#Chronicles of Cisco
Explore tagged Tumblr posts
Text
This is your reminder that alter programming/trauma-based mind control is a Satanic Panic conspiracy theory. The stuff you might have heard about gem programming, ribbon programming, Greek letter programming, etc., specifically comes from Fritz Springmeier and Cisco Wheeler, two far right conspiracy theorists who claimed, among many other things, that:
A global satanic conspiracy intends to enthrone the Antichrist in the year 2000. The push toward gay rights is part of this plan.
Said global satanic conspiracy has been practicing trauma-based mind control/alter programming for thousands of years.
The Nazis' eugenics program wasn't actually about eugenics. It was actually a front for researching mind control, and that Project Monarch was based on research conducted by Dr. Josef Mengele (whom they claim was an "adept in Caballistic magic.")
Fairy tales, fantasy media, movies, and television shows are full of deliberate programming. Some (but not all) of the media they implicate includes The Wizard of Oz, The Chronicles of Narnia, Alice in Wonderland, Disney films in general, A Little Princess, Star Trek, Star Wars, E.T., Tiny Toons, The Simpsons, Frankenstein, Bewitched, and Labyrinth.
Basically, anything that doesn't fit the most narrow-minded picture of Good Wholesome Christian Entertainment is is part of the Illuminati's plan to corrupt the youth and lead them down the patch of witchcraft and into satanism.
They claim, and I quote, "drugs, torture, hypnosis and MPD all work to enhance memory" and "most slaves have some photographic memory capability." They also claim that systemwide photographic memory can be created through brain stem scarring.
Babies can learn to read by six months old with the use of subliminal tapes.
Direct quote, "Vice-President Al Gore is a vampire and carries a briefcase of blood with him."
Hillary Clinton is an Illuminati Grand Dame and programmer.
Adrenochrome is a secret black market drug. (Adrenochrome isn't a drug at all.)
Fritz Springmeier and Cisco Wheeler's work is basically a modern mishmash of antisemitic conspiracy tropes and witch panic tropes. Fritz cites fucking Edith Starr Miller as one of his sources.
So why do people "remember" TBMC/RAMCOA? Because they've been coached into it. You can coach people into remembering all kinds of things, as we can very easily see by observing the starseed movement, where people remember past lives in nonexistent places like Lemuria.
If alter programming was a real thing, literature on it would have to exist. I'm talking like, actual manuals that describe in full detail how to conduct all of these rituals and whatnot without killing the victim. The first people who claimed to have experienced this claimed they were programmed back in the 50's, which means it's been seventy years. Not a single manual on this has turned up anywhere; not even in the most depraved child molesters' homes or laptop computers.
RAMCOA is repackaged SRA is repackaged antisemitism and witch panic, end of story.
#alter programming conspiracy theory#project monarch#monarch mind control#conspiracy theorists#conspiracy theorist#conspiracy theories#conspiracy theory#conspiracism#fritz springmeier#sra#satanic ritual abuse#alter programming#did#osdd#did osdd#cisco wheeler#ritual abuse
70 notes
·
View notes
Text


RIP chronicles of Cisco he would have loved the boop button
97 notes
·
View notes
Text

