#What is Performance Management Software
Explore tagged Tumblr posts
Text
Benefits of Performance Management Software in Australia
Learn how Australian companies are using performance management software to streamline evaluations, improve feedback, and support employee development.
#Benefits of Performance Management Software in Australia#What is Performance Management Software#Performance management system#Performance management software#Performance Management Software in Australia
0 notes
Text
Diploma in Taxation
#Title : What is computer accounting course#1. Introduction to Computer Accounting Course#What is Computer Accounting?#In today’s fast-paced world#businesses rely heavily on technology for their financial operations. A computer accounting course teaches individuals how to use computer#prepare reports#and ensure compliance with financial regulations. The shift from traditional manual accounting to computerized accounting has revolutionize#bookkeepers#and financial analysts.#The Importance of Computer Accounting in Modern Business#Computerized accounting has simplified tasks that once took hours or even days to complete. Instead of using paper ledgers and manual entri#businesses can now perform tasks like invoicing#payroll management#financial reporting#and budgeting with the help of accounting software. This digital transformation ensures more accuracy#efficiency#and speed in business operations.#2. Key Features of Computer Accounting Courses#Course Structure and Duration#A computer accounting course typically covers a wide range of topics#from basic accounting principles to advanced financial software applications. The course duration can vary based on the level of depth and#while diploma and degree programs may take months or even years to complete.#Basic Level: Introduction to Accounting Software#Intermediate Level: Managing Accounts#Transactions#and Reports#Advanced Level: Auditing#Taxation#and Financial Planning#Software Covered in the Course
1 note
·
View note
Text
#contingentworkforce#vendor management solutions#vendor management software#talentacquisition#vendor performance#what is a vms#vendor management tools#vendormanagement#directsourcing#vms software#vms provider#vms management#vms onboarding
0 notes
Text
The winter rebound



✦ Pairing: Bucky Barnes/Fem!Reader
✦ Word count: ~3,6k
✦ Rating: Explicit
✦ Warnings/tags: Avengers!Bucky, alcohol consumption, fluff, pwp, smut, oral (fem receiving), piv sex, safe sex, dirty talk.
✦ Summary: You go with your friend to Stark's holiday party
✦ Note: This was the first thing I wrote and published when I got back into the marvel fandom, so it's a super self-indulgent piece! But I hope you like it anyway! As always, please comment and/or reblog! Asks are always welcome!
Masterlist | AO3
It was Friday. You watched yourself in the mirror and told yourself that you would have fun tonight. Forget about your ex of five years who broke off your engagement a month before the holidays, whom you had spent the last three weeks crying over.
Tonight you were accompanying your best friend to the annual Stark holiday party, and you would not think about him once during the night, while you danced and drank yourself into a stupor.
Standing outside the huge compound made you anxious. Maybe it was too soon to meet the real world without him. No! Don’t think about that asshole! You cut yourself off before your thoughts started to spiral.
“Come on!” your friend Lily laughed. Her genuine smile was contagious and you returned it, squaring your shoulders and forcing every dumb thought down before you took her arm as the two of you made your way down the gold and red carpet. At the end, two large glass doors were opened by life-sized mechanical nutcrackers.
“I sure hope those don’t spring to life and ruin this party too,” you mumbled. Lily giggled, “Don’t worry, I helped with the software, unless Mr. Stark went a completely different direction there should be no worries.” “So there is a possibility,” you joked as the doors closed behind you.
If she answered you didn’t hear because you were too busy taking in the amazing winter-themed party. The waiters were also dressed as nutcrackers and there were dancers in amazing outfits performing all over the floor. Music played in the background and some were moving to the beat while others stood around and talked.
Honestly, you had expected more people, like at least two hundred but there were only about fifty in the huge hall. Not only the regular people, like your friend, who helped with software, hardware, management, and the day-to-day running's of the compound, but it was impossible not to notice the heroes also in attendance.
Not all of them were there, no sign of Thor or Loki, or the Guardians, but this was your first time so close to any hero ever, you would take what you could get.
“Come, I’ll introduce you to everyone,” Lily said and started to pull you along while you gazed at the shifting decorations adorning the walls, obvious to the blue eyes that followed you with interest from the bar.
Too many names spun through your brain, accompanied by the alcohol your friend had been plying you with.
Everyone you had met so far had been incredibly nice and friendly and hadn’t minded when you asked all the dumb questions about working at such a place.
Finally, it came down to the big event, meeting Mr. Stark and maybe the rest of the Avengers currently there.
Lily stepped up to her boss and greeted him and Pepper Potts like they were friends rather than her superiors and then introduced you. Not a lot of people got to shake hands with Iron Man and Pepper Potts but now you had, and it was totally normal.
“Interesting hair color,” Tony Stark pointed out. “Is it meant to look like that?” It was such an old man thing to say you could only laugh as Pepper elbowed him in the ribs. “I am sorry,” Pepper apologized but you waved it off.
“He is paying for everything I drink, so if he wants to make fun of my hair, it’s fine.” Pepper gave you a relieved look and was about to say something else when a voice interrupted.
“It looks like the Aurora Borealis.”
Bucky Barnes had appeared out of nowhere, like the skilled assassin he had been trained to be. It was like he had materialized out of thin air at your side and you jumped when he spoke.
Before you knew what you were doing, you reached out, slapping your palm against his hard chest, and said “For fuck’s sake,” while your other hand rested over the heart trying to work its way out of your chest.
Then you realized what you’d done and pulled back your hand quickly, covering your mouth. Bucky stared back at you, mouth slightly open, while Lily and Tony both cackled in amusement. “That’s what you get Barnes,” your friend pointed out.
With a crooked smile, Bucky just said, “How about I buy you a drink to make up for it?” and held out his arm. “As long as it’s crazy expensive since the old man made fun of my hair,” you shot over your shoulder at Tony as you took the offered arm.
Your friend winked at you before she returned to her conversation with Natasha Romanoff, whom you would just have to say hello to some other time.
Bucky led you the short way to the bar and you eased your way on to the chair, making sure not to get tangled in your long dress, as Bucky leaned over the bar and asked for the most expensive champagne they had.
“I’m Bucky,” he said. “I know,” you smiled at him before introducing yourself too.
In no time there were two flutes in front of you, he offered you one, saying cheers before you took the first sip. The unabashed moan that left you wasn’t meant to be sexual but Bucky stopped his glass halfway to his lips to just stare at you. It cracked you up, “Sorry,” you said, “I’ve never tasted champagne this good before.” He also took a sip, his eyes widening a little, and when he’d swallowed all he said was, “Wow.” “I could get used to this,” you took another mouth and closed your eyes.
When you opened them again you found him looking at you and it made a shiver go down your spine. For the first time in a long time, you felt desire pool in your lower belly. “Will this make up for Stark’s comment?” he asked. “It will absolutely!” you promised. “I think your hair looks great and I’m like twice his age so…” he trailed off.
“My friend, Lily, has told me about these crazy old super soldiers, but you look spry for your age,” you winked at him. “You can only imagine,” he flirted back, and your cheeks heated. You had forgotten about this, about the utter intoxication of flirting with a man and having it returned to you.
After several weeks of drought, your body suddenly knew what arousal was again and flooded you with it, making your heart beat twice as fast and your skin flush. “Oh, you want me to think of everything you can do?” you asked with a raised eyebrow. “Anything you want, doll,” he leaned forward, “But I’m sure your imagination won’t hold a candle to the real thing.” “Are you going to show me?” “If you want to,” he smirked and you felt yourself grow wetter by the second.
You leaned in too, unable to resist him and not wanting to either. You wanted to get lost in him for as long as he would have you. He finished off the rest of his champagne like it was a shot of liquor.
“Come on, I have just the place,” he smiled, holding out his hand. Not even second-guessing yourself for a moment you finished your glass and let him lead you away.
