complexity.
No subscriptions, no monthly fees, and no API costs—just one lifetime payment for access to endless possibilities. Designed for both beginners and experts, Neuro is here to make AI accessible to everyone while maximizing productivity and profitability.
Features & Benefits
What makes Neuro a must-have tool? Here’s a closer look at its features and benefits:
Universal AI Access Neuro gives you access to popular AI models like ChatGPT, MidJourney, Claude, Google Gemini, Microsoft Copilot, and more—all from one dashboard. No subscriptions or individual platform costs required.
Create Almost Anything Generate websites, funnels, branding materials, logos, motion videos, 4K images, chatbots, software, apps, and more—all in just seconds.
19x Better Results Neuro enhances the performance of every AI model, delivering higher quality and more accurate outputs compared to using the models alone.
Lightning-Fast Performance Build a complete website or automate tasks in as little as 9 seconds.
No Experience Needed Perfect for beginners—no technical skills, experience, or learning curve required.
Zero Ongoing Costs Pay once and enjoy lifetime access with no API fees or recurring payments.
Intuitive Dashboard User-friendly, 100% fail-proof interface for seamless task automation and content generation.
Commercial License Included Generate and sell content, designs, or services without restrictions—and keep 100% of the profits.
Versatile Business Applications Launch businesses from scratch, automate repetitive tasks, and create scalable income streams in minutes.
Risk-Free Purchase Backed by a 30-day money-back guarantee, your investment is fully protected.
How Does Neuro Work?
Using Neuro is as simple as it is powerful. Here’s a step-by-step breakdown of how it works:
Access the Dashboard Once you purchase Neuro, log into its intuitive dashboard where all the AI models are integrated in one place.
Search & Unlock Any AI Model Use the search functionality to find the AI model you need—whether it’s ChatGPT for content, Canva AI for design, or MidJourney for image generation. No separate subscriptions required!
Select Your Task Choose what you want to create: websites, branding, videos, logos, motion graphics, or even chatbots.
Automate & Generate Neuro enhances the AI model’s performance, allowing you to create high-quality outputs faster than ever before. Generate an entire website in just 9 seconds or automate complex tasks with zero experience.
Save & Sell With the included commercial license, you can sell everything you create—keeping 100% of the profit. Build a business or offer services with ease.
Repeat Without Limits Neuro places no limits on the tasks you can perform or the number of AI models you can access. Everything you need is at your fingertips, forever.
Who Is It For?
Neuro is designed to cater to a wide range of users, including:
Entrepreneurs & Business Owners: Build websites, create branding, and automate tasks to scale your business fast.
Content Creators & Designers: Access powerful tools for generating images, videos, and designs without paying for premium subscriptions.
Marketers: Create funnels, landing pages, and promotional content in record time.
Freelancers: Offer high-value services like chatbot creation, website development, and graphic design without investing in expensive software.
Beginners & Non-Tech Savvy Users: With its intuitive interface, anyone can use Neuro without prior experience or technical knowledge.
AI Enthusiasts: Experiment with multiple AI models and unlock their full potential in one place.
Why Choosing It?
Here’s why Neuro stands out in the crowded AI market:
Cost-Effective: Say goodbye to expensive subscriptions for individual AI models. Neuro gives you lifetime access with a single payment.
All-in-One Solution: No need to juggle between different apps or platforms. Neuro consolidates everything into one easy-to-use dashboard.
Enhanced AI Results: Get better outputs and faster performance with Neuro’s unique optimization.
Unlimited Potential: Whether you’re creating, automating, or selling, Neuro removes all restrictions.
Risk-Free: With the 30-day money-back guarantee, trying Neuro comes with no risk to you.
FAQs
What is Neuro? Neuro is a universal AI app that gives you access to all major AI models in one dashboard without subscriptions or API costs.
Which AI models can I access? Neuro integrates with ChatGPT, Claude, MidJourney, Google Gemini, Microsoft Copilot, Canva AI, Jasper, and more.
Do I need technical skills to use Neuro? No, Neuro is designed for users of all skill levels. The dashboard is intuitive and beginner-friendly.
Is there a limit to how much I can use Neuro? No, there are no limits. Neuro allows unlimited use for generating content, automating tasks, and more.
What can I create with Neuro? You can generate websites, logos, videos, apps, chatbots, motion graphics, and much more.
Do I need to pay for API costs or subscriptions? No, Neuro eliminates all API costs and subscription fees. You pay once and access everything.
Does it include a commercial license? Yes, the commercial license allows you to sell anything you create using Neuro and keep 100% of the profits.
What if I’m not satisfied with Neuro? Neuro comes with a 30-day money-back guarantee, so your purchase is completely risk-free.
2 notes
·
View notes
Text
Protect Your Laravel APIs: Common Vulnerabilities and Fixes
API Vulnerabilities in Laravel: What You Need to Know
As web applications evolve, securing APIs becomes a critical aspect of overall cybersecurity. Laravel, being one of the most popular PHP frameworks, provides many features to help developers create robust APIs. However, like any software, APIs in Laravel are susceptible to certain vulnerabilities that can leave your system open to attack.