House of Huawei by Eva Dou
A fascinating insight into a Chinese telecoms giant and its detractors
Huawei is not exactly a household name. If you’ve heard of it, you either follow the smartphone market closely – it is the main China-based manufacturer of high-end phones – or else consume a lot of news, because the company is at the centre of an ongoing US-China trade war.
But this enormous business is one of the world’s biggest producers of behind-the-scenes equipment that enables fibre broadband, 4G and 5G phone networks. Its hardware is inside communications systems across the world.
That has prompted alarm from US lawmakers of both parties, who accuse Huawei of acting as an agent for China’s government and using its technology for espionage. The company insists it merely complies with the local laws wherever it operates, just like its US rivals. Nevertheless, its equipment has been ripped out of infrastructure in the UK at the behest of the government, its execs and staffers have been arrested across the world, and it has been pilloried for its involvement in China’s oppression of Uyghur Muslims in Xinjiang.
Into this murky world of allegation and counter-allegation comes the veteran telecoms reporter Eva Dou. Her book chronicles the history of Huawei since its inception, as well as the lives of founder Ren Zhengfei and his family, starting with the dramatic 2019 arrest of his daughter Meng Wanzhou, Huawei’s chief financial officer, at the behest of US authorities.
Dou’s command of her subject is indisputable and her book is meticulous and determinedly even-handed. House of Huawei reveals much, but never speculates or grandstands – leaving that to the politicians of all stripes for whom hyperbole about Huawei comes more easily.
At its core, this book is the history of a large, successful business. That doesn’t mean it’s boring, though: there’s the story of efforts to haul 5G equipment above Everest base camp in order to broadcast the Beijing Olympics torch relay. We hear about the early efforts of Ren and his team, working around the clock in stiflingly hot offices, to make analogue telephone network switches capable of routing up to 10,000 calls; and gain insights into the near-impossible political dance a company must perform in order to operate worldwide without falling foul of the changing desires of China’s ruling Communist party.
Dou makes us better equipped to consider questions including: is this a regular company, or an extension of the Chinese state? How safe should other countries feel about using Huawei equipment? Is China’s exploitation of its technology sector really that different to the way the US authorities exploited Google, Facebook and others, as revealed by Edward Snowden?
Early in Huawei’s history, Ren appeared to give the game away in remarks to the then general secretary of the Communist party. “A country without its own program-controlled switches is like one without an army,” he argued, making the case for why the authorities should support his company’s growth. “Its software must be held in the hands of the Chinese government.”
But for each damning event, there is another that introduces doubt. The book reveals an arrangement from when Huawei operated in the UK that gave GCHQ unprecedented access to its source code and operations centre. US intelligence agencies seemed as able to exploit Huawei equipment for surveillance purposes as China’s. While Huawei’s equipment was certainly used to monitor Uyghur Muslims in Xinjiang, it was hardware from the US company Cisco that made China’s so-called Great Firewall possible.
Anyone hoping for definitive answers will not find them here, but the journey is far from wasted. The intricate reporting of Huawei, in all its ambiguity and complexity, sheds much light on the murky nature of modern geopolitics. The people who shout loudest about Huawei don’t know more than anyone else about it. Eva Dou does.
Daily inspiration. Discover more photos at Just for Books…?
12 notes
·
View notes
Text
For years, it's been an inconvenient truth within the cybersecurity industry that the network security devices sold to protect customers from spies and cybercriminals are, themselves, often the machines those intruders hack to gain access to their targets. Again and again, vulnerabilities in “perimeter�� devices like firewalls and VPN appliances have become footholds for sophisticated hackers trying to break into the very systems those appliances were designed to safeguard.
Now one cybersecurity vendor is revealing how intensely—and for how long—it has battled with one group of hackers that have sought to exploit its products to their own advantage. For more than five years, the UK cybersecurity firm Sophos engaged in a cat-and-mouse game with one loosely connected team of adversaries who targeted its firewalls. The company went so far as to track down and monitor the specific devices on which the hackers were testing their intrusion techniques, surveil the hackers at work, and ultimately trace that focused, years-long exploitation effort to a single network of vulnerability researchers in Chengdu, China.