Bucky took you through a side door, into a corridor that led to the heart of the compound which was now deserted, and finally into a large room with a domed ceiling.
It looked like a cinema almost, except the screen was the whole ceiling, and in the middle of the floor was an enormous sofa-like thing that easily fit several people.
After Bucky pressed something on a side panel the room lit up with the Aurora Borealis.
You let go of his hand, staring with huge eyes at the display. Maybe you had misinterpreted his intentions and they were actually pure, not at all the filthy things you had thought this would end up being.
Never had you been happier to be wrong.
This time when he appeared out of nowhere he didn’t scare you, he gripped your waist with the vibranium arm and spun you into his chest, before using his other hand to pinch your chin between his fingers.
“I’m going to kiss you, tell me if I should stop,” he breathed. Instead of answering with words you surged up and crushed your lips against his, wrapping your arms around his neck, and pulling him impossibly closer.
It was almost like he expected you to be timid or something because, for a few seconds, he didn’t move, but then he rushed into action, moving his lips and kissing you like a man starved.
Desire flooded you, making every one of his touches feel like fire even through the fabric of your dress. He moved you backward until your knees hit the oversized sofa, and you laid down.
Bucky’s face was burning with desire as he looked down on you, before he could move or say anything you grabbed your skirt and pulled it up until it bunched around your waist so that you were able to spread your legs without restraint.
The growl erupting from his chest made you smile and you crooked your finger toward him. He knelt between your legs, grabbing your thighs to spread them even more before he leaned down over you to capture your lips again.
The action made the hard cock in his jeans brush against your heated core, making you moan into his mouth.
He pulled back, eyes wild, “Your sounds make me fucking crazy.” he groaned, moving his hands down your naked legs, caressing them and gripping them, like he couldn’t decide if he wanted to be rough or gentle.
“Hope so,” you smiled and started to tug at his suit jacket, needing to see his body. He obliged by sitting back and ridding his upper body of clothing. As soon as you could your hands splayed out across the expanse of his naked torso, feeling the hard muscles under the soft skin.
Your eyes grazed over the scars on his left shoulder but didn’t pay it any mind. The man had trauma, that was no secret, but tonight you didn’t need to delve into that. Instead, you sat up, kissing the skin you could reach and licking at his nipple, making him moan most deliciously.
He reached around you to unzip your dress and you whined when you had to move away from him to let him pull it off you. Now you were almost completely naked with the super soldier, except for the thong you wore that did little to hide anything from him, and your heels.
Without another word, he stood up and unbuttoned his pants, peeling them off and kicking off his shoes in the process, before he was back over you. Now it was his turn to taste your skin and when he closed his mouth around a nipple, using his vibranium hand to pinch the other, you released a high-pitched mewl you never heard from yourself before.
That only spurred him on, alternating between sucking and licking at you, squeezing or pinching your sensitive buds. The pleasure was too much, like you would implode or maybe even come from just him playing with your tits. You fisted the fabric under you, pushing your chest even more into him as moans and words tumbled from your lips.
“Bucky, please!” you tried forming a coherent sentence but failed. “What do you need, doll?” he asked, lips shiny with his spit as he looked up at you. “Touch me, make me come, please Bucky,” you didn’t want to wait another second for the pleasure you had missed for a lot longer than the weeks since your break up. This temporary connection with a stranger was already better than what you had experienced over several years.
“Can I taste you?” his voice was husky, filled with restrained want. “Yes!” you smiled and raised yourself on your elbows.
You watched as he kissed his way down your form, pulling off your thong and throwing it away. He grabbed your thighs and spread them wide before letting the thumb of his vibranium hand slowly drag up, separating your folds, groaning, almost whispering “Fuck, your pussy is perfect,” and leaning in to carefully lick up your spread lips. You fell back, staring up at the beautiful display as Bucky Barnes, the Winter Soldier, one of the Avengers, ate you out with perfection.
Every move he made sent sparks through your entire body and pulled cries from you. Your hands tangled in his hair, not pulling or pushing, just needing to anchor yourself on something. Nothing would hold a candle to this for the rest of your life you suspected, because even though you had just met, Bucky Barnes took his sweet time, caressing his hands up and down your sides, down your legs, and back up again, using his tongue and lips to make your body blaze.
Your crescendo built steadily, as did your voice, the closer you got the more you pleaded and begged, even though he was doing exactly what you wanted him to. When two fingers on his right hand breached you with no problem your back bowed, the pleasure rushing through you, and when he crooked them and moved them inside you, it was everything the dam needed to break and the coil inside you snapped.
You screamed his name as the orgasm hit you like a freight train. What was even better was that he worked you through it, coaxing every last drop of pleasure out of you before you had to instead beg him to stop.
"Too much," you whimpered when the uttermost tip of his tongue gently floated across your clit. "No, darling, not enough. A man could get addicted to hearing you scream his name."
You whimpered again, your body rocking with overstimulation at every pass of his tongue. It was wonderful to hear him say those things but you needed more.
"Please tell me you have a condom so you can fuck me," you groaned and that made him stop, staring at you from between your legs before kissing up the side of your thigh to sit back on his heels before he got up. He freed himself from his underwear before he bent down to grab his pants and pulled a condom from a pocket and that gave you a chance to admire him. His cock was hard, glistening, and a lot bigger than what you were previously used to, but that only sparked more excitement in your lower stomach.
"Hands and knees, baby," he smiled and made a twirling motion with his fingers. You wasted no time rolling over, and getting into position. His flesh hand slapped your ass playfully when he knelt behind you and when you moaned he chuckled. "You like that huh?" he asked as the tip of his cock started to press into you.
He was big, you whined and whimpered with every inch he pressed into you. Maybe why he took his time eating you, because he needed you to be as aroused as possible for it to fit. You clawed at the fabric, feeling like you were having an out-of-body experience with how he filled you.
"So good, taking it all," he praised when his hips were finally flush with your ass. Trying to answer him with words was out of the question, instead, you rocked your body, feeling his cock press against everything inside you, giving you the most delicious sensation you probably ever felt.
His hand landed on your ass again and that spurred you on, starting to move a bit faster. "Look at you, fucking yourself on my cock," he sounded a little breathless and you wished you could see him. "Do you like it, darling? Do you like my cock filling you to the brim?"
Fuck, Bucky Barnes had a mouth on him you had not expected. He grabbed your hips and helped you along, starting to fuck you deep and hard, pulling almost all the way out before shoving back in again.
With every move, you cried out in sheer ecstasy. Bucky kept on telling you how good you sounded, he didn't mind at all that you were loud.
The pace was hard but not hurried, he seemed to like taking his time, not rushing through the action just to get to the finish line. But it was driving you mad, it felt like you were at the precipice constantly, ready to tip over but needing something more to do it.
Then he grabbed you around the waist and pulled you up until you were flush against his chest, his pace never stopping. "Hi, sweet thing, enjoying yourself?" he wasn't even winded and you were a panting, whimpering mess, feeling like you were about to lose it.
"Yes, Bucky, please touch me, make me come again." He kissed your shoulder, "My pleasure," was his answer and his left hand descended on your aching clit.
A shudder and a scream passed through you when he started to rub small circles over it. Suddenly you were so close to the edge you could almost taste it, and Bucky knew it too.
"That's right, come on my cock, doll. Can you do that for me? Be good and come for me?" he said between kissing up your neck, moving the arm around your waist up to grab your jaw, and turning your head to the side. The kiss was sloppy but delicious, and with the aid of his fingers and so full of his cock the orgasm took you by full force, making you shake in his grip.
He released your mouth and let the sounds you made fill up the room, pressing his mouth to the side of your head and telling you over and over again how fucking good you felt coming around him.
If he hadn’t held you up, you would have collapsed no doubt, but Bucky had no problem keeping you up as he found his own release, pressing his forehead against your neck and mumbling obscenities, his hips stuttering against your ass.
Now he was breathing heavier, holding you tight against him with both arms, letting his fingers draw random patterns on your skin.