In this blog post, we’ll explore common API vulnerabilities in Laravel and how you can address them, using practical coding examples. Additionally, we’ll introduce our free Website Security Scanner tool, which can help you assess and protect your web applications.
Common API Vulnerabilities in Laravel
Laravel APIs, like any other API, can suffer from common security vulnerabilities if not properly secured. Some of these vulnerabilities include:
>> SQL Injection SQL injection attacks occur when an attacker is able to manipulate an SQL query to execute arbitrary code. If a Laravel API fails to properly sanitize user inputs, this type of vulnerability can be exploited.
Example Vulnerability:
$user = DB::select("SELECT * FROM users WHERE username = '" . $request->input('username') . "'");
Solution: Laravel’s query builder automatically escapes parameters, preventing SQL injection. Use the query builder or Eloquent ORM like this:
$user = DB::table('users')->where('username', $request->input('username'))->first();
>> Cross-Site Scripting (XSS) XSS attacks happen when an attacker injects malicious scripts into web pages, which can then be executed in the browser of a user who views the page.
Example Vulnerability:
return response()->json(['message' => $request->input('message')]);
Solution: Always sanitize user input and escape any dynamic content. Laravel provides built-in XSS protection by escaping data before rendering it in views:
return response()->json(['message' => e($request->input('message'))]);
>> Improper Authentication and Authorization Without proper authentication, unauthorized users may gain access to sensitive data. Similarly, improper authorization can allow unauthorized users to perform actions they shouldn't be able to.
Example Vulnerability:
Route::post('update-profile', 'UserController@updateProfile');
Solution: Always use Laravel’s built-in authentication middleware to protect sensitive routes:
Route::middleware('auth:api')->post('update-profile', 'UserController@updateProfile');
>> Insecure API Endpoints Exposing too many endpoints or sensitive data can create a security risk. It’s important to limit access to API routes and use proper HTTP methods for each action.
Example Vulnerability:
Route::get('user-details', 'UserController@getUserDetails');
Solution: Restrict sensitive routes to authenticated users and use proper HTTP methods like GET, POST, PUT, and DELETE:
Route::middleware('auth:api')->get('user-details', 'UserController@getUserDetails');
How to Use Our Free Website Security Checker Tool
If you're unsure about the security posture of your Laravel API or any other web application, we offer a free Website Security Checker tool. This tool allows you to perform an automatic security scan on your website to detect vulnerabilities, including API security flaws.
Step 1: Visit our free Website Security Checker at https://free.pentesttesting.com. Step 2: Enter your website URL and click "Start Test". Step 3: Review the comprehensive vulnerability assessment report to identify areas that need attention.
Screenshot of the free tools webpage where you can access security assessment tools.
Example Report: Vulnerability Assessment
Once the scan is completed, you'll receive a detailed report that highlights any vulnerabilities, such as SQL injection risks, XSS vulnerabilities, and issues with authentication. This will help you take immediate action to secure your API endpoints.
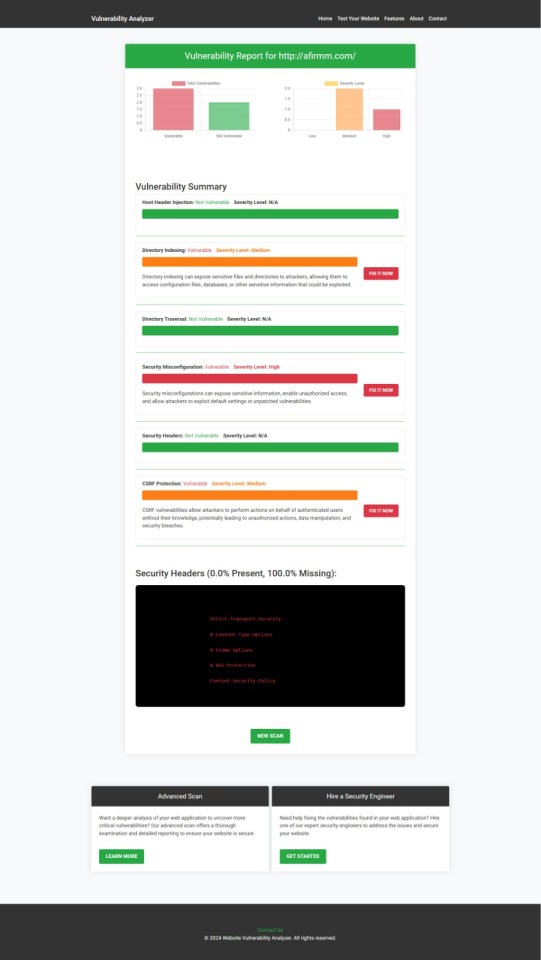
An example of a vulnerability assessment report generated with our free tool provides insights into possible vulnerabilities.
Conclusion: Strengthen Your API Security Today
API vulnerabilities in Laravel are common, but with the right precautions and coding practices, you can protect your web application. Make sure to always sanitize user input, implement strong authentication mechanisms, and use proper route protection. Additionally, take advantage of our tool to check Website vulnerability to ensure your Laravel APIs remain secure.
For more information on securing your Laravel applications try our Website Security Checker.
#cyber security#cybersecurity#data security#pentesting#security#the security breach show#laravel#php#api
2 notes
·
View notes