On Thursday, Sophos chronicled that half-decade-long war with those Chinese hackers in a report that details its escalating tit-for-tat. The company went as far as discreetly installing its own “implants” on the Chinese hackers' Sophos devices to monitor and preempt their attempts at exploiting its firewalls. Sophos researchers even eventually obtained from the hackers' test machines a specimen of “bootkit” malware designed to hide undetectably in the firewalls' low-level code used to boot up the devices, a trick that has never been seen in the wild.
In the process, Sophos analysts identified a series of hacking campaigns that had started with indiscriminate mass exploitation of its products but eventually became more stealthy and targeted, hitting nuclear energy suppliers and regulators, military targets including a military hospital, telecoms, government and intelligence agencies, and the airport of one national capital. While most of the targets—which Sophos declined to identify in greater detail—were in South and Southeast Asia, a smaller number were in Europe, the Middle East, and the United States.
Sophos' report ties those multiple hacking campaigns—with varying levels of confidence—to Chinese state-sponsored hacking groups including those known as APT41, APT31, and Volt Typhoon, the latter of which is a particularly aggressive team that has sought the ability to disrupt critical infrastructure in the US, including power grids. But the common thread throughout those efforts to hack Sophos' devices, the company says, is not one of those previously identified hackers groups but instead a broader network of researchers that appears to have developed hacking techniques and supplied them to the Chinese government. Sophos' analysts tie that exploit development to an academic institute and a contractor, both around Chengdu: Sichuan Silence Information Technology—a firm previously tied by Meta to Chinese state-run disinformation efforts—and the University of Electronic Science and Technology of China.
Sophos says it’s telling that story now not just to share a glimpse of China's pipeline of hacking research and development, but also to break the cybersecurity industry's awkward silence around the larger issue of vulnerabilities in security appliances serving as entry points for hackers. In just the past year, for instance, flaws in security products from other vendors including Ivanti, Fortinet, Cisco, and Palo Alto have all been exploited in mass hacking or targeted intrusion campaigns. “This is becoming a bit of an open secret. People understand this is happening, but unfortunately everyone is zip,” says Sophos chief information security officer Ross McKerchar, miming pulling a zipper across his lips. “We're taking a different approach, trying to be very transparent, to address this head-on and meet our adversary on the battlefield.”
From One Hacked Display to Waves of Mass Intrusion
As Sophos tells it, the company's long-running battle with the Chinese hackers began in 2018 with a breach of Sophos itself. The company discovered a malware infection on a computer running a display screen in the Ahmedabad office of its India-based subsidiary Cyberoam. The malware had gotten Sophos' attention due to its noisy scanning of the network. But when the company's analysts looked more closely, they found that the hackers behind it had already compromised other machines on the Cyberoam network with a more sophisticated rootkit they identified as CloudSnooper. In retrospect, the company believes that initial intrusion was designed to gain intelligence about Sophos products that would enable follow-on attacks on its customers.
Then in the spring of 2020, Sophos began to learn about a broad campaign of indiscriminate infections of tens of thousands of firewalls around the world in an apparent attempt to install a trojan called Asnarök and create what it calls “operational relay boxes” or ORBs—essentially a botnet of compromised machines the hackers could use as launching points for other operations. The campaign was surprisingly well resourced, exploiting multiple zero-day vulnerabilities the hackers appeared to have discovered in Sophos appliances. Only a bug in the malware's cleanup attempts on a small fraction of the affected machines allowed Sophos to analyze the intrusions and begin to study the hackers targeting its products.
As Sophos pushed out patches to its firewalls, its team responsible for threat intelligence and incident response, which it calls X-Ops, also began an effort to track its adversary: Sophos included in its “hotfix" for the hackers' intrusions additional code that would collect more data from customers' devices. That new data collection revealed that a single Sophos device registered in February of 2020 in Chengdu showed signs of early alterations similar to the Asnarök malware. “We started to find tiny little indicators of the attack that predated any other activity,” McKerchar says.