You were in a post-orgasmic haze, only existing in that moment with no past or future, only his warm body, and a sated need. "Gonna need to let you go now, darling," he said in a low voice "Lay down." His arms loosened around you and you braced yourself with your arms and eased yourself down on your side.
Bucky got up, probably to dispose of the condom, before laying down behind you. You hadn't expected him to want to cuddle, but he draped his arm across your side, pulling you flush against him.
"You okay?" he asked in a whisper. "Fan-fucking-tastic," you answered with a small laugh and felt a million times lighter all of a sudden.
After a few minutes of laying there, you felt like you'd been gone from the party long enough, but judging by Bucky’s heavy breathing, he had fallen asleep behind you.
He didn't wake as you gathered your things. When you found the thong, you looked at it, looked over at his gorgeous form laying there, and giggled as you found his pants and stuffed the thong down his pocket.
With the help of some items in your clutch, you patched up your make-up and fixed your hair before slipping out and closing the door behind you.
It was a small miracle that you could find your way back to the party but you did and immediately went to the bar for a drink.
Lily found you minutes later and she just raised an eyebrow, you shrugged and tilted your glass towards hers, clinking them together, and then you both burst out laughing.
*
Monday rolled around and it was hard to work because you kept getting lost in the memories of Friday night.
His eyes, his scent, his voice as he said those things to you. You squeezed your legs together and stifled a low moan.
Suddenly your phone chimed and pulled you back into the real world. A text from Lily.
[So, Bucky Barnes just came by and asked for your number. I gave it, of course, just so you know!] [Okay? Did he say why he needed it?] [Apparently, you left something(????) here on Friday and he wanted to return it.] [Hmm, okay, thanks!] [What did you leave?!?!?!?] [Don't be so nosey, go back to work!]
Your stomach did a flip when the next message was from an unknown number. It had a picture attached, your thong tangled in his fingers, and the text [You left these.] For a second you imagined him using them as he got himself off. You bit your lips as you responded. [Keep them or throw them away, I have more, don't worry.] even added a little wink-emoji.
[I want to return them, personally. Are you free this afternoon?] His response was quick and very to the point.
A wonderful shudder traveled through you at the thought of seeing him again. You had meant for this to be a one-time thing, something to get you back into the world and learn to exist without your ex but there wasn't any harm in seeing where this could go, and hopefully, you would have a lot more amazing sex on top of it.
[Sure, I get off at five.]
#bucky barnes#bucky barnes x reader#bucky barnes x you#bucky barnes x female reader#bucky barnes imagine#bucky barnes fanfiction#bucky barnes fic#bucky barnes smut#bucky x reader#bucky x you#bucky x female reader#bucky imagine#bucky fanfic#bucky fic#bucky smut#veltana writes
724 notes
·
View notes
Text
☁︎。⋆。 ゚☾ ゚。⋆ how to resume ⋆。゚☾。⋆。 ゚☁︎ ゚
after 10 years & 6 jobs in corporate america, i would like to share how to game the system. we all want the biggest payoff for the least amount of work, right?
know thine enemy: beating the robots
i see a lot of misinformation about how AI is used to scrape resumes. i can't speak for every company but most corporations use what is called applicant tracking software (ATS).
no respectable company is using chatgpt to sort applications. i don't know how you'd even write the prompt to get a consumer-facing product to do this. i guarantee that target, walmart, bank of america, whatever, they are all using B2B SaaS enterprise solutions. there is not one hiring manager plinking away at at a large language model.
ATS scans your resume in comparison to the job posting, parses which resumes contain key words, and presents the recruiter and/or hiring manager with resumes with a high "score." the goal of writing your resume is to get your "score" as high as possible.
but tumblr user lightyaoigami, how do i beat the robots?
great question, y/n. you will want to seek out an ATS resume checker. i have personally found success with jobscan, which is not free, but works extremely well. there is a free trial period, and other ATS scanners are in fact free. some of these tools are so sophisticated that they can actually help build your resume from scratch with your input. i wrote my own resume and used jobscan to compare it to the applications i was finishing.
do not use chatgpt to write your resume or cover letter. it is painfully obvious. here is a tutorial on how to use jobscan. for the zillionth time i do not work for jobscan nor am i a #jobscanpartner i am just a person who used this tool to land a job at a challenging time.
the resume checkers will tell you what words and/or phrases you need to shoehorn into your bullet points - i.e., if you are applying for a job that requires you to be a strong collaborator, the resume checker might suggest you include the phrase "cross-functional teams." you can easily re-word your bullets to include this with a little noodling.
don't i need a cover letter?
it depends on the job. after you have about 5 years of experience, i would say that they are largely unnecessary. while i was laid off, i applied to about 100 jobs in a three-month period (#blessed to have been hired quickly). i did not submit a cover letter for any of them, and i had a solid rate of phone screens/interviews after submission despite not having a cover letter. if you are absolutely required to write one, do not have chatgpt do it for you. use a guide from a human being who knows what they are talking about, like ask a manager or betterup.
but i don't even know where to start!
i know it's hard, but you have to have a bit of entrepreneurial spirit here. google duckduckgo is your friend. don't pull any bean soup what-about-me-isms. if you truly don't know where to start, look for an ATS-optimized resume template.
a word about neurodivergence and job applications
i, like many of you, am autistic. i am intimately familiar with how painful it is to expend limited energy on this demoralizing task only to have your "reward" be an equally, if not more so, demoralizing work experience. i don't have a lot of advice for this beyond craft your worksona like you're making a d&d character (or a fursona or a sim or an OC or whatever made up blorbo generator you personally enjoy).
and, remember, while a lot of office work is really uncomfortable and involves stuff like "talking in meetings" and "answering the phone," these things are not an inherent risk. discomfort is not tantamount to danger, and we all have to do uncomfortable things in order to thrive. there are a lot of ways to do this and there is no one-size-fits-all answer. not everyone can mask for extended periods, so be your own judge of what you can or can't do.
i like to think of work as a drag show where i perform this other personality in exchange for money. it is much easier to do this than to fight tooth and nail to be unmasked at work, which can be a risk to your livelihood and peace of mind. i don't think it's a good thing that we have to mask at work, but it's an important survival skill.
⋆。゚☁︎。⋆。 ゚☾ ゚。⋆ good luck ⋆。゚☾。⋆。 ゚☁︎ ゚。⋆
640 notes
·
View notes
Text

He should be arrested for violating our privacy. He was not vetted by congress and has no security clearance.
Contact your state’s attorney general and request help.
Can we ask the ACLU to file a class action suit? Who’s with me?
“Let’s get into the details. Musk’s staffers have been caught plugging external hard drives into federal agency systems and reportedly locking others out of private rooms to perform—who knows what actions. This behavior violates key cybersecurity laws under FISMA and NIST guidelines, which are designed to protect sensitive federal information. Here’s why this is a serious problem.
Federal systems are strictly regulated, allowing only approved devices to connect. Unauthorized external drives can introduce viruses, ransomware, or other harmful software that may compromise entire networks and disrupt essential operations. This puts system stability and continuity of services at risk, endangering critical infrastructure.
These devices could also be used to steal or damage critical information, including personal data for millions of Americans—such as Social Security recipients and taxpayers. Unauthorized access creates significant vulnerabilities, exposing sensitive data to the risk of cyberattacks. Such attacks could cripple vital services and compromise the privacy and safety of millions of people.
Additionally, federal agencies have strict access controls to prevent unauthorized data manipulation or theft. When unauthorized devices are connected, these protections are bypassed, allowing unauthorized users to potentially alter or extract sensitive data. This undermines system integrity and opens the door to both internal and external threats.
External drives also often lack essential security features, such as encryption and antivirus scanning, making them vulnerable to cybercriminal exploitation. These security gaps further increase the risk of data breaches and system compromise, which can have far-reaching consequences.
Federal systems handle trillions of dollars in payments and manage personal data for millions of U.S. citizens. By bypassing cybersecurity laws and protocols, Musk’s staffers are putting these systems—and the public—at serious risk. This activity is illegal, reckless, and unacceptable. Immediate oversight and intervention are necessary to stop these violations!” ~ A N P S
225 notes
·
View notes
Text
Have YOU got an old Windows PC Microsoft has told you can't run Windows 11? It's time to give it a new life!
How to install Windows 11 on unsupported PC Hardware using Rufus. You can also disable some other Windows 11 bullshit like data harvesting and needing a Microsoft account.
It has been in the news a lot lately that Windows 11 isn't allowed to be installed on PCs without certain requirements, including the TPM 2.0, a chip that was only included in PCs made in 2018 or later. This means that once Windows 10 stops receiving security updates, those PCs will not be able to (officially) run a safe, updated version of Windows anymore. This has led to an estimated 240 million PCs bound for the landfill. Thanks Microsoft! I get you don't want to be seen as the insecure one, but creating this much waste can't be the solution.
(I know nerds, Linux is a thing. I love you but we are not having that conversation. If you want to use Linux on an old PC you are already doing it and you don't need to tell me about it. People need Windows for all sorts of reasons that Linux won't cut.)
So lately I have been helping some under privileged teens get set up with PCs. Their school was giving away their old lab computers, and these kids would usually have no chance to afford even a basic computer. They had their hard drives pulled so I have been setting them up with SSDs, but the question was, what to do about the operating system? So I looked into it and I found out there IS actually a way to bypass Microsoft's system requirement and put Windows 11 on PCs as old as 2010.
You will need: Rufus: An open source ISO burning tool.
A Windows 11 ISO: Available from Microsoft.
A USB Flash Drive, at least 16GB.
A working PC to make the ISO, and a PC from 2018 or older you want to install Windows 11 on.
Here is the guide I used, but I will put it in my own words as well.
Download your Windows 11 ISO, and plug in your USB drive. It will be erased, so don't have anything valuable on it. Run Rufus, select your USB drive in the Device window, and select your Windows 11 ISO with the Select button. (There is supposed to be a feature in Rufus to download your ISO but I couldn't get it to work.?
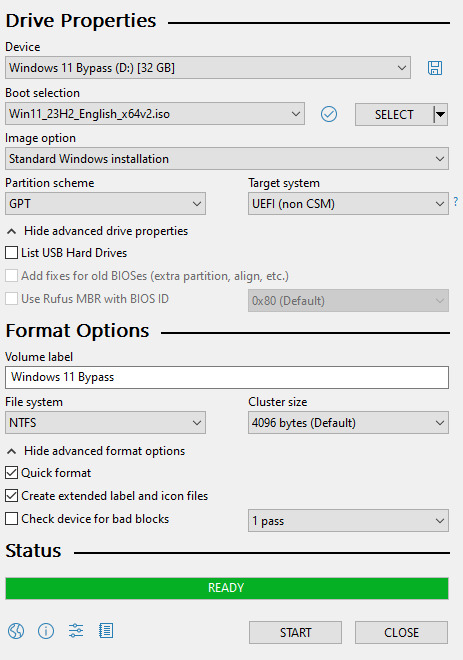
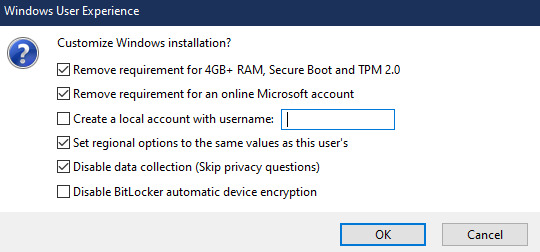
Choose standard windows installation, and follow the screenshot for your settings. Once you are done that, press Start, and then the magic happens. Another window pops up allowing you to remove the system requirements, the need for a microsoft account, and turn off data collecting. Just click the options you want, and press ok to write your iso to a drive.
From there you just need to use the USB drive to install windows. I won't go into details here, but here are some resources if you don't know how to do it.
Boot your PC from a USB Drive
Install Windows 11 from USB Drive
If you had a licensed copy of Windows 10, Windows 11 will already be licensed. If you don't, then perhaps you can use some kind of... Activation Scripts for Microsoft software, that will allow you to activate them. Of course I cannot link such tools here. So there you go, now you can save a PC made from before 2018 from the landfill, and maybe give it to a deserving teen in the process. The more we can extend the lives of technology and keep it out of the trash, the better.
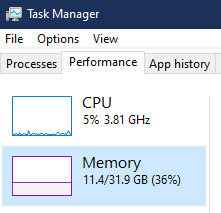
Additional note: This removes the requirement for having 4GB Minimum of RAM, but I think that requirement should honestly be higher. Windows 11 will be unusable slow on any system with below 8GB of RAM. 8GB is the minimum I think you should have before trying this but it still really not enough for modern use outside of light web and office work. I wouldn't recommend trying this on anything with 4GB or less. I am honestly shocked they are still selling brand new Windows 11 PCs with 4GB of ram. If you're not sure how much RAM you have, you can find out in the performance tab of Task Manager in Windows, if you click the More Details icon on the bottom right. If you don't have enough, RAM for old systems is super cheap and widely available so it would definitely be worth upgrading if you have a ram starved machine you'd like to give a new life.
#Windows#Windows 11#tech#tech advice#pc#TPM 2.0#rufus#open source#open source software#technology#tech tips
725 notes
·
View notes
Text
I recently made a post about Severance that speculated about what Lumon is doing, based on all the evidence we’ve been given so far. And in my theory crafting I posited that the severance procedure is being marketed to the general public as a convenient way for you to bypass unpleasant situations, but in actuality what Lumon is hoping for is to create millions of sleeper agents for their corporate interests. I mean, the OTC proves that you can wake innies up whenever and that the separation isn’t exclusive to the Lumon building. And the shit they’re doing to Gemma indicates that you can have more than one innie.
So imagine my surprise when I found out Ben Stiller published a short story that acts as a companion piece to Severance, and in this short story that theory I came up with is basically confirmed!
The short story follow a different branch of Lumon where a woman working at MDR manages to make contact with her innie through a coded language she had developed as a child and which isn’t detectable by the code detectors. By passing notes between her innie and outtie she learns that when certain MDR files are completed they often correspond to tragic events on the outside. A rival companies proprietary software mysteriously fire bombed hours after a MDR file with a similar name was completed for example. Scared about what this could mean she tries to raise awareness about it, and promptly her innie gets punished by Lumon, and then shortly afterwards the protagonist herself mysteriously dies in a car accident.
This short story heavily implies that whatever the files are that MDR are refining have real world consequences. It implies that severed people might be planted all over the world and Lumon can activate them whenever to perform a certain task (plant a bomb, smuggle information, dispose of a threat, etc) and the outtie would be none the wiser. And if they’re doing that already, imagine how much power and control they’d have if the general population were to buy in to getting the severance procedure.
The short story is called The Lexington Letter by the way, in case anyone is curious.
71 notes
·
View notes
Text
alt text under cut
Alt National Park Service·
Let’s get into the details. Musk’s staffers have been caught plugging external hard drives into federal agency systems and reportedly locking others out of private rooms to perform—who knows what actions. This behavior violates key cybersecurity laws under FISMA and NIST guidelines, which are designed to protect sensitive federal information. Here’s why this is a serious problem.
Federal systems are strictly regulated, allowing only approved devices to connect. Unauthorized external drives can introduce viruses, ransomware, or other harmful software that may compromise entire networks and disrupt essential operations. This puts system stability and continuity of services at risk, endangering critical infrastructure.
These devices could also be used to steal or damage critical information, including personal data for millions of Americans—such as Social Security recipients and taxpayers. Unauthorized access creates significant vulnerabilities, exposing sensitive data to the risk of cyberattacks. Such attacks could cripple vital services and compromise the privacy and safety of millions of people.