Using registration data and records of downloads of code Sophos made available to its customers, the X-Ops team eventually identified a handful of machines it believed were being used as guinea pig devices for Chinese hackers as they sought to find vulnerabilities and test their intrusion techniques prior to deployment. Some of them seemed to have been obtained by a Chengdu-based company called Sichuan Silence Information Technology. Others were tied to an individual who used the handle TStark, whom X-Ops analysts then found had held a position at the University of Electronic Science and Technology of China, also in Chengdu.
X-Ops analysts could even observe individuals using computers and IP addresses tied to the test devices reading Sophos' online materials that detailed the firewalls' architecture. “We could see them researching us,” McKerchar says.
In late April of 2020, Dutch police worked with Sophos to seize a Netherlands-based server that Sophos had identified as being used in the Asnarök infection wave. In June of that year, however, the hackers launched another round of their mass intrusions, and Sophos found they had significantly reduced the complexity and “noise” of their malware in an attempt to evade detection. Yet through the increased data collection from its devices and the intelligence it had assembled on the Chengdu exploit development group, Sophos was able to spot the malware and push out patches for the vulnerabilities the hackers had used within a week, and even identify a “patient zero” machine where the new malware had first been tested two months earlier.
The next month, X-Ops took its most aggressive step yet in countering the effort to exploit its devices, deploying its own spy implants to the Sophos devices in Chengdu they were testing on—essentially hacking the hackers, albeit only through code added to a few installations of its own products the hackers had obtained. Sophos says that preemptive surveillance allowed the company to obtain key portions of the hackers' code and head off a third wave of their intrusions, catching it after only two customers had been compromised and pushing out a patch designed to block the attacks, while obfuscating that fix to avoid tipping off the hackers to Sophos' full knowledge of their techniques.
“In the first wave, we were on the back foot. In the second wave, it was an even match,” says McKerchar. “The third attack, we preempted.”
A New Phase of the Game
Starting in 2021, Sophos says it began to see far more targeted attacks from Chinese hacker groups exploiting its products, many of which it was able to uncover due to its efforts to surveil the research of the Chengdu-based exploit development network. Over the next two years, the hackers continued hijack vulnerabilities in Sophos appliances in a wide variety of targeted attacks hitting dozens of targets in Asia and the West.
In September of 2022, for instance, Sophos found a campaign exploiting a vulnerability in its products that had breached military and intelligence agencies in a Southeast Asian country, as well as other targets including water utilities and electric generation facilities in the same region. Later, Sophos says, a different Chinese state-sponsored group appears to have exploited a bypass for its patch for that vulnerability to target government agencies outside of Asia, in one instance hacking an embassy shortly before it was set to host officials from China's ruling Communist Party. It also found intrusions at another country's nuclear energy regulatory agency, then a military facility in the same country and the airport of the country's capital city, as well as other hacking incidents that targeted Tibetan exiles.
“We just opened the door on a huge amount of high-end targeted activity, a Pandora's Box of threat intelligence," McKerchar says.
As the hackers' tooling continued to evolve in response to Sophos' attempts to head them off, the company's X-Ops researchers at one point pulled from a test device they were surveilling a unique new specimen of malware: The hackers had built a “bootkit,” an early attempt at malware designed to infect a Sophos firewall's low-level code that's used to boot up the device before its operating system is loaded, which would make the malware far harder to detect—the first time Sophos believes that sort of firewall bootkit has ever been seen.
X-Ops never found that bootkit deployed on an actual victim's machine, but Sophos CISO McKerchar says he can't rule out that it was in fact used somewhere and evaded detection. “We certainly tried to hunt for it, and we have some capability to do that,” says McKerchar. “But I would be brash to say it's never been used in the wild.”
As Sophos has tried to understand the motives of the Chengdu-based network of hackers digging up vulnerabilities and providing them to the Chinese state, that picture has been complicated by the strange fact that the researchers finding those flaws may have on two occasions also reported them to Sophos itself through its “bug bounty” program. On one occasion, for instance, the exact vulnerability used in a hacking campaign was reported to Sophos by a researcher with a Chinese IP address just after it was first used in an exploitation campaign—Sophos paid the researcher $20,000 for their findings.