Additionally, federal agencies have strict access controls to prevent unauthorized data manipulation or theft. When unauthorized devices are connected, these protections are bypassed, allowing unauthorized users to potentially alter or extract sensitive data. This undermines system integrity and opens the door to both internal and external threats.
External drives also often lack essential security features, such as encryption and antivirus scanning, making them vulnerable to cybercriminal exploitation. These security gaps further increase the risk of data breaches and system compromise, which can have far-reaching consequences.
Federal systems handle trillions of dollars in payments and manage personal data for millions of U.S. citizens. By bypassing cybersecurity laws and protocols, Musk’s staffers are putting these systems—and the public—at serious risk. This activity is illegal, reckless, and unacceptable. Immediate oversight and intervention are necessary to stop these violations!
64 notes
·
View notes
Text
How to Write Trades and Cultures More Effectively
When developing characters, it's crucial to consider both small and major aspects of their identities. Even if certain details don’t make it into the final story, understanding everything about your character helps define their goals, personality, and role within the plot.
Among these elements, two critical aspects are trade and culture—both shape how a character interacts with their world and influences their decisions. In this post, I’ll explore why trades and backgrounds matter, how they impact character development, and ways to integrate them into storytelling.
What Are Trades?
Trades refer to a character’s occupation, skills, or specialized knowledge—whether they’re in a formal profession or have learned a craft through experience.
Why Trades Matter in Character Development
A character’s trade plays a major role in shaping their skills, mindset, experiences, and worldview. It influences:
- How they approach problems
- Their daily interactions
- Their values and priorities
For example:
- A doctor sees life through healing and responsibility. They might be compassionate, skilled at managing people, and prioritize others' well-being—or, if motivated by money, they could take advantage of patients instead.
- A soldier fights for what they believe in. They often display discipline, resilience, and loyalty but may also struggle with past traumas no one else understands.
These elements help define character motivation and strengthen storytelling, showing why a character makes certain choices and how they evolve over time.
How Backgrounds Shape Character Perspectives
A character’s upbringing, culture, education, and personal experiences shape their personality and beliefs. This influences their decision-making, relationships, and moral outlook.
Key Factors That Shape Backgrounds:
- Wealth – Characters raised in financial stability may value status and image, while those from poverty may prioritize resourcefulness and survival.
- Family Dynamics – A character raised in a loving home may express warmth, while one from a chaotic household may struggle with relationships or seek independence.
- Hardships – Facing difficulties can make a character more compassionate or more guarded, depending on how they respond to challenges.
- Privilege – Some characters may be unaware of societal struggles, assuming others have the same opportunities they do. Others challenge privilege, striving for fairness.
How Location Influences Backgrounds
A character’s surroundings shape expectations, skills, and behaviors:
- City Life – Fast-paced and demanding, often leading to characters who value efficiency and precision.
- Rural or Tribal Life – Strong emphasis on self-sufficiency, community, and survival skills.
- Nomadic or Remote Living – Adaptability, resourcefulness, and deep connection with nature.
Understanding regional influences ensures characters feel authentic and rooted in their environment.
Examples of Careers & Trades
Here’s a diverse mix of occupations and trades to consider for your characters:
Skilled Trades & Hands-On Careers
- Carpenter, Electrician, Plumber, Mechanic, Blacksmith, Welder, Tailor
Medical & Science-Related Professions
- Doctor, Nurse, Pharmacist, Biologist, Psychologist, Chemist, Researcher
Military & Law Enforcement
- Soldier, Police Officer, Spy, FBI Agent, Bodyguard, Detective
Creative & Artistic Careers
- Writer, Painter, Actor, Musician, Graphic Designer, Photographer, Film Director
Business & Technology
- Entrepreneur, Software Developer, Engineer, Accountant, Analyst, Marketing Expert
Education & Mentorship
- Teacher, Professor, Tutor, Historian, Librarian, Public Speaker
Survival & Adventure-Based Trades
- Explorer, Sailor, Ranger, Astronaut, Survivalist, Guide
Unconventional Careers
- Hacker, Fortune Teller, Stunt Performer, Cryptologist, Auctioneer, Game Developer
How Trades & Backgrounds Impact Character Growth
Each profession requires specific skills, emotions, and beliefs, making characters unique within their role. This shapes:
- Problem-solving abilities
- Resilience and adaptability
- Patience, empathy, and integrity
A well-developed character evolves naturally, with their trade and background seamlessly fitting into their personal growth.
How to Effectively Integrate Trades & Backgrounds into Your Story
1. Research Thoroughly – Every culture and profession has unique nuances. Realism enhances authenticity and respect for diverse experiences.
2. Build Around the Character Arc – Design a character’s skills, motivations, and weaknesses to align with their growth and trade.
3. Consider Cultural Influence – A profession may be viewed differently across cultures, requiring accurate representation.
4. Avoid Stereotypes – Even characters within the same trade or culture should have individual personalities and experiences.
5. Expand Beyond Their Career – A character’s interests, hobbies, and struggles should extend beyond their occupation, making them multidimensional.
Conclusion
Thoughtfully integrating trades and backgrounds adds realism, depth, and emotional weight to storytelling. By crafting characters with unique experiences and skill sets, writers create immersive worlds that resonate with audiences.
Developing these elements will help shape memorable characters who feel rooted in their world—characters who stand out and keep readers engaged.
Happy writing!
#writing community#creative writing#writing tips#writingjourney#fiction writing#character development#writing inspiration#story building#buildbettercharacters#cultural representation#author life
52 notes
·
View notes
Text
The Brutalist’s most intriguing and controversial technical feature points forward rather than back: in January, the film’s editor Dávid Jancsó revealed that he and Corbet used tools from AI speech software company Respeecher to make the Hungarian-language dialogue spoken by Adrien Brody (who plays the protagonist, Hungarian émigré architect László Tóth) and Felicity Jones (who plays Tóth’s wife Erzsébet) sound more Hungarian. In response to the ensuing backlash, Corbet clarified that the actors worked “for months” with a dialect coach to perfect their accents; AI was used “in Hungarian language dialogue editing only, specifically to refine certain vowels and letters for accuracy.” In this way, Corbet seemed to suggest, the production’s two central performances were protected against the howls of outrage that would have erupted from the world’s 14 million native Hungarian speakers had The Brutalist made it to screens with Brody and Jones playing linguistically unconvincing Magyars. Far from offending the idea of originality and authorship in performance, AI in fact saved Brody and Jones from committing crimes against the Uralic language family; I shudder even to imagine how comically inept their performances might have been without this technological assist, a catastrophe of fumbled agglutinations, misplaced geminates, and amateur-hour syllable stresses that would have no doubt robbed The Brutalist of much of its awards season élan. This all seems a little silly, not to say hypocritical. Defenders of this slimy deception claim the use of AI in film is no different than CGI or automated dialogue replacement, tools commonly deployed in the editing suite for picture and audio enhancement. But CGI and ADR don’t tamper with the substance of a performance, which is what’s at issue here. Few of us will have any appreciation for the corrected accents in The Brutalist: as is the case, I imagine, for most of the people who’ve seen the film, I don’t speak Hungarian. But I do speak bullshit, and that’s what this feels like. This is not to argue that synthetic co-pilots and assistants of the type that have proliferated in recent years hold no utility at all. Beyond the creative sector, AI’s potential and applications are limitless, and the technology seems poised to unleash a bold new era of growth and optimization. AI will enable smoother reductions in headcount by giving managers more granular data on the output and sentiment of unproductive workers; it will allow loan sharks and crypto scammers to get better at customer service; it will offer health insurance companies the flexibility to more meaningfully tie premiums to diet, lifestyle, and sociability, creating billions in savings; it will help surveillance and private security solution providers improve their expertise in facial recognition and gait analysis; it will power a revolution in effective “pre-targeting” for the Big Pharma, buy-now-pay-later, and drone industries. Within just a few years advances like these will unlock massive productivity gains that we’ll all be able to enjoy in hell, since the energy-hungry data centers on which generative AI relies will have fried the planet and humanity will be extinct.