That bizarre incongruity with the Chengdu-based researchers' apparent role as suppliers of intrusion techniques for Chinese state hacking groups and its bug bounty reports to Sophos, McKerchar argues, show perhaps how loose the connections are between the researchers finding these vulnerabilities and the state hackers exploiting those bugs. “I think this is a security research community which is patriotically aligned with PRC objectives,” he says, referencing the People's Republic of China. “But they're not averse to making a bit of money on the side.”
Contacts at the University of Electronic Science and Technology China didn't respond to WIRED's request for comment on Sophos' report. Sichuan Silence Information Technology couldn't be reached for comment, and appears to have no working website.
Sophos' timeline of its struggle against a highly adaptive adversaries sussing out its products' hackable flaws points to the success of China's efforts to corral its security research community and funnel its discoveries of vulnerabilities to the government, says Dakota Cary, a researcher at the Atlantic Council, a nonpartisan think tank, who has focused on that Chinese exploit development pipeline. He points to China's efforts, for instance, to foster hacking competitions as a source of intrusion techniques for its offensive hacking efforts, as well as 2021 legislation that requires researchers and companies based in China to report to the government any hackable bug they find in a product.
“In Sophos' document, you see the interconnectedness of that system kind of shine through,” says Cary. “The culture of these organizations working together or competing for work, and the way that the government is trying to centralize collection of vulnerabilities and then distribute those tools to offensive teams—you see all of that reflected.”
Sophos' report also warns, however, that in the most recent phase of its long-running conflict with the Chinese hackers, they appear more than ever before to have shifted from finding new vulnerabilities in firewalls to exploiting outdated, years-old installations of its products that are no longer receiving updates. That means, company CEO Joe Levy writes in an accompanying document, that device owners need to get rid of unsupported “end-of-life” devices, and security vendors need to be clear with customers about the end-of-life dates of those machines to avoid letting them become unpatched points of entry onto their network. Sophos says it's seen more than a thousand end-of-life devices targeted in just the past 18 months.
“The only problem now isn't the zero-day vulnerability,” says Levy, using the term “zero-day” to mean a newly discovered hackable flaw in software that has no patch. “The problem is the 365-day vulnerability, or the 1,500-day vulnerability, where you've got devices that are on the internet that have lapsed into a state of neglect.”
That warning was echoed by Cybersecurity and Infrastructure Security Agency assistant director for cybersecurity Jeff Greene, who stresses the risk of Chinese hackers exploiting older, unpatched systems, as well as the broader, ironic threat of network perimeter appliances serving as entry points for hackers. “These edge devices often have inherent insecurities, they’re often not managed once they’re put out, they're not patched," says Greene. “We’ll leave a trail of these devices for a long time that attackers will be looking to compromise.”
Sophos CISO McKerchar says the company is revealing its five-year fight with the Chengdu-based hacking network to amplify those warnings, but also to end a kind of cybersecurity industry omertà around the growing issue of security companies' own products creating vulnerabilities for their customers. “Trust in the industry has been massively eroded in the past few years. There's a huge amount of skepticism across about the way that vendors are handling these risks, but we've relied on silence instead,” says McKerchar. “We want to show a bit of vulnerability ourselves, recognize that we've had problems, then tell the story about how we stepped up.”
8 notes
·
View notes
Text
[RERUN] The Arrowverse (Doing for TV what the MCU did for movies), Part 4: Legends of Tomorrow
[All images are owned by DC Comics and Warner Bros-Discovery. I hope I’m too small-fry to sue…]
While Supergirl debuted a year before the subject of this chapter, it didn’t officially join the Arrowverse until Season 2, the same year as…
youtube
(Thanks to Midnite TV)
Legends of Tomorrow once again brought a few things to the Arrowverse. The first was a rotating/ensemble cast. Where the other three series had an obvious central figure (I mean, their names are the titles of the series!) with a strong supporting cast, Legends was designed such that anyone could join or leave at any time (In fact, only 1 member of the original crew of 9 lasted the entire series. I will only be covering the crew from Season 1 (and one other for reasons that will be explained later) in this review)
The second is humor. While all of the Arrowverse shows can have their light-hearted moments, there are times where Legends skirts just this side of campy, including fighting a giant death god with a cross between Elmo and a giant Furby.
youtube
(Thanks to Swoope)
Legends of Tomorrow chronicles (see what I did there?) the crew of the timeship Waverider.