3 March 2025
37 notes
·
View notes
Text
you can tell when someone has been thoroughly housebroken by having a call center or a retail job because they're this combination of people-pleasing to a pitiable degree and helpless due to only being able to execute tasks that have been dictated to them in a meticulously step by step way. they're too used to being at the whims of a capricious manager. they're too afraid to apply force or presence, lest they slip-up and get reprimanded. and like, I get it, I'm very introverted and people-pleasey too, it's brutal out there, but it's tiring to be on the other end of interacting with these people in a work setting and have to find a way to nicely explain over and over that there doesn't exist a roadmap neatly laying out what exact performance is expected of every small interaction. that if you want to get better at using some resources or software it's best to experiment with it on your own (muscle memory > recall memory). what actually makes this all annoying is that some of them will hate being told this, because ambiguity intimidates them. they've been so thoroughly whipped that autonomy is overwhelming and burdensome. they want to be a part of the machine. hentai mindbreak doujin have nothing on whatever this is.
71 notes
·
View notes
Text

Let’s get into the details. Musk’s staffers have been caught plugging external hard drives into federal agency systems and reportedly locking others out of private rooms to perform—who knows what actions. This behavior violates key cybersecurity laws under FISMA and NIST guidelines, which are designed to protect sensitive federal information. Here’s why this is a serious problem.
Federal systems are strictly regulated, allowing only approved devices to connect. Unauthorized external drives can introduce viruses, ransomware, or other harmful software that may compromise entire networks and disrupt essential operations. This puts system stability and continuity of services at risk, endangering critical infrastructure.
These devices could also be used to steal or damage critical information, including personal data for millions of Americans—such as Social Security recipients and taxpayers. Unauthorized access creates significant vulnerabilities, exposing sensitive data to the risk of cyberattacks. Such attacks could cripple vital services and compromise the privacy and safety of millions of people.
Additionally, federal agencies have strict access controls to prevent unauthorized data manipulation or theft. When unauthorized devices are connected, these protections are bypassed, allowing unauthorized users to potentially alter or extract sensitive data. This undermines system integrity and opens the door to both internal and external threats.
External drives also often lack essential security features, such as encryption and antivirus scanning, making them vulnerable to cybercriminal exploitation. These security gaps further increase the risk of data breaches and system compromise, which can have far-reaching consequences.
Federal systems handle trillions of dollars in payments and manage personal data for millions of U.S. citizens. By bypassing cybersecurity laws and protocols, Musk’s staffers are putting these systems—and the public—at serious risk. This activity is illegal, reckless, and unacceptable. Immediate oversight and intervention are necessary to stop these violations!
42 notes
·
View notes
Text
Subprime gadgets

I'm on tour with my new, nationally bestselling novel The Bezzle! Catch me THIS SUNDAY in ANAHEIM at WONDERCON: YA Fantasy, Room 207, 10 a.m.; Signing, 11 a.m.; Teaching Writing, 2 p.m., Room 213CD.

The promise of feudal security: "Surrender control over your digital life so that we, the wise, giant corporation, can ensure that you aren't tricked into catastrophic blunders that expose you to harm":
https://locusmag.com/2021/01/cory-doctorow-neofeudalism-and-the-digital-manor/
The tech giant is a feudal warlord whose platform is a fortress; move into the fortress and the warlord will defend you against the bandits roaming the lawless land beyond its walls.
That's the promise, here's the failure: What happens when the warlord decides to attack you? If a tech giant decides to do something that harms you, the fortress becomes a prison and the thick walls keep you in.
Apple does this all the time: "click this box and we will use our control over our platform to stop Facebook from spying on you" (Ios as fortress). "No matter what box you click, we will spy on you and because we control which apps you can install, we can stop you from blocking our spying" (Ios as prison):
https://pluralistic.net/2022/11/14/luxury-surveillance/#liar-liar
But it's not just Apple – any corporation that arrogates to itself the right to override your own choices about your technology will eventually yield to temptation, using that veto to help itself at your expense:
https://pluralistic.net/2023/07/28/microincentives-and-enshittification/
Once the corporation puts the gun on the mantelpiece in Act One, they're begging their KPI-obsessed managers to take it down and shoot you in the head with it in anticipation of of their annual Act Three performance review:
https://pluralistic.net/2023/12/08/playstationed/#tyler-james-hill
One particularly pernicious form of control is "trusted computing" and its handmaiden, "remote attestation." Broadly, this is when a device is designed to gather information about how it is configured and to send verifiable testaments about that configuration to third parties, even if you want to lie to those people:
https://www.eff.org/deeplinks/2023/08/your-computer-should-say-what-you-tell-it-say-1
New HP printers are designed to continuously monitor how you use them – and data-mine the documents you print for marketing data. You have to hand over a credit-card in order to use them, and HP reserves the right to fine you if your printer is unreachable, which would frustrate their ability to spy on you and charge you rent:
https://arstechnica.com/gadgets/2024/02/hp-wants-you-to-pay-up-to-36-month-to-rent-a-printer-that-it-monitors/
Under normal circumstances, this technological attack would prompt a defense, like an aftermarket mod that prevents your printer's computer from monitoring you. This is "adversarial interoperability," a once-common technological move:
https://www.eff.org/deeplinks/2019/10/adversarial-interoperability
An adversarial interoperator seeking to protect HP printer users from HP could gin up fake telemetry to send to HP, so they wouldn't be able to tell that you'd seized the means of computation, triggering fines charged to your credit card.
Enter remote attestation: if HP can create a sealed "trusted platform module" or a (less reliable) "secure enclave" that gathers and cryptographically signs information about which software your printer is running, HP can detect when you have modified it. They can force your printer to rat you out – to spill your secrets to your enemy.
Remote attestation is already a reliable feature of mobile platforms, allowing agencies and corporations whose services you use to make sure that you're perfectly defenseless – not blocking ads or tracking, or doing anything else that shifts power from them to you – before they agree to communicate with your device.
What's more, these "trusted computing" systems aren't just technological impediments to your digital wellbeing – they also carry the force of law. Under Section 1201 of the Digital Millennium Copyright Act, these snitch-chips are "an effective means of access control" which means that anyone who helps you bypass them faces a $500,000 fine and a five-year prison sentence for a first offense.
Feudal security builds fortresses out of trusted computing and remote attestation and promises to use them to defend you from marauders. Remote attestation lets them determine whether your device has been compromised by someone seeking to harm you – it gives them a reliable testament about your device's configuration even if your device has been poisoned by bandits:
https://pluralistic.net/2020/12/05/trusting-trust/#thompsons-devil
The fact that you can't override your computer's remote attestations means that you can't be tricked into doing so. That's a part of your computer that belongs to the manufacturer, not you, and it only takes orders from its owner. So long as the benevolent dictator remains benevolent, this is a protective against your own lapses, follies and missteps. But if the corporate warlord turns bandit, this makes you powerless to stop them from devouring you whole.
With that out of the way, let's talk about debt.
Debt is a normal feature of any economy, but today's debt plays a different role from the normal debt that characterized life before wages stagnated and inequality skyrocketed. 40 years ago, neoliberalism – with its assaults on unions and regulations – kicked off a multigenerational process of taking wealth away from working people to make the rich richer.
Have you ever watched a genius pickpocket like Apollo Robbins work? When Robins lifts your wristwatch, he curls his fingers around your wrist, expertly adding pressure to simulate the effect of a watchband, even as he takes away your watch. Then, he gradually releases his grip, so slowly that you don't even notice:
https://www.reddit.com/r/nextfuckinglevel/comments/ppqjya/apollo_robbins_a_master_pickpocket_effortlessly/
For the wealthy to successfully impoverish the rest of us, they had to provide something that made us feel like we were still doing OK, even as they stole our wages, our savings, and our futures. So, even as they shipped our jobs overseas in search of weak environmental laws and weaker labor protection, they shared some of the savings with us, letting us buy more with less. But if your wages keep stagnating, it doesn't matter how cheap a big-screen TV gets, because you're tapped out.