Initially captained by Rip Hunter (played by Arthur Darvill, who played Rory Williams during Matt Smith’s tenure as the Doctor), a rogue agent of a group known as the Time Masters, as he attempts to change his history by preventing the rise of an immortal tyrant by defeating him in the past.
[JUMPING AHEAD: When Hunter manages to finally succeed (oh, you knew he’d do it eventually!), the Time Masters are disbanded. Therefore, Hunter leaves the Waverider to form the Time Bureau, whose job it is to deal with aberrations in the time stream caused by the Time Masters’ absence]
However, Hunter knows he can’t do this alone, so he goes to early 21st century Star City and Central City to recruit beings to help him. They are (with backgrounds)…
When the Queen’s Gambit was sabotaged, Oliver Queen thought he was the sole survivor. However, in his 5 years of hell, he discovered that Sara Lance survived and was trained by the League of Assassins, returning to Starling City as the Black Canary. However, she was killed and resurrected (not going into how at this time), being reborn as…

…the White Canary. In addition to being a trained assassin and combatant, Sara is (and I apologize if I give this more weight than it likely needs, but it’s a large part of her character) pansexual and has a hell of an appetite. A number of early shows involve scenes of Sara seducing various historical figures.
When Hunter leaves the Waverider, he leaves Sara in charge. Not entirely sure that was a wise choice, but given the other options among the crew…
Anyway…