So in tandem with cheap goods from overseas sweatshops, we got easy credit: access to debt. As wages fell, debt rose up to fill the gap. For a while, it's felt OK. Your wages might be falling off, the cost of health care and university might be skyrocketing, but everything was getting cheaper, it was so easy to borrow, and your principal asset – your family home – was going up in value, too.
This period was a "bezzle," John Kenneth Galbraith's name for "The magic interval when a confidence trickster knows he has the money he has appropriated but the victim does not yet understand that he has lost it." It's the moment after Apollo Robbins has your watch but before you notice it's gone. In that moment, both you and Robbins feel like you have a watch – the world's supply of watch-derived happiness actually goes up for a moment.
There's a natural limit to debt-fueled consumption: as Michael Hudson says, "debts that can't be paid, won't be paid." Once the debtor owes more than they can pay back – or even service – creditors become less willing to advance credit to them. Worse, they start to demand the right to liquidate the debtor's assets. That can trigger some pretty intense political instability, especially when the only substantial asset most debtors own is the roof over their heads:
https://pluralistic.net/2022/11/06/the-end-of-the-road-to-serfdom/
"Debts that can't be paid, won't be paid," but that doesn't stop creditors from trying to get blood from our stones. As more of us became bankrupt, the bankruptcy system was gutted, turned into a punitive measure designed to terrorize people into continuing to pay down their debts long past the point where they can reasonably do so:
https://pluralistic.net/2022/10/09/bankruptcy-protects-fake-people-brutalizes-real-ones/
Enter "subprime" – loans advanced to people who stand no meaningful chance of every paying them back. We all remember the subprime housing bubble, in which complex and deceptive mortgages were extended to borrowers on the promise that they could either flip or remortgage their house before the subprime mortgages detonated when their "teaser rates" expired and the price of staying in your home doubled or tripled.
Subprime housing loans were extended on the belief that people would meekly render themselves homeless once the music stopped, forfeiting all the money they'd plowed into their homes because the contract said they had to. For a brief minute there, it looked like there would be a rebellion against mass foreclosure, but then Obama and Timothy Geithner decreed that millions of Americans would have to lose their homes to "foam the runways" for the banks:
https://wallstreetonparade.com/2012/08/how-treasury-secretary-geithner-foamed-the-runways-with-childrens-shattered-lives/
That's one way to run a subprime shop: offer predatory loans to people who can't afford them and then confiscate their assets when they – inevitably – fail to pay their debts off.
But there's another form of subprime, familiar to loan sharks through the ages: lend money at punitive interest rates, such that the borrower can never repay the debt, and then terrorize the borrower into making payments for as long as possible. Do this right and the borrower will pay you several times the value of the loan, and still owe you a bundle. If the borrower ever earns anything, you'll have a claim on it. Think of Americans who borrowed $79,000 to go to university, paid back $190,000 and still owe $236,000:
https://pluralistic.net/2020/12/04/kawaski-trawick/#strike-debt
This kind of loan-sharking is profitable, but labor-intensive. It requires that the debtor make payments they fundamentally can't afford. The usurer needs to get their straw right down into the very bottom of the borrower's milkshake and suck up every drop. You need to convince the debtor to sell their wedding ring, then dip into their kid's college fund, then steal their father's coin collection, and, then break into cars to steal the stereos. It takes a lot of person-to-person work to keep your sucker sufficiently motivated to do all that.
This is where digital meets subprime. There's $1T worth of subprime car-loans in America. These are pure predation: the lender sells a beater to a mark, offering a low down-payment loan with a low initial interest rate. The borrower makes payments at that rate for a couple of months, but then the rate blows up to more than they can afford.
Trusted computing makes this marginal racket into a serious industry. First, there's the ability of the car to narc you out to the repo man by reporting on its location. Tesla does one better: if you get behind in your payments, your Tesla immobilizes itself and phones home, waits for the repo man to come to the parking lot, then it backs itself out of the spot while honking its horn and flashing its lights:
https://tiremeetsroad.com/2021/03/18/tesla-allegedly-remotely-unlocks-model-3-owners-car-uses-smart-summon-to-help-repo-agent/
That immobilization trick shows how a canny subprime car-lender can combine the two kinds of subprime: they can secure the loan against an asset (the car), but also coerce borrowers into prioritizing repayment over other necessities of life. After your car immobilizes itself, you just might decide to call the dealership and put down your credit card, even if that means not being able to afford groceries or child support or rent.
One thing we can say about digital tools: they're flexible. Any sadistic motivational technique a lender can dream up, a computerized device can execute. The subprime car market relies on a spectrum of coercive tactics: cars that immobilize themselves, sure, but how about cars that turn on their speakers to max and blare a continuous recording telling you that you're a deadbeat and demanding payment?
https://archive.nytimes.com/dealbook.nytimes.com/2014/09/24/miss-a-payment-good-luck-moving-that-car/
The more a subprime lender can rely on a gadget to torment you on their behalf, the more loans they can issue. Here, at last, is a form of automation-driven mass unemployment: normally, an economy that has been fully captured by wealthy oligarchs needs squadrons of cruel arm-breakers to convince the plebs to prioritize debt service over survival. The infinitely flexible, tireless digital arm-breakers enabled by trusted computing have deprived all of those skilled torturers of their rightful employment:
https://pluralistic.net/2021/04/02/innovation-unlocks-markets/#digital-arm-breakers
The world leader in trusted computing isn't cars, though – it's phones. Long before anyone figured out how to make a car take orders from its manufacturer over the objections of its driver, Apple and Google were inventing "curating computing" whose app stores determined which software you could run and how you could run it.
Back in 2021, Indian subprime lenders hit on the strategy of securing their loans by loading borrowers' phones up with digital arm-breaking software:
https://restofworld.org/2021/loans-that-hijack-your-phone-are-coming-to-india/
The software would gather statistics on your app usage. When you missed a payment, the phone would block you from accessing your most frequently used app. If that didn't motivate you to pay, you'd lose your second-most favorite app, then your third, fourth, etc.
This kind of digital arm-breaking is only possible if your phone is designed to prioritize remote instructions – from the manufacturer and its app makers – over your own. It also only works if the digital arm-breaking company can confirm that you haven't jailbroken your phone, which might allow you to send fake data back saying that your apps have been disabled, while you continue to use those apps. In other words, this kind of digital sadism only works if you've got trusted computing and remote attestation.
Enter "Device Lock Controller," an app that comes pre-installed on some Google Pixel phones. To quote from the app's description: "Device Lock Controller enables device management for credit providers. Your provider can remotely restrict access to your device if you don't make payments":
https://lemmy.world/post/13359866
Google's pitch to Android users is that their "walled garden" is a fortress that keeps people who want to do bad things to you from reaching you. But they're pre-installing software that turns the fortress into a prison that you can't escape if they decide to let someone come after you.
There's a certain kind of economist who looks at these forms of automated, fine-grained punishments and sees nothing but a tool for producing an "efficient market" in debt. For them, the ability to automate arm-breaking results in loans being offered to good, hardworking people who would otherwise be deprived of credit, because lenders will judge that these borrowers can be "incentivized" into continuing payments even to the point of total destitution.
This is classic efficient market hypothesis brain worms, the kind of cognitive dead-end that you arrive at when you conceive of people in purely economic terms, without considering the power relationships between them. It's a dead end you navigate to if you only think about things as they are today – vast numbers of indebted people who command fewer assets and lower wages than at any time since WWII – and treat this as a "natural" state: "how can these poors expect to be offered more debt unless they agree to have their all-important pocket computers booby-trapped?"