When the S.T.A.R. Labs particle accelerator accident occurred, Ronnie Raymond and Professor Martin Stein were close together. The Dark Matter fused them into one being. Raymond was eventually able to separate himself from Stein, and with help from Cisco Ramone managed to build a device that would help control their abilities when joined into a being known as Firestorm.

However, Raymond was killed closing a dimensional breach that threatened to destroy the universe.

Eventually, Stein would find a new partner in Jefferson “Jax” Jackson.

While merged, Jax has control of Firestorm while Stein advises via their psychic link. In addition to the obvious flame powers, Firestorm has flight and can transform matter into other matter (such as an unstable meteor into water.
youtube
(Thanks to Spidersonicj)

Industrialist Ray Palmer (played by Brandon Routh, who previously played a certain S-clad hero in Superman Returns) developed an armored exoskeleton known as the Advanced Technology Operating Mechanism (A.T.O.M.) However, the suit developed a glitch, shrinking Palmer to a size smaller than an insect. Thus was born…

The Atom

Carter Hall and Kendra Saunders are old souls dating back to ancient Egypt. They reincarnate through the ages, always eventually finding one another. In this incarnation, they become…

Hawkman and Hawkgirl

Finally, Leonard Snart and Mick Rory were small-time criminals in Central City before they hit the big time by raiding a research facility, stealing guns that could generate extreme cold and heat and adopting the monikers…

Captain Cold and Heatwave
The crew (collectively known as “The Legends”) mostly dealt with beings that were out of their time period (aberrations), but in Season 4, the focus changed to mystical threats, and for that, they needed a specialist

Enter John Constantine, Master of the Occult (a few years removed from his own TV show on NBC. More on him in a future chapter)
The series ran for 7 seasons, and while not as “required viewing” as the others (in fact, Legends “opted out” of most of the Arrowverse crossover events), though members of the Legends usually found their way into the narrative), it was a fun ride with some interesting side-stories with members of the cast (including finding out Rory is an aspiring romance novelist!)
If you would like to watch the series, it’s available on Netflix or behind your favorite paywall. If you would like to see a specific episode reviewed, please let me know!
Speaking of crossover events, that leads us to the next chapter, who didn’t debut in her own series, but in a crossover.
youtube
(Thanks to Legends Universe)
…but that’s a story for another chapter.
#dc comics#arrowverse#legends of tomorrow#rip hunter#white canary#the atom#firestorm#hawkman#hawkgirl#captain cold#heatwave#arthur darvill#caity lotz#brandon routh#time travel#fan colored glasses#i hate reruns
4 notes
·
View notes
Text
2 notes
·
View notes
Text
What's up gamers, it's me: Sam Flynn (real) 😎
I go by he/him pronouns, and I am a part of the Filipino fandom. I'm also 20 years old.
This is my main blog, I post bullshit and mostly fandom things. My current fandoms/interests include:
Xenoblade Chronicles, League of Legends, Brawl Stars, Pokemon, Nimona, Tron, Parappa the Rapper, Mortal Kombat(?), Kingdom Hearts, Total Drama, Red Rising, Hunger Games, Dr. Stone, Delicious in Dungeon, Frieren, Smash Bros, Minecraft, The Good Place, Brooklyn 99, Danganronpa (?) and a bunch of other things i am probably forgetting.
Here are some guys who make music I think sound good:
Daft Punk, Arctic Monkeys, The Strokes, Franz Ferdinand, Judas Priest, Modjo, San Cisco, The Drums, Zack Tabudlo, Queen, Elvis, John Coltrane, STAYC
I have an art & writing blog! @creativesamflynn :) I post my OCs, writings, and art over there.
I also have another blog for dumping random videos and images. It's @iconicsamflynn
I'm just here for the vibes and vibes alone 😎
If you wanna be moots, I'm totally down for it. Just lemme know or something, idk :P
This post will probably get repeatedly edited every time I remember something about me I forgot to put on here.
so uh yeah, i might delete this/unpin it later. idk, just straighten your back and drink water or something
4 notes
·
View notes
Text
Lauriver Chronicles
by Lauriverfanboy1 After 5 years in hell, Oliver Queen is finally returning home to his family, his friends, and the woman he loves, but he's no longer the man he used to be. Now that he's home, he has one mission, to save his city. As he learns to navigate his new double life, he also finds that he won't be as alone as he thought he'd be. Part Two of New World Chronicles. Words: 6720, Chapters: 6/?, Language: English Series: Part 2 of New World Chronicles Fandoms: Arrow (TV 2012), Batman - Fandom, Titans - Fandom, DC's Legends of Tomorrow (TV) Rating: Not Rated Warnings: Creator Chose Not To Use Archive Warnings Categories: F/F, F/M Characters: Oliver Queen, John Diggle, Laurel Lance, Thea Queen, Helena Wayne, Winn Schott, Lyla Michaels, Bruce Wayne, Malcolm Merlyn, Selina Kyle, Dick Grayson, Sara Lance, Ava Sharpe, Tommy Merlyn, Slade Wilson, Moira Queen, Robert Queen, Quentin Lance, Dinah Lance, Roy Harper, Donna Troy, Barry Allen, Iris West, Cisco Ramon, Kara Danvers Relationships: Oliver Queen/Laurel Lance, John Diggle/Lyla Michaels, Thea Queen/Helena Wayne, Oliver Queen & Bruce Wayne, Barry Allen & Oliver Queen, Sara Lance/Ava Sharpe, Roy Harper/Donna Troy Additional Tags: repost via https://ift.tt/sMxZbRE
0 notes
Note
📖 + The Flash?
So far I have:
The Malcolm Thawne amnesia fic - an AU where Malcolm ends up being the one dying at the end of S1, but after being yanked through the singularity to Earth-3 his dormant meta powers activate and heal him but both the physical and mental trauma have done a number on his memory and he remembers nothing about who he is. Jay Garrick takes him under his wing and he slowly starts to remember fragments (namely that he had a brother), but there's a question mark over whether he'll ever regain all his memories or not.
A Ramon brothers fic set just after S1 - Dante, already worried about Cisco after the events of the S1 finale, becomes even more worried when Cisco becomes increasingly stressed over something (they talk and this is how he finds out Eowells murdered his brother in an alternate timeline)
The Theodore Thawne chronicles AKA why I might end up watching at S5 as well as S4, as S5 plays a big role. Theodore, having fled to Canada with his family after his powers manifested, finds out that his old childhood friend, Nora, has been visiting Eobard, realises this means nothing good, and also runs back to 2018/19 to try and get through to her - this series will be at least a few fics long with Theodore experiencing several timeline changes (notably going from Raised In A Bad Future to Raised In A Good Future) and will end up meeting his long-dead uncle Eddie in the last fic (though the last fic will mostly be from Eddie and Malcolm's POV)
Originally-a-flufftober-fic-before-I-changed-my-mind - a fairytale retelling of The Flash (with added Westhallen)
Eddie and Ronnie survive the events of S1 but no one realises that for months because they get yanked through to Earth-3 by the Singularity - Eddie takes some time to recover and Ronnie frets over him the whole time because he feels guilty over what happened, feeling that if he'd only gotten down there quicker Eddie wouldn't have had to shoot himself (and feeling even more guilty when it becomes clear that it was actually the combination of Eddie's depression and Eobard's words during the two week captivity). They eventually become good friends.
Send me 📖 + a fandom, and I’ll tell you a muse (or several muses) from this fandom I’ve thought about writing
0 notes
Photo