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/03/29/boobytrap/#device-lock-controller

Image: Oatsy (modified) https://www.flickr.com/photos/oatsy40/21647688003
CC BY 2.0 https://creativecommons.org/licenses/by/2.0/
#pluralistic#debt#subprime#armbreakers#mobile#google#android#apps#drm#technological self-determination#efficient market hypothesis brainworms#law and political economy#gadgets#boobytraps#app stores#curated computing#og app#trusted computing
230 notes
·
View notes
Text
.𖥔 ݁ ˖ computer specs explained - processors ˖ ݁݁ 𖥔.
shopping for a laptop (or determining what your laptop can do) can be confusing. even as a computer science major, it took me a long time to get familiar with all of it! in this series, i'm breaking down each term, number, and specification, so you can determine what's best for you.
if you have more specific questions, my askbox is open, or feel free to send me a DM. let's talk processors!



what does the processor do?
the processor (also called the CPU) is the brain of a computer. it executes all the instructions needed to run applications. your internet browser, video editing software, games, and messaging apps are all managed by your processor. the code that makes them run is sent to your processor piece by piece, and the processor executes all of them simultaneously. it's the most important part of your computer!
what do the numbers mean?
two things determine how well your processor will perform: number of cores and clock speed. these numbers are often thrown all together when talking about the processor: e.g., "AMD Ryzen 7 7730U 2.0GHz Processor". AMD is the brand, Ryzen 7 7730U is the specific model, and 2.0GHz is the clock speed.
the number of cores determines how many of those individual instructions the computer can run at once. in other words, it's how much "brain space" your processor has. more cores means your computer can run more complicated programs.
each core may have 1 or 2 threads, which divide the core into pieces to run smaller programs more efficiently. a complicated program may need multiple threads or multiple cores, but simple programs can fit onto a single thread of a single core.
the clock speed is measured in gigahertz (GHz), which you may recognize as a frequency measurement. without getting too much into how processors work, the clock speed indicates how quickly your computer can execute instructions. it has to do with how quickly electrical pulses are sent through the CPU.
most CPUs have at least 4 cores and a clock speed of around 2.0GHz. modern Intel brand processors have two types of core: higher clock speed "P-cores" (for performance), and lower clock speed "E-cores" (for efficiency). in this case, the important number of cores to look at are the P-cores; more E-cores will just mean your machine is better at multi-tasking.
rowan recommends...
...as much processor as you'll realistically use. don't spend a lot on a powerful processor if you only surf the web, and don't try to cut corners if you like to play games or use video editing software.
there are two major CPU manufacturers: Intel and AMD. i've only personally used Intel CPUs, but most people won't notice the difference between an Intel and an AMD. if you're choosing between two similarly priced processors, choose the one with a higher clock speed.
for surfing the web, word processors, and small apps like Discord or Spotify: an Intel i3/AMD Ryzen 3 is perfectly fine.
for simple programming, music production, or games like Minecraft or Stardew Valley: choose an Intel i5/AMD Ryzen 5 with a clock speed of at least 2.0GHz.
for video editing, rendering, 3D modeling, complex programming, or high-performance games: an Intel i7 or i9, or an AMD Ryzen 7, with as high of a clock speed as you can afford.

thanks for reading and good luck! again, if you have specific questions, feel free to ask a question or DM. :3
next in series: memory
#lab#tags for reach ->#codeblr#studyblr#wonyoungism#glow up#it girl#becoming her#productivity#tech#vintage tech#academia#pc games#computer advice#this is a girlblog#horror game protagonist#dream girl#coquette#fawn aesthetic
35 notes
·
View notes
Note
reading that Tarantulas and Prowl processor overload ask has revived one of my recently dormant fetishes
(this is an expansion on the forced porn download ask actually, wasn't really done b4 sending)
Prowl's archives just being a massive database of miscellaneous data, which seems like a fully practical thing that he'd do for simulation work at first glance, but in truth, he just never deletes anything because he gets off to the feeling of being just sooooo full in places no physical sensation can reach.
He wasn't always like this, you see. Prowl used to maintain good software management habits. He'd defrag according to a strict schedule, used connection buffers often and cleared his processing queues before recharge. He would never think twice about netdiving into shady websites with nasty popups, let alone download anything from there. But eventually, as his processors develop at that exponential pace his handlers noticed upon bringing him online, Prowl got bolder.
Bold enough to make a slip up and plug into a corrupt mainframe, triggering that forced download and kickstarting his fetish for good. He barely remembers anything about that incident other than an overwhelming mental barrage of arousal. Sometimes Prowl wonders if his colleagues at the time knew just what was literally going through his head as he slumped over on the console, seizing in place as they frantically tried to disconnect him safely. Maybe they caught the scent of his overload under his panels, and chose not to say anything.
Prowl would of course say that he was perfectly fine after that incident, but he'd be haunted by that instance of utter bliss he'd felt when like 30 terrabytes of ERP chatlogs and erotic flashgames burned through his neural circuitry. Eventually, he'd start by visiting a library. Full of clean and safe data to indulge in. Then he started logging all non-confidential precinct data, like routine security footage that's get deleted anyways, and dispatch call recordings. Then he started downloading from legal websites, then onto not so legal ones.
He even has backup and extra hard drives stored in his office and habisuite in plain sight, since no one else but other archivists and data specialists would catch on to his kink in the first place. Every once in a while, he'd plug himself into all these units and just let all that data flood through him, his fans and cooling systems squealing in effort to keep up with the deluge of information forcing it's way through his staticy brain, reducing his overclocked cognitive units into jello as his RAM gets consumed by pure uncontrollable math.
He loves the feel of his mind being pounded by googols of nonsense, it makes him hornier than anything else. He'd save anything from the internet, books and numeric databases are his usual go tos; high definition media are a must, the more graphically and audially intensive the better; the most unoptimized and performance heavy video games, anything that would fill up his hungry battle computer until it's full to bursting and melting.
Sometimes when he feels extra naughty, he'd even fire up the various malware and viruses the Spec Ops team would bring back, on top of all the seedy ones he'd find online. He'd trigger them in his processor and lie back in his berth, finger his fluttering pussy and feel the malicious software start tearing through his brain as his battle computer instinctively fights back, making him feel soooo hot all over. And every time he overloads, it sweeps all of his progress, and the self cleaning protocols will just have to restart as he writhes helplessly in the dark of his room.
Software sanctity? Fuck that, he'd hit anything as long as it demolishes his brain and make him into a silly, messy, spasming horny mess. A real dataslut.
god this is so good. He's quite literally overloading his processor out. It's almost like an addiction. Of course, Prowl could stop any time he wants... he could, he just doesn't want to! After a while, pumping his head full of junk data and malicious viruses is the only way Prowl can even have a fulfilling orgasm. Being full of miscellaneous data is just not enough. It's a pleasant pressure in his constantly calculating brain, yes, but if he wants to cum, he needs something stronger. He'll keep frying his brain inside of his helm as long as he gets to feel that electrifying thrill of his battle computer struggling to deflect the attacks on his mainframe.
It feels like he's falling apart at the circuits, delicate wiring so hot that it's disintegrating into dust, and all he can do is frantically rub his soaking wet valve through it all, optics bright and staring off into space as his HUD floods with nonsense. All his senses are completely taken over by the foreign malware, all he knows is that he feels so good.
Honestly, I wonder what would happen if he got stuck like that. Just for a day or two. And someone had to find him in his apartment, face twisted in pure bliss as his frame keeps twitching even after countless hours of continuous overloads. Of course, Prowl's processor gets cleaned out after that, yet he can't help but want to repeat it... to feel so absolutely stuffed and overwhelmed with data that he's just a wet, helpless thing. To give up control and let his processor sink into endless pleasure.
But for now, he's got a morning shift at the precinct to finish.
50 notes
·
View notes