Okay Fangirls and Fanboys, I have decided, after much deliberation (but really because Kamilla keeps begging me to “get with the times”) that it is time for this blog… to be REBORN. Like a caterpillar becomes a beautiful butterfly… or like Taylor Swift whenever she releases a new album. You get it.
Basically, it’s time to take the Chronicles of Cisco to the next level. And that level is…
INSTAGRAM.
I’m told that Instagram is the schway place to be in 2019 for an influencer such as myself. And yeah, I realize I’m nine years late to the party, but so what? At least I showed up. Besides, work keeps me pretty busy during the week in case you hadn’t noticed.
Anyway, I’d like to thank you, my loyal readers, for following along with these here Chronicles. Your support has meant the world to me and I hope you’ll continue to stay in touch on the new platform. Change, as they say, is the spice of life, so follow @cwtheflash for more “hot” takes from me, Cisco – aka, your favorite member of Team Flash.
246 notes
·
View notes
Photo




The Flash Season 5 Finale “Goodbye Vibe”
#the flash#the flash season 5#the flash cw#the cw the flash#flash#cisco ramon#carlos valdes#chronicles of cisco
9 notes
·
View notes
Photo










top 15 dctv female antagonists (as voted by my followers): 5. shawna baez / peek-a-boo → “I’m thinking lasers. I love a good light show.”
#theflashedit#dctvedit#shawnabaezedit#shawna baez#flash#dctv#flash 1x12#flash 1x22#flash 4x01#chronicles of cisco#topfemvills#meggifs#*#**#gun /#remember when she just wanted to be free#250
439 notes
·
View notes
Video
tumblr
questions i ask myself everyday:
why was this scene between cisco and barry deleted??
(scene from 1x23)
#the flash#barry allen#cisco ramon#grant gustin#carlos valdes#deleted scene#the cw#vibe#reverb#caitlin snow#dr wells#harrison wells#star labs#flashvibe#kid flash#killer frost#barry/cisco#bartholomew allen#francisco ramon#chronicles of cisco#metahuman#particle accelerator#barrisco
1K notes
·
View notes
Text
anyway so if any of you follow/read Chronicles of Cisco (@chroniclesofcisco), they just posted even more foreshadowing for HR being the one to have died or somehow swapped places with Iris (or something).
7 notes
·
View notes
Text
Lauriver Chronicles
read it on AO3 at https://ift.tt/sMxZbRE by Lauriverfanboy1 After 5 years in hell, Oliver Queen is finally returning home to his family, his friends, and the woman he loves, but he's no longer the man he used to be. Now that he's home, he has one mission, to save his city. As he learns to navigate his new double life, he also finds that he won't be as alone as he thought he'd be. Part Two of New World Chronicles. Words: 6720, Chapters: 6/?, Language: English Series: Part 2 of New World Chronicles Fandoms: Arrow (TV 2012), Batman - Fandom, Titans - Fandom, DC's Legends of Tomorrow (TV) Rating: Not Rated Warnings: Creator Chose Not To Use Archive Warnings Categories: F/F, F/M Characters: Oliver Queen, John Diggle, Laurel Lance, Thea Queen, Helena Wayne, Winn Schott, Lyla Michaels, Bruce Wayne, Malcolm Merlyn, Selina Kyle, Dick Grayson, Sara Lance, Ava Sharpe, Tommy Merlyn, Slade Wilson, Moira Queen, Robert Queen, Quentin Lance, Dinah Lance, Roy Harper, Donna Troy, Barry Allen, Iris West, Cisco Ramon, Kara Danvers Relationships: Oliver Queen/Laurel Lance, John Diggle/Lyla Michaels, Thea Queen/Helena Wayne, Oliver Queen & Bruce Wayne, Barry Allen & Oliver Queen, Sara Lance/Ava Sharpe, Roy Harper/Donna Troy Additional Tags: repost read it on AO3 at https://ift.tt/sMxZbRE
1 note
·
View note
Text

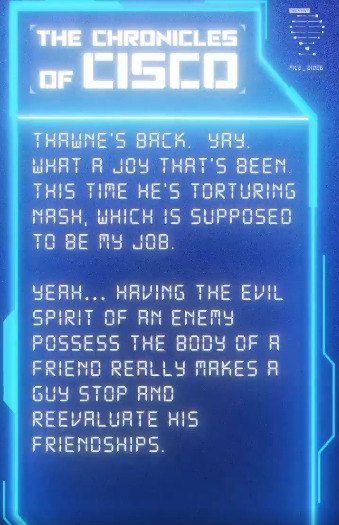

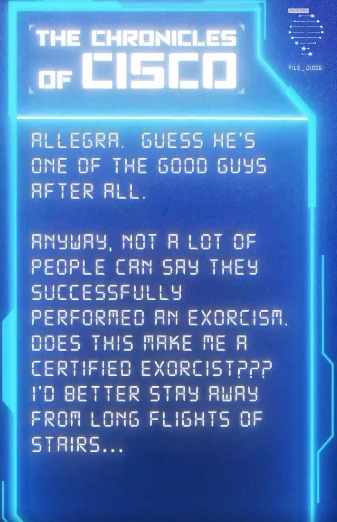
"Thawne's back... This time he's torturing Nash, which is supposed to be my job..."
Cisco's thoughts on Nash (@CavanaghTom) in the Chronicles of Cisco, via @CW_TheFlash IG story
I feel like Tom and Carlos worked on this together when writing it.
#the Chronicles of cisco#the flash cw#cw the flash#nash wells#eobard thawne#cisco ramon#the flash season 6#oof#poor baby
46 notes
·
View